BN305 Virtual Private Networks: Exploring Technologies & Security
VerifiedAdded on 2023/04/21
|14
|701
|165
Report
AI Summary
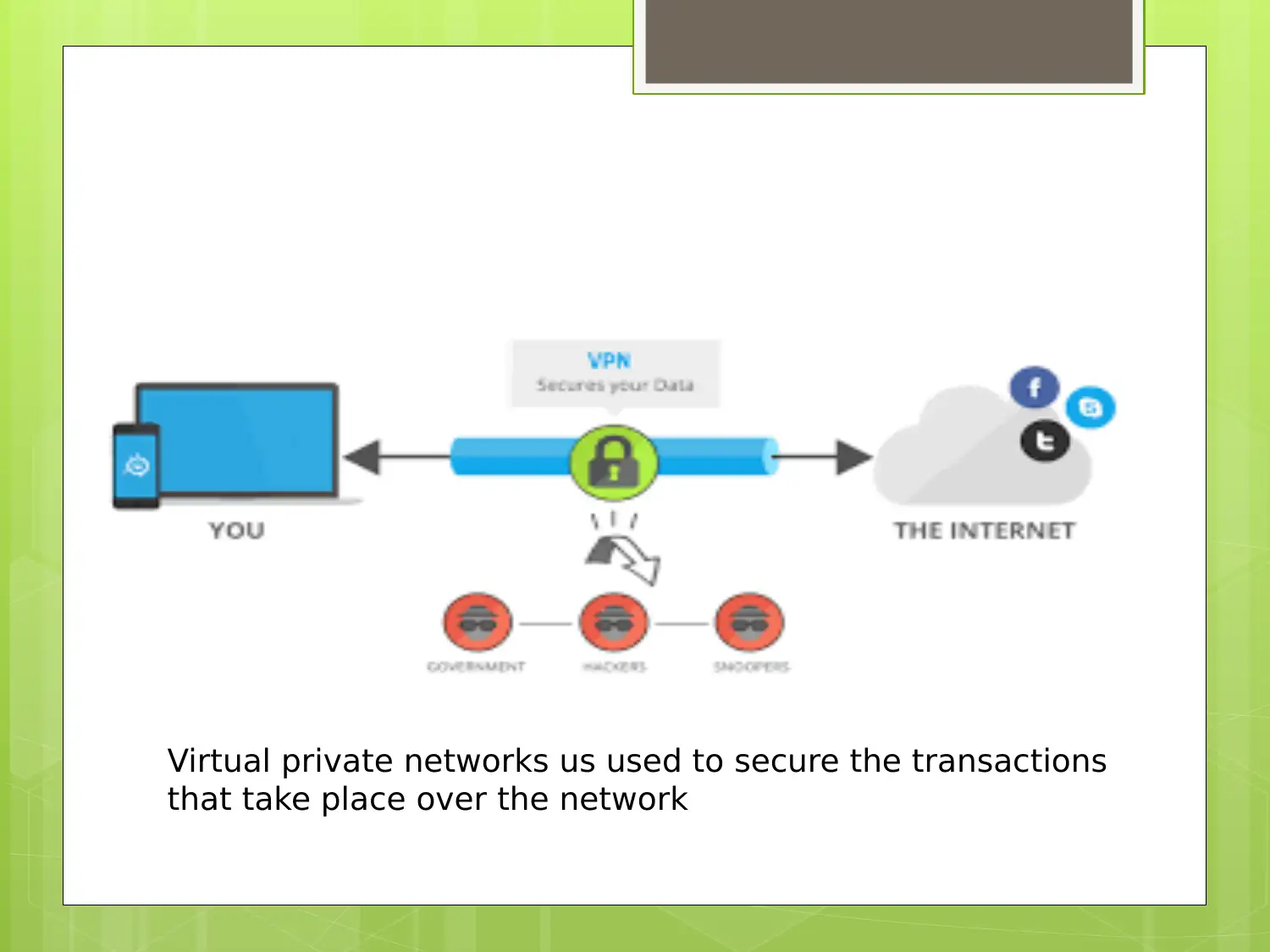
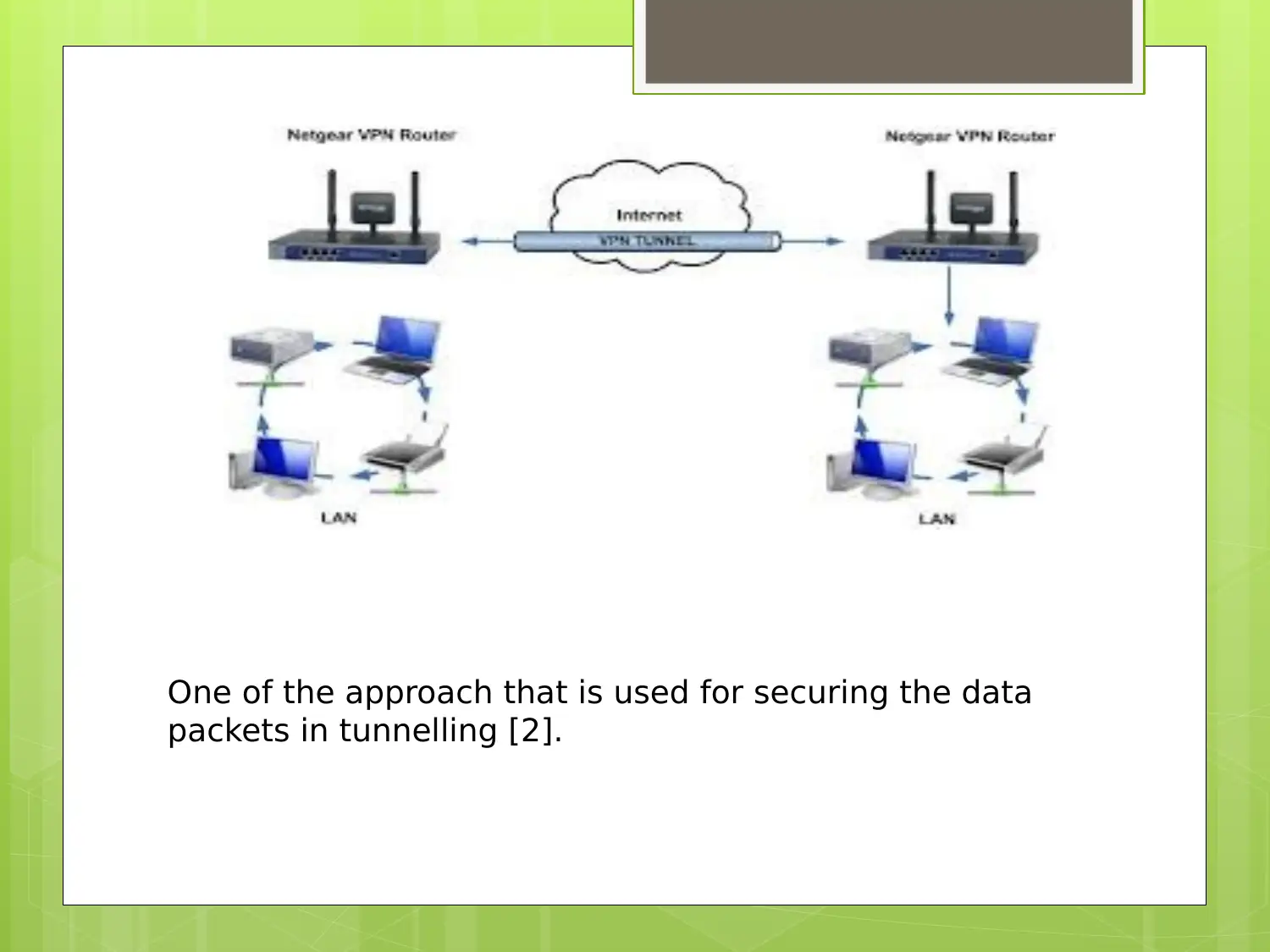
This report provides an overview of Virtual Private Network (VPN) technology, tracing its history back to 1996 and the development of PPTP. It highlights the use of VPNs for secure data transmission over public networks, emphasizing their role in establishing secure point-to-point connections and data encryption. The report also addresses the challenges and drawbacks of VPN implementation, including the need for advanced technical understanding and potential security vulnerabilities in wireless connections. It further explores the scope of VPNs in reducing security breaches and unauthorized network access, along with future research areas such as open-source projects, protocol obfuscation, and network access control. The report concludes by emphasizing the growing importance of VPNs and their potential to replace traditional firewalls, while also noting the current limitations related to network security understanding and configuration.
1 out of 14















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)