Comprehensive Report on Biometric Systems, PETs and WSN Security
VerifiedAdded on 2024/06/27
|10
|2590
|244
Report
AI Summary
This report provides an in-depth analysis of biometric systems used for access control, focusing on fingerprint, hand geometry, and iris recognition technologies, detailing their advantages, disadvantages, and applications. It further explores privacy-enhancing technologies (PETs) such as data minimization, data tracking, and anonymity for internet security, illustrating their use with examples. Additionally, the report examines wireless sensor networks (WSNs), outlining their architecture and protocol stack, and discusses various threats and vulnerabilities, including denial-of-service attacks like jamming, collisions, and tampering, offering recommendations for mitigation. The document emphasizes the importance of security and privacy in modern technological landscapes and proposes strategies for enhancing both.
(a) Research into the different types of biometric systems which are currently
available for access control systems. Briefly describe the techniques and
technologies used for each type and discuss the advantages and disadvantages of
the three types below. Give an example application when each type could be
used:
• Fingerprint
• Hand Geometry
• Iris Recognition
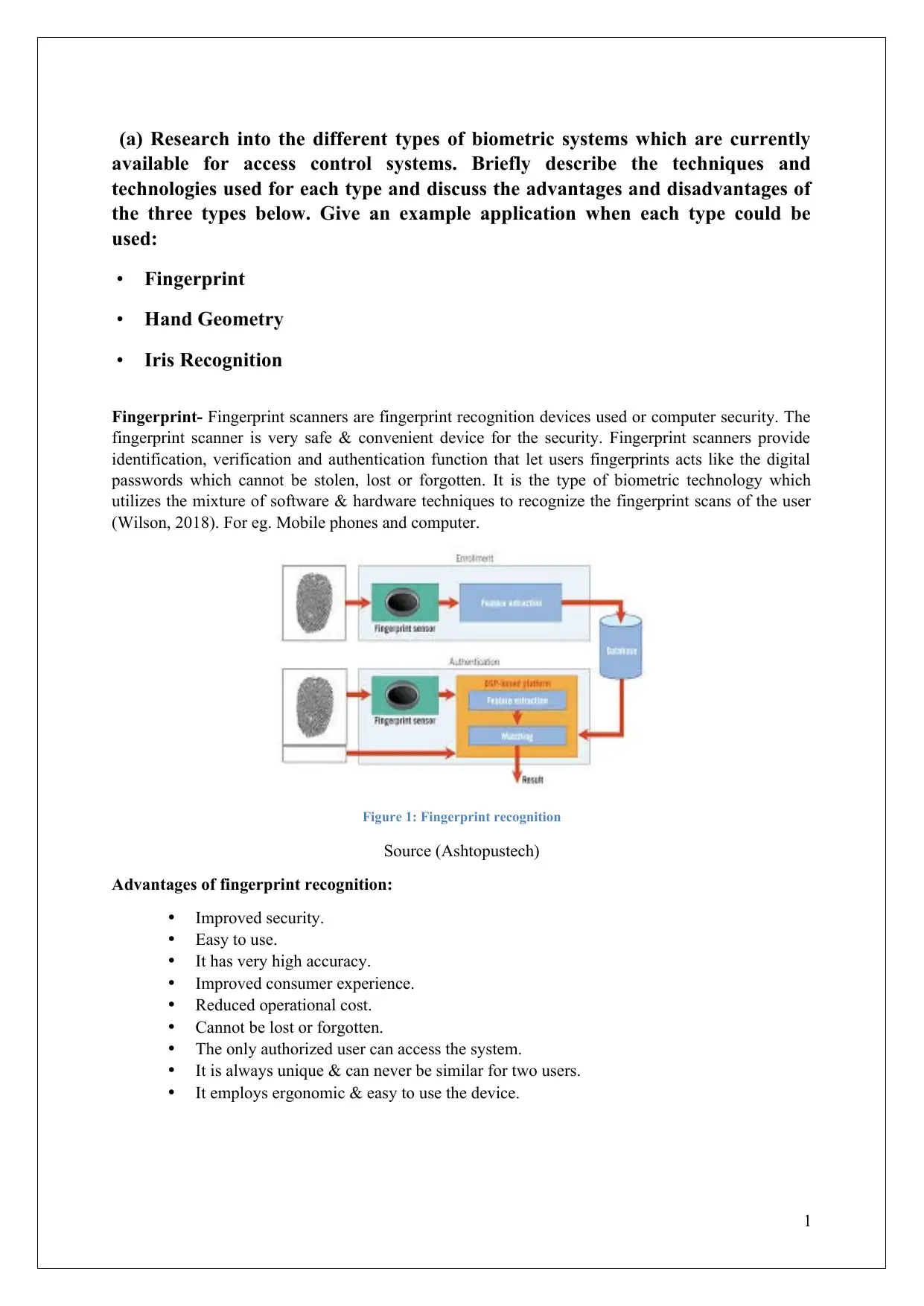
Fingerprint- Fingerprint scanners are fingerprint recognition devices used or computer security. The
fingerprint scanner is very safe & convenient device for the security. Fingerprint scanners provide
identification, verification and authentication function that let users fingerprints acts like the digital
passwords which cannot be stolen, lost or forgotten. It is the type of biometric technology which
utilizes the mixture of software & hardware techniques to recognize the fingerprint scans of the user
(Wilson, 2018). For eg. Mobile phones and computer.
Figure 1: Fingerprint recognition
Source (Ashtopustech)
Advantages of fingerprint recognition:
Improved security.
Easy to use.
It has very high accuracy.
Improved consumer experience.
Reduced operational cost.
Cannot be lost or forgotten.
The only authorized user can access the system.
It is always unique & can never be similar for two users.
It employs ergonomic & easy to use the device.
1
available for access control systems. Briefly describe the techniques and
technologies used for each type and discuss the advantages and disadvantages of
the three types below. Give an example application when each type could be
used:
• Fingerprint
• Hand Geometry
• Iris Recognition
Fingerprint- Fingerprint scanners are fingerprint recognition devices used or computer security. The
fingerprint scanner is very safe & convenient device for the security. Fingerprint scanners provide
identification, verification and authentication function that let users fingerprints acts like the digital
passwords which cannot be stolen, lost or forgotten. It is the type of biometric technology which
utilizes the mixture of software & hardware techniques to recognize the fingerprint scans of the user
(Wilson, 2018). For eg. Mobile phones and computer.
Figure 1: Fingerprint recognition
Source (Ashtopustech)
Advantages of fingerprint recognition:
Improved security.
Easy to use.
It has very high accuracy.
Improved consumer experience.
Reduced operational cost.
Cannot be lost or forgotten.
The only authorized user can access the system.
It is always unique & can never be similar for two users.
It employs ergonomic & easy to use the device.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disadvantages of fingerprint recognition:
The system is not 100% accurate.
It is not possible to reset once compromised.
It requires additional & integration hardware.
Environment & usage can affect measurement (Esguerra, 2016).
Hand geometry- Hand geometry is a type of biometric recognition technique which identifies the
users by their hands’ shape. Hand geometry recognition technique measure users hand dimensions &
compare those dimensions or measurements with the measurements which are stored in the file. This
device uses an easy method to record and measure the length, thickness, width or surface area of
user’s hand.
Advantages of using hand geometry-
Simple, inexpensive and easy to use.
Less intrusive than retinal, fingerprints.
Easy to collect hand geometry data.
It has low computational cost.
Hand geometry biometric is able to operate in the challenging environment.
Hand geometry is a reliable, established core technology.
Hand geometry is based on stable physiological characteristics (Schmitthammer, 2015).
Disadvantages of using hand geometry-
Considerable size.
Very expensive.
Hand geometry recognition is not unique & cannot use in an identification system.
The data size is very large for hand geometry recognition.
Hand geometry has limited accuracy.
Iris recognition- It is the very reliable technique of biometric identification among all the biometric
techniques such as facial, palm vein and fingerprint. Iris recognition used mathematical recognition
technique on the video image for identification. Iris recognition technology is based on the distortion-
free & high-resolution image of irises of the human eye. For eg., Many countries use iris recognition
technology at their borders. These include the Jordan or UAE.
Figure 2: Block diagram of Iris recognition
Source (Research gate)
2
The system is not 100% accurate.
It is not possible to reset once compromised.
It requires additional & integration hardware.
Environment & usage can affect measurement (Esguerra, 2016).
Hand geometry- Hand geometry is a type of biometric recognition technique which identifies the
users by their hands’ shape. Hand geometry recognition technique measure users hand dimensions &
compare those dimensions or measurements with the measurements which are stored in the file. This
device uses an easy method to record and measure the length, thickness, width or surface area of
user’s hand.
Advantages of using hand geometry-
Simple, inexpensive and easy to use.
Less intrusive than retinal, fingerprints.
Easy to collect hand geometry data.
It has low computational cost.
Hand geometry biometric is able to operate in the challenging environment.
Hand geometry is a reliable, established core technology.
Hand geometry is based on stable physiological characteristics (Schmitthammer, 2015).
Disadvantages of using hand geometry-
Considerable size.
Very expensive.
Hand geometry recognition is not unique & cannot use in an identification system.
The data size is very large for hand geometry recognition.
Hand geometry has limited accuracy.
Iris recognition- It is the very reliable technique of biometric identification among all the biometric
techniques such as facial, palm vein and fingerprint. Iris recognition used mathematical recognition
technique on the video image for identification. Iris recognition technology is based on the distortion-
free & high-resolution image of irises of the human eye. For eg., Many countries use iris recognition
technology at their borders. These include the Jordan or UAE.
Figure 2: Block diagram of Iris recognition
Source (Research gate)
2

Advantages of using Iris recognition-
Accuracy- Iris recognition is the best biometric technology in terms of the accuracy. The
false rejection & false acceptance rate is low in this technology.
Scalability-Iris recognition technology is very highly scalable & used in both small and
large-scale programs.
Distance- It can be easily done from a normal distance.
Easy to use- This system is play & plug compared to other techniques of biometric
recognition. It is a very comfortable process for users.
Fast- Iris recognition is very fast biometric recognition technology user can easily
complete within a few seconds.
Randomness- The degree of randomness is very high in iris recognition system which
makes the iris system unique.
Traceable- The decision making and encoding of the iris recognition system are highly
traceable. It takes 30 milliseconds to analysis the image & the subsequent encoding.
Iris recognition is capable of reliable identification as well as verification.
Iris recognition maintains the stability of characteristics.
Disadvantages of using Iris recognition-
Iris recognition has an inclination for the false rejection.
Acquisition of the image requires moderate training and attentiveness.
It requires a lot of memory to store the data (Thakkar, 2018).
3
Accuracy- Iris recognition is the best biometric technology in terms of the accuracy. The
false rejection & false acceptance rate is low in this technology.
Scalability-Iris recognition technology is very highly scalable & used in both small and
large-scale programs.
Distance- It can be easily done from a normal distance.
Easy to use- This system is play & plug compared to other techniques of biometric
recognition. It is a very comfortable process for users.
Fast- Iris recognition is very fast biometric recognition technology user can easily
complete within a few seconds.
Randomness- The degree of randomness is very high in iris recognition system which
makes the iris system unique.
Traceable- The decision making and encoding of the iris recognition system are highly
traceable. It takes 30 milliseconds to analysis the image & the subsequent encoding.
Iris recognition is capable of reliable identification as well as verification.
Iris recognition maintains the stability of characteristics.
Disadvantages of using Iris recognition-
Iris recognition has an inclination for the false rejection.
Acquisition of the image requires moderate training and attentiveness.
It requires a lot of memory to store the data (Thakkar, 2018).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

(b) Other than security concerns, privacy is considered a core value and is
recognized either implicitly or explicitly as a fundamental human right. Privacy-
enhancing technologies (PETs) can be defined as technologies that enforce legal
privacy principles in order to protect and enhance the privacy of users of
information technology. Research and discuss three PETs which can be used on
the Internet. Use examples to illustrate your answer.
Privacy enhancing technologies-
Privacy enhancing technologies is described as specific methods which are used for data protection.
These technologies allow users to protect the privacy of data providers to & handled by application or
services. PET is a system of ICT which measures the security of information by minimizing or
eliminating data thereby preventing unwanted or unnecessary handling of data, without loss of
information system (Kenny, 2018).
The objective of privacy enhancing technologies is to keep the data safe or ensure the user that their
data is confidential.
Data minimization- Data minimization is a privacy principle which requires the applications &
services only process minimum amount of information. The objective of this principle is to minimize
the personal information and data collected or used by the online service providers. Privacy enhancing
technologies in data minimization include a website that intentionally chooses not to store & collect
personal data such as IP addresses, search terms and search history. Data minimization used various
tools to protect the privacy of data by deleting the browsing history or other system activities. An
example of data minimization tool is privacy eraser, which is used to erase all the digital footprints-
cookies, web browser cache, address bar history, browsing history, saved passwords, typed URLs,
search history, temporary files, recent documents, autocomplete form history, and recycle bin. There
are some limitations for protection provided by the private browsing modes such as-
If the malicious has infected the computer system that it can track your online
activities.
If the computer is connected to a commercial network, the commercial network
administrator can potentially see what site has been visited.
The online history is accessed by the internet service provider.
If the system has protection software then they can easily track private browsing
sessions.
Ephemeral communications is another type of data minimization tool which is developed in response
to the permanence of internet conversation. There are some tools which automatically expires video,
messages or other content. Examples of such tools are wickr, Firechat, Snapchat or Confide.
Data tracking- Data tracking is used to manage an individual’s data properly. It also allows the user
to track data disclosure across various sites. Data track tool is used for data tracks which provide the
history of all the online transactions. Data track also provide transparency to the user of their online
transaction.
There are various types of tools which are used to track and manage the data such as
TweetReach.
Klout.
Boradreader
Likealyzer
Mention
4
recognized either implicitly or explicitly as a fundamental human right. Privacy-
enhancing technologies (PETs) can be defined as technologies that enforce legal
privacy principles in order to protect and enhance the privacy of users of
information technology. Research and discuss three PETs which can be used on
the Internet. Use examples to illustrate your answer.
Privacy enhancing technologies-
Privacy enhancing technologies is described as specific methods which are used for data protection.
These technologies allow users to protect the privacy of data providers to & handled by application or
services. PET is a system of ICT which measures the security of information by minimizing or
eliminating data thereby preventing unwanted or unnecessary handling of data, without loss of
information system (Kenny, 2018).
The objective of privacy enhancing technologies is to keep the data safe or ensure the user that their
data is confidential.
Data minimization- Data minimization is a privacy principle which requires the applications &
services only process minimum amount of information. The objective of this principle is to minimize
the personal information and data collected or used by the online service providers. Privacy enhancing
technologies in data minimization include a website that intentionally chooses not to store & collect
personal data such as IP addresses, search terms and search history. Data minimization used various
tools to protect the privacy of data by deleting the browsing history or other system activities. An
example of data minimization tool is privacy eraser, which is used to erase all the digital footprints-
cookies, web browser cache, address bar history, browsing history, saved passwords, typed URLs,
search history, temporary files, recent documents, autocomplete form history, and recycle bin. There
are some limitations for protection provided by the private browsing modes such as-
If the malicious has infected the computer system that it can track your online
activities.
If the computer is connected to a commercial network, the commercial network
administrator can potentially see what site has been visited.
The online history is accessed by the internet service provider.
If the system has protection software then they can easily track private browsing
sessions.
Ephemeral communications is another type of data minimization tool which is developed in response
to the permanence of internet conversation. There are some tools which automatically expires video,
messages or other content. Examples of such tools are wickr, Firechat, Snapchat or Confide.
Data tracking- Data tracking is used to manage an individual’s data properly. It also allows the user
to track data disclosure across various sites. Data track tool is used for data tracks which provide the
history of all the online transactions. Data track also provide transparency to the user of their online
transaction.
There are various types of tools which are used to track and manage the data such as
TweetReach.
Klout.
Boradreader
Likealyzer
Mention
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Social Mention
Google alerts
Anonymity- It is the property of network security. There are various identification/identity states
which are possible ranging from fully identified to fully anonymous. PETs can also allow users to
select the degree of anonymity they wish. Communication anonymizers hide the real identity of the
user & replace the identity with non-traceable identity. Users can be applied to web browsing, peer to
peer networking, mail, instant messaging, VoIP and chat. Tor is most known communications
anonymizers. It is the free or world-wide network on the internet which groups and individuals can
use to connect to the news site, to keep the website from tracking them, instant network service and
other network services. There are various types of anonymity protection such as
Receiver anonymity- The server doesn’t know whom the messages are designated.
Sender anonymity- The receiver doesn’t know who sends the messages.
Unlinkability of receiver and sender- Linkability is a possibility to link between the
various actions on the internet.
Publisher anonymity
Information anonymity
Client anonymity
5
Google alerts
Anonymity- It is the property of network security. There are various identification/identity states
which are possible ranging from fully identified to fully anonymous. PETs can also allow users to
select the degree of anonymity they wish. Communication anonymizers hide the real identity of the
user & replace the identity with non-traceable identity. Users can be applied to web browsing, peer to
peer networking, mail, instant messaging, VoIP and chat. Tor is most known communications
anonymizers. It is the free or world-wide network on the internet which groups and individuals can
use to connect to the news site, to keep the website from tracking them, instant network service and
other network services. There are various types of anonymity protection such as
Receiver anonymity- The server doesn’t know whom the messages are designated.
Sender anonymity- The receiver doesn’t know who sends the messages.
Unlinkability of receiver and sender- Linkability is a possibility to link between the
various actions on the internet.
Publisher anonymity
Information anonymity
Client anonymity
5
(a) Wireless sensor networks (WSNs) can be described as a network of nodes
that makes a collaborative effort in sensing data around its periphery and its
surrounding environment. Research into the area of WSNs and understand the
WSN architecture and protocol stack. Discuss three different types of threats and
vulnerabilities which can be used to attack the WSN. Give your
recommendations on how the threats and vulnerabilities can be mitigated for the
WSN.
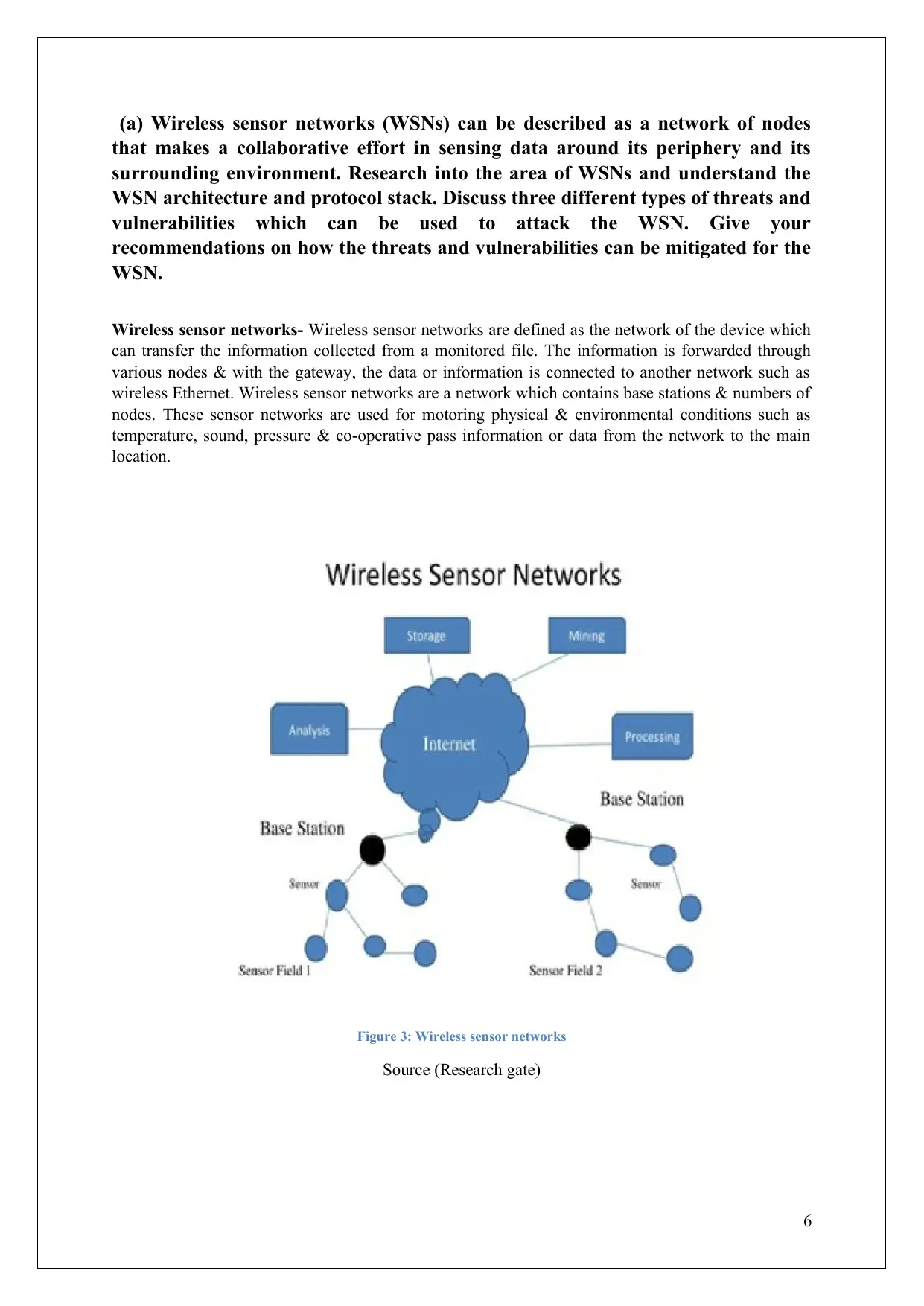
Wireless sensor networks- Wireless sensor networks are defined as the network of the device which
can transfer the information collected from a monitored file. The information is forwarded through
various nodes & with the gateway, the data or information is connected to another network such as
wireless Ethernet. Wireless sensor networks are a network which contains base stations & numbers of
nodes. These sensor networks are used for motoring physical & environmental conditions such as
temperature, sound, pressure & co-operative pass information or data from the network to the main
location.
Figure 3: Wireless sensor networks
Source (Research gate)
6
that makes a collaborative effort in sensing data around its periphery and its
surrounding environment. Research into the area of WSNs and understand the
WSN architecture and protocol stack. Discuss three different types of threats and
vulnerabilities which can be used to attack the WSN. Give your
recommendations on how the threats and vulnerabilities can be mitigated for the
WSN.
Wireless sensor networks- Wireless sensor networks are defined as the network of the device which
can transfer the information collected from a monitored file. The information is forwarded through
various nodes & with the gateway, the data or information is connected to another network such as
wireless Ethernet. Wireless sensor networks are a network which contains base stations & numbers of
nodes. These sensor networks are used for motoring physical & environmental conditions such as
temperature, sound, pressure & co-operative pass information or data from the network to the main
location.
Figure 3: Wireless sensor networks
Source (Research gate)
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The architecture of wireless sensor network- The architecture of WSN follows the OSI model. The
architecture of wireless sensor networks includes 5 layers or 3 cross layers. Sensor network requires 5
layers such as transport, network, data link, physical and application layer. Wireless network used 3
layers to accomplish the network & make the sensor to work together.
Figure 4: Architecture of wireless sensor network
Source (Elprocus)
Application layer- Application layer is used for the traffic management& provides software for
various applications which change the data in the clear form. The sensor network is arranged in
various applications in multiple fields such as military, medical, environmental and agriculture.
Transport layer- Transport layer is used to deliver messages between the hosts. In this layer, data is
traveling in forms of segments. It is also responsible for the creation of end to end connections
between the destination and source IP.
Network Layer- The network layer is used to deliver the data packet from source to destination
across various links. This layer also responsible for the packet forwarding and it breaks the larger data
packets into small data packets.
Data link layer- Data link layer is used to transfer the data or information between the adjacent
network nodes in the wide network. Data bits are decoded, encoded or organized in a data link layer.
Physical layer- This layer deals with the bit level transmission among several devices. The physical
layer is responsible for the selection of modulation & data encryption, signal detection, frequency,
generation of the carrier frequency.
Threats attacks in wireless sensor networks- Security is necessary for a wireless network because
of the broadcast nature of transmission medium.
Attacks on WSN can be categorized from 2 different levels:
1. Attacks against the basic mechanism.
2. Attacks against the security mechanism.
Denial of service attacks- DOS attacks are created by the accidental failure of malicious actions or
nodes. In DOS attacks the opponent efforts to disrupt, destroy or subvert the network.
7
architecture of wireless sensor networks includes 5 layers or 3 cross layers. Sensor network requires 5
layers such as transport, network, data link, physical and application layer. Wireless network used 3
layers to accomplish the network & make the sensor to work together.
Figure 4: Architecture of wireless sensor network
Source (Elprocus)
Application layer- Application layer is used for the traffic management& provides software for
various applications which change the data in the clear form. The sensor network is arranged in
various applications in multiple fields such as military, medical, environmental and agriculture.
Transport layer- Transport layer is used to deliver messages between the hosts. In this layer, data is
traveling in forms of segments. It is also responsible for the creation of end to end connections
between the destination and source IP.
Network Layer- The network layer is used to deliver the data packet from source to destination
across various links. This layer also responsible for the packet forwarding and it breaks the larger data
packets into small data packets.
Data link layer- Data link layer is used to transfer the data or information between the adjacent
network nodes in the wide network. Data bits are decoded, encoded or organized in a data link layer.
Physical layer- This layer deals with the bit level transmission among several devices. The physical
layer is responsible for the selection of modulation & data encryption, signal detection, frequency,
generation of the carrier frequency.
Threats attacks in wireless sensor networks- Security is necessary for a wireless network because
of the broadcast nature of transmission medium.
Attacks on WSN can be categorized from 2 different levels:
1. Attacks against the basic mechanism.
2. Attacks against the security mechanism.
Denial of service attacks- DOS attacks are created by the accidental failure of malicious actions or
nodes. In DOS attacks the opponent efforts to disrupt, destroy or subvert the network.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
• Jamming- It is a denial of service attack at the physical layer. It interfaces with those radio
frequencies which are used by the network’s nodes. It creates resource exhaustion and radio
interface.
• Collisions- It is a denial of service attack at the link layer. When 2 or more nodes try to
communicate on the same network at the same frequency collision occurs. When there is a
collision of a data packet it creates some changes in data portion and causes mismatching of
checksum.
• Tampering- Tampering is a DOS attack in the physical layer. An attacker can access the system
or extract the sensitive information.
• Exhaustion- It is a DOS attack at the data link layer. An attacker may use the repeated collisions
to cause source exhaustion.
• Flooding- It is another type of DOS attack in the transport layer.
• Unfairness- Unfairness is a DOS attack in the transport layer. By using the data link layer attack
an attacker can cause unfairness in the network.
• Desynchronization- Desynchronization is defined as the disruption in an existing connection.
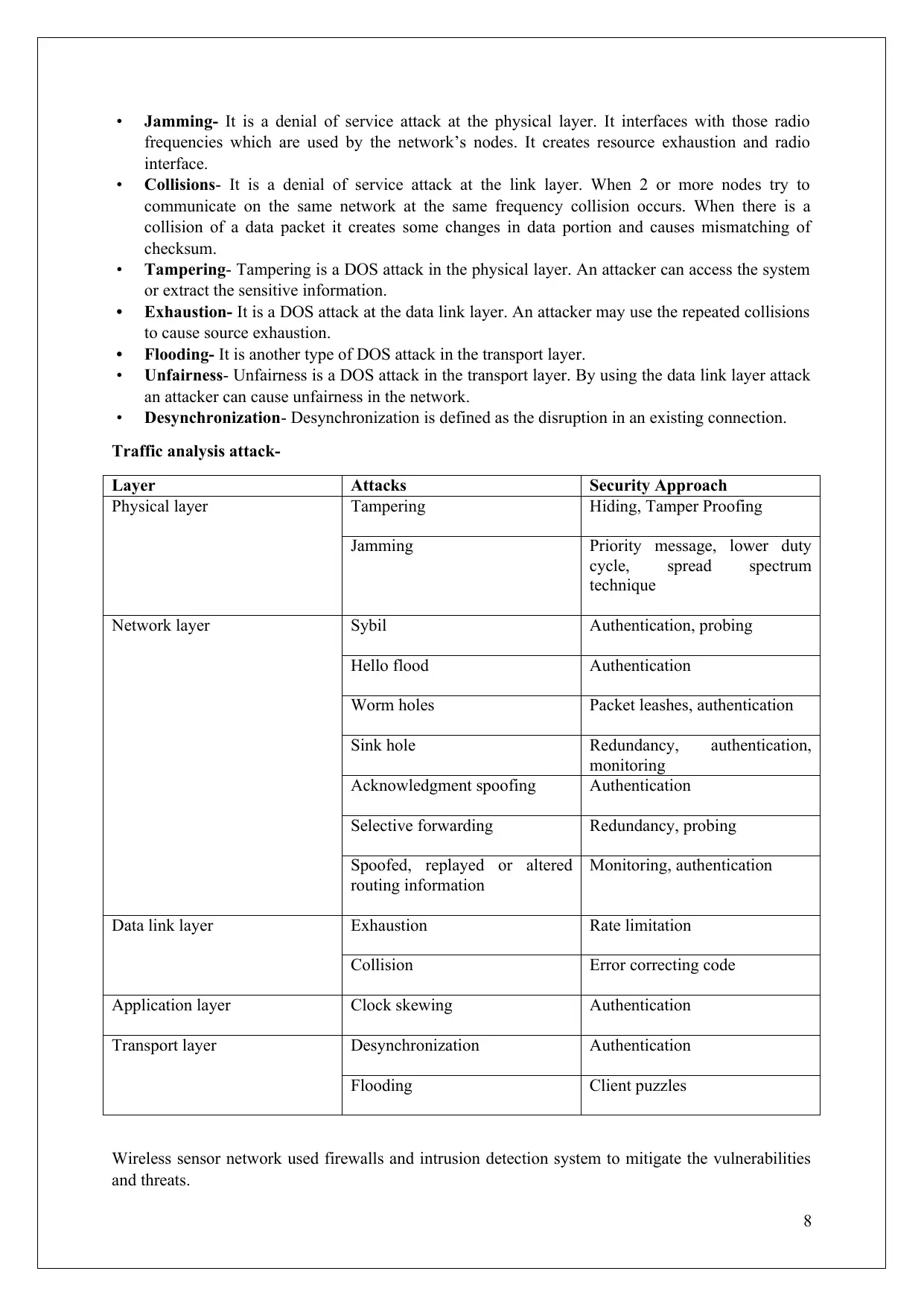
Traffic analysis attack-
Layer Attacks Security Approach
Physical layer Tampering Hiding, Tamper Proofing
Jamming Priority message, lower duty
cycle, spread spectrum
technique
Network layer Sybil Authentication, probing
Hello flood Authentication
Worm holes Packet leashes, authentication
Sink hole Redundancy, authentication,
monitoring
Acknowledgment spoofing Authentication
Selective forwarding Redundancy, probing
Spoofed, replayed or altered
routing information
Monitoring, authentication
Data link layer Exhaustion Rate limitation
Collision Error correcting code
Application layer Clock skewing Authentication
Transport layer Desynchronization Authentication
Flooding Client puzzles
Wireless sensor network used firewalls and intrusion detection system to mitigate the vulnerabilities
and threats.
8
frequencies which are used by the network’s nodes. It creates resource exhaustion and radio
interface.
• Collisions- It is a denial of service attack at the link layer. When 2 or more nodes try to
communicate on the same network at the same frequency collision occurs. When there is a
collision of a data packet it creates some changes in data portion and causes mismatching of
checksum.
• Tampering- Tampering is a DOS attack in the physical layer. An attacker can access the system
or extract the sensitive information.
• Exhaustion- It is a DOS attack at the data link layer. An attacker may use the repeated collisions
to cause source exhaustion.
• Flooding- It is another type of DOS attack in the transport layer.
• Unfairness- Unfairness is a DOS attack in the transport layer. By using the data link layer attack
an attacker can cause unfairness in the network.
• Desynchronization- Desynchronization is defined as the disruption in an existing connection.
Traffic analysis attack-
Layer Attacks Security Approach
Physical layer Tampering Hiding, Tamper Proofing
Jamming Priority message, lower duty
cycle, spread spectrum
technique
Network layer Sybil Authentication, probing
Hello flood Authentication
Worm holes Packet leashes, authentication
Sink hole Redundancy, authentication,
monitoring
Acknowledgment spoofing Authentication
Selective forwarding Redundancy, probing
Spoofed, replayed or altered
routing information
Monitoring, authentication
Data link layer Exhaustion Rate limitation
Collision Error correcting code
Application layer Clock skewing Authentication
Transport layer Desynchronization Authentication
Flooding Client puzzles
Wireless sensor network used firewalls and intrusion detection system to mitigate the vulnerabilities
and threats.
8
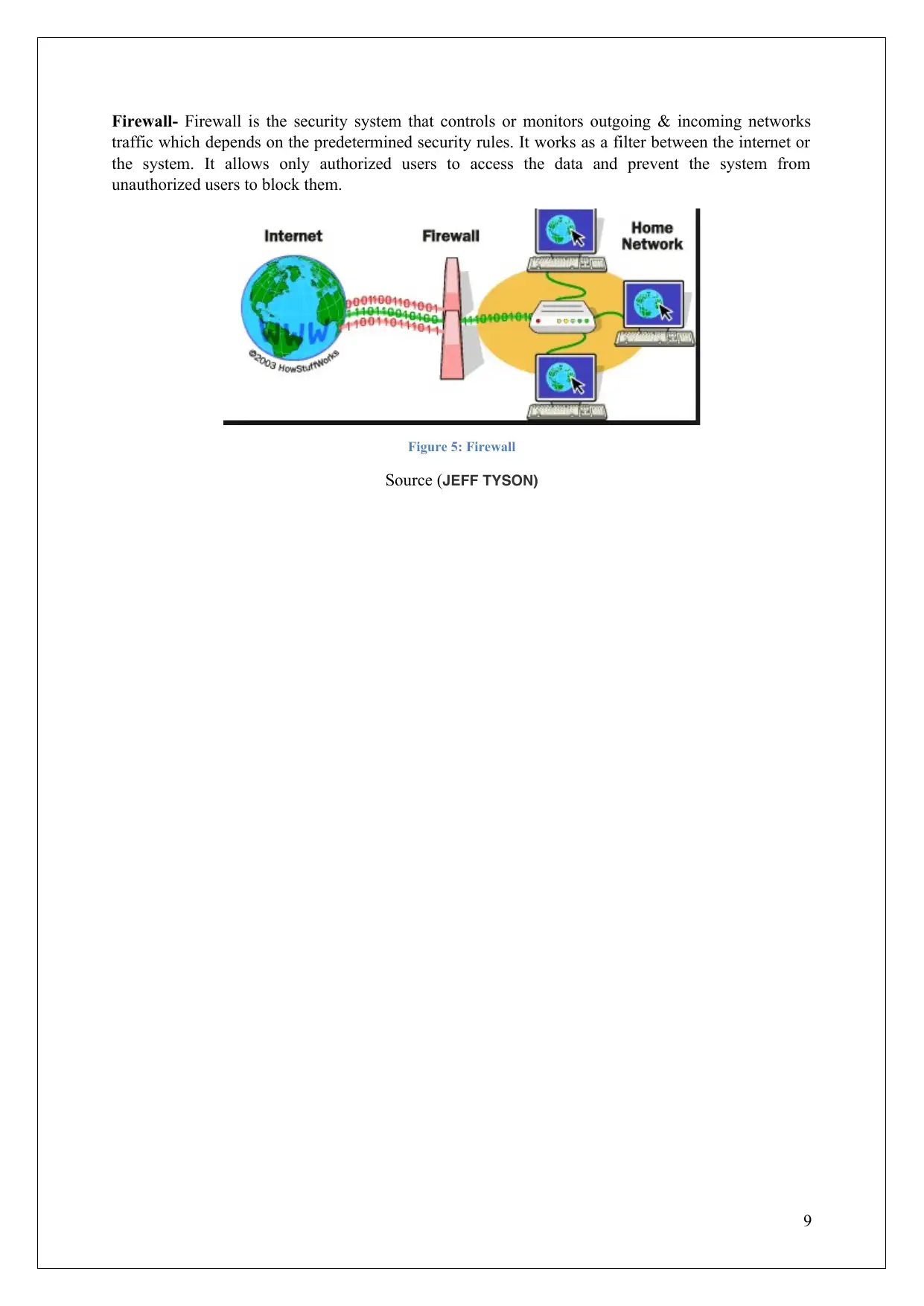
Firewall- Firewall is the security system that controls or monitors outgoing & incoming networks
traffic which depends on the predetermined security rules. It works as a filter between the internet or
the system. It allows only authorized users to access the data and prevent the system from
unauthorized users to block them.
Figure 5: Firewall
Source (JEFF TYSON)
9
traffic which depends on the predetermined security rules. It works as a filter between the internet or
the system. It allows only authorized users to access the data and prevent the system from
unauthorized users to block them.
Figure 5: Firewall
Source (JEFF TYSON)
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References-
Esguerra, M. (2016). What are the advantages and disadvantages of fingerprinting? -
Bayt.com Specialties. Retrieved from https://www.bayt.com/en/specialties/q/288971/what-
are-the-advantages-and-disadvantages-of-fingerprinting/
johnson, S. (2018). Biometric Fingerprint Scanners Advantages & Disadvantages |
Techwalla.com. Retrieved from https://www.techwalla.com/articles/biometric-fingerprint-
scanners-advantages-disadvantages
Kenny, S. (2018). An Introduction to Privacy Enhancing Technologies. Retrieved from
https://iapp.org/news/a/2008-05-introduction-to-privacy-enhancing-technologies/
Schmitthammer, F. (2015). Retrieved from https://www.linkedin.com/pulse/advantages-
disadvantages-biometric-system-fred-schmitthammer
Thakkar, D. (2018). Biometric Iris Recognition and Its Application. Retrieved from
https://www.bayometric.com/biometric-iris-recognition-application/
triggs, R. (2018). How fingerprint scanners work: optical, capacitive, and ultrasonic variants
explained. Retrieved from https://www.androidauthority.com/how-fingerprint-scanners-work-
670934/
V. Wilson, T. (2018). How Biometrics Works. Retrieved from
https://science.howstuffworks.com/biometrics2.htm
10
Esguerra, M. (2016). What are the advantages and disadvantages of fingerprinting? -
Bayt.com Specialties. Retrieved from https://www.bayt.com/en/specialties/q/288971/what-
are-the-advantages-and-disadvantages-of-fingerprinting/
johnson, S. (2018). Biometric Fingerprint Scanners Advantages & Disadvantages |
Techwalla.com. Retrieved from https://www.techwalla.com/articles/biometric-fingerprint-
scanners-advantages-disadvantages
Kenny, S. (2018). An Introduction to Privacy Enhancing Technologies. Retrieved from
https://iapp.org/news/a/2008-05-introduction-to-privacy-enhancing-technologies/
Schmitthammer, F. (2015). Retrieved from https://www.linkedin.com/pulse/advantages-
disadvantages-biometric-system-fred-schmitthammer
Thakkar, D. (2018). Biometric Iris Recognition and Its Application. Retrieved from
https://www.bayometric.com/biometric-iris-recognition-application/
triggs, R. (2018). How fingerprint scanners work: optical, capacitive, and ultrasonic variants
explained. Retrieved from https://www.androidauthority.com/how-fingerprint-scanners-work-
670934/
V. Wilson, T. (2018). How Biometrics Works. Retrieved from
https://science.howstuffworks.com/biometrics2.htm
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





