ITC 595: Biometrics Authentication for Enhanced Security & Privacy
VerifiedAdded on 2024/05/21
|9
|2439
|231
Report
AI Summary
This report provides an overview of biometrics authentication, focusing on its use for security and privacy. It discusses the advantages and disadvantages of biometric systems, various authentication methods including fingerprint, retina scan, and facial recognition, and their application in organizations. The report includes a literature review, a proposed two-step authentication design, and an analysis of biometric technologies in relation to data security and organizational infrastructure. It also addresses the increasing need for biometrics in the context of the Internet of Things (IoT) and the limitations of traditional password-based security. The study concludes that biometrics authentication offers a more secure and user-friendly alternative for protecting sensitive data and preventing unauthorized access.

ITC 595 – Assessment 5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Contents
Abstract:...........................................................................................................................................3
Introduction:....................................................................................................................................3
Literature Review............................................................................................................................6
Proposed Design..............................................................................................................................7
Conclusion:......................................................................................................................................8
Acknowledgement:..........................................................................................................................8
References........................................................................................................................................9
Abstract:...........................................................................................................................................3
Introduction:....................................................................................................................................3
Literature Review............................................................................................................................6
Proposed Design..............................................................................................................................7
Conclusion:......................................................................................................................................8
Acknowledgement:..........................................................................................................................8
References........................................................................................................................................9
Abstract:
Biometrics is the process which used to identify and authenticate the behavioural and physical
characteristic of a person. In short, it is the measurement of life and study of the living beings. In
the field of computer science, it used as the access control and identification of the groups. The
aim of the further report is to research about on the topic of Biometrics for authentication that is
used for security and privacy implementation. It will include the use of biometrics in various
organizations with their advantages and disadvantages. Identify the relevant technology and their
use in organizations in compare with biometric. The encryption format with the infrastructure of
the organization is followed in the report.
Introduction:
Biometrics is basically used to identify the physical and behavioural characteristics which are
under surveillance. These are the two types of the biometrics, behavioural and physiological.
Biometrics is the alternative of the username and password. Various types of the process include
the authentication like, fingerprints, retina scan, face recognition, DNA match and voice
recognition. The report is based on the security and privacy implications through the biometrics
process. The advantages and disadvantages of the biometric will be discussed in the further
report. The working of the biometrics will explain, regarding the authentication process of the
organizations. The discussion and research will be on the different topic of the security of the
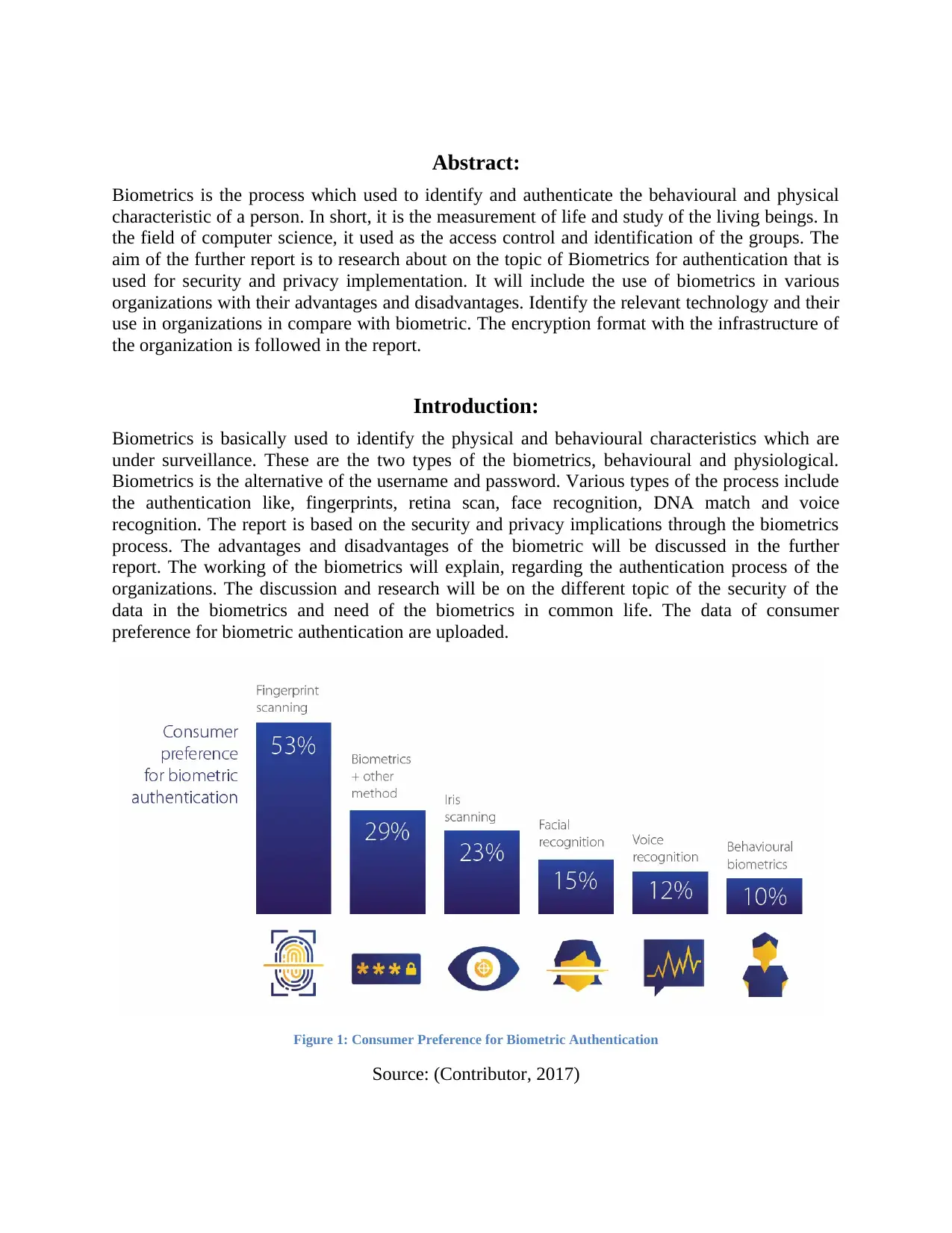
data in the biometrics and need of the biometrics in common life. The data of consumer
preference for biometric authentication are uploaded.
Figure 1: Consumer Preference for Biometric Authentication
Source: (Contributor, 2017)
Biometrics is the process which used to identify and authenticate the behavioural and physical
characteristic of a person. In short, it is the measurement of life and study of the living beings. In
the field of computer science, it used as the access control and identification of the groups. The
aim of the further report is to research about on the topic of Biometrics for authentication that is
used for security and privacy implementation. It will include the use of biometrics in various
organizations with their advantages and disadvantages. Identify the relevant technology and their
use in organizations in compare with biometric. The encryption format with the infrastructure of
the organization is followed in the report.
Introduction:
Biometrics is basically used to identify the physical and behavioural characteristics which are
under surveillance. These are the two types of the biometrics, behavioural and physiological.
Biometrics is the alternative of the username and password. Various types of the process include
the authentication like, fingerprints, retina scan, face recognition, DNA match and voice
recognition. The report is based on the security and privacy implications through the biometrics
process. The advantages and disadvantages of the biometric will be discussed in the further
report. The working of the biometrics will explain, regarding the authentication process of the
organizations. The discussion and research will be on the different topic of the security of the
data in the biometrics and need of the biometrics in common life. The data of consumer
preference for biometric authentication are uploaded.
Figure 1: Consumer Preference for Biometric Authentication
Source: (Contributor, 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research Paper:
The research paper is going to include the results of the different research on the biometrics. The
behavioural of the biometrics includes the gestures pattern and walking gait for the
authentication process. The working process of the biometrics is used in the organizations and a
place where the authentication is requiring for the security of the data. There are various types of
the authentication like, biological, behavioural and morphological. In the digital era of the
technology, there are too many resources to store and save the data but the user wants a secure
place about that he is assured that his data will be safe in future. Now it is the responsibility of
the owner or company who used to save people’s data that used latest techniques to manage the
data. This is the requirement of this research paper. Now it is more difficult to protect
confidential data or information from the hackers. Keys and password are not sufficient to save
your data so the use of biometrics is continuously increasing with different variations. Biometric
has the feature that a system which is encrypted with the biometric system, can open by the
person not by the manually with entering username and password.
Some factors of the biometric, which make it more important and give us a reason to create this
section, research paper of the report, these are it is safe, scalable, user-friendly, accurate and
time-saving. Millions of devices are connected to the internet at a time and they are continuously
sending and receiving the messages. At that time, an authorized access can interrupt the network
and access your files of any device but in the case of biometric authentication, it can’t be
possible without permission of the user. The use of the biometrics in the organization, make
secure the business assets as well as the server rooms. It stops the unauthorized access and
continues the workflow (THAKKAR, 2018).
The research paper is going to include the results of the different research on the biometrics. The
behavioural of the biometrics includes the gestures pattern and walking gait for the
authentication process. The working process of the biometrics is used in the organizations and a
place where the authentication is requiring for the security of the data. There are various types of
the authentication like, biological, behavioural and morphological. In the digital era of the
technology, there are too many resources to store and save the data but the user wants a secure
place about that he is assured that his data will be safe in future. Now it is the responsibility of
the owner or company who used to save people’s data that used latest techniques to manage the
data. This is the requirement of this research paper. Now it is more difficult to protect
confidential data or information from the hackers. Keys and password are not sufficient to save
your data so the use of biometrics is continuously increasing with different variations. Biometric
has the feature that a system which is encrypted with the biometric system, can open by the
person not by the manually with entering username and password.
Some factors of the biometric, which make it more important and give us a reason to create this
section, research paper of the report, these are it is safe, scalable, user-friendly, accurate and
time-saving. Millions of devices are connected to the internet at a time and they are continuously
sending and receiving the messages. At that time, an authorized access can interrupt the network
and access your files of any device but in the case of biometric authentication, it can’t be
possible without permission of the user. The use of the biometrics in the organization, make
secure the business assets as well as the server rooms. It stops the unauthorized access and
continues the workflow (THAKKAR, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Research Justification:
The research is completed in the first section names as a research paper on the biometric
authentication. Use of biometric system in the organization, make it more secure and give access
to the user to access the device and other authenticate components of the organization. Remote
access allows the biometrics with the implementation of the internet of things (IoT). Internet of
things can manage the biometrics authentication with the use of remote access. It helps to extract
the biometric system of any organization. The justification is the effect of above research on
biometric authentication. Biometric system is helpful to resolve the issues of an organization.
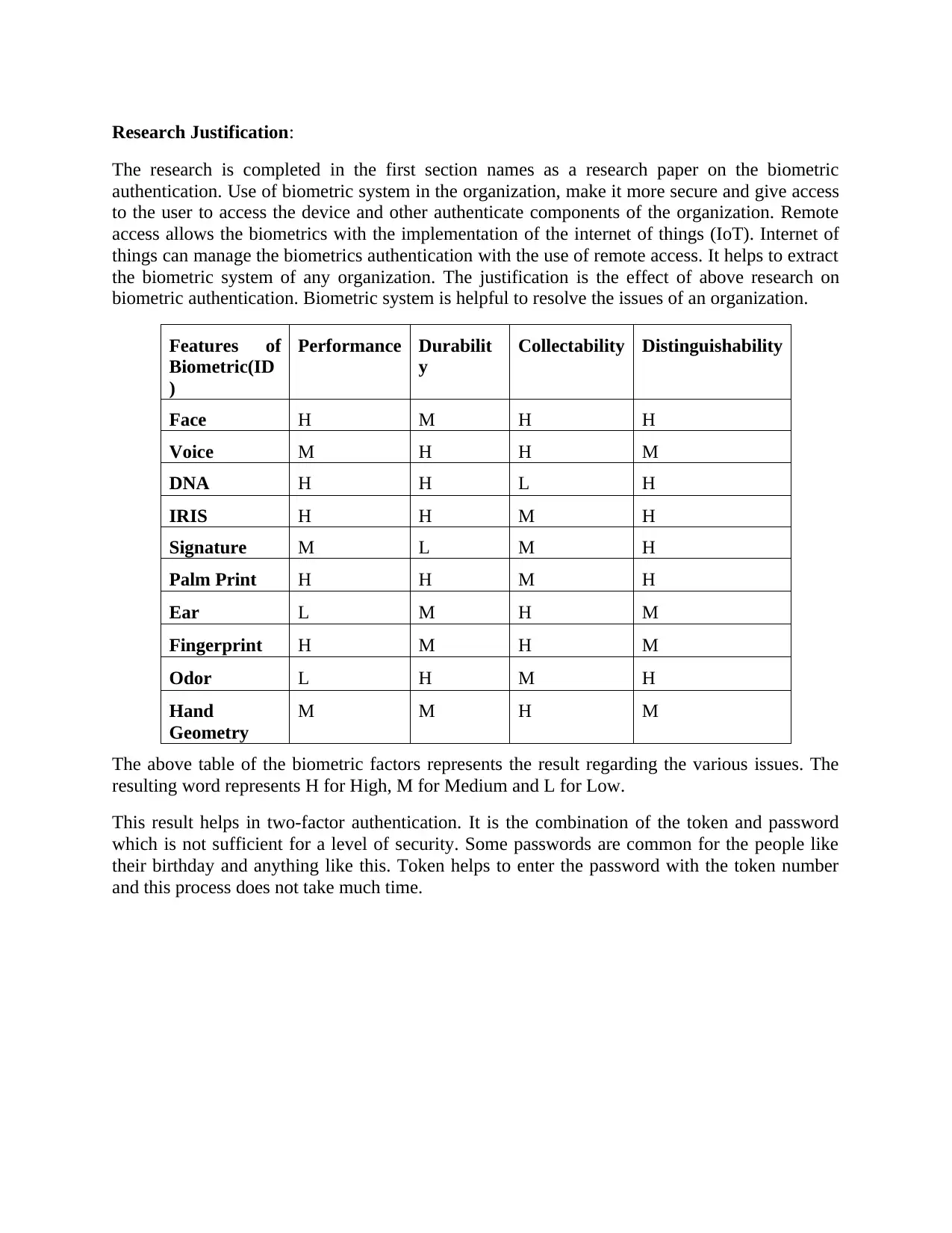
Features of
Biometric(ID
)
Performance Durabilit
y
Collectability Distinguishability
Face H M H H
Voice M H H M
DNA H H L H
IRIS H H M H
Signature M L M H
Palm Print H H M H
Ear L M H M
Fingerprint H M H M
Odor L H M H
Hand
Geometry
M M H M
The above table of the biometric factors represents the result regarding the various issues. The
resulting word represents H for High, M for Medium and L for Low.
This result helps in two-factor authentication. It is the combination of the token and password
which is not sufficient for a level of security. Some passwords are common for the people like
their birthday and anything like this. Token helps to enter the password with the token number
and this process does not take much time.
The research is completed in the first section names as a research paper on the biometric
authentication. Use of biometric system in the organization, make it more secure and give access
to the user to access the device and other authenticate components of the organization. Remote
access allows the biometrics with the implementation of the internet of things (IoT). Internet of
things can manage the biometrics authentication with the use of remote access. It helps to extract
the biometric system of any organization. The justification is the effect of above research on
biometric authentication. Biometric system is helpful to resolve the issues of an organization.
Features of
Biometric(ID
)
Performance Durabilit
y
Collectability Distinguishability
Face H M H H
Voice M H H M
DNA H H L H
IRIS H H M H
Signature M L M H
Palm Print H H M H
Ear L M H M
Fingerprint H M H M
Odor L H M H
Hand
Geometry
M M H M
The above table of the biometric factors represents the result regarding the various issues. The
resulting word represents H for High, M for Medium and L for Low.
This result helps in two-factor authentication. It is the combination of the token and password
which is not sufficient for a level of security. Some passwords are common for the people like
their birthday and anything like this. Token helps to enter the password with the token number
and this process does not take much time.

Literature Review
Biometrics is useful to protect the computers, servers with the assets of the business. The user
can use the functionality of biometric as an individual system. Biometric uses full compare then
password. Each of employees has his own identity and password need to share with each of the
employees of the origination. Biometric is the future of latest technology or electronic security
which is used by most of the companies in the world. Microsoft launches operating system
window 10 with the feature of the biometric platform which makes the authentication process
more reliable and convenient. Here are the characteristics of biometrics which are important for
the implementation of security and privacy in an organization.
Universal: everyone can use the biometric system
Unique: it is unique for each person which can differentiate between two
Invariable: a person can use it in his whole life without any interrupt of technology
Recordable: the data and information can be collect and store with security
Measurable: the functions of the system can be measurable with the comparison
These are some points which are useful in the implication of privacy and security of biometrics
authentication. Basically, the use of biometrics in an organization is for the identification and
authentication (Biometrics, 2018).
The identification process is used to recognize a person in the group of people who are registered
in the database. This process maintains the privacy of an organization. At the other side, the
authentication process is to recognize the person with the use of the biometric chip. This type of
chip is used in the passport to verify a person at the airport.
The security of the biometric can be implemented with the use of its categories in which some of
them we discussed above. Basically, the categories are, biological, behavioural and
morphological. The biological category includes the Blood and DNA for the use of security.
Behavioural used the physical activity of a user for the authentication like a way of walking,
signature and keyboard strokes. At last the morphological is the major biometric authentication
which widely in the organizations for security and privacy like, face recognition, fingerprints,
voice match, iris, the shape of the hand and many more. The biometrics of the morphological
authentication is more effective and reliable like face, iris and fingerprint.
Here are some reasons to use the biometric authentication like:
Keys and passwords have not enough security to secure the data from kept out of the
hands of unauthorized individuals and hackers. Internet of things is connected with the
most of platforms and devices so it requires enabling the biometric security in the
organization. The biometric authentication is unique for each person. The reasons that
why we need biometric in future:
The landscape of IoT is more complex: the IoT is a larger field that is necessary to
protect the devices from the unwanted access. It is not enough to keep the traditional
Biometrics is useful to protect the computers, servers with the assets of the business. The user
can use the functionality of biometric as an individual system. Biometric uses full compare then
password. Each of employees has his own identity and password need to share with each of the
employees of the origination. Biometric is the future of latest technology or electronic security
which is used by most of the companies in the world. Microsoft launches operating system
window 10 with the feature of the biometric platform which makes the authentication process
more reliable and convenient. Here are the characteristics of biometrics which are important for
the implementation of security and privacy in an organization.
Universal: everyone can use the biometric system
Unique: it is unique for each person which can differentiate between two
Invariable: a person can use it in his whole life without any interrupt of technology
Recordable: the data and information can be collect and store with security
Measurable: the functions of the system can be measurable with the comparison
These are some points which are useful in the implication of privacy and security of biometrics
authentication. Basically, the use of biometrics in an organization is for the identification and
authentication (Biometrics, 2018).
The identification process is used to recognize a person in the group of people who are registered
in the database. This process maintains the privacy of an organization. At the other side, the
authentication process is to recognize the person with the use of the biometric chip. This type of
chip is used in the passport to verify a person at the airport.
The security of the biometric can be implemented with the use of its categories in which some of
them we discussed above. Basically, the categories are, biological, behavioural and
morphological. The biological category includes the Blood and DNA for the use of security.
Behavioural used the physical activity of a user for the authentication like a way of walking,
signature and keyboard strokes. At last the morphological is the major biometric authentication
which widely in the organizations for security and privacy like, face recognition, fingerprints,
voice match, iris, the shape of the hand and many more. The biometrics of the morphological
authentication is more effective and reliable like face, iris and fingerprint.
Here are some reasons to use the biometric authentication like:
Keys and passwords have not enough security to secure the data from kept out of the
hands of unauthorized individuals and hackers. Internet of things is connected with the
most of platforms and devices so it requires enabling the biometric security in the
organization. The biometric authentication is unique for each person. The reasons that
why we need biometric in future:
The landscape of IoT is more complex: the IoT is a larger field that is necessary to
protect the devices from the unwanted access. It is not enough to keep the traditional
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

password to protect the devices like, mobile, sensors, tablet and services which are based
on the cloud.
Password, not enough: in the tech-world, the two-factor authentication is the more
reliable base to protect the data and assets of the organization, smartphones, and server
rooms. Most of the people use the same characters to secure their devices and data, this
term is explained by the IoT portal. In this case of security, the 2FA verification is not
enough to secure and keep private the data. Use of the physical tokens is also not
providing the successful result as compare the biometric authentication (cmarsden, 2015).
There is the various use of the biometrics in daily life like fingerprint recognition in cell phones,
iris, face and voice recognition in various devices and components which used to added more
security and privacy. The example of biometrics in daily life is as follows:
Transpiration Vehicle: voice recognition technique is used in the cars to unlock it through
the Bluetooth or other electronics devices.
Security of Airport: iris scanned techniques with the fingerprints combination is used at
the Airport for the security and privacy. Visitors and travellers must sign in with the
biometrics systems and their details stored in the database. This database is used at the
international level to save the time of waiting in queues with passport verification. Just
walk through the scanner and look into the camera, machine scan your retina with
fingerprints in few seconds.
Entrance in building: biometrics techniques are used in bindings of offices, colleges and
others. Thumb or iris authentication is used mostly in this biometrics.
Blood Banks: in the medical research area, the identity of a person is a necessary term as
a donor. Doctors issue cards which contain all the required information of a patient or
donor. This information also stores in the digital database for a long time which can be
accessed by the both just use their biometric recognition.
Institutions: more than 30% institutes used the biometric authentication for implications
of privacy and security in their organization. The biometric used to record the attendance,
to issues the library books, entrance in the lab, verification authentication for the exams
and for many other activities.
There are also so many uses of the biometrics authentication in various fields like,
Border control
Healthcare
Voter registration or civil identity (Trader, 2013)
Proposed Design
The two-step authentication is used in the proposed design of the biometrics authentication that
makes it better with increasing the efficiency. The biometric authentication in the two-step
on the cloud.
Password, not enough: in the tech-world, the two-factor authentication is the more
reliable base to protect the data and assets of the organization, smartphones, and server
rooms. Most of the people use the same characters to secure their devices and data, this
term is explained by the IoT portal. In this case of security, the 2FA verification is not
enough to secure and keep private the data. Use of the physical tokens is also not
providing the successful result as compare the biometric authentication (cmarsden, 2015).
There is the various use of the biometrics in daily life like fingerprint recognition in cell phones,
iris, face and voice recognition in various devices and components which used to added more
security and privacy. The example of biometrics in daily life is as follows:
Transpiration Vehicle: voice recognition technique is used in the cars to unlock it through
the Bluetooth or other electronics devices.
Security of Airport: iris scanned techniques with the fingerprints combination is used at
the Airport for the security and privacy. Visitors and travellers must sign in with the
biometrics systems and their details stored in the database. This database is used at the
international level to save the time of waiting in queues with passport verification. Just
walk through the scanner and look into the camera, machine scan your retina with
fingerprints in few seconds.
Entrance in building: biometrics techniques are used in bindings of offices, colleges and
others. Thumb or iris authentication is used mostly in this biometrics.
Blood Banks: in the medical research area, the identity of a person is a necessary term as
a donor. Doctors issue cards which contain all the required information of a patient or
donor. This information also stores in the digital database for a long time which can be
accessed by the both just use their biometric recognition.
Institutions: more than 30% institutes used the biometric authentication for implications
of privacy and security in their organization. The biometric used to record the attendance,
to issues the library books, entrance in the lab, verification authentication for the exams
and for many other activities.
There are also so many uses of the biometrics authentication in various fields like,
Border control
Healthcare
Voter registration or civil identity (Trader, 2013)
Proposed Design
The two-step authentication is used in the proposed design of the biometrics authentication that
makes it better with increasing the efficiency. The biometric authentication in the two-step
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

verification is stored in the smart card. This smart card can be used with voice recognition and
secret key or password. Multi-factor authentication is also used in the biometric authentication. It
has more than one method of authentications. Some of them are given below:
Password Elimination: Remove the password and use the behavioural and physiological
characteristics for the authentication. There is no need to reset the password and remove
complexity with the use of biometrics.
Certificate Management: Implement the security and privacy with the biometric encryption and
decryption techniques. It used the PKI (public key infrastructure) for both techniques.
Credential Management: make strong credential with the use of biometrics to prevent the
unauthorized access. Use with just one time enrol and no need to implement the complex system.
Network Authentication: multi-factor authentication technique is used to safe the server and data
from unauthorized access with the scanning process (Thakkar, 2018).
Conclusion:
Biometrics authentication used to prevent the system from unauthorized access. Different types
of authentication are explained in the report. The implication of biometrics for security and
privacy are resolved by using the different methods. The basic use of biometric is to identify the
authentication with the physical and behavioural characteristics of the user. This research
includes the complete process of a biometric authentication. Literature is used to making a better
system for the biometric authentication. Sometimes biometrics system could fail because of
uncertain users. The several attacks on the biometrics system could harm the integrity of the
system.
Acknowledgement:
The above research is completed on the topic of “Biometrics for authentication: security and
privacy implications”. The work is complete according to the given template to fulfil the given
requirements. The APA reference is used in the research paper.
secret key or password. Multi-factor authentication is also used in the biometric authentication. It
has more than one method of authentications. Some of them are given below:
Password Elimination: Remove the password and use the behavioural and physiological
characteristics for the authentication. There is no need to reset the password and remove
complexity with the use of biometrics.
Certificate Management: Implement the security and privacy with the biometric encryption and
decryption techniques. It used the PKI (public key infrastructure) for both techniques.
Credential Management: make strong credential with the use of biometrics to prevent the
unauthorized access. Use with just one time enrol and no need to implement the complex system.
Network Authentication: multi-factor authentication technique is used to safe the server and data
from unauthorized access with the scanning process (Thakkar, 2018).
Conclusion:
Biometrics authentication used to prevent the system from unauthorized access. Different types
of authentication are explained in the report. The implication of biometrics for security and
privacy are resolved by using the different methods. The basic use of biometric is to identify the
authentication with the physical and behavioural characteristics of the user. This research
includes the complete process of a biometric authentication. Literature is used to making a better
system for the biometric authentication. Sometimes biometrics system could fail because of
uncertain users. The several attacks on the biometrics system could harm the integrity of the
system.
Acknowledgement:
The above research is completed on the topic of “Biometrics for authentication: security and
privacy implications”. The work is complete according to the given template to fulfil the given
requirements. The APA reference is used in the research paper.

References
Biometrics. (2018). Retrieved from https://www.morpho.com/en/biometrics
cmarsden. (2015). 4 REASONS WHY BIOMETRIC SECURITY IS THE WAY
FORWARD [Blog]. Retrieved from http://www.digitus-biometrics.com/blog/4-reasons-
why-biometric-security-is-the-way-forward/
Contributor, P. (2017). Australian banks to kill PINs by pushing towards biometric
authentication. Retrieved from http://www.paymentscardsandmobile.com/kill-pins-by-
pushing-towards-biometric-authentication/
THAKKAR, D. (2018). BIOMETRIC SECURITY, FUTURE OF BIOMETRICS, TWO-
FACTOR AUTHENTICATION [Blog]. Retrieved from
https://www.bayometric.com/increasing-importance-of-biometric-security/
THAKKAR, D. (2018). MFA (Multi-factor Authentication) With Biometrics [Blog].
Retrieved from https://www.bayometric.com/mfa-multi-factor-authentication-biometrics/
Trader, J. (2013). 5 Ways Biometric Technology is Used in Everyday Life [Blog].
Retrieved from http://www.m2sys.com/blog/guest-blog-posts/5-ways-biometric-
technology-is-used-in-everyday-life/
Biometrics. (2018). Retrieved from https://www.morpho.com/en/biometrics
cmarsden. (2015). 4 REASONS WHY BIOMETRIC SECURITY IS THE WAY
FORWARD [Blog]. Retrieved from http://www.digitus-biometrics.com/blog/4-reasons-
why-biometric-security-is-the-way-forward/
Contributor, P. (2017). Australian banks to kill PINs by pushing towards biometric
authentication. Retrieved from http://www.paymentscardsandmobile.com/kill-pins-by-
pushing-towards-biometric-authentication/
THAKKAR, D. (2018). BIOMETRIC SECURITY, FUTURE OF BIOMETRICS, TWO-
FACTOR AUTHENTICATION [Blog]. Retrieved from
https://www.bayometric.com/increasing-importance-of-biometric-security/
THAKKAR, D. (2018). MFA (Multi-factor Authentication) With Biometrics [Blog].
Retrieved from https://www.bayometric.com/mfa-multi-factor-authentication-biometrics/
Trader, J. (2013). 5 Ways Biometric Technology is Used in Everyday Life [Blog].
Retrieved from http://www.m2sys.com/blog/guest-blog-posts/5-ways-biometric-
technology-is-used-in-everyday-life/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




