BN208 - Network Application: Hypervisor and Container Virtualization
VerifiedAdded on 2023/06/07
|14
|2963
|133
Report
AI Summary
This report provides a detailed overview of hypervisor-based server virtualization technology, data centers, and container-based virtualization, exploring their descriptions, purposes, working models, scalability issues, features, weaknesses, and social-technical aspects. Hypervisor virtualization is discussed in terms of creating and running virtual machines, enhancing hardware efficiency, and providing security. Data centers are examined for their role in data backup, compliance, configuration management, and remediation. Container-based virtualization, also known as operating system virtualization, is analyzed for its application in providing secure environments for applications and efficient resource allocation. The report concludes by highlighting the scalability and adaptability of these technologies, while also acknowledging their limitations and the importance of considering social-technical factors in their implementation. This document is ideal for students seeking to understand the nuances of network application technologies and their impact on modern IT infrastructure. Desklib provides access to similar solved assignments and study tools to aid students in their academic endeavors.

NETWORK APPLICATION
Name
Course Code:
Date of Submission
Name
Course Code:
Date of Submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
Hypervisor-Based Server Virtualization Technology..................................................................................3
Description..............................................................................................................................................3
Purpose of the application.......................................................................................................................3
Working model........................................................................................................................................4
Scalability issues.....................................................................................................................................4
Features and weakness.............................................................................................................................4
Social technical aspects...........................................................................................................................5
Data centers.................................................................................................................................................6
Purpose of application.............................................................................................................................6
Working model........................................................................................................................................7
Scalability issues.....................................................................................................................................9
Features and Weakness..........................................................................................................................10
Social technical Aspects........................................................................................................................10
Container-based virtualization...................................................................................................................11
Purpose of the application.....................................................................................................................11
Working model......................................................................................................................................11
Scalability issues...................................................................................................................................12
Features and Weakness of the application.............................................................................................12
Social technical aspects.........................................................................................................................12
Conclusion.................................................................................................................................................12
References.................................................................................................................................................13
Introduction.................................................................................................................................................3
Hypervisor-Based Server Virtualization Technology..................................................................................3
Description..............................................................................................................................................3
Purpose of the application.......................................................................................................................3
Working model........................................................................................................................................4
Scalability issues.....................................................................................................................................4
Features and weakness.............................................................................................................................4
Social technical aspects...........................................................................................................................5
Data centers.................................................................................................................................................6
Purpose of application.............................................................................................................................6
Working model........................................................................................................................................7
Scalability issues.....................................................................................................................................9
Features and Weakness..........................................................................................................................10
Social technical Aspects........................................................................................................................10
Container-based virtualization...................................................................................................................11
Purpose of the application.....................................................................................................................11
Working model......................................................................................................................................11
Scalability issues...................................................................................................................................12
Features and Weakness of the application.............................................................................................12
Social technical aspects.........................................................................................................................12
Conclusion.................................................................................................................................................12
References.................................................................................................................................................13
Introduction
Hypervisor virtualization technology is described as computer applications that create a virtual
machine and runs it. It is a technology that is commonly used and it has enabled more than one
operating system to run on one physical platform. On the other hand, data centers can be
described as a facility within an organization that is central, located to carry out IT activities
within an organization. These activities may include storage, retrieval and processing of data.
Data centers are important to an organization since they promote communication through
enhancing data exchange. These technologies have increased communication and business
operations in many enterprises. This report describes their characteristics, scalability and their
weakness in general.
Hypervisor-Based Server Virtualization Technology
Description
This is a technology that explains how computers create virtual machines and run them.
Operating system designers face serious problems while isolating software and allowing sharing
of applications between them [1]. This shows that each application has different layouts but
share some objects. Hypervisor strives to provide full separation between virtual machines by
providing support in sharing of resources in computers. The technology has made single
machines to host multiple software that are unrelated which run independent of the organization.
The applications do not need to actually share data, they run on the same kernel as a single
operating system. Currently, one can have different types of operating system installed in his
machine and use them without facing any problems.
Purpose of the application
There are many ideas that enhance the use of hypervisor virtualization technology. They include
[2].
The technology is used in securing work environment in laptops.
It enhances efficient use of hardware components by reducing usage of hardware
systems. This lowers maintenance costs and power usage in any organization.
Detection of malicious attacks in the real time.
Hypervisor virtualization technology is described as computer applications that create a virtual
machine and runs it. It is a technology that is commonly used and it has enabled more than one
operating system to run on one physical platform. On the other hand, data centers can be
described as a facility within an organization that is central, located to carry out IT activities
within an organization. These activities may include storage, retrieval and processing of data.
Data centers are important to an organization since they promote communication through
enhancing data exchange. These technologies have increased communication and business
operations in many enterprises. This report describes their characteristics, scalability and their
weakness in general.
Hypervisor-Based Server Virtualization Technology
Description
This is a technology that explains how computers create virtual machines and run them.
Operating system designers face serious problems while isolating software and allowing sharing
of applications between them [1]. This shows that each application has different layouts but
share some objects. Hypervisor strives to provide full separation between virtual machines by
providing support in sharing of resources in computers. The technology has made single
machines to host multiple software that are unrelated which run independent of the organization.
The applications do not need to actually share data, they run on the same kernel as a single
operating system. Currently, one can have different types of operating system installed in his
machine and use them without facing any problems.
Purpose of the application
There are many ideas that enhance the use of hypervisor virtualization technology. They include
[2].
The technology is used in securing work environment in laptops.
It enhances efficient use of hardware components by reducing usage of hardware
systems. This lowers maintenance costs and power usage in any organization.
Detection of malicious attacks in the real time.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

It increases availability especially on the server side by providing features that are not
found on the server.
Used in disaster recovery like data back up in case there is any loss.
Debugging failing systems.
The technology is also used by programmers in development of software and testing
them.
IT centers use the technology in merging servers onto effective hardware.
Virtual technology is used in selling private servers to companies.
It creates space in server rooms or data centers.
Working model
If the server needs to execute a hypervisor, it loads the technology into a client operating system
of the VM. Then the technology provides correct CPU resource to memory bandwidth for the
machine. A VM can create requests to the hypervisor using many ways including API calls.
There two kinds of this technology:
i. Embedded or hosted hypervisors - They run as software using operating systems such as
windows
ii. Bare metal or native hypervisors - this occurs when hypervisors run on hosts hardware
components to manage the VM.
Comparison between embedded and native hypervisors
Native run directly on the server while embedded run on operating systems
Scalability issues
It was difficulty to replicate hypervisors before. Currently they are highly scalable and flexible.
This means that they can be changed and moved if it is required. For this to occur, one needs to
know about methods that are used in data replication. Volume in machines must be replicated to
enable the technology to run more efficiently.
Features and weakness
The technology has following features and weakness [3].
Features
It can be easily installed
Easy to use
found on the server.
Used in disaster recovery like data back up in case there is any loss.
Debugging failing systems.
The technology is also used by programmers in development of software and testing
them.
IT centers use the technology in merging servers onto effective hardware.
Virtual technology is used in selling private servers to companies.
It creates space in server rooms or data centers.
Working model
If the server needs to execute a hypervisor, it loads the technology into a client operating system
of the VM. Then the technology provides correct CPU resource to memory bandwidth for the
machine. A VM can create requests to the hypervisor using many ways including API calls.
There two kinds of this technology:
i. Embedded or hosted hypervisors - They run as software using operating systems such as
windows
ii. Bare metal or native hypervisors - this occurs when hypervisors run on hosts hardware
components to manage the VM.
Comparison between embedded and native hypervisors
Native run directly on the server while embedded run on operating systems
Scalability issues
It was difficulty to replicate hypervisors before. Currently they are highly scalable and flexible.
This means that they can be changed and moved if it is required. For this to occur, one needs to
know about methods that are used in data replication. Volume in machines must be replicated to
enable the technology to run more efficiently.
Features and weakness
The technology has following features and weakness [3].
Features
It can be easily installed
Easy to use
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Weakness
Extra costs are involved - installation of the technology requires additional hardware and
software thus increasing the cost.
Software licensing - the software that is used with this technology requires license which
increases the cost of setting up and using the technology.
Its installation and usage require skilled personnel on the technology. This creates extra
labor.
Social technical aspects
Technical aspects of the network is that it provides high data security especially when it is used
on the server side. It works with high scalability and flexibility.
Extra costs are involved - installation of the technology requires additional hardware and
software thus increasing the cost.
Software licensing - the software that is used with this technology requires license which
increases the cost of setting up and using the technology.
Its installation and usage require skilled personnel on the technology. This creates extra
labor.
Social technical aspects
Technical aspects of the network is that it provides high data security especially when it is used
on the server side. It works with high scalability and flexibility.

Data centers
The growing need of organizations to store and retrieve data for future use has led to
development and establishment of data centers. Today data centers contain thousands of
computers with appropriate and significant bandwidth requirements. Different organizations will
have different layouts of their data centers depending on their requirements and the type of data
that is required to be stored for future use [4]. Well-designed data centers meet the following
requirements:
Scalable bandwidth - for faster communication between two hosts that are found within
the network.
Economics of scale - the cost of installation must be very low.
Backward compatibility - the system should be backwardly compatible with the hosts
and other resources in the network.
Purpose of application
Data centers have the following functions in any network [5].
Backup of data - it backups data automatically on the server.
Compliance - it defines the normal roles of the organization.
It determines the software that is running in the network.
Configuration - it is used for changing management of devices that are being used in the
network.
Remediation - it identifies and fixes issues in the network.
It provides consistency in the network
It is used in patching where by it automatically downloads and installs any updates that
are available in the system.
It’s used in application management and printer management.
It’s used as a service desk where by users can request for some details and wait for
provisioning.
The growing need of organizations to store and retrieve data for future use has led to
development and establishment of data centers. Today data centers contain thousands of
computers with appropriate and significant bandwidth requirements. Different organizations will
have different layouts of their data centers depending on their requirements and the type of data
that is required to be stored for future use [4]. Well-designed data centers meet the following
requirements:
Scalable bandwidth - for faster communication between two hosts that are found within
the network.
Economics of scale - the cost of installation must be very low.
Backward compatibility - the system should be backwardly compatible with the hosts
and other resources in the network.
Purpose of application
Data centers have the following functions in any network [5].
Backup of data - it backups data automatically on the server.
Compliance - it defines the normal roles of the organization.
It determines the software that is running in the network.
Configuration - it is used for changing management of devices that are being used in the
network.
Remediation - it identifies and fixes issues in the network.
It provides consistency in the network
It is used in patching where by it automatically downloads and installs any updates that
are available in the system.
It’s used in application management and printer management.
It’s used as a service desk where by users can request for some details and wait for
provisioning.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
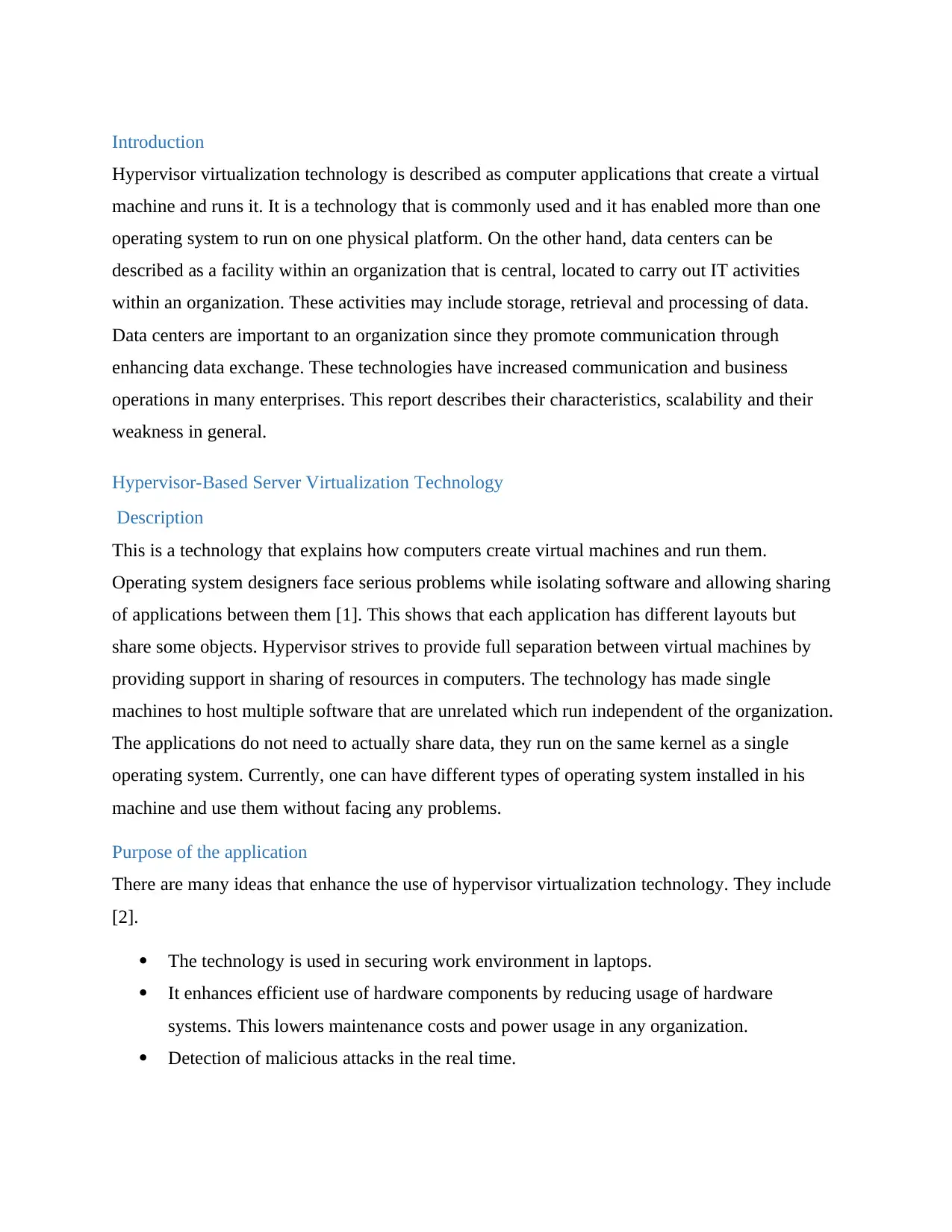
Working model
A data center is made up of power, storage and applications that are required to support an
organization. The data center’s infrastructure is at the center of the IT from which all the content
is passed through. A good model of data center is highly planned and scalable. It has high
performance.
The figure below shows a structure of a working model of data center that is linked to the cloud
for data backup. This design is called basic layer design
Figure 1. Basic layer design of a data center as illustrated in [11, fig 1]
A data center should be highly flexible to deploy and support new features. This is because
flexible data centers have ability to support new application features. We have different design
models of data centers as explained below.
A data center is made up of power, storage and applications that are required to support an
organization. The data center’s infrastructure is at the center of the IT from which all the content
is passed through. A good model of data center is highly planned and scalable. It has high
performance.
The figure below shows a structure of a working model of data center that is linked to the cloud
for data backup. This design is called basic layer design
Figure 1. Basic layer design of a data center as illustrated in [11, fig 1]
A data center should be highly flexible to deploy and support new features. This is because
flexible data centers have ability to support new application features. We have different design
models of data centers as explained below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
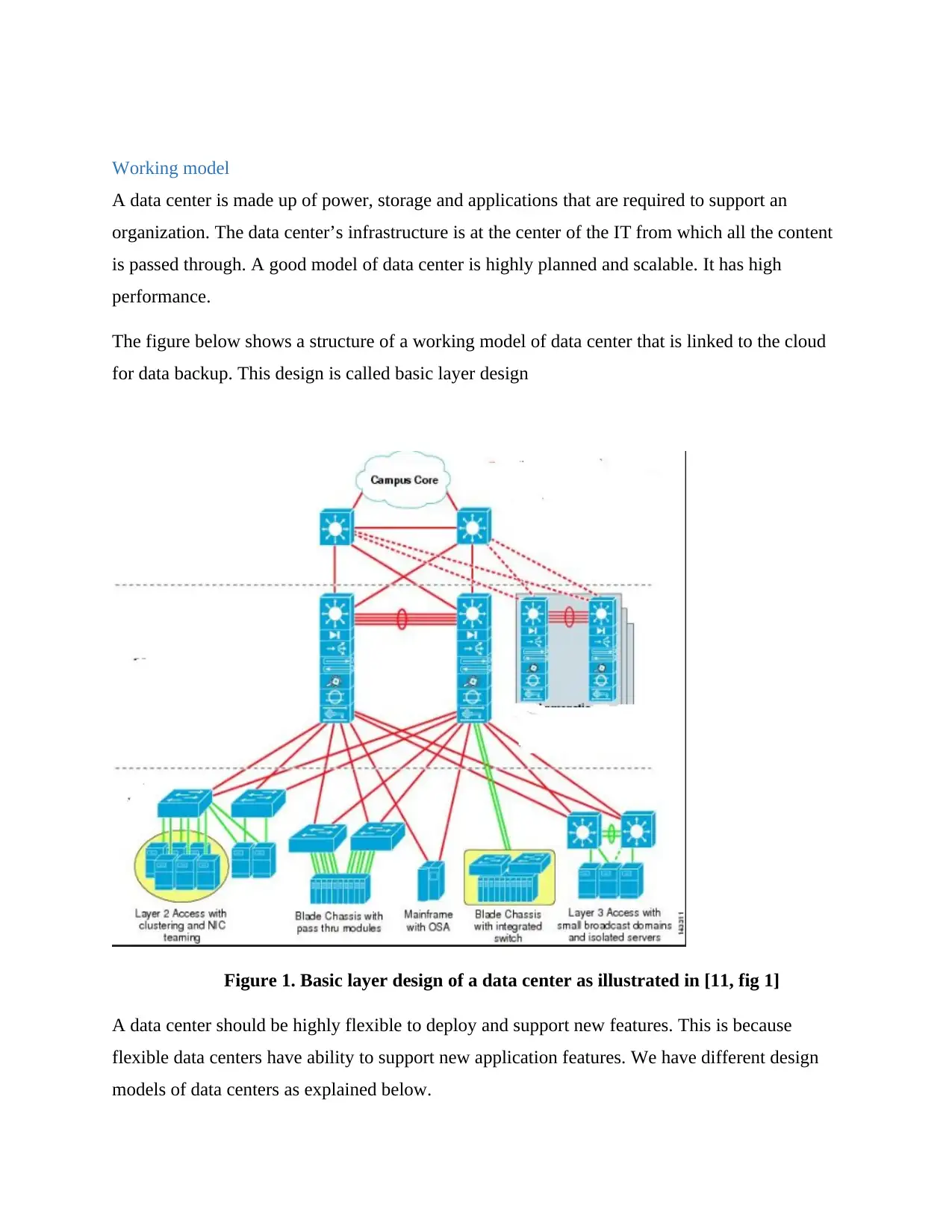
Multi-Tier Model
This is the common model of data center mainly used in Http–based applications. The model
includes web, applications and database tiers of servers. It uses a software that runs as a different
process on a machine using interposes communication when the process are build such that they
run from different machines. It promotes security and resilience of the data centers. The
security of the data centers is increased because an attacker can access a web server without
breaking into application and database servers [6]. Loading of a balance network traffic promotes
resilience between the tiers. Firewalls are placed between the tiers to provide security in the data
center. The following diagram shows a multi-tier model of a data center.
Fig 2. Multi-tier model of a data center as illustrated in [11, fig 2]
This is the common model of data center mainly used in Http–based applications. The model
includes web, applications and database tiers of servers. It uses a software that runs as a different
process on a machine using interposes communication when the process are build such that they
run from different machines. It promotes security and resilience of the data centers. The
security of the data centers is increased because an attacker can access a web server without
breaking into application and database servers [6]. Loading of a balance network traffic promotes
resilience between the tiers. Firewalls are placed between the tiers to provide security in the data
center. The following diagram shows a multi-tier model of a data center.
Fig 2. Multi-tier model of a data center as illustrated in [11, fig 2]
Server Cluster Model
These data centers are used for many purposes because they are highly available and have
increased power. This model enhances high performance of clusters which have many forms.
Clusters have common goals of combining multiple CPUS together. This promotes high speed of
the network. This kind of data models is mostly used in universities and in military research for
unique applications. This kind of data center is also used in weather stations and in seismology
for analysis.
Scalability issues
Data centers have some scalability issues as explained below [7].
Data center scalability is the ability of data center to keep working even if its volume and size is
changed. Data centers increase the speed of data processing if they are increased into a large size.
These companies maintain data centers in order to save money. When a company wants to
improve their data centers, they determine the extent to which the data center can be improved
to. If a data center is over built, then there will be wastage of resources. Although sometimes
business organization overbuild data centers because it is not easy to estimate the required size of
a data center.
More so, the scalability and the flexibility of a data center enable the organization to build
quickly at scale and in the nick of time to meet their client's expectations. Likewise, the server
farm versatility is additionally bringing the advantage of high-thickness, vitality productivity and
also the capacity to lessen the expenses over the lifetime of data center speculation.
Moreover, one approach to make an adaptable server farm is by keeping up its area. A few
organizations are generally searching for a territory to locate the server farm. Indeed, there is an
open door for the future development that can be assume control without having more risky
things for its extension, or with no issue of the expensive comforts.
The development of informal communication and thriving utilization of cell phones is the
undeniable reason of the need of scalability. Data centers adaptability itself likewise expands the
high security for records that the organizations keep. It influences the organizations to end up
more dependable and trust-commendable. It is additionally about the requirement for speed. As
These data centers are used for many purposes because they are highly available and have
increased power. This model enhances high performance of clusters which have many forms.
Clusters have common goals of combining multiple CPUS together. This promotes high speed of
the network. This kind of data models is mostly used in universities and in military research for
unique applications. This kind of data center is also used in weather stations and in seismology
for analysis.
Scalability issues
Data centers have some scalability issues as explained below [7].
Data center scalability is the ability of data center to keep working even if its volume and size is
changed. Data centers increase the speed of data processing if they are increased into a large size.
These companies maintain data centers in order to save money. When a company wants to
improve their data centers, they determine the extent to which the data center can be improved
to. If a data center is over built, then there will be wastage of resources. Although sometimes
business organization overbuild data centers because it is not easy to estimate the required size of
a data center.
More so, the scalability and the flexibility of a data center enable the organization to build
quickly at scale and in the nick of time to meet their client's expectations. Likewise, the server
farm versatility is additionally bringing the advantage of high-thickness, vitality productivity and
also the capacity to lessen the expenses over the lifetime of data center speculation.
Moreover, one approach to make an adaptable server farm is by keeping up its area. A few
organizations are generally searching for a territory to locate the server farm. Indeed, there is an
open door for the future development that can be assume control without having more risky
things for its extension, or with no issue of the expensive comforts.
The development of informal communication and thriving utilization of cell phones is the
undeniable reason of the need of scalability. Data centers adaptability itself likewise expands the
high security for records that the organizations keep. It influences the organizations to end up
more dependable and trust-commendable. It is additionally about the requirement for speed. As
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the outcome to be focused, the organizations ought to have a focused on approach for server
farm flexibility and versatility.
Features and Weakness
Features
Has high availability
Highly secured
Requires dependable power
Stores large amount of data.
It has high compliance
It requires room for expansion.
Weakness
It reduces one to one communications among customers
Security related issues increase due to its reliability
Experiences challenges due to natural disasters.
Data center is located far way hence incur travel expenses.
Social technical Aspects
The purpose for the Data Center and Server Room Standards is to describe the base prerequisites
for outlining, introducing, anchoring, checking, keeping up, securing, and decommissioning a
server farm
Data centers in Australia
Global switch Sidney west
Equinix
Nextdc
farm flexibility and versatility.
Features and Weakness
Features
Has high availability
Highly secured
Requires dependable power
Stores large amount of data.
It has high compliance
It requires room for expansion.
Weakness
It reduces one to one communications among customers
Security related issues increase due to its reliability
Experiences challenges due to natural disasters.
Data center is located far way hence incur travel expenses.
Social technical Aspects
The purpose for the Data Center and Server Room Standards is to describe the base prerequisites
for outlining, introducing, anchoring, checking, keeping up, securing, and decommissioning a
server farm
Data centers in Australia
Global switch Sidney west
Equinix
Nextdc
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Container-based virtualization
Also called operating system virtualization is where the layer being virtualize is running as
application within an operating system. The operating system runs on the kernel and the
hardware node is isolated. The isolated hardware is called the container [8].
Purpose of the application
It’s used as a backup for data.
It provides environment for applications to run
It provides security to its contents
They compute a lot of data on the same server
Can be used to locate resources easily
They are used in decreasing the cost of operating system
They are the best to be used in micro services
Working model
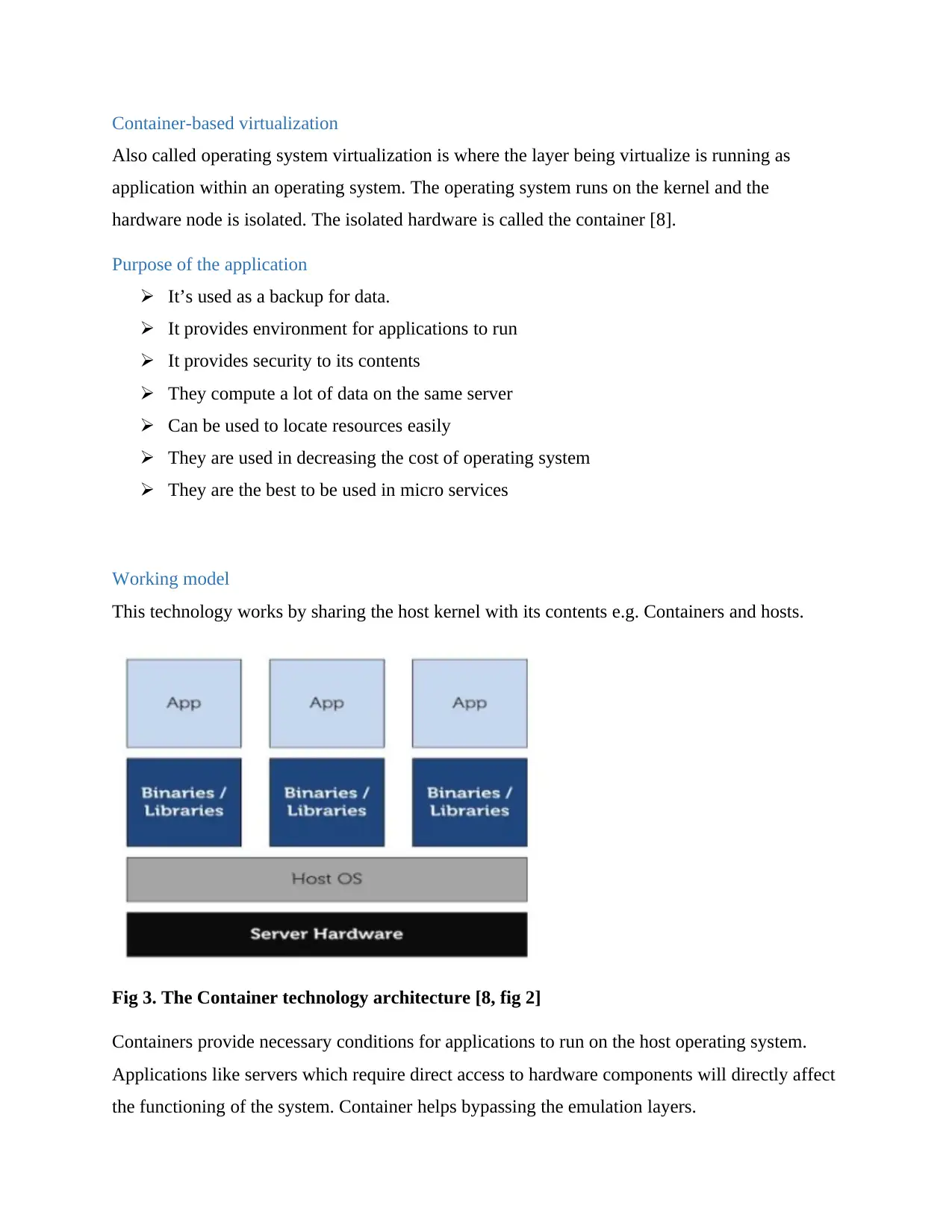
This technology works by sharing the host kernel with its contents e.g. Containers and hosts.
Fig 3. The Container technology architecture [8, fig 2]
Containers provide necessary conditions for applications to run on the host operating system.
Applications like servers which require direct access to hardware components will directly affect
the functioning of the system. Container helps bypassing the emulation layers.
Also called operating system virtualization is where the layer being virtualize is running as
application within an operating system. The operating system runs on the kernel and the
hardware node is isolated. The isolated hardware is called the container [8].
Purpose of the application
It’s used as a backup for data.
It provides environment for applications to run
It provides security to its contents
They compute a lot of data on the same server
Can be used to locate resources easily
They are used in decreasing the cost of operating system
They are the best to be used in micro services
Working model
This technology works by sharing the host kernel with its contents e.g. Containers and hosts.
Fig 3. The Container technology architecture [8, fig 2]
Containers provide necessary conditions for applications to run on the host operating system.
Applications like servers which require direct access to hardware components will directly affect
the functioning of the system. Container helps bypassing the emulation layers.

Scalability issues
Containers tend to have high scalability and adaptability but they are not perfect for every
workload that they handle. Containers have received high virtualization technology that has great
impact on its scalability [10]. It supports cloud computing and application development
Features and Weakness of the application
Features
It has increased scalability resources
It has increased running periods
Has significance over other technologies
Weakness
It is not perfect for all task
it grapes with dependence
It has weak isolation
It has limited tools
Social technical aspects
The reason for the container virtualization technology is to portray the base requirements for
sketching out, presenting, tying down, checking, keeping up, anchoring and decommissioning
the kernel.
Conclusion
Data centers should be highly protected since they store very important information of an
organizations. Other technologies like hypervisor technology are of much significant to the
society since they allow two different operating systems to run on the same machine. This has
made life much simpler since individuals can now purchase only one PC and use different
operating systems on the same laptop.
Containers tend to have high scalability and adaptability but they are not perfect for every
workload that they handle. Containers have received high virtualization technology that has great
impact on its scalability [10]. It supports cloud computing and application development
Features and Weakness of the application
Features
It has increased scalability resources
It has increased running periods
Has significance over other technologies
Weakness
It is not perfect for all task
it grapes with dependence
It has weak isolation
It has limited tools
Social technical aspects
The reason for the container virtualization technology is to portray the base requirements for
sketching out, presenting, tying down, checking, keeping up, anchoring and decommissioning
the kernel.
Conclusion
Data centers should be highly protected since they store very important information of an
organizations. Other technologies like hypervisor technology are of much significant to the
society since they allow two different operating systems to run on the same machine. This has
made life much simpler since individuals can now purchase only one PC and use different
operating systems on the same laptop.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





