IT Security Research Project: Biometrics Authentication and Privacy
VerifiedAdded on 2022/09/29
|8
|1733
|23
Project
AI Summary
This research project examines biometrics authentication in the context of information security and privacy. It explores various biometric methods including retina scan, iris recognition, finger scanning, finger vein ID, face recognition, and voice recognition. The study investigates how these technologies are employed for user authentication and access control, addressing the research question of how biometric authentication is utilized to enhance security and protect privacy. The methodology involves a qualitative analysis of existing literature, drawing from databases like IEEE, Google Scholar, ACM, and EndNote, and focusing on peer-reviewed articles published between 2012 and 2019. The project reviews the existing literature, highlighting the contributions and limitations of prior research. The findings indicate that biometric authentication is widely used for security and privacy, with a focus on examples like Iris recognition and retina scan, and that biometric based security management for access control is a secure mechanism that ensures security and privacy. The project concludes by emphasizing the need for further research on the impacts of biometric authentication on individuals.

Running head: IT SECURITY RESEARCH PROJECT 1
Biometrics for authentication: security and privacy implications
Student
Tutor
Institutional Affiliation
Date
Biometrics for authentication: security and privacy implications
Student
Tutor
Institutional Affiliation
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT SECURITY RESEARCH PROJECT 2
Biometrics for authentication: security and privacy implications
Introduction
Biometric authentication has been gaining more attention in the information security
sector in the recent decades. It involves the process involving a comparison of the data for
characteristics of an individual to that in the biometric template of the individual to identify if
there is any resemblance. This security strategy can be used in various cases ranging from
opening door locks to accessing computer terminals. It is as well used in proving identity of
people in form of authentication. This is achieved in multi-facet approaches some of which
include the use of retina scan, Iris recognition, finger scanning, finger vein ID, face recognition
as well as voice recognition technologies.
Finger printing is the example of visual biometrics that is most used. Following its
considerable ramification in security sector, the biometrics authentication for security and
privacy has attracted researchers. As such, there are a considerable number of literature on this
subject, however, only a few literature explore this critical sector to a considerable extent.
Following this rationale, this study seek to explore this critical aspect into details. In doing so,
the researchers will examine the current literature that on the subject of study.
Aim
This study aims to explore the current literature on the biometrics authentication and its
implications in the security and privacy. This will be achieved by focusing on various examples
of biometrics including: retina scan, Iris recognition, finger scanning, finger vein ID, face
recognition as well as voice recognition.
Research question
Biometrics for authentication: security and privacy implications
Introduction
Biometric authentication has been gaining more attention in the information security
sector in the recent decades. It involves the process involving a comparison of the data for
characteristics of an individual to that in the biometric template of the individual to identify if
there is any resemblance. This security strategy can be used in various cases ranging from
opening door locks to accessing computer terminals. It is as well used in proving identity of
people in form of authentication. This is achieved in multi-facet approaches some of which
include the use of retina scan, Iris recognition, finger scanning, finger vein ID, face recognition
as well as voice recognition technologies.
Finger printing is the example of visual biometrics that is most used. Following its
considerable ramification in security sector, the biometrics authentication for security and
privacy has attracted researchers. As such, there are a considerable number of literature on this
subject, however, only a few literature explore this critical sector to a considerable extent.
Following this rationale, this study seek to explore this critical aspect into details. In doing so,
the researchers will examine the current literature that on the subject of study.
Aim
This study aims to explore the current literature on the biometrics authentication and its
implications in the security and privacy. This will be achieved by focusing on various examples
of biometrics including: retina scan, Iris recognition, finger scanning, finger vein ID, face
recognition as well as voice recognition.
Research question

IT SECURITY RESEARCH PROJECT 3
As it explore the underlying problem identified in the previous sections, this research attempt
to provide solution to the following question:
a. How is the biometric authentication used in security and privacy?
As there are multitudinous literature on this subject, it is important to examine their
relevance as far as the biometrics authentication and its security and privacy implications are
concerned, thus the relevance of the research question.
Methodology
This approach was mainly based on qualitative analysis. By this, a number of literature
were examined using various reference management applications or libraries. The libraries that
were used for the research include IEEE, google scholar, ACM library and EndNote. In the
search process, various keywords were used. The keywords used include: “Biometric
authentication”, “Biometric authentication for security and privacy”, “Biometric authentication
in information security” and “Biometric authentication implication in security and privacy.” The
search keys resulted to massive literature on the subject of study. Table 1 shows a summary of
the literature retrieved from the databases.
From the multitudinous literature obtained from the libraries, a few peer reviewed
literature that were relevant and coherent with the subject of study were selected for a detailed
investigation. The literature selected fall within 2012 to 2019 range. The relevant data were
obtained which the researchers analyzed and used to provide a solution to the research question.
As it explore the underlying problem identified in the previous sections, this research attempt
to provide solution to the following question:
a. How is the biometric authentication used in security and privacy?
As there are multitudinous literature on this subject, it is important to examine their
relevance as far as the biometrics authentication and its security and privacy implications are
concerned, thus the relevance of the research question.
Methodology
This approach was mainly based on qualitative analysis. By this, a number of literature
were examined using various reference management applications or libraries. The libraries that
were used for the research include IEEE, google scholar, ACM library and EndNote. In the
search process, various keywords were used. The keywords used include: “Biometric
authentication”, “Biometric authentication for security and privacy”, “Biometric authentication
in information security” and “Biometric authentication implication in security and privacy.” The
search keys resulted to massive literature on the subject of study. Table 1 shows a summary of
the literature retrieved from the databases.
From the multitudinous literature obtained from the libraries, a few peer reviewed
literature that were relevant and coherent with the subject of study were selected for a detailed
investigation. The literature selected fall within 2012 to 2019 range. The relevant data were
obtained which the researchers analyzed and used to provide a solution to the research question.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
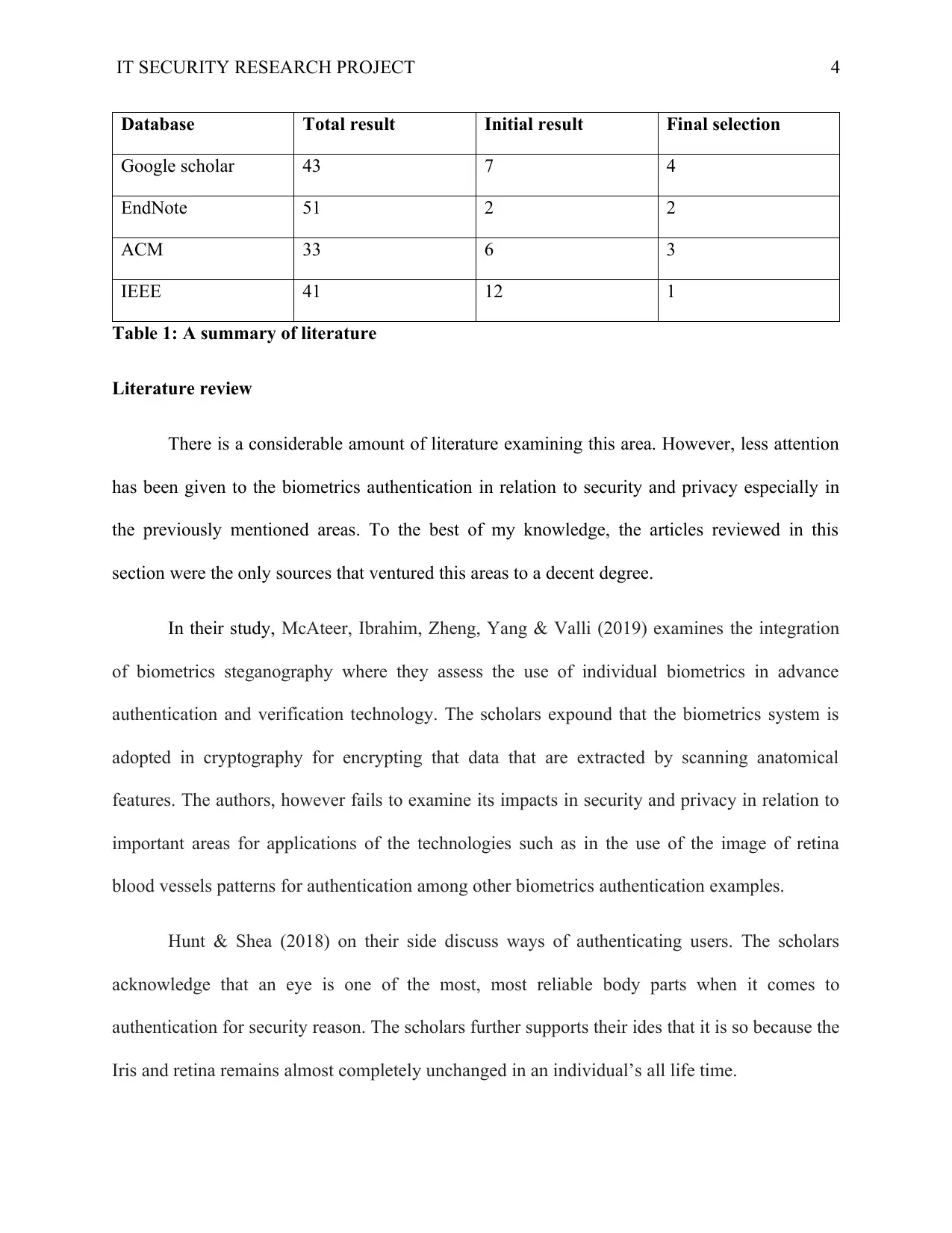
IT SECURITY RESEARCH PROJECT 4
Database Total result Initial result Final selection
Google scholar 43 7 4
EndNote 51 2 2
ACM 33 6 3
IEEE 41 12 1
Table 1: A summary of literature
Literature review
There is a considerable amount of literature examining this area. However, less attention
has been given to the biometrics authentication in relation to security and privacy especially in
the previously mentioned areas. To the best of my knowledge, the articles reviewed in this
section were the only sources that ventured this areas to a decent degree.
In their study, McAteer, Ibrahim, Zheng, Yang & Valli (2019) examines the integration
of biometrics steganography where they assess the use of individual biometrics in advance
authentication and verification technology. The scholars expound that the biometrics system is
adopted in cryptography for encrypting that data that are extracted by scanning anatomical
features. The authors, however fails to examine its impacts in security and privacy in relation to
important areas for applications of the technologies such as in the use of the image of retina
blood vessels patterns for authentication among other biometrics authentication examples.
Hunt & Shea (2018) on their side discuss ways of authenticating users. The scholars
acknowledge that an eye is one of the most, most reliable body parts when it comes to
authentication for security reason. The scholars further supports their ides that it is so because the
Iris and retina remains almost completely unchanged in an individual’s all life time.
Database Total result Initial result Final selection
Google scholar 43 7 4
EndNote 51 2 2
ACM 33 6 3
IEEE 41 12 1
Table 1: A summary of literature
Literature review
There is a considerable amount of literature examining this area. However, less attention
has been given to the biometrics authentication in relation to security and privacy especially in
the previously mentioned areas. To the best of my knowledge, the articles reviewed in this
section were the only sources that ventured this areas to a decent degree.
In their study, McAteer, Ibrahim, Zheng, Yang & Valli (2019) examines the integration
of biometrics steganography where they assess the use of individual biometrics in advance
authentication and verification technology. The scholars expound that the biometrics system is
adopted in cryptography for encrypting that data that are extracted by scanning anatomical
features. The authors, however fails to examine its impacts in security and privacy in relation to
important areas for applications of the technologies such as in the use of the image of retina
blood vessels patterns for authentication among other biometrics authentication examples.
Hunt & Shea (2018) on their side discuss ways of authenticating users. The scholars
acknowledge that an eye is one of the most, most reliable body parts when it comes to
authentication for security reason. The scholars further supports their ides that it is so because the
Iris and retina remains almost completely unchanged in an individual’s all life time.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT SECURITY RESEARCH PROJECT 5
The researchers in Jain & Nandakumar (2012), on their side examines biometrics
authentication in relation to system security and user privacy. The authors to a decent degree
explored biometrics authentication for security and user privacy. In their study, they look at the
variability of biometrics characteristics with a significant attention paid to biometrics
authentication used in large information systems.
Luckhardt (2012) in their work, explore the biometrics authentication and verifications.
The authors explain the security features including passwords and bypass within the context of
finger print biometrics authentication. In their study which involved the examination of three
biometrics authentication modalities, the study explored voice biometrics and password entry, it
was found that speaking out pins was faster in the biometrics entry. The authors further analyzed
face recognitions biometrics and concluded that there is cognitive and motor difference in the
modalities for biometrics authentication.
Findings and Discussion
As seen in the literature above, as much as the studies examined have contributed
significantly to the success of this research, there is limited information regarding biometrics
authentication with regards to security and privacy, especially in the areas like face recognition,
finger vein ID, finger scanning, Iris recognition and retina scan.
However, from the literature examined above, it can be observed that biometric
authentication is widely used in security and privacy. The authors in Hunt & Shea (2018) to a
considerable extent explored the Irish recognition and retina scan, however, little attention was
given to voice recognition and fingerprint scan. The Iris recognition technology marks features
The researchers in Jain & Nandakumar (2012), on their side examines biometrics
authentication in relation to system security and user privacy. The authors to a decent degree
explored biometrics authentication for security and user privacy. In their study, they look at the
variability of biometrics characteristics with a significant attention paid to biometrics
authentication used in large information systems.
Luckhardt (2012) in their work, explore the biometrics authentication and verifications.
The authors explain the security features including passwords and bypass within the context of
finger print biometrics authentication. In their study which involved the examination of three
biometrics authentication modalities, the study explored voice biometrics and password entry, it
was found that speaking out pins was faster in the biometrics entry. The authors further analyzed
face recognitions biometrics and concluded that there is cognitive and motor difference in the
modalities for biometrics authentication.
Findings and Discussion
As seen in the literature above, as much as the studies examined have contributed
significantly to the success of this research, there is limited information regarding biometrics
authentication with regards to security and privacy, especially in the areas like face recognition,
finger vein ID, finger scanning, Iris recognition and retina scan.
However, from the literature examined above, it can be observed that biometric
authentication is widely used in security and privacy. The authors in Hunt & Shea (2018) to a
considerable extent explored the Irish recognition and retina scan, however, little attention was
given to voice recognition and fingerprint scan. The Iris recognition technology marks features

IT SECURITY RESEARCH PROJECT 6
which are examined cameras and kept in the system then further used in authenticating the users
to ensure the system is accessed by legitimate users (Bhatia, 2013; McNay, 2013; Bhatia, 2013).
According to Yuan, Sun & Lv (2016), the finger scanners captures the photos of fingers
after which partner are printed then changed to identity codes. These codes are kept within the
system and later used to authenticate individuals. The face recognition, on the other hand
involves the use of infrared dots in mapping people’s faces and later used in authenticating users.
Voice recognition, however, as discussed involves the use of characteristics of voice. This
method uses various psychological features as well as individual behavior (Aley-Raz, Krause,
Salmon & Gazit, 2013; Pawle & Pawar, 2013). The system records the voice along with some of
the voice’s measurable features such as vocal tracks, convert into IDs and store. These features
are then used later to authenticate users to ensure that the system is accessed by the right person.
Conclusion
In summary, this document has presented a research on biometrics authentication in
relation to security and privacy. Various literature have been examined with the aid of a number
of reference management application. The findings of the study suggest that biometric based
security management for access control is a secure mechanism that ensure security and privacy.
This research provides a stepping stone for future studies. As the current research has
investigated the biometrics authentication in relation to security and privacy, the future
researchers should explore the impacts of biometrics authentication on individuals.
which are examined cameras and kept in the system then further used in authenticating the users
to ensure the system is accessed by legitimate users (Bhatia, 2013; McNay, 2013; Bhatia, 2013).
According to Yuan, Sun & Lv (2016), the finger scanners captures the photos of fingers
after which partner are printed then changed to identity codes. These codes are kept within the
system and later used to authenticate individuals. The face recognition, on the other hand
involves the use of infrared dots in mapping people’s faces and later used in authenticating users.
Voice recognition, however, as discussed involves the use of characteristics of voice. This
method uses various psychological features as well as individual behavior (Aley-Raz, Krause,
Salmon & Gazit, 2013; Pawle & Pawar, 2013). The system records the voice along with some of
the voice’s measurable features such as vocal tracks, convert into IDs and store. These features
are then used later to authenticate users to ensure that the system is accessed by the right person.
Conclusion
In summary, this document has presented a research on biometrics authentication in
relation to security and privacy. Various literature have been examined with the aid of a number
of reference management application. The findings of the study suggest that biometric based
security management for access control is a secure mechanism that ensure security and privacy.
This research provides a stepping stone for future studies. As the current research has
investigated the biometrics authentication in relation to security and privacy, the future
researchers should explore the impacts of biometrics authentication on individuals.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT SECURITY RESEARCH PROJECT 7
References
Aley-Raz, A., Krause, N. M., Salmon, M. I., & Gazit, R. Y. (2013). U.S. Patent No. 8,442,824.
Washington, DC: U.S. Patent and Trademark Office.
Bhatia, R. (2013). Biometrics and face recognition techniques. International Journal of
Advanced Research in Computer Science and Software Engineering, 3(5).
Bhatia, R. (2013). Biometrics and face recognition techniques. International Journal of
Advanced Research in Computer Science and Software Engineering, 3(5).
Hunt, H. C., & Shea, A. (2018). U.S. Patent Application No. 10/078,783.
Jain, A. K., & Nandakumar, K. (2012). Biometric Authentication: System Security and User
Privacy. IEEE Computer, 45(11), 87-92.
Luckhardt, G. W. (2012). U.S. Patent No. 8,159,328. Washington, DC: U.S. Patent and
Trademark Office.
McAteer, I., Ibrahim, A., Zheng, G., Yang, W., & Valli, C. (2019). Integration of biometrics and
steganography: A comprehensive review. Technologies, 7(2), 34.
McNay, J. H. (2013). U.S. Patent No. 8,451,105. Washington, DC: U.S. Patent and Trademark
Office.
Pawle, A. A., & Pawar, V. P. (2013). Face recognition system (FRS) on cloud computing for
user authentication. International Journal of Soft Computing and Engineering
(IJSCE), 3(4), 189-192.
References
Aley-Raz, A., Krause, N. M., Salmon, M. I., & Gazit, R. Y. (2013). U.S. Patent No. 8,442,824.
Washington, DC: U.S. Patent and Trademark Office.
Bhatia, R. (2013). Biometrics and face recognition techniques. International Journal of
Advanced Research in Computer Science and Software Engineering, 3(5).
Bhatia, R. (2013). Biometrics and face recognition techniques. International Journal of
Advanced Research in Computer Science and Software Engineering, 3(5).
Hunt, H. C., & Shea, A. (2018). U.S. Patent Application No. 10/078,783.
Jain, A. K., & Nandakumar, K. (2012). Biometric Authentication: System Security and User
Privacy. IEEE Computer, 45(11), 87-92.
Luckhardt, G. W. (2012). U.S. Patent No. 8,159,328. Washington, DC: U.S. Patent and
Trademark Office.
McAteer, I., Ibrahim, A., Zheng, G., Yang, W., & Valli, C. (2019). Integration of biometrics and
steganography: A comprehensive review. Technologies, 7(2), 34.
McNay, J. H. (2013). U.S. Patent No. 8,451,105. Washington, DC: U.S. Patent and Trademark
Office.
Pawle, A. A., & Pawar, V. P. (2013). Face recognition system (FRS) on cloud computing for
user authentication. International Journal of Soft Computing and Engineering
(IJSCE), 3(4), 189-192.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT SECURITY RESEARCH PROJECT 8
Yuan, C., Sun, X., & Lv, R. (2016). Fingerprint liveness detection based on multi-scale LPQ and
PCA. China Communications, 13(7), 60-65.
Yuan, C., Sun, X., & Lv, R. (2016). Fingerprint liveness detection based on multi-scale LPQ and
PCA. China Communications, 13(7), 60-65.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





