Case Study: Analyzing Business Information Systems at Rainbow Illusion
VerifiedAdded on 2022/09/17
|16
|3590
|22
Case Study
AI Summary
This case study analyzes the business information system of Rainbow Illusion, a retail chain selling readymade female clothes. The report examines the company's strengths in controlling sales, including the use of a distributed computing system, diversified payment methods, and invoice analysis at various stages. It differentiates between distributed and centralized computing systems, highlighting the advantages of the former. The case study also explores potential vulnerabilities that could lead to fraud, focusing on employee-related risks and situational pressures. It then discusses the importance of installing a distributed system to replace the centralized system. The assignment covers transaction cycles, financial reporting, management reporting systems, and e-commerce while addressing risks in computer-based systems, internal control processes, and opportunities for computer fraud. The report concludes with a review of the company's strengths and weaknesses in its current system.

Running Head: BUSINESS INFORMATION SYSTEM
Business Information System
Name of the University
Name of the Student
Author Note
Business Information System
Name of the University
Name of the Student
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BUSINESS INFORMATION SYSTEM
Executive Summary
The goal of the report is to analyse the strengths that can avoid the possible
problematic instances occurring in the store of Rainbow Illusion that sales readymade
female cloths. The store follows a chain process for the management of invoices also
several reviewing process is done that is later documented by the assistant manager by
reconciliation process. This report also differentiate between the distributed computing
system and the centralised computing system. The comparison shows that the
distributed system has several merits over the centralised system.
Executive Summary
The goal of the report is to analyse the strengths that can avoid the possible
problematic instances occurring in the store of Rainbow Illusion that sales readymade
female cloths. The store follows a chain process for the management of invoices also
several reviewing process is done that is later documented by the assistant manager by
reconciliation process. This report also differentiate between the distributed computing
system and the centralised computing system. The comparison shows that the
distributed system has several merits over the centralised system.

2BUSINESS INFORMATION SYSTEM
Table of Contents
Introduction........................................................................................................................3
Strength of Rainbow illusion in controlling sales...............................................................3
Advantages of the strengths..............................................................................................5
Increase of Fraud by situational pressure.........................................................................7
Aim for installation of distributed system replacing the centralized system......................8
Conclusion.......................................................................................................................11
References.......................................................................................................................12
Table of Contents
Introduction........................................................................................................................3
Strength of Rainbow illusion in controlling sales...............................................................3
Advantages of the strengths..............................................................................................5
Increase of Fraud by situational pressure.........................................................................7
Aim for installation of distributed system replacing the centralized system......................8
Conclusion.......................................................................................................................11
References.......................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BUSINESS INFORMATION SYSTEM
Introduction
This report illustrates about the illusion of the strength of the RAINBOW. This is
an array of retail stores incorporating approximately 30 outlets in the arena of South
Wales and Victoria. They deal with the purpose of vending the readymade outfits
especially designed to serve the requirements of the females. This report also mentions
about the particular instances that do not receive proper attention from the end of the
organization owing to the lack of the potential and available resources thereby rendering
strengths to the organization.
This report also mentions about the two contrasting instances that will eventually
facilitate the encounter of forged activities by the organization. This report also
thoroughly discusses about the installation of a distributed system fetching the purpose
of computation in the organization instead of the installation of a centralised system for
the purpose of computation.
Strength of Rainbow illusion in controlling sales
A brief introduction to the distributed system fetching the computational
purpose: The infrastructure of the Rainbow Illusion that deals with the processing
activities is subcategorised into a diversified number of categories incorporating the
activities like the proper and methodical selection of the items, preparation of the invoice
and finally dispatching the same to the targeted customers. All of the above-mentioned
steps are recognized by the adequate number of representatives. The expertise of the
representatives have limited access to the required one in case of a particular stage the
particular citation of which that deserves mention in this scenario is the capability of one
Introduction
This report illustrates about the illusion of the strength of the RAINBOW. This is
an array of retail stores incorporating approximately 30 outlets in the arena of South
Wales and Victoria. They deal with the purpose of vending the readymade outfits
especially designed to serve the requirements of the females. This report also mentions
about the particular instances that do not receive proper attention from the end of the
organization owing to the lack of the potential and available resources thereby rendering
strengths to the organization.
This report also mentions about the two contrasting instances that will eventually
facilitate the encounter of forged activities by the organization. This report also
thoroughly discusses about the installation of a distributed system fetching the purpose
of computation in the organization instead of the installation of a centralised system for
the purpose of computation.
Strength of Rainbow illusion in controlling sales
A brief introduction to the distributed system fetching the computational
purpose: The infrastructure of the Rainbow Illusion that deals with the processing
activities is subcategorised into a diversified number of categories incorporating the
activities like the proper and methodical selection of the items, preparation of the invoice
and finally dispatching the same to the targeted customers. All of the above-mentioned
steps are recognized by the adequate number of representatives. The expertise of the
representatives have limited access to the required one in case of a particular stage the
particular citation of which that deserves mention in this scenario is the capability of one
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BUSINESS INFORMATION SYSTEM
process to uninterrupt the other persisting processes (Morita et al. 2015). Hence, it can
be inferred that rainbow Illusion abides by the execution of the distributed system
fetching the purpose of computation activities. Every department is allocated to a group
of responsibilities to undergo and perform. There is the proper maintenance of the
chronology of the consecutive steps. Hence, the conclusion states that all the processes
associated with each steps are unique and it is comparatively easy to track and gain
access over the information in relevance to the processes.
1. Diversified mode of payment for different systems: The mode of payment
associated with the purchase process of various clothing outfits is diversified.
This incorporates the following procedures- payment processed through cheque,
payment process affiliated by card, payment through the provision of liquid cash
and also there is the provision of other payment gateways including e-wallet. For
the purpose of keeping records and documents in support of the transactions
made (Morita et al. 2015). The documentation procedure is executed in 4 ways
abiding by the structures of an ideal transaction. This provides a common
platform facilitating transaction through diversified payment modes incorporating
the payment through the cards, cheques and liquid cash.
2. Thorough and profound analysis of the invoice status at all the stages:
After the selection of the desired product, Rainbow Illusion provides a feature of
preparation of a manual invoice that would be prepared by the sales
representative. After the preparation of the manual invoice, the invoice is further
sent to the cashier at the cash counter (Wu 2017). The invoice is checked and
the input for the ordered items is done by the cashier. Hence, this crosschecking
process to uninterrupt the other persisting processes (Morita et al. 2015). Hence, it can
be inferred that rainbow Illusion abides by the execution of the distributed system
fetching the purpose of computation activities. Every department is allocated to a group
of responsibilities to undergo and perform. There is the proper maintenance of the
chronology of the consecutive steps. Hence, the conclusion states that all the processes
associated with each steps are unique and it is comparatively easy to track and gain
access over the information in relevance to the processes.
1. Diversified mode of payment for different systems: The mode of payment
associated with the purchase process of various clothing outfits is diversified.
This incorporates the following procedures- payment processed through cheque,
payment process affiliated by card, payment through the provision of liquid cash
and also there is the provision of other payment gateways including e-wallet. For
the purpose of keeping records and documents in support of the transactions
made (Morita et al. 2015). The documentation procedure is executed in 4 ways
abiding by the structures of an ideal transaction. This provides a common
platform facilitating transaction through diversified payment modes incorporating
the payment through the cards, cheques and liquid cash.
2. Thorough and profound analysis of the invoice status at all the stages:
After the selection of the desired product, Rainbow Illusion provides a feature of
preparation of a manual invoice that would be prepared by the sales
representative. After the preparation of the manual invoice, the invoice is further
sent to the cashier at the cash counter (Wu 2017). The invoice is checked and
the input for the ordered items is done by the cashier. Hence, this crosschecking

5BUSINESS INFORMATION SYSTEM
of the order details make the orders validated and the purchase procedure
becomes free of any errors.
3. Input post to sales after analysis of invoice: The initial execution of the
process of data input is done by manual processes by the representatives.
Afterwards, the invoice is sent to the cashier (Krinsky et al. 2017). The cashier
who is available at the cash counter at that point of time is responsible for
performing analysis of the invoice and fetches the purpose of entering input data
associated with the sales purpose. Thorough and proper analysis of the invoice
leads to the validation of the purchased item. In case of the entrain of any sorts
of error, the clarification is done immediately owing to the validation of the
invoice.
4. Proper maintenance of the chain process: There is a chain procedure that is
followed in a systematic order throughout the purchase processes (Snapp et al.
2017). These procedures are interconnected. Based on the priority set up by the
authority, the transactions are executed in that sequence. All the responsibilities
in relevance to the manual data entry and the validation of the invoice, are
uniformly distributed among the diversified authorities. The range incorporates
the initiation with the representatives of the sales and culminating with the higher
post managers.
5. Reconciliation of transaction record: The procedure of reconciliation refers to
the tracking and accounting of the data that is collected from the transaction
performed in an entire day. This is indeed a crucial function that is needed to be
executed on a day-to-day basis (Snapp et al. 2017). This entire procedure is
of the order details make the orders validated and the purchase procedure
becomes free of any errors.
3. Input post to sales after analysis of invoice: The initial execution of the
process of data input is done by manual processes by the representatives.
Afterwards, the invoice is sent to the cashier (Krinsky et al. 2017). The cashier
who is available at the cash counter at that point of time is responsible for
performing analysis of the invoice and fetches the purpose of entering input data
associated with the sales purpose. Thorough and proper analysis of the invoice
leads to the validation of the purchased item. In case of the entrain of any sorts
of error, the clarification is done immediately owing to the validation of the
invoice.
4. Proper maintenance of the chain process: There is a chain procedure that is
followed in a systematic order throughout the purchase processes (Snapp et al.
2017). These procedures are interconnected. Based on the priority set up by the
authority, the transactions are executed in that sequence. All the responsibilities
in relevance to the manual data entry and the validation of the invoice, are
uniformly distributed among the diversified authorities. The range incorporates
the initiation with the representatives of the sales and culminating with the higher
post managers.
5. Reconciliation of transaction record: The procedure of reconciliation refers to
the tracking and accounting of the data that is collected from the transaction
performed in an entire day. This is indeed a crucial function that is needed to be
executed on a day-to-day basis (Snapp et al. 2017). This entire procedure is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BUSINESS INFORMATION SYSTEM
monitored and executed by the assistant manager in charge of the store. The
reconciliation report is reviewed by the assistant manager of the store at the day
end. The reconciliation report is prepared by the assistant manager appointed by
the Rainbow Illusion.
Advantages of the strengths
The strengths possessed by the Rainbow Illusion fetching the purpose of sales
control on the behalf of the organization permits them with the certain instances that will
eventually compel them to overlook certain instances, which in turn can render a
negative impact on the business. Abiding by the proper chronology, the first key
strength is to introduce a distributed system for the purpose of computation of the
business system. This distributed computing system classifies the transaction
procedure into several steps (Krinsky et al. 2017). The individuals directly or indirectly
involved at different steps of transactions are directly responsible to accomplish the
tasks allocated to them. Classification of the representatives on the basis of category,
eventually minimizes the risks and errors that may creep into the scenario in the later
times. In the event of the occurrence of an error, the procedure of the detection of the
same in a specific department will be comparatively easy. The required corrections and
the amendments can be executed in a concise tiome frame. The computing system that
is distributed as per category, automates the store by reducing the dependency on the
representatives. This procedure is executed in an efficient manner.
Abiding by the chronological order, the second key strength is top incorporate
monitored and executed by the assistant manager in charge of the store. The
reconciliation report is reviewed by the assistant manager of the store at the day
end. The reconciliation report is prepared by the assistant manager appointed by
the Rainbow Illusion.
Advantages of the strengths
The strengths possessed by the Rainbow Illusion fetching the purpose of sales
control on the behalf of the organization permits them with the certain instances that will
eventually compel them to overlook certain instances, which in turn can render a
negative impact on the business. Abiding by the proper chronology, the first key
strength is to introduce a distributed system for the purpose of computation of the
business system. This distributed computing system classifies the transaction
procedure into several steps (Krinsky et al. 2017). The individuals directly or indirectly
involved at different steps of transactions are directly responsible to accomplish the
tasks allocated to them. Classification of the representatives on the basis of category,
eventually minimizes the risks and errors that may creep into the scenario in the later
times. In the event of the occurrence of an error, the procedure of the detection of the
same in a specific department will be comparatively easy. The required corrections and
the amendments can be executed in a concise tiome frame. The computing system that
is distributed as per category, automates the store by reducing the dependency on the
representatives. This procedure is executed in an efficient manner.
Abiding by the chronological order, the second key strength is top incorporate
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BUSINESS INFORMATION SYSTEM
diversified modes for the purpose of payment associated with the purchase of a
particular commodity (Pagalday et al. 2018). This facilitates the acknowledgement and
the identification of the modes of payment and their after effects. The employment of a
single system facilitating the purpose of payment will turn out to be a time consuming
procedure owing to the remittance of the sorting procedure. Hence, the suggested
methodology is the incorporation of the separate and discrete system fetching the
purpose of tracking down the issues associated with the order.
In the line of chronology, the third dominant strength is to analyse the invoice of
the transaction that imparts stability to the system at all stages incorporating the minute
details in relevance to the transaction (Prey et al. 2018). The outcome is beneficial in
the regard that negligible errors are detected in the concerned invoices leading to an
enhancement in the accuracy of the procedures employed to fetch the required
purpose. Thus the organization renders full assurance of the less error oriented systems
facilitated through the intrusion of these procedures in the mode of transaction.
The fourth strength is to maintain a harmonised chain procedure through proper
analysis of the methods incorporated within the infrastructure of the procedure prior to
the dispatch of the orders (Morita et al. 2015) . The relationship between the stage of
authority and the corresponding responsibility is directly proportional. The enhancement
in the level of the authority is witnessed by the elevation in the level of the
corresponding responsibilities. This facilitates the multiple verification of the process
and confirmation of the same. This minimizes the percentage of the occurrence of the
error.
The fifth fundamental strength wipes out the possibilities of the entrain of the
diversified modes for the purpose of payment associated with the purchase of a
particular commodity (Pagalday et al. 2018). This facilitates the acknowledgement and
the identification of the modes of payment and their after effects. The employment of a
single system facilitating the purpose of payment will turn out to be a time consuming
procedure owing to the remittance of the sorting procedure. Hence, the suggested
methodology is the incorporation of the separate and discrete system fetching the
purpose of tracking down the issues associated with the order.
In the line of chronology, the third dominant strength is to analyse the invoice of
the transaction that imparts stability to the system at all stages incorporating the minute
details in relevance to the transaction (Prey et al. 2018). The outcome is beneficial in
the regard that negligible errors are detected in the concerned invoices leading to an
enhancement in the accuracy of the procedures employed to fetch the required
purpose. Thus the organization renders full assurance of the less error oriented systems
facilitated through the intrusion of these procedures in the mode of transaction.
The fourth strength is to maintain a harmonised chain procedure through proper
analysis of the methods incorporated within the infrastructure of the procedure prior to
the dispatch of the orders (Morita et al. 2015) . The relationship between the stage of
authority and the corresponding responsibility is directly proportional. The enhancement
in the level of the authority is witnessed by the elevation in the level of the
corresponding responsibilities. This facilitates the multiple verification of the process
and confirmation of the same. This minimizes the percentage of the occurrence of the
error.
The fifth fundamental strength wipes out the possibilities of the entrain of the

8BUSINESS INFORMATION SYSTEM
errors creeping into the system owing to the thoroughly analysis of the invoice in
subsequent stages. The succeeding procedure is the manual input of the data (Wu
2017).
The ultimate strength that is the sixth strength is to document the entire
procedure of transaction. The final outcome is the collection and the accumulation of the
multiple fragments of the transactions (Wu 2017). The procedure of reconciliation that is
incorporated within the structural framework of the system is capable to successfully
wipe out all the abandoned confusion that can creep between the departments at any
point of time. There is the provision for the maintenance of the hard copy in relevance to
the electronic transactions done. This facilitates to sort the data in a structured array. In
the event of the occurrence of an error, there is the provision for the recollection of the
data in a rectified format exhibited by the concerned authority responsible for the
purpose of maintenance of the concerned department.
Increase of Fraud by situational pressure
There are certain vulnerabilities associated with the system, which exposes the
system to forged activities in some influenced and manipulated scenarios. The prime
target in this situation are the employees of the organization (Chen, Wu and Miau
2015). . The potential strengths of the scenario imparts profound impact on the
involvement of the organization in regards to the occurrence of the highlighted issues
encircling the targeted employee. The category of the scenarios can be personal or
professional in nature depending upon the situation. The outcome of such situation
often results in the forged activities in regards to the finance and the information based
errors creeping into the system owing to the thoroughly analysis of the invoice in
subsequent stages. The succeeding procedure is the manual input of the data (Wu
2017).
The ultimate strength that is the sixth strength is to document the entire
procedure of transaction. The final outcome is the collection and the accumulation of the
multiple fragments of the transactions (Wu 2017). The procedure of reconciliation that is
incorporated within the structural framework of the system is capable to successfully
wipe out all the abandoned confusion that can creep between the departments at any
point of time. There is the provision for the maintenance of the hard copy in relevance to
the electronic transactions done. This facilitates to sort the data in a structured array. In
the event of the occurrence of an error, there is the provision for the recollection of the
data in a rectified format exhibited by the concerned authority responsible for the
purpose of maintenance of the concerned department.
Increase of Fraud by situational pressure
There are certain vulnerabilities associated with the system, which exposes the
system to forged activities in some influenced and manipulated scenarios. The prime
target in this situation are the employees of the organization (Chen, Wu and Miau
2015). . The potential strengths of the scenario imparts profound impact on the
involvement of the organization in regards to the occurrence of the highlighted issues
encircling the targeted employee. The category of the scenarios can be personal or
professional in nature depending upon the situation. The outcome of such situation
often results in the forged activities in regards to the finance and the information based
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BUSINESS INFORMATION SYSTEM
aspects of the organization. There is the existence of two such forged based situations,
which accounts for the encounter of the fraudulent based enterprises:
1. In the scenarios when an employee of the organization is facing risks and
encountering potential threats on the behalf of some lawbreakers for the
accomplishment of the purpose of his customised interest. That particular
employee is responsible for the forged activities to the organization. This sort of
situation compels the employees to get indulged in imparting negative impact to
the store.
2. An employee is subjected to get sick at any point of time and in due course of the
treatment procedure, a good amount of capital is incurred on the behalf of the
organization.
The prime instance that gains supremacy in this regard is the activities of
threatening and blackmailing. The occurrence of this situation owes to the
accomplishment of the target of extortion. The categories of risks and threats are of
two types- personal and professional approach (May and Bhardwa 2018). The prime
target of the extortion activities is to execute the forged activities to the company
rendered through the employees in due course of revenue generation and the
information. These blackmails and the threats are witnessed among the rival
organizations. The major drawbacks in this regard is the scenarios are exposed in
the public forum only after the proper execution of the forged activities.
Challenges are encountered in the detection of the pre occurrence of the forged
activities. Several organizations witness fraudulent activities in regards to the
revenue or information through the extortion activities.
aspects of the organization. There is the existence of two such forged based situations,
which accounts for the encounter of the fraudulent based enterprises:
1. In the scenarios when an employee of the organization is facing risks and
encountering potential threats on the behalf of some lawbreakers for the
accomplishment of the purpose of his customised interest. That particular
employee is responsible for the forged activities to the organization. This sort of
situation compels the employees to get indulged in imparting negative impact to
the store.
2. An employee is subjected to get sick at any point of time and in due course of the
treatment procedure, a good amount of capital is incurred on the behalf of the
organization.
The prime instance that gains supremacy in this regard is the activities of
threatening and blackmailing. The occurrence of this situation owes to the
accomplishment of the target of extortion. The categories of risks and threats are of
two types- personal and professional approach (May and Bhardwa 2018). The prime
target of the extortion activities is to execute the forged activities to the company
rendered through the employees in due course of revenue generation and the
information. These blackmails and the threats are witnessed among the rival
organizations. The major drawbacks in this regard is the scenarios are exposed in
the public forum only after the proper execution of the forged activities.
Challenges are encountered in the detection of the pre occurrence of the forged
activities. Several organizations witness fraudulent activities in regards to the
revenue or information through the extortion activities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
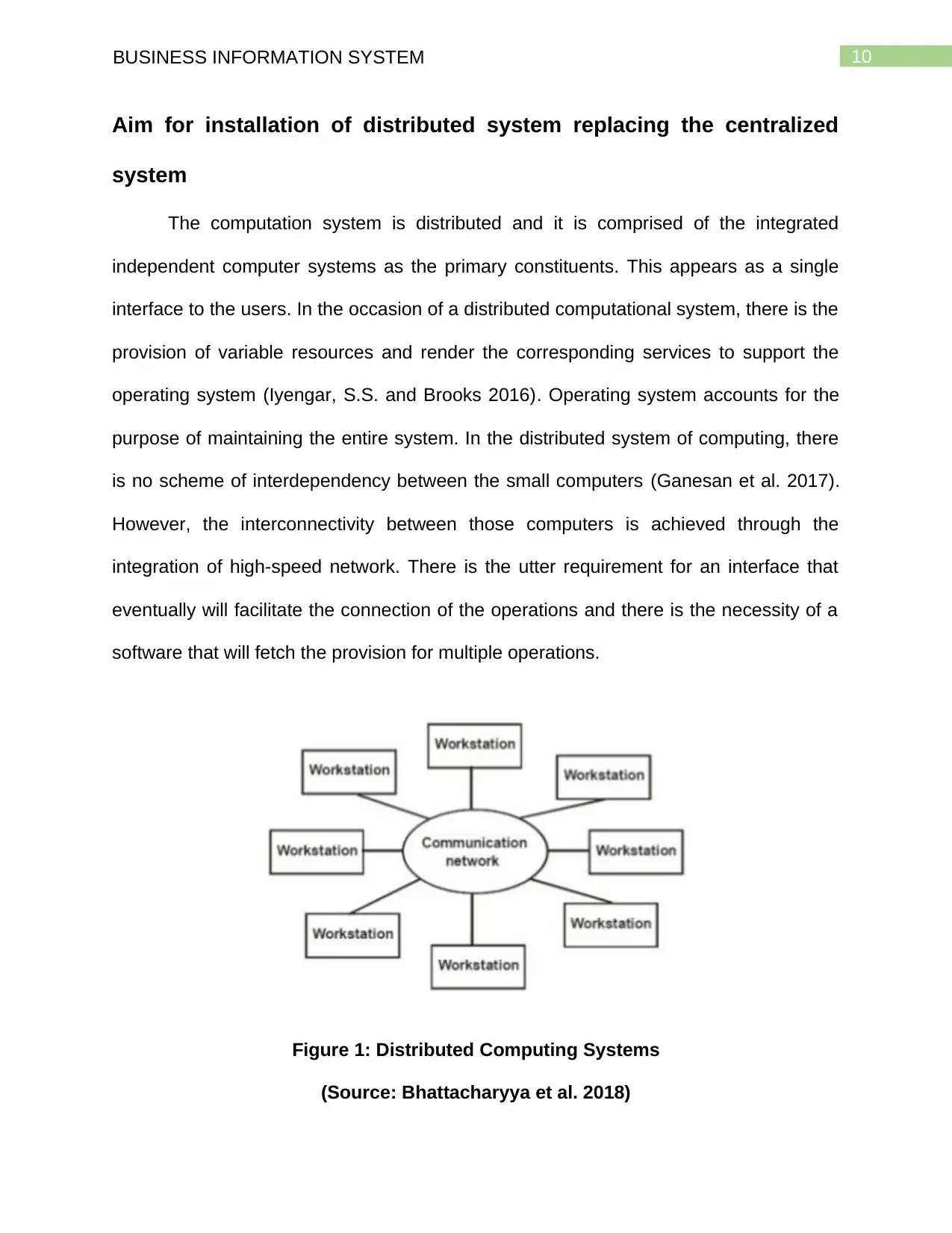
10BUSINESS INFORMATION SYSTEM
Aim for installation of distributed system replacing the centralized
system
The computation system is distributed and it is comprised of the integrated
independent computer systems as the primary constituents. This appears as a single
interface to the users. In the occasion of a distributed computational system, there is the
provision of variable resources and render the corresponding services to support the
operating system (Iyengar, S.S. and Brooks 2016). Operating system accounts for the
purpose of maintaining the entire system. In the distributed system of computing, there
is no scheme of interdependency between the small computers (Ganesan et al. 2017).
However, the interconnectivity between those computers is achieved through the
integration of high-speed network. There is the utter requirement for an interface that
eventually will facilitate the connection of the operations and there is the necessity of a
software that will fetch the provision for multiple operations.
Figure 1: Distributed Computing Systems
(Source: Bhattacharyya et al. 2018)
Aim for installation of distributed system replacing the centralized
system
The computation system is distributed and it is comprised of the integrated
independent computer systems as the primary constituents. This appears as a single
interface to the users. In the occasion of a distributed computational system, there is the
provision of variable resources and render the corresponding services to support the
operating system (Iyengar, S.S. and Brooks 2016). Operating system accounts for the
purpose of maintaining the entire system. In the distributed system of computing, there
is no scheme of interdependency between the small computers (Ganesan et al. 2017).
However, the interconnectivity between those computers is achieved through the
integration of high-speed network. There is the utter requirement for an interface that
eventually will facilitate the connection of the operations and there is the necessity of a
software that will fetch the provision for multiple operations.
Figure 1: Distributed Computing Systems
(Source: Bhattacharyya et al. 2018)

11BUSINESS INFORMATION SYSTEM
Several organizations have installed the distributed computing system within their
infrastructure for availing the overriding of the benefits on the top of the centralised
system for computation. The beneficial aspects are:
Fault and redundancy tolerance- The capability of a distributed computing
system is much higher in contrast to the systems that are centralized in nature.
In the particular scenario where a particular system gets out of order, there is no
negative impact on the business operation of the organization (Sanders et al.
2016). However, this is not the case of the centralised system for the
computation activities. A particular citation in this scenario is the operation of the
40 systems at a time, when all of the sudden a particular system gets out of
order. Since the system is not a centralised a system of computation, the
disorder of a single system will not render hindrance in the way of the operation
of the system.
Cost effectiveness- In terms of cost effectiveness, distributed computational
system gains supremacy over the centralised system for the computation (Wu
2017). The cost incurred after the installation purpose is higher in the case of
centralised computational system in contrast to the distributed computational
system. Even the cost incurred after the maintenance purpose is also higher in
the case of the centralised system for the computation when contrasted to the
distributed system for computation.
Scalability and Modular Development- In terms of the scalability, the
distributed computational system is at elevation owing to the horizontal variation
on the top of the system (Yang, Xiao and Poor 2018). The incorporation of the
Several organizations have installed the distributed computing system within their
infrastructure for availing the overriding of the benefits on the top of the centralised
system for computation. The beneficial aspects are:
Fault and redundancy tolerance- The capability of a distributed computing
system is much higher in contrast to the systems that are centralized in nature.
In the particular scenario where a particular system gets out of order, there is no
negative impact on the business operation of the organization (Sanders et al.
2016). However, this is not the case of the centralised system for the
computation activities. A particular citation in this scenario is the operation of the
40 systems at a time, when all of the sudden a particular system gets out of
order. Since the system is not a centralised a system of computation, the
disorder of a single system will not render hindrance in the way of the operation
of the system.
Cost effectiveness- In terms of cost effectiveness, distributed computational
system gains supremacy over the centralised system for the computation (Wu
2017). The cost incurred after the installation purpose is higher in the case of
centralised computational system in contrast to the distributed computational
system. Even the cost incurred after the maintenance purpose is also higher in
the case of the centralised system for the computation when contrasted to the
distributed system for computation.
Scalability and Modular Development- In terms of the scalability, the
distributed computational system is at elevation owing to the horizontal variation
on the top of the system (Yang, Xiao and Poor 2018). The incorporation of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





