Charles Sturt University: Biometric Authentication in Security Systems
VerifiedAdded on 2022/11/28
|7
|3210
|268
Report
AI Summary
This report provides a comprehensive overview of biometric authentication, examining its role in modern security systems. It delves into various biometric technologies, including fingerprint, iris, and face recognition, highlighting their functionalities, benefits, and applications. The report discusses the increasing popularity of biometric systems due to their reliability and ease of use, while also addressing the challenges and issues associated with their implementation, such as technical faults and security vulnerabilities. It analyzes the evolution of biometric authentication, comparing it with traditional methods like passwords and tokens, and identifies areas for future research, such as addressing security gaps and enhancing the accuracy and reliability of biometric systems. The report also emphasizes the importance of cryptography and secure data storage in biometric systems, providing a detailed analysis of their impact on security and authentication processes. The report critically analyzes limitations and issues faced in the biometric systems. The speed of authentications have been high in the biometric authentication systems.
BIOMETRIC FOR AUTHENTICATION
A. Author
ITC595 MIT, School of Computing & Mathematics, Charles Sturt University
author@first-third.edu.au
A. Author
ITC595 MIT, School of Computing & Mathematics, Charles Sturt University
author@first-third.edu.au
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION..............................................................................................................................................3
OVERVIEW OF BIOMETRIC TECHNOLOGY.............................................................................................3
TYPES OF BIOMETRICS................................................................................................................................4
BENEFITS OF BIOMETRIC AUTHENTICATION........................................................................................5
ISSUES IN BIOMETRIC AUTHENTICATION..............................................................................................6
CONCLUSION..................................................................................................................................................6
REFERENCES...................................................................................................................................................6
INTRODUCTION..............................................................................................................................................3
OVERVIEW OF BIOMETRIC TECHNOLOGY.............................................................................................3
TYPES OF BIOMETRICS................................................................................................................................4
BENEFITS OF BIOMETRIC AUTHENTICATION........................................................................................5
ISSUES IN BIOMETRIC AUTHENTICATION..............................................................................................6
CONCLUSION..................................................................................................................................................6
REFERENCES...................................................................................................................................................6
ABSTRACT – Biometry has been playing an important role in
security systems. This paper has focused on biometrics,
passcodes and security tokens used in security systems.
Biometrics based authentication systems have been
becoming popular in the market. Various applications of
biometric technology in security systems have been
discussed in the paper. Challenges in the biometric
technology have been discussed in the paper. The speed of
authentications have been high in the biometric
authentication systems. The database have been using fast
search algorithm in the server that help in fast searching of
query claimed by user. In several cases, it becomes difficult
to attack a biometric systems for getting authentication to
the system.
Keywords— Biometric authentication, Fingerprint recognition,
Iris recognition and Face recognition
INTRODUCTION
Humans have been recognizing each other with the help of
several distinct characteristics. They used to recognize with
the help of face when meeting with each other and by vice
when speaking with each other. However, modern technology
has been based on computer based recognition system
including biometric. Biometric technology has been one of the
authentication method. It consists of identifying people by
different physical characteristics. This report has been based
on understanding the concept of biometric and its working in
authentication systems. The benefits of biometric security
systems have been discussed in the report. This report
critically analyses limitations and issues faced in the biometric
systems.
OVERVIEW OF BIOMETRIC TECHNOLOGY
Biometrics have been an automated methods for
identifying person or verifying identity of person based on
behavioral and physiological characteristics. Biometric based
authentication has been authentic identity verification that
have been based in individual physiological characteristics
including fingerprint, eyes, voice and face (Chatterjee et al.,
2018). The biometrics based authentication frameworks are
winding up such a great amount of prevalent as the
unwavering quality and the simplicity of utilization is
expanding for a long time. Biometric authentication has been
providing accurate and convenient approach for security
systems. It include concept of cryptography in it. The basic
concept of cryptography has been based on encrypting data
and information during transfer. Biometric data is personal
private information that has been unique and permanent
linked with person and is not replaced with keys and
passwords (Lu et al., 2015).
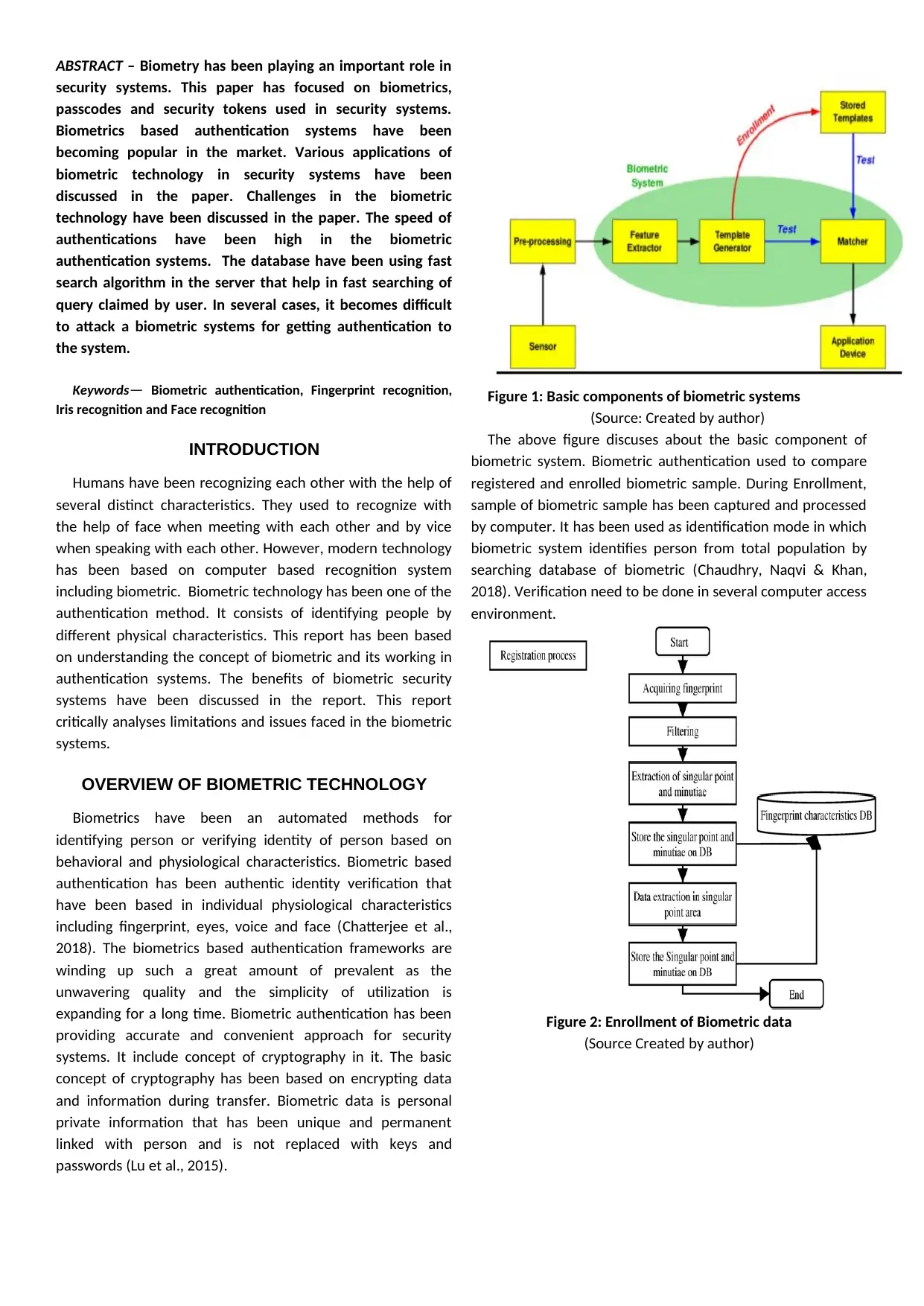
Figure 1: Basic components of biometric systems
(Source: Created by author)
The above figure discuses about the basic component of
biometric system. Biometric authentication used to compare
registered and enrolled biometric sample. During Enrollment,
sample of biometric sample has been captured and processed
by computer. It has been used as identification mode in which
biometric system identifies person from total population by
searching database of biometric (Chaudhry, Naqvi & Khan,
2018). Verification need to be done in several computer access
environment.
Figure 2: Enrollment of Biometric data
(Source Created by author)
security systems. This paper has focused on biometrics,
passcodes and security tokens used in security systems.
Biometrics based authentication systems have been
becoming popular in the market. Various applications of
biometric technology in security systems have been
discussed in the paper. Challenges in the biometric
technology have been discussed in the paper. The speed of
authentications have been high in the biometric
authentication systems. The database have been using fast
search algorithm in the server that help in fast searching of
query claimed by user. In several cases, it becomes difficult
to attack a biometric systems for getting authentication to
the system.
Keywords— Biometric authentication, Fingerprint recognition,
Iris recognition and Face recognition
INTRODUCTION
Humans have been recognizing each other with the help of
several distinct characteristics. They used to recognize with
the help of face when meeting with each other and by vice
when speaking with each other. However, modern technology
has been based on computer based recognition system
including biometric. Biometric technology has been one of the
authentication method. It consists of identifying people by
different physical characteristics. This report has been based
on understanding the concept of biometric and its working in
authentication systems. The benefits of biometric security
systems have been discussed in the report. This report
critically analyses limitations and issues faced in the biometric
systems.
OVERVIEW OF BIOMETRIC TECHNOLOGY
Biometrics have been an automated methods for
identifying person or verifying identity of person based on
behavioral and physiological characteristics. Biometric based
authentication has been authentic identity verification that
have been based in individual physiological characteristics
including fingerprint, eyes, voice and face (Chatterjee et al.,
2018). The biometrics based authentication frameworks are
winding up such a great amount of prevalent as the
unwavering quality and the simplicity of utilization is
expanding for a long time. Biometric authentication has been
providing accurate and convenient approach for security
systems. It include concept of cryptography in it. The basic
concept of cryptography has been based on encrypting data
and information during transfer. Biometric data is personal
private information that has been unique and permanent
linked with person and is not replaced with keys and
passwords (Lu et al., 2015).
Figure 1: Basic components of biometric systems
(Source: Created by author)
The above figure discuses about the basic component of
biometric system. Biometric authentication used to compare
registered and enrolled biometric sample. During Enrollment,
sample of biometric sample has been captured and processed
by computer. It has been used as identification mode in which
biometric system identifies person from total population by
searching database of biometric (Chaudhry, Naqvi & Khan,
2018). Verification need to be done in several computer access
environment.
Figure 2: Enrollment of Biometric data
(Source Created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
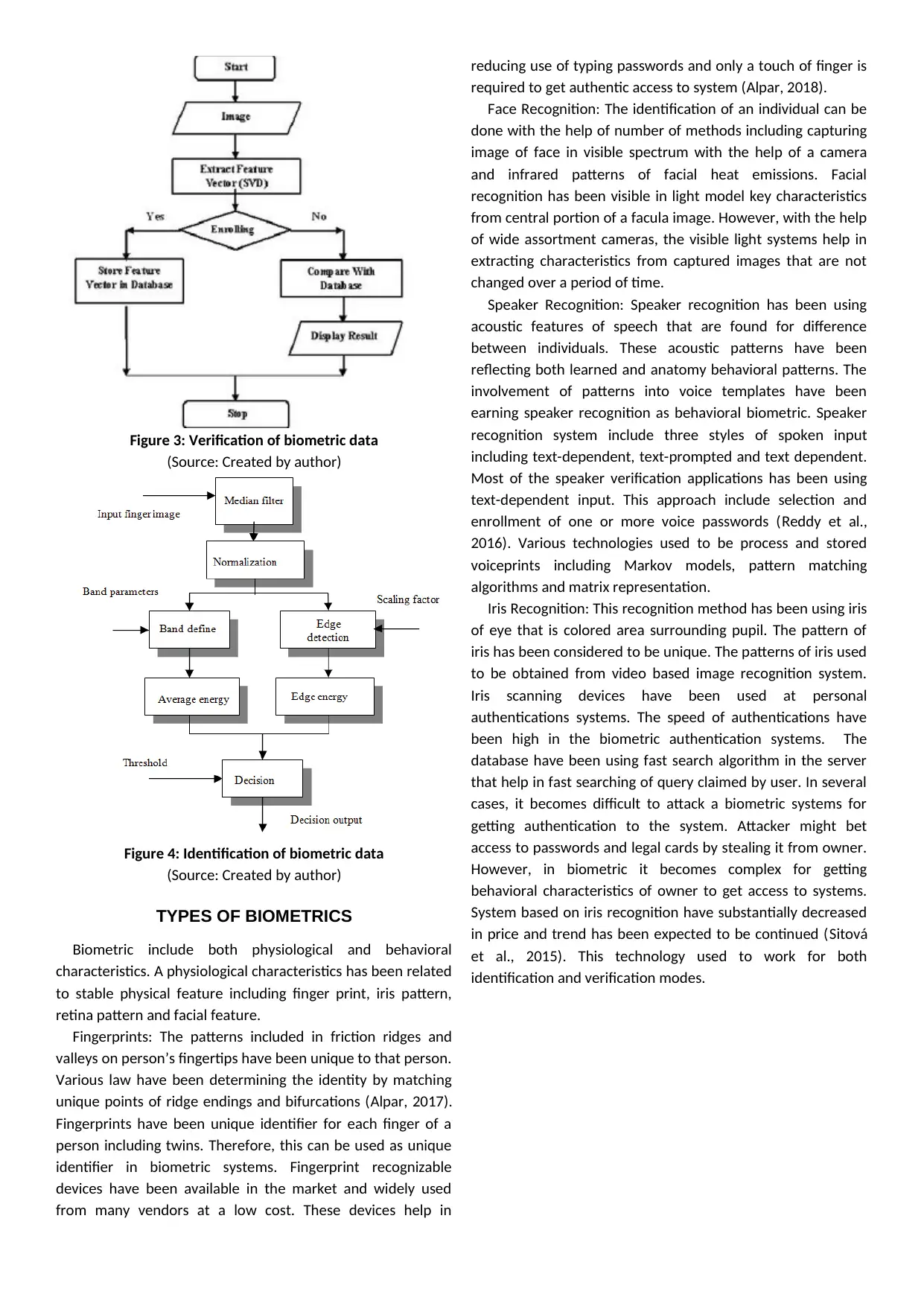
Figure 3: Verification of biometric data
(Source: Created by author)
Figure 4: Identification of biometric data
(Source: Created by author)
TYPES OF BIOMETRICS
Biometric include both physiological and behavioral
characteristics. A physiological characteristics has been related
to stable physical feature including finger print, iris pattern,
retina pattern and facial feature.
Fingerprints: The patterns included in friction ridges and
valleys on person’s fingertips have been unique to that person.
Various law have been determining the identity by matching
unique points of ridge endings and bifurcations (Alpar, 2017).
Fingerprints have been unique identifier for each finger of a
person including twins. Therefore, this can be used as unique
identifier in biometric systems. Fingerprint recognizable
devices have been available in the market and widely used
from many vendors at a low cost. These devices help in
reducing use of typing passwords and only a touch of finger is
required to get authentic access to system (Alpar, 2018).
Face Recognition: The identification of an individual can be
done with the help of number of methods including capturing
image of face in visible spectrum with the help of a camera
and infrared patterns of facial heat emissions. Facial
recognition has been visible in light model key characteristics
from central portion of a facula image. However, with the help
of wide assortment cameras, the visible light systems help in
extracting characteristics from captured images that are not
changed over a period of time.
Speaker Recognition: Speaker recognition has been using
acoustic features of speech that are found for difference
between individuals. These acoustic patterns have been
reflecting both learned and anatomy behavioral patterns. The
involvement of patterns into voice templates have been
earning speaker recognition as behavioral biometric. Speaker
recognition system include three styles of spoken input
including text-dependent, text-prompted and text dependent.
Most of the speaker verification applications has been using
text-dependent input. This approach include selection and
enrollment of one or more voice passwords (Reddy et al.,
2016). Various technologies used to be process and stored
voiceprints including Markov models, pattern matching
algorithms and matrix representation.
Iris Recognition: This recognition method has been using iris
of eye that is colored area surrounding pupil. The pattern of
iris has been considered to be unique. The patterns of iris used
to be obtained from video based image recognition system.
Iris scanning devices have been used at personal
authentications systems. The speed of authentications have
been high in the biometric authentication systems. The
database have been using fast search algorithm in the server
that help in fast searching of query claimed by user. In several
cases, it becomes difficult to attack a biometric systems for
getting authentication to the system. Attacker might bet
access to passwords and legal cards by stealing it from owner.
However, in biometric it becomes complex for getting
behavioral characteristics of owner to get access to systems.
System based on iris recognition have substantially decreased
in price and trend has been expected to be continued (Sitová
et al., 2015). This technology used to work for both
identification and verification modes.
(Source: Created by author)
Figure 4: Identification of biometric data
(Source: Created by author)
TYPES OF BIOMETRICS
Biometric include both physiological and behavioral
characteristics. A physiological characteristics has been related
to stable physical feature including finger print, iris pattern,
retina pattern and facial feature.
Fingerprints: The patterns included in friction ridges and
valleys on person’s fingertips have been unique to that person.
Various law have been determining the identity by matching
unique points of ridge endings and bifurcations (Alpar, 2017).
Fingerprints have been unique identifier for each finger of a
person including twins. Therefore, this can be used as unique
identifier in biometric systems. Fingerprint recognizable
devices have been available in the market and widely used
from many vendors at a low cost. These devices help in
reducing use of typing passwords and only a touch of finger is
required to get authentic access to system (Alpar, 2018).
Face Recognition: The identification of an individual can be
done with the help of number of methods including capturing
image of face in visible spectrum with the help of a camera
and infrared patterns of facial heat emissions. Facial
recognition has been visible in light model key characteristics
from central portion of a facula image. However, with the help
of wide assortment cameras, the visible light systems help in
extracting characteristics from captured images that are not
changed over a period of time.
Speaker Recognition: Speaker recognition has been using
acoustic features of speech that are found for difference
between individuals. These acoustic patterns have been
reflecting both learned and anatomy behavioral patterns. The
involvement of patterns into voice templates have been
earning speaker recognition as behavioral biometric. Speaker
recognition system include three styles of spoken input
including text-dependent, text-prompted and text dependent.
Most of the speaker verification applications has been using
text-dependent input. This approach include selection and
enrollment of one or more voice passwords (Reddy et al.,
2016). Various technologies used to be process and stored
voiceprints including Markov models, pattern matching
algorithms and matrix representation.
Iris Recognition: This recognition method has been using iris
of eye that is colored area surrounding pupil. The pattern of
iris has been considered to be unique. The patterns of iris used
to be obtained from video based image recognition system.
Iris scanning devices have been used at personal
authentications systems. The speed of authentications have
been high in the biometric authentication systems. The
database have been using fast search algorithm in the server
that help in fast searching of query claimed by user. In several
cases, it becomes difficult to attack a biometric systems for
getting authentication to the system. Attacker might bet
access to passwords and legal cards by stealing it from owner.
However, in biometric it becomes complex for getting
behavioral characteristics of owner to get access to systems.
System based on iris recognition have substantially decreased
in price and trend has been expected to be continued (Sitová
et al., 2015). This technology used to work for both
identification and verification modes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 5: Stages included in Iris recognition
(Source: Created by author)
BENEFITS OF BIOMETRIC AUTHENTICATION
The primary benefit of biometric authentication methods
over other authentication methods have been it authenticate
the user. These methods have been using real human
physiological and behavioral characteristics for authenticating
users. This biometric features have been permanent and
unique in nature (Odelu, Das & Goswami, 2015). The use of
biometric authentication systems have been providing proper
security to authentication systems in the network. It also helps
in restricting unauthentic users from entering into biometric
system. Another advantage is that biometric objects cannot be
stolen with respect to tokens, keys and passcodes. The
accuracy of iris scanner might get affected by changing in
might in the environment. For the decades, the password has
been implied just for the confirmation of the clients on PCs. At
the point when clients are expecting to recall longer and
progressively complex passwords, an increasingly secure and
advantageous answer for the validation of the clients is
required (He and Wang, 2015). The unique identifiers have
been helping in maintaining a secured approach in the
biometric systems. The authentication levels of the biometric
systems have been highly secured. The use of different
utilization of biometric identifiers have been helping in
providing secured lock to systems. Most of the biometric
techniques have been cannot be lost and stolen. This
advantage is for system administrators who have to remember
a lot of passwords for different systems in an organization
(Han, Xie & Liu, 2017). The speed of authentications have been
high in the biometric authentication systems. The database
have been using fast search algorithm in the server that help
in fast searching of query claimed by user. In several cases, it
becomes difficult to attack a biometric systems for getting
authentication to the system. Attacker might bet access to
passwords and legal cards by stealing it from owner. However,
in biometric it becomes complex for getting behavioral
characteristics of owner to get access to systems.
It decrease organizational cost for implementing security
system in the operations. Biometric systems are widely used
in organization and are of cheap cost. Biometric security has
helped in enhancing security. The approval and PC time have
been changed (Nigam & Gupta, 2015). At present, it can't be
seen that, the component on the completion of remote of a
PC based framework. The biometrics euthentication structures
are ending up such a lot of predominant as the steadfast
quality and the effortlessness of usage is extending for quite a
while (Mir and Nikooghadam, (2015). The advancement of
execution of that structures is an issue that is so much
noteworthy. The arrangement of affirmation is a cryptography
related segment that is such a lot of noteworthy, through that
the correspondence parties had the alternative to confirm
each other in an area of an open framework. For satisfying the
rational application need such a noteworthy number of
techniques, for instance, adroit cards have been proposed
anyway most of plans had some genuine drawbacks (Odelu et
al., 2015). Nevertheless, the systems for the biometric, for
instance, iris checking or exceptional imprint affirmation has
grabbed a wide thought. The structures that are related to the
biometric approval, can perceive the customers by the
quantifiable human traits of them. Notwithstanding the way
that a progressively noticeable security structure is ensured by
the biometric check. The structure considers a biometric data
that is gotten and set away similarly as adjusted the sound
data inside a database (Rane et al., 2013).
ISSUES IN BIOMETRIC AUTHENTICATION
There have been several cases where, there have been false
authentication of individuals due to technical fault in biometric
systems (Kumar et al., 2017). Technical issues have been a big
issue in biometric authentication system. There have been
several cases of cyber-attacks in the biometric systems
reported. Biometric data used to be stored over the cloud
database over the internet. Therefore, various harmful
malware and virus breach into the network server of the
biometric system. Biometric systems are not private enough as
all the physiological behavior of human beings are open to all.
Human used to provide fingerprints all over around during
holding anything or using their hand at any work (Alzubaidi &
Kalita, 2016). Therefore, attackers might target this and get
this fingerprints and use it for accessing to important systems.
Images of particular person is uploaded over various internet
websites including different platforms of social media.
Therefore, fetching a particular image of individual has been
become an easy task for hackers over the internet. These
issues have been creating negative impact in the use of the
biometric can various organization. Another disadvantage is
related to physical disability of an individual. Individuals having
disability in physical behavior including having no hands, eye
sight disorder and speaking disability will not be able to use
biometric systems. The accuracy of biometric systems have
(Source: Created by author)
BENEFITS OF BIOMETRIC AUTHENTICATION
The primary benefit of biometric authentication methods
over other authentication methods have been it authenticate
the user. These methods have been using real human
physiological and behavioral characteristics for authenticating
users. This biometric features have been permanent and
unique in nature (Odelu, Das & Goswami, 2015). The use of
biometric authentication systems have been providing proper
security to authentication systems in the network. It also helps
in restricting unauthentic users from entering into biometric
system. Another advantage is that biometric objects cannot be
stolen with respect to tokens, keys and passcodes. The
accuracy of iris scanner might get affected by changing in
might in the environment. For the decades, the password has
been implied just for the confirmation of the clients on PCs. At
the point when clients are expecting to recall longer and
progressively complex passwords, an increasingly secure and
advantageous answer for the validation of the clients is
required (He and Wang, 2015). The unique identifiers have
been helping in maintaining a secured approach in the
biometric systems. The authentication levels of the biometric
systems have been highly secured. The use of different
utilization of biometric identifiers have been helping in
providing secured lock to systems. Most of the biometric
techniques have been cannot be lost and stolen. This
advantage is for system administrators who have to remember
a lot of passwords for different systems in an organization
(Han, Xie & Liu, 2017). The speed of authentications have been
high in the biometric authentication systems. The database
have been using fast search algorithm in the server that help
in fast searching of query claimed by user. In several cases, it
becomes difficult to attack a biometric systems for getting
authentication to the system. Attacker might bet access to
passwords and legal cards by stealing it from owner. However,
in biometric it becomes complex for getting behavioral
characteristics of owner to get access to systems.
It decrease organizational cost for implementing security
system in the operations. Biometric systems are widely used
in organization and are of cheap cost. Biometric security has
helped in enhancing security. The approval and PC time have
been changed (Nigam & Gupta, 2015). At present, it can't be
seen that, the component on the completion of remote of a
PC based framework. The biometrics euthentication structures
are ending up such a lot of predominant as the steadfast
quality and the effortlessness of usage is extending for quite a
while (Mir and Nikooghadam, (2015). The advancement of
execution of that structures is an issue that is so much
noteworthy. The arrangement of affirmation is a cryptography
related segment that is such a lot of noteworthy, through that
the correspondence parties had the alternative to confirm
each other in an area of an open framework. For satisfying the
rational application need such a noteworthy number of
techniques, for instance, adroit cards have been proposed
anyway most of plans had some genuine drawbacks (Odelu et
al., 2015). Nevertheless, the systems for the biometric, for
instance, iris checking or exceptional imprint affirmation has
grabbed a wide thought. The structures that are related to the
biometric approval, can perceive the customers by the
quantifiable human traits of them. Notwithstanding the way
that a progressively noticeable security structure is ensured by
the biometric check. The structure considers a biometric data
that is gotten and set away similarly as adjusted the sound
data inside a database (Rane et al., 2013).
ISSUES IN BIOMETRIC AUTHENTICATION
There have been several cases where, there have been false
authentication of individuals due to technical fault in biometric
systems (Kumar et al., 2017). Technical issues have been a big
issue in biometric authentication system. There have been
several cases of cyber-attacks in the biometric systems
reported. Biometric data used to be stored over the cloud
database over the internet. Therefore, various harmful
malware and virus breach into the network server of the
biometric system. Biometric systems are not private enough as
all the physiological behavior of human beings are open to all.
Human used to provide fingerprints all over around during
holding anything or using their hand at any work (Alzubaidi &
Kalita, 2016). Therefore, attackers might target this and get
this fingerprints and use it for accessing to important systems.
Images of particular person is uploaded over various internet
websites including different platforms of social media.
Therefore, fetching a particular image of individual has been
become an easy task for hackers over the internet. These
issues have been creating negative impact in the use of the
biometric can various organization. Another disadvantage is
related to physical disability of an individual. Individuals having
disability in physical behavior including having no hands, eye
sight disorder and speaking disability will not be able to use
biometric systems. The accuracy of biometric systems have

been an issue in organization (Ngo et al., 2015). The accuracy
of iris scanner might get affected by changing in might in the
environment. For the decades, the password has been implied
just for the confirmation of the clients on PCs. At the point
when clients are expecting to recall longer and progressively
complex passwords, an increasingly secure and advantageous
answer for the validation of the clients is required (He and
Wang, 2015). The biometrics based authentication
frameworks are winding up such a great amount of prevalent
as the unwavering quality and the simplicity of utilization is
expanding for a long time (Mir and Nikooghadam, (2015). The
development of execution of that frameworks is challenge.
The plan of confirmation is a cryptography related component
that is such a great amount of significant, through that the
correspondence parties had the option to verify each other in
a domain of an open system. For fulfilling the down to earth
application necessity such a significant number of methods,
for example, credit cards are used however the majority of the
plans had some real downsides (Odelu et al., 2015). Be that as
it may, the techniques for the biometric, for example, iris
checking or unique mark confirmation has picked up a wide
consideration. The frameworks that are identified with the
biometric validation, can recognize the clients by the
quantifiable human attributes of them. In spite of the fact that
a more prominent security framework is guaranteed by the
biometric verification (Hammudoglu et al., 2017). The
biometric verification is essentially a safe procedure which is
depended on the organic trademark that is special. The
framework thinks about a biometric information that is caught
and put away just as acclimated the credible information
inside a database (Rane et al., 2013). The confirmation will
affirm just if both of the examples coordinate. Normally, the
biometric verification is utilizing for the administration of
getting to computerized and physical assets like rooms,
structures and above all the registering gadgets.
CONCLUSION
People have been perceiving each other with the assistance
of a few particular qualities. They used to perceive with the
assistance of face when meeting with one another and by bad
habit when talking with one another. Nonetheless, current
innovation has been founded on PC based acknowledgment
framework including biometric. Biometric innovation has been
one of the validation technique. It comprises of recognizing
individuals by various physical qualities. This report has been
founded on understanding the idea of biometric and its
working in validation frameworks. The advantages of
biometric security frameworks have been examined in the
report. This report fundamentally investigations constraints
and issues looked in the biometric frameworks.
REFERENCES
Alpar, O. (2017). Frequency spectrograms for biometric
keystroke authentication using neural network based
classifier. Knowledge-Based Systems, 116, 163-171.
Alpar, O. (2018). Biometric touchstroke authentication by
fuzzy proximity of touch locations. Future Generation
Computer Systems, 86, 71-80.
Alzubaidi, A., & Kalita, J. (2016). Authentication of
smartphone users using behavioral biometrics. IEEE
Communications Surveys & Tutorials, 18(3), 1998-2026.
Chatterjee, S., Roy, S., Das, A. K., Chattopadhyay, S.,
Kumar, N., & Vasilakos, A. V. (2018). Secure biometric-
based authentication scheme using Chebyshev chaotic
map for multi-server environment. IEEE Transactions on
Dependable and Secure Computing, 15(5), 824-839.
Chaudhry, S. A., Naqvi, H., & Khan, M. K. (2018). An
enhanced lightweight anonymous biometric based
authentication scheme for TMIS. Multimedia Tools and
Applications, 77(5), 5503-5524.
Hammudoglu, J. S., Sparreboom, J., Rauhamaa, J. I., Faber,
J. K., Guerchi, L. C., Samiotis, I. P., ... & Pouwelse, J. A.
(2017). Portable Trust: biometric-based authentication
and blockchain storage for self-sovereign identity
systems. arXiv preprint arXiv:1706.03744.
Han, L., Xie, Q., & Liu, W. (2017). An Improved Biometric
Based Authentication Scheme with User Anonymity Using
Elliptic Curve Cryptosystem. IJ Network Security, 19(3),
469-478.
He, D., & Wang, D. (2015). Robust biometrics-based
authentication scheme for multiserver environment. IEEE
Systems Journal, 9(3), 816-823.
Khan, I., Chaudhry, S. A., Sher, M., Khan, J. I., & Khan, M.
K. (2018). An anonymous and provably secure biometric-
based authentication scheme using chaotic maps for
accessing medical drop box data. The Journal of
Supercomputing, 74(8), 3685-3703.
Kumar, T., Braeken, A., Liyanage, M., & Ylianttila, M.
(2017, May). Identity privacy preserving biometric based
authentication scheme for Naked healthcare
environment. In 2017 IEEE International Conference on
Communications (ICC) (pp. 1-7). IEEE.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced
biometric-based authentication scheme for telecare
medicine information systems using elliptic curve
cryptosystem. Journal of medical systems, 39(3), 32.
Mir, O., & Nikooghadam, M. (2015). A secure biometrics
based authentication with key agreement scheme in
telemedicine networks for e-health services. Wireless
Personal Communications, 83(4), 2439-2461.
Ngo, D. C. L., Teoh, A. B. J., & Hu, J. (Eds.).
(2015). Biometric security. Cambridge Scholars Publishing.
Nigam, A., & Gupta, P. (2015). Designing an accurate hand
biometric based authentication system fusing finger
of iris scanner might get affected by changing in might in the
environment. For the decades, the password has been implied
just for the confirmation of the clients on PCs. At the point
when clients are expecting to recall longer and progressively
complex passwords, an increasingly secure and advantageous
answer for the validation of the clients is required (He and
Wang, 2015). The biometrics based authentication
frameworks are winding up such a great amount of prevalent
as the unwavering quality and the simplicity of utilization is
expanding for a long time (Mir and Nikooghadam, (2015). The
development of execution of that frameworks is challenge.
The plan of confirmation is a cryptography related component
that is such a great amount of significant, through that the
correspondence parties had the option to verify each other in
a domain of an open system. For fulfilling the down to earth
application necessity such a significant number of methods,
for example, credit cards are used however the majority of the
plans had some real downsides (Odelu et al., 2015). Be that as
it may, the techniques for the biometric, for example, iris
checking or unique mark confirmation has picked up a wide
consideration. The frameworks that are identified with the
biometric validation, can recognize the clients by the
quantifiable human attributes of them. In spite of the fact that
a more prominent security framework is guaranteed by the
biometric verification (Hammudoglu et al., 2017). The
biometric verification is essentially a safe procedure which is
depended on the organic trademark that is special. The
framework thinks about a biometric information that is caught
and put away just as acclimated the credible information
inside a database (Rane et al., 2013). The confirmation will
affirm just if both of the examples coordinate. Normally, the
biometric verification is utilizing for the administration of
getting to computerized and physical assets like rooms,
structures and above all the registering gadgets.
CONCLUSION
People have been perceiving each other with the assistance
of a few particular qualities. They used to perceive with the
assistance of face when meeting with one another and by bad
habit when talking with one another. Nonetheless, current
innovation has been founded on PC based acknowledgment
framework including biometric. Biometric innovation has been
one of the validation technique. It comprises of recognizing
individuals by various physical qualities. This report has been
founded on understanding the idea of biometric and its
working in validation frameworks. The advantages of
biometric security frameworks have been examined in the
report. This report fundamentally investigations constraints
and issues looked in the biometric frameworks.
REFERENCES
Alpar, O. (2017). Frequency spectrograms for biometric
keystroke authentication using neural network based
classifier. Knowledge-Based Systems, 116, 163-171.
Alpar, O. (2018). Biometric touchstroke authentication by
fuzzy proximity of touch locations. Future Generation
Computer Systems, 86, 71-80.
Alzubaidi, A., & Kalita, J. (2016). Authentication of
smartphone users using behavioral biometrics. IEEE
Communications Surveys & Tutorials, 18(3), 1998-2026.
Chatterjee, S., Roy, S., Das, A. K., Chattopadhyay, S.,
Kumar, N., & Vasilakos, A. V. (2018). Secure biometric-
based authentication scheme using Chebyshev chaotic
map for multi-server environment. IEEE Transactions on
Dependable and Secure Computing, 15(5), 824-839.
Chaudhry, S. A., Naqvi, H., & Khan, M. K. (2018). An
enhanced lightweight anonymous biometric based
authentication scheme for TMIS. Multimedia Tools and
Applications, 77(5), 5503-5524.
Hammudoglu, J. S., Sparreboom, J., Rauhamaa, J. I., Faber,
J. K., Guerchi, L. C., Samiotis, I. P., ... & Pouwelse, J. A.
(2017). Portable Trust: biometric-based authentication
and blockchain storage for self-sovereign identity
systems. arXiv preprint arXiv:1706.03744.
Han, L., Xie, Q., & Liu, W. (2017). An Improved Biometric
Based Authentication Scheme with User Anonymity Using
Elliptic Curve Cryptosystem. IJ Network Security, 19(3),
469-478.
He, D., & Wang, D. (2015). Robust biometrics-based
authentication scheme for multiserver environment. IEEE
Systems Journal, 9(3), 816-823.
Khan, I., Chaudhry, S. A., Sher, M., Khan, J. I., & Khan, M.
K. (2018). An anonymous and provably secure biometric-
based authentication scheme using chaotic maps for
accessing medical drop box data. The Journal of
Supercomputing, 74(8), 3685-3703.
Kumar, T., Braeken, A., Liyanage, M., & Ylianttila, M.
(2017, May). Identity privacy preserving biometric based
authentication scheme for Naked healthcare
environment. In 2017 IEEE International Conference on
Communications (ICC) (pp. 1-7). IEEE.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced
biometric-based authentication scheme for telecare
medicine information systems using elliptic curve
cryptosystem. Journal of medical systems, 39(3), 32.
Mir, O., & Nikooghadam, M. (2015). A secure biometrics
based authentication with key agreement scheme in
telemedicine networks for e-health services. Wireless
Personal Communications, 83(4), 2439-2461.
Ngo, D. C. L., Teoh, A. B. J., & Hu, J. (Eds.).
(2015). Biometric security. Cambridge Scholars Publishing.
Nigam, A., & Gupta, P. (2015). Designing an accurate hand
biometric based authentication system fusing finger
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

knuckleprint and palmprint. Neurocomputing, 151, 1120-
1132.
Odelu, V., Das, A. K., & Goswami, A. (2015). A secure
biometrics-based multi-server authentication protocol
using smart cards. IEEE Transactions on Information
Forensics and Security, 10(9), 1953-1966.
Reddy, A. G., Das, A. K., Odelu, V., & Yoo, K. Y. (2016). An
enhanced biometric based authentication with key-
agreement protocol for multi-server architecture based
on elliptic curve cryptography. PloS one, 11(5), e0154308.
1132.
Odelu, V., Das, A. K., & Goswami, A. (2015). A secure
biometrics-based multi-server authentication protocol
using smart cards. IEEE Transactions on Information
Forensics and Security, 10(9), 1953-1966.
Reddy, A. G., Das, A. K., Odelu, V., & Yoo, K. Y. (2016). An
enhanced biometric based authentication with key-
agreement protocol for multi-server architecture based
on elliptic curve cryptography. PloS one, 11(5), e0154308.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





