Report on Blockchain Security: Architectures, Applications, and Issues
VerifiedAdded on 2023/01/06
|10
|2673
|81
Report
AI Summary
This report provides a comprehensive overview of blockchain security. It begins by introducing the concept of blockchain and its importance in securing digital transactions. The main body of the report delves into the architectures and applications related to blockchain security, differentiating between centralized, decentralized, and distributed ledgers, and exploring the various elements of blockchain architecture such as nodes, transactions, blocks, chains, miners, and consensus mechanisms. Furthermore, the report identifies and analyzes critical security problems within blockchain systems, including 51 percent attacks, exchange hacks, and social engineering, offering potential solutions to mitigate these risks. The report also includes a literature research section that summarizes key concepts and findings from relevant academic sources. Overall, the report aims to provide a clear understanding of blockchain security challenges and the methods for addressing them.
Block chain
Security
1
Security
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION ..........................................................................................................................3
MAIN BODY...................................................................................................................................3
1. Architectures and application which are related to the block chain security..........................3
2. Security problems and their solution in the block chain security...........................................6
CONCLUSION ...............................................................................................................................7
LITERATURE RESEARCH ..........................................................................................................8
REFERENCES................................................................................................................................9
2
INTRODUCTION ..........................................................................................................................3
MAIN BODY...................................................................................................................................3
1. Architectures and application which are related to the block chain security..........................3
2. Security problems and their solution in the block chain security...........................................6
CONCLUSION ...............................................................................................................................7
LITERATURE RESEARCH ..........................................................................................................8
REFERENCES................................................................................................................................9
2

INTRODUCTION
In computing area system and network security is essential as that will help in conducting
work in effective as well as secure manner. A system security is consist of all facets which help
in accessing information or data assets. On the other hand network security is considered as
broad term which cover multitude of technologies, processes and device (Bodkhe and et.al.,
2020). It is mainly a rules as well as configuration planned in order to protect accessibility,
confidentiality and integrity of computer network through both hardware and software. The
respective report is based on block chain security which is a digitized as well as decentralised
ledger which boasts of tightly assured and peer to peer encryption act of confirming
transactions. Topics covered in respective report are architectures and application which are
related to the block chain security as well as it also include security problems and their solution
in the block chain security.
MAIN BODY
1. Architectures and application which are related to the block chain security
A block chain is considered as the name which implies as a chain of digital blocks which
contain records related to transactions. The records saved on a block chain are fully secured by
using cryptography. In this network associates have its own private keys which assigned to
transactions that they make as well as act as the personal digital signature (Khan and et.al.,
2020). In addition to this block chain is consist of distributed, public ledger as well as
decentralised. In 1991 first time term block chain was described. It is generally considered as
technology which have core characteristics of security, accountability as well as decentralisation.
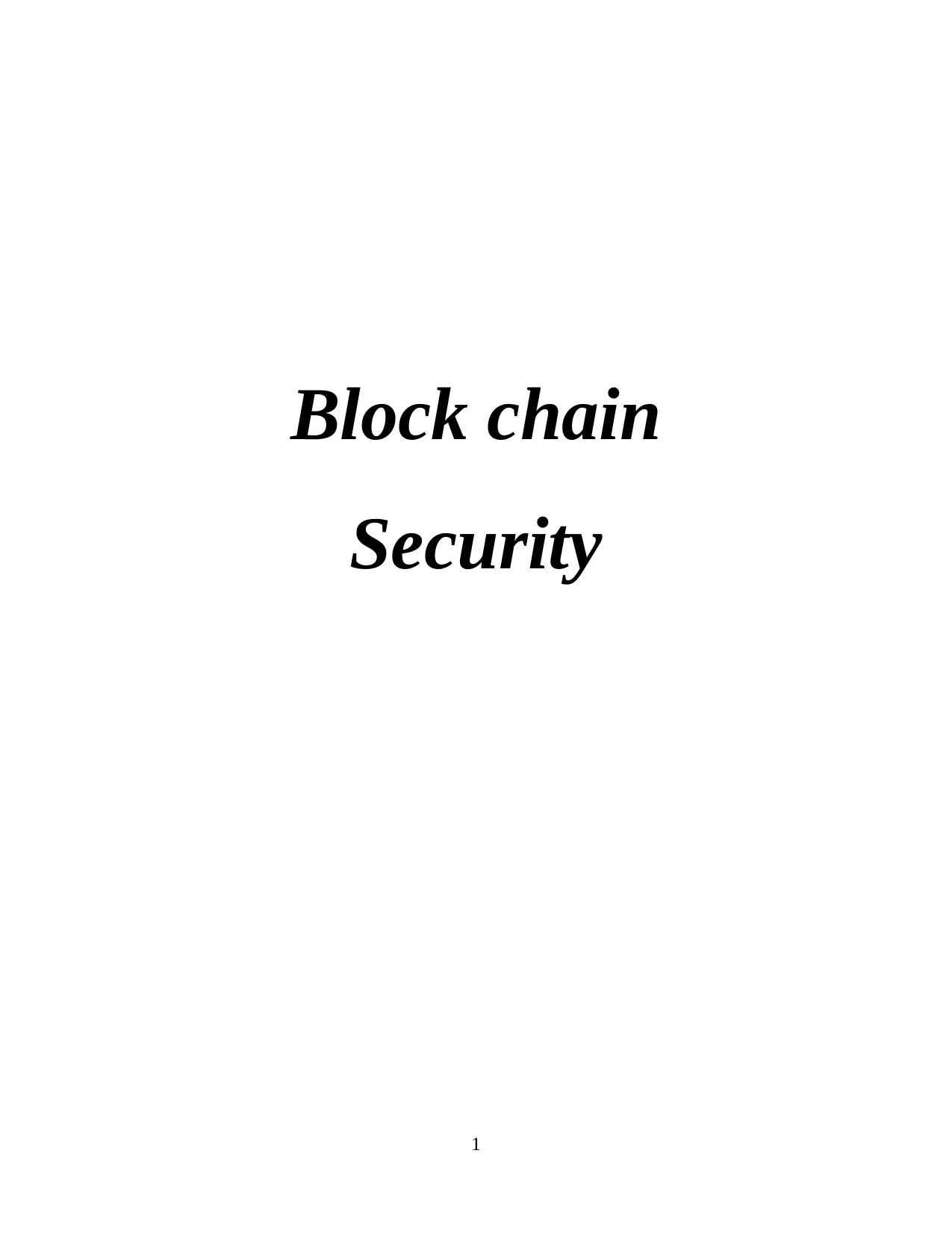
Architecture of block chain security -
The block chain security architecture is divided into three section i.e. centralized,
decentralized and distributed ledgers.
3
In computing area system and network security is essential as that will help in conducting
work in effective as well as secure manner. A system security is consist of all facets which help
in accessing information or data assets. On the other hand network security is considered as
broad term which cover multitude of technologies, processes and device (Bodkhe and et.al.,
2020). It is mainly a rules as well as configuration planned in order to protect accessibility,
confidentiality and integrity of computer network through both hardware and software. The
respective report is based on block chain security which is a digitized as well as decentralised
ledger which boasts of tightly assured and peer to peer encryption act of confirming
transactions. Topics covered in respective report are architectures and application which are
related to the block chain security as well as it also include security problems and their solution
in the block chain security.
MAIN BODY
1. Architectures and application which are related to the block chain security
A block chain is considered as the name which implies as a chain of digital blocks which
contain records related to transactions. The records saved on a block chain are fully secured by
using cryptography. In this network associates have its own private keys which assigned to
transactions that they make as well as act as the personal digital signature (Khan and et.al.,
2020). In addition to this block chain is consist of distributed, public ledger as well as
decentralised. In 1991 first time term block chain was described. It is generally considered as
technology which have core characteristics of security, accountability as well as decentralisation.
Architecture of block chain security -
The block chain security architecture is divided into three section i.e. centralized,
decentralized and distributed ledgers.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
A typical centralized block chain security is considered as system which is private in
nature since it governed or managed by a particular single group or company. But now block
chain is removing the centralized security system as in this decision power is based on the single
entity. It is also considered as the traditional security system which is simple to access the data
or information over one server as well as to download the information.
Decentralization security system did not have any core authority to dictate the truth to
any other participants in new in the network (Li and et.al., 2020). In this every participants
related to this network can easily access the history of transactions or confirm the new
transactions. In addition to this, respective security system can be use by any person without
4
Illustration 1: Block chain security architectures
Source: Blockchain Architecture Basics: Components, Structure, Benefits & Creation,
2020
nature since it governed or managed by a particular single group or company. But now block
chain is removing the centralized security system as in this decision power is based on the single
entity. It is also considered as the traditional security system which is simple to access the data
or information over one server as well as to download the information.
Decentralization security system did not have any core authority to dictate the truth to
any other participants in new in the network (Li and et.al., 2020). In this every participants
related to this network can easily access the history of transactions or confirm the new
transactions. In addition to this, respective security system can be use by any person without
4
Illustration 1: Block chain security architectures
Source: Blockchain Architecture Basics: Components, Structure, Benefits & Creation,
2020
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
using an intermediary successfully and effectively. Moreover it is also related to the request
which is access the information or data which has to be processed by the thousands of devices.
In addition to this third block chain security system architectures is distributed ledger
which is a kind of database which spread across multiple regions, sites or participants. On the
basis surface, distributed ledger is determined exactly how a system probably envision a block
chain (Mohanty and et.al., 2020). Along with this, whole block chains are considered as
distributed ledgers but it is also determined that not all distributed ledgers are names as block
chains.
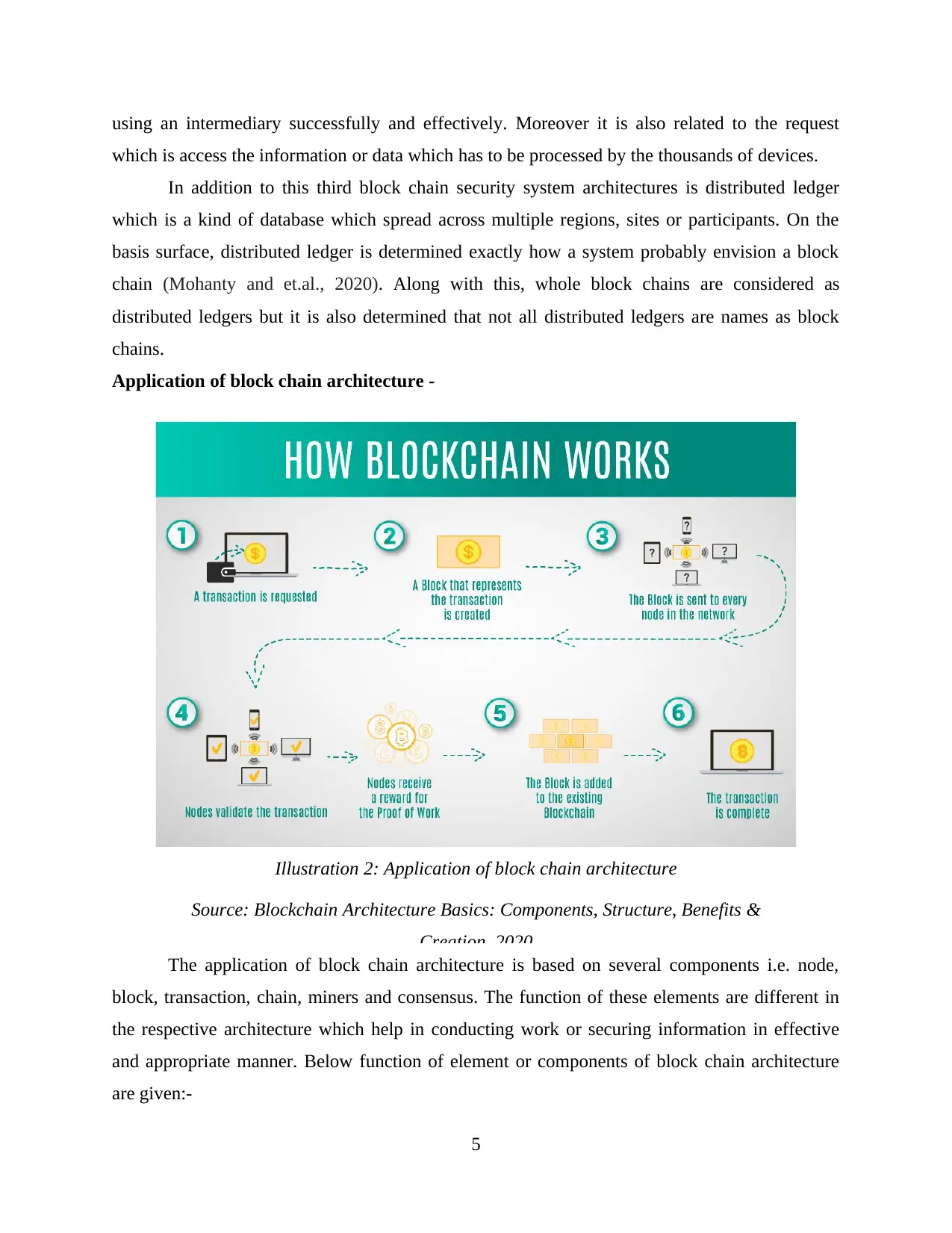
Application of block chain architecture -
The application of block chain architecture is based on several components i.e. node,
block, transaction, chain, miners and consensus. The function of these elements are different in
the respective architecture which help in conducting work or securing information in effective
and appropriate manner. Below function of element or components of block chain architecture
are given:-
5
Illustration 2: Application of block chain architecture
Source: Blockchain Architecture Basics: Components, Structure, Benefits &
Creation, 2020
which is access the information or data which has to be processed by the thousands of devices.
In addition to this third block chain security system architectures is distributed ledger
which is a kind of database which spread across multiple regions, sites or participants. On the
basis surface, distributed ledger is determined exactly how a system probably envision a block
chain (Mohanty and et.al., 2020). Along with this, whole block chains are considered as
distributed ledgers but it is also determined that not all distributed ledgers are names as block
chains.
Application of block chain architecture -
The application of block chain architecture is based on several components i.e. node,
block, transaction, chain, miners and consensus. The function of these elements are different in
the respective architecture which help in conducting work or securing information in effective
and appropriate manner. Below function of element or components of block chain architecture
are given:-
5
Illustration 2: Application of block chain architecture
Source: Blockchain Architecture Basics: Components, Structure, Benefits &
Creation, 2020

Node – It is related to computer or user within the block chain architecture (in this each
has an independent copy of the all block chain ledger).
Transaction – It is related with the smallest building block of the block chain system
(information, record and so on) which serve the intention of block chain.
Block – It is considered as a data structure which is used for keeping the set of
transactions that is distributed to all the nodes in network system (SenguptaRuj and Bit,
2020).
Chain – It is determined as the sequence of blocks in a particular order.
Miners – It is determined as the specific nodes that perform the activity related to block
verification procedure before adding anything to the structure of block chain.
Consensus or consensus protocol – It is considered as set of rules as well as arrangements
which help in carry out operations related to the block chain.
These are the main components on which application of block chain architecture through
that it can be ensure that system is working effectively as well as all data are save in secure as
well as safe manner.
2. Security problems and their solution in the block chain security
Block chain is considered as new application model of computer technology such as
point to point transmission, distributed data storage, encryption algorithms and consensus
mechanisms (Specter, Koppel and Weitzner, 2020). It is an essential concept of the Bitcoin as
well as it is essentially a decentralized database. In addition to this, there are several security
issues which are consist with the block chain as well as that is essential to resolve in order to
attain the desire goal and outcome. Below some of the main security issues or problems are
block chain along with their solution are mentioned:-
51 percent attacks – in this transaction will be reversed as well as caused double spends
through gaining majority control over a block chain hashrate through malicious entities.
There are several famous cryptocurrencies related to it such as Verge, Zen Cash,
Ethereum Classic at which victims of 51 percent attacks in year 2018 (Top 5 Blockchain
Security Issues in 2019, 2020). This will leads to loss of $ 20 million due to the block
chain security issues. Along with this, in order to prevent from 51 percent attack there are
several factors need to consider such as using higher hashrate as well as it also include
avoiding of using proof of work (POW) consensus mechanism can be determined to take.
6
has an independent copy of the all block chain ledger).
Transaction – It is related with the smallest building block of the block chain system
(information, record and so on) which serve the intention of block chain.
Block – It is considered as a data structure which is used for keeping the set of
transactions that is distributed to all the nodes in network system (SenguptaRuj and Bit,
2020).
Chain – It is determined as the sequence of blocks in a particular order.
Miners – It is determined as the specific nodes that perform the activity related to block
verification procedure before adding anything to the structure of block chain.
Consensus or consensus protocol – It is considered as set of rules as well as arrangements
which help in carry out operations related to the block chain.
These are the main components on which application of block chain architecture through
that it can be ensure that system is working effectively as well as all data are save in secure as
well as safe manner.
2. Security problems and their solution in the block chain security
Block chain is considered as new application model of computer technology such as
point to point transmission, distributed data storage, encryption algorithms and consensus
mechanisms (Specter, Koppel and Weitzner, 2020). It is an essential concept of the Bitcoin as
well as it is essentially a decentralized database. In addition to this, there are several security
issues which are consist with the block chain as well as that is essential to resolve in order to
attain the desire goal and outcome. Below some of the main security issues or problems are
block chain along with their solution are mentioned:-
51 percent attacks – in this transaction will be reversed as well as caused double spends
through gaining majority control over a block chain hashrate through malicious entities.
There are several famous cryptocurrencies related to it such as Verge, Zen Cash,
Ethereum Classic at which victims of 51 percent attacks in year 2018 (Top 5 Blockchain
Security Issues in 2019, 2020). This will leads to loss of $ 20 million due to the block
chain security issues. Along with this, in order to prevent from 51 percent attack there are
several factors need to consider such as using higher hashrate as well as it also include
avoiding of using proof of work (POW) consensus mechanism can be determined to take.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Exchange hack – In this cryptocurrency exchange are very common as well as popular
among the hackers as it have huge crypto keeping without the sufficient or effective
security protection (Yuen and et.al., 2020). There are many cryptocurrency exchange
level the decentralisation advantages of block chains as it is centralized born. This will
leads to loss of $ 900 million last year because of this block chain security issues. In
addition to this, for preventing from the exchange hack it is essential to store funds safety
through the hardware or paper wallet. It is so because this will apply negligible online
touchpoints in order to protect money away from the despiteful online hackers.
Social engineering – It is available in several form but it mainly obtained from the private
key, cryptocurrency, login information or data and many other direct information. In this
phishing is one of the most communal form of the social engineering (Zaghloul and et.al.,
2020). De-spitefully actors copy someone on which a person trust in messages, social
media and email account. Due to this clock chain security issues there is loss take place
of around $ 3 million in a year. So in order to prevent from the social engineering attacks
it is essential to make sure that a person never send their personal information like login
credentials or any private key to any one. This is so because if a person trust and give
their login id or private key then it may be leads to trap.
These are the main issues which are related to the block chain security and it is essential
for a person as well as company to understand it as well as follow the steps for preventing from
the trap.
CONCLUSION
By analysing above mentioned topics it can be summarised that in computing area system
as well as network security is necessary because that will aid in accomplishing work or project in
proper manner. Moreover it also in ensuring that information or data are safe as well as secure in
specific system. In this system security is related to all facet that leads to accessing data or
information assets as well as network security is determined as broad term that cover multitude
of process, device and technology. This is generally considered as the rules and configurations
which are developed in order to secure accessibility, integrity and confidentiality related to the
computer network by using hardware as well as software. In the management of system and
network security block chain security is considered as main application which are adopted by a
company in order to secure information or data. The architecture of block chain security is
7
among the hackers as it have huge crypto keeping without the sufficient or effective
security protection (Yuen and et.al., 2020). There are many cryptocurrency exchange
level the decentralisation advantages of block chains as it is centralized born. This will
leads to loss of $ 900 million last year because of this block chain security issues. In
addition to this, for preventing from the exchange hack it is essential to store funds safety
through the hardware or paper wallet. It is so because this will apply negligible online
touchpoints in order to protect money away from the despiteful online hackers.
Social engineering – It is available in several form but it mainly obtained from the private
key, cryptocurrency, login information or data and many other direct information. In this
phishing is one of the most communal form of the social engineering (Zaghloul and et.al.,
2020). De-spitefully actors copy someone on which a person trust in messages, social
media and email account. Due to this clock chain security issues there is loss take place
of around $ 3 million in a year. So in order to prevent from the social engineering attacks
it is essential to make sure that a person never send their personal information like login
credentials or any private key to any one. This is so because if a person trust and give
their login id or private key then it may be leads to trap.
These are the main issues which are related to the block chain security and it is essential
for a person as well as company to understand it as well as follow the steps for preventing from
the trap.
CONCLUSION
By analysing above mentioned topics it can be summarised that in computing area system
as well as network security is necessary because that will aid in accomplishing work or project in
proper manner. Moreover it also in ensuring that information or data are safe as well as secure in
specific system. In this system security is related to all facet that leads to accessing data or
information assets as well as network security is determined as broad term that cover multitude
of process, device and technology. This is generally considered as the rules and configurations
which are developed in order to secure accessibility, integrity and confidentiality related to the
computer network by using hardware as well as software. In the management of system and
network security block chain security is considered as main application which are adopted by a
company in order to secure information or data. The architecture of block chain security is
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

divided into three section i.e. centralized, decentralized and distributed ledgers. Moreover, its
application is based on the several components i.e. node, block, transaction, chain, miners and
consensus. In addition to this there are several security issues are related to the block chain
which need to determine by a company as well as it is also essential to develop strategies related
to it in effective manner.
LITERATURE RESEARCH
According to Pan, X. and et. al., (2020), block chain was first determined in 1991. There
were a group of researchers who were looking to create a tool in order to timestamp the
documents which are digitally used. This was necessary so that the documents could not be
changed or backdated for any benefits. There are different core technologies such as
decentralisation, security issues and accountability which are helping in Blockchain system.
When looking into architectural system of Blockchain it is divided into three parts that are
centralised, decentralised and distributed ledgers. A centralised Blockchain security is one which
has private governance and is managed by single group or a company. On the other hand or the
centralise security system does not have any core authority which can dictate the truth of the
participants in this network. It is often seen that in decentralised architectural block chain
security system access to history of transaction is very easy. When looking into third factor that
is distributed leisure it is seen that there are various databases in multiple regions which helps in
determining multiple regions, sites and the participants.
According to Xie, J. and et. al., (2019), Blockchain is an application model for computer
technology which can be distributed data storage, point-to-point transmission, various encrypted
algorithms and so on. It is an important concept of bitcoin and also as initially decentralised
database. The following data blog contains various information about different batches of bitcoin
transactions and also verify the validity of information in order to generate the next upcoming
blocks. There are different of security issues which have been seen in block chains such as the
transaction which are reversed are often causing double spends and also gaining majority control
block chains. There are also a number of exchange hacks due to crypto currency exchanges.
When it comes to social engineering it is often seen that private keys, login information and
more can be hacked by social engineer trackers and my attack the account. When looking
towards software flaws it is often seen that there are a number of software which may lead to
flaws in block chain technology. No order to make sure that these floors can be prevented it is
8
application is based on the several components i.e. node, block, transaction, chain, miners and
consensus. In addition to this there are several security issues are related to the block chain
which need to determine by a company as well as it is also essential to develop strategies related
to it in effective manner.
LITERATURE RESEARCH
According to Pan, X. and et. al., (2020), block chain was first determined in 1991. There
were a group of researchers who were looking to create a tool in order to timestamp the
documents which are digitally used. This was necessary so that the documents could not be
changed or backdated for any benefits. There are different core technologies such as
decentralisation, security issues and accountability which are helping in Blockchain system.
When looking into architectural system of Blockchain it is divided into three parts that are
centralised, decentralised and distributed ledgers. A centralised Blockchain security is one which
has private governance and is managed by single group or a company. On the other hand or the
centralise security system does not have any core authority which can dictate the truth of the
participants in this network. It is often seen that in decentralised architectural block chain
security system access to history of transaction is very easy. When looking into third factor that
is distributed leisure it is seen that there are various databases in multiple regions which helps in
determining multiple regions, sites and the participants.
According to Xie, J. and et. al., (2019), Blockchain is an application model for computer
technology which can be distributed data storage, point-to-point transmission, various encrypted
algorithms and so on. It is an important concept of bitcoin and also as initially decentralised
database. The following data blog contains various information about different batches of bitcoin
transactions and also verify the validity of information in order to generate the next upcoming
blocks. There are different of security issues which have been seen in block chains such as the
transaction which are reversed are often causing double spends and also gaining majority control
block chains. There are also a number of exchange hacks due to crypto currency exchanges.
When it comes to social engineering it is often seen that private keys, login information and
more can be hacked by social engineer trackers and my attack the account. When looking
towards software flaws it is often seen that there are a number of software which may lead to
flaws in block chain technology. No order to make sure that these floors can be prevented it is
8

necessary to check the audits and find any loopholes by third-party which can be used to secure
the Blockchain system. Crypto jacking also leads to a number of different issues in performance
as it increases the use of electricity and opens doors to a number of different unauthorised
computers in the system. There are a number of steps which can be taken to prevent malware
attacks such as frequently checking any mysterious programs and also making sure that regular
security checks are injected in the website.
9
the Blockchain system. Crypto jacking also leads to a number of different issues in performance
as it increases the use of electricity and opens doors to a number of different unauthorised
computers in the system. There are a number of steps which can be taken to prevent malware
attacks such as frequently checking any mysterious programs and also making sure that regular
security checks are injected in the website.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Books and Journals
Bodkhe, U. and et.al., 2020. Blockchain for industry 4.0: a comprehensive review. IEEE
Access. 8. pp.79764-79800.
Khan, F. A., and et.al., 2020. Blockchain technology, improvement suggestions, security
challenges on smart grid and its application in healthcare for sustainable
development. Sustainable Cities and Society. 55. p.102018.
Li, X. and et.al., 2020. A survey on the security of blockchain systems. Future Generation
Computer Systems. 107. pp.841-853.
Mohanty, S.N. and et.al., 2020. An efficient Lightweight integrated Blockchain (ELIB) model
for IoT security and privacy. Future Generation Computer Systems. 102. pp.1027-1037.
Sengupta, J., Ruj, S. and Bit, S.D., 2020. A Comprehensive survey on attacks, security issues and
blockchain solutions for IoT and IIoT. Journal of Network and Computer
Applications. 149. p.102481.
Specter, M. A., Koppel, J. and Weitzner, D., 2020. The Ballot is Busted Before the Blockchain:
A Security Analysis of Voatz, the First Internet Voting Application Used in US Federal
Elections. In 29th {USENIX} Security Symposium ({USENIX} Security 20) (pp. 1535-
1553).
Yuen, T. H. and et.al., 2020, February. RingCT 3.0 for blockchain confidential transaction:
Shorter size and stronger security. In International Conference on Financial
Cryptography and Data Security (pp. 464-483). Springer, Cham.
Zaghloul, E. and et.al., 2020. Bitcoin and blockchain: Security and privacy. IEEE Internet of
Things Journal.
Pan, X. and et. al.,2020. Blockchain technology and enterprise operational capabilities: An
empirical test. International Journal of Information Management, 52, p.101946.
Xie, J. and et. al., 2019. A survey of blockchain technology applied to smart cities: Research
issues and challenges. IEEE Communications Surveys & Tutorials, 21(3), pp.2794-
2830.
Online
Blockchain Architecture Basics: Components, Structure, Benefits & Creation. 2020. [Online].
Available through: <https://mlsdev.com/blog/156-how-to-build-your-own-blockchain-
architecture>.
Top 5 Blockchain Security Issues in 2019. 2020. [Online]. Available through:
<https://lifars.com/2019/12/top-5-blockchain-security-issues-in-2019/>.
10
Books and Journals
Bodkhe, U. and et.al., 2020. Blockchain for industry 4.0: a comprehensive review. IEEE
Access. 8. pp.79764-79800.
Khan, F. A., and et.al., 2020. Blockchain technology, improvement suggestions, security
challenges on smart grid and its application in healthcare for sustainable
development. Sustainable Cities and Society. 55. p.102018.
Li, X. and et.al., 2020. A survey on the security of blockchain systems. Future Generation
Computer Systems. 107. pp.841-853.
Mohanty, S.N. and et.al., 2020. An efficient Lightweight integrated Blockchain (ELIB) model
for IoT security and privacy. Future Generation Computer Systems. 102. pp.1027-1037.
Sengupta, J., Ruj, S. and Bit, S.D., 2020. A Comprehensive survey on attacks, security issues and
blockchain solutions for IoT and IIoT. Journal of Network and Computer
Applications. 149. p.102481.
Specter, M. A., Koppel, J. and Weitzner, D., 2020. The Ballot is Busted Before the Blockchain:
A Security Analysis of Voatz, the First Internet Voting Application Used in US Federal
Elections. In 29th {USENIX} Security Symposium ({USENIX} Security 20) (pp. 1535-
1553).
Yuen, T. H. and et.al., 2020, February. RingCT 3.0 for blockchain confidential transaction:
Shorter size and stronger security. In International Conference on Financial
Cryptography and Data Security (pp. 464-483). Springer, Cham.
Zaghloul, E. and et.al., 2020. Bitcoin and blockchain: Security and privacy. IEEE Internet of
Things Journal.
Pan, X. and et. al.,2020. Blockchain technology and enterprise operational capabilities: An
empirical test. International Journal of Information Management, 52, p.101946.
Xie, J. and et. al., 2019. A survey of blockchain technology applied to smart cities: Research
issues and challenges. IEEE Communications Surveys & Tutorials, 21(3), pp.2794-
2830.
Online
Blockchain Architecture Basics: Components, Structure, Benefits & Creation. 2020. [Online].
Available through: <https://mlsdev.com/blog/156-how-to-build-your-own-blockchain-
architecture>.
Top 5 Blockchain Security Issues in 2019. 2020. [Online]. Available through:
<https://lifars.com/2019/12/top-5-blockchain-security-issues-in-2019/>.
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





