BN202 Internetworking Technologies: Network Analysis & Plan
VerifiedAdded on 2023/04/03
|16
|1147
|247
Report
AI Summary
This report presents a network requirement analysis and plan for HiTech, focusing on eliminating current network problems and aligning the network with the organization's growth. The project scope includes dividing the network into sub-groups by department, reducing broadcast messages, minimizing packet loss and congestion, and improving network uptime. Functional requirements include enhancing bandwidth utilization, enabling load balancing, and using centralized network management. Non-functional requirements address user training, power backup, hardware compatibility, and topology selection. The network design employs a three-layer hierarchical model with a layer three switching device configured as a VTP server. The report also includes network topology diagrams, switch and router configurations, DHCP configuration details, and access point/server configuration guidelines, along with Netsim configurations and references.

Running head: INTERNETWORKING TECHNOLOGIES
Assignment 2 - Network requirement analysis and plan
Name of the Student
Name of the University
Author’s Note
Assignment 2 - Network requirement analysis and plan
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNETWORKING TECHNOLOGIES
Project Scope
The implementation of network solution for HiTech would help the organization to eliminate the
current problems and the scope of the project are listed below:
Incorporating current organizational growth and aligning the network with the
organizational framework such that the design is optimized and help in increasing the
efficiency of the users.
Dividing the network into smaller sub groups according to the name of the department such
that the bandwidth is utilized efficiently and error in device of one of the department does
not affect the whole network.
To reduce the broadcast message and eliminate packet loss, jitter and congestion in the
network and increase the network uptime.
To handle large number of traffic from the different department and reduce the response
time of the network with the implementation of redundant link and virtualization of server.
To secure the router and switch configuration with password such that it cannot be modified
for creating backdoor for the intruder to access the internal resources of the network.
Project requirements
Functional Requirement
● To minimize packet loss, congestion and jitter and enable quality of service for improving the
network performance.
● To improve the utilization of bandwidth, traffic management and monitor the network for
identification of flow of data packets between the different areas of the network.
● To enable load balancing and use multiple path to reach the destination address such that
the response is minimized and reliability of the network in improved.
● To use centralized management of the network and configure the switch with VTP server
such that it can be used for configuring the VLAN and distributing with the client switches for
minimizing the configuration and troubleshooting time.
INTERNETWORKING TECHNOLOGIES
Project Scope
The implementation of network solution for HiTech would help the organization to eliminate the
current problems and the scope of the project are listed below:
Incorporating current organizational growth and aligning the network with the
organizational framework such that the design is optimized and help in increasing the
efficiency of the users.
Dividing the network into smaller sub groups according to the name of the department such
that the bandwidth is utilized efficiently and error in device of one of the department does
not affect the whole network.
To reduce the broadcast message and eliminate packet loss, jitter and congestion in the
network and increase the network uptime.
To handle large number of traffic from the different department and reduce the response
time of the network with the implementation of redundant link and virtualization of server.
To secure the router and switch configuration with password such that it cannot be modified
for creating backdoor for the intruder to access the internal resources of the network.
Project requirements
Functional Requirement
● To minimize packet loss, congestion and jitter and enable quality of service for improving the
network performance.
● To improve the utilization of bandwidth, traffic management and monitor the network for
identification of flow of data packets between the different areas of the network.
● To enable load balancing and use multiple path to reach the destination address such that
the response is minimized and reliability of the network in improved.
● To use centralized management of the network and configure the switch with VTP server
such that it can be used for configuring the VLAN and distributing with the client switches for
minimizing the configuration and troubleshooting time.

2
INTERNETWORKING TECHNOLOGIES
● To configure the router with DHCP scope such that the device connected in the network
automatically gets the IP address from the router interface.
● To develop an IP address plan and record the IP address used for each of the subnet such
that the network can be troubleshoot for any errors easily
Non Functional Requirement
● To develop a training plan for the users of the network for aware them about the
consequences of misusing the network or visiting malicious websites
● To arrange power backup for the network device such that the network can withstand the
power disruption condition.
● To identify the hardware device that are needed for the configuration of the network and
reviewing the compatibility of the device with the other device already installed in the
network.
● To select a network topology that would be suitable for meeting the current organizational
structure and implement for redesigning the network.
Network Design strategy
For the development of the network design research is performed on the technology that can be
applied for the network development. Identification of the technology helps in selecting the
appropriate network device that is needed to be installed for management of communication
between each of the department. The design of the network is prepared based on the organizational
framework and implementation of three-layer hierarchical model such that redundancy of the
network is maintained and meets the functional and nonfunctional requirement. Layer three
switching device is selected as the core switch and configured as VTP server such that VLAN
information are shared with the client switches installed for distribution of the network and
connecting the end device. The redundant link are connected with the port and they are configured
as switch port mode trunk for carrying the VLAN information with the other network device. For
enabling the access of the VLAN for each of the network the switches are configured with switch
port mode access and the VLAN configured for the department are allowed access such that the PC
INTERNETWORKING TECHNOLOGIES
● To configure the router with DHCP scope such that the device connected in the network
automatically gets the IP address from the router interface.
● To develop an IP address plan and record the IP address used for each of the subnet such
that the network can be troubleshoot for any errors easily
Non Functional Requirement
● To develop a training plan for the users of the network for aware them about the
consequences of misusing the network or visiting malicious websites
● To arrange power backup for the network device such that the network can withstand the
power disruption condition.
● To identify the hardware device that are needed for the configuration of the network and
reviewing the compatibility of the device with the other device already installed in the
network.
● To select a network topology that would be suitable for meeting the current organizational
structure and implement for redesigning the network.
Network Design strategy
For the development of the network design research is performed on the technology that can be
applied for the network development. Identification of the technology helps in selecting the
appropriate network device that is needed to be installed for management of communication
between each of the department. The design of the network is prepared based on the organizational
framework and implementation of three-layer hierarchical model such that redundancy of the
network is maintained and meets the functional and nonfunctional requirement. Layer three
switching device is selected as the core switch and configured as VTP server such that VLAN
information are shared with the client switches installed for distribution of the network and
connecting the end device. The redundant link are connected with the port and they are configured
as switch port mode trunk for carrying the VLAN information with the other network device. For
enabling the access of the VLAN for each of the network the switches are configured with switch
port mode access and the VLAN configured for the department are allowed access such that the PC
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INTERNETWORKING TECHNOLOGIES
connected with the switch automatically gets configured with the IP address configured in the router
for the intended department.
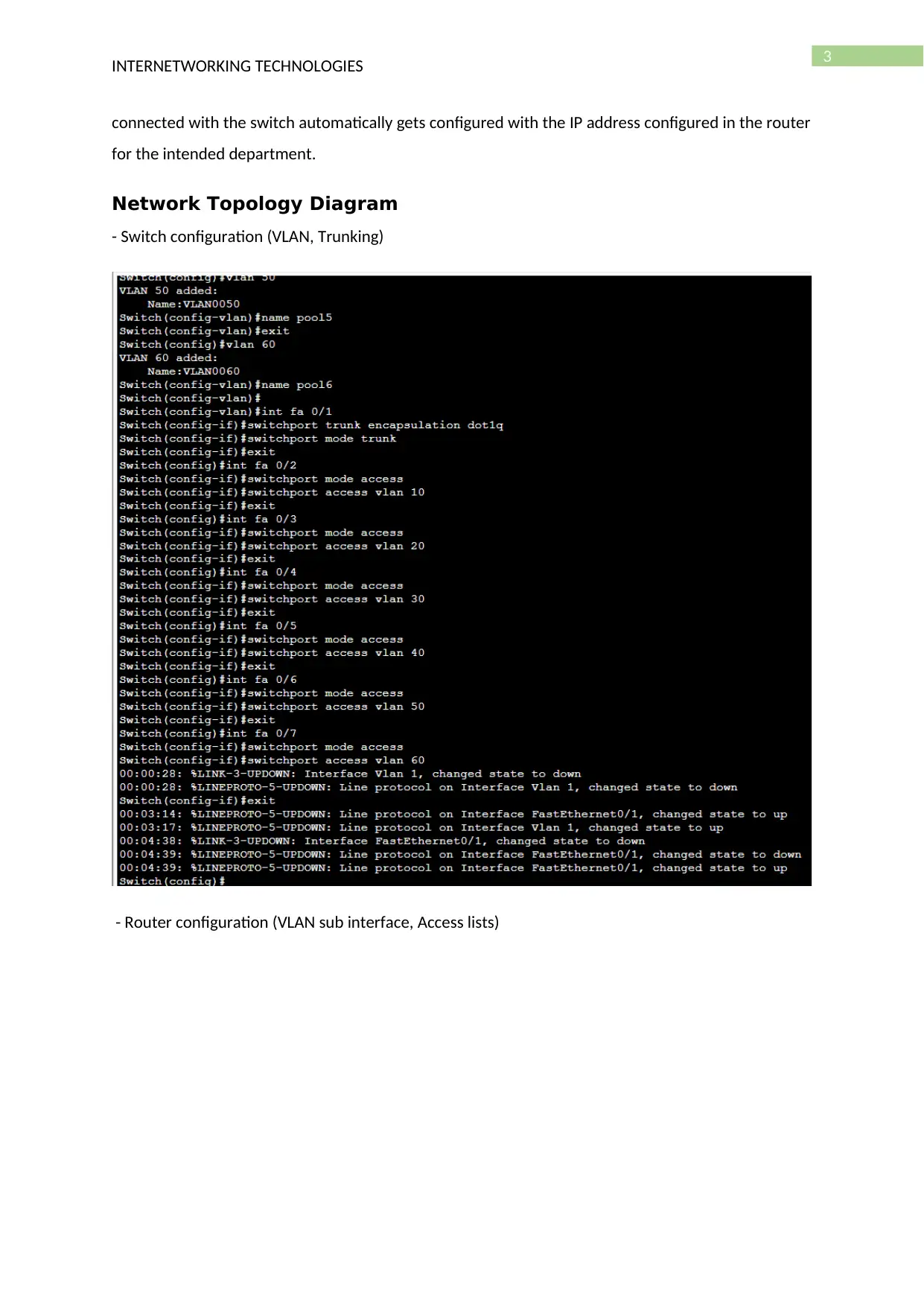
Network Topology Diagram
- Switch configuration (VLAN, Trunking)
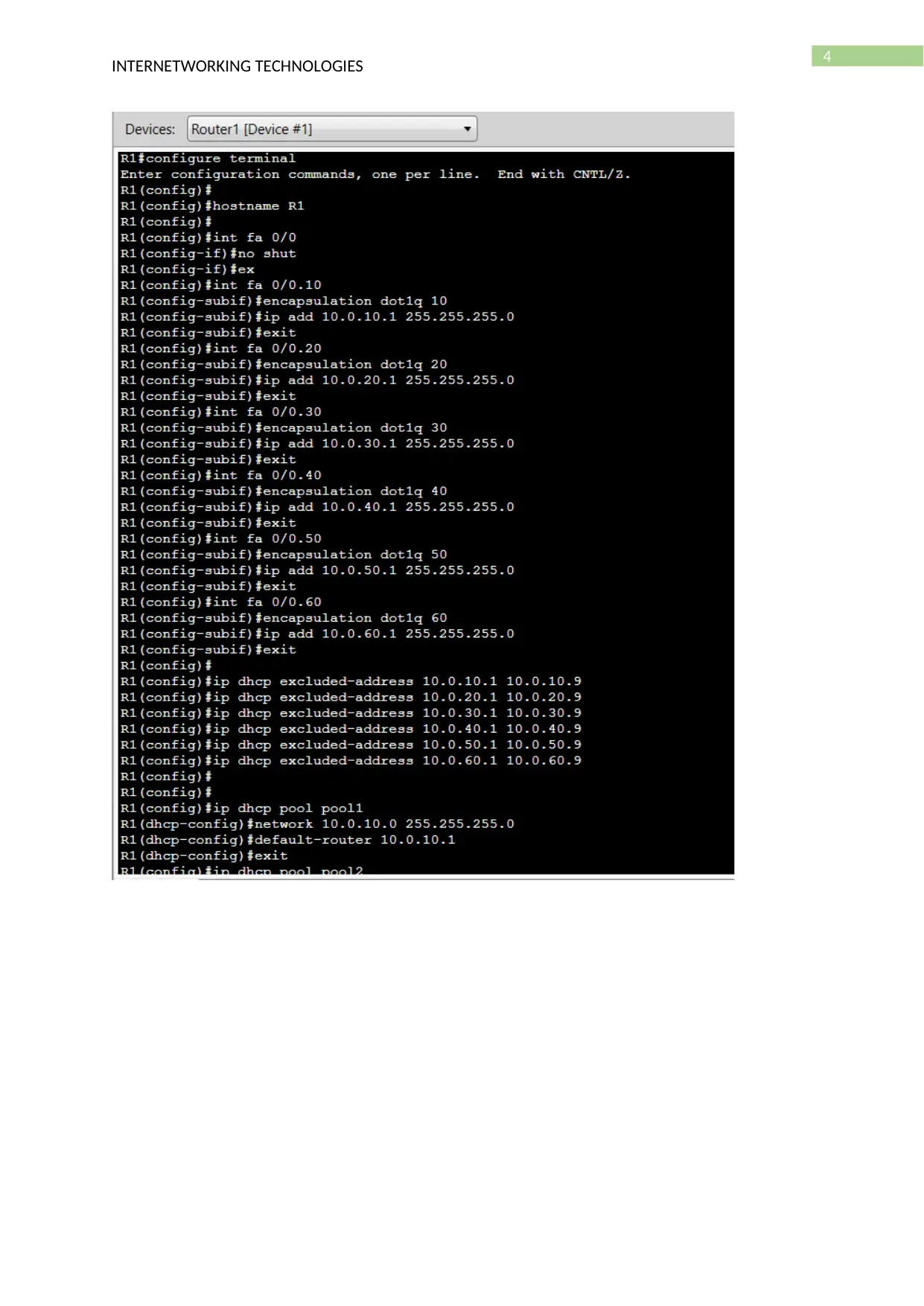
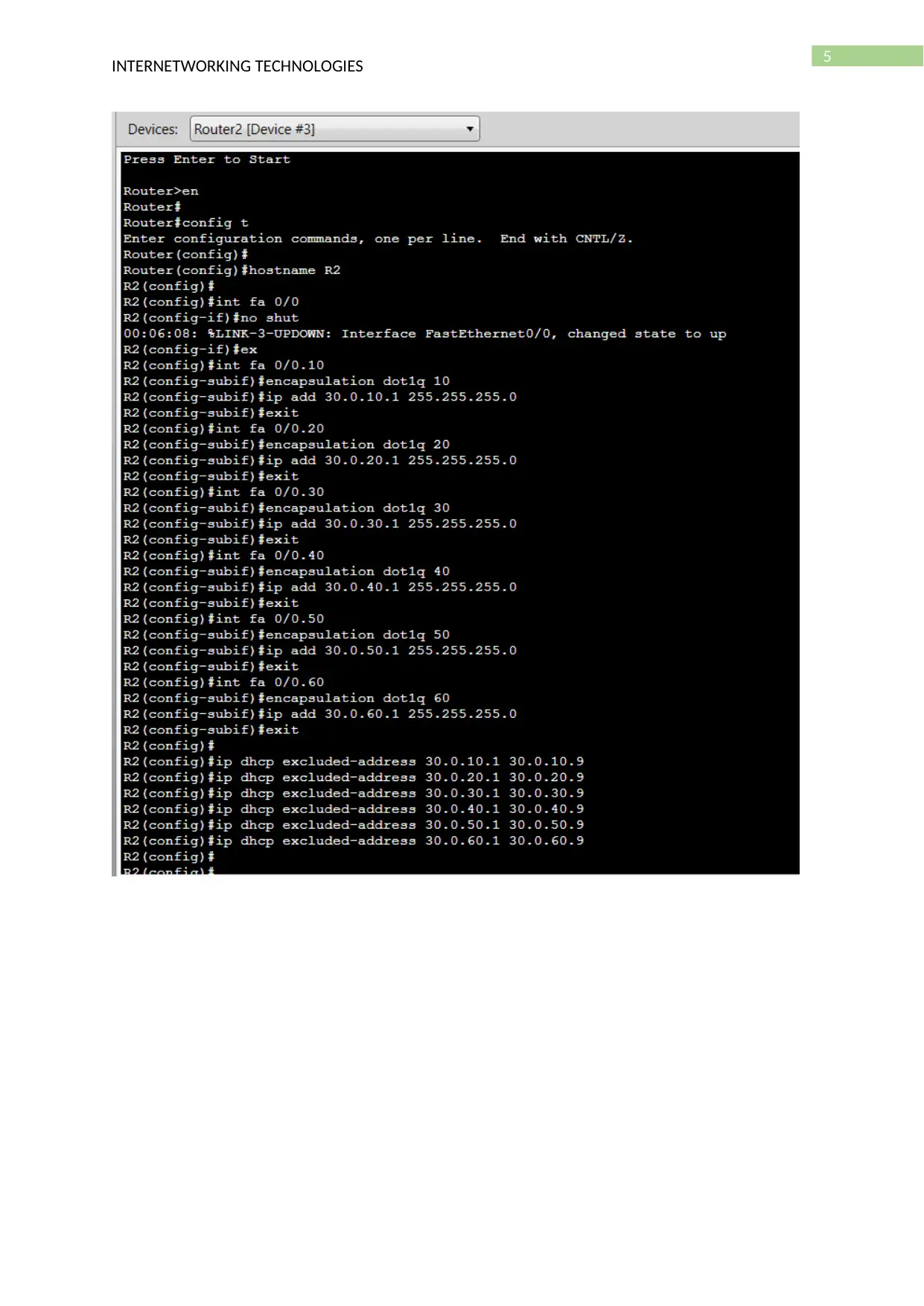
- Router configuration (VLAN sub interface, Access lists)
INTERNETWORKING TECHNOLOGIES
connected with the switch automatically gets configured with the IP address configured in the router
for the intended department.
Network Topology Diagram
- Switch configuration (VLAN, Trunking)
- Router configuration (VLAN sub interface, Access lists)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INTERNETWORKING TECHNOLOGIES
INTERNETWORKING TECHNOLOGIES
5
INTERNETWORKING TECHNOLOGIES
INTERNETWORKING TECHNOLOGIES
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTERNETWORKING TECHNOLOGIES
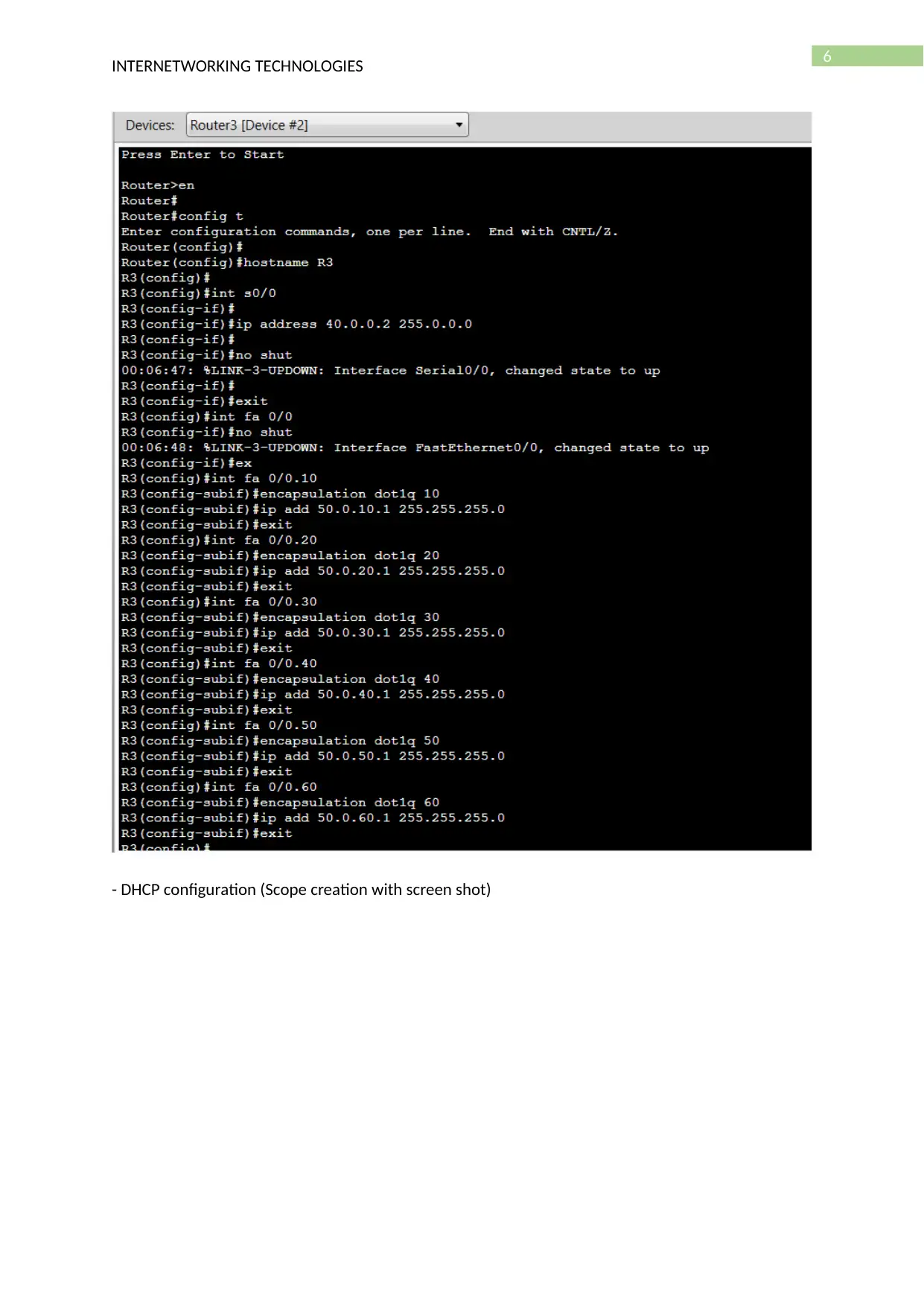
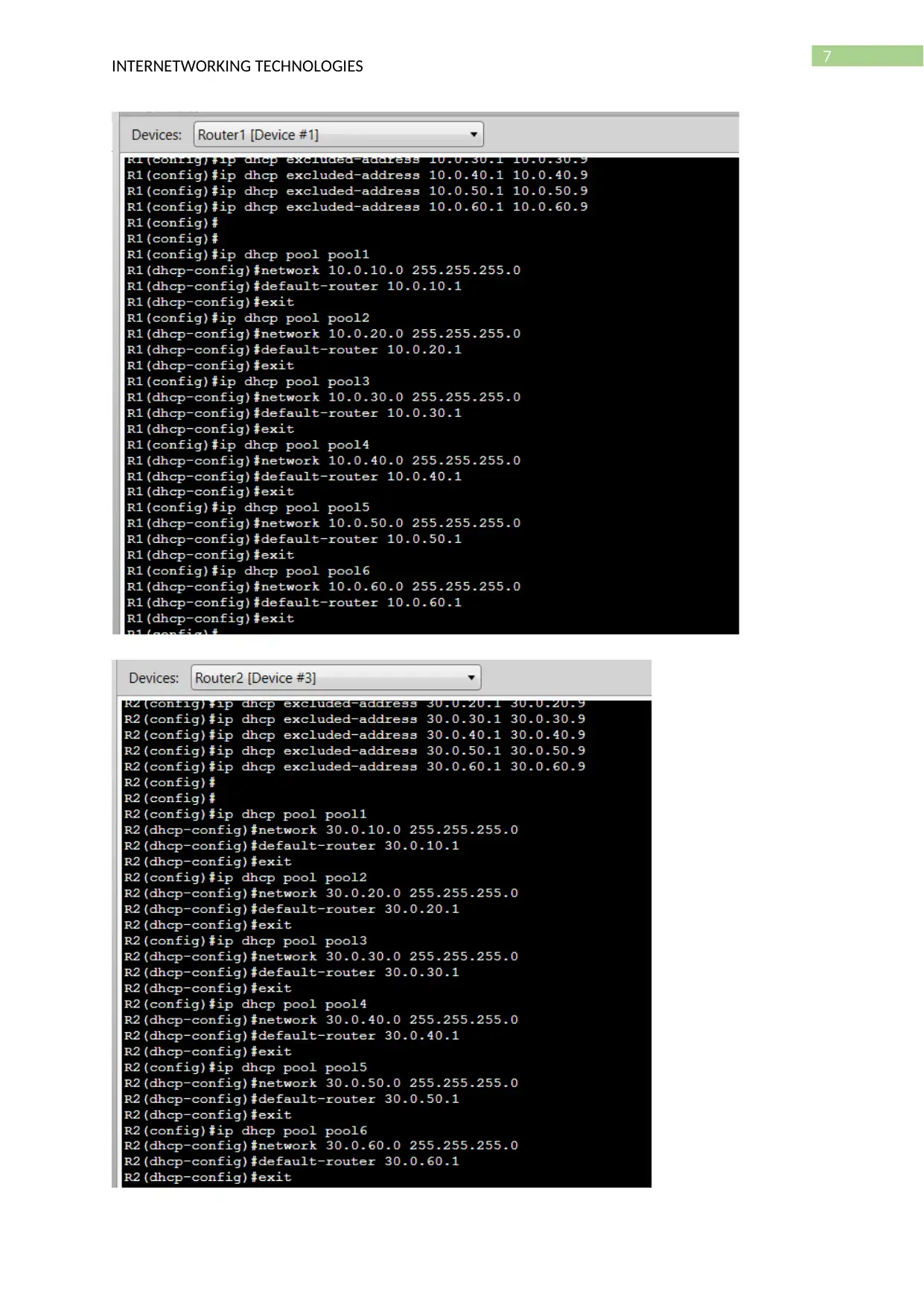
- DHCP configuration (Scope creation with screen shot)
INTERNETWORKING TECHNOLOGIES
- DHCP configuration (Scope creation with screen shot)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INTERNETWORKING TECHNOLOGIES
INTERNETWORKING TECHNOLOGIES
8
INTERNETWORKING TECHNOLOGIES
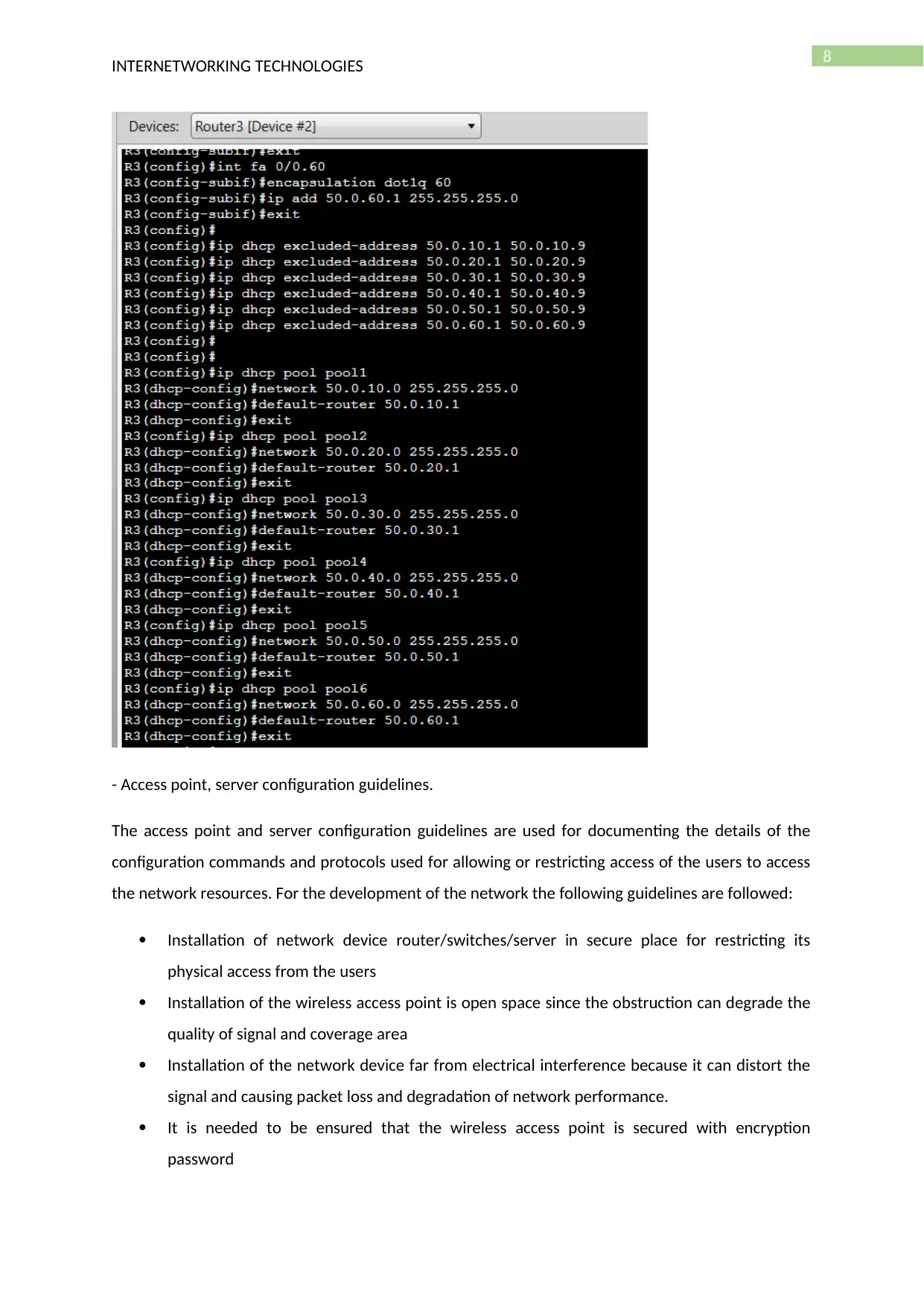
- Access point, server configuration guidelines.
The access point and server configuration guidelines are used for documenting the details of the
configuration commands and protocols used for allowing or restricting access of the users to access
the network resources. For the development of the network the following guidelines are followed:
Installation of network device router/switches/server in secure place for restricting its
physical access from the users
Installation of the wireless access point is open space since the obstruction can degrade the
quality of signal and coverage area
Installation of the network device far from electrical interference because it can distort the
signal and causing packet loss and degradation of network performance.
It is needed to be ensured that the wireless access point is secured with encryption
password
INTERNETWORKING TECHNOLOGIES
- Access point, server configuration guidelines.
The access point and server configuration guidelines are used for documenting the details of the
configuration commands and protocols used for allowing or restricting access of the users to access
the network resources. For the development of the network the following guidelines are followed:
Installation of network device router/switches/server in secure place for restricting its
physical access from the users
Installation of the wireless access point is open space since the obstruction can degrade the
quality of signal and coverage area
Installation of the network device far from electrical interference because it can distort the
signal and causing packet loss and degradation of network performance.
It is needed to be ensured that the wireless access point is secured with encryption
password
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INTERNETWORKING TECHNOLOGIES
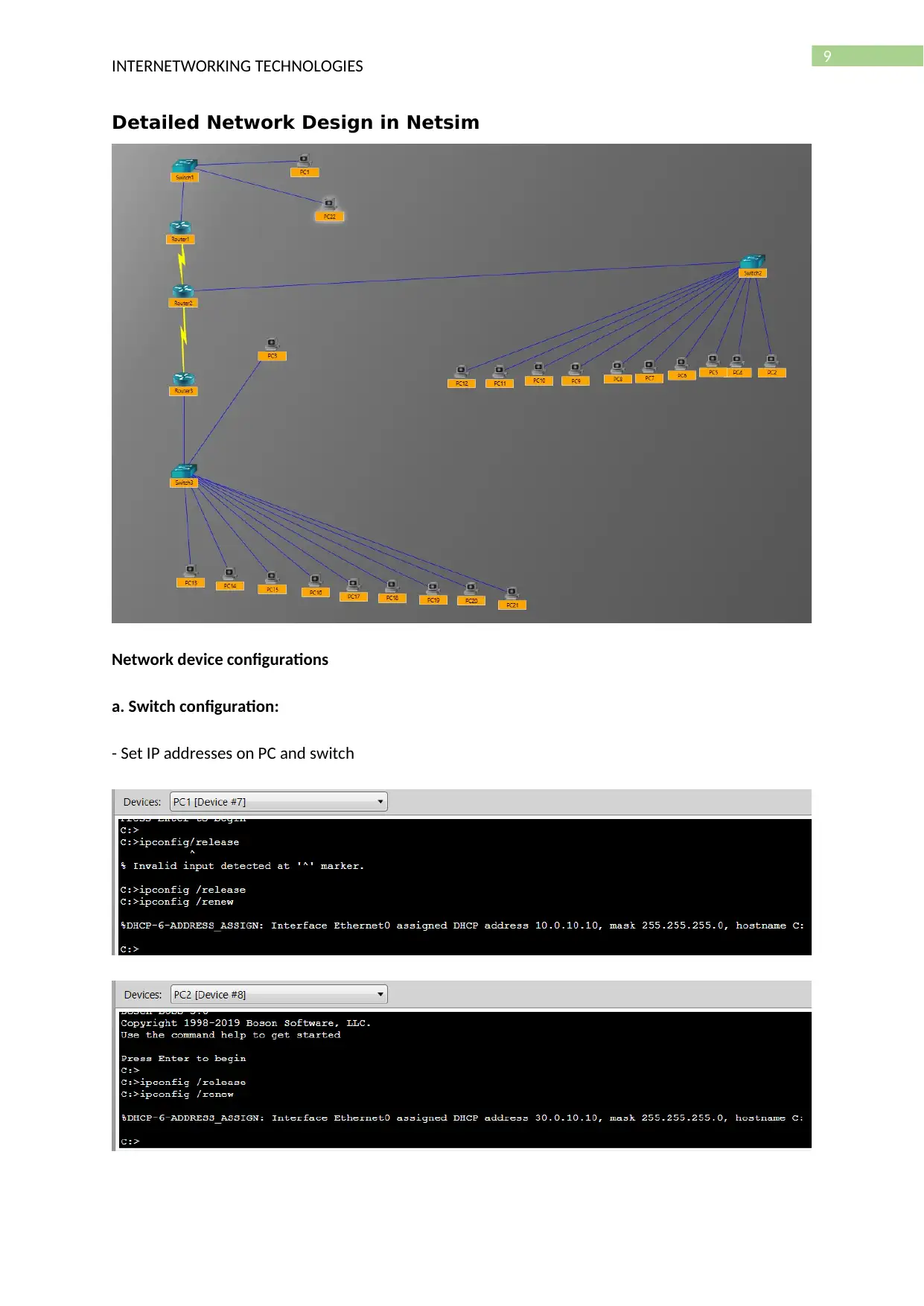
Detailed Network Design in Netsim
Network device configurations
a. Switch configuration:
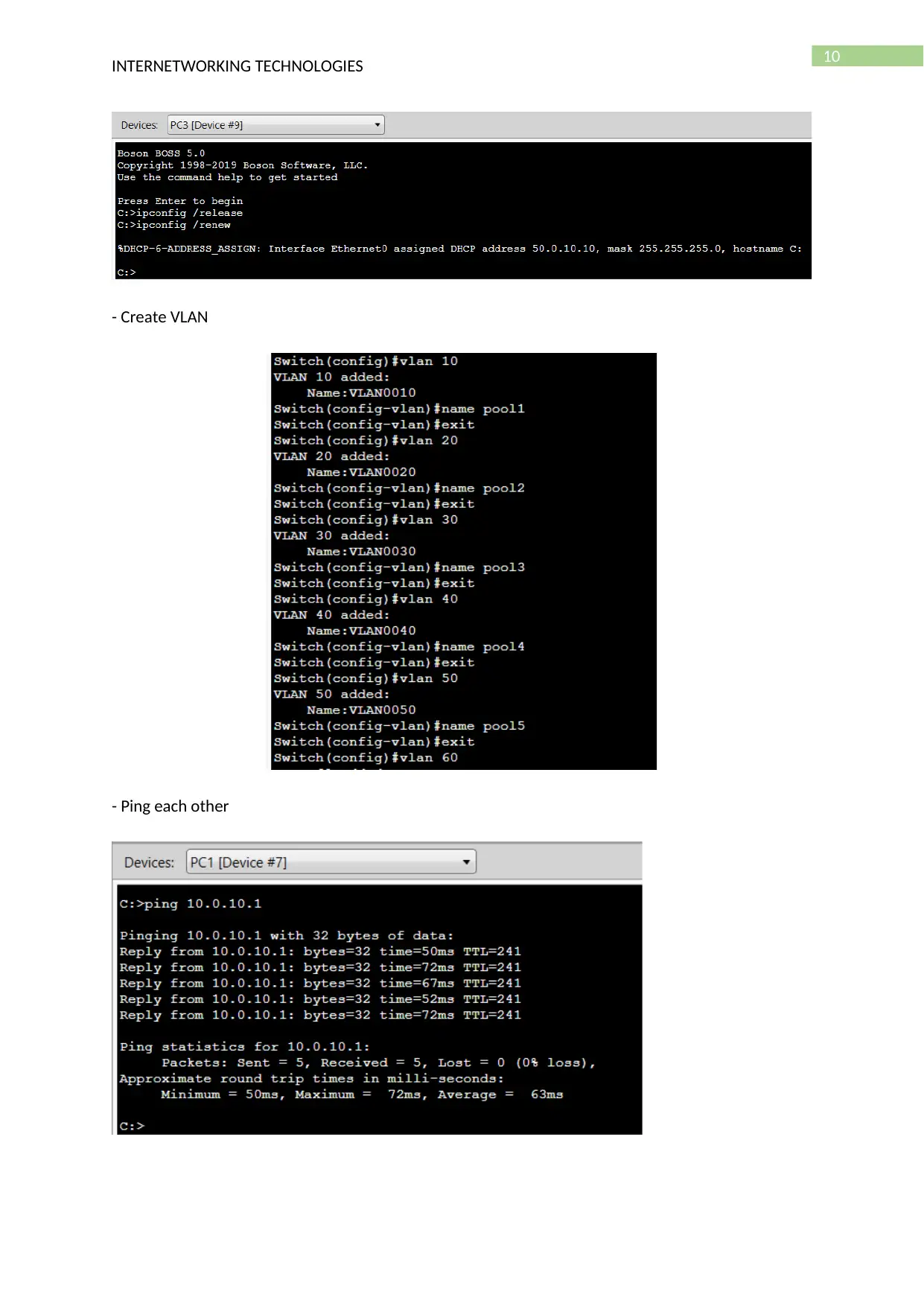
- Set IP addresses on PC and switch
INTERNETWORKING TECHNOLOGIES
Detailed Network Design in Netsim
Network device configurations
a. Switch configuration:
- Set IP addresses on PC and switch
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
INTERNETWORKING TECHNOLOGIES
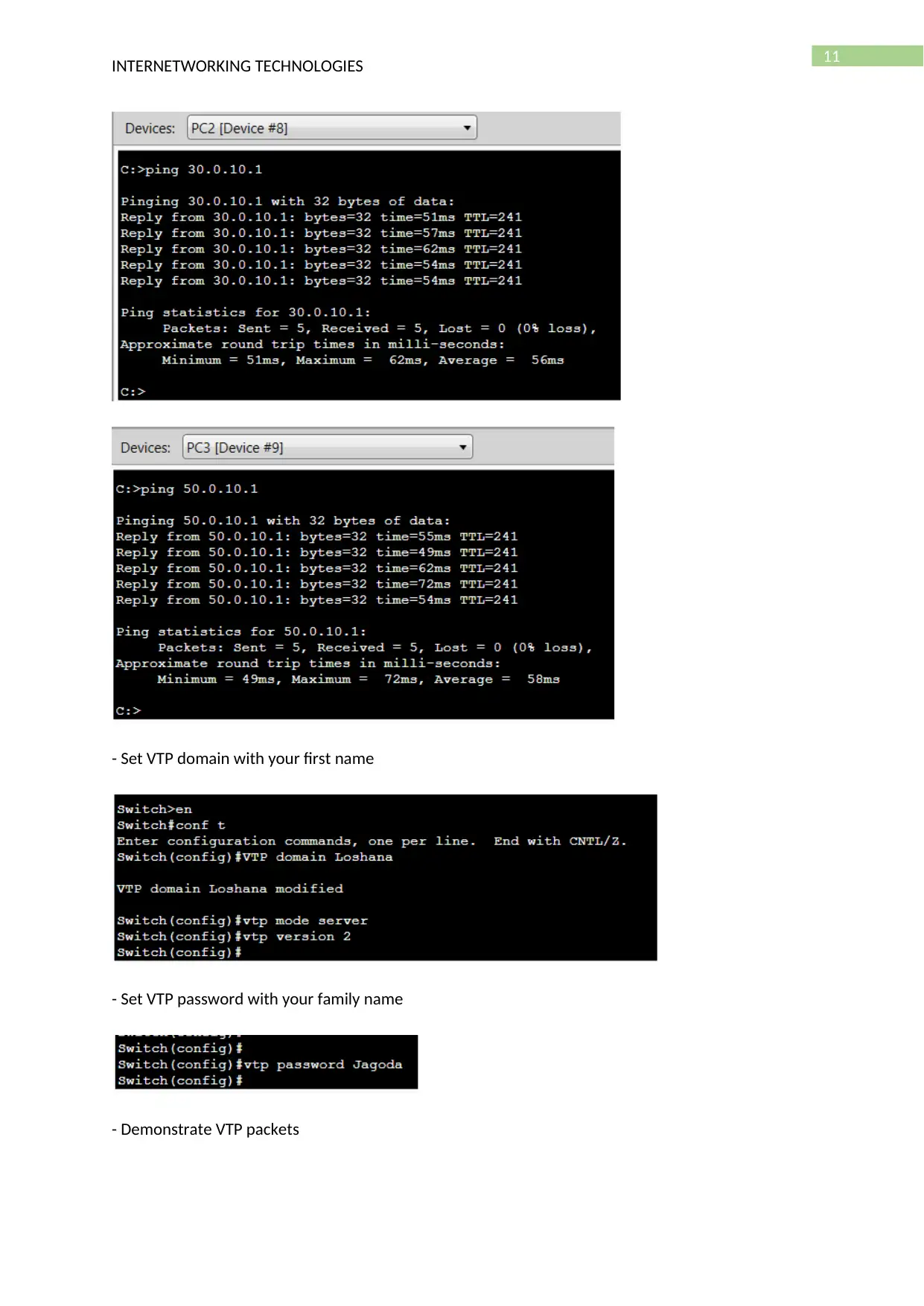
- Create VLAN
- Ping each other
INTERNETWORKING TECHNOLOGIES
- Create VLAN
- Ping each other
11
INTERNETWORKING TECHNOLOGIES
- Set VTP domain with your first name
- Set VTP password with your family name
- Demonstrate VTP packets
INTERNETWORKING TECHNOLOGIES
- Set VTP domain with your first name
- Set VTP password with your family name
- Demonstrate VTP packets
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



