Advanced Network Design: Excelfior Company Network Redesign - BN321
VerifiedAdded on 2023/06/04
|7
|1377
|434
Report
AI Summary
This report presents an advanced network design solution for Excelfior Company, a Melbourne-based digital communication firm specializing in website design, hosting, and management. The project addresses the company's need for a secure and scalable network due to existing network issues. The solution involves gathering requirements using a top-down methodology, focusing on business and technical needs, and proposing a network design utilizing Cisco devices for cost-effectiveness and scalability. Key performance metrics such as latency, bandwidth, throughput, and uptime are considered to ensure optimal network performance. The report outlines the current network's limitations and the proposed design's advantages in providing a reliable and secure network infrastructure for Excelfior Company, aiming to accommodate their network load for the next five years. Desklib provides access to this and many other solved assignments for students.

Advanced Network Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Project Objective...............................................................................................................2
2 Task - 1 Requirement Gathering.....................................................................................2
2.1 Questionnaire.............................................................................................................2
2.2 Technique used for collecting the requirements.....................................................3
3 Task - 2 Network Design..................................................................................................4
3.1 Performance Metrics.................................................................................................4
4 References..........................................................................................................................6
1
1 Project Objective...............................................................................................................2
2 Task - 1 Requirement Gathering.....................................................................................2
2.1 Questionnaire.............................................................................................................2
2.2 Technique used for collecting the requirements.....................................................3
3 Task - 2 Network Design..................................................................................................4
3.1 Performance Metrics.................................................................................................4
4 References..........................................................................................................................6
1

1 Project Objective
This project is used to create the effective and secure network design for Excelfior
Company. This company is located at Melbourne and it based on digital communication
company. It specialises in designing, hosting and managing the corporate websites. This
company has admin, marketing, finance and accounts departments and also has the set of
frond and back end developers and flash designers. But, the current network is does not
provides the secure network and it has lot of network issues. So, this company decided to
rebuild their overall network to provide the effective and scalable network for a company.
Although, user needs to rebuild, manage and operate the new, secure and domain based
network system for Excelfior Company. The proposed network design should be provide the
scalable and effective network design by use the latest technologies which is used to
accommodate their network load now and another five years. First, user needs to gather the
requirements for rebuild the overall network and identify the technique used for collecting the
requirement and create the network design with performance metrics. These are will be
discussed and analysed in detail.
2 Task - 1 Requirement Gathering
Outlining adaptable system frameworks to meet the present great business and IT needs
and patterns is an incredible assignment, paying little respect to whether it is an endeavour or
community sort of framework. This is especially evident when the framework was proposed
for advances and necessities huge years earlier and the business grasps new IT developments
to energize the achievement of its goals yet the business' present framework was not expected
to address these new advances' essentials. Thusly, to achieve the wanted for target of a given
layout, the framework fashioner must hold a procedure that handles the arrangement in a
sorted out way [1].
2.1 Questionnaire
What tasks would the client like to automate or make more efficient?
How important is network security?
What business applications does the client need to support?
Does the client have an existing network, and what is its function?
What is the estimated size of the network?
2
This project is used to create the effective and secure network design for Excelfior
Company. This company is located at Melbourne and it based on digital communication
company. It specialises in designing, hosting and managing the corporate websites. This
company has admin, marketing, finance and accounts departments and also has the set of
frond and back end developers and flash designers. But, the current network is does not
provides the secure network and it has lot of network issues. So, this company decided to
rebuild their overall network to provide the effective and scalable network for a company.
Although, user needs to rebuild, manage and operate the new, secure and domain based
network system for Excelfior Company. The proposed network design should be provide the
scalable and effective network design by use the latest technologies which is used to
accommodate their network load now and another five years. First, user needs to gather the
requirements for rebuild the overall network and identify the technique used for collecting the
requirement and create the network design with performance metrics. These are will be
discussed and analysed in detail.
2 Task - 1 Requirement Gathering
Outlining adaptable system frameworks to meet the present great business and IT needs
and patterns is an incredible assignment, paying little respect to whether it is an endeavour or
community sort of framework. This is especially evident when the framework was proposed
for advances and necessities huge years earlier and the business grasps new IT developments
to energize the achievement of its goals yet the business' present framework was not expected
to address these new advances' essentials. Thusly, to achieve the wanted for target of a given
layout, the framework fashioner must hold a procedure that handles the arrangement in a
sorted out way [1].
2.1 Questionnaire
What tasks would the client like to automate or make more efficient?
How important is network security?
What business applications does the client need to support?
Does the client have an existing network, and what is its function?
What is the estimated size of the network?
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
How many users will the network service?
What types of external connections will the network need?
2.2 Technique used for collecting the requirements
There are two normal ways to deal with examine and configuration systems:
Top down methodology
Bottom up methodology
Here, we are using top down methodology.
The top down system approach enhances the layout strategy by part the arrangement
errands to make it more based on the diagram scope and performed in a more controlled
manner, which can finally help compose modellers to see organize plan courses of action
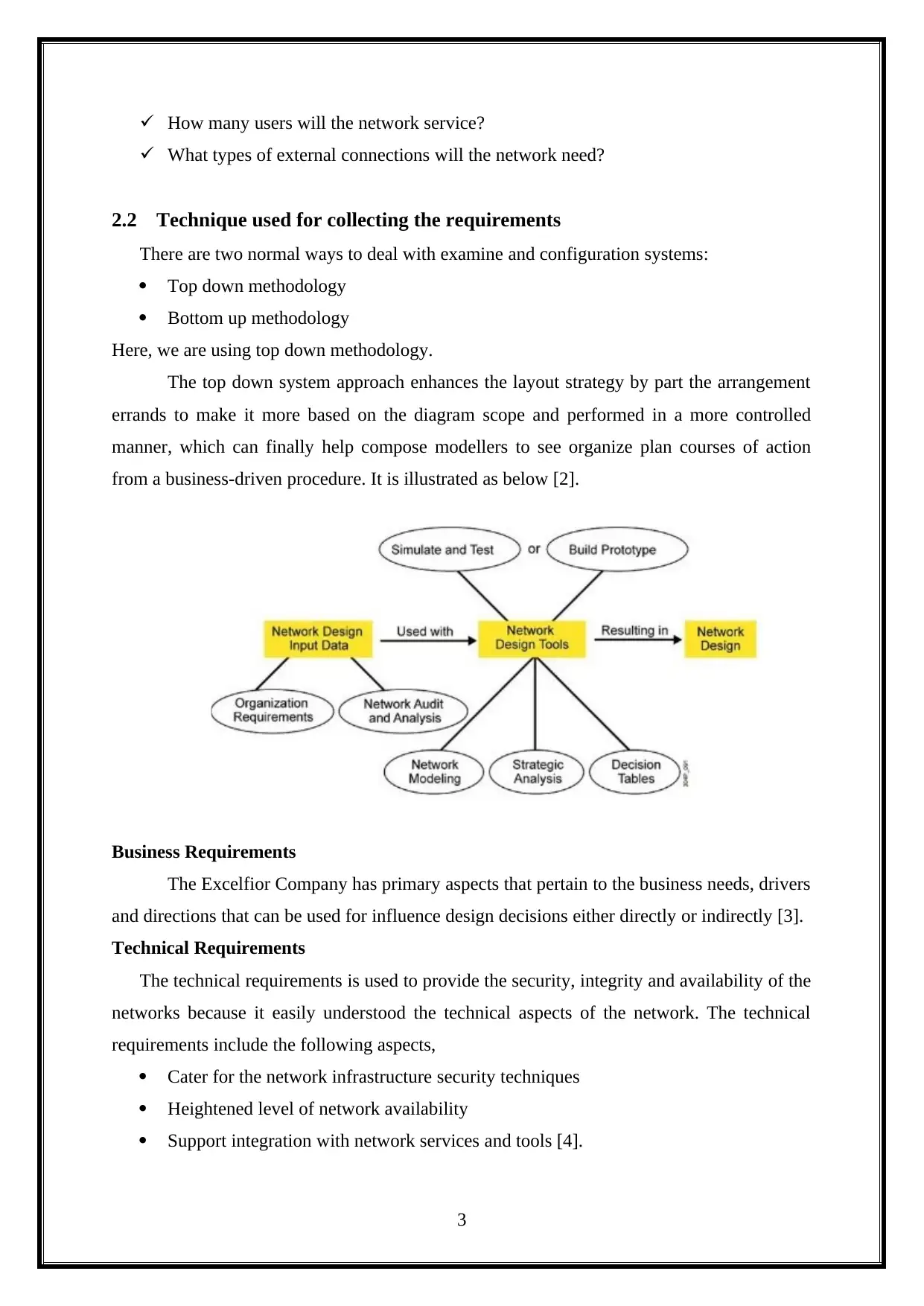
from a business-driven procedure. It is illustrated as below [2].
Business Requirements
The Excelfior Company has primary aspects that pertain to the business needs, drivers
and directions that can be used for influence design decisions either directly or indirectly [3].
Technical Requirements
The technical requirements is used to provide the security, integrity and availability of the
networks because it easily understood the technical aspects of the network. The technical
requirements include the following aspects,
Cater for the network infrastructure security techniques
Heightened level of network availability
Support integration with network services and tools [4].
3
What types of external connections will the network need?
2.2 Technique used for collecting the requirements
There are two normal ways to deal with examine and configuration systems:
Top down methodology
Bottom up methodology
Here, we are using top down methodology.
The top down system approach enhances the layout strategy by part the arrangement
errands to make it more based on the diagram scope and performed in a more controlled
manner, which can finally help compose modellers to see organize plan courses of action
from a business-driven procedure. It is illustrated as below [2].
Business Requirements
The Excelfior Company has primary aspects that pertain to the business needs, drivers
and directions that can be used for influence design decisions either directly or indirectly [3].
Technical Requirements
The technical requirements is used to provide the security, integrity and availability of the
networks because it easily understood the technical aspects of the network. The technical
requirements include the following aspects,
Cater for the network infrastructure security techniques
Heightened level of network availability
Support integration with network services and tools [4].
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
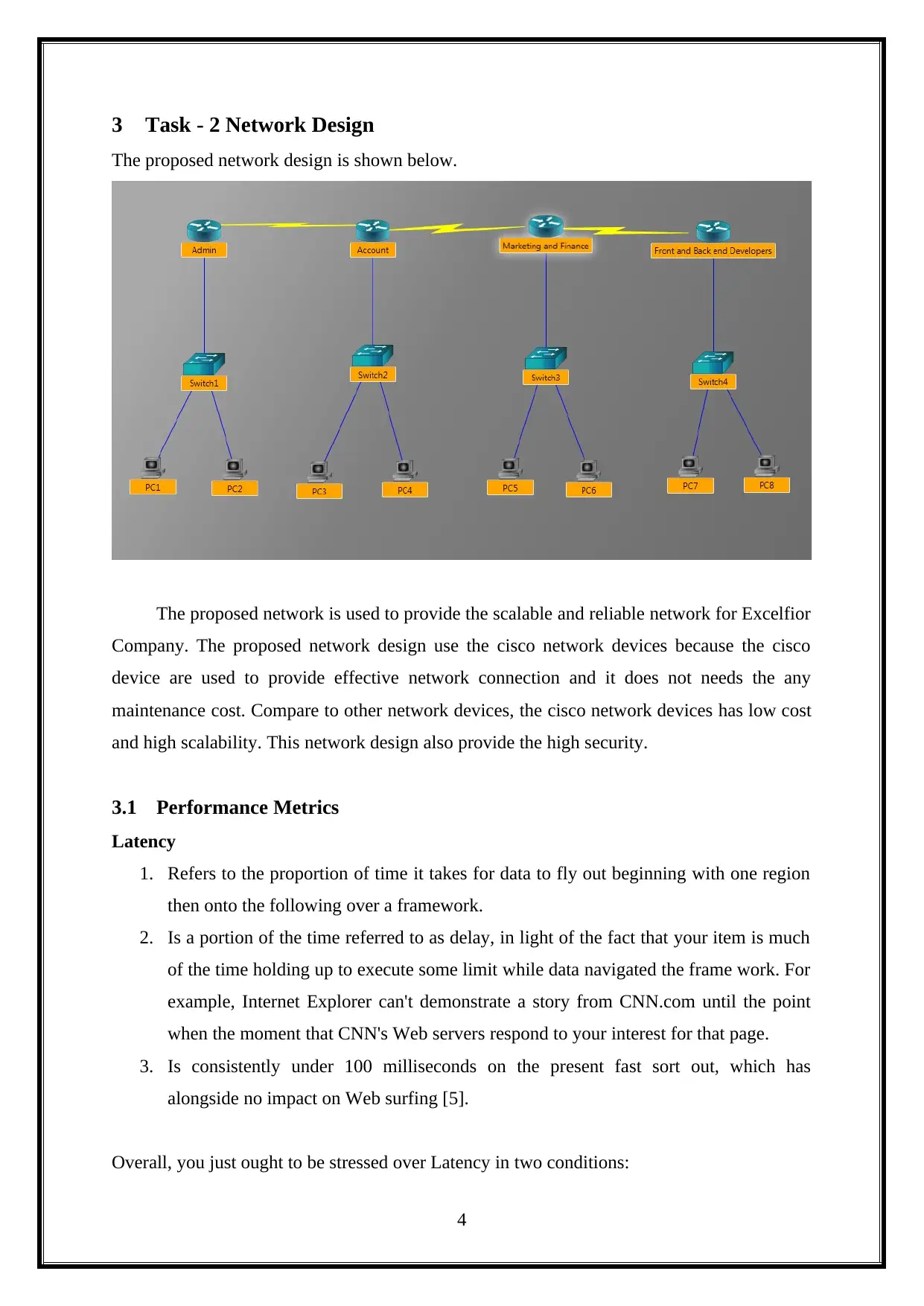
3 Task - 2 Network Design
The proposed network design is shown below.
The proposed network is used to provide the scalable and reliable network for Excelfior
Company. The proposed network design use the cisco network devices because the cisco
device are used to provide effective network connection and it does not needs the any
maintenance cost. Compare to other network devices, the cisco network devices has low cost
and high scalability. This network design also provide the high security.
3.1 Performance Metrics
Latency
1. Refers to the proportion of time it takes for data to fly out beginning with one region
then onto the following over a framework.
2. Is a portion of the time referred to as delay, in light of the fact that your item is much
of the time holding up to execute some limit while data navigated the frame work. For
example, Internet Explorer can't demonstrate a story from CNN.com until the point
when the moment that CNN's Web servers respond to your interest for that page.
3. Is consistently under 100 milliseconds on the present fast sort out, which has
alongside no impact on Web surfing [5].
Overall, you just ought to be stressed over Latency in two conditions:
4
The proposed network design is shown below.
The proposed network is used to provide the scalable and reliable network for Excelfior
Company. The proposed network design use the cisco network devices because the cisco
device are used to provide effective network connection and it does not needs the any
maintenance cost. Compare to other network devices, the cisco network devices has low cost
and high scalability. This network design also provide the high security.
3.1 Performance Metrics
Latency
1. Refers to the proportion of time it takes for data to fly out beginning with one region
then onto the following over a framework.
2. Is a portion of the time referred to as delay, in light of the fact that your item is much
of the time holding up to execute some limit while data navigated the frame work. For
example, Internet Explorer can't demonstrate a story from CNN.com until the point
when the moment that CNN's Web servers respond to your interest for that page.
3. Is consistently under 100 milliseconds on the present fast sort out, which has
alongside no impact on Web surfing [5].
Overall, you just ought to be stressed over Latency in two conditions:
4

At the point when your staff and advocates whimper about a direct affiliation, high
Latency could be a bit of the issue, anyway you presumably won't have the ability to
make a move other than contact your ISP and demand that they address the issue.
Second, on the off chance that you're aiming to present Voice over IP (VoIP) or
whatever other application that relies upon live, continuous transmission of video or
sound, you need to get some data about their lethargy. Ongoing voice and video
applications are unstable to arrange delays. For instance, with VoIP, you'll see that the
sound is uneven, with heaps of stops and dropped syllables. Jitter suggests assortment
in the proportion of Latency, and it has a relative negative impact on ongoing
correspondence.
Data transmission and throughput
These two terms are now and again used on the other hand, and anyway they are
associated, they're not precisely the same. On multi day-to-day commence, you'll generally
watch them checked in Kbps (kilobits consistently), Mbps (megabits consistently) or Gbps
(gigabits consistently). Exchange speed generally suggests a speculative most noteworthy,
while throughput is a real-world, convenient estimation. The refinement is critical in light of
the way that ISPs will as a rule advance their information exchange limit, which is as often as
possible higher than the throughput that you'll truly get. In various settings, you'll see the
terms transmission limit, throughput and speed used then again.
Uptime or responsiveness
Uptime, all over alluded to as availability or responsiveness, insinuates the proportion
of time that a PC or a framework affiliation is working and usable.
5
Latency could be a bit of the issue, anyway you presumably won't have the ability to
make a move other than contact your ISP and demand that they address the issue.
Second, on the off chance that you're aiming to present Voice over IP (VoIP) or
whatever other application that relies upon live, continuous transmission of video or
sound, you need to get some data about their lethargy. Ongoing voice and video
applications are unstable to arrange delays. For instance, with VoIP, you'll see that the
sound is uneven, with heaps of stops and dropped syllables. Jitter suggests assortment
in the proportion of Latency, and it has a relative negative impact on ongoing
correspondence.
Data transmission and throughput
These two terms are now and again used on the other hand, and anyway they are
associated, they're not precisely the same. On multi day-to-day commence, you'll generally
watch them checked in Kbps (kilobits consistently), Mbps (megabits consistently) or Gbps
(gigabits consistently). Exchange speed generally suggests a speculative most noteworthy,
while throughput is a real-world, convenient estimation. The refinement is critical in light of
the way that ISPs will as a rule advance their information exchange limit, which is as often as
possible higher than the throughput that you'll truly get. In various settings, you'll see the
terms transmission limit, throughput and speed used then again.
Uptime or responsiveness
Uptime, all over alluded to as availability or responsiveness, insinuates the proportion
of time that a PC or a framework affiliation is working and usable.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4 References
[1]"Determining Your Networking Requirements > Introduction to Cisco Network
Design", Ciscopress.com, 2018. [Online]. Available:
http://www.ciscopress.com/articles/article.asp?p=25259&seqNum=6. [Accessed: 24-
Sep- 2018].
[2]"Network Performance Metrics Defined | TechSoup for
Libraries", Techsoupforlibraries.org, 2018. [Online]. Available:
http://www.techsoupforlibraries.org/planning-for-success/networking-and-security/
tools/network-performance-metrics-defined. [Accessed: 24- Sep- 2018].
[3]"Network Design Requirements: Analysis and Design Principles", Community.cisco.com,
2018. [Online]. Available:
https://community.cisco.com/legacyfs/online/ccde_9781587144615_chapter1.pdf.
[Accessed: 24- Sep- 2018].
[4]"Gathering Network Requirements", Ptgmedia.pearsoncmg.com, 2018. [Online].
Available: http://ptgmedia.pearsoncmg.com/imprint_downloads/cisco/irc/prepubchaps/
2125_ch02.pdf. [Accessed: 24- Sep- 2018].
[5]J. Deng, "Requirements Analysis", 2018. [Online]. Available: https://piazza-
resources.s3.amazonaws.com/ibj403np9hm2dm/idy6qkk4y903yx/L15_req1nup.pdf?X-
Amz-. [Accessed: 31- Aug- 2015].
6
[1]"Determining Your Networking Requirements > Introduction to Cisco Network
Design", Ciscopress.com, 2018. [Online]. Available:
http://www.ciscopress.com/articles/article.asp?p=25259&seqNum=6. [Accessed: 24-
Sep- 2018].
[2]"Network Performance Metrics Defined | TechSoup for
Libraries", Techsoupforlibraries.org, 2018. [Online]. Available:
http://www.techsoupforlibraries.org/planning-for-success/networking-and-security/
tools/network-performance-metrics-defined. [Accessed: 24- Sep- 2018].
[3]"Network Design Requirements: Analysis and Design Principles", Community.cisco.com,
2018. [Online]. Available:
https://community.cisco.com/legacyfs/online/ccde_9781587144615_chapter1.pdf.
[Accessed: 24- Sep- 2018].
[4]"Gathering Network Requirements", Ptgmedia.pearsoncmg.com, 2018. [Online].
Available: http://ptgmedia.pearsoncmg.com/imprint_downloads/cisco/irc/prepubchaps/
2125_ch02.pdf. [Accessed: 24- Sep- 2018].
[5]J. Deng, "Requirements Analysis", 2018. [Online]. Available: https://piazza-
resources.s3.amazonaws.com/ibj403np9hm2dm/idy6qkk4y903yx/L15_req1nup.pdf?X-
Amz-. [Accessed: 31- Aug- 2015].
6
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




