Blockchain-Based Cybersecurity in Financial Services Project
VerifiedAdded on 2022/10/06
|15
|2340
|19
Project
AI Summary
This project proposal delves into the application of blockchain technology to enhance cybersecurity within the financial services industry. The research begins by identifying the rising threat of cyberattacks and the vulnerabilities within interconnected financial networks. It justifies the purpose of using blockchain to improve security, detailing research questions such as blockchain's security-focused applications, its implementation in cybersecurity, and methods for managing security without cryptocurrency tokens. The methodology includes an analysis of existing literature, qualitative research methods, and various data collection and system design methods, along with considerations for ethical issues and compliance requirements. The project plan outlines deliverables, a work breakdown structure, risk analysis, and a Gantt chart to illustrate the project's timeline and milestones. The project aims to provide insights into how blockchain can be utilized to create a more secure and robust financial ecosystem.

Running head: EMERGING TECHNOLOGY AND INNOVATION
EMERGING TECHNOLOGY AND INNOVATION
Name of the Student:
Name of the University:
Author Note:
EMERGING TECHNOLOGY AND INNOVATION
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
EMERGING TECHNOLOGY AND INNOVATION
Table of Contents
Topic..........................................................................................................................................3
1. Rationale................................................................................................................................3
1.1 Problem Domain..............................................................................................................3
1.2 Purpose and justification..................................................................................................4
2. Supervisor Approval..............................................................................................................4
3. Research Questions................................................................................................................4
4. Conceptual or theoretical framework.....................................................................................5
5. Methodology..........................................................................................................................5
5.1 Analysis of sources of information..................................................................................5
5.2 Research Methods............................................................................................................6
5.3 Data collection or system design methods.......................................................................6
5.4 Ethical Issues....................................................................................................................7
5.5 Compliance Requirements...............................................................................................8
6. Project Plan............................................................................................................................8
6.1 Deliverables......................................................................................................................8
6.2 Work Breakdown Structure............................................................................................10
6.3 Risk Analysis.................................................................................................................10
6.4 Duration..........................................................................................................................11
6.5 Gantt Chart.....................................................................................................................12
7. References............................................................................................................................13
EMERGING TECHNOLOGY AND INNOVATION
Table of Contents
Topic..........................................................................................................................................3
1. Rationale................................................................................................................................3
1.1 Problem Domain..............................................................................................................3
1.2 Purpose and justification..................................................................................................4
2. Supervisor Approval..............................................................................................................4
3. Research Questions................................................................................................................4
4. Conceptual or theoretical framework.....................................................................................5
5. Methodology..........................................................................................................................5
5.1 Analysis of sources of information..................................................................................5
5.2 Research Methods............................................................................................................6
5.3 Data collection or system design methods.......................................................................6
5.4 Ethical Issues....................................................................................................................7
5.5 Compliance Requirements...............................................................................................8
6. Project Plan............................................................................................................................8
6.1 Deliverables......................................................................................................................8
6.2 Work Breakdown Structure............................................................................................10
6.3 Risk Analysis.................................................................................................................10
6.4 Duration..........................................................................................................................11
6.5 Gantt Chart.....................................................................................................................12
7. References............................................................................................................................13

2
EMERGING TECHNOLOGY AND INNOVATION
Topic- Cyber security using blockchain in financial services
1. Rationale
1.1 Problem Domain
Related to recent outcomes, the frequency of the cyber-attacks taking place
within the financial systems have identified cyber security as one of the most rising
threat to the financial service industry (Singh & Singh, 2016). However, due to the
interconnected network shared by the financial systems, an individual bank hit by a
specific cyber-attack has an effect upon the other banks as well as the financial
organizations lying within the same concerned field.
All of these considerations have been applied with an equal force of allowing
the blockchains to come into play as a consideration of the interconnections. Since,
the financial systems utilize and implement the use of blockchains provisioning only
the trusted organizations to have a share within the data as and when required
(Trautman, 2016). The implementation of the blockchain leads to the enhancement of
services as well as the operations, the participants within the industry along with the
consideration of cyber security abilities with the high rising risks associated to it.
Despite the presence of benefits related to the implementation of blockchains
with the cyber security, the vulnerability of such technology relate to the risks sharing
an involvement within the human element. That includes the maintenance of
confidentiality, availability of private keys as well as integrity can include the risk to
cyber security, which can take place due to an ingestion from any external sources
(Sankar, Sindhu & Sethumadhavan, 2017). To overcome with all of these attacks, a
robust and strong program related to the cyber security is in demand of urgent
attention to deal with the cyber threats. Such steps require rigid support since the
EMERGING TECHNOLOGY AND INNOVATION
Topic- Cyber security using blockchain in financial services
1. Rationale
1.1 Problem Domain
Related to recent outcomes, the frequency of the cyber-attacks taking place
within the financial systems have identified cyber security as one of the most rising
threat to the financial service industry (Singh & Singh, 2016). However, due to the
interconnected network shared by the financial systems, an individual bank hit by a
specific cyber-attack has an effect upon the other banks as well as the financial
organizations lying within the same concerned field.
All of these considerations have been applied with an equal force of allowing
the blockchains to come into play as a consideration of the interconnections. Since,
the financial systems utilize and implement the use of blockchains provisioning only
the trusted organizations to have a share within the data as and when required
(Trautman, 2016). The implementation of the blockchain leads to the enhancement of
services as well as the operations, the participants within the industry along with the
consideration of cyber security abilities with the high rising risks associated to it.
Despite the presence of benefits related to the implementation of blockchains
with the cyber security, the vulnerability of such technology relate to the risks sharing
an involvement within the human element. That includes the maintenance of
confidentiality, availability of private keys as well as integrity can include the risk to
cyber security, which can take place due to an ingestion from any external sources
(Sankar, Sindhu & Sethumadhavan, 2017). To overcome with all of these attacks, a
robust and strong program related to the cyber security is in demand of urgent
attention to deal with the cyber threats. Such steps require rigid support since the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
EMERGING TECHNOLOGY AND INNOVATION
hackers acquire more knowledge related to the provisioned blockchains as well as the
vulnerabilities related to it.
1.2 Purpose and justification
When the tools related to public policy are being considered, which aim at the
enhancement of security related to blockchains, that of cyber security as well as the
authority over the already existing rules, laws and industry guidance still remain as
the effective cyber security program derived from the blockchain deployments
(Kshetri, 2017). Howsoever, most of the providers related to cloud service which
particularly provide support to the financial industries having controls in all these
places.
When it is acting as an encouragement to the financial institutions having a
familiarity with the guidelines as well as the regulations, the cyber security are very
much relevant to the blockchain (Puthal et al., 2018). This particular process related to
the application of such standards requires newer stakeholders for the industry as well
as the related government.
2. Supervisor Approval
Yes.
3. Research Questions
What are the various security focused mainly upon the blockchain
applications?
How is the blockchain implemented and utilized within the improvement of
cyber security?
EMERGING TECHNOLOGY AND INNOVATION
hackers acquire more knowledge related to the provisioned blockchains as well as the
vulnerabilities related to it.
1.2 Purpose and justification
When the tools related to public policy are being considered, which aim at the
enhancement of security related to blockchains, that of cyber security as well as the
authority over the already existing rules, laws and industry guidance still remain as
the effective cyber security program derived from the blockchain deployments
(Kshetri, 2017). Howsoever, most of the providers related to cloud service which
particularly provide support to the financial industries having controls in all these
places.
When it is acting as an encouragement to the financial institutions having a
familiarity with the guidelines as well as the regulations, the cyber security are very
much relevant to the blockchain (Puthal et al., 2018). This particular process related to
the application of such standards requires newer stakeholders for the industry as well
as the related government.
2. Supervisor Approval
Yes.
3. Research Questions
What are the various security focused mainly upon the blockchain
applications?
How is the blockchain implemented and utilized within the improvement of
cyber security?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
EMERGING TECHNOLOGY AND INNOVATION
What are the various methods which are available for the blockchains related
solutions in the process of managing security without the requirement of
crypto currency token in the financial sectors?
4. Conceptual or theoretical framework
A number of different use cases related to that of the blockchain have provided
diversifications which taken away the focus from crypto currency to that of the
implementations within the field of financial systems (Ahram et al., 2017). A current review
of the already existing current applications will help with the understanding of the full impact
within the blockchain technology completely related to the cyber security, which is providing
the entire security to the financial systems, which are existing all around the globe.
The various features related to the blockchain can have a deployment for the process
of solving the problems, which is related to the security of the existing devices along with
that of the network as well as the users (Weigold, Weigold & Russell, 2013). These entire
specific features shall provide a different understanding related to all of the methods, which
can be utilized to implement the particular blockchain related to the digital infrastructure for
the specific purposes related to that of security.
Cyber security related blockchains are very commonly referred and maintained
through a proofing mechanism through which the miners can showcase to the rest of the
network that they should make investments within significant resources for the provisioning
of validating transactions (Oh, 2014). This particular answer will aim at the particular data
which refers to the addresses of how particularly a specific blockchain can be maintained
without the actual requirement to protect the risks which have been directly provide a threat
to the existing cyber security within the field of financial sectors.
EMERGING TECHNOLOGY AND INNOVATION
What are the various methods which are available for the blockchains related
solutions in the process of managing security without the requirement of
crypto currency token in the financial sectors?
4. Conceptual or theoretical framework
A number of different use cases related to that of the blockchain have provided
diversifications which taken away the focus from crypto currency to that of the
implementations within the field of financial systems (Ahram et al., 2017). A current review
of the already existing current applications will help with the understanding of the full impact
within the blockchain technology completely related to the cyber security, which is providing
the entire security to the financial systems, which are existing all around the globe.
The various features related to the blockchain can have a deployment for the process
of solving the problems, which is related to the security of the existing devices along with
that of the network as well as the users (Weigold, Weigold & Russell, 2013). These entire
specific features shall provide a different understanding related to all of the methods, which
can be utilized to implement the particular blockchain related to the digital infrastructure for
the specific purposes related to that of security.
Cyber security related blockchains are very commonly referred and maintained
through a proofing mechanism through which the miners can showcase to the rest of the
network that they should make investments within significant resources for the provisioning
of validating transactions (Oh, 2014). This particular answer will aim at the particular data
which refers to the addresses of how particularly a specific blockchain can be maintained
without the actual requirement to protect the risks which have been directly provide a threat
to the existing cyber security within the field of financial sectors.

5
EMERGING TECHNOLOGY AND INNOVATION
5. Methodology
5.1 Analysis of sources of information
Within this research proposal, 12 references have been looked into for the
specific information mentioned within this research proposal, which includes all the data
related to cyber security, the different methods of data collection as well as the blockchain
security, which is being implemented within the financial sector.
The style of referencing within this research proposal is APA.
5.2 Research Methods
The procedure for research methods can be referred to the specific systema
as well as the scientific process for the methods of data collection, analysis, implication and
compilation, which pertains to any kind of project (Berthiaume et al., 2014). The existing
types of research methods can be basically divided into two parts, (1) Quantitative research
and (2) Qualitative research.
i) Quantitative research- gives a brief description about the infers as well as the
resolutions of the problems utilizing the numbers (Berthiaume et al., 2014). The
most attention is placed upon the collection of data which is numerical along with
the summary of the collected data as well as the chalking out of inferences
differed from the collected data.
ii) Qualitative research- is basically referred to as the research based upon the words,
emotions, sounds and the feelings also including the non-numerical data along
with the inclusion of unquantifiable elements present. Hence, it is considered that
the nature of data, which is not having a provision to be measured by any
numerical data, is referred to as the qualitative information.
EMERGING TECHNOLOGY AND INNOVATION
5. Methodology
5.1 Analysis of sources of information
Within this research proposal, 12 references have been looked into for the
specific information mentioned within this research proposal, which includes all the data
related to cyber security, the different methods of data collection as well as the blockchain
security, which is being implemented within the financial sector.
The style of referencing within this research proposal is APA.
5.2 Research Methods
The procedure for research methods can be referred to the specific systema
as well as the scientific process for the methods of data collection, analysis, implication and
compilation, which pertains to any kind of project (Berthiaume et al., 2014). The existing
types of research methods can be basically divided into two parts, (1) Quantitative research
and (2) Qualitative research.
i) Quantitative research- gives a brief description about the infers as well as the
resolutions of the problems utilizing the numbers (Berthiaume et al., 2014). The
most attention is placed upon the collection of data which is numerical along with
the summary of the collected data as well as the chalking out of inferences
differed from the collected data.
ii) Qualitative research- is basically referred to as the research based upon the words,
emotions, sounds and the feelings also including the non-numerical data along
with the inclusion of unquantifiable elements present. Hence, it is considered that
the nature of data, which is not having a provision to be measured by any
numerical data, is referred to as the qualitative information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
EMERGING TECHNOLOGY AND INNOVATION
Within this research proposal, the qualitative approach of research has been attained,
since there is no collection of data from the quantitative sources, which includes data
present in the form of numbers.
5.3 Data collection or system design methods
This particular process referring to the data collection methods or design of system
methods generally refer to the different procedures or sources from which the data can be
collected for a particular research proposal (Taylor, Bogdan & DeVault, 2015). The types of
data collection or system design methods are,
i) Interview-which specifically intends to the procedure of specifically
asking in person face-to-face questions, to which the respective person
replies and identifies the answers as data, which can be included within
the report.
ii) Observation- this refers to the observation of various scenarios, which
can lead to the collection of necessary data.
iii) Sampling- this refers to that particular procedure of sampling out a set
of information from a place, which can be utilized for the research
proposal.
5.4 Ethical Issues
Various issues related to ethics, which should be taken into consideration
while doing the research proposal are (Cope, 2014),
i) Honesty as well as Integrity
ii) Objectivity
iii) Carefulness
iv) Openness
EMERGING TECHNOLOGY AND INNOVATION
Within this research proposal, the qualitative approach of research has been attained,
since there is no collection of data from the quantitative sources, which includes data
present in the form of numbers.
5.3 Data collection or system design methods
This particular process referring to the data collection methods or design of system
methods generally refer to the different procedures or sources from which the data can be
collected for a particular research proposal (Taylor, Bogdan & DeVault, 2015). The types of
data collection or system design methods are,
i) Interview-which specifically intends to the procedure of specifically
asking in person face-to-face questions, to which the respective person
replies and identifies the answers as data, which can be included within
the report.
ii) Observation- this refers to the observation of various scenarios, which
can lead to the collection of necessary data.
iii) Sampling- this refers to that particular procedure of sampling out a set
of information from a place, which can be utilized for the research
proposal.
5.4 Ethical Issues
Various issues related to ethics, which should be taken into consideration
while doing the research proposal are (Cope, 2014),
i) Honesty as well as Integrity
ii) Objectivity
iii) Carefulness
iv) Openness
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
EMERGING TECHNOLOGY AND INNOVATION
v) Respect for intellectual property
vi) Confidentiality
vii) Publication of Response
viii) Legality
ix) Care for animals
x) Protection of Human subjects
5.5 Compliance Requirements
The compliances, which should be met before the research proposal are,
i) Eligibility of principal investigator
ii) Conflict of Interest (COI)
iii) Human Research Protection Program (HRPP)
iv) Institutional Animal Care and Use Committee (IACUC)
v) Patent Policy Acknowledgement Agreement (PPAA)
vi) Veterans Administration Memorandum of Understanding ( VA MOU)
6. Project Plan
6.1 Deliverables
Task Name
Weekly Progress Reporting
Submitting the weekly progress report
Follow-up of weekly reports
Discussion of format
EMERGING TECHNOLOGY AND INNOVATION
v) Respect for intellectual property
vi) Confidentiality
vii) Publication of Response
viii) Legality
ix) Care for animals
x) Protection of Human subjects
5.5 Compliance Requirements
The compliances, which should be met before the research proposal are,
i) Eligibility of principal investigator
ii) Conflict of Interest (COI)
iii) Human Research Protection Program (HRPP)
iv) Institutional Animal Care and Use Committee (IACUC)
v) Patent Policy Acknowledgement Agreement (PPAA)
vi) Veterans Administration Memorandum of Understanding ( VA MOU)
6. Project Plan
6.1 Deliverables
Task Name
Weekly Progress Reporting
Submitting the weekly progress report
Follow-up of weekly reports
Discussion of format

8
EMERGING TECHNOLOGY AND INNOVATION
Following of study schedule
Project proposal and plan development
Using of project blog
Updating the blog weekly
Annotated Bibliography
Collection of articles
Analysis of bibliography
Using of Search tools
Installation of EndNote X7
Checking of academic integrity
Building and writing of annotated bibliography
Technology review
Using of PRIMO search tool
EMERGING TECHNOLOGY AND INNOVATION
Following of study schedule
Project proposal and plan development
Using of project blog
Updating the blog weekly
Annotated Bibliography
Collection of articles
Analysis of bibliography
Using of Search tools
Installation of EndNote X7
Checking of academic integrity
Building and writing of annotated bibliography
Technology review
Using of PRIMO search tool
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
EMERGING TECHNOLOGY AND INNOVATION
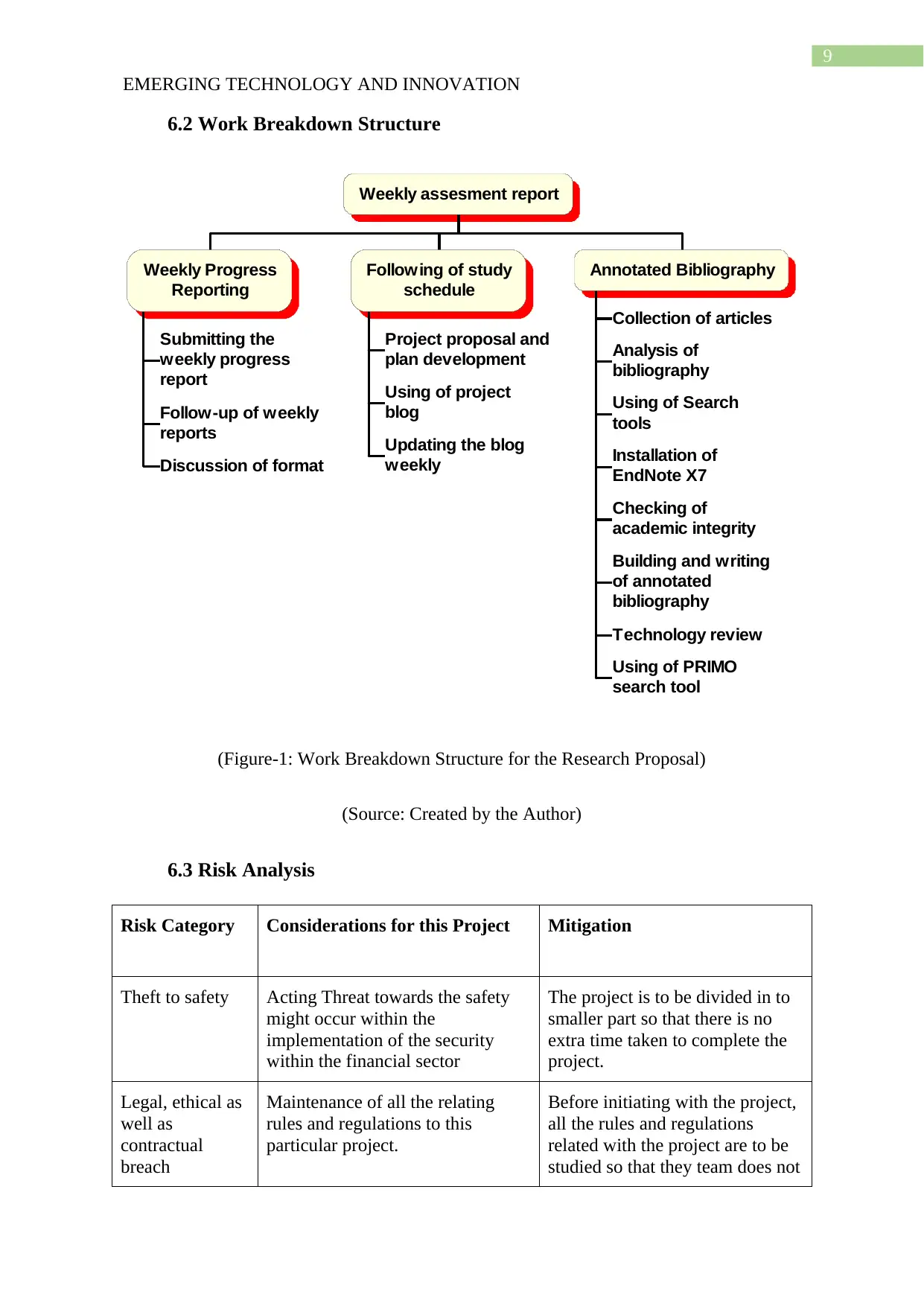
6.2 Work Breakdown Structure
Weekly assesment report
Weekly Progress
Reporting
Submitting the
weekly progress
report
Follow-up of weekly
reports
Discussion of format
Following of study
schedule
Project proposal and
plan development
Using of project
blog
Updating the blog
weekly
Annotated Bibliography
Collection of articles
Analysis of
bibliography
Using of Search
tools
Installation of
EndNote X7
Checking of
academic integrity
Building and writing
of annotated
bibliography
Technology review
Using of PRIMO
search tool
(Figure-1: Work Breakdown Structure for the Research Proposal)
(Source: Created by the Author)
6.3 Risk Analysis
Risk Category Considerations for this Project Mitigation
Theft to safety Acting Threat towards the safety
might occur within the
implementation of the security
within the financial sector
The project is to be divided in to
smaller part so that there is no
extra time taken to complete the
project.
Legal, ethical as
well as
contractual
breach
Maintenance of all the relating
rules and regulations to this
particular project.
Before initiating with the project,
all the rules and regulations
related with the project are to be
studied so that they team does not
EMERGING TECHNOLOGY AND INNOVATION
6.2 Work Breakdown Structure
Weekly assesment report
Weekly Progress
Reporting
Submitting the
weekly progress
report
Follow-up of weekly
reports
Discussion of format
Following of study
schedule
Project proposal and
plan development
Using of project
blog
Updating the blog
weekly
Annotated Bibliography
Collection of articles
Analysis of
bibliography
Using of Search
tools
Installation of
EndNote X7
Checking of
academic integrity
Building and writing
of annotated
bibliography
Technology review
Using of PRIMO
search tool
(Figure-1: Work Breakdown Structure for the Research Proposal)
(Source: Created by the Author)
6.3 Risk Analysis
Risk Category Considerations for this Project Mitigation
Theft to safety Acting Threat towards the safety
might occur within the
implementation of the security
within the financial sector
The project is to be divided in to
smaller part so that there is no
extra time taken to complete the
project.
Legal, ethical as
well as
contractual
breach
Maintenance of all the relating
rules and regulations to this
particular project.
Before initiating with the project,
all the rules and regulations
related with the project are to be
studied so that they team does not
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
EMERGING TECHNOLOGY AND INNOVATION
face any problem in future for
completing the project.
Unethical
engagement of
client
There is no unethical engagement
of the client associated with the
project. All the clients associated
with the project are ethical.
As there is no unethical
engagement of client in the
project, the project does not have
any mitigation strategy.
Threat to
achieve the
objective of the
project
The objective of the project is
achieved through all the processes
in the project schedule.
There should be no mitigation
process as the objective of the
project is to be fulfilled.
6.4 Duration
The duration of this project is for 70 days that is 12 weeks, starting from the
date of 8/8/19 and having the end of project at 11/13/19.
EMERGING TECHNOLOGY AND INNOVATION
face any problem in future for
completing the project.
Unethical
engagement of
client
There is no unethical engagement
of the client associated with the
project. All the clients associated
with the project are ethical.
As there is no unethical
engagement of client in the
project, the project does not have
any mitigation strategy.
Threat to
achieve the
objective of the
project
The objective of the project is
achieved through all the processes
in the project schedule.
There should be no mitigation
process as the objective of the
project is to be fulfilled.
6.4 Duration
The duration of this project is for 70 days that is 12 weeks, starting from the
date of 8/8/19 and having the end of project at 11/13/19.

11
EMERGING TECHNOLOGY AND INNOVATION
EMERGING TECHNOLOGY AND INNOVATION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




