Report on Biometric Authentication Methods: Security and Comparison
VerifiedAdded on 2019/12/28
|22
|4890
|366
Report
AI Summary
This report provides a comprehensive overview of biometric authentication, exploring its advantages and disadvantages compared to traditional password and PIN-based systems. It begins with an introduction to the concept of biometric authentication, emphasizing its role in enhancing security and usability. The report then delves into the different types of biometrics, including physiological (fingerprints, eyes, DNA, face, handprints, voice) and behavioral (signature, gait, keystrokes) methods, providing detailed descriptions of each. A significant portion of the report is dedicated to analyzing the advantages of biometric authentication, such as its uniqueness and convenience, while also addressing its drawbacks, including potential limitations, cost, and privacy concerns. The report includes a comparison between biometric authentication and traditional methods, followed by a conclusion summarizing the key findings and discussing the future of biometric security. References to books and websites are provided for further research.

Biometric authentication over
Password and PIN authentication
Submitted by:
Date:
Page 1 of 22
Password and PIN authentication
Submitted by:
Date:
Page 1 of 22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Content
1. Introduction
2. The risk assessment process
3. Biometric is one authentication method
4. TYPES AND DESCRIPTION OF BIOMETRICS
5. PHYSIOLOGICAL BIOMETRIC
6. BEHAVIORAL BIOMETRIC
7. Advantages of the biometric authentication
8. Drawbacks of the biometric authentication
9. Comparison
10. Conclusions
Page 2 of 22
1. Introduction
2. The risk assessment process
3. Biometric is one authentication method
4. TYPES AND DESCRIPTION OF BIOMETRICS
5. PHYSIOLOGICAL BIOMETRIC
6. BEHAVIORAL BIOMETRIC
7. Advantages of the biometric authentication
8. Drawbacks of the biometric authentication
9. Comparison
10. Conclusions
Page 2 of 22

Introduction
Passwords have dominated human-computer authentication for 50 years
despite consensus among researchers that we need something more secure
and deserve something more user friendly. Much published research has
focused on specific aspects of the problem that can be easily formalized but
do not actually have a major influence on real-world design goals, which are
never authentication per se, but rather protection of user accounts and
sensitive data. As an example of this disconnect, academic research often
recommends strict password-composition policies (such as length
requirements and mandating digits and non-alphabetic characters) despite
the lack of evidence that they actually reduce harm.
We argue that critically revisiting authentication as a whole and passwords’
role therein is required to understand today’s situation and provide a
meaningful look ahead. Passwords were originally deployed in the 1960s for
access to time-shared mainframe computers, an environment
unrecognizable by today’s Web users. Many practices have survived with few
changes even if no longer appropriate. While partly attributable to inertia,
this also represents a failure of the academic literature to provide
approaches that are convincingly better than current practices.
Financial institutions engaging in any form of Internet banking should have
effective and reliable methods to authenticate customers. An effective
authentication system is necessary for compliance with requirements to
safeguard customer information,3 to prevent money laundering and terrorist
financing,4 to reduce fraud, to inhibit identity theft, and to promote the legal
enforceability of their electronic agreements and transactions. The risks of
doing business with unauthorized or incorrectly identified persons in an
Internet banking environment can result in financial loss and reputation
damage through fraud, disclosure of customer information, corruption of
data, or unenforceable agreements.
There are a variety of technologies and methodologies financial institutions
can use to authenticate customers. These methods include the use of
customer passwords, personal identification numbers (PINs), digital
certificates using a public key infrastructure (PKI), physical devices such as
smart cards, one-time passwords (OTPs), USB plug-ins or other types of
“tokens”, transaction profile scripts, biometric identification, and others. (The
appendix to this guidance contains a more detailed discussion of
Page 3 of 22
Passwords have dominated human-computer authentication for 50 years
despite consensus among researchers that we need something more secure
and deserve something more user friendly. Much published research has
focused on specific aspects of the problem that can be easily formalized but
do not actually have a major influence on real-world design goals, which are
never authentication per se, but rather protection of user accounts and
sensitive data. As an example of this disconnect, academic research often
recommends strict password-composition policies (such as length
requirements and mandating digits and non-alphabetic characters) despite
the lack of evidence that they actually reduce harm.
We argue that critically revisiting authentication as a whole and passwords’
role therein is required to understand today’s situation and provide a
meaningful look ahead. Passwords were originally deployed in the 1960s for
access to time-shared mainframe computers, an environment
unrecognizable by today’s Web users. Many practices have survived with few
changes even if no longer appropriate. While partly attributable to inertia,
this also represents a failure of the academic literature to provide
approaches that are convincingly better than current practices.
Financial institutions engaging in any form of Internet banking should have
effective and reliable methods to authenticate customers. An effective
authentication system is necessary for compliance with requirements to
safeguard customer information,3 to prevent money laundering and terrorist
financing,4 to reduce fraud, to inhibit identity theft, and to promote the legal
enforceability of their electronic agreements and transactions. The risks of
doing business with unauthorized or incorrectly identified persons in an
Internet banking environment can result in financial loss and reputation
damage through fraud, disclosure of customer information, corruption of
data, or unenforceable agreements.
There are a variety of technologies and methodologies financial institutions
can use to authenticate customers. These methods include the use of
customer passwords, personal identification numbers (PINs), digital
certificates using a public key infrastructure (PKI), physical devices such as
smart cards, one-time passwords (OTPs), USB plug-ins or other types of
“tokens”, transaction profile scripts, biometric identification, and others. (The
appendix to this guidance contains a more detailed discussion of
Page 3 of 22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

authentication techniques.) The level of risk protection afforded by each of
these techniques varies.
The selection and use of authentication technologies and methods should
depend upon the results of the financial institution’s risk assessment
process. Authentication methodologies involve three basic “factors”:
o Something the user knows (e.g., password, PIN);
o Something the user has (e.g., ATM card, smart card); and
o Something the user is (e.g., biometric characteristic, such as a
fingerprint).
The risk assessment process should:
o Identify all transactions and levels of access associated with Internet-
based customer products and services;
o Identify and assess the risk mitigation techniques, including
authentication methodologies, employed for each transaction type and
level of access; and
o Include the ability to gauge the effectiveness of risk mitigation
techniques for current and changing risk factors for each transaction
type and level of access.
The security literature distinguishes between online attackers who must
interact with a legitimate party to authenticate and offline attackers who are
limited only in terms of their computational resources.
Superficially, offline attackers are far more powerful, as they typically can
make an unbounded number of guesses and compare them against a known
hash of the password. Yet many additional avenues of attack are available to
the online attacker: stealing the password using client-side malware,
phishing the password using a spoofed site, eavesdropping the password as
it is transmitted, stealing the password from the authentication server,
stealing the password from a second authentication server where the user
has reused it, and subverting the automated password reset process.
A critical observation is that strong passwords do not help against any of
these other attacks. Even the strongest passwords are still static secrets that
can be replayed and are equally vulnerable to phishing, theft, and
Page 4 of 22
these techniques varies.
The selection and use of authentication technologies and methods should
depend upon the results of the financial institution’s risk assessment
process. Authentication methodologies involve three basic “factors”:
o Something the user knows (e.g., password, PIN);
o Something the user has (e.g., ATM card, smart card); and
o Something the user is (e.g., biometric characteristic, such as a
fingerprint).
The risk assessment process should:
o Identify all transactions and levels of access associated with Internet-
based customer products and services;
o Identify and assess the risk mitigation techniques, including
authentication methodologies, employed for each transaction type and
level of access; and
o Include the ability to gauge the effectiveness of risk mitigation
techniques for current and changing risk factors for each transaction
type and level of access.
The security literature distinguishes between online attackers who must
interact with a legitimate party to authenticate and offline attackers who are
limited only in terms of their computational resources.
Superficially, offline attackers are far more powerful, as they typically can
make an unbounded number of guesses and compare them against a known
hash of the password. Yet many additional avenues of attack are available to
the online attacker: stealing the password using client-side malware,
phishing the password using a spoofed site, eavesdropping the password as
it is transmitted, stealing the password from the authentication server,
stealing the password from a second authentication server where the user
has reused it, and subverting the automated password reset process.
A critical observation is that strong passwords do not help against any of
these other attacks. Even the strongest passwords are still static secrets that
can be replayed and are equally vulnerable to phishing, theft, and
Page 4 of 22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
eavesdropping. Mandating stronger passwords does nothing to increase
security against such attacks.
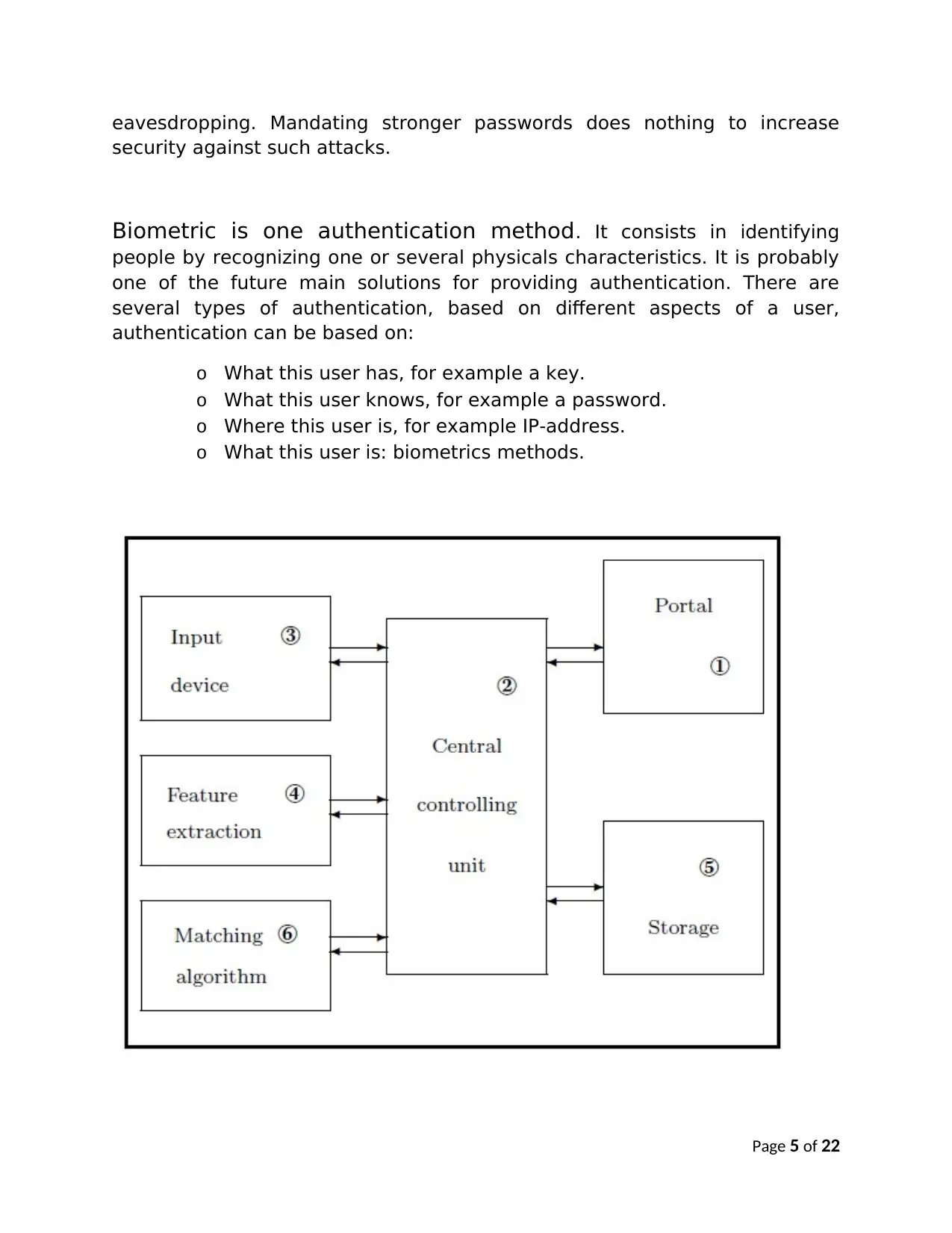
Biometric is one authentication method. It consists in identifying
people by recognizing one or several physicals characteristics. It is probably
one of the future main solutions for providing authentication. There are
several types of authentication, based on different aspects of a user,
authentication can be based on:
o What this user has, for example a key.
o What this user knows, for example a password.
o Where this user is, for example IP-address.
o What this user is: biometrics methods.
Page 5 of 22
security against such attacks.
Biometric is one authentication method. It consists in identifying
people by recognizing one or several physicals characteristics. It is probably
one of the future main solutions for providing authentication. There are
several types of authentication, based on different aspects of a user,
authentication can be based on:
o What this user has, for example a key.
o What this user knows, for example a password.
o Where this user is, for example IP-address.
o What this user is: biometrics methods.
Page 5 of 22
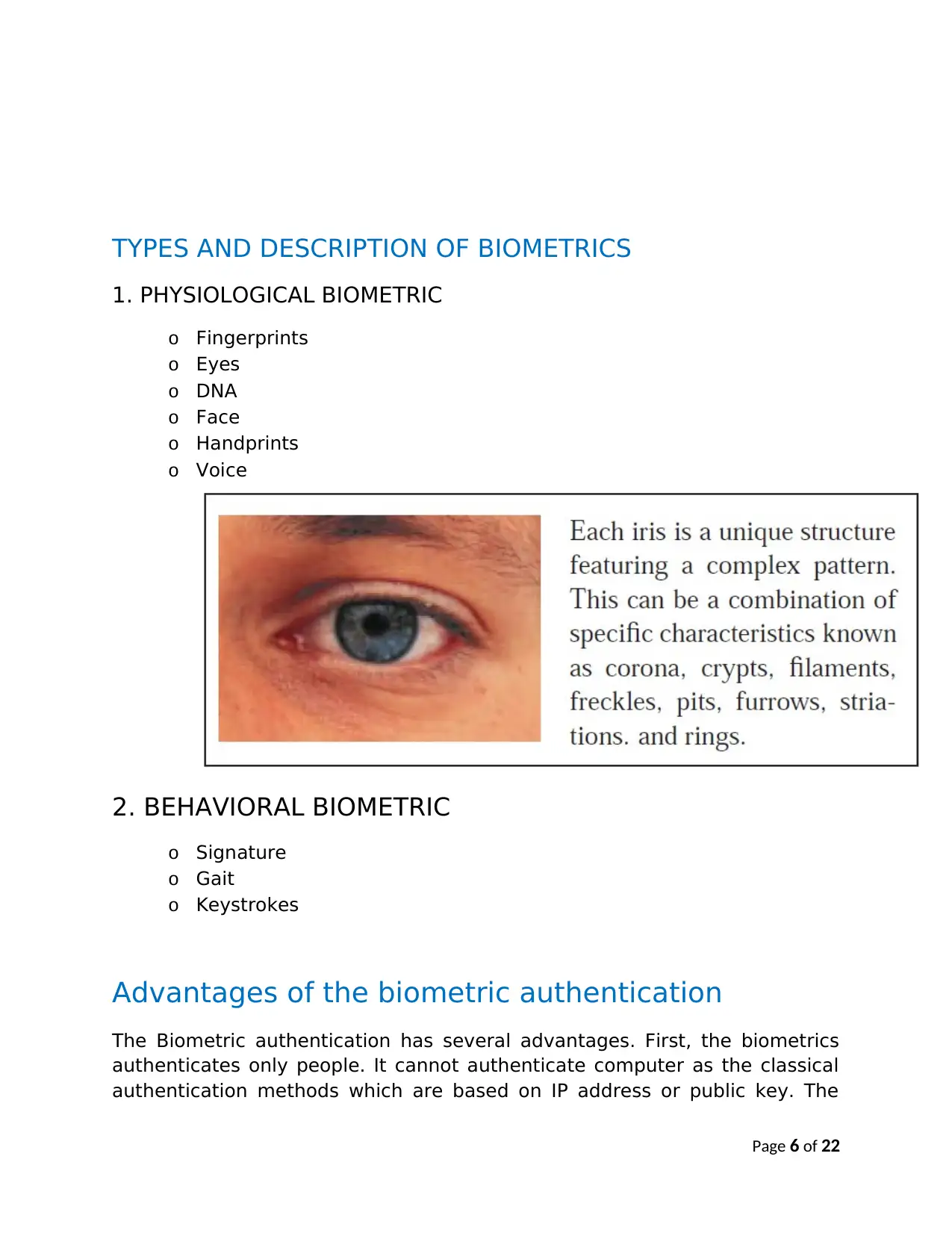
TYPES AND DESCRIPTION OF BIOMETRICS
1. PHYSIOLOGICAL BIOMETRIC
o Fingerprints
o Eyes
o DNA
o Face
o Handprints
o Voice
2. BEHAVIORAL BIOMETRIC
o Signature
o Gait
o Keystrokes
Advantages of the biometric authentication
The Biometric authentication has several advantages. First, the biometrics
authenticates only people. It cannot authenticate computer as the classical
authentication methods which are based on IP address or public key. The
Page 6 of 22
1. PHYSIOLOGICAL BIOMETRIC
o Fingerprints
o Eyes
o DNA
o Face
o Handprints
o Voice
2. BEHAVIORAL BIOMETRIC
o Signature
o Gait
o Keystrokes
Advantages of the biometric authentication
The Biometric authentication has several advantages. First, the biometrics
authenticates only people. It cannot authenticate computer as the classical
authentication methods which are based on IP address or public key. The
Page 6 of 22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

biometric characteristics that are used in authentication systems are unique
for each person.
The major advantage of the biometrics is
that you have always with you your way to authenticate yourself. For
example, you can forget a password or lost an access card. It is impossible to
forget your fingerprint, your gait, your signature. Biometric is more practical
for the user as to remember several passwords for example. It can reduce
the cost of password and access-card administration. As soon as the
biometric system is set up, there is only a few of administration.
In most of the case, it is more difficult to attack a biometric authentication
system as attacking an authentication system based on password or access-
card. You can guess a password or steal an access card. It seems more
difficult to fool a good biometric authentication system.
Drawbacks of the biometric authentication
The first drawback of biometric authentication is that some methods can’t
work for some people. For example, it is impossible to use fingerprint
authentication for someone who has no hands. Some behavioral
authentication methods can’t work if something is changed in your life.
For example, if you have new shoes, perhaps your gait will change, and it
can be a problem to authenticate you. Furthermore, if one of your fingers is
severely hurt, the fingerprints authentication will not work. Some
characteristics as your face can also change with the age. Moreover, most of
the biometrics authentications systems are still in developing state and it
Page 7 of 22
for each person.
The major advantage of the biometrics is
that you have always with you your way to authenticate yourself. For
example, you can forget a password or lost an access card. It is impossible to
forget your fingerprint, your gait, your signature. Biometric is more practical
for the user as to remember several passwords for example. It can reduce
the cost of password and access-card administration. As soon as the
biometric system is set up, there is only a few of administration.
In most of the case, it is more difficult to attack a biometric authentication
system as attacking an authentication system based on password or access-
card. You can guess a password or steal an access card. It seems more
difficult to fool a good biometric authentication system.
Drawbacks of the biometric authentication
The first drawback of biometric authentication is that some methods can’t
work for some people. For example, it is impossible to use fingerprint
authentication for someone who has no hands. Some behavioral
authentication methods can’t work if something is changed in your life.
For example, if you have new shoes, perhaps your gait will change, and it
can be a problem to authenticate you. Furthermore, if one of your fingers is
severely hurt, the fingerprints authentication will not work. Some
characteristics as your face can also change with the age. Moreover, most of
the biometrics authentications systems are still in developing state and it
Page 7 of 22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
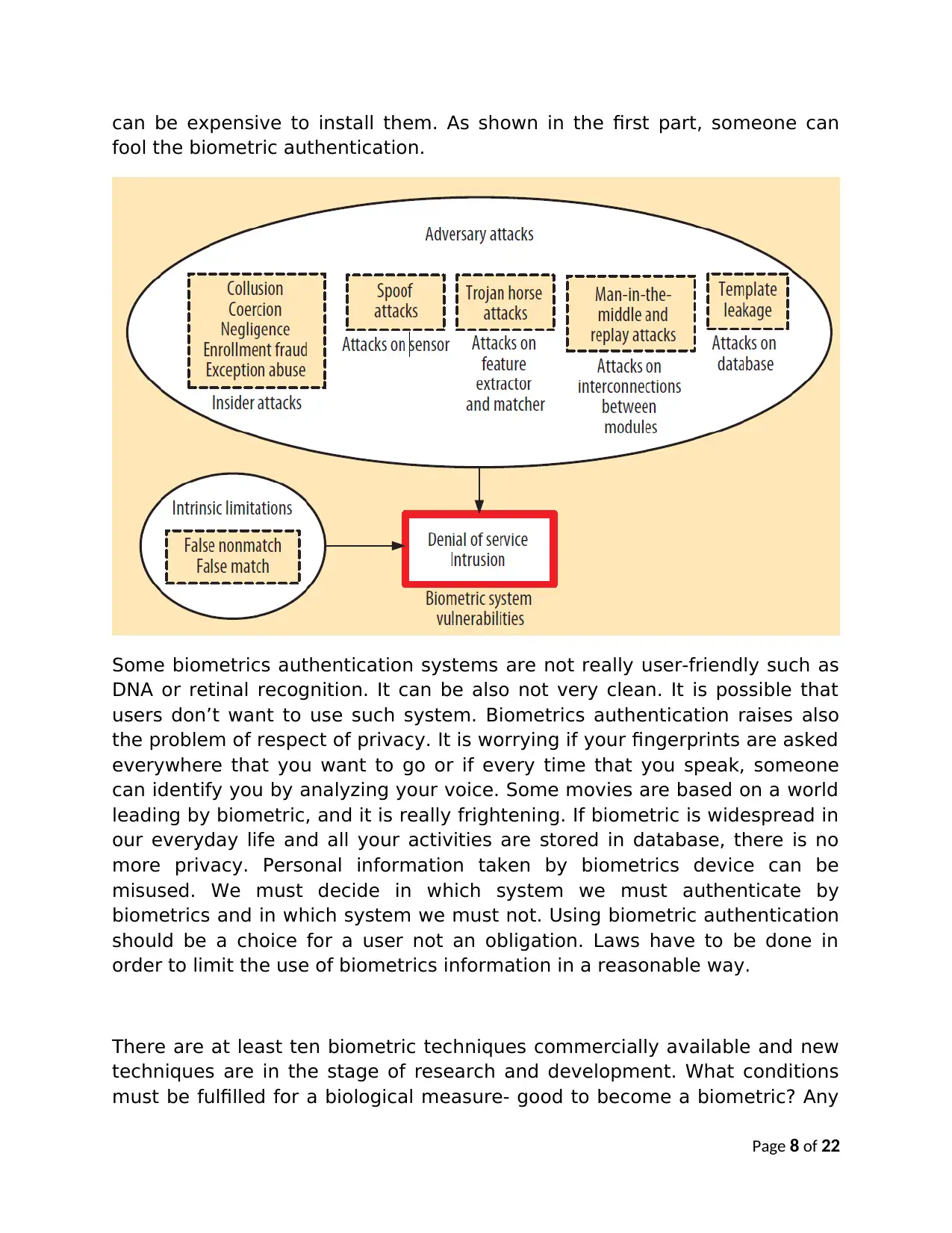
can be expensive to install them. As shown in the first part, someone can
fool the biometric authentication.
Some biometrics authentication systems are not really user-friendly such as
DNA or retinal recognition. It can be also not very clean. It is possible that
users don’t want to use such system. Biometrics authentication raises also
the problem of respect of privacy. It is worrying if your fingerprints are asked
everywhere that you want to go or if every time that you speak, someone
can identify you by analyzing your voice. Some movies are based on a world
leading by biometric, and it is really frightening. If biometric is widespread in
our everyday life and all your activities are stored in database, there is no
more privacy. Personal information taken by biometrics device can be
misused. We must decide in which system we must authenticate by
biometrics and in which system we must not. Using biometric authentication
should be a choice for a user not an obligation. Laws have to be done in
order to limit the use of biometrics information in a reasonable way.
There are at least ten biometric techniques commercially available and new
techniques are in the stage of research and development. What conditions
must be fulfilled for a biological measure- good to become a biometric? Any
Page 8 of 22
fool the biometric authentication.
Some biometrics authentication systems are not really user-friendly such as
DNA or retinal recognition. It can be also not very clean. It is possible that
users don’t want to use such system. Biometrics authentication raises also
the problem of respect of privacy. It is worrying if your fingerprints are asked
everywhere that you want to go or if every time that you speak, someone
can identify you by analyzing your voice. Some movies are based on a world
leading by biometric, and it is really frightening. If biometric is widespread in
our everyday life and all your activities are stored in database, there is no
more privacy. Personal information taken by biometrics device can be
misused. We must decide in which system we must authenticate by
biometrics and in which system we must not. Using biometric authentication
should be a choice for a user not an obligation. Laws have to be done in
order to limit the use of biometrics information in a reasonable way.
There are at least ten biometric techniques commercially available and new
techniques are in the stage of research and development. What conditions
must be fulfilled for a biological measure- good to become a biometric? Any
Page 8 of 22
human physiological or behave- biometrics oral characteristics can become a
biometric provided the following properties are fulfilled.
Universality: This means that every person should have the characteristics. It
is really difficult to get 100% coverage. There are mute people, people
without fingers or with injured eyes. All these cases must be handled.
Uniqueness: This means that no two persons should be the same in terms of
the biometric characteristics. Fingerprints have a high discrimination rate
and the probability of two persons with the same iris is estimated as low as
1: 1052. Identical twins, on the other side, cannot be easily distinguished by
face recognition and DNA-analysis systems.
Permanence: This means that the characteristics should be invariant with
time. While the iris usually remains stable over decades, a person’s face
changes significantly with time. The signature and its dynamics may change
as well and the finger is a frequent subject to injuries.
Collectability: This means that the characteristics must be measured
quantitatively and obtaining the characteristics should be easy. Face
recognition systems are not intrusive and obtaining of a face image is easy.
In the contrast the DNA analysis requires a blood or other bodily sample. The
retina scan is rather intrusive as well.
Performance: This refers to the achievable identification/verification accuracy
and the resources and working or environmental conditions needed to
achieve an acceptable accuracy. The crossover accuracy of iris-based
systems is under 1% and the system is able to compare over 4.
Acceptability: This indicates to what extend people are willing to accept the
biometric system. Face recognition systems are personally not intrusive, but
there are countries where taking pictures of persons is not viable. The retina
scanner requires an infrared laser beam directed through the cornea of the
eye. This is rather invasive and only few users accept this technology.
Page 9 of 22
biometric provided the following properties are fulfilled.
Universality: This means that every person should have the characteristics. It
is really difficult to get 100% coverage. There are mute people, people
without fingers or with injured eyes. All these cases must be handled.
Uniqueness: This means that no two persons should be the same in terms of
the biometric characteristics. Fingerprints have a high discrimination rate
and the probability of two persons with the same iris is estimated as low as
1: 1052. Identical twins, on the other side, cannot be easily distinguished by
face recognition and DNA-analysis systems.
Permanence: This means that the characteristics should be invariant with
time. While the iris usually remains stable over decades, a person’s face
changes significantly with time. The signature and its dynamics may change
as well and the finger is a frequent subject to injuries.
Collectability: This means that the characteristics must be measured
quantitatively and obtaining the characteristics should be easy. Face
recognition systems are not intrusive and obtaining of a face image is easy.
In the contrast the DNA analysis requires a blood or other bodily sample. The
retina scan is rather intrusive as well.
Performance: This refers to the achievable identification/verification accuracy
and the resources and working or environmental conditions needed to
achieve an acceptable accuracy. The crossover accuracy of iris-based
systems is under 1% and the system is able to compare over 4.
Acceptability: This indicates to what extend people are willing to accept the
biometric system. Face recognition systems are personally not intrusive, but
there are countries where taking pictures of persons is not viable. The retina
scanner requires an infrared laser beam directed through the cornea of the
eye. This is rather invasive and only few users accept this technology.
Page 9 of 22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Circumvention: This refers to how difficult it is to fool the system by
fraudulent techniques. An automated access control system that can be
easily fooled with a fingerprint model or a picture of a user’s face does not
provide much security.
Comparison
The currently computed characteristics are then compared with the
characteristics obtained during enrollment. This process is very dependent
on the nature of the biometric technology used. Sometimes the desired
security threshold is a parameter of the matching process, sometimes the
biometric system returns a score within similarity a range. If the system
performs verification then the newly trained characteristics are compared
only with one master template (or with a small number of master templates,
e.g. a set of master templates for a few different fingers). For an
identification request the new characteristics are matched against a large
number of master templates (either against all the records in the database
or if the database is clustered then against the relevant part of the database)
Page 10 of 22
fraudulent techniques. An automated access control system that can be
easily fooled with a fingerprint model or a picture of a user’s face does not
provide much security.
Comparison
The currently computed characteristics are then compared with the
characteristics obtained during enrollment. This process is very dependent
on the nature of the biometric technology used. Sometimes the desired
security threshold is a parameter of the matching process, sometimes the
biometric system returns a score within similarity a range. If the system
performs verification then the newly trained characteristics are compared
only with one master template (or with a small number of master templates,
e.g. a set of master templates for a few different fingers). For an
identification request the new characteristics are matched against a large
number of master templates (either against all the records in the database
or if the database is clustered then against the relevant part of the database)
Page 10 of 22
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusions
Even if the accuracy of the biometric techniques is not perfect yet, there are
many mature biometric systems available now. Proper design and
implementation of the biometric system can indeed increase the overall
security, especially the smartcard based solutions seem to be very
promising. Making a secure biometric system is, however, not as easy as it
might appear. The word biometrics is very often used as a synonym for the
perfect security. This is a misleading view. There are numerous conditions
that must be taken in account when designing a secure biometric system.
First, it is necessary to realize that biometrics are not secrets. This implies be
careful that biometric measurements cannot be used as capability tokens
and it is not secure to generate any cryptographic keys from them. Second,
it is necessary to trust the input device and make the communication link
secure. Third, the input device needs to check the liveness of the person
being measured and the device itself should be verified for example by a
challenge-response protocol.
References:
Books:
[1] Introduction to Computer Security (Matt Bishop)
[2] Network Security- Private Communication in a public world (Charlie
Kaufman, Radia Perlman, Mike Spenicer)
Web:
[3] http://en.wikipedia.org/wiki/Biometrics
[4]http://www.biometrics.dod.mil
[5]http://www.eff.org/Privacy/Surveillance/biometrics/
[6]http://www.globalsecurity.org/security/systems/biometrics.htm
Page 11 of 22
Even if the accuracy of the biometric techniques is not perfect yet, there are
many mature biometric systems available now. Proper design and
implementation of the biometric system can indeed increase the overall
security, especially the smartcard based solutions seem to be very
promising. Making a secure biometric system is, however, not as easy as it
might appear. The word biometrics is very often used as a synonym for the
perfect security. This is a misleading view. There are numerous conditions
that must be taken in account when designing a secure biometric system.
First, it is necessary to realize that biometrics are not secrets. This implies be
careful that biometric measurements cannot be used as capability tokens
and it is not secure to generate any cryptographic keys from them. Second,
it is necessary to trust the input device and make the communication link
secure. Third, the input device needs to check the liveness of the person
being measured and the device itself should be verified for example by a
challenge-response protocol.
References:
Books:
[1] Introduction to Computer Security (Matt Bishop)
[2] Network Security- Private Communication in a public world (Charlie
Kaufman, Radia Perlman, Mike Spenicer)
Web:
[3] http://en.wikipedia.org/wiki/Biometrics
[4]http://www.biometrics.dod.mil
[5]http://www.eff.org/Privacy/Surveillance/biometrics/
[6]http://www.globalsecurity.org/security/systems/biometrics.htm
Page 11 of 22

[7] Common Criteria for Information Technology Security Evaluation, v 2.1,
1999.
[8] Department of Defense (1985). Trusted Computer System Evaluation
Criteria.
[9] Jain, A., Bolle, R. and Pankanti S. (1999). BIOMETRICS: Personal
Identification in Networked Society. Kluwer Academic Publishers. Biometric
Authentication — Security and Usability 13
[10] National Institute of Standards and Technology (1994 and 2001).
Security Requirements for Cryptographic Modules, FIPS PUB 140-1/2.
[11] Newham, E. (1995). The biometric report. SBJ Services.
[12] Maty´aˇs, V., ˇ R´ıha, Z. (2000). Biometric Authentication Systems.
Technical report.
http://www.ecom-monitor.com/papers/biometricsTR2000.pdf.
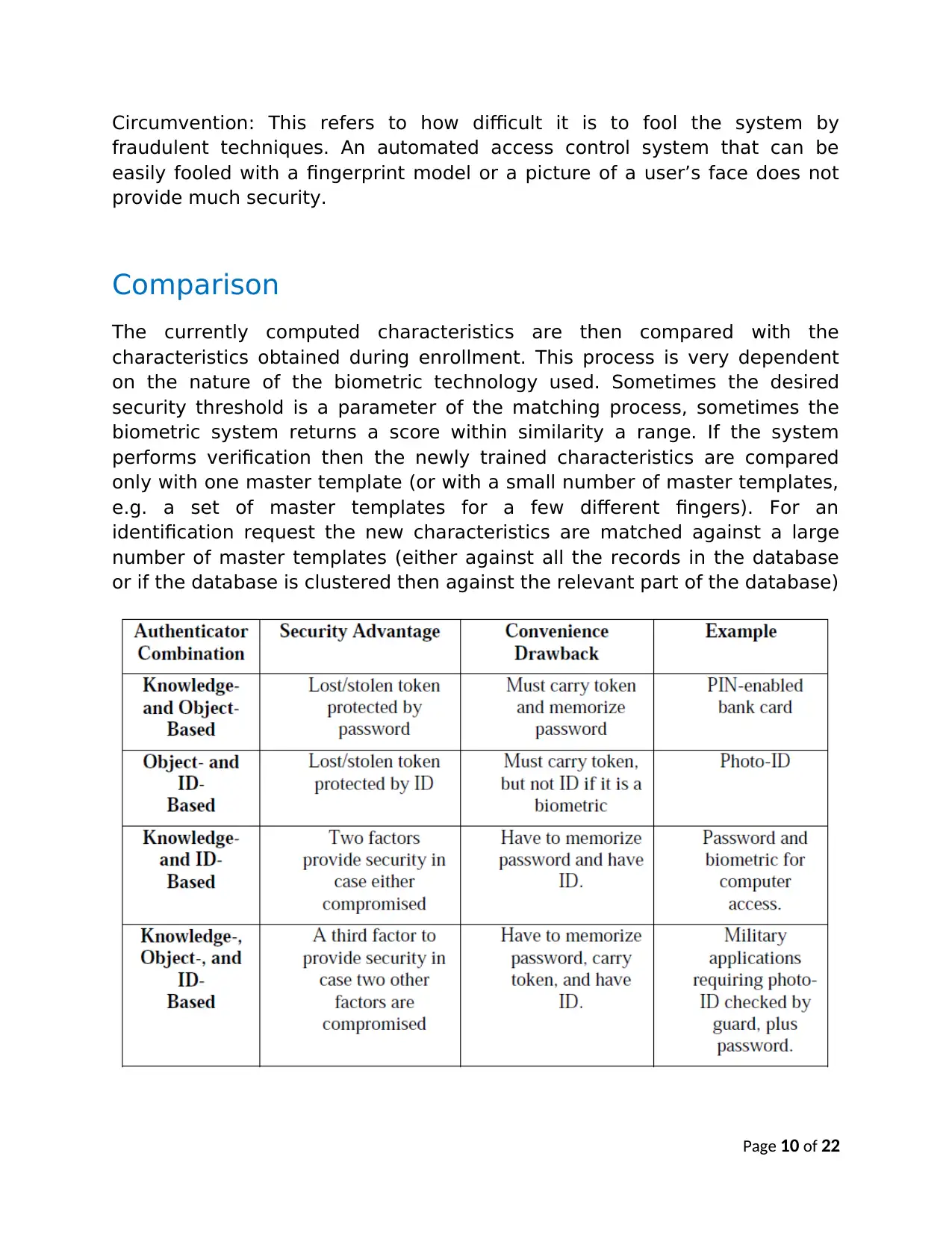
Token authentication in banking industry
Password has been the standard means for user authentication on
computers. However, as users are required to remember more, longer, and
changing passwords, it is evident that a more convenient and secure solution
to user authentication is necessary. This paper examines passwords, security
tokens, and biometrics – which we collectively call authenticators – and
compares these authenticators and their combinations. We examine
effectiveness against several attacks and suitability for particular security
specifications such as compromise detection and non-repudiation.
Examples of authenticator combinations and protocols are described to show
tradeoffs and solutions that meet chosen, practical requirements. The paper
endeavors to offer a comprehensive picture of user authentication solutions
for the purposes of evaluating options for use and identifying deficiencies
requiring further research.
Page 12 of 22
1999.
[8] Department of Defense (1985). Trusted Computer System Evaluation
Criteria.
[9] Jain, A., Bolle, R. and Pankanti S. (1999). BIOMETRICS: Personal
Identification in Networked Society. Kluwer Academic Publishers. Biometric
Authentication — Security and Usability 13
[10] National Institute of Standards and Technology (1994 and 2001).
Security Requirements for Cryptographic Modules, FIPS PUB 140-1/2.
[11] Newham, E. (1995). The biometric report. SBJ Services.
[12] Maty´aˇs, V., ˇ R´ıha, Z. (2000). Biometric Authentication Systems.
Technical report.
http://www.ecom-monitor.com/papers/biometricsTR2000.pdf.
Token authentication in banking industry
Password has been the standard means for user authentication on
computers. However, as users are required to remember more, longer, and
changing passwords, it is evident that a more convenient and secure solution
to user authentication is necessary. This paper examines passwords, security
tokens, and biometrics – which we collectively call authenticators – and
compares these authenticators and their combinations. We examine
effectiveness against several attacks and suitability for particular security
specifications such as compromise detection and non-repudiation.
Examples of authenticator combinations and protocols are described to show
tradeoffs and solutions that meet chosen, practical requirements. The paper
endeavors to offer a comprehensive picture of user authentication solutions
for the purposes of evaluating options for use and identifying deficiencies
requiring further research.
Page 12 of 22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





