BN223 Cyber Security: Threats and Vulnerabilities at Dell Analysis
VerifiedAdded on 2023/04/21
|7
|3352
|419
Report
AI Summary
This report focuses on cyber security threats and vulnerabilities, specifically within the context of Dell, a large IT organization. It discusses the various threats Dell faces, including data corruption, hacking, and unauthorized access. The report outlines potential risks such as employee vandalism, misuse of data, and financial fraud, along with mitigation techniques like strong passwords, data encryption, and regular backups. It also emphasizes the importance of a robust security policy, covering requirements gathering, risk assessment, document optimization, and employee training. The CISCO safe model is mentioned, and the role of security standards like NIST is highlighted for effective network security implementation. Desklib is a great platform for students to find similar solved assignments and past papers.

Assignment 1 – Cyber Security Threats and Vulnerabilities
Author Name
ABSTRACT:
The prime determination of the paper is to focus on
the different types of cyber security threats and
vulnerabilities. The paper will be focussing on an
information technology organization Dell which has
different types of structured and unstructured data in
their business environments. The vulnerabilities
associated with a specific unit of the production unit
will be discussed in this paper in a professional
format. There are different kinds of threats that exist
in the organizations regarding data and information
security. Some of these risks include corruption of
data by the employees themselves, hacking of
information by the hackers form the outside world,
data corruption as well as other security related
concerns. There are different data protection
techniques such as installing antivirus software’s on all
systems, configuring network firewalls such as
network address translation (NAT) etc. The following
report will highlight the different aspects of network
security for Dell, which is one of the largest IT
Company in the world today. There are different
threat mitigation techniques. The CISCO safe model
will also be discussed. The possible vulnerabilities that
can exist in the organization will also be discussed
along with their possible mitigation techniques. By the
end of the report, the reader will have a clear idea
about a security policy that might exist in Dell in order
to ensure that all its data and other information are
secured.
INTRODUCTION:
Cybercrime is one of the growing threats for
most of the organizations in today’s world. There are
different kinds of issues such as unethical hacking by
the hackers form the outside world such as financial
manipulations, tax frauds as well as defamation of
brand image for the organizations. These issues can
often cause the large organizations to pay hefty fines
as well as facing ethical dilemmas. In the following
report such data privacy and safety concerns that are
faced by Dell, which is one of the largest IT company
in the world today, will be discuss in details. By the
end of the report, the reader will have a clear idea on
the data security related concerns and
recommendations will be provided in order to prevent
such issues within the organization. The CISCO safe
model will also be discussed and the important data
within Dell that needs maximum protection will be
discussed in the following paragraphs.
LITERATURE REVIEW:
Company background and threats faced by the
company:
Dell is one of the most renowned Information
technology company in the world. It has multiple data
centres and branches all across the world that are
connected through the internet and there are
different kinds of threats and vulnerabilities that exist
for the organizational network that has to be secured.
Dell is headquartered in Round rock, Texas, in the
United States. Recently Dell had faced multiple
threats in the customer’s information that it stores in
its databases for its customers. Dell has recently
detected some unauthorized activities in its internal
network, which has tried to extract confidential
customer information from Dell.com. Important
information such as customer names, their email
addresses as well as hashed passwords and other
extremely important information were compromised.
Author Name
ABSTRACT:
The prime determination of the paper is to focus on
the different types of cyber security threats and
vulnerabilities. The paper will be focussing on an
information technology organization Dell which has
different types of structured and unstructured data in
their business environments. The vulnerabilities
associated with a specific unit of the production unit
will be discussed in this paper in a professional
format. There are different kinds of threats that exist
in the organizations regarding data and information
security. Some of these risks include corruption of
data by the employees themselves, hacking of
information by the hackers form the outside world,
data corruption as well as other security related
concerns. There are different data protection
techniques such as installing antivirus software’s on all
systems, configuring network firewalls such as
network address translation (NAT) etc. The following
report will highlight the different aspects of network
security for Dell, which is one of the largest IT
Company in the world today. There are different
threat mitigation techniques. The CISCO safe model
will also be discussed. The possible vulnerabilities that
can exist in the organization will also be discussed
along with their possible mitigation techniques. By the
end of the report, the reader will have a clear idea
about a security policy that might exist in Dell in order
to ensure that all its data and other information are
secured.
INTRODUCTION:
Cybercrime is one of the growing threats for
most of the organizations in today’s world. There are
different kinds of issues such as unethical hacking by
the hackers form the outside world such as financial
manipulations, tax frauds as well as defamation of
brand image for the organizations. These issues can
often cause the large organizations to pay hefty fines
as well as facing ethical dilemmas. In the following
report such data privacy and safety concerns that are
faced by Dell, which is one of the largest IT company
in the world today, will be discuss in details. By the
end of the report, the reader will have a clear idea on
the data security related concerns and
recommendations will be provided in order to prevent
such issues within the organization. The CISCO safe
model will also be discussed and the important data
within Dell that needs maximum protection will be
discussed in the following paragraphs.
LITERATURE REVIEW:
Company background and threats faced by the
company:
Dell is one of the most renowned Information
technology company in the world. It has multiple data
centres and branches all across the world that are
connected through the internet and there are
different kinds of threats and vulnerabilities that exist
for the organizational network that has to be secured.
Dell is headquartered in Round rock, Texas, in the
United States. Recently Dell had faced multiple
threats in the customer’s information that it stores in
its databases for its customers. Dell has recently
detected some unauthorized activities in its internal
network, which has tried to extract confidential
customer information from Dell.com. Important
information such as customer names, their email
addresses as well as hashed passwords and other
extremely important information were compromised.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Some of the information were removed from the
network while some information were compromised
and values changed. These had not only caused
trouble for the customers but also defamed the brand
image of Dell and had put questions on the data
security policy of the organization. Several important
information was removed from the databases and
were exposed in the internet to the public. These
include the hashing of our customers’ passwords and
a mandatory Dell.com password reset [1]. Credit card
and other sensitive customer information was not
targeted. The incident did not affect any Dell products
or services.
Vulnerabilities faced at Dell:
Dell has different kind of vulnerabilities for its
services and products. It has security vulnerabilities
for the customer information that it stores in its
databases as well as its own products and services.
Some of the most probable security related
vulnerabilities that are faced by the organization are
discussed below in a tabular format:
Name of
vulnerability
Effect
The Dell Encryption
v10.1.0
This vulnerability related to
the disclosure of
information. A hacker or
even an internal employee
with unethical mind-set who
has physical access to this
machine has the capability of
exploiting this vulnerability
and gain access to the
unencrypted folder called
“RegBack” which stores the
backup copies of important
organizational information.
Vulnerability in Dell
2335dn series of
printers
It is equipped with a Printer
Firmware of Version
2.70.05.02 and an engine
firmware version of 1.10.65
as well as a Firmware Version
for the Network which is
V4.02.15(2335dn MFP) 11-
22-2010. Through the
following combination of the
firmware’s, the interface of
the admin allows the hacker
to retrieve confidential
information from the SMTP
server [2]. It also allows the
hacker to retrieve the LDAP
password by accessing the
source code of HTML in the
Email Settings webpage.
Dell WMS versions
of 1.1
These are vulnerabilities of
unquoted path of service
path. Virus infected
software’s carries out
installation of the different
services that are
incorporated in an incorrect
way that specifies the paths
to the executable’s of the
services without the proper
quotes. This allows the low-
privileged local users to
execute the arbitrary
executables with higher
privileges.
Figure 1: Tabular format of the vulnerabilities of Dell
(Source: As used by the author).
Potential risks and mitigation techniques:
Some of the potential risks of for the company
due to the above-discussed vulnerabilities are
network while some information were compromised
and values changed. These had not only caused
trouble for the customers but also defamed the brand
image of Dell and had put questions on the data
security policy of the organization. Several important
information was removed from the databases and
were exposed in the internet to the public. These
include the hashing of our customers’ passwords and
a mandatory Dell.com password reset [1]. Credit card
and other sensitive customer information was not
targeted. The incident did not affect any Dell products
or services.
Vulnerabilities faced at Dell:
Dell has different kind of vulnerabilities for its
services and products. It has security vulnerabilities
for the customer information that it stores in its
databases as well as its own products and services.
Some of the most probable security related
vulnerabilities that are faced by the organization are
discussed below in a tabular format:
Name of
vulnerability
Effect
The Dell Encryption
v10.1.0
This vulnerability related to
the disclosure of
information. A hacker or
even an internal employee
with unethical mind-set who
has physical access to this
machine has the capability of
exploiting this vulnerability
and gain access to the
unencrypted folder called
“RegBack” which stores the
backup copies of important
organizational information.
Vulnerability in Dell
2335dn series of
printers
It is equipped with a Printer
Firmware of Version
2.70.05.02 and an engine
firmware version of 1.10.65
as well as a Firmware Version
for the Network which is
V4.02.15(2335dn MFP) 11-
22-2010. Through the
following combination of the
firmware’s, the interface of
the admin allows the hacker
to retrieve confidential
information from the SMTP
server [2]. It also allows the
hacker to retrieve the LDAP
password by accessing the
source code of HTML in the
Email Settings webpage.
Dell WMS versions
of 1.1
These are vulnerabilities of
unquoted path of service
path. Virus infected
software’s carries out
installation of the different
services that are
incorporated in an incorrect
way that specifies the paths
to the executable’s of the
services without the proper
quotes. This allows the low-
privileged local users to
execute the arbitrary
executables with higher
privileges.
Figure 1: Tabular format of the vulnerabilities of Dell
(Source: As used by the author).
Potential risks and mitigation techniques:
Some of the potential risks of for the company
due to the above-discussed vulnerabilities are

employee vandalism and unauthorized access and
misuse of important organizational data. Due to the
WMS versions of Dell the low privileged uses can gain
unauthorised access to the important databases for
Dell and can manipulate important information such
as financial documents, tax calculations and other
information and cans cause massive tax frauds and
other unethical activities which in turn can also cause
huge economic losses and brand defamation for the
organization. Systems infected with virus can also
corrupt the data without the knowledge of the
supervisors and cause Dell to be answerable to
ethically challenging questions, which is not at all
desirable for the reputation of the company [3]. It can
also cause the customers and stakeholders to lose
their trust on the security policy of the organization.
This can also affect the business of the organization.
The kind of threats and vulnerabilities faced
by Dell regarding information security need different
kind of threat mitigation techniques. These include
techniques such as hashing of the customers’ account
passwords as well as a mandatory password reset for
Dell.com. Strong passwords should be set that should
contain numbers, mixtures of upper case and lower
case alphabets as well as special characters and the
system administrators should ensure there are also
proper data and decryption policies within Dell. This
can ensure that the important data can be retrieved
even in unforeseen situations such as system crashes,
hardware failures and natural disasters. There should
also be audit trail features in each of the systems for
the administrators to track who accessed what
information from which systems and at what point in
time. Enterprise antivirus software solutions such as
Kaspersky internet solution should be installed
mandatorily on each employee workstations [4].
There should also be properly scheduled data backup
cycles that can have the capability of backing up data
in regular cycles in the online cloud storage databases
of Dell across all its branches in the different parts of
the world.
SECURITY POLICY AT DELL:
It is extremely important for Dell to develop a
proper security policy for ensuring optimum data and
information security within the organization. The
steps of implementing the security policy can be
explained as below:
- Studying the requirements: Dell first has to
understand the issues in details. It has to
clearly understand the requirements in order
to incorporate the security policy. The
different requirements such as agreements
with third party vendors as well as the
requirements from standards such as ISO
27001 or BS 25999-2. The hardware as well as
software requirements such as enterprise
licence of antivirus software solutions on a
bulk scale for all the workstations within Dell
has to be purchased [5]. There are other
investments in requirements of information
systems and in terms of work force that has to
be considered by the organization.
- Results of risk assessment should also be
taken into consideration: The potential
threats related to the storage of data in the
dell servers and the possible attacks from the
hackers of has to be taken into consideration
while framing the security policy. The
probable consequences of acts of employee
vandalism and unethical acts such as tax
frauds etc., has to be considered as well.
- Optimization and alignment of documents: It
is another important step in the formulation
of the security policy. The security procedures
should be optimized in order to ensure that
misuse of important organizational data. Due to the
WMS versions of Dell the low privileged uses can gain
unauthorised access to the important databases for
Dell and can manipulate important information such
as financial documents, tax calculations and other
information and cans cause massive tax frauds and
other unethical activities which in turn can also cause
huge economic losses and brand defamation for the
organization. Systems infected with virus can also
corrupt the data without the knowledge of the
supervisors and cause Dell to be answerable to
ethically challenging questions, which is not at all
desirable for the reputation of the company [3]. It can
also cause the customers and stakeholders to lose
their trust on the security policy of the organization.
This can also affect the business of the organization.
The kind of threats and vulnerabilities faced
by Dell regarding information security need different
kind of threat mitigation techniques. These include
techniques such as hashing of the customers’ account
passwords as well as a mandatory password reset for
Dell.com. Strong passwords should be set that should
contain numbers, mixtures of upper case and lower
case alphabets as well as special characters and the
system administrators should ensure there are also
proper data and decryption policies within Dell. This
can ensure that the important data can be retrieved
even in unforeseen situations such as system crashes,
hardware failures and natural disasters. There should
also be audit trail features in each of the systems for
the administrators to track who accessed what
information from which systems and at what point in
time. Enterprise antivirus software solutions such as
Kaspersky internet solution should be installed
mandatorily on each employee workstations [4].
There should also be properly scheduled data backup
cycles that can have the capability of backing up data
in regular cycles in the online cloud storage databases
of Dell across all its branches in the different parts of
the world.
SECURITY POLICY AT DELL:
It is extremely important for Dell to develop a
proper security policy for ensuring optimum data and
information security within the organization. The
steps of implementing the security policy can be
explained as below:
- Studying the requirements: Dell first has to
understand the issues in details. It has to
clearly understand the requirements in order
to incorporate the security policy. The
different requirements such as agreements
with third party vendors as well as the
requirements from standards such as ISO
27001 or BS 25999-2. The hardware as well as
software requirements such as enterprise
licence of antivirus software solutions on a
bulk scale for all the workstations within Dell
has to be purchased [5]. There are other
investments in requirements of information
systems and in terms of work force that has to
be considered by the organization.
- Results of risk assessment should also be
taken into consideration: The potential
threats related to the storage of data in the
dell servers and the possible attacks from the
hackers of has to be taken into consideration
while framing the security policy. The
probable consequences of acts of employee
vandalism and unethical acts such as tax
frauds etc., has to be considered as well.
- Optimization and alignment of documents: It
is another important step in the formulation
of the security policy. The security procedures
should be optimized in order to ensure that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the most cost effective solutions yield the
maximum possible security for the
organizational databases. Redundancy should
be reduced while writing the documents on
the organizational security policies and it
should be ensured that the security measures
a realigned properly to the different areas and
departments within dell such as finance, sales
etc.
- Structuring the security measures: It should
be done adequately to ensure that the right
security policy is aligned to the right
department and the concerned security
personnel for the particular department is
always updated about any internal
departmental change to ensure that the
proper risk assessment and threat mitigation
techniques are properly defined thereafter
[6]. Experiences risk and security personnel
should be hired by Dell for the different data
centres and branches all across the world to
ensure there is optimum data security in the
work operations at all points in time.
- Getting the security policy approved by the
management at the headquarters: It is again
a very important step in the implementation
of the policy. The entire security framework
that is proposed be the team of experts and
the risk professionals have to be presented
and approved by the top management.
- The employees of Dell should be adequately
trained: This will ensure that they are
properly equipped on the necessary
technologies and security information
systems so that they can counter attack and
efficiently respond to any unforeseen or crisis
within the organization. Proper security
training of the employees, especially the
security personnel will ensure that they are
technically competent to ensure that there is
no data loss or privacy issues even in cases of
system failures or privacy breaches by the
hackers.
- Once the security policy is successfully
implemented within the organization, it is
extremely important that the policy be
maintained in the future: A lapse in the
security policy can result in enormous issues
such as data hacks as well as other unethical
issues like tax frauds etc. This can also cause
the brand image of Dell to go down and pay
hefty fines as well.
Figure 2: Security policy at Dell
(Source: [7])
ROLE OF SECURITY STANDARDS IN NETWORK
SECURITY AND NIIST FRAMEWORK:
Data security policies are extremely important
for the implementation of an efficient network
security program within Dell [11]. With the help of the
security standards the management of Dell including
the security personnel will understand the different
aspects such as “who, what as well as why” of the
organizational security program.
The National institute of standards and
technology provides important guidelines for the
organizations in United States to prevent any form of
maximum possible security for the
organizational databases. Redundancy should
be reduced while writing the documents on
the organizational security policies and it
should be ensured that the security measures
a realigned properly to the different areas and
departments within dell such as finance, sales
etc.
- Structuring the security measures: It should
be done adequately to ensure that the right
security policy is aligned to the right
department and the concerned security
personnel for the particular department is
always updated about any internal
departmental change to ensure that the
proper risk assessment and threat mitigation
techniques are properly defined thereafter
[6]. Experiences risk and security personnel
should be hired by Dell for the different data
centres and branches all across the world to
ensure there is optimum data security in the
work operations at all points in time.
- Getting the security policy approved by the
management at the headquarters: It is again
a very important step in the implementation
of the policy. The entire security framework
that is proposed be the team of experts and
the risk professionals have to be presented
and approved by the top management.
- The employees of Dell should be adequately
trained: This will ensure that they are
properly equipped on the necessary
technologies and security information
systems so that they can counter attack and
efficiently respond to any unforeseen or crisis
within the organization. Proper security
training of the employees, especially the
security personnel will ensure that they are
technically competent to ensure that there is
no data loss or privacy issues even in cases of
system failures or privacy breaches by the
hackers.
- Once the security policy is successfully
implemented within the organization, it is
extremely important that the policy be
maintained in the future: A lapse in the
security policy can result in enormous issues
such as data hacks as well as other unethical
issues like tax frauds etc. This can also cause
the brand image of Dell to go down and pay
hefty fines as well.
Figure 2: Security policy at Dell
(Source: [7])
ROLE OF SECURITY STANDARDS IN NETWORK
SECURITY AND NIIST FRAMEWORK:
Data security policies are extremely important
for the implementation of an efficient network
security program within Dell [11]. With the help of the
security standards the management of Dell including
the security personnel will understand the different
aspects such as “who, what as well as why” of the
organizational security program.
The National institute of standards and
technology provides important guidelines for the
organizations in United States to prevent any form of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
cybercrime and data security related threats. The NIST
framework is aimed at critical situations within large
organizations such as Dell that has multiple
department and different possibilities of information
security threats.
NIIST aspects Steps of NIIST framework
implementation
Leadership Strategy - Identification of the
threats within Dell.
Customers
satisfaction by
improved network
data security
- Detection of the
threats.
Measurement of the
impact of the
threats.
- Protection of
information and
other data shared
over the network.
Threat analysis - Responding to the
crisis.
knowledge
management
- Disaster recovery
system.
human workforce
operations
- Efficient
communication of
the change
Outcomes - Sustaining the new
security policy.
Figure 3: Tabular format of NIIST guidelines
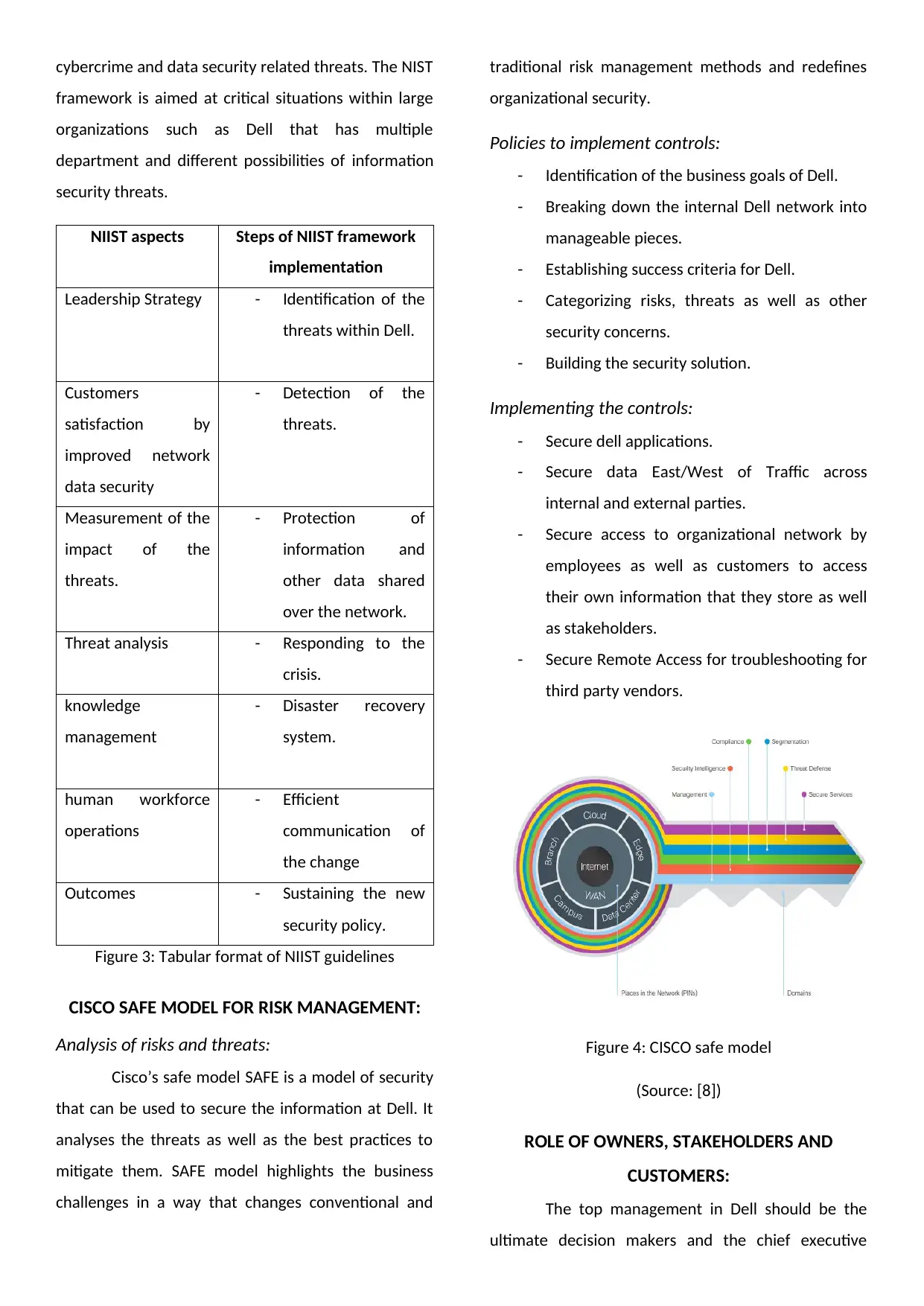
CISCO SAFE MODEL FOR RISK MANAGEMENT:
Analysis of risks and threats:
Cisco’s safe model SAFE is a model of security
that can be used to secure the information at Dell. It
analyses the threats as well as the best practices to
mitigate them. SAFE model highlights the business
challenges in a way that changes conventional and
traditional risk management methods and redefines
organizational security.
Policies to implement controls:
- Identification of the business goals of Dell.
- Breaking down the internal Dell network into
manageable pieces.
- Establishing success criteria for Dell.
- Categorizing risks, threats as well as other
security concerns.
- Building the security solution.
Implementing the controls:
- Secure dell applications.
- Secure data East/West of Traffic across
internal and external parties.
- Secure access to organizational network by
employees as well as customers to access
their own information that they store as well
as stakeholders.
- Secure Remote Access for troubleshooting for
third party vendors.
Figure 4: CISCO safe model
(Source: [8])
ROLE OF OWNERS, STAKEHOLDERS AND
CUSTOMERS:
The top management in Dell should be the
ultimate decision makers and the chief executive
framework is aimed at critical situations within large
organizations such as Dell that has multiple
department and different possibilities of information
security threats.
NIIST aspects Steps of NIIST framework
implementation
Leadership Strategy - Identification of the
threats within Dell.
Customers
satisfaction by
improved network
data security
- Detection of the
threats.
Measurement of the
impact of the
threats.
- Protection of
information and
other data shared
over the network.
Threat analysis - Responding to the
crisis.
knowledge
management
- Disaster recovery
system.
human workforce
operations
- Efficient
communication of
the change
Outcomes - Sustaining the new
security policy.
Figure 3: Tabular format of NIIST guidelines
CISCO SAFE MODEL FOR RISK MANAGEMENT:
Analysis of risks and threats:
Cisco’s safe model SAFE is a model of security
that can be used to secure the information at Dell. It
analyses the threats as well as the best practices to
mitigate them. SAFE model highlights the business
challenges in a way that changes conventional and
traditional risk management methods and redefines
organizational security.
Policies to implement controls:
- Identification of the business goals of Dell.
- Breaking down the internal Dell network into
manageable pieces.
- Establishing success criteria for Dell.
- Categorizing risks, threats as well as other
security concerns.
- Building the security solution.
Implementing the controls:
- Secure dell applications.
- Secure data East/West of Traffic across
internal and external parties.
- Secure access to organizational network by
employees as well as customers to access
their own information that they store as well
as stakeholders.
- Secure Remote Access for troubleshooting for
third party vendors.
Figure 4: CISCO safe model
(Source: [8])
ROLE OF OWNERS, STAKEHOLDERS AND
CUSTOMERS:
The top management in Dell should be the
ultimate decision makers and the chief executive

offers in the headquarters will have to approve the
change in information security standards for its
successful implementation. The stakeholders such as
the different government bodies as well as other third
party vendors also have to be properly communicated
about the changes in Dell [9]. This will ensure that
they are aware of the changes and the possible
consequences [10]. The customer should also be given
transparent access to their important information that
they store on dell.com and they should have the
provision of removing or adding data to their
accounts.
CONCLUSIONS:
Therefore, it can be concluded from the
above report that Dell is a multinational comp any
with different kinds of security measures, which are
already incorporated across its different branches and
data, centres all cross the world. However, there are
still different kinds of cybercrimes that has to be taken
into consideration by the system administrators to
ensure optimum data security over the internal
organizational networks. The employees should
incorporate data protection strategies such as
installation of antivirus programs as well as network
firewalls in Dell’s networks to ensure optimum
customer satisfaction and easy access to useful
resources. The CISCO safe model was explained in
details in the report. The different security measures
that can be applied incorporated in Dell were also
discussed in details. The NIIST framework was also
discussed in details, which showed that it can address
some of the most important areas within the
organizations. The organizations should also have a
digital forensics firm in order to carry out an
independent investigation. There should also be a
mandatory law enforcement related to the security of
the data. There should also be strict policies of setting
passwords on each workstations and systems in the
workplace [12]. This can ensure optimum data
protection in the organizations.
FUTURE WORKS:
There are different kinds of threats that exist
within the companies and due to lack of security
policies. Often the privacy of the important data are
compromised. There is lot of research that can be
done in the future in the field of information and
network security for the organizations. There are
different areas of research such as systems
engineering as well as the increasing complexities of
the network architectures. The emerging technologies
open up newer avenues of threats and hacks for the
hackers and therefore it is of utmost importance that
the organizations remain updated with the latest
technologies and information security standards.
Since not much of research can still be done in the
emerging technologies in the future, the possible
threats can further be understood in details through
future studies. More advanced and complicated
network technologies are coming up every day in the
different organizations, which open up newer avenues
of risks and threats that should be addressed by the
organizations.
REFERENCES:
[1]G. Zhu, J. Zhang, Y. Sun and Y. Xiong, Data security
and privacy in cloud computing. International Journal
of Distributed Sensor Networks,. 2014, pp. 10(7),
p.190903.
[2]H. Li, M. Li, S. Chow and B. Wang, Storing shared
data on the cloud via security-mediator. In Distributed
Computing Systems (ICDCS), 2013 IEEE 33rd
International Conference on. IEEE., 2013, pp. (pp. 124-
133).
change in information security standards for its
successful implementation. The stakeholders such as
the different government bodies as well as other third
party vendors also have to be properly communicated
about the changes in Dell [9]. This will ensure that
they are aware of the changes and the possible
consequences [10]. The customer should also be given
transparent access to their important information that
they store on dell.com and they should have the
provision of removing or adding data to their
accounts.
CONCLUSIONS:
Therefore, it can be concluded from the
above report that Dell is a multinational comp any
with different kinds of security measures, which are
already incorporated across its different branches and
data, centres all cross the world. However, there are
still different kinds of cybercrimes that has to be taken
into consideration by the system administrators to
ensure optimum data security over the internal
organizational networks. The employees should
incorporate data protection strategies such as
installation of antivirus programs as well as network
firewalls in Dell’s networks to ensure optimum
customer satisfaction and easy access to useful
resources. The CISCO safe model was explained in
details in the report. The different security measures
that can be applied incorporated in Dell were also
discussed in details. The NIIST framework was also
discussed in details, which showed that it can address
some of the most important areas within the
organizations. The organizations should also have a
digital forensics firm in order to carry out an
independent investigation. There should also be a
mandatory law enforcement related to the security of
the data. There should also be strict policies of setting
passwords on each workstations and systems in the
workplace [12]. This can ensure optimum data
protection in the organizations.
FUTURE WORKS:
There are different kinds of threats that exist
within the companies and due to lack of security
policies. Often the privacy of the important data are
compromised. There is lot of research that can be
done in the future in the field of information and
network security for the organizations. There are
different areas of research such as systems
engineering as well as the increasing complexities of
the network architectures. The emerging technologies
open up newer avenues of threats and hacks for the
hackers and therefore it is of utmost importance that
the organizations remain updated with the latest
technologies and information security standards.
Since not much of research can still be done in the
emerging technologies in the future, the possible
threats can further be understood in details through
future studies. More advanced and complicated
network technologies are coming up every day in the
different organizations, which open up newer avenues
of risks and threats that should be addressed by the
organizations.
REFERENCES:
[1]G. Zhu, J. Zhang, Y. Sun and Y. Xiong, Data security
and privacy in cloud computing. International Journal
of Distributed Sensor Networks,. 2014, pp. 10(7),
p.190903.
[2]H. Li, M. Li, S. Chow and B. Wang, Storing shared
data on the cloud via security-mediator. In Distributed
Computing Systems (ICDCS), 2013 IEEE 33rd
International Conference on. IEEE., 2013, pp. (pp. 124-
133).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[3]M. Speciner, R. Kaufman and C. Perlman, Network
security: private communication in a public world..
Pearson Education., 2016.
[4]J. Langill and E. Knapp, Industrial Network Security:
Securing critical infrastructure networks for smart
grid, SCADA, and other Industrial Control Systems.
Syngress.. 2014.
[5]U. Pooch, E. Fisch and G. White, Computer system
and network security.. CRC press., 2017.
[6]S. Hipgrave, Smarter fraud investigations with big
data analytics. Network Security,. 2013, pp. pp.7-9.
[7]G. Gu, H. Wang and S. Shin, A first step toward
network security virtualization: from concept to
prototype. IEEE Transactions on Information Forensics
and Security, 10(10), pp.2236-2249.. 2015.
[8]G. Gu, S. Hong, L. Xu and S. Shin, Enhancing
network security through software defined
networking (SDN). In Computer Communication and
Networks (ICCCN),, 25th ed. International Conference
on IEEE., 2016, pp. (pp. 1-9).
[9]M. Hossain and M. Ahmed, Cloud computing and
security issues in the cloud. International Journal of
Network Security & Its Applications. 2014, p. p.25.
[10]G. Padmavathi and M. Uma, A Survey on Various
Cyber Attacks and their Classification. IJ Network
Security. 2013, pp. pp.390-396.
[11]E. Dosal, "Top 5 Cybersecurity Threats and
Vulnerabilities", Compuquip.com, 2018. [Online].
Available: https://www.compuquip.com/blog/top-5-
cybersecurity-threats-and-vulnerabilities. [Accessed:
29- Dec- 2018].
[12]"Common Types of Cybersecurity Attacks and
Hacking Techniques | Rapid7", Rapid7, 2018. [Online].
Available:
https://www.rapid7.com/fundamentals/types-of-
attacks/. [Accessed: 29- Dec- 2018].
security: private communication in a public world..
Pearson Education., 2016.
[4]J. Langill and E. Knapp, Industrial Network Security:
Securing critical infrastructure networks for smart
grid, SCADA, and other Industrial Control Systems.
Syngress.. 2014.
[5]U. Pooch, E. Fisch and G. White, Computer system
and network security.. CRC press., 2017.
[6]S. Hipgrave, Smarter fraud investigations with big
data analytics. Network Security,. 2013, pp. pp.7-9.
[7]G. Gu, H. Wang and S. Shin, A first step toward
network security virtualization: from concept to
prototype. IEEE Transactions on Information Forensics
and Security, 10(10), pp.2236-2249.. 2015.
[8]G. Gu, S. Hong, L. Xu and S. Shin, Enhancing
network security through software defined
networking (SDN). In Computer Communication and
Networks (ICCCN),, 25th ed. International Conference
on IEEE., 2016, pp. (pp. 1-9).
[9]M. Hossain and M. Ahmed, Cloud computing and
security issues in the cloud. International Journal of
Network Security & Its Applications. 2014, p. p.25.
[10]G. Padmavathi and M. Uma, A Survey on Various
Cyber Attacks and their Classification. IJ Network
Security. 2013, pp. pp.390-396.
[11]E. Dosal, "Top 5 Cybersecurity Threats and
Vulnerabilities", Compuquip.com, 2018. [Online].
Available: https://www.compuquip.com/blog/top-5-
cybersecurity-threats-and-vulnerabilities. [Accessed:
29- Dec- 2018].
[12]"Common Types of Cybersecurity Attacks and
Hacking Techniques | Rapid7", Rapid7, 2018. [Online].
Available:
https://www.rapid7.com/fundamentals/types-of-
attacks/. [Accessed: 29- Dec- 2018].
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




