Project Proposal: Analyzing Blockchain's Role in Securing IoT Networks
VerifiedAdded on 2022/08/31
|14
|3273
|20
Project
AI Summary
This project proposal investigates the potential of blockchain technology to enhance the security of Internet of Things (IoT) networks. It begins with an introduction to the increasing security threats in the field of social engineering and the vulnerabilities of IoT devices, such as data breaches and ransomware attacks. The rationale highlights the need for improved data security in IoT, driven by the increasing use of smart devices and the associated risks of data theft and privacy violations. The proposal outlines research questions focused on identifying security threats, the role of blockchain in securing user information, and potential limitations of blockchain in IoT security. The methodology involves a descriptive investigation using secondary data from peer-reviewed journals, with qualitative data analysis. The project plan includes a work breakdown structure, risk analysis, and a Gantt chart to manage the research process. The proposal explores the potential of blockchain, including its ability to maintain fundamental safety principles, secure transactions, and prevent network node failures. It also addresses the limitations of blockchain, such as its impact on processing power and scalability. The project aims to evaluate the effectiveness of blockchain in securing IoT devices and networks, contributing to a better understanding of data security in the evolving technological landscape.

Running head: POSSIBLE SECURITY CHANGE BREACHES
Possible security change breaches
Possible security change breaches
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1POSSIBLE SECURITY CHANGE BREACHES
Table of Contents
Introduction................................................................................................................................3
Rationale....................................................................................................................................3
Problem domain.....................................................................................................................3
Purpose and Justification........................................................................................................4
Supervisor approval: Yes...........................................................................................................4
Research Questions....................................................................................................................4
Conceptual Framework..............................................................................................................5
Motivation of the research.....................................................................................................5
Significance of the research...................................................................................................5
Findings of the researchers.....................................................................................................6
Materials and Methodology.......................................................................................................6
Research methods...................................................................................................................6
Data collection methods.........................................................................................................7
Ethical issues of the research.................................................................................................7
Compliance Requirements.....................................................................................................7
Solution of the problem..........................................................................................................7
Procedures of the research.....................................................................................................9
Project Plan..............................................................................................................................10
Work Breakdown Structure..................................................................................................10
Risk analysis.........................................................................................................................10
Duration................................................................................................................................11
Gantt chart............................................................................................................................12
References................................................................................................................................13
Table of Contents
Introduction................................................................................................................................3
Rationale....................................................................................................................................3
Problem domain.....................................................................................................................3
Purpose and Justification........................................................................................................4
Supervisor approval: Yes...........................................................................................................4
Research Questions....................................................................................................................4
Conceptual Framework..............................................................................................................5
Motivation of the research.....................................................................................................5
Significance of the research...................................................................................................5
Findings of the researchers.....................................................................................................6
Materials and Methodology.......................................................................................................6
Research methods...................................................................................................................6
Data collection methods.........................................................................................................7
Ethical issues of the research.................................................................................................7
Compliance Requirements.....................................................................................................7
Solution of the problem..........................................................................................................7
Procedures of the research.....................................................................................................9
Project Plan..............................................................................................................................10
Work Breakdown Structure..................................................................................................10
Risk analysis.........................................................................................................................10
Duration................................................................................................................................11
Gantt chart............................................................................................................................12
References................................................................................................................................13

2POSSIBLE SECURITY CHANGE BREACHES
Introduction
The extensive progress in the field of social engineering has led to the increase of
several security threats (Zheng, Xie, Dai, Chen, & Wang, 2018). These security threats
include ransomware and DDoS attacks, in each of these security attacks, essential data are
compromised from a system by the social engineers. In order to get back the essential data,
the victims has to pay ransom amounts in the form of bit coins (Wu, Du, Wang, & Lin,
2018). Identification of the network security vulnerabilities and the use of Intrusion Detection
System was very much useful to minimize the threats coming to these security attacks.
Currently, the social engineers are using new platforms and entirely new concepts to
compromise a network or an Internet of Things (IoT) based device (Viriyasitavat, Da Xu, Bi,
& Sapsomboon, 2019). Block chain Technology (BCT) is one of the most significant
disruptive technologies which can increase data transparency and can be very much useful to
enhance data security.
IoT based systems and devices are deployed both in our society as well as in
corporate establishments to enhance the automation and control, monitoring the essential
information, save huge amount of time and money required for the business operations (Tian,
2017). Complexities faced in our society and in offices are solved using IoT devices, thus
these devices must be free from any sort of security threats. These problems needs to get
resolved hence it is the prime motivation of this proposal. This project proposal shall be very
beneficial as it will help to identifying whether BCT is capable enough to improve the data
security of the IoT based devices.
Introduction
The extensive progress in the field of social engineering has led to the increase of
several security threats (Zheng, Xie, Dai, Chen, & Wang, 2018). These security threats
include ransomware and DDoS attacks, in each of these security attacks, essential data are
compromised from a system by the social engineers. In order to get back the essential data,
the victims has to pay ransom amounts in the form of bit coins (Wu, Du, Wang, & Lin,
2018). Identification of the network security vulnerabilities and the use of Intrusion Detection
System was very much useful to minimize the threats coming to these security attacks.
Currently, the social engineers are using new platforms and entirely new concepts to
compromise a network or an Internet of Things (IoT) based device (Viriyasitavat, Da Xu, Bi,
& Sapsomboon, 2019). Block chain Technology (BCT) is one of the most significant
disruptive technologies which can increase data transparency and can be very much useful to
enhance data security.
IoT based systems and devices are deployed both in our society as well as in
corporate establishments to enhance the automation and control, monitoring the essential
information, save huge amount of time and money required for the business operations (Tian,
2017). Complexities faced in our society and in offices are solved using IoT devices, thus
these devices must be free from any sort of security threats. These problems needs to get
resolved hence it is the prime motivation of this proposal. This project proposal shall be very
beneficial as it will help to identifying whether BCT is capable enough to improve the data
security of the IoT based devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3POSSIBLE SECURITY CHANGE BREACHES
Rationale
Problem domain
Improvement of connectivity in the modern world had both good and bad effect in our
society (Zhang & Wen, 2017). On the one hand, use of IoT based tools such as computers,
smart phones, smart home appliances, and automation tools is very much useful to make the
complex calculations in a fast and accurate modus, and one the other hand, there are
numerous security issues associated with each of these devices (Ouaddah, Abou Elkalam, &
Ait Ouahman, 2016). These security attacks can occur due to absence of security updates in
the IoT based devices, clicking on phishing emails, use of IoT as botnet platform, unsafe
communication using the IoT based devices, use of the default security passwords,
personalized information leaks, data theft, and lack of knowledge (Li et al., 2017). These are
the probable problems related with the deployment of IoT devices. Each of these problems
can have huge adverse impact in our society as well as the economy of a country. Thus, this
proposal shall be very much significant to understand how these problems can get addressed
so that the efficiency and the productivity of the IoT devices are maintained.
Purpose and Justification
BCT is very much capable of maintaining fundamental safety principles which have
to be maintained in the first place in every IoT based devices. Most of the resources and the
transactions which are conducted using the IoT devices can be secured using BCT. The hash
functions can be secured using BCT, at the same time, the decentralizing capability of BCT is
also very much beneficial to address the data security threats (Kshetri, 2017). Fault tolerance
of the IoT devices can also be maintained using BCT. At the same time, the liveliness of
those devices can also be maintained using BCT. This the purpose of this proposal is very
Rationale
Problem domain
Improvement of connectivity in the modern world had both good and bad effect in our
society (Zhang & Wen, 2017). On the one hand, use of IoT based tools such as computers,
smart phones, smart home appliances, and automation tools is very much useful to make the
complex calculations in a fast and accurate modus, and one the other hand, there are
numerous security issues associated with each of these devices (Ouaddah, Abou Elkalam, &
Ait Ouahman, 2016). These security attacks can occur due to absence of security updates in
the IoT based devices, clicking on phishing emails, use of IoT as botnet platform, unsafe
communication using the IoT based devices, use of the default security passwords,
personalized information leaks, data theft, and lack of knowledge (Li et al., 2017). These are
the probable problems related with the deployment of IoT devices. Each of these problems
can have huge adverse impact in our society as well as the economy of a country. Thus, this
proposal shall be very much significant to understand how these problems can get addressed
so that the efficiency and the productivity of the IoT devices are maintained.
Purpose and Justification
BCT is very much capable of maintaining fundamental safety principles which have
to be maintained in the first place in every IoT based devices. Most of the resources and the
transactions which are conducted using the IoT devices can be secured using BCT. The hash
functions can be secured using BCT, at the same time, the decentralizing capability of BCT is
also very much beneficial to address the data security threats (Kshetri, 2017). Fault tolerance
of the IoT devices can also be maintained using BCT. At the same time, the liveliness of
those devices can also be maintained using BCT. This the purpose of this proposal is very
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4POSSIBLE SECURITY CHANGE BREACHES
much justified as these capabilities of BCT can help to minimise or address the security
attacks on the IoT devices.
Supervisor approval: Yes
Research Questions
The research questions of this proposal are as followings:
What are the security attacks which can impact the performance of the IoT based
devices?
How can BCT secure the user information from the IoT based devices?
What are the possibilities of BCT failing to secure the IoT devices?
Is BCT is secured enough in the IoT devices?
Conceptual Framework
Explanation of the entire data security phenomenon of IoT devices can be understood
from this conceptual framework.
Motivation of the research
There are numerous security lapses related with the deployment of IoT based devices
such as insufficient testing of the devices, irregular updating of the devices, IoT
malware, IoT botnets, home invasions, hardware issues of the devices, lack of secure
update mechanism, insecure storage and transfer of data. These are the current security
problems of the IoT devices which has to get resolved. However, there are few security
measures which can minimize some of the above stated security concerns such as the IoT
security analytics, use of the public key infrastructure, ensure the security of the network
where the IoT is connected, and data authentication. Thus, this proposal shall be very much
useful to understand the ways by which BCT can secure user information.
much justified as these capabilities of BCT can help to minimise or address the security
attacks on the IoT devices.
Supervisor approval: Yes
Research Questions
The research questions of this proposal are as followings:
What are the security attacks which can impact the performance of the IoT based
devices?
How can BCT secure the user information from the IoT based devices?
What are the possibilities of BCT failing to secure the IoT devices?
Is BCT is secured enough in the IoT devices?
Conceptual Framework
Explanation of the entire data security phenomenon of IoT devices can be understood
from this conceptual framework.
Motivation of the research
There are numerous security lapses related with the deployment of IoT based devices
such as insufficient testing of the devices, irregular updating of the devices, IoT
malware, IoT botnets, home invasions, hardware issues of the devices, lack of secure
update mechanism, insecure storage and transfer of data. These are the current security
problems of the IoT devices which has to get resolved. However, there are few security
measures which can minimize some of the above stated security concerns such as the IoT
security analytics, use of the public key infrastructure, ensure the security of the network
where the IoT is connected, and data authentication. Thus, this proposal shall be very much
useful to understand the ways by which BCT can secure user information.

5POSSIBLE SECURITY CHANGE BREACHES
Significance of the research
This proposal will help its readers to understand the capabilities of BCT to ensure the
security of the user information which moves in or out of the IoT based devices. The data
security problems related to the IoT based devices must be resolved as early as possible as the
strengths and the opportunities of the social engineers all around the world is increasing every
day. Human psychology is being exploited by social engineers prior to the ant data security
attack. New social engineering techniques are being adopted by hackers to compromise data
from an IoT based device. Currently, there are no real social engineering prevention
techniques which can address the threats coming from the hackers. The centralizing feature of
the IoT systems makes it easier for hackers to compromise any sort of security attacks
(Atlam, Alenezi, Alassafi, & Wills, 2018). This research shall be very much important to
comprehend the capabilities of BCT to deal with these security threats.
Findings of the researchers
The researchers in this area are trying to find out the whether BCT in IoT always
secured or not is capable enough as there are other drawbacks related with the deployment of
BCT as well, in terms of its inability to provide network security, issues with the block chain
entries and lack of regulations. The researchers are concerned whether the limitations of this
disruptive technology can actually be useful to secure user information from ant IoT based
device.
Materials and Methodology
Research methods
This proposal shall be considering a descriptive type of investigation where each of
the discussions shall be supported with theories and relevant models. There are diverse
categories of relevant secondary information that are available in the peer-reviewed journals
Significance of the research
This proposal will help its readers to understand the capabilities of BCT to ensure the
security of the user information which moves in or out of the IoT based devices. The data
security problems related to the IoT based devices must be resolved as early as possible as the
strengths and the opportunities of the social engineers all around the world is increasing every
day. Human psychology is being exploited by social engineers prior to the ant data security
attack. New social engineering techniques are being adopted by hackers to compromise data
from an IoT based device. Currently, there are no real social engineering prevention
techniques which can address the threats coming from the hackers. The centralizing feature of
the IoT systems makes it easier for hackers to compromise any sort of security attacks
(Atlam, Alenezi, Alassafi, & Wills, 2018). This research shall be very much important to
comprehend the capabilities of BCT to deal with these security threats.
Findings of the researchers
The researchers in this area are trying to find out the whether BCT in IoT always
secured or not is capable enough as there are other drawbacks related with the deployment of
BCT as well, in terms of its inability to provide network security, issues with the block chain
entries and lack of regulations. The researchers are concerned whether the limitations of this
disruptive technology can actually be useful to secure user information from ant IoT based
device.
Materials and Methodology
Research methods
This proposal shall be considering a descriptive type of investigation where each of
the discussions shall be supported with theories and relevant models. There are diverse
categories of relevant secondary information that are available in the peer-reviewed journals
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6POSSIBLE SECURITY CHANGE BREACHES
and data from different perspectives can be interpreted from those theories. The sampling
method which shall be considered in this proposal is the probabilistic sampling method.
The main reason behind the selection of this sampling method is collection of all the relevant
and updated data. As a result, this proposal shall be free from any sort of outdated or
irrelevant information. The data collected from secondary resources shall be analysed using
qualitative data analysis technique, which means a detailed explanation and interpretation
of the collected data shall be given. The reason behind the selection of this analysis technique
is the lack of numerical value in the data which will be collected from the secondary sources.
Lack of time for doing the research and lack of budget are the prime limitations of this
proposal as well. The other two risks of this project are data redundancy and the ethical risks.
Selection of irrelevant secondary data can lead to risks like data redundancy and ethical risk
are discussed in the following sections of this proposal. The availability of these two could
have enhanced the validity of this proposal even further.
Data collection methods
This proposal shall only be considering secondary data collection method where
data shall be taken from peer-reviewed journals which are available in secondary sources.
Shortage of budget is the main reason behind selecting this data collection procedure in the
proposal.
Ethical issues of the research
There are two categories of ethical issues which is directly linked with the data
collection procedure. Maintaining the originality and integrity of the secondary data is the
prime ethical considerations of this proposal. The other ethical consideration is that the
collected secondary data cannot be used for any other purposes apart from this proposal. The
and data from different perspectives can be interpreted from those theories. The sampling
method which shall be considered in this proposal is the probabilistic sampling method.
The main reason behind the selection of this sampling method is collection of all the relevant
and updated data. As a result, this proposal shall be free from any sort of outdated or
irrelevant information. The data collected from secondary resources shall be analysed using
qualitative data analysis technique, which means a detailed explanation and interpretation
of the collected data shall be given. The reason behind the selection of this analysis technique
is the lack of numerical value in the data which will be collected from the secondary sources.
Lack of time for doing the research and lack of budget are the prime limitations of this
proposal as well. The other two risks of this project are data redundancy and the ethical risks.
Selection of irrelevant secondary data can lead to risks like data redundancy and ethical risk
are discussed in the following sections of this proposal. The availability of these two could
have enhanced the validity of this proposal even further.
Data collection methods
This proposal shall only be considering secondary data collection method where
data shall be taken from peer-reviewed journals which are available in secondary sources.
Shortage of budget is the main reason behind selecting this data collection procedure in the
proposal.
Ethical issues of the research
There are two categories of ethical issues which is directly linked with the data
collection procedure. Maintaining the originality and integrity of the secondary data is the
prime ethical considerations of this proposal. The other ethical consideration is that the
collected secondary data cannot be used for any other purposes apart from this proposal. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7POSSIBLE SECURITY CHANGE BREACHES
scholars whose opinion or theories is considered in this proposal shall be given credit in the
concluding section of this proposal in the reference page.
Compliance Requirements
Like the other countries of the world, countries like Australia have their own BCT
regulations (roadmap, 2020). Based on the policies adopted by the government of Australia, it
can be said that this disruptive technology can be used for optimising business operations
however, financial transactions cannot be done using this technology. Even if they removed
their double taxation policy for bit coin transactions, the government wants to use this
technology to boost consumer spending and encouraging them to purchase goods.
Solution of the problem
The decentralizing capability of BCT can be very much useful to secure the network
which are used by the IoT based devices (Jayaraman, Saleh, & King, 2019). Securing the
network with the peer to peer communication model supported by BCT can be very much
useful to maintain the security of the transactional data in an IoT based system. BCT can play
a huge role in stopping the failure of the network nodes which are connected with the IoT
based devices (Huckle, Bhattacharya, White, & Beloff, 2016). The distributed file sharing
capability of the IoT devices can be improved using BCT as it will help to maintain the
consistency of the user information of the IoT based devices, at the same time, this capability
can also enhance the efficiency of the network used by these devices (Chanson, Bogner,
Bilgeri, Fleisch, & Wortmann, 2019). The data security issue which occurs among two IoT
based devices can also be addressed with the help of autonomous device coordination (Ferrag
et al., 2018).
scholars whose opinion or theories is considered in this proposal shall be given credit in the
concluding section of this proposal in the reference page.
Compliance Requirements
Like the other countries of the world, countries like Australia have their own BCT
regulations (roadmap, 2020). Based on the policies adopted by the government of Australia, it
can be said that this disruptive technology can be used for optimising business operations
however, financial transactions cannot be done using this technology. Even if they removed
their double taxation policy for bit coin transactions, the government wants to use this
technology to boost consumer spending and encouraging them to purchase goods.
Solution of the problem
The decentralizing capability of BCT can be very much useful to secure the network
which are used by the IoT based devices (Jayaraman, Saleh, & King, 2019). Securing the
network with the peer to peer communication model supported by BCT can be very much
useful to maintain the security of the transactional data in an IoT based system. BCT can play
a huge role in stopping the failure of the network nodes which are connected with the IoT
based devices (Huckle, Bhattacharya, White, & Beloff, 2016). The distributed file sharing
capability of the IoT devices can be improved using BCT as it will help to maintain the
consistency of the user information of the IoT based devices, at the same time, this capability
can also enhance the efficiency of the network used by these devices (Chanson, Bogner,
Bilgeri, Fleisch, & Wortmann, 2019). The data security issue which occurs among two IoT
based devices can also be addressed with the help of autonomous device coordination (Ferrag
et al., 2018).

8POSSIBLE SECURITY CHANGE BREACHES
Figure 1: Decentralizing IoT network using BCT
Source:(Ferrag et al., 2018)
The data tracking ability of the connected IoT devices can be enhanced using help of
BCT as well. The single point failure of the IoT devices can also be minimized using the
decentralizing capability of BCT. According to Fernández-Caramés and Fraga-Lamas (2018),
the cryptographic algorithms which are used by BCT is very much secure as well as
confidential regarding the protection of user information from IoT based device. The ledger
of this disruptive technology is not at all vulnerable to the cyber security attacks such DDoS
and Ransomware.
However, in order to address the use of the advanced social engineering approaches
maintained by the hackers both encryption and distributed ledger of BCT must be enabled in
the IoT based devices. The security of user information can also be maintained using smart
contracts (Dorri, Kanhere, & Jurdak, 2016). However, the processing power of the IoT based
devices might fall due to the use of distributed ledger as well. The falling out of the
processing power may lead to other issues as well, such as the scalability issues.
Figure 1: Decentralizing IoT network using BCT
Source:(Ferrag et al., 2018)
The data tracking ability of the connected IoT devices can be enhanced using help of
BCT as well. The single point failure of the IoT devices can also be minimized using the
decentralizing capability of BCT. According to Fernández-Caramés and Fraga-Lamas (2018),
the cryptographic algorithms which are used by BCT is very much secure as well as
confidential regarding the protection of user information from IoT based device. The ledger
of this disruptive technology is not at all vulnerable to the cyber security attacks such DDoS
and Ransomware.
However, in order to address the use of the advanced social engineering approaches
maintained by the hackers both encryption and distributed ledger of BCT must be enabled in
the IoT based devices. The security of user information can also be maintained using smart
contracts (Dorri, Kanhere, & Jurdak, 2016). However, the processing power of the IoT based
devices might fall due to the use of distributed ledger as well. The falling out of the
processing power may lead to other issues as well, such as the scalability issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9POSSIBLE SECURITY CHANGE BREACHES
Procedures of the research
The procedures which will be followed in this proposal can be understood from this
section of the paper.
The research shall be initiated with the identification of the probable security threats
relayed with the use of IoT based devices.
The needs of conducting the project shall be proposed in the following step. After
identifying the problems, a set of research questions shall be proposed along with the
motivation of doing this research.
The current and previous researches shall be mentioned in the ensuing segment of
this proposal.
After this step, the details of the methodology which will be considered by the
analysts while conducting the research shall be stated with proper justification, such
as the procedure of analysing and collecting data.
The solution of the identified problems of IoT shall be mentioned from the
perspectives of popular scholars who have stated their opinion in the peer-reviewed
journals.
Procedures of the research
The procedures which will be followed in this proposal can be understood from this
section of the paper.
The research shall be initiated with the identification of the probable security threats
relayed with the use of IoT based devices.
The needs of conducting the project shall be proposed in the following step. After
identifying the problems, a set of research questions shall be proposed along with the
motivation of doing this research.
The current and previous researches shall be mentioned in the ensuing segment of
this proposal.
After this step, the details of the methodology which will be considered by the
analysts while conducting the research shall be stated with proper justification, such
as the procedure of analysing and collecting data.
The solution of the identified problems of IoT shall be mentioned from the
perspectives of popular scholars who have stated their opinion in the peer-reviewed
journals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
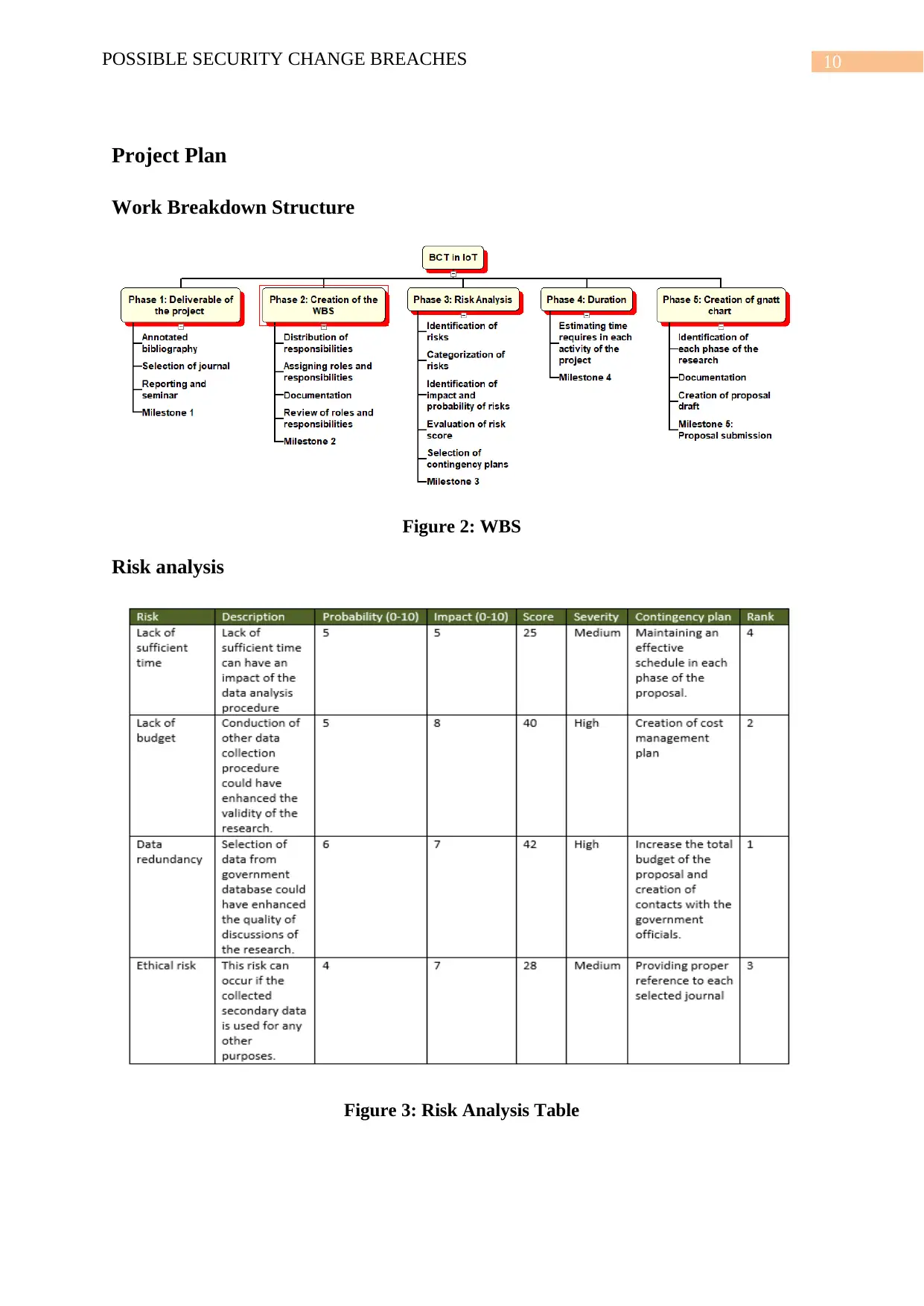
10POSSIBLE SECURITY CHANGE BREACHES
Project Plan
Work Breakdown Structure
Figure 2: WBS
Risk analysis
Figure 3: Risk Analysis Table
Project Plan
Work Breakdown Structure
Figure 2: WBS
Risk analysis
Figure 3: Risk Analysis Table
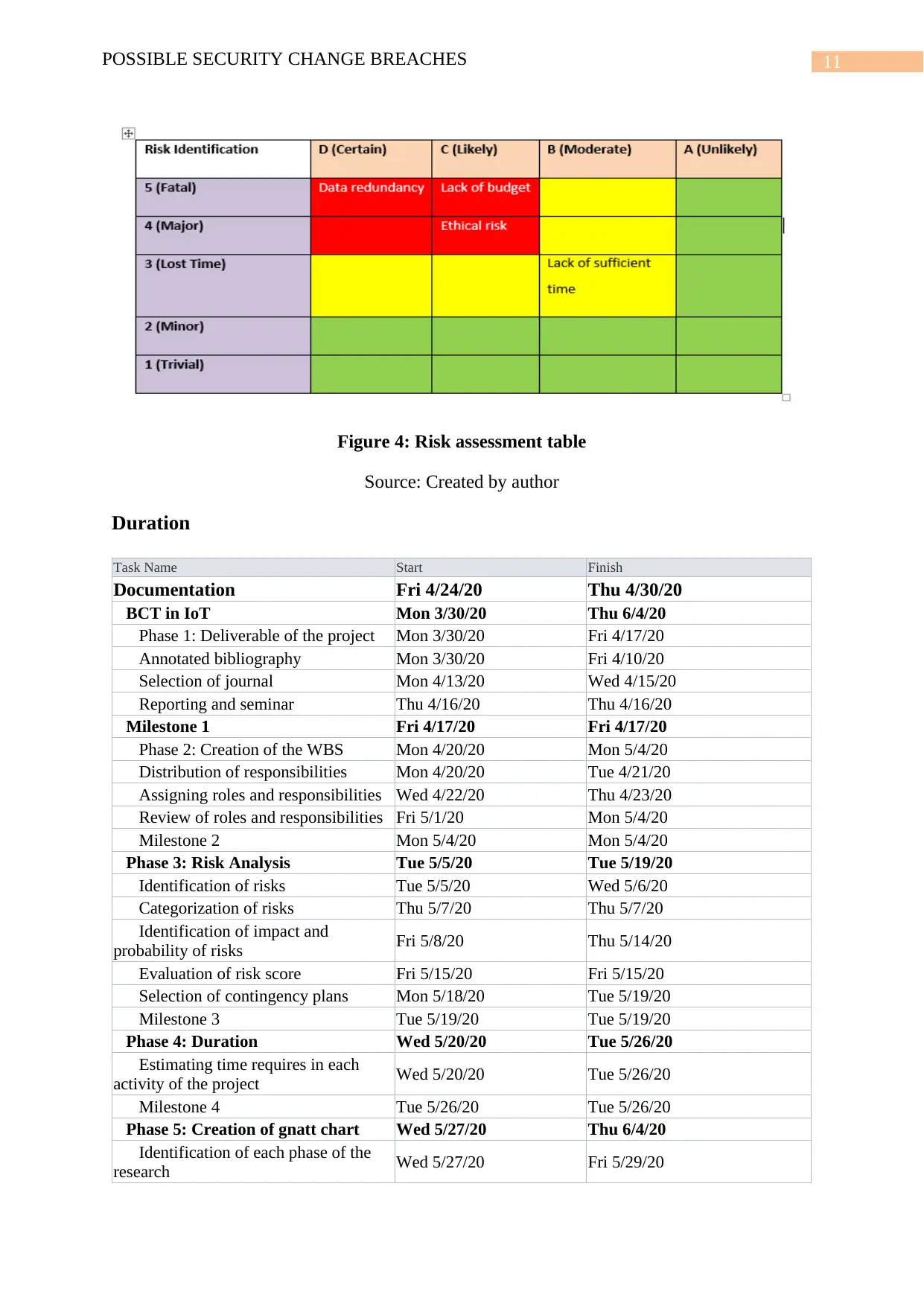
11POSSIBLE SECURITY CHANGE BREACHES
Figure 4: Risk assessment table
Source: Created by author
Duration
Task Name Start Finish
Documentation Fri 4/24/20 Thu 4/30/20
BCT in IoT Mon 3/30/20 Thu 6/4/20
Phase 1: Deliverable of the project Mon 3/30/20 Fri 4/17/20
Annotated bibliography Mon 3/30/20 Fri 4/10/20
Selection of journal Mon 4/13/20 Wed 4/15/20
Reporting and seminar Thu 4/16/20 Thu 4/16/20
Milestone 1 Fri 4/17/20 Fri 4/17/20
Phase 2: Creation of the WBS Mon 4/20/20 Mon 5/4/20
Distribution of responsibilities Mon 4/20/20 Tue 4/21/20
Assigning roles and responsibilities Wed 4/22/20 Thu 4/23/20
Review of roles and responsibilities Fri 5/1/20 Mon 5/4/20
Milestone 2 Mon 5/4/20 Mon 5/4/20
Phase 3: Risk Analysis Tue 5/5/20 Tue 5/19/20
Identification of risks Tue 5/5/20 Wed 5/6/20
Categorization of risks Thu 5/7/20 Thu 5/7/20
Identification of impact and
probability of risks Fri 5/8/20 Thu 5/14/20
Evaluation of risk score Fri 5/15/20 Fri 5/15/20
Selection of contingency plans Mon 5/18/20 Tue 5/19/20
Milestone 3 Tue 5/19/20 Tue 5/19/20
Phase 4: Duration Wed 5/20/20 Tue 5/26/20
Estimating time requires in each
activity of the project Wed 5/20/20 Tue 5/26/20
Milestone 4 Tue 5/26/20 Tue 5/26/20
Phase 5: Creation of gnatt chart Wed 5/27/20 Thu 6/4/20
Identification of each phase of the
research Wed 5/27/20 Fri 5/29/20
Figure 4: Risk assessment table
Source: Created by author
Duration
Task Name Start Finish
Documentation Fri 4/24/20 Thu 4/30/20
BCT in IoT Mon 3/30/20 Thu 6/4/20
Phase 1: Deliverable of the project Mon 3/30/20 Fri 4/17/20
Annotated bibliography Mon 3/30/20 Fri 4/10/20
Selection of journal Mon 4/13/20 Wed 4/15/20
Reporting and seminar Thu 4/16/20 Thu 4/16/20
Milestone 1 Fri 4/17/20 Fri 4/17/20
Phase 2: Creation of the WBS Mon 4/20/20 Mon 5/4/20
Distribution of responsibilities Mon 4/20/20 Tue 4/21/20
Assigning roles and responsibilities Wed 4/22/20 Thu 4/23/20
Review of roles and responsibilities Fri 5/1/20 Mon 5/4/20
Milestone 2 Mon 5/4/20 Mon 5/4/20
Phase 3: Risk Analysis Tue 5/5/20 Tue 5/19/20
Identification of risks Tue 5/5/20 Wed 5/6/20
Categorization of risks Thu 5/7/20 Thu 5/7/20
Identification of impact and
probability of risks Fri 5/8/20 Thu 5/14/20
Evaluation of risk score Fri 5/15/20 Fri 5/15/20
Selection of contingency plans Mon 5/18/20 Tue 5/19/20
Milestone 3 Tue 5/19/20 Tue 5/19/20
Phase 4: Duration Wed 5/20/20 Tue 5/26/20
Estimating time requires in each
activity of the project Wed 5/20/20 Tue 5/26/20
Milestone 4 Tue 5/26/20 Tue 5/26/20
Phase 5: Creation of gnatt chart Wed 5/27/20 Thu 6/4/20
Identification of each phase of the
research Wed 5/27/20 Fri 5/29/20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





