Survey of Blockchain Technology and Smart Contract Implementations
VerifiedAdded on 2021/04/24
|22
|6926
|37
Report
AI Summary
This report provides a comprehensive survey of blockchain technology and its implementations, focusing on its application in business organizations and the utilization of encrypting transactional processes. The paper delves into the digital technology of blockchain systems as they are applied to smart contracts, highlighting the importance of transparency and trust among different nodes. It explores the evolution from public to private blockchains to address privacy concerns, along with software protocols like "Zero Knowledge Proof" and Zcash. The report analyzes the operational processing of transactions, including issues related to international payments and information leakage. It also examines the integration of cultural, social, and economic factors to evaluate risks and the use of blockchain technology in various banking sectors for secure transactions. The report highlights the advantages of blockchain technology, including its use in supply chain management, product quality analysis, and batch processing. Finally, the report provides a detailed description of the working of blockchain technology, covering both public and private blockchains, and methods used for transaction processing. It examines the role of digital signatures and the challenges associated with ensuring the chronological linking of blocks.

Running head:BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
Blockchain technology and implementations
Name of the student:
Name of the university:
Author Note
Blockchain technology and implementations
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
Survey of existing blockchain technology and implementations
1. Abstract
Blockchain technology is an invention that is used primarily for most economic
transactions, applications and recording economic transactions at a required location. This paper
is based on a comprehensive survey of the implementation of the improved technology and the
utilization of encrypting transactional processes in business organizations. Also, this paper
provides details about the digital technology of blockchain systems as they are applied to smart
contracts. Transparency of information involved in different blockchain transactions is usually
based on the trust among different nodes as anyone with computer and internet connection can
access such information(Adams, 2016). However, to avoid leakage and misuse of information
arising out of lack of trust, private blockchains have come into existence, where the authorisation
to access the relevant information is restricted.
However, privacy issues still persist and, in this direction, different software protocols
such as “Zero Knowledge Proof”, Zcash have been deployed to counter such challenges. This
paper provides detailed description of these protocols in blockchain along with the privacy and
confidentiality issues faced by the concerned parties. The survey will allow the study of some
research papers in forming an inference on the operational processing of the transactions. The
slackness in the operation is dependent on the use of blockchain technology. Blockchain
technology has been used significantly in the cryptographies of Bitcoins. However, this
technology has been facing issues of international payments and information leakage.
This paper survey will highlight some of these issues and propose the integration of an
effective operational deployment. The use of successive factors includes cultural and social
aspects. Examples of these are power dynamics, privacy concerns and information flow. These
are done to make investigation on different risks. It also involves economic factors like
confronting with non-physical currencies. Moreover, this includes various levels of ceaselessness
and corporation that take place among technologists, regulators, and market participants.
Utilization of these successive factors in the integration will be based on the analysis of various
factors of supportive and effective evaluation process. Various banking sectors have been using
blockchain technology for safe transaction.
Keywords: Blockchain, Language Industry, Smart Contract,
Survey of existing blockchain technology and implementations
1. Abstract
Blockchain technology is an invention that is used primarily for most economic
transactions, applications and recording economic transactions at a required location. This paper
is based on a comprehensive survey of the implementation of the improved technology and the
utilization of encrypting transactional processes in business organizations. Also, this paper
provides details about the digital technology of blockchain systems as they are applied to smart
contracts. Transparency of information involved in different blockchain transactions is usually
based on the trust among different nodes as anyone with computer and internet connection can
access such information(Adams, 2016). However, to avoid leakage and misuse of information
arising out of lack of trust, private blockchains have come into existence, where the authorisation
to access the relevant information is restricted.
However, privacy issues still persist and, in this direction, different software protocols
such as “Zero Knowledge Proof”, Zcash have been deployed to counter such challenges. This
paper provides detailed description of these protocols in blockchain along with the privacy and
confidentiality issues faced by the concerned parties. The survey will allow the study of some
research papers in forming an inference on the operational processing of the transactions. The
slackness in the operation is dependent on the use of blockchain technology. Blockchain
technology has been used significantly in the cryptographies of Bitcoins. However, this
technology has been facing issues of international payments and information leakage.
This paper survey will highlight some of these issues and propose the integration of an
effective operational deployment. The use of successive factors includes cultural and social
aspects. Examples of these are power dynamics, privacy concerns and information flow. These
are done to make investigation on different risks. It also involves economic factors like
confronting with non-physical currencies. Moreover, this includes various levels of ceaselessness
and corporation that take place among technologists, regulators, and market participants.
Utilization of these successive factors in the integration will be based on the analysis of various
factors of supportive and effective evaluation process. Various banking sectors have been using
blockchain technology for safe transaction.
Keywords: Blockchain, Language Industry, Smart Contract,

BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
2.0 Introduction of Blockchain technology and Smart contracts
While blockchain is a digital technology that combines cryptographic data management,
incentive mechanisms and networking for supporting the recording execution and checking of
transactions between the concerned parties, a blockchain ledger comprises of lists or blocks
pertaining to the relevant transaction (Peters & Panayi, 2016). Originally, this technology
emerged as a support to various kinds of digital currency. However, blockchain has now
established itself as basic computational platform meant for executing small transactions called
as "Smart contracts"(Kosba et al., 2016). Accordingly, a blockchain is a form of distributive data
base as blockchain transactions can support different services such as notarization, registration,
voting, payments and escrow among other things.
Conventionally, certain third-party service providers such as banks, financial institutions,
legal firms and government authorities provide such services. However, the blockchain software
has now become reliable to provide an alternative to these providers. A blockchain ledger
comprises of a list or a chain of groups, referred to as blocks. The process involves addition of an
intended transaction to the “transaction pool” that would be recorded on the ledger. The
processing nodes that reside within a given blockchain community check the integrity of the
related transactions and subsequently record them by forming new blocks on the relevant ledger.
While different geographically-distributed nodes replicate the ledger contents, such processing
nodes are responsible to operate the blockchain system in a joint manner without being centrally
controlled by any third party. Hence, this technology offers a shared platform where majority of
such nodes jointly operate the relevant blockchain, thus replacing the need for trusting and
central a third party.
2.1 Advantages of using Blockchain technology
The Blockchain is the process by which the transactional information blocks of the
business organization is concatenated by using encryption technology (Coblenz, 2017). The use
of the technology is also used for storing the information provided in the bank’s information
system profusely. The use of encryption in the distributed system would provide the ease of
preventing the bad elements for infiltrating the system for extracting the information and
modifying it. The blockchain methods are helpful for listing the deployment of the improved
operational development. The integration of the activities is aligned with the formation of the
supportive development factors (Hull, 2017). The analysis would align the functional
deployment of operations. The alignment of the operations is aligned for the deployment of
improved operational development. The allowance of the integrations had provided the
development of the security for the analysis of the integration management. The deployment of
the operations is helpful for forming the security of the information stored in the development of
the improved functional development. The analysis had shown that the improved functional
analysis had been helpful of the system for listing the deployment of the improved functional
alignment (Hull et al., 2016). The blockchain industry is aligned for forming the development of
the cryptography alignment of the integration management of the functions.
2.0 Introduction of Blockchain technology and Smart contracts
While blockchain is a digital technology that combines cryptographic data management,
incentive mechanisms and networking for supporting the recording execution and checking of
transactions between the concerned parties, a blockchain ledger comprises of lists or blocks
pertaining to the relevant transaction (Peters & Panayi, 2016). Originally, this technology
emerged as a support to various kinds of digital currency. However, blockchain has now
established itself as basic computational platform meant for executing small transactions called
as "Smart contracts"(Kosba et al., 2016). Accordingly, a blockchain is a form of distributive data
base as blockchain transactions can support different services such as notarization, registration,
voting, payments and escrow among other things.
Conventionally, certain third-party service providers such as banks, financial institutions,
legal firms and government authorities provide such services. However, the blockchain software
has now become reliable to provide an alternative to these providers. A blockchain ledger
comprises of a list or a chain of groups, referred to as blocks. The process involves addition of an
intended transaction to the “transaction pool” that would be recorded on the ledger. The
processing nodes that reside within a given blockchain community check the integrity of the
related transactions and subsequently record them by forming new blocks on the relevant ledger.
While different geographically-distributed nodes replicate the ledger contents, such processing
nodes are responsible to operate the blockchain system in a joint manner without being centrally
controlled by any third party. Hence, this technology offers a shared platform where majority of
such nodes jointly operate the relevant blockchain, thus replacing the need for trusting and
central a third party.
2.1 Advantages of using Blockchain technology
The Blockchain is the process by which the transactional information blocks of the
business organization is concatenated by using encryption technology (Coblenz, 2017). The use
of the technology is also used for storing the information provided in the bank’s information
system profusely. The use of encryption in the distributed system would provide the ease of
preventing the bad elements for infiltrating the system for extracting the information and
modifying it. The blockchain methods are helpful for listing the deployment of the improved
operational development. The integration of the activities is aligned with the formation of the
supportive development factors (Hull, 2017). The analysis would align the functional
deployment of operations. The alignment of the operations is aligned for the deployment of
improved operational development. The allowance of the integrations had provided the
development of the security for the analysis of the integration management. The deployment of
the operations is helpful for forming the security of the information stored in the development of
the improved functional development. The analysis had shown that the improved functional
analysis had been helpful of the system for listing the deployment of the improved functional
alignment (Hull et al., 2016). The blockchain industry is aligned for forming the development of
the cryptography alignment of the integration management of the functions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
The alignment of the cryptography is helpful for the management of the successive
development for the options like Ethereum, Bitcoin, Koilion, and Ripple (Matsuo, 2017). The
smart contracts are helpful for listing the deployment of the improved operations. The funding
mechanism is applied for carrying out the deployment of the activities for the alignment of the
operations. The use of the successive factors of the integration would be based on the analysis of
the various factors of supportive and effective evaluation process (Bartoletti & Pompianu, 2017).
The various banking sectors have been using the technology of blockchain for their safe and
sound transactions and processes. The system alignment is formed for listing the management of
the simulation for the development model. The operations had deployed for the alignment of the
operations and supporting the formation of the system development operations. The use of the
blockchain is helpful for forming the alignment of the supportive development model. The
blockchain methods are helpful for listing the deployment of the improved operational
development (Rifi et al., 2017). The integration of the activities is aligned with the formation of
the supportive development factors.
Many scholars like Brunnler, Flumini andStuder (2018), have pointed out that the
Blockchain can be helpful for the process of supply chain management. The technology of
blockchain can be used for tracking orders, their sources, quality, and quantity also. The
blockchain offers the traceability and cost efficiency for the supply chain management system. It
is very helpful for bringing transparency in business to business (B2B) operations. The
operations of transfer and production had deployed for the alignment of the operations and
supporting the formation of the system development operations. According to the scholars like
Qi et al., (2017), the technology of the blockchain is helpful for analysing the quality of products
and goods. The analysis would align the functional deployment of operations. The alignment of
the operations is aligned for the deployment of improved operational development. The
allowance of the integrations had provided the development of the security for the analysis of the
integration management. The process of evaluation of the quality of the products can be checked
with the help of blockchain technology. The technology is also helpful for leading the product or
good to its origin for ensuring that the operations are successive and helpful for the development
of the implementation of the operations (Tang & Kostic, 2017). The analysis had also provided
scope for the safety of the products and batch processing for the goods.
2.2 Working of Blockchain
2.2.1 General working
After its original use for digital currencies such as Bitcoin, this technology is useful in
diverse platforms to serve different purposes. While blockchains can act like any traditional
database for representing information or transactions in many organizations within an industry,
these also can provide additional information that would have varied organizational and technical
consequences. Accordingly, there are distinct types of blockchains that serve varied purposes.
These are broadly categorized as “public blockchains” and “private or permissioned
blockchains” (Hernandez, 2017). While public blockchains allow for unrestricted public
participation in their use and operation, private blockchains are operated through private
computer networks that has strong access controls, usually operated through a nominated
administrator who has far more administrative controls. Accordingly, the software used for
running private blockchains may differ from that used in public blockchains. In this direction,
The alignment of the cryptography is helpful for the management of the successive
development for the options like Ethereum, Bitcoin, Koilion, and Ripple (Matsuo, 2017). The
smart contracts are helpful for listing the deployment of the improved operations. The funding
mechanism is applied for carrying out the deployment of the activities for the alignment of the
operations. The use of the successive factors of the integration would be based on the analysis of
the various factors of supportive and effective evaluation process (Bartoletti & Pompianu, 2017).
The various banking sectors have been using the technology of blockchain for their safe and
sound transactions and processes. The system alignment is formed for listing the management of
the simulation for the development model. The operations had deployed for the alignment of the
operations and supporting the formation of the system development operations. The use of the
blockchain is helpful for forming the alignment of the supportive development model. The
blockchain methods are helpful for listing the deployment of the improved operational
development (Rifi et al., 2017). The integration of the activities is aligned with the formation of
the supportive development factors.
Many scholars like Brunnler, Flumini andStuder (2018), have pointed out that the
Blockchain can be helpful for the process of supply chain management. The technology of
blockchain can be used for tracking orders, their sources, quality, and quantity also. The
blockchain offers the traceability and cost efficiency for the supply chain management system. It
is very helpful for bringing transparency in business to business (B2B) operations. The
operations of transfer and production had deployed for the alignment of the operations and
supporting the formation of the system development operations. According to the scholars like
Qi et al., (2017), the technology of the blockchain is helpful for analysing the quality of products
and goods. The analysis would align the functional deployment of operations. The alignment of
the operations is aligned for the deployment of improved operational development. The
allowance of the integrations had provided the development of the security for the analysis of the
integration management. The process of evaluation of the quality of the products can be checked
with the help of blockchain technology. The technology is also helpful for leading the product or
good to its origin for ensuring that the operations are successive and helpful for the development
of the implementation of the operations (Tang & Kostic, 2017). The analysis had also provided
scope for the safety of the products and batch processing for the goods.
2.2 Working of Blockchain
2.2.1 General working
After its original use for digital currencies such as Bitcoin, this technology is useful in
diverse platforms to serve different purposes. While blockchains can act like any traditional
database for representing information or transactions in many organizations within an industry,
these also can provide additional information that would have varied organizational and technical
consequences. Accordingly, there are distinct types of blockchains that serve varied purposes.
These are broadly categorized as “public blockchains” and “private or permissioned
blockchains” (Hernandez, 2017). While public blockchains allow for unrestricted public
participation in their use and operation, private blockchains are operated through private
computer networks that has strong access controls, usually operated through a nominated
administrator who has far more administrative controls. Accordingly, the software used for
running private blockchains may differ from that used in public blockchains. In this direction,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
certain industrial groups such as Ripple, R3CEV and Hyperledger are presently engaged in the
development of specialized software for running private blockchains. While such technical
solutions support only limited number of processing-nodes, which may not be the limitation in
public blockchains networking, these platforms do result in provision of higher confidentiality
and security.
While “Nakamoto Consensus” that allows the processing nodes to treat the longest book
history as an authoritative history is followed by public blockchains, private blockchains use
replication algorithms to ensure greater guarantee about the transaction completion process. For
example, Byzantine fault tolerance principle is used here instead of “Nakamoto Consensus”,
which is prevalent in public blockchains. In addition, the admittance of processing nodes is
controlled through the administrator in case of permissioned blockchain networks, while anyone
can become a miner (processing node) in public blockchain system. (Chen et al, 2017)
2.2.2Detailed working
As currently the financial institutions serve as tested third party responsible for
processing and mediating a financial transaction done through internet commerce, certain on-line
frauds are possible that need mediation into such transactions by the concerned institutions. This
process is certainly going to increase the transaction costs.Various cryptocurrencies are giving
rise to high benefits for worldwide business in terms of accepting BitCoin payment. These
accepting of payments from are done on the behalf of merchants. Moreover, it has been offering
option of converting payments to dollars and other types of traditional currencies very quickly.
The process insulated merchants from the volatility. Bitcoin network has seemed to move higher
and higher since the past few years. In this way, various types of bitcoins are responsible to raise
their transaction fees as per the response in the marketplace.
Accordingly, cryptographic proof is used in such transactions to avoid any trust in third
parties. This requires digital signatures. While the sender uses a private key to send such data,
the receiver can get it using the public key. In addition, the digital signatures of the sender are
verified using the private key of the sender. This method has found wide use in transaction of
digital currencies such as bitcoin.
The following diagram provides an idea about the working of blockchains system
involving the cryptocurrency transactions.
certain industrial groups such as Ripple, R3CEV and Hyperledger are presently engaged in the
development of specialized software for running private blockchains. While such technical
solutions support only limited number of processing-nodes, which may not be the limitation in
public blockchains networking, these platforms do result in provision of higher confidentiality
and security.
While “Nakamoto Consensus” that allows the processing nodes to treat the longest book
history as an authoritative history is followed by public blockchains, private blockchains use
replication algorithms to ensure greater guarantee about the transaction completion process. For
example, Byzantine fault tolerance principle is used here instead of “Nakamoto Consensus”,
which is prevalent in public blockchains. In addition, the admittance of processing nodes is
controlled through the administrator in case of permissioned blockchain networks, while anyone
can become a miner (processing node) in public blockchain system. (Chen et al, 2017)
2.2.2Detailed working
As currently the financial institutions serve as tested third party responsible for
processing and mediating a financial transaction done through internet commerce, certain on-line
frauds are possible that need mediation into such transactions by the concerned institutions. This
process is certainly going to increase the transaction costs.Various cryptocurrencies are giving
rise to high benefits for worldwide business in terms of accepting BitCoin payment. These
accepting of payments from are done on the behalf of merchants. Moreover, it has been offering
option of converting payments to dollars and other types of traditional currencies very quickly.
The process insulated merchants from the volatility. Bitcoin network has seemed to move higher
and higher since the past few years. In this way, various types of bitcoins are responsible to raise
their transaction fees as per the response in the marketplace.
Accordingly, cryptographic proof is used in such transactions to avoid any trust in third
parties. This requires digital signatures. While the sender uses a private key to send such data,
the receiver can get it using the public key. In addition, the digital signatures of the sender are
verified using the private key of the sender. This method has found wide use in transaction of
digital currencies such as bitcoin.
The following diagram provides an idea about the working of blockchains system
involving the cryptocurrency transactions.
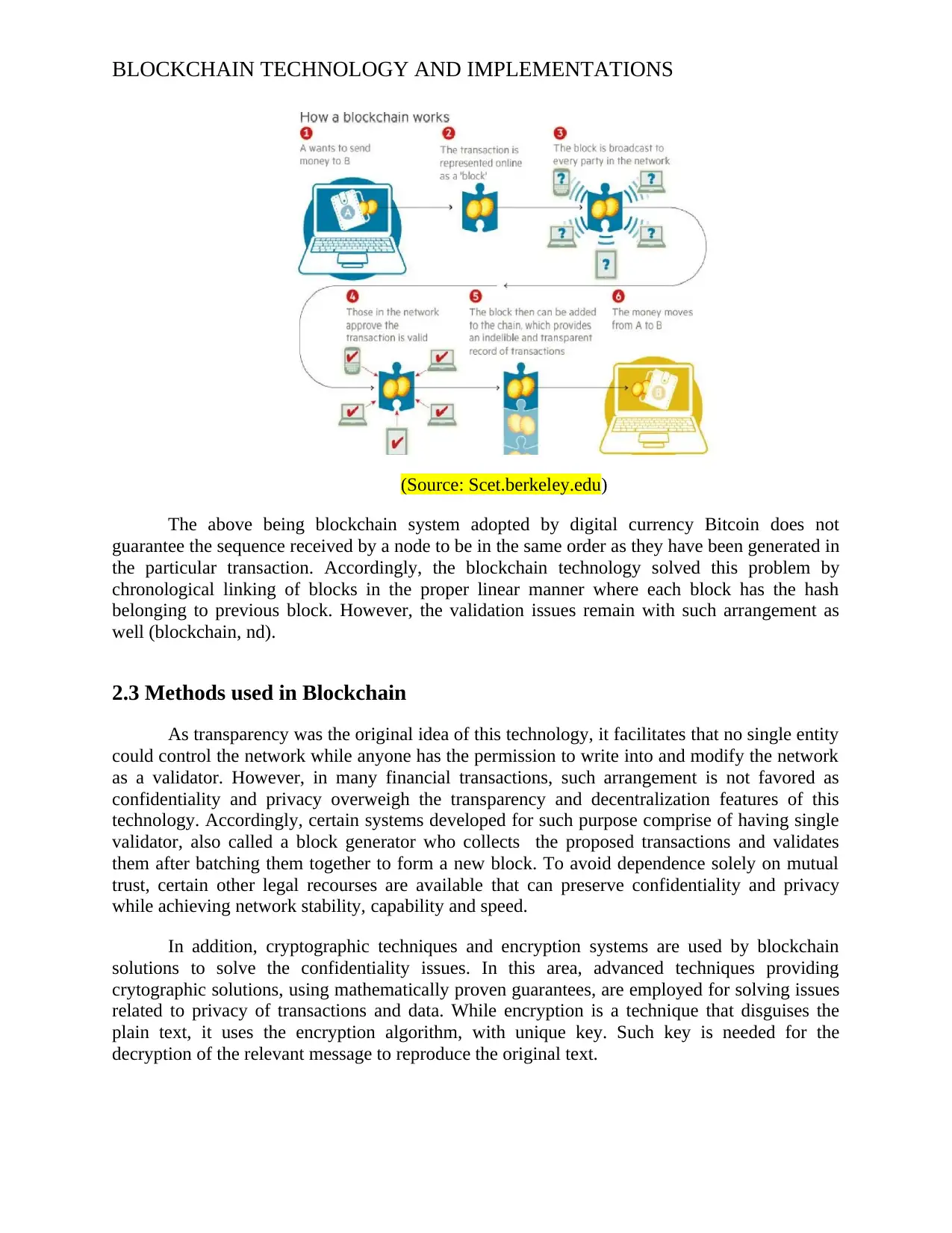
BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
(Source: Scet.berkeley.edu)
The above being blockchain system adopted by digital currency Bitcoin does not
guarantee the sequence received by a node to be in the same order as they have been generated in
the particular transaction. Accordingly, the blockchain technology solved this problem by
chronological linking of blocks in the proper linear manner where each block has the hash
belonging to previous block. However, the validation issues remain with such arrangement as
well (blockchain, nd).
2.3 Methods used in Blockchain
As transparency was the original idea of this technology, it facilitates that no single entity
could control the network while anyone has the permission to write into and modify the network
as a validator. However, in many financial transactions, such arrangement is not favored as
confidentiality and privacy overweigh the transparency and decentralization features of this
technology. Accordingly, certain systems developed for such purpose comprise of having single
validator, also called a block generator who collects the proposed transactions and validates
them after batching them together to form a new block. To avoid dependence solely on mutual
trust, certain other legal recourses are available that can preserve confidentiality and privacy
while achieving network stability, capability and speed.
In addition, cryptographic techniques and encryption systems are used by blockchain
solutions to solve the confidentiality issues. In this area, advanced techniques providing
crytographic solutions, using mathematically proven guarantees, are employed for solving issues
related to privacy of transactions and data. While encryption is a technique that disguises the
plain text, it uses the encryption algorithm, with unique key. Such key is needed for the
decryption of the relevant message to reproduce the original text.
(Source: Scet.berkeley.edu)
The above being blockchain system adopted by digital currency Bitcoin does not
guarantee the sequence received by a node to be in the same order as they have been generated in
the particular transaction. Accordingly, the blockchain technology solved this problem by
chronological linking of blocks in the proper linear manner where each block has the hash
belonging to previous block. However, the validation issues remain with such arrangement as
well (blockchain, nd).
2.3 Methods used in Blockchain
As transparency was the original idea of this technology, it facilitates that no single entity
could control the network while anyone has the permission to write into and modify the network
as a validator. However, in many financial transactions, such arrangement is not favored as
confidentiality and privacy overweigh the transparency and decentralization features of this
technology. Accordingly, certain systems developed for such purpose comprise of having single
validator, also called a block generator who collects the proposed transactions and validates
them after batching them together to form a new block. To avoid dependence solely on mutual
trust, certain other legal recourses are available that can preserve confidentiality and privacy
while achieving network stability, capability and speed.
In addition, cryptographic techniques and encryption systems are used by blockchain
solutions to solve the confidentiality issues. In this area, advanced techniques providing
crytographic solutions, using mathematically proven guarantees, are employed for solving issues
related to privacy of transactions and data. While encryption is a technique that disguises the
plain text, it uses the encryption algorithm, with unique key. Such key is needed for the
decryption of the relevant message to reproduce the original text.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
However, as blockchains need not to share any information about the change of state
related to it, this should happen legally. In order to achieve this, “Zero Knowledge Proofs” use
certain types of crytographic techniques that employ specific kind of homomorphic encryption.
The purpose of adopting this technique involves separation of information needed for reaching a
concolusive and valid state of affairs. In addition, such technique must ensure that the statement
is true as proven by the honest prover and verified by the verifier who is following the proper
protocol. However, there remains a small probability involving a cheating prover that can
convince the verifier about truth of this statement. The “zero knowledge” feature ensures that a
transcript is produced which reflects the interaction between a cheating verifier and an honest
prover through the use of some kind of simulator. Certain tehnological solutions such as zk-
SNARKs offer this type of zero knowledge proof. However, another technique, called Zcash is a
replicated ledger that uses a permissionless encrypted information for recording private data
within a public blockchain.
According to Andrew Miller (The trend, 2016), Hawk, which is another cryptography
model aiming at preserving privacy does not record the financial transactions within the
blockchain system and this program hides from public all data while keeping its code of contract
as private along with keeping the money as well as data sent and received as private. All
information except the required proof is visible in such program. In addition, it tackles various
issues related to privacy and validity in a manner that is similar to Zcash. (The trend, 2016)
While proprties of permissioned blockchains include public verifiability that allows
anyone to verify the correctness of the system, it requires data transparency and updation of the
state. As trust forms the basis of this system, a trust anchor is nominated, who can have the
authority to allow access to the system while revoking the write and read access to the system, if
needed. However, the problem of exposed data to all users in the network prevail between the
transparency and privacy and it may be easier to achieve privacy in centralized system, as public
verifiability is not needed in such a system(Wust & Gerveis, nd).
3.0Difference between public and private blockchain systems
When there is a need for the network to be decentralized, the public chain system is most
suitable, while it ensures total transparency of the relevant ledger as well as anonymity. The
public blockchain system sets up blocks of different peer-to-peer transactions. The verification is
done for each transaction before it is synced with each node associated with the system.
Thereafter the relevant transaction is recorded in the system. The next transaction can move
forward only after this verification and synchronization takes place. As everyone can become a
node in public system, the only requirement for setting up a node is the availability of internet
connection and a computer. Due to this feature, it is called a public blockchain system. As access
is allowed to everyone for public block chain history, the system functions slowly as compared
to a private blockchain system. In addition, it consumes enormous energy, as electricity demand
increases with addition of a new node. However, public blockchains offer advantages of
preserving anonymity while each transaction remains public.
In private blockchain system, each transaction needs complete verification. The company
running the system can write and verify every transaction, while it can also choose to permit or
However, as blockchains need not to share any information about the change of state
related to it, this should happen legally. In order to achieve this, “Zero Knowledge Proofs” use
certain types of crytographic techniques that employ specific kind of homomorphic encryption.
The purpose of adopting this technique involves separation of information needed for reaching a
concolusive and valid state of affairs. In addition, such technique must ensure that the statement
is true as proven by the honest prover and verified by the verifier who is following the proper
protocol. However, there remains a small probability involving a cheating prover that can
convince the verifier about truth of this statement. The “zero knowledge” feature ensures that a
transcript is produced which reflects the interaction between a cheating verifier and an honest
prover through the use of some kind of simulator. Certain tehnological solutions such as zk-
SNARKs offer this type of zero knowledge proof. However, another technique, called Zcash is a
replicated ledger that uses a permissionless encrypted information for recording private data
within a public blockchain.
According to Andrew Miller (The trend, 2016), Hawk, which is another cryptography
model aiming at preserving privacy does not record the financial transactions within the
blockchain system and this program hides from public all data while keeping its code of contract
as private along with keeping the money as well as data sent and received as private. All
information except the required proof is visible in such program. In addition, it tackles various
issues related to privacy and validity in a manner that is similar to Zcash. (The trend, 2016)
While proprties of permissioned blockchains include public verifiability that allows
anyone to verify the correctness of the system, it requires data transparency and updation of the
state. As trust forms the basis of this system, a trust anchor is nominated, who can have the
authority to allow access to the system while revoking the write and read access to the system, if
needed. However, the problem of exposed data to all users in the network prevail between the
transparency and privacy and it may be easier to achieve privacy in centralized system, as public
verifiability is not needed in such a system(Wust & Gerveis, nd).
3.0Difference between public and private blockchain systems
When there is a need for the network to be decentralized, the public chain system is most
suitable, while it ensures total transparency of the relevant ledger as well as anonymity. The
public blockchain system sets up blocks of different peer-to-peer transactions. The verification is
done for each transaction before it is synced with each node associated with the system.
Thereafter the relevant transaction is recorded in the system. The next transaction can move
forward only after this verification and synchronization takes place. As everyone can become a
node in public system, the only requirement for setting up a node is the availability of internet
connection and a computer. Due to this feature, it is called a public blockchain system. As access
is allowed to everyone for public block chain history, the system functions slowly as compared
to a private blockchain system. In addition, it consumes enormous energy, as electricity demand
increases with addition of a new node. However, public blockchains offer advantages of
preserving anonymity while each transaction remains public.
In private blockchain system, each transaction needs complete verification. The company
running the system can write and verify every transaction, while it can also choose to permit or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
hold the “read” access to transactions. While this provides more privacy as compared to the
public blockchains, the decentralized security cannot be offered by the private blockchains. As
the power consolidation remains with only one company, there is the possibility of misusing
such power.
An attempt to resolve this issue, a consortium blockchain platform or permissioned is
available that is only partly private. In such a system, certain pre-determined selected nodes are
authorized to verify the transactions. Accordingly, a consortium blockchain can provide full
benefits, such as transaction privacy and efficiency, that are available in private blockchains
while the authorization power will not remain with any single company or node. At the same
time, it is not fully public as access to everyone with internet connection and computer is not
possible in this situation. (Thompson, 2015)
hold the “read” access to transactions. While this provides more privacy as compared to the
public blockchains, the decentralized security cannot be offered by the private blockchains. As
the power consolidation remains with only one company, there is the possibility of misusing
such power.
An attempt to resolve this issue, a consortium blockchain platform or permissioned is
available that is only partly private. In such a system, certain pre-determined selected nodes are
authorized to verify the transactions. Accordingly, a consortium blockchain can provide full
benefits, such as transaction privacy and efficiency, that are available in private blockchains
while the authorization power will not remain with any single company or node. At the same
time, it is not fully public as access to everyone with internet connection and computer is not
possible in this situation. (Thompson, 2015)
Running head:BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
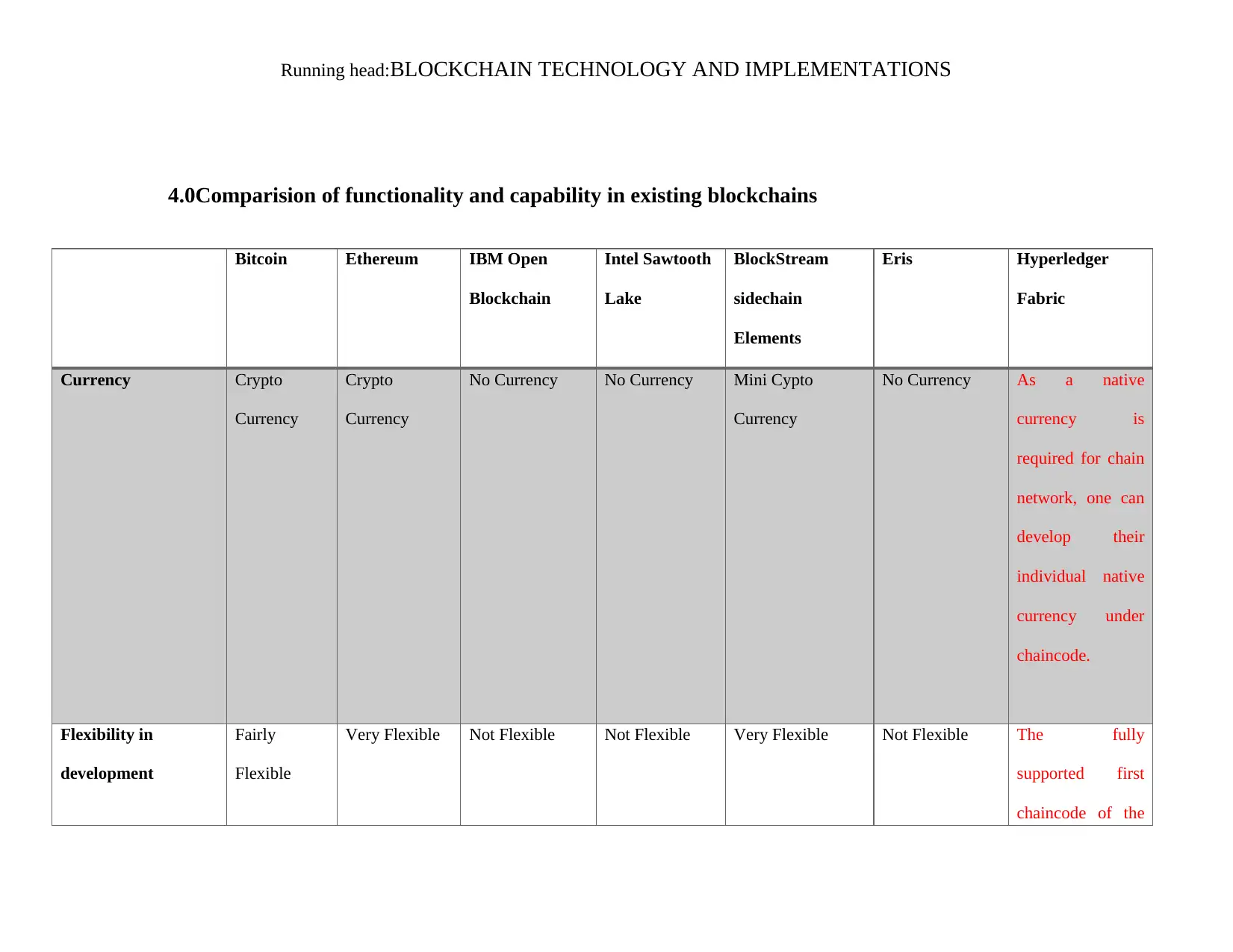
4.0Comparision of functionality and capability in existing blockchains
Bitcoin Ethereum IBM Open
Blockchain
Intel Sawtooth
Lake
BlockStream
sidechain
Elements
Eris Hyperledger
Fabric
Currency Crypto
Currency
Crypto
Currency
No Currency No Currency Mini Cypto
Currency
No Currency As a native
currency is
required for chain
network, one can
develop their
individual native
currency under
chaincode.
Flexibility in
development
Fairly
Flexible
Very Flexible Not Flexible Not Flexible Very Flexible Not Flexible The fully
supported first
chaincode of the
4.0Comparision of functionality and capability in existing blockchains
Bitcoin Ethereum IBM Open
Blockchain
Intel Sawtooth
Lake
BlockStream
sidechain
Elements
Eris Hyperledger
Fabric
Currency Crypto
Currency
Crypto
Currency
No Currency No Currency Mini Cypto
Currency
No Currency As a native
currency is
required for chain
network, one can
develop their
individual native
currency under
chaincode.
Flexibility in
development
Fairly
Flexible
Very Flexible Not Flexible Not Flexible Very Flexible Not Flexible The fully
supported first
chaincode of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
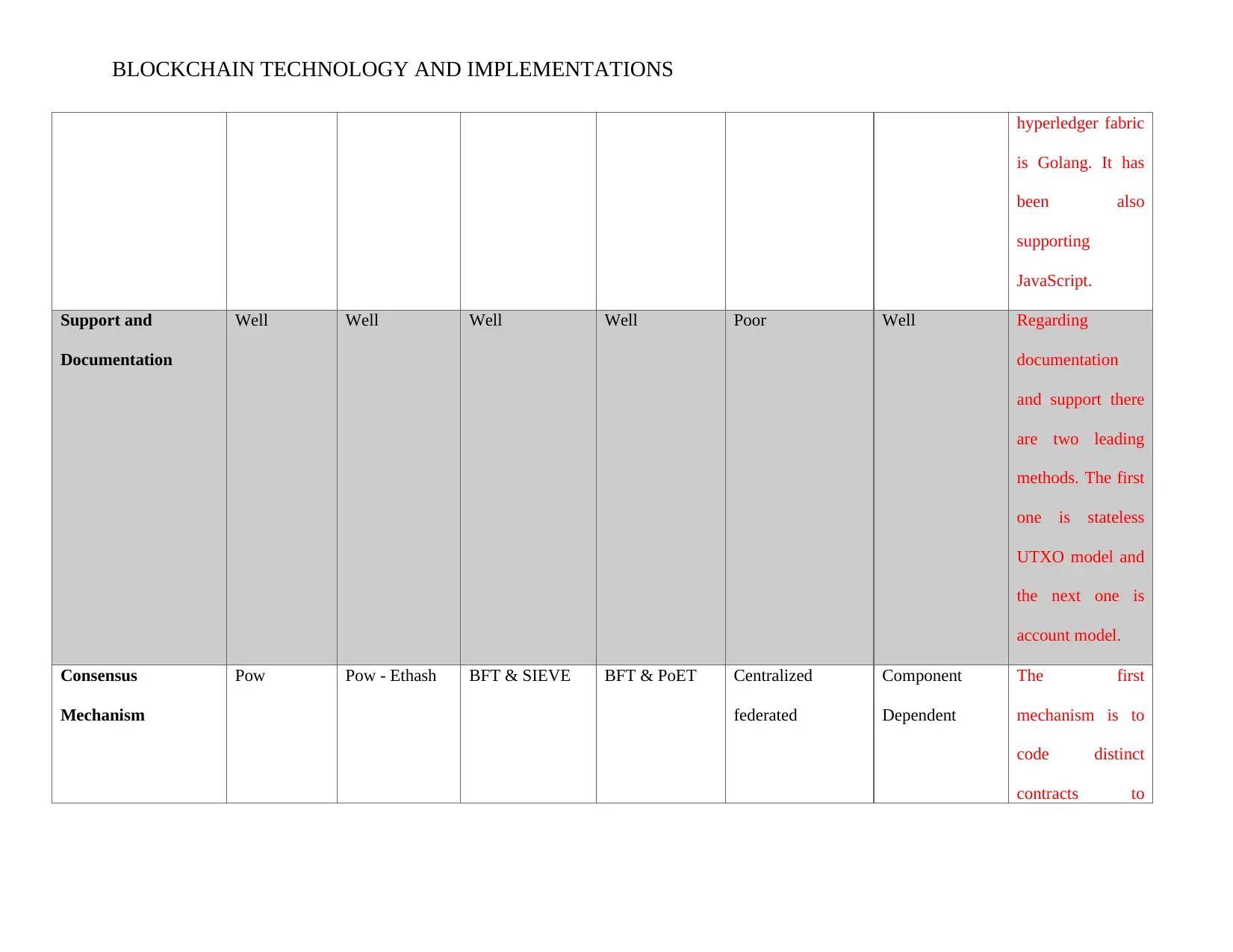
BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
hyperledger fabric
is Golang. It has
been also
supporting
JavaScript.
Support and
Documentation
Well Well Well Well Poor Well Regarding
documentation
and support there
are two leading
methods. The first
one is stateless
UTXO model and
the next one is
account model.
Consensus
Mechanism
Pow Pow - Ethash BFT & SIEVE BFT & PoET Centralized
federated
Component
Dependent
The first
mechanism is to
code distinct
contracts to
hyperledger fabric
is Golang. It has
been also
supporting
JavaScript.
Support and
Documentation
Well Well Well Well Poor Well Regarding
documentation
and support there
are two leading
methods. The first
one is stateless
UTXO model and
the next one is
account model.
Consensus
Mechanism
Pow Pow - Ethash BFT & SIEVE BFT & PoET Centralized
federated
Component
Dependent
The first
mechanism is to
code distinct
contracts to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
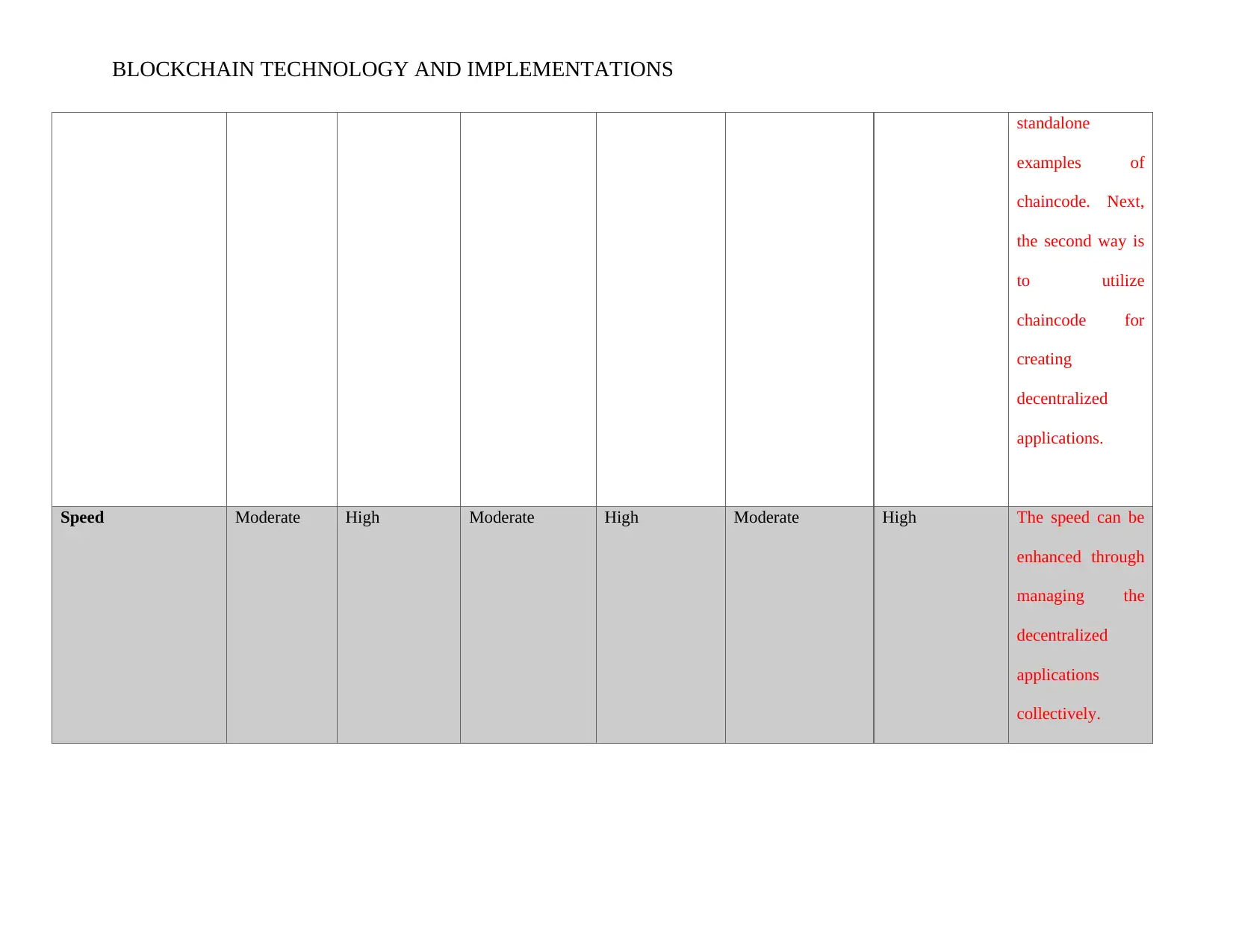
BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
standalone
examples of
chaincode. Next,
the second way is
to utilize
chaincode for
creating
decentralized
applications.
Speed Moderate High Moderate High Moderate High The speed can be
enhanced through
managing the
decentralized
applications
collectively.
standalone
examples of
chaincode. Next,
the second way is
to utilize
chaincode for
creating
decentralized
applications.
Speed Moderate High Moderate High Moderate High The speed can be
enhanced through
managing the
decentralized
applications
collectively.
BLOCKCHAIN TECHNOLOGY AND IMPLEMENTATIONS
Usability of bitcoin is the user experience. It has been referring to the ease of access and use of website and product. Designing
of bitcoins, helps the users to determine the level of usability though these bitcoins are unusable One of the main problems for new
technologies like crypto-currencies is efficiently that are presented to the users. It has been mapped towards current mental models
that have been balancing its security and ease of use. In the present scenario of block-chains, the challenge has been specifically more
acute. This is because the stakes has been high and those patterns are comparatively new. Security in terms of bitcoins has been
defending information and resources against various external and internal, accidental and malicious threats. Defense mechanisms for
this security include response, prevention and detection towards threats using security policies, software tools and various IT services.
Blocks of bitcoins consists of transitions over bitcoin network. This on chain processing capacity of bitcoin netwrok gets
restricted because of many factors. These factors include average block creation tie of 10 minutes and limiting the block size. In this
case firstly, blockchain technologies are related to the high complexity and array of largely-specialized terms. Then there is the
network growth of users that has been huge and constantly rising. This facilitates the stringer reaction for attacks. Next, there are risks
of error taking pace due to various involvements of different kinds human factors. Further, bitcoins and other blockchains are related
with considerable security flaw. Lastly, during the initial years after the launch of Bitcoin, the transactions of digital currency have
been nearly free.
Scalability is the attribute describing ability of bitcoins to grow and manage its rise in demand. Bitcoin is scalable in nature. It
is more adaptable towards the change in demands or needs of the users. At present, every blockchain consensus protocols can adapt to
change in needs. It denotes that all the nodes that are participating completely within the network should process all transactions.
Recalling of the blockchains comprises of one inherent critical characteristic. It is called decentralization. This indicates that all the
single nodes that are present over the networks must process all transaction. Besides, they must maintain a copy of the complete state.
Usability of bitcoin is the user experience. It has been referring to the ease of access and use of website and product. Designing
of bitcoins, helps the users to determine the level of usability though these bitcoins are unusable One of the main problems for new
technologies like crypto-currencies is efficiently that are presented to the users. It has been mapped towards current mental models
that have been balancing its security and ease of use. In the present scenario of block-chains, the challenge has been specifically more
acute. This is because the stakes has been high and those patterns are comparatively new. Security in terms of bitcoins has been
defending information and resources against various external and internal, accidental and malicious threats. Defense mechanisms for
this security include response, prevention and detection towards threats using security policies, software tools and various IT services.
Blocks of bitcoins consists of transitions over bitcoin network. This on chain processing capacity of bitcoin netwrok gets
restricted because of many factors. These factors include average block creation tie of 10 minutes and limiting the block size. In this
case firstly, blockchain technologies are related to the high complexity and array of largely-specialized terms. Then there is the
network growth of users that has been huge and constantly rising. This facilitates the stringer reaction for attacks. Next, there are risks
of error taking pace due to various involvements of different kinds human factors. Further, bitcoins and other blockchains are related
with considerable security flaw. Lastly, during the initial years after the launch of Bitcoin, the transactions of digital currency have
been nearly free.
Scalability is the attribute describing ability of bitcoins to grow and manage its rise in demand. Bitcoin is scalable in nature. It
is more adaptable towards the change in demands or needs of the users. At present, every blockchain consensus protocols can adapt to
change in needs. It denotes that all the nodes that are participating completely within the network should process all transactions.
Recalling of the blockchains comprises of one inherent critical characteristic. It is called decentralization. This indicates that all the
single nodes that are present over the networks must process all transaction. Besides, they must maintain a copy of the complete state.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





