Blockchain Security Analysis: A Comprehensive Research Proposal
VerifiedAdded on 2023/02/01
|27
|6372
|48
Project
AI Summary
This research proposal undertakes a thorough analysis of blockchain security, addressing the growing need for robust data protection in the era of big data. The study begins with an executive summary that outlines the project's objectives, methodology, and anticipated outcomes. The introduction emphasizes the importance of blockchain technology as a secure solution, despite its inherent vulnerabilities. The literature review provides a comprehensive overview of existing research, highlighting blockchain vulnerabilities, real-world attack examples, and the economic impact of security breaches. The research questions explore the safety of blockchain technology, guiding the methodology section, which outlines theoretical frameworks and methods. The experimental setup details the tools and techniques for vulnerability analysis, focusing on smart contract technology. The proposal also includes a project planning section that outlines activities, resources, and timelines. The study explores various attack vectors such as selfish mining, DAO attacks, BGP hijacking, and private key security, along with criminal activities like ransomware and money laundering. The proposal concludes with a discussion of the findings and their relevance to enhancing blockchain security.

1
BLOCK CHAIN SECURITY ANALYSIS
Name
Institution Affiliation
Date
BLOCK CHAIN SECURITY ANALYSIS
Name
Institution Affiliation
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Block Chain Security Analysis
Contents
Executive Summary............................................................................................................................................... 3
Introduction.............................................................................................................................................................. 3
Literature Review................................................................................................................................................... 4
Research Question.................................................................................................................................................. 9
Methodology/Theoretical Content.................................................................................................................. 9
Experimental Setup............................................................................................................................................. 11
Results, Outcomes, and Relevance................................................................................................................ 13
Project Planning And Gantt Chart................................................................................................................. 15
Conclusion............................................................................................................................................................... 20
References............................................................................................................................................................... 22
Block Chain Security Analysis
Contents
Executive Summary............................................................................................................................................... 3
Introduction.............................................................................................................................................................. 3
Literature Review................................................................................................................................................... 4
Research Question.................................................................................................................................................. 9
Methodology/Theoretical Content.................................................................................................................. 9
Experimental Setup............................................................................................................................................. 11
Results, Outcomes, and Relevance................................................................................................................ 13
Project Planning And Gantt Chart................................................................................................................. 15
Conclusion............................................................................................................................................................... 20
References............................................................................................................................................................... 22

3
Executive Summary
This proposal research undertakes steps to find the bottom line of the research’s
objective. For a better understanding of the topic, the research proposal stipulates the literature
that has been conducted by other scholars. The literature review cuts a broad area of blockchain
vulnerabilities. Apart from identifying the vulnerable areas of the blockchain, the literature
review demonstrates the real examples of attacks that have been initiated on the blockchain
technologies and in particular, the smart card technology. After that, the research questions are
then clearly expounded to present a clear direction for the research. The research questions
provided specific areas to do examinations and tests. The main research question in the proposal
is the inquiry of whether the blockchain technology is safe enough. After that, the methodology
section demonstrates the different theoretical frameworks and the methods that will be used to
carry out the research. The experimental setup acutely demonstrated the tools that will be used in
carrying out the research. The main tools identified are the breaking down of the vulnerability
areas using specific bugs that the smart card blockchain technology is vulnerable. Thereafter, the
proposal demonstrates the projected outcomes of the research data. The identification of the data
that will be used in the research paves the way for the kind out the outcome that is expected. The
project planning section clearly shows the activities that will be carried out, the resources that
will be needed and the time frame for carrying out the research activities.
Introduction
The world’s rate of data collection is in a rapid increase. This defines the era of big data
with social media applications collecting the majority of data. Owing to that, there is a huge need
for increased data security. The blockchain technology is the newest technology that is projected
to take over. Compared to its counterparts, the blockchain technology serves as the safest
Executive Summary
This proposal research undertakes steps to find the bottom line of the research’s
objective. For a better understanding of the topic, the research proposal stipulates the literature
that has been conducted by other scholars. The literature review cuts a broad area of blockchain
vulnerabilities. Apart from identifying the vulnerable areas of the blockchain, the literature
review demonstrates the real examples of attacks that have been initiated on the blockchain
technologies and in particular, the smart card technology. After that, the research questions are
then clearly expounded to present a clear direction for the research. The research questions
provided specific areas to do examinations and tests. The main research question in the proposal
is the inquiry of whether the blockchain technology is safe enough. After that, the methodology
section demonstrates the different theoretical frameworks and the methods that will be used to
carry out the research. The experimental setup acutely demonstrated the tools that will be used in
carrying out the research. The main tools identified are the breaking down of the vulnerability
areas using specific bugs that the smart card blockchain technology is vulnerable. Thereafter, the
proposal demonstrates the projected outcomes of the research data. The identification of the data
that will be used in the research paves the way for the kind out the outcome that is expected. The
project planning section clearly shows the activities that will be carried out, the resources that
will be needed and the time frame for carrying out the research activities.
Introduction
The world’s rate of data collection is in a rapid increase. This defines the era of big data
with social media applications collecting the majority of data. Owing to that, there is a huge need
for increased data security. The blockchain technology is the newest technology that is projected
to take over. Compared to its counterparts, the blockchain technology serves as the safest
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
because of its decentralized nature. This report stands on the position that the blockchain
technology is a safe haven yet because of the vulnerabilities it has. The detailed areas of
vulnerability will be useful in improving the security of Bitcoin technology.
Literature Review
Block Chain Security Analysis
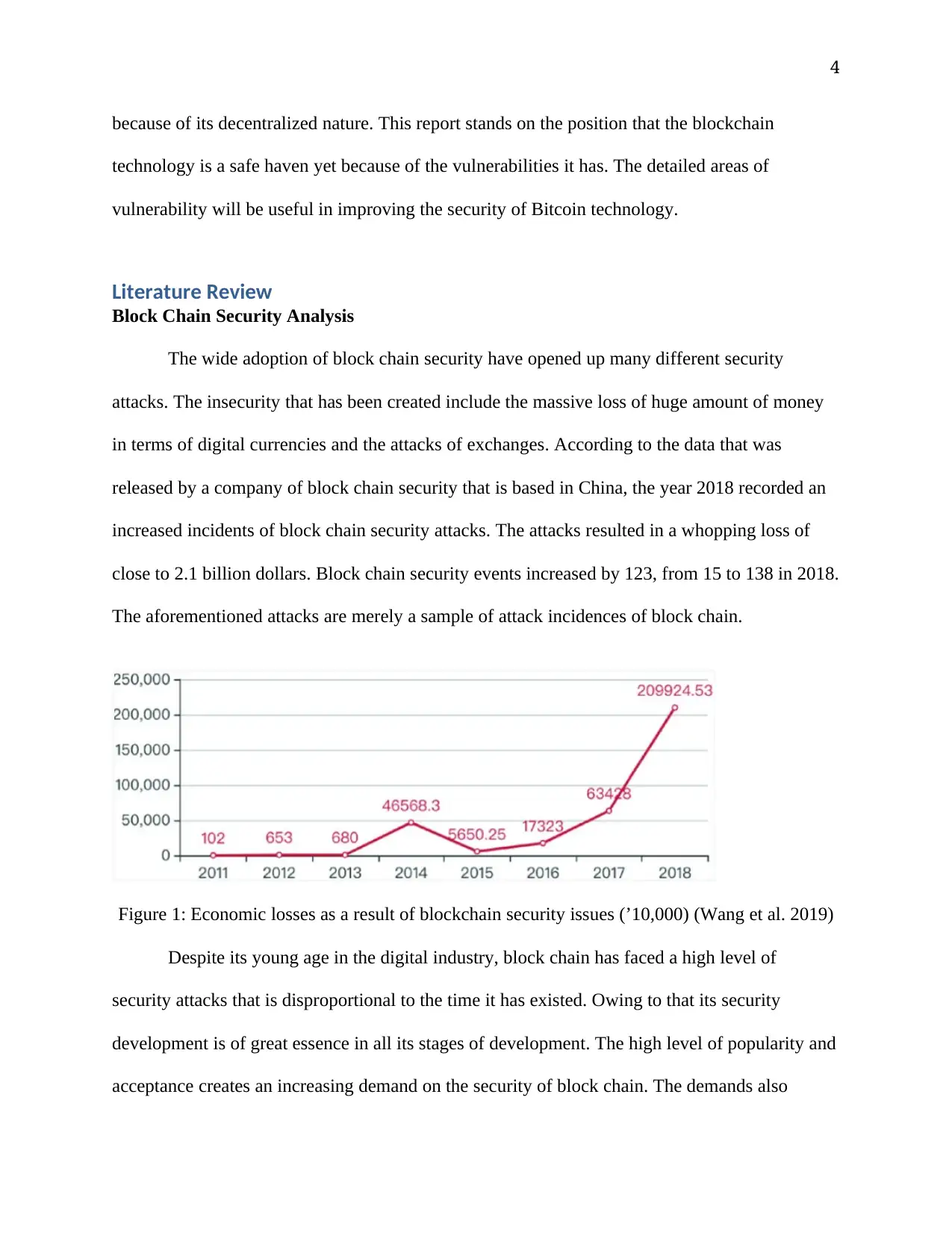
The wide adoption of block chain security have opened up many different security
attacks. The insecurity that has been created include the massive loss of huge amount of money
in terms of digital currencies and the attacks of exchanges. According to the data that was
released by a company of block chain security that is based in China, the year 2018 recorded an
increased incidents of block chain security attacks. The attacks resulted in a whopping loss of
close to 2.1 billion dollars. Block chain security events increased by 123, from 15 to 138 in 2018.
The aforementioned attacks are merely a sample of attack incidences of block chain.
Figure 1: Economic losses as a result of blockchain security issues (’10,000) (Wang et al. 2019)
Despite its young age in the digital industry, block chain has faced a high level of
security attacks that is disproportional to the time it has existed. Owing to that its security
development is of great essence in all its stages of development. The high level of popularity and
acceptance creates an increasing demand on the security of block chain. The demands also
because of its decentralized nature. This report stands on the position that the blockchain
technology is a safe haven yet because of the vulnerabilities it has. The detailed areas of
vulnerability will be useful in improving the security of Bitcoin technology.
Literature Review
Block Chain Security Analysis
The wide adoption of block chain security have opened up many different security
attacks. The insecurity that has been created include the massive loss of huge amount of money
in terms of digital currencies and the attacks of exchanges. According to the data that was
released by a company of block chain security that is based in China, the year 2018 recorded an
increased incidents of block chain security attacks. The attacks resulted in a whopping loss of
close to 2.1 billion dollars. Block chain security events increased by 123, from 15 to 138 in 2018.
The aforementioned attacks are merely a sample of attack incidences of block chain.
Figure 1: Economic losses as a result of blockchain security issues (’10,000) (Wang et al. 2019)
Despite its young age in the digital industry, block chain has faced a high level of
security attacks that is disproportional to the time it has existed. Owing to that its security
development is of great essence in all its stages of development. The high level of popularity and
acceptance creates an increasing demand on the security of block chain. The demands also
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
resonate around storage and privacy protection, transmission and application of data, security
solutions, authentication mechanisms, privacy protection, data protection and regulation of
information.
Individual Blockchain Layers’ Security Analysis
The block chain structure is divided into the following layers: smart contract, incentive,
application, data layers and consensus.
Application Layer
This layer deals with the centralized nodes’ security. That encompasses the exchanges
that involves the digital currency transactions and the management of large amounts of funds.
The point of weakness that normally opens up chances of attacks include the fact that the nodes
are present in many failure points of the entire system of block chain, alongside the high
vulnerability of attacks with a relatively low cost (Eyal et al. 2016). Therefore, the layer is
normally a potential target for most attackers.
Incentive layer
The role of this layer is the provision of some incentives aimed at encouraging nodes to
participate in the process of security verification of the block chain technology. The block
chain’s safety is a participation factor in many nodes. For instance, the security of bitcoin block
chain largely depends on great harsh power that is created by numerous nodes participation,
involved in various security proofs and checks (Khan & Salah 2018). That renders an attacker to
offer a large totaling volume.
Consensus Layer
resonate around storage and privacy protection, transmission and application of data, security
solutions, authentication mechanisms, privacy protection, data protection and regulation of
information.
Individual Blockchain Layers’ Security Analysis
The block chain structure is divided into the following layers: smart contract, incentive,
application, data layers and consensus.
Application Layer
This layer deals with the centralized nodes’ security. That encompasses the exchanges
that involves the digital currency transactions and the management of large amounts of funds.
The point of weakness that normally opens up chances of attacks include the fact that the nodes
are present in many failure points of the entire system of block chain, alongside the high
vulnerability of attacks with a relatively low cost (Eyal et al. 2016). Therefore, the layer is
normally a potential target for most attackers.
Incentive layer
The role of this layer is the provision of some incentives aimed at encouraging nodes to
participate in the process of security verification of the block chain technology. The block
chain’s safety is a participation factor in many nodes. For instance, the security of bitcoin block
chain largely depends on great harsh power that is created by numerous nodes participation,
involved in various security proofs and checks (Khan & Salah 2018). That renders an attacker to
offer a large totaling volume.
Consensus Layer

6
Blockchain utilizes the following consensus mechanisms: Proof of Stake, Proof of Work
and Delegated Proof of Stake. The likely attacks on this platforms are; Bribe Attack, Long-Rang
Attack, Precompiling Attack, Sybil Attack and Accumulation Attack.
Data Layer
Signature & encryption system and block data are the main data layer elements.
Bloc data: The bloc data is normally targeted with malicious information like virus signatures
and subjects that are political and sensitive. The feature of block chain to prevent the deleting of
information after posting exposes block chain to many hitches. A group of researchers from
RTWH Aachen University and Goethe University Frankfurt pointed out that 59 files of all the
1600 documents were associated with supposed politically sensitive content, violations of
privacy and illegal pictures of children (Lin & Liao 2017).
Cases of Major Attacks
The Attack of Selfish Mining
This kind of attack is normally conducted by attackers for purposes of getting rewards
that are unmerited or putting the honest miners’ power of computing under waste. In that case,
the attacker attempt to forking a private chain while privately holding the discovered blocks.
Thereafter, self-centered miners would attempt to mine on the chain that is private while trying
on the maintenance of longer private branches than the public branch because of the fact that
they hold more discovered blocks that are new (Iansiti and Lakhani, 2017). In the meantime,
honest miners will continue mining on the chain that is public. Just when the public branch nears
the length of the private branch, new blocks that are mined by attackers are revealed. In the
process, miners who are honest will be forced to join the selfish miners’ branch as the selfish
Blockchain utilizes the following consensus mechanisms: Proof of Stake, Proof of Work
and Delegated Proof of Stake. The likely attacks on this platforms are; Bribe Attack, Long-Rang
Attack, Precompiling Attack, Sybil Attack and Accumulation Attack.
Data Layer
Signature & encryption system and block data are the main data layer elements.
Bloc data: The bloc data is normally targeted with malicious information like virus signatures
and subjects that are political and sensitive. The feature of block chain to prevent the deleting of
information after posting exposes block chain to many hitches. A group of researchers from
RTWH Aachen University and Goethe University Frankfurt pointed out that 59 files of all the
1600 documents were associated with supposed politically sensitive content, violations of
privacy and illegal pictures of children (Lin & Liao 2017).
Cases of Major Attacks
The Attack of Selfish Mining
This kind of attack is normally conducted by attackers for purposes of getting rewards
that are unmerited or putting the honest miners’ power of computing under waste. In that case,
the attacker attempt to forking a private chain while privately holding the discovered blocks.
Thereafter, self-centered miners would attempt to mine on the chain that is private while trying
on the maintenance of longer private branches than the public branch because of the fact that
they hold more discovered blocks that are new (Iansiti and Lakhani, 2017). In the meantime,
honest miners will continue mining on the chain that is public. Just when the public branch nears
the length of the private branch, new blocks that are mined by attackers are revealed. In the
process, miners who are honest will be forced to join the selfish miners’ branch as the selfish
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
miners gain a competitive advantage. In essence, the attack undermines blockchain’s nature of a
decentralized system.
DAO Attack
DAO refers to a smart contract that was deployed in Ethereum on the 28th of May 2016.
The smart contract implacement a platform that is funded by a crowd. The contract was only
attacked after 20 days of deployment. DAO has already raised a total of 150 million US$ before
the attack, setting a record of being the biggest crowdfund, stealing approximately 60 million
US$. In that case, the reentry vulnerability was exploited by the attacker. That was done by first
publishing malicious smart contracts with withdraw () call function to DAO in the callback
function. Thus, the malicious smart contract will again, be invoked. All the DAO’ Ether is there
left exposed to the attacker’s theft.
BGP Hijacking Attack
Border Gateway Protocol (BGP) refers to de-facto routing protocol the manner of IP
packets destination forwarding. The interception of blockchain network traffic occurs through
the leveraging or manipulation of the Border Gateway Protocol. The Border Gateway Protocol
normally requires the network operator’s control. That too can potentially be exploited for
purposes of delaying network messages. The mining power distribution affects the number of
vulnerable internet prefixes that are successful. Some Bitcoin mining pools have high
centralization and thus will have a huge effect when attacked by BGP hijackers. The attack may
occur through the delay of block propagation speed (Shafagh et al 2017). Hijackers intercept the
connections of Bitcoin miners to the pool server of the mining pool. Therefore, it was possible to
undertake the theft of cryptocurrency (Mangia et al 2019). The attack that took place collected
approximately 83,000 US$ worth of cryptocurrency over a period of two months. The network
miners gain a competitive advantage. In essence, the attack undermines blockchain’s nature of a
decentralized system.
DAO Attack
DAO refers to a smart contract that was deployed in Ethereum on the 28th of May 2016.
The smart contract implacement a platform that is funded by a crowd. The contract was only
attacked after 20 days of deployment. DAO has already raised a total of 150 million US$ before
the attack, setting a record of being the biggest crowdfund, stealing approximately 60 million
US$. In that case, the reentry vulnerability was exploited by the attacker. That was done by first
publishing malicious smart contracts with withdraw () call function to DAO in the callback
function. Thus, the malicious smart contract will again, be invoked. All the DAO’ Ether is there
left exposed to the attacker’s theft.
BGP Hijacking Attack
Border Gateway Protocol (BGP) refers to de-facto routing protocol the manner of IP
packets destination forwarding. The interception of blockchain network traffic occurs through
the leveraging or manipulation of the Border Gateway Protocol. The Border Gateway Protocol
normally requires the network operator’s control. That too can potentially be exploited for
purposes of delaying network messages. The mining power distribution affects the number of
vulnerable internet prefixes that are successful. Some Bitcoin mining pools have high
centralization and thus will have a huge effect when attacked by BGP hijackers. The attack may
occur through the delay of block propagation speed (Shafagh et al 2017). Hijackers intercept the
connections of Bitcoin miners to the pool server of the mining pool. Therefore, it was possible to
undertake the theft of cryptocurrency (Mangia et al 2019). The attack that took place collected
approximately 83,000 US$ worth of cryptocurrency over a period of two months. The network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
operators only have the monitoring systems because of the narrow deployment of BGP security
extensions.
Private Key Security
A private key of a user is the unique identity and security credential that is normally
maintained and generated by a user as opposed to a third party agency. For instance, users must
import a private key to create a cold storage wallet in the storage in Bitcoin. Researchers have
also made a discovery on the vulnerability of the Elliptic Curve Digital Signature Algorithm
(ECDSA) scheme. This vulnerability enables an attacker to recover the private key of a user
because of its lack to generate randomness in the event of the signature process. The unfortunate
situation, unfortunately, is that once the private key is stolen, it cannot be recovered and the
account of the victim will face a huge risk of tampering with by criminals (Biswas and
Muthukkumarasamy, 2016). It will also be hard if not impossible to track down the behaviors of
criminals considering the fact that blockchain is independent of any centralized party.
Criminal Activity
There is a possibility of users of Bitcoin having several addresses and the addresses
having no true reflection or relationship with the real-life identity. That has opened up chances
for criminal activities through the use of Bitcoin technology (Dorri et al., 2017). Users of Bitcoin
can sell or buy products through the trading platforms that are the third party. In that case, it will
be difficult to track down the behaviors of users or subject them to legal sanctions because of the
anonymity of the process. The ability of attackers to hide their details and identity increases the
risk of attacks. There are a number of criminal activities with Bitcoins and they are discussed
below;
i) Ransomware
operators only have the monitoring systems because of the narrow deployment of BGP security
extensions.
Private Key Security
A private key of a user is the unique identity and security credential that is normally
maintained and generated by a user as opposed to a third party agency. For instance, users must
import a private key to create a cold storage wallet in the storage in Bitcoin. Researchers have
also made a discovery on the vulnerability of the Elliptic Curve Digital Signature Algorithm
(ECDSA) scheme. This vulnerability enables an attacker to recover the private key of a user
because of its lack to generate randomness in the event of the signature process. The unfortunate
situation, unfortunately, is that once the private key is stolen, it cannot be recovered and the
account of the victim will face a huge risk of tampering with by criminals (Biswas and
Muthukkumarasamy, 2016). It will also be hard if not impossible to track down the behaviors of
criminals considering the fact that blockchain is independent of any centralized party.
Criminal Activity
There is a possibility of users of Bitcoin having several addresses and the addresses
having no true reflection or relationship with the real-life identity. That has opened up chances
for criminal activities through the use of Bitcoin technology (Dorri et al., 2017). Users of Bitcoin
can sell or buy products through the trading platforms that are the third party. In that case, it will
be difficult to track down the behaviors of users or subject them to legal sanctions because of the
anonymity of the process. The ability of attackers to hide their details and identity increases the
risk of attacks. There are a number of criminal activities with Bitcoins and they are discussed
below;
i) Ransomware

9
In this activity, criminals normally use Bitcoin as a trading currency and to extort money
using ransomware. For example, there was a rapid spread of ransomware called CTB-Locker
CTB-Locker worldwide through the disguise of mail attachments. When users tried clicking on
the attachments, the ransomware would begin running in the system’s background, encrypting
close to 114 types of every file. The attackers would then blackmail the users to pay them certain
amounts of Bitcoin or else they would not restore the encrypted files. A similar attack happened
again in 2017 where ransomware called WannaCry caused an infection to approximately
230,000 victims in two days, affecting 150 countries. The WannaCry ransomware exploited a
Windows system vulnerability and spread and encrypted files of victims in exchange of Bitcoin
ransom.
Underground Market
Illegal and underground markets normally use Bitcoin as the main currency. For instance,
the Silk Road is a well-known marketplace operating as a Tor hidden service as it uses Bitcoin as
its main currency (Kiayias, and Panagiotakos, 2015). Most of the items being sold in the
marketplace of Silk Road are illegal. They include drugs, weed, prescription, books, benzos,
cocaine, cannabis, blotter, and pills. Therefore, Bitcoin makes underground market transactions
more convenient, causing increasing harm to social security.
Money Laundering
The network virtual payment and anonymity features of Bitcoin has made it popular in
comparison with other currencies. Bitcoin technology also has the advantage of bearing the
lowest risk of money laundering. However, Dark Wallet is a Bitcoin application capable of
making the transactions of Bitcoin entirely private and stealth. In that case, Dark Wallet has the
In this activity, criminals normally use Bitcoin as a trading currency and to extort money
using ransomware. For example, there was a rapid spread of ransomware called CTB-Locker
CTB-Locker worldwide through the disguise of mail attachments. When users tried clicking on
the attachments, the ransomware would begin running in the system’s background, encrypting
close to 114 types of every file. The attackers would then blackmail the users to pay them certain
amounts of Bitcoin or else they would not restore the encrypted files. A similar attack happened
again in 2017 where ransomware called WannaCry caused an infection to approximately
230,000 victims in two days, affecting 150 countries. The WannaCry ransomware exploited a
Windows system vulnerability and spread and encrypted files of victims in exchange of Bitcoin
ransom.
Underground Market
Illegal and underground markets normally use Bitcoin as the main currency. For instance,
the Silk Road is a well-known marketplace operating as a Tor hidden service as it uses Bitcoin as
its main currency (Kiayias, and Panagiotakos, 2015). Most of the items being sold in the
marketplace of Silk Road are illegal. They include drugs, weed, prescription, books, benzos,
cocaine, cannabis, blotter, and pills. Therefore, Bitcoin makes underground market transactions
more convenient, causing increasing harm to social security.
Money Laundering
The network virtual payment and anonymity features of Bitcoin has made it popular in
comparison with other currencies. Bitcoin technology also has the advantage of bearing the
lowest risk of money laundering. However, Dark Wallet is a Bitcoin application capable of
making the transactions of Bitcoin entirely private and stealth. In that case, Dark Wallet has the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
ability to encrypt transaction information while mixing the valid coins of users with chaff coins.
That makes the practice of money laundering easier.
Double Spending
Double Spending is basically a situation where a consumer utilizes cryptocurrency for
transactions, multiple times. For example, race attacks could be utilized by attackers for purposes
of double spending. This kind of attack is normally simple to use in cases of blockchains based
on PoW. That is possible because an attacker utilizes or exploits the intermediate period between
two initiations of transactions to launch an attack quickly. Before the invalidation mining of the
second transaction, the attacker would have already gotten the output of the first transaction.
That results in a double spending situation.
Transaction Privacy Leakage
Blockchain systems normally take measures and responsibilities of protecting the privacy
of users during transactions transactions. That is because of the ability to trace the behavior of
users in the blockchain. Zeash and Bitcoin normally use accounts that are one time for storing
the cryptocurrency received. Every transaction needs the assigning of private keys. That will
confuse the attacker from understanding whether the same user receives the cryptocurrency in
different transactions. Users in Monero normally include chaff coins which are also called
mixins during a transaction initiation to confuse attackers from inferring the actual coins linkage
to the transaction spend.
Research Question
i) How safe is the Block Chain technology?
ii) What are the specific areas of blockchain technology?
iii) What are some of the vulnerable areas of smart card blockchain technology?
ability to encrypt transaction information while mixing the valid coins of users with chaff coins.
That makes the practice of money laundering easier.
Double Spending
Double Spending is basically a situation where a consumer utilizes cryptocurrency for
transactions, multiple times. For example, race attacks could be utilized by attackers for purposes
of double spending. This kind of attack is normally simple to use in cases of blockchains based
on PoW. That is possible because an attacker utilizes or exploits the intermediate period between
two initiations of transactions to launch an attack quickly. Before the invalidation mining of the
second transaction, the attacker would have already gotten the output of the first transaction.
That results in a double spending situation.
Transaction Privacy Leakage
Blockchain systems normally take measures and responsibilities of protecting the privacy
of users during transactions transactions. That is because of the ability to trace the behavior of
users in the blockchain. Zeash and Bitcoin normally use accounts that are one time for storing
the cryptocurrency received. Every transaction needs the assigning of private keys. That will
confuse the attacker from understanding whether the same user receives the cryptocurrency in
different transactions. Users in Monero normally include chaff coins which are also called
mixins during a transaction initiation to confuse attackers from inferring the actual coins linkage
to the transaction spend.
Research Question
i) How safe is the Block Chain technology?
ii) What are the specific areas of blockchain technology?
iii) What are some of the vulnerable areas of smart card blockchain technology?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
The questions above boil down to demonstrating the fact that that the blockchain technology is
not as safe as purported. Discovering the specific area of blockchain technology vulnerable areas
will provide a chance for making the evidential argument of the fact that the blockchain
technology is insecure. The first question of the problem statement provides a wide direction for
the research proposal. The second research question narrows down to the specific areas of
blockchain vulnerabilities. That will open up the research proposal to using the case of the smart
card technology in the identification of the specific areas of blockchain vulnerabilities. The
research questions will thus be helpful to deal with the loopholes through the provision of
necessary intervention mechanisms.
Methodology/Theoretical Content
The Blockchain technology has had its application in many fields namely; economics,
medicine, software engineering internet of things among others. The Turing-complete
programming languages introduction has made it possible for users to develop smart contracts.
The contracts in that case, that runs on blockchain makes a mark on the beginning of the 2.0 era
blockchain. Ethereum is one of the most used blockchains that support smart contracts. The
technology already has 317,506 smart contracts and over 75,000 transactions that happen daily.
The massive and wide use of smart contracts has opened up opportunities for attacks considering
its huge financial handling (Huh, Cho and Kim, 2017). June 2016 suffered a fatal attack with
criminals attacking the DAO smart contact through the exploitation of the vulnerability of
recursive call. Through that, the attackers were successful to steal about 60 million$.
Hypothesis for Testing
Analysis of Block Chain security vulnerabilities
The questions above boil down to demonstrating the fact that that the blockchain technology is
not as safe as purported. Discovering the specific area of blockchain technology vulnerable areas
will provide a chance for making the evidential argument of the fact that the blockchain
technology is insecure. The first question of the problem statement provides a wide direction for
the research proposal. The second research question narrows down to the specific areas of
blockchain vulnerabilities. That will open up the research proposal to using the case of the smart
card technology in the identification of the specific areas of blockchain vulnerabilities. The
research questions will thus be helpful to deal with the loopholes through the provision of
necessary intervention mechanisms.
Methodology/Theoretical Content
The Blockchain technology has had its application in many fields namely; economics,
medicine, software engineering internet of things among others. The Turing-complete
programming languages introduction has made it possible for users to develop smart contracts.
The contracts in that case, that runs on blockchain makes a mark on the beginning of the 2.0 era
blockchain. Ethereum is one of the most used blockchains that support smart contracts. The
technology already has 317,506 smart contracts and over 75,000 transactions that happen daily.
The massive and wide use of smart contracts has opened up opportunities for attacks considering
its huge financial handling (Huh, Cho and Kim, 2017). June 2016 suffered a fatal attack with
criminals attacking the DAO smart contact through the exploitation of the vulnerability of
recursive call. Through that, the attackers were successful to steal about 60 million$.
Hypothesis for Testing
Analysis of Block Chain security vulnerabilities

12
The blockchain technology has been deemed to be the most secure technology because of
its decentralized nature. This research proposal aims at discrediting this argument, to some extent
by undertaking an analysis of the loopholes existing in the Bitcoin technology. This proposal
identifies the areas of vulnerability that will be tested to provide the state of Bitcoin security. The
different theoretical approaches that will be used in the proposal will include four areas of bugs
used for investigating the vulnerabilities of the blockchain technology. The steps to be
undertaken in the project will involve the identification of smart contract companies with active
users and customers. Different smart contract companies will be used to get a wider scope of
results. In that case, sample smart contract users will be used to launch test attacks using the
vulnerability areas identified (Koirala, Zhu & Neopane, 2016). The vulnerability areas identified
include; transaction-ordering dependence, timestamp dependence, mishandling exceptions, and
reentrancy vulnerability. The tests are meant to practically and evidently demonstrate the
vulnerabilities of Bitcoin technologies (Thapa, Dahlhaug & Thapa, 2015). Other theoretical
examples will be used to back up the experiments that have been carried. In that case, the
research will try to find examples of major attacks that happened in recent times. The need to
find cases of theft using the vulnerabilities in blockchain will be used in the identification of
weak areas and corrective measures being undertaken (Rajkarnikar, Neopane & Thapa, 2015).
The successful cases of stealing money from users of smart card and personal credentials of
smart contracts will be documented. The documented results will show some of the resources
that were compromised and how they were compromised. To secure the companies’ operations,
the identified loopholes will be corrected first before they are made public (Iansiti and Lakhani,
2017). If the vulnerabilities of the companies are made public, attackers could still take
advantage to launch attacks (Crosby et al., 2016). Therefore, the research specialists will try as
The blockchain technology has been deemed to be the most secure technology because of
its decentralized nature. This research proposal aims at discrediting this argument, to some extent
by undertaking an analysis of the loopholes existing in the Bitcoin technology. This proposal
identifies the areas of vulnerability that will be tested to provide the state of Bitcoin security. The
different theoretical approaches that will be used in the proposal will include four areas of bugs
used for investigating the vulnerabilities of the blockchain technology. The steps to be
undertaken in the project will involve the identification of smart contract companies with active
users and customers. Different smart contract companies will be used to get a wider scope of
results. In that case, sample smart contract users will be used to launch test attacks using the
vulnerability areas identified (Koirala, Zhu & Neopane, 2016). The vulnerability areas identified
include; transaction-ordering dependence, timestamp dependence, mishandling exceptions, and
reentrancy vulnerability. The tests are meant to practically and evidently demonstrate the
vulnerabilities of Bitcoin technologies (Thapa, Dahlhaug & Thapa, 2015). Other theoretical
examples will be used to back up the experiments that have been carried. In that case, the
research will try to find examples of major attacks that happened in recent times. The need to
find cases of theft using the vulnerabilities in blockchain will be used in the identification of
weak areas and corrective measures being undertaken (Rajkarnikar, Neopane & Thapa, 2015).
The successful cases of stealing money from users of smart card and personal credentials of
smart contracts will be documented. The documented results will show some of the resources
that were compromised and how they were compromised. To secure the companies’ operations,
the identified loopholes will be corrected first before they are made public (Iansiti and Lakhani,
2017). If the vulnerabilities of the companies are made public, attackers could still take
advantage to launch attacks (Crosby et al., 2016). Therefore, the research specialists will try as
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





