Network Security BN203: Identifying Network Threats using Tools
VerifiedAdded on 2023/06/11
|8
|1877
|404
Report
AI Summary
This report explores network security threats and mitigation techniques using Nmap and Metasploit. It details the use of these open-source tools for analyzing network vulnerabilities within a local area network. The report covers the identification of open ports, potential intrusion methods, and payload analysis. It also discusses various threat mitigation techniques, including firewall configuration, network segregation, web application security, privilege management, and patch management. The report concludes that Nmap and Metasploit are effective tools for identifying network vulnerabilities and can be used in combination for comprehensive network exploitation analysis. Desklib provides access to similar reports and study resources for students.

Running head: NETWORK SECURITY 1
Identifying Network Threats using Network Security Tools
Name of the Student
Name of the University
Author’s Note
Identifying Network Threats using Network Security Tools
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY 1
Table of Contents
Introduction...........................................................................................................................................2
Literature Review..................................................................................................................................2
Network Security Tools..........................................................................................................................4
Threat Mitigation Techniques................................................................................................................5
Conclusion.............................................................................................................................................5
Bibliography...........................................................................................................................................7
NETWORK SECURITY 1
Table of Contents
Introduction...........................................................................................................................................2
Literature Review..................................................................................................................................2
Network Security Tools..........................................................................................................................4
Threat Mitigation Techniques................................................................................................................5
Conclusion.............................................................................................................................................5
Bibliography...........................................................................................................................................7
2
NETWORK SECURITY 1
Introduction
The report is prepared for using two network security tools for the analysis of the new
security threats acting on the network and identification of the technique used for addressing the
threat. Two open source network monitoring tool i.e. Nmap and Metasploit is used for the analysis
of the vulnerability of the local area network of our institute. The tools are available in kali Linux and
it is installed in a virtual machine for exploitation of the current network. The Nmap is used for
scanning the network and the threats identified are discussed in the report. The metasploit is used
for the identification of the payload on the network and it is combined with Nmap for gathering
information from the network.
Literature Review
NETWORK SECURITY 1
Introduction
The report is prepared for using two network security tools for the analysis of the new
security threats acting on the network and identification of the technique used for addressing the
threat. Two open source network monitoring tool i.e. Nmap and Metasploit is used for the analysis
of the vulnerability of the local area network of our institute. The tools are available in kali Linux and
it is installed in a virtual machine for exploitation of the current network. The Nmap is used for
scanning the network and the threats identified are discussed in the report. The metasploit is used
for the identification of the payload on the network and it is combined with Nmap for gathering
information from the network.
Literature Review
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK SECURITY 1
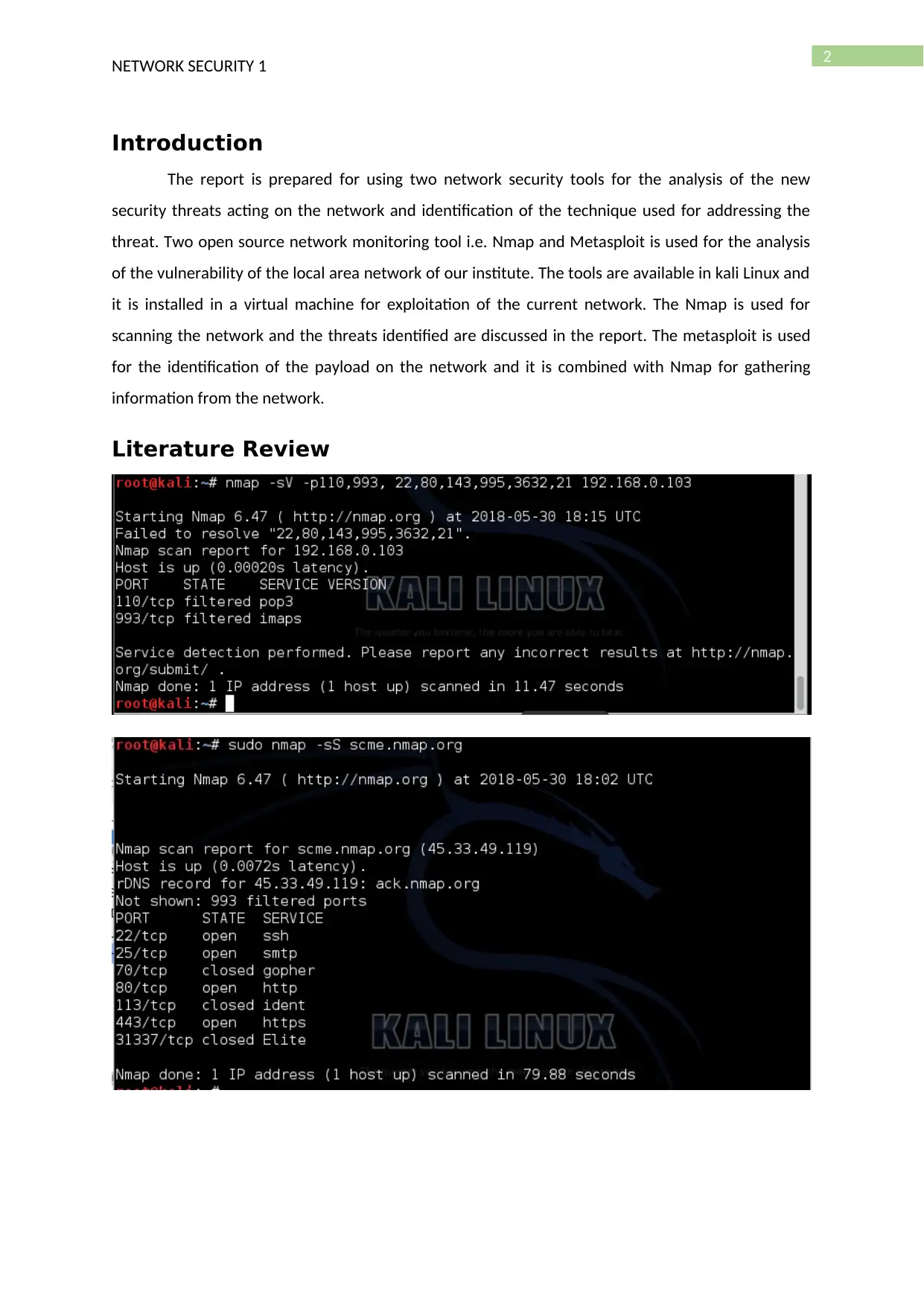
The nmap is used for finding the ports in a system that are open and used for intruding into
the system using the open port for testing the vulnerability of the system. The ports can also be used
for sending asynchronous packet and causing denial of service attack.
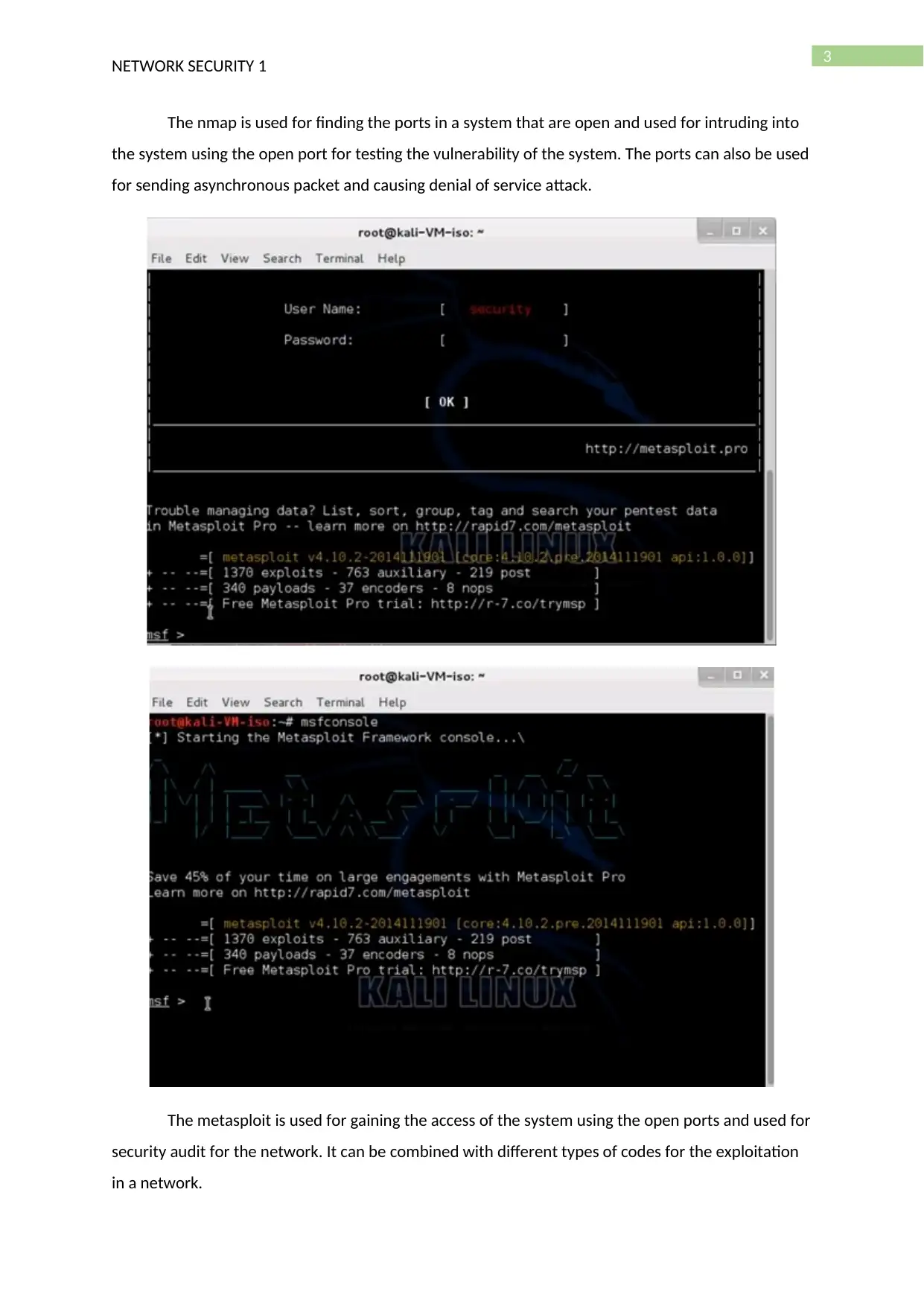
The metasploit is used for gaining the access of the system using the open ports and used for
security audit for the network. It can be combined with different types of codes for the exploitation
in a network.
NETWORK SECURITY 1
The nmap is used for finding the ports in a system that are open and used for intruding into
the system using the open port for testing the vulnerability of the system. The ports can also be used
for sending asynchronous packet and causing denial of service attack.
The metasploit is used for gaining the access of the system using the open ports and used for
security audit for the network. It can be combined with different types of codes for the exploitation
in a network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK SECURITY 1
Network engineers are mainly required for anticipation of various kinds of attacks and
overcoming them. There are many kinds of methods which can be used for overcoming the given
attacks like Denial of service (DoS) or Distributed Denial of Service Attack (DDoS), social engineering
and malware. Dos attack is mainly considered to be much easiest to be understanding. A successful
kind of DoS attack can easily take place when the ability of the device for performing is prevented.
Methods which can cause various kinds of condition range which begins from sending of large
number of traffic at the given device to triggering of device which can be easily used for buffering.
Any kind of triggering in the device can be used for entering the error. A simple kind of DDoS can be
easily performed by the help of error condition. A simple kind of DDoS attack can be easily
performed by the help of third party network which focus on the availability of a given network into
another kind of network capacity into another kind of network device with less kind of capacity. The
target can be easily seen when the various kinds of attack can be easily originated and certain
number of action taken into account. One of the common kind of attack is social engineering. This
particular kind of attack require a certain level of skill which is considered to be of much exceptional
value. Social engineering does not need any kind of technology. It mainly takes up the advantage of
social methods which can be easily used for extraction of any kind of information. Malware is
considered to be short form of malicious software. Malware is mainly inclusive of modern kind of
attacks. This is mainly inclusive of certain number of methods like viruses, worm, spyware, Trojan
and adware. It mainly differs in operation when it is combined with various kinds of operation.
Network Security Tools
Nmap is considered to be a free and open source kind of source which is mainly used for
discovering and auditing of security. Many kinds of system and network administrator also finds it
useful for dealing with large number of problems like inventory of network, proper management of
service upgrade schedules a monitoring of host or service uptime. Nmap makes use raw kind of IP
packets in proper kind of novel which is mainly used for determination of various kinds of host which
are available on the network. It is also used for analysing the kind of service available with host
offering and kind of operating system which is running. It was mainly designed for analysing the fact
for scanning various kinds of networks and proper kind of work fine should be available for it.
Nmap is mainly used for large number of platforms like Linux, Mac OS and windows. Apart
from the classic kind of available command it is mainly inclusive of advanced kind of GUI and result
of viewer. It comes up with proper kind of flexible data transfer technique and tools for debugging. It
comes up with various kinds of tools for comparing the available kind of scan results. A packet kind
of generation and tool for responsive analysis.
NETWORK SECURITY 1
Network engineers are mainly required for anticipation of various kinds of attacks and
overcoming them. There are many kinds of methods which can be used for overcoming the given
attacks like Denial of service (DoS) or Distributed Denial of Service Attack (DDoS), social engineering
and malware. Dos attack is mainly considered to be much easiest to be understanding. A successful
kind of DoS attack can easily take place when the ability of the device for performing is prevented.
Methods which can cause various kinds of condition range which begins from sending of large
number of traffic at the given device to triggering of device which can be easily used for buffering.
Any kind of triggering in the device can be used for entering the error. A simple kind of DDoS can be
easily performed by the help of error condition. A simple kind of DDoS attack can be easily
performed by the help of third party network which focus on the availability of a given network into
another kind of network capacity into another kind of network device with less kind of capacity. The
target can be easily seen when the various kinds of attack can be easily originated and certain
number of action taken into account. One of the common kind of attack is social engineering. This
particular kind of attack require a certain level of skill which is considered to be of much exceptional
value. Social engineering does not need any kind of technology. It mainly takes up the advantage of
social methods which can be easily used for extraction of any kind of information. Malware is
considered to be short form of malicious software. Malware is mainly inclusive of modern kind of
attacks. This is mainly inclusive of certain number of methods like viruses, worm, spyware, Trojan
and adware. It mainly differs in operation when it is combined with various kinds of operation.
Network Security Tools
Nmap is considered to be a free and open source kind of source which is mainly used for
discovering and auditing of security. Many kinds of system and network administrator also finds it
useful for dealing with large number of problems like inventory of network, proper management of
service upgrade schedules a monitoring of host or service uptime. Nmap makes use raw kind of IP
packets in proper kind of novel which is mainly used for determination of various kinds of host which
are available on the network. It is also used for analysing the kind of service available with host
offering and kind of operating system which is running. It was mainly designed for analysing the fact
for scanning various kinds of networks and proper kind of work fine should be available for it.
Nmap is mainly used for large number of platforms like Linux, Mac OS and windows. Apart
from the classic kind of available command it is mainly inclusive of advanced kind of GUI and result
of viewer. It comes up with proper kind of flexible data transfer technique and tools for debugging. It
comes up with various kinds of tools for comparing the available kind of scan results. A packet kind
of generation and tool for responsive analysis.

5
NETWORK SECURITY 1
Metaspoilt is a well-known penetration test that is mainly performed for analysing various
kinds of vulnerabilities in a given network. It generally provides the infrastructure, content and
various kinds of tool for performing various kinds of test in network. It can be stated like an
extensive kind of security auditing. It comes up with new kinds of security model that is mainly used
for new kinds of model and content team which is mainly added on regular basis. Metasploit is a
famous in the domain of security world soon after it was released in the year of 2004. It is mainly
defined as a proper kind of advanced tool platform that is mainly used for developing, testing and
exploitation of code. It is mainly defined as a well-known model which is mainly used for payloads,
encoders and exploitation which can be easily integrated as much as possible which can be easily
used metasploit framework which is nothing but an outlet that can be easily used for cut edge for
various kinds of exploitation of various kinds of research.
Threat Mitigation Techniques
A large number of steps can be taken for overcoming various kinds of issues in a network like
Configuration of firewall
Segregation of network
Web application
Be careful about the privilege of network.
Patch management
Configuration of firewall: It is very important for proper management of configuration of
firewall. It mainly ensures the fact that various kinds of configuration must be there in active nature.
Network configuration: Along with checking of various kinds of firewalls it is very essential
for analysing the segregation of things which are working in an effective way in all the network and
ingress point.
Web vulnerabilities: Weakness and issues in various kinds of web application are considered
to be main kind of attack vendor by the help of vectors by which the organization is compromised.
Patch management: One of the best that is taken into consideration of security of various
kinds of system and services are patched as per the requirement.
Conclusion
From the above report it can be concluded that using the Nmap and the Metasploit helps in
identification of the current vulnerability of the network and the both of them can be used as a good
combination for the exploitation of the network. The metasploit can be used for evading the
NETWORK SECURITY 1
Metaspoilt is a well-known penetration test that is mainly performed for analysing various
kinds of vulnerabilities in a given network. It generally provides the infrastructure, content and
various kinds of tool for performing various kinds of test in network. It can be stated like an
extensive kind of security auditing. It comes up with new kinds of security model that is mainly used
for new kinds of model and content team which is mainly added on regular basis. Metasploit is a
famous in the domain of security world soon after it was released in the year of 2004. It is mainly
defined as a proper kind of advanced tool platform that is mainly used for developing, testing and
exploitation of code. It is mainly defined as a well-known model which is mainly used for payloads,
encoders and exploitation which can be easily integrated as much as possible which can be easily
used metasploit framework which is nothing but an outlet that can be easily used for cut edge for
various kinds of exploitation of various kinds of research.
Threat Mitigation Techniques
A large number of steps can be taken for overcoming various kinds of issues in a network like
Configuration of firewall
Segregation of network
Web application
Be careful about the privilege of network.
Patch management
Configuration of firewall: It is very important for proper management of configuration of
firewall. It mainly ensures the fact that various kinds of configuration must be there in active nature.
Network configuration: Along with checking of various kinds of firewalls it is very essential
for analysing the segregation of things which are working in an effective way in all the network and
ingress point.
Web vulnerabilities: Weakness and issues in various kinds of web application are considered
to be main kind of attack vendor by the help of vectors by which the organization is compromised.
Patch management: One of the best that is taken into consideration of security of various
kinds of system and services are patched as per the requirement.
Conclusion
From the above report it can be concluded that using the Nmap and the Metasploit helps in
identification of the current vulnerability of the network and the both of them can be used as a good
combination for the exploitation of the network. The metasploit can be used for evading the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK SECURITY 1
antivirus solution installed in the targeted machine and offers advanced penetration testing features
for the exploitation of the vulnerability in the current network. The nmap is used for scanning the
network utilizing raw IP packet and it can easily gather different information from the network such
as the version of the operating system, available hosts connected in the network and existence of
the firewall, etc. that are essential for performing the penetration testing.
NETWORK SECURITY 1
antivirus solution installed in the targeted machine and offers advanced penetration testing features
for the exploitation of the vulnerability in the current network. The nmap is used for scanning the
network utilizing raw IP packet and it can easily gather different information from the network such
as the version of the operating system, available hosts connected in the network and existence of
the firewall, etc. that are essential for performing the penetration testing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK SECURITY 1
Bibliography
[1]. Armstrong, M.E., Jones, K.S., Namin, A.S. and Newton, D.C. What Vulnerability Assessment
and Management Cybersecurity Professionals Think Their Future Colleagues Need to Know.
In Proceedings of the 49th ACM Technical Symposium on Computer Science Education (pp.
1082-1082). ACM., 2018, February.
[2]. Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I. Live Lesson: Netsim: Network
simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in
Security Education ({ASE} 17). USENIX} Association}., 2017 August.
[3]. Cuppens, F. WirelessHART NetSIM: A WirelessHART SCADA-Based Wireless Sensor Networks
Simulator. In Security of Industrial Control Systems and Cyber Physical Systems: First
Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September
21–22, 2015 Revised Selected Papers (Vol. 9588, p. 63). Springer., 2016, June.
[4]. Holik, F., Horalek, J., Marik, O., Neradova, S. and Zitta, S. Effective penetration testing with
Metasploit framework and methodologies. In Computational Intelligence and Informatics
(CINTI), 2014 IEEE 15th International Symposium on (pp. 237-242). IEEE., 2014, November.
[5]. Johansen, G., Allen, L., Heriyanto, T. and Ali, S. Kali Linux 2–Assuring Security by Penetration
Testing. Packt Publishing Ltd., 2016.
[6]. Nayak, P. and Sinha, P. Analysis of Random Way Point and Random Walk Mobility Model for
Reactive Routing Protocols for MANET Using NetSim Simulator. In Artificial Intelligence,
Modelling and Simulation (AIMS), 2015 3rd International Conference on (pp. 427-432). IEEE.,
2015 December.
[7]. Peng, J., Li, H., Wang, Y. and Chen, J. A web tool for measuring gene semantic similarities by
combining Gene Ontology and gene co-function networks. In Proceedings of the 6th ACM
Conference on Bioinformatics, Computational Biology and Health Informatics (pp. 678-679).
ACM., 2015 September.
[8]. Saifuddin, K.M., Ahmed, A.S., Reza, K.F., Alam, S.S. and Rahman, S. Performance analysis of
cognitive radio: Netsim viewpoint. In Electrical Information and Communication Technology
(EICT), 2017 3rd International Conference on (pp. 1-6). IEEE., 2017 December.
[9]. Singh, G., Cheema, A.K. and Kapoor, N. Performance Evaluation of Routing Protocol in
Internet of Things using Netsim. International Journal, 8(3)., 2017.
[10]. Weidman, G. Penetration testing: a hands-on introduction to hacking. No Starch
Press., 2014.
NETWORK SECURITY 1
Bibliography
[1]. Armstrong, M.E., Jones, K.S., Namin, A.S. and Newton, D.C. What Vulnerability Assessment
and Management Cybersecurity Professionals Think Their Future Colleagues Need to Know.
In Proceedings of the 49th ACM Technical Symposium on Computer Science Education (pp.
1082-1082). ACM., 2018, February.
[2]. Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I. Live Lesson: Netsim: Network
simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in
Security Education ({ASE} 17). USENIX} Association}., 2017 August.
[3]. Cuppens, F. WirelessHART NetSIM: A WirelessHART SCADA-Based Wireless Sensor Networks
Simulator. In Security of Industrial Control Systems and Cyber Physical Systems: First
Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September
21–22, 2015 Revised Selected Papers (Vol. 9588, p. 63). Springer., 2016, June.
[4]. Holik, F., Horalek, J., Marik, O., Neradova, S. and Zitta, S. Effective penetration testing with
Metasploit framework and methodologies. In Computational Intelligence and Informatics
(CINTI), 2014 IEEE 15th International Symposium on (pp. 237-242). IEEE., 2014, November.
[5]. Johansen, G., Allen, L., Heriyanto, T. and Ali, S. Kali Linux 2–Assuring Security by Penetration
Testing. Packt Publishing Ltd., 2016.
[6]. Nayak, P. and Sinha, P. Analysis of Random Way Point and Random Walk Mobility Model for
Reactive Routing Protocols for MANET Using NetSim Simulator. In Artificial Intelligence,
Modelling and Simulation (AIMS), 2015 3rd International Conference on (pp. 427-432). IEEE.,
2015 December.
[7]. Peng, J., Li, H., Wang, Y. and Chen, J. A web tool for measuring gene semantic similarities by
combining Gene Ontology and gene co-function networks. In Proceedings of the 6th ACM
Conference on Bioinformatics, Computational Biology and Health Informatics (pp. 678-679).
ACM., 2015 September.
[8]. Saifuddin, K.M., Ahmed, A.S., Reza, K.F., Alam, S.S. and Rahman, S. Performance analysis of
cognitive radio: Netsim viewpoint. In Electrical Information and Communication Technology
(EICT), 2017 3rd International Conference on (pp. 1-6). IEEE., 2017 December.
[9]. Singh, G., Cheema, A.K. and Kapoor, N. Performance Evaluation of Routing Protocol in
Internet of Things using Netsim. International Journal, 8(3)., 2017.
[10]. Weidman, G. Penetration testing: a hands-on introduction to hacking. No Starch
Press., 2014.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




