Biometrics in E-Secure Transactions: Security and Privacy Analysis
VerifiedAdded on 2022/11/13
|4
|672
|306
Report
AI Summary
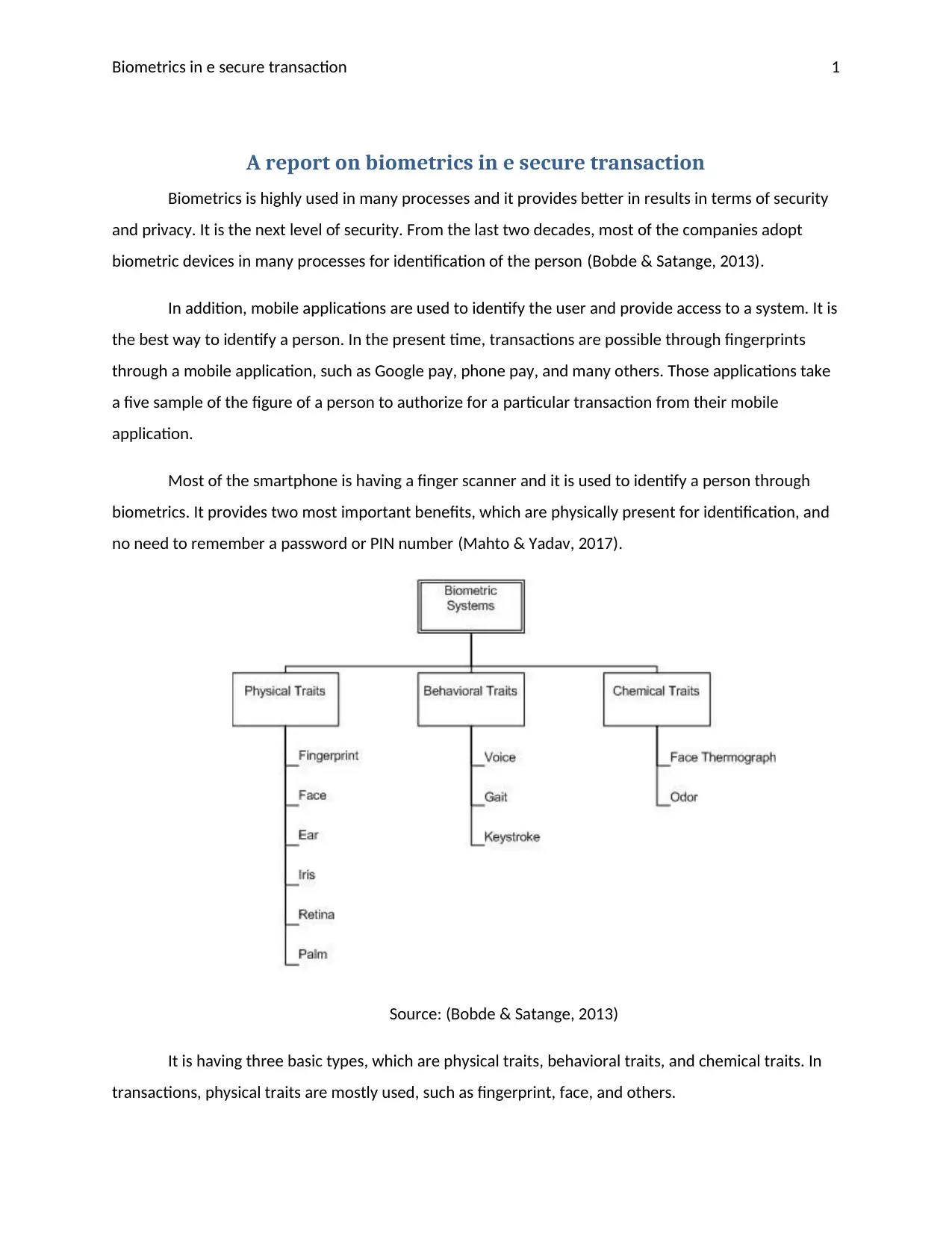
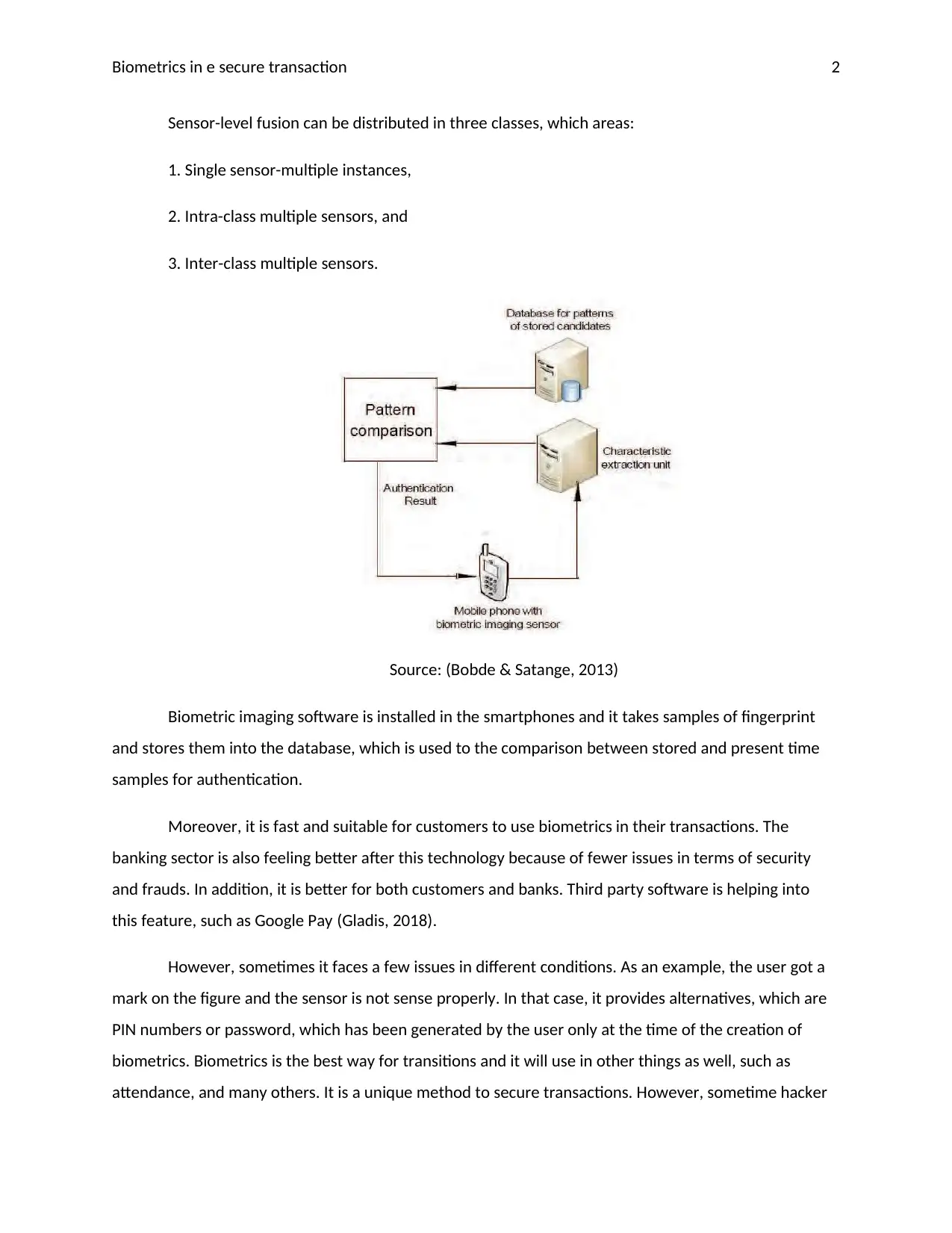
This report explores the application of biometrics in e-secure transactions, highlighting the increasing adoption of biometric devices for user identification and authentication. It focuses on the use of fingerprint scanning in mobile applications like Google Pay and Phone Pay, emphasizing the convenience and security benefits, such as eliminating the need for passwords or PINs. The report categorizes biometrics into physical, behavioral, and chemical traits, with a focus on physical traits like fingerprints. It also touches upon sensor-level fusion classes. The analysis includes the role of biometric imaging software, its advantages for customers and the banking sector, and potential issues such as sensor malfunctions. The report concludes by underscoring the importance of biometrics in securing transactions and its potential for broader applications while acknowledging potential disadvantages and security vulnerabilities.
1 out of 4





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)