BN305 - Virtual Private Networks: SSL/VPN Technologies Report
VerifiedAdded on 2022/12/22
|11
|2172
|1
Report
AI Summary
This report provides a comprehensive analysis of SSL/VPN technologies and their applications in securing organizational data. It begins by highlighting the significance of VPNs for contemporary organizations, emphasizing their role in protecting data in a data-driven environment. The report then delves into the specifics of SSL/VPN, comparing it to IPSEC/VPN and focusing on key aspects such as authentication and access control, including SSL/TLS handshake, digital signatures, and methods for communication between server and client. It further explores confidentiality and integrity mechanisms within SSL communication, detailing the role of symmetric encryption and hash algorithms, as well as different VPN client software options and support for simultaneous users. Finally, the report addresses anti-replay attacks and the procedures to mitigate them, concluding with recommendations for strengthening organizational security against cyber threats. The report also includes a detailed reference list.

Running head: APPLICATION OF SSL/VPN
APPLICATION OF SSL/VPN
Name of the Student
Name of the University
Author Note
APPLICATION OF SSL/VPN
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
APPLICATION OF SSL/VPN
Table of Contents
Introduction:..........................................................................................................................................2
Discussion:.............................................................................................................................................2
The significance of VPN for contemporary organisations:.................................................................2
Application of SSL/VPN:.....................................................................................................................2
1. Authentication and Access Control............................................................................................2
2. Confidentiality and Integrity......................................................................................................6
3. Anti-Replay................................................................................................................................6
Conclusion:............................................................................................................................................7
References:............................................................................................................................................8
APPLICATION OF SSL/VPN
Table of Contents
Introduction:..........................................................................................................................................2
Discussion:.............................................................................................................................................2
The significance of VPN for contemporary organisations:.................................................................2
Application of SSL/VPN:.....................................................................................................................2
1. Authentication and Access Control............................................................................................2
2. Confidentiality and Integrity......................................................................................................6
3. Anti-Replay................................................................................................................................6
Conclusion:............................................................................................................................................7
References:............................................................................................................................................8

2
APPLICATION OF SSL/VPN
Introduction:
This report has analysed importance of VPN for organisations to secure data over a network. In this
context, SSL/VPN is chosen over IPSEC/VPN and application of this VPN is discussed in this report.
The report discuss various concepts related to SSL/VPN such as Authentication and Access Control,
Confidentiality and Integrity, how this is ensured, important mechanism related to SSL
confidentiality and integrity for enhancing data security is described in details in this report. Theories
related to anti-replay is discussed as well. Along with theoretical discussion, practical tasks applying
these concepts is analysed in this report for providing a detailed overview about these theoretical
concepts.
Discussion:
The significance of VPN for contemporary organisations:
Today organisations are data are data driven and hence security of these organizations are of prime
importance to the organizations. Hence, it is extremely important for the contemporary
organizations to secure their organizational data, which might affect their business success in the
competitive market [1]. VPN provides an easy yet effective solution to secure these data through
encryption, which makes it a significant choice for data security.
Application of SSL/VPN:
1. Authentication and Access Control
1.1. Communication of browser with server
When communicating with sever, the browser ensures that it is communicating to the right server.
However this not a simple process and there are various process that is required for this. This report
discuss this technique in details.
APPLICATION OF SSL/VPN
Introduction:
This report has analysed importance of VPN for organisations to secure data over a network. In this
context, SSL/VPN is chosen over IPSEC/VPN and application of this VPN is discussed in this report.
The report discuss various concepts related to SSL/VPN such as Authentication and Access Control,
Confidentiality and Integrity, how this is ensured, important mechanism related to SSL
confidentiality and integrity for enhancing data security is described in details in this report. Theories
related to anti-replay is discussed as well. Along with theoretical discussion, practical tasks applying
these concepts is analysed in this report for providing a detailed overview about these theoretical
concepts.
Discussion:
The significance of VPN for contemporary organisations:
Today organisations are data are data driven and hence security of these organizations are of prime
importance to the organizations. Hence, it is extremely important for the contemporary
organizations to secure their organizational data, which might affect their business success in the
competitive market [1]. VPN provides an easy yet effective solution to secure these data through
encryption, which makes it a significant choice for data security.
Application of SSL/VPN:
1. Authentication and Access Control
1.1. Communication of browser with server
When communicating with sever, the browser ensures that it is communicating to the right server.
However this not a simple process and there are various process that is required for this. This report
discuss this technique in details.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
APPLICATION OF SSL/VPN
APPLICATION OF SSL/VPN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
APPLICATION OF SSL/VPN
SSL and TLS authentication
SSL and TSL ensures authentication through a mechanism known as SSL or TSL handshake. In this
process, the secret key to decrypt the encrypted information is computed with the public key of the
server [2]. If the server wants to decrypt the sent information, server has to generate that secret key
with appropriate private key only known to client, which ensures data authentication.
1.2. Working principle of digital signatures and its role in authentication process
Digital signatures are nothing but the cryptography value that is assigned with digital data and it is
similar to Physical signature that is often done on physical documents.
The scheme of the digital signature is an extension of public key cryptography. Here in this report,
the working procedure of the digital signature scheme is described in details [3].
At first, a public-private key pair is provided to each person who adopts this scheme
Now two different key players are considered for encryption-decryption and signing-
verifying of the document
A person who signs the data provide data to Hash Function and this produces a hash of data
The hash value produced in this step is then provided to a signature algorithm, which creates
a digitally created signature on the provided hash
After integrating signature with data this is sent to another person who verifies this digital
signature along with the verification key is then fed to the verification algorithm value is
provided
A person who verifies this is responsible for generating a hash value with Hash Function on
the data that is received from another person.
In order to decide whether the digital signature is valid or not this hash value is compared
with the output generated from the verification algorithm
APPLICATION OF SSL/VPN
SSL and TLS authentication
SSL and TSL ensures authentication through a mechanism known as SSL or TSL handshake. In this
process, the secret key to decrypt the encrypted information is computed with the public key of the
server [2]. If the server wants to decrypt the sent information, server has to generate that secret key
with appropriate private key only known to client, which ensures data authentication.
1.2. Working principle of digital signatures and its role in authentication process
Digital signatures are nothing but the cryptography value that is assigned with digital data and it is
similar to Physical signature that is often done on physical documents.
The scheme of the digital signature is an extension of public key cryptography. Here in this report,
the working procedure of the digital signature scheme is described in details [3].
At first, a public-private key pair is provided to each person who adopts this scheme
Now two different key players are considered for encryption-decryption and signing-
verifying of the document
A person who signs the data provide data to Hash Function and this produces a hash of data
The hash value produced in this step is then provided to a signature algorithm, which creates
a digitally created signature on the provided hash
After integrating signature with data this is sent to another person who verifies this digital
signature along with the verification key is then fed to the verification algorithm value is
provided
A person who verifies this is responsible for generating a hash value with Hash Function on
the data that is received from another person.
In order to decide whether the digital signature is valid or not this hash value is compared
with the output generated from the verification algorithm
5
APPLICATION OF SSL/VPN
APPLICATION OF SSL/VPN
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
APPLICATION OF SSL/VPN
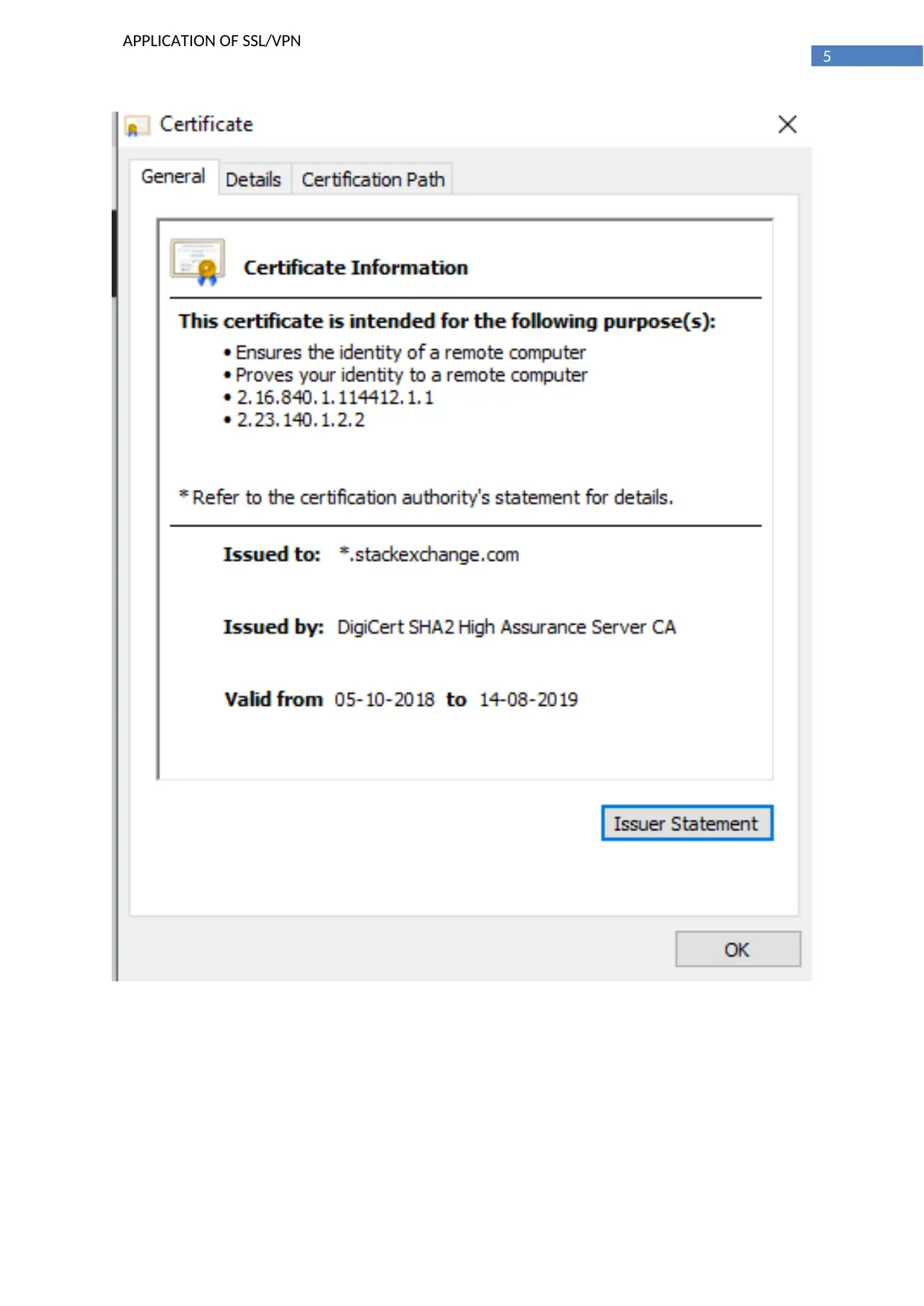
Details of certificate verification: A digital signature provides authentication for data digital
signatures are created with the help of private key that is known to the person who signs the
document and private key is not known to any other person. Hence, it is quite impossible to create a
fake or duplicate signature for these data [4]. even if there is any modification made in the original
document the signature that is created with acknowledgement from both sender and receiver will
not be valid which will provide an indication to put the party that and possible modification has been
made in the original document. Hence, digital data is an excellent way to ensure the authenticity of
any digital document.
1.3. Methods for communication between server and client
While communication between server and client is initiated, it is important that the server make
sure that it is communicating to the right client. Now to ensure that several methods are there [5]:
User account: it is the most efficient way to ensure authenticity of client. When
communication with the server is made from the registered user account, server easily
recognizes it
Cookies: When a cookie is set on the client machine, it provides a distinct identity per
session, which helps server to recognize the client
IP address: IP address of network makes a sever aware of the identity of the client, however
it might not be unique as it applies for an entire network which might lead to false
identification of the client
1.4. The centralized access control for a variety of organizational resources
Centralized access control is the process to establish a secure access to all of the IT resources of an
organization. it provides system administration from anywhere with same level of authority.
SSL provides a secret key for communication over the network and all of the devices that is
connected to the SSL VPN is encrypted with this secret key. Hence, if this secret key is known, it is
possible to control security of data communicated from those devices with sane level of
authenticity.
1.5. The Network access control for SSL/VPN
It is a set of policy applied for controlling access to SSL VPN. It defines a set of parameters such as
antivirus software, operating system, java version and based on these parameters administrator
decides if a user is granted permission or not to login to the VPN network.
APPLICATION OF SSL/VPN
Details of certificate verification: A digital signature provides authentication for data digital
signatures are created with the help of private key that is known to the person who signs the
document and private key is not known to any other person. Hence, it is quite impossible to create a
fake or duplicate signature for these data [4]. even if there is any modification made in the original
document the signature that is created with acknowledgement from both sender and receiver will
not be valid which will provide an indication to put the party that and possible modification has been
made in the original document. Hence, digital data is an excellent way to ensure the authenticity of
any digital document.
1.3. Methods for communication between server and client
While communication between server and client is initiated, it is important that the server make
sure that it is communicating to the right client. Now to ensure that several methods are there [5]:
User account: it is the most efficient way to ensure authenticity of client. When
communication with the server is made from the registered user account, server easily
recognizes it
Cookies: When a cookie is set on the client machine, it provides a distinct identity per
session, which helps server to recognize the client
IP address: IP address of network makes a sever aware of the identity of the client, however
it might not be unique as it applies for an entire network which might lead to false
identification of the client
1.4. The centralized access control for a variety of organizational resources
Centralized access control is the process to establish a secure access to all of the IT resources of an
organization. it provides system administration from anywhere with same level of authority.
SSL provides a secret key for communication over the network and all of the devices that is
connected to the SSL VPN is encrypted with this secret key. Hence, if this secret key is known, it is
possible to control security of data communicated from those devices with sane level of
authenticity.
1.5. The Network access control for SSL/VPN
It is a set of policy applied for controlling access to SSL VPN. It defines a set of parameters such as
antivirus software, operating system, java version and based on these parameters administrator
decides if a user is granted permission or not to login to the VPN network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
APPLICATION OF SSL/VPN
2. Confidentiality and Integrity
2.1. Procedure to achieve the confidentiality and integrity in SSL communication
In SSL communication when data is an exchange between a web browser and web server, there is
standard encryption that is applied to the transmitted data providing data confidentiality [5]. Now in
order to decrypt this data decryption key is exchanged between a web browser and the web server
does ensure Data integrity.
Server & client agreement on one cipher suit: During SSL or TSL handshake, a server sent a server
hello message to the client that includes details about the cipher suit that the server has chosen
from the provided list sent by the client in client hello message. Once this is accepted, that particular
cipher key is chosen in the overall communication proses [6].
2.2. The role of symmetric encryption and hash algorithms in SSL communication
In SSL communication, symmetric encryption provides two keys that are efficient in performing data
encryption. These keys are symmetric of nature means both of these keys are able to encrypt as well
as decrypt data [7].
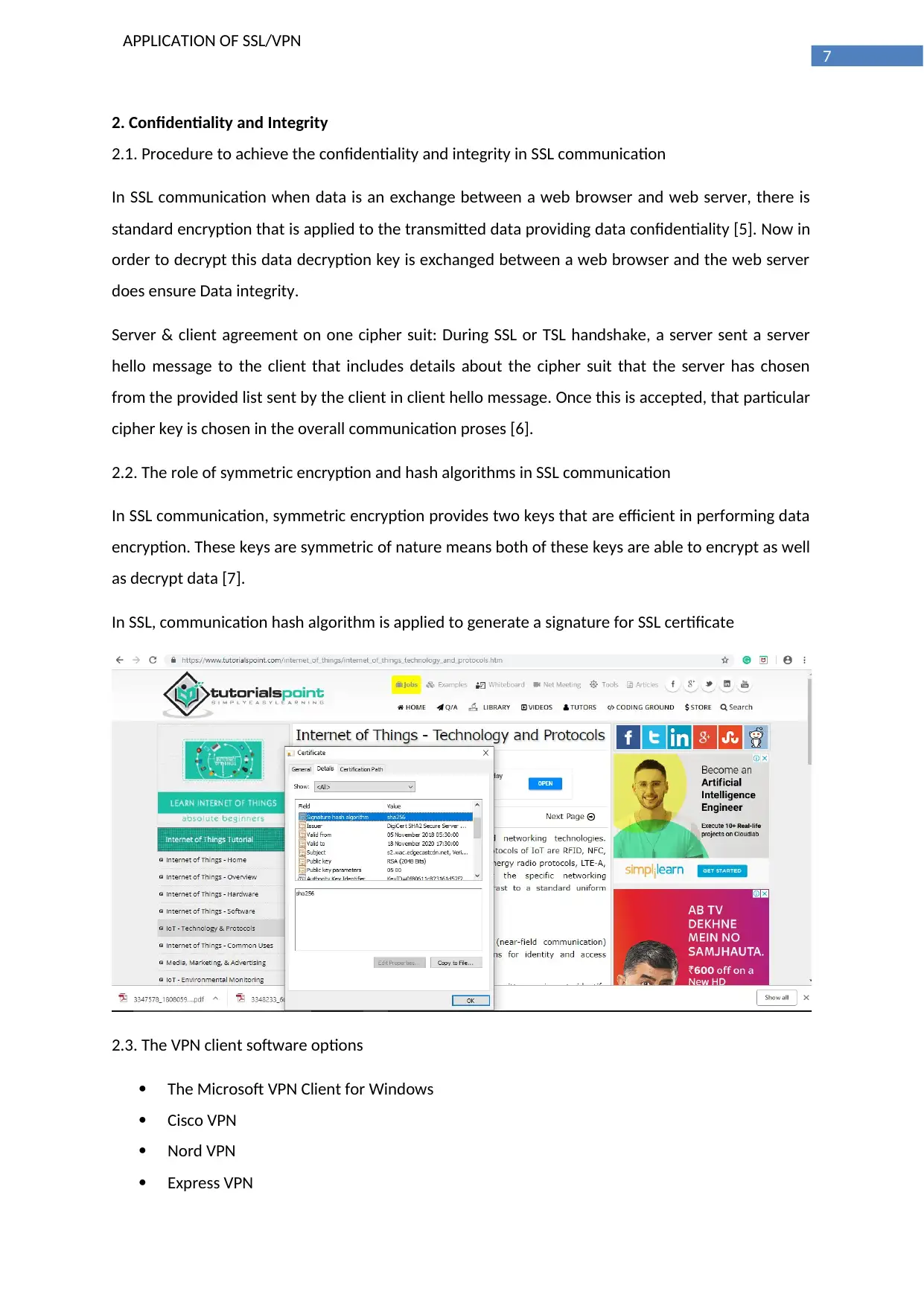
In SSL, communication hash algorithm is applied to generate a signature for SSL certificate
2.3. The VPN client software options
The Microsoft VPN Client for Windows
Cisco VPN
Nord VPN
Express VPN
APPLICATION OF SSL/VPN
2. Confidentiality and Integrity
2.1. Procedure to achieve the confidentiality and integrity in SSL communication
In SSL communication when data is an exchange between a web browser and web server, there is
standard encryption that is applied to the transmitted data providing data confidentiality [5]. Now in
order to decrypt this data decryption key is exchanged between a web browser and the web server
does ensure Data integrity.
Server & client agreement on one cipher suit: During SSL or TSL handshake, a server sent a server
hello message to the client that includes details about the cipher suit that the server has chosen
from the provided list sent by the client in client hello message. Once this is accepted, that particular
cipher key is chosen in the overall communication proses [6].
2.2. The role of symmetric encryption and hash algorithms in SSL communication
In SSL communication, symmetric encryption provides two keys that are efficient in performing data
encryption. These keys are symmetric of nature means both of these keys are able to encrypt as well
as decrypt data [7].
In SSL, communication hash algorithm is applied to generate a signature for SSL certificate
2.3. The VPN client software options
The Microsoft VPN Client for Windows
Cisco VPN
Nord VPN
Express VPN

8
APPLICATION OF SSL/VPN
NCP Secure Entry Client for Win32/64
OpenVPN 2.4.3
2.4. The Support for simultaneous users at VPN
VPN provides support for connection for simultaneous users for a single VPN subscription. Although
connection of speed and performance depends on a VPN service provider, most VPN services allow
to login to the service from different user account. Hence it does not require to purchase different
VPN services for different users for a single subscription.
3. Anti-Replay
3.1. Procedure to mitigate the anti-replay attacks in SSL communication
In replay attack, attackers or cyber-criminals often get hold of the network. Then communication
over the network is intercepted. Hackers then might resend it as well for confusing receivers.
Hackers do this, to convince revivers into doing something that hackers want them to do. What
makes this technique even more dangerous is that it does not require expertise to execute this type
of techniques [8]. Once the message is collected from, the network is it is easy to decrypt and it does
not require expertise for this.
In order to protect information while communicating through an SSL based channel, message
authentication code or MAC is generated. It provides protection for the SSL based communication
channel itself. This code is produced with the help of mac secret and a sequence number. This makes
it difficult for hackers to intercept message easily and then decrypt that with simple tools [3]. This
security mechanism provided by MAC is what ensures the integrity of data.
3.2. Procedure to protect organization against SSL attacks
Integration of HTTPS protocol with website instead of HTTP
Integrating HTTP strict transport security or HSTS which ensures that browsers only
communicate through connections that are only secured with HTTPS
Applying 256 bit encryption instead of 32 or 64 and 128 bit encryption too
Cipher suits that are weak is disabled or avoided
Conclusion:
This report has analysed importance of VPN for organisations to secure data over a network. As VPN
encrypts data that is communicated through a network, it enhances data security. Though SSL and
IPSEC, both offers VPN service, SSL based VPN provides better security than IPSEC based VPN. SSL
based VPN provides access control while communication between web browser and server takes
APPLICATION OF SSL/VPN
NCP Secure Entry Client for Win32/64
OpenVPN 2.4.3
2.4. The Support for simultaneous users at VPN
VPN provides support for connection for simultaneous users for a single VPN subscription. Although
connection of speed and performance depends on a VPN service provider, most VPN services allow
to login to the service from different user account. Hence it does not require to purchase different
VPN services for different users for a single subscription.
3. Anti-Replay
3.1. Procedure to mitigate the anti-replay attacks in SSL communication
In replay attack, attackers or cyber-criminals often get hold of the network. Then communication
over the network is intercepted. Hackers then might resend it as well for confusing receivers.
Hackers do this, to convince revivers into doing something that hackers want them to do. What
makes this technique even more dangerous is that it does not require expertise to execute this type
of techniques [8]. Once the message is collected from, the network is it is easy to decrypt and it does
not require expertise for this.
In order to protect information while communicating through an SSL based channel, message
authentication code or MAC is generated. It provides protection for the SSL based communication
channel itself. This code is produced with the help of mac secret and a sequence number. This makes
it difficult for hackers to intercept message easily and then decrypt that with simple tools [3]. This
security mechanism provided by MAC is what ensures the integrity of data.
3.2. Procedure to protect organization against SSL attacks
Integration of HTTPS protocol with website instead of HTTP
Integrating HTTP strict transport security or HSTS which ensures that browsers only
communicate through connections that are only secured with HTTPS
Applying 256 bit encryption instead of 32 or 64 and 128 bit encryption too
Cipher suits that are weak is disabled or avoided
Conclusion:
This report has analysed importance of VPN for organisations to secure data over a network. As VPN
encrypts data that is communicated through a network, it enhances data security. Though SSL and
IPSEC, both offers VPN service, SSL based VPN provides better security than IPSEC based VPN. SSL
based VPN provides access control while communication between web browser and server takes
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
APPLICATION OF SSL/VPN
place. It also provides techniques to authenticate a communication between server and client. Data
encryption service provided by SSL/VPN includes digital signature, which increases security of digital
data and makes it difficult to decrypt original data. SSL/VPN also provides data confidentiality and
data authenticity during communication. Along with that, SSL/VPN provides measures and
techniques to ensure anti-replay so that it is difficult for the hackers to decrypt data during
communication for enhanced security against cyber-crime.
APPLICATION OF SSL/VPN
place. It also provides techniques to authenticate a communication between server and client. Data
encryption service provided by SSL/VPN includes digital signature, which increases security of digital
data and makes it difficult to decrypt original data. SSL/VPN also provides data confidentiality and
data authenticity during communication. Along with that, SSL/VPN provides measures and
techniques to ensure anti-replay so that it is difficult for the hackers to decrypt data during
communication for enhanced security against cyber-crime.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
APPLICATION OF SSL/VPN
References:
[1] "IBM Knowledge Center", Ibm.com, 2019. [Online]. Available:
https://www.ibm.com/support/knowledgecenter/en/SSRMWJ_6.0.0.13/com.ibm.isim.doc/
securing/tsk/tsk_ic_security_ssl_itim_test.htm. [Accessed: 29- Apr- 2019].
[2] A. Moradi, A. Lodi and S. Hashemi, "On the difficulty of virtual private network instances",
Networks, vol. 63, no. 4, pp. 327-333, 2014. Available: 10.1002/net.21548.
[3] B. Rajkumar and G. Narsimha, "Trust Based Certificate Revocation for Secure Routing in MANET",
Procedia Computer Science, vol. 92, pp. 431-441, 2016. Available: 10.1016/j.procs.2016.07.334.
[4] "Bot Net Detection by Using SSL Encryption", International Journal of Research and Applications,
vol. 2, no. 6, pp. 275-277, 2015. Available: 10.17812/ijra.2.6(49)2015.
[5] M. Alnatheer, "Secure Socket Layer (SSL) Impact on Web Server Performance", Journal of
Advances in Computer Networks, vol. 2, no. 3, pp. 211-217, 2014. Available:
10.7763/jacn.2014.v2.114.
[6] S. Homayoun, A. Jalili and M. Keshtgari, "Performance Analysis of Multiple Virtualized Servers",
Computer Engineering and Applications Journal, vol. 4, no. 3, pp. 183-188, 2015. Available:
10.18495/comengapp.v4i3.150.
[7] H. Redzovic, A. Smiljanic and B. Savic, "Performance evaluation of software routers with VPN
features", Telfor Journal, vol. 9, no. 2, pp. 74-79, 2017. Available: 10.5937/telfor1702074r.
[8] "SSL VPN Security", Cisco, 2019. [Online]. Available:
https://www.cisco.com/c/en/us/about/security-center/ssl-vpn-security.html. [Accessed: 30- Apr-
2019].
APPLICATION OF SSL/VPN
References:
[1] "IBM Knowledge Center", Ibm.com, 2019. [Online]. Available:
https://www.ibm.com/support/knowledgecenter/en/SSRMWJ_6.0.0.13/com.ibm.isim.doc/
securing/tsk/tsk_ic_security_ssl_itim_test.htm. [Accessed: 29- Apr- 2019].
[2] A. Moradi, A. Lodi and S. Hashemi, "On the difficulty of virtual private network instances",
Networks, vol. 63, no. 4, pp. 327-333, 2014. Available: 10.1002/net.21548.
[3] B. Rajkumar and G. Narsimha, "Trust Based Certificate Revocation for Secure Routing in MANET",
Procedia Computer Science, vol. 92, pp. 431-441, 2016. Available: 10.1016/j.procs.2016.07.334.
[4] "Bot Net Detection by Using SSL Encryption", International Journal of Research and Applications,
vol. 2, no. 6, pp. 275-277, 2015. Available: 10.17812/ijra.2.6(49)2015.
[5] M. Alnatheer, "Secure Socket Layer (SSL) Impact on Web Server Performance", Journal of
Advances in Computer Networks, vol. 2, no. 3, pp. 211-217, 2014. Available:
10.7763/jacn.2014.v2.114.
[6] S. Homayoun, A. Jalili and M. Keshtgari, "Performance Analysis of Multiple Virtualized Servers",
Computer Engineering and Applications Journal, vol. 4, no. 3, pp. 183-188, 2015. Available:
10.18495/comengapp.v4i3.150.
[7] H. Redzovic, A. Smiljanic and B. Savic, "Performance evaluation of software routers with VPN
features", Telfor Journal, vol. 9, no. 2, pp. 74-79, 2017. Available: 10.5937/telfor1702074r.
[8] "SSL VPN Security", Cisco, 2019. [Online]. Available:
https://www.cisco.com/c/en/us/about/security-center/ssl-vpn-security.html. [Accessed: 30- Apr-
2019].
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




