MN502: Analysis of Botnet Threats and Mitigation Techniques
VerifiedAdded on 2022/09/18
|12
|2283
|21
Report
AI Summary
This report provides a comprehensive overview of botnets, exploring their structure, operation, and the significant threats they pose to network security. It begins by defining botnets and their impact, then delves into various botnet variants, including IRC, P2P, and hybrid models, detailing their architectures and communication methods. The report identifies key threats, such as DDoS attacks, traffic monitoring, spamming, and keylogging. Furthermore, it examines various mitigation techniques, including distributed asset management and patch management systems. The report analyzes real-world botnet attacks like Mirai, Methbot, and 3ve, illustrating their impact. Finally, it concludes by emphasizing the harmful effects of botnets and the importance of security measures to protect sensitive data.

Running head: OVERVIEW OF NETWORK SECURITY
OVERVIEW OF NETWORK SECURITY
Name of the Student
Name of the University
Author Note
OVERVIEW OF NETWORK SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OVERVIEW OF NETWORK SECURITY 1
Table of Contents
Introduction:...............................................................................................................................3
Variants of botnet:......................................................................................................................3
Peer to peer botnet:.................................................................................................................3
IRC botnet:.............................................................................................................................4
Hybrid botnet:........................................................................................................................5
Botnet architecture:....................................................................................................................6
Botnet operations and communication:......................................................................................7
Threats of Botnet:.......................................................................................................................7
DDoS attack:..........................................................................................................................7
Traffic monitoring and spamming:........................................................................................7
Keylogging:............................................................................................................................8
Mitigation techniques:................................................................................................................8
Distributed and Separated assets:...........................................................................................8
Patch systems for preventing Dos and other Exploits:...........................................................8
Botnet attacks:............................................................................................................................9
Mirai attack:...........................................................................................................................9
Methbot attack:.......................................................................................................................9
3ve attack:..............................................................................................................................9
Conclusion:................................................................................................................................9
Table of Contents
Introduction:...............................................................................................................................3
Variants of botnet:......................................................................................................................3
Peer to peer botnet:.................................................................................................................3
IRC botnet:.............................................................................................................................4
Hybrid botnet:........................................................................................................................5
Botnet architecture:....................................................................................................................6
Botnet operations and communication:......................................................................................7
Threats of Botnet:.......................................................................................................................7
DDoS attack:..........................................................................................................................7
Traffic monitoring and spamming:........................................................................................7
Keylogging:............................................................................................................................8
Mitigation techniques:................................................................................................................8
Distributed and Separated assets:...........................................................................................8
Patch systems for preventing Dos and other Exploits:...........................................................8
Botnet attacks:............................................................................................................................9
Mirai attack:...........................................................................................................................9
Methbot attack:.......................................................................................................................9
3ve attack:..............................................................................................................................9
Conclusion:................................................................................................................................9

2OVERVIEW OF NETWORK SECURITY
References:...............................................................................................................................11
Introduction:
The botnet is actually a group of computers that are connected in the coordinated
fashion. Each of the computers in the botnet is known as a bot. All of the bots are able to
form a network of computers that are compromised. The computers are fully controlled by
one of the third parties as well as used for transmitting spam or malware or for launching
attacks. The botnet can also know as the zombie army [1]. The impact of botnet on the users
can be both indirectly and directly. At present most of the people are storing data and
contains that are highly sensitive like legal or financial details. With the impact of botnet, the
sensitive and confidential information and data can be becoming vulnerable. This is also a big
problem that if any device belongs to government or company, the impact of botnet can harm
confidential and sensitive data of the organisation. The purpose of this paper is to discuss
about botnet, its impact, architecture, mitigation techniques and at last the paper will provide
a brief conclusion based on the entire paper.
Variants of botnet:
There are so many variations of botnet. Basically, there are four types of botnets on the basis
of C&C channels which are as per following:
i. IRC (Internet Relay Chat) botnet
P2P (Peer to Peer) botnet
ii. HTTP (Hyper Text Transfer protocol) botnet
iii. Hybrid botnet.
References:...............................................................................................................................11
Introduction:
The botnet is actually a group of computers that are connected in the coordinated
fashion. Each of the computers in the botnet is known as a bot. All of the bots are able to
form a network of computers that are compromised. The computers are fully controlled by
one of the third parties as well as used for transmitting spam or malware or for launching
attacks. The botnet can also know as the zombie army [1]. The impact of botnet on the users
can be both indirectly and directly. At present most of the people are storing data and
contains that are highly sensitive like legal or financial details. With the impact of botnet, the
sensitive and confidential information and data can be becoming vulnerable. This is also a big
problem that if any device belongs to government or company, the impact of botnet can harm
confidential and sensitive data of the organisation. The purpose of this paper is to discuss
about botnet, its impact, architecture, mitigation techniques and at last the paper will provide
a brief conclusion based on the entire paper.
Variants of botnet:
There are so many variations of botnet. Basically, there are four types of botnets on the basis
of C&C channels which are as per following:
i. IRC (Internet Relay Chat) botnet
P2P (Peer to Peer) botnet
ii. HTTP (Hyper Text Transfer protocol) botnet
iii. Hybrid botnet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3OVERVIEW OF NETWORK SECURITY
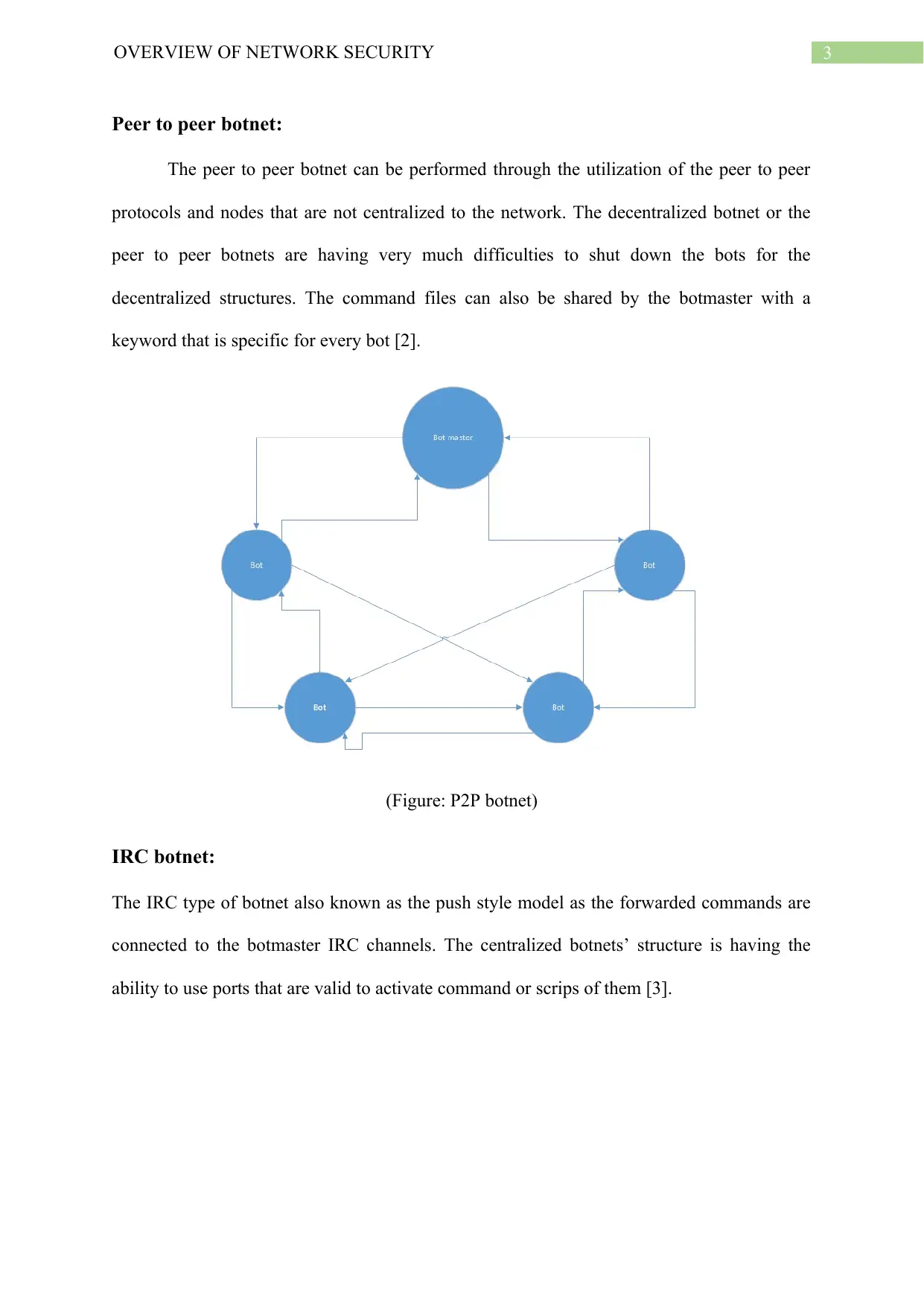
Peer to peer botnet:
The peer to peer botnet can be performed through the utilization of the peer to peer
protocols and nodes that are not centralized to the network. The decentralized botnet or the
peer to peer botnets are having very much difficulties to shut down the bots for the
decentralized structures. The command files can also be shared by the botmaster with a
keyword that is specific for every bot [2].
(Figure: P2P botnet)
IRC botnet:
The IRC type of botnet also known as the push style model as the forwarded commands are
connected to the botmaster IRC channels. The centralized botnets’ structure is having the
ability to use ports that are valid to activate command or scrips of them [3].
Peer to peer botnet:
The peer to peer botnet can be performed through the utilization of the peer to peer
protocols and nodes that are not centralized to the network. The decentralized botnet or the
peer to peer botnets are having very much difficulties to shut down the bots for the
decentralized structures. The command files can also be shared by the botmaster with a
keyword that is specific for every bot [2].
(Figure: P2P botnet)
IRC botnet:
The IRC type of botnet also known as the push style model as the forwarded commands are
connected to the botmaster IRC channels. The centralized botnets’ structure is having the
ability to use ports that are valid to activate command or scrips of them [3].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4OVERVIEW OF NETWORK SECURITY
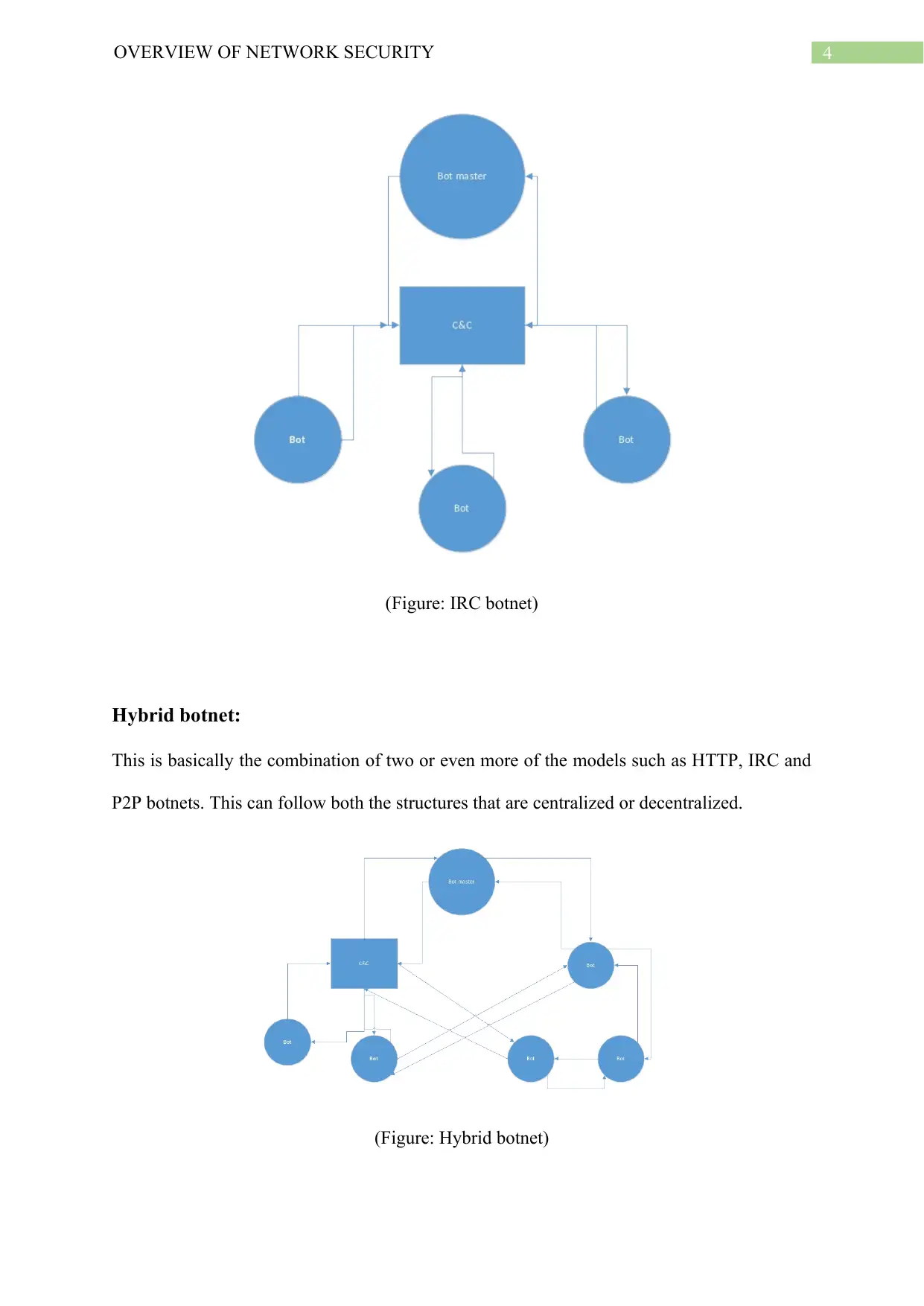
(Figure: IRC botnet)
Hybrid botnet:
This is basically the combination of two or even more of the models such as HTTP, IRC and
P2P botnets. This can follow both the structures that are centralized or decentralized.
(Figure: Hybrid botnet)
(Figure: IRC botnet)
Hybrid botnet:
This is basically the combination of two or even more of the models such as HTTP, IRC and
P2P botnets. This can follow both the structures that are centralized or decentralized.
(Figure: Hybrid botnet)
5OVERVIEW OF NETWORK SECURITY
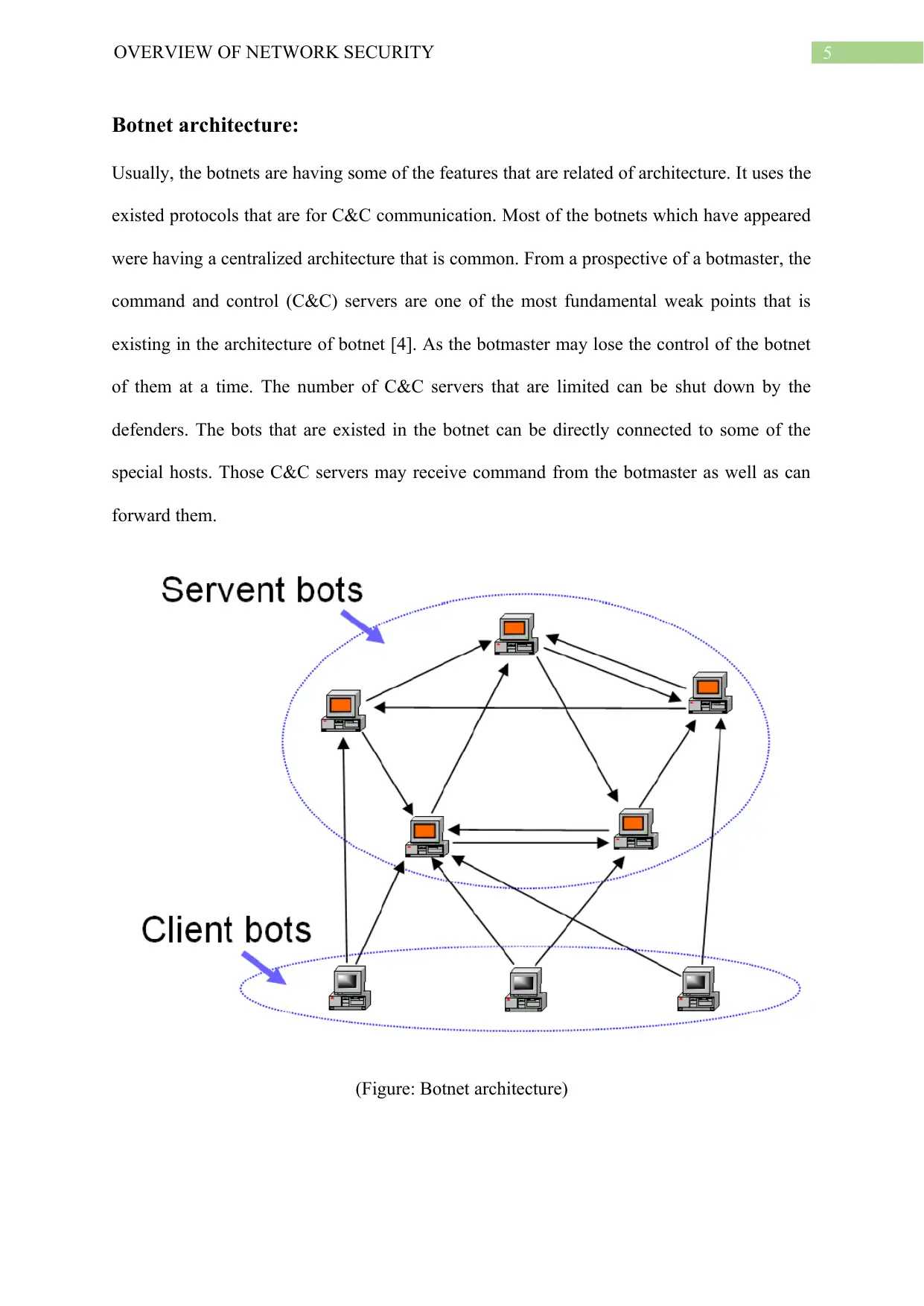
Botnet architecture:
Usually, the botnets are having some of the features that are related of architecture. It uses the
existed protocols that are for C&C communication. Most of the botnets which have appeared
were having a centralized architecture that is common. From a prospective of a botmaster, the
command and control (C&C) servers are one of the most fundamental weak points that is
existing in the architecture of botnet [4]. As the botmaster may lose the control of the botnet
of them at a time. The number of C&C servers that are limited can be shut down by the
defenders. The bots that are existed in the botnet can be directly connected to some of the
special hosts. Those C&C servers may receive command from the botmaster as well as can
forward them.
(Figure: Botnet architecture)
Botnet architecture:
Usually, the botnets are having some of the features that are related of architecture. It uses the
existed protocols that are for C&C communication. Most of the botnets which have appeared
were having a centralized architecture that is common. From a prospective of a botmaster, the
command and control (C&C) servers are one of the most fundamental weak points that is
existing in the architecture of botnet [4]. As the botmaster may lose the control of the botnet
of them at a time. The number of C&C servers that are limited can be shut down by the
defenders. The bots that are existed in the botnet can be directly connected to some of the
special hosts. Those C&C servers may receive command from the botmaster as well as can
forward them.
(Figure: Botnet architecture)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6OVERVIEW OF NETWORK SECURITY
A victim host could be infected through targeting the vulnerabilities that are known or even
by the programs that have got infected. At the time the hosts will be infected, the bots will get
the ability to utilize mechanisms which are to maintenance and control the hosts which are
infected such as NetBIOS and RPCDCOM. The scan of propagation can be done on the
single ports which are able to be accessed from the address ranges.
Botnet operations and communication:
The users can get the ability by the botnet that they will be able to execute a small list of
some of the commands that are simple which are including the ability to update as well as
remove the software that are downloaded as well as the machines which have got infected.
The machines and downloaded software have got the ability by the botnet that they will be
able to refine the machines that will execute the operating system or commands within a
given time. The botnets can take part in the illegal activities which can be the cause of traffic
in network which is totally unwanted [5]. The detection of removal of bots are such a task
that are so much important. The pattern of communication is basically the sequence of the
messages that are exchanged and needed for a specific scenario of communication.
Threats of Botnet:
DDoS attack:
A botnet may be utilized for a DDoS attack (Distributed denial of operations service) for
destroying the connectivity as well as services of a network. It can be done by over-burdening
the resources of computers or through consuming the victims’ bandwidth. The common most
attacks that are implemented are UDP flood and TCP SYN attacks. The DDoS attacks are
limited not only to the internet servers however this may be targeted to any of the services
that are connected to the web.
A victim host could be infected through targeting the vulnerabilities that are known or even
by the programs that have got infected. At the time the hosts will be infected, the bots will get
the ability to utilize mechanisms which are to maintenance and control the hosts which are
infected such as NetBIOS and RPCDCOM. The scan of propagation can be done on the
single ports which are able to be accessed from the address ranges.
Botnet operations and communication:
The users can get the ability by the botnet that they will be able to execute a small list of
some of the commands that are simple which are including the ability to update as well as
remove the software that are downloaded as well as the machines which have got infected.
The machines and downloaded software have got the ability by the botnet that they will be
able to refine the machines that will execute the operating system or commands within a
given time. The botnets can take part in the illegal activities which can be the cause of traffic
in network which is totally unwanted [5]. The detection of removal of bots are such a task
that are so much important. The pattern of communication is basically the sequence of the
messages that are exchanged and needed for a specific scenario of communication.
Threats of Botnet:
DDoS attack:
A botnet may be utilized for a DDoS attack (Distributed denial of operations service) for
destroying the connectivity as well as services of a network. It can be done by over-burdening
the resources of computers or through consuming the victims’ bandwidth. The common most
attacks that are implemented are UDP flood and TCP SYN attacks. The DDoS attacks are
limited not only to the internet servers however this may be targeted to any of the services
that are connected to the web.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7OVERVIEW OF NETWORK SECURITY
Traffic monitoring and spamming:
A bot can also be used like a sniffer that is for identifying the confidential and sensitive data
in the zombies or the machines that are infected [6]. This is also able to locate the competitor
type of botnets if they will be installed into the similar machines as well as it can also be
hijacked by the hackers. Some of the bots can offer for opening a socks V5/V4 proxy.
Keylogging:
This is becoming so much easy with the help of keylogger, for a botmaster that he can
retrieve the confidential and sensitive information, as well as they can steal the data too. By
utilizing the keylogger program, a hacker is able to gather only the type of keys which can
come in a sequence of words that are interesting such as Yahoo and PayPal.
Mitigation techniques:
To stop the attacks related to botnet or to mitigate them is a procedure that is multifaceted.
There are existed some aspects for the mitigation that will be having effect to the end users
and the roles of DevOps [7]. There are existed some of the techniques for mitigation they are
as follows:
Distributed and Separated assets:
The separated as well as distributed assets which are having existence in the networking to
make the botnets harder that they can attack. In general, the event management as well as the
security related information or the system that can do analytics can be used such as that they
can develop rules for filtering [8]. The users have been given allowance for studying the
aspects like payload, signatures, HTTP headers, origin IP addresses, JavaScript footprints as
well as cookies.
Traffic monitoring and spamming:
A bot can also be used like a sniffer that is for identifying the confidential and sensitive data
in the zombies or the machines that are infected [6]. This is also able to locate the competitor
type of botnets if they will be installed into the similar machines as well as it can also be
hijacked by the hackers. Some of the bots can offer for opening a socks V5/V4 proxy.
Keylogging:
This is becoming so much easy with the help of keylogger, for a botmaster that he can
retrieve the confidential and sensitive information, as well as they can steal the data too. By
utilizing the keylogger program, a hacker is able to gather only the type of keys which can
come in a sequence of words that are interesting such as Yahoo and PayPal.
Mitigation techniques:
To stop the attacks related to botnet or to mitigate them is a procedure that is multifaceted.
There are existed some aspects for the mitigation that will be having effect to the end users
and the roles of DevOps [7]. There are existed some of the techniques for mitigation they are
as follows:
Distributed and Separated assets:
The separated as well as distributed assets which are having existence in the networking to
make the botnets harder that they can attack. In general, the event management as well as the
security related information or the system that can do analytics can be used such as that they
can develop rules for filtering [8]. The users have been given allowance for studying the
aspects like payload, signatures, HTTP headers, origin IP addresses, JavaScript footprints as
well as cookies.

8OVERVIEW OF NETWORK SECURITY
Patch systems for preventing Dos and other Exploits:
This is including updates of software as well as security patches for the network firewalls as
well as for the routers, PCs, hardware, servers or some of the other workstations and devices
that are connected [9]. The users are required to change the default password of them as well
as they are also required to install the daily updates as well as security patches for mitigating
botnet attacks.
Botnet attacks:
Mirai attack:
The digital smart devices that were running on the basis of the ARC based processors were
infected by the Mirai attack that was happened in the year 2016 [10]. The attack was actually
done when the authors launched a DDoS attack in the web based server of them. From this
attack over 6 millions of devices were infected.
Methbot attack:
This attack is one of the hugest malwares ever. It was actually a digital based advertises. This
was acquired more than one thousand of the IP addresses in that the US based ISps were.
More than 6k domains as well as over 25k URLs were got affected by this attack. The attack
was happened in the year 2016.
3ve attack:
The 3ve attack happen when it was the year 2018. The 3ve attack was the beginner to give
rise to the different sub operations that were interconnected to each other. Each of the sub
operations was able for evading the investigation after the fraud of perpetrating
advertisement. More than 1.7 million of the computers and a huge number of the servers of
the networks [11]. The severs were able for generating fake traffic with the help of the bots.
Patch systems for preventing Dos and other Exploits:
This is including updates of software as well as security patches for the network firewalls as
well as for the routers, PCs, hardware, servers or some of the other workstations and devices
that are connected [9]. The users are required to change the default password of them as well
as they are also required to install the daily updates as well as security patches for mitigating
botnet attacks.
Botnet attacks:
Mirai attack:
The digital smart devices that were running on the basis of the ARC based processors were
infected by the Mirai attack that was happened in the year 2016 [10]. The attack was actually
done when the authors launched a DDoS attack in the web based server of them. From this
attack over 6 millions of devices were infected.
Methbot attack:
This attack is one of the hugest malwares ever. It was actually a digital based advertises. This
was acquired more than one thousand of the IP addresses in that the US based ISps were.
More than 6k domains as well as over 25k URLs were got affected by this attack. The attack
was happened in the year 2016.
3ve attack:
The 3ve attack happen when it was the year 2018. The 3ve attack was the beginner to give
rise to the different sub operations that were interconnected to each other. Each of the sub
operations was able for evading the investigation after the fraud of perpetrating
advertisement. More than 1.7 million of the computers and a huge number of the servers of
the networks [11]. The severs were able for generating fake traffic with the help of the bots.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9OVERVIEW OF NETWORK SECURITY
More than 5000 websites were counterfire by this attack. The websites were also having over
60000+ accounts.
Conclusion:
Thus, it can be concluded that botnet is so much harmful for the present era. The computers
are fully controlled by one of the third parties as well as used for transmitting spam or
malware or for launching attacks. At present most of the people are storing data and contains
that are highly sensitive like legal or financial details. This is also a big problem that if any
device belongs to government or company, the impact of botnet can harm confidential and
sensitive data of the organisation.
More than 5000 websites were counterfire by this attack. The websites were also having over
60000+ accounts.
Conclusion:
Thus, it can be concluded that botnet is so much harmful for the present era. The computers
are fully controlled by one of the third parties as well as used for transmitting spam or
malware or for launching attacks. At present most of the people are storing data and contains
that are highly sensitive like legal or financial details. This is also a big problem that if any
device belongs to government or company, the impact of botnet can harm confidential and
sensitive data of the organisation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10OVERVIEW OF NETWORK SECURITY
References:
[1] Sinha, Kapil, Arun Viswanathan, and Julian Bunn. "Tracking Temporal Evolution of
Network Activity for Botnet Detection." arXiv preprint arXiv:1908.03443 2019.
[2] Kwon, Jonghoon, Jehyun Lee, Heejo Lee, and Adrian Perrig. "PsyBoG: A scalable botnet
detection method for large-scale DNS traffic." Computer Networks 97: 48-73, 2016.
[3] Meidan, Yair, Michael Bohadana, Yael Mathov, Yisroel Mirsky, Asaf Shabtai, Dominik
Breitenbacher, and Yuval Elovici. "N-BaIoT—Network-based detection of IoT botnet
attacks using deep autoencoders." IEEE Pervasive Computing 17, no. 3 : 12-22, 2018.
[4] Wang, Jing, and Ioannis Ch Paschalidis. "Botnet detection based on anomaly and
community detection." IEEE Transactions on Control of Network Systems 4, no. 2 : 392-
404, 2016.
[5] Chowdhury, Sudipta, Mojtaba Khanzadeh, Ravi Akula, Fangyan Zhang, Song Zhang,
Hugh Medal, Mohammad Marufuzzaman, and Linkan Bian. "Botnet detection using
graph-based feature clustering." Journal of Big Data 4, no. 1 : 14, 2017.
[6] Schiavoni, Stefano, Federico Maggi, Lorenzo Cavallaro, and Stefano Zanero. "Phoenix:
DGA-based botnet tracking and intelligence." In International Conference on Detection
of Intrusions and Malware, and Vulnerability Assessment, pp. 192-211, 2014.
[7] Abokhodair, Norah, Daisy Yoo, and David W. McDonald. "Dissecting a social botnet:
Growth, content and influence in Twitter." In Proceedings of the 18th ACM Conference
on Computer Supported Cooperative Work & Social Computing, pp. 839-851. ACM,
2015.
[8] Dainotti, Alberto, Alistair King, Kimberly Claffy, Ferdinando Papale, and Antonio
Pescapé. "Analysis of a/0 stealth scan from a botnet." IEEE/ACM Transactions on
Networking (TON)23, no. 2 : 341-354, 2015.
References:
[1] Sinha, Kapil, Arun Viswanathan, and Julian Bunn. "Tracking Temporal Evolution of
Network Activity for Botnet Detection." arXiv preprint arXiv:1908.03443 2019.
[2] Kwon, Jonghoon, Jehyun Lee, Heejo Lee, and Adrian Perrig. "PsyBoG: A scalable botnet
detection method for large-scale DNS traffic." Computer Networks 97: 48-73, 2016.
[3] Meidan, Yair, Michael Bohadana, Yael Mathov, Yisroel Mirsky, Asaf Shabtai, Dominik
Breitenbacher, and Yuval Elovici. "N-BaIoT—Network-based detection of IoT botnet
attacks using deep autoencoders." IEEE Pervasive Computing 17, no. 3 : 12-22, 2018.
[4] Wang, Jing, and Ioannis Ch Paschalidis. "Botnet detection based on anomaly and
community detection." IEEE Transactions on Control of Network Systems 4, no. 2 : 392-
404, 2016.
[5] Chowdhury, Sudipta, Mojtaba Khanzadeh, Ravi Akula, Fangyan Zhang, Song Zhang,
Hugh Medal, Mohammad Marufuzzaman, and Linkan Bian. "Botnet detection using
graph-based feature clustering." Journal of Big Data 4, no. 1 : 14, 2017.
[6] Schiavoni, Stefano, Federico Maggi, Lorenzo Cavallaro, and Stefano Zanero. "Phoenix:
DGA-based botnet tracking and intelligence." In International Conference on Detection
of Intrusions and Malware, and Vulnerability Assessment, pp. 192-211, 2014.
[7] Abokhodair, Norah, Daisy Yoo, and David W. McDonald. "Dissecting a social botnet:
Growth, content and influence in Twitter." In Proceedings of the 18th ACM Conference
on Computer Supported Cooperative Work & Social Computing, pp. 839-851. ACM,
2015.
[8] Dainotti, Alberto, Alistair King, Kimberly Claffy, Ferdinando Papale, and Antonio
Pescapé. "Analysis of a/0 stealth scan from a botnet." IEEE/ACM Transactions on
Networking (TON)23, no. 2 : 341-354, 2015.

11OVERVIEW OF NETWORK SECURITY
[9] Karim, Ahmad, Rosli Bin Salleh, Muhammad Shiraz, Syed Adeel Ali Shah, Irfan Awan,
and Nor Badrul Anuar. "Botnet detection techniques: review, future trends, and
issues." Journal of Zhejiang University SCIENCE C 15, no. 11 : 943-983, 2014.
[10] Hoque, Nazrul, Dhruba K. Bhattacharyya, and Jugal K. Kalita. "Botnet in DDoS
attacks: trends and challenges." IEEE Communications Surveys & Tutorials 17, no. 4 :
2242-2270, 2015.
[11] Gadelrab, Mohammed S., Muhammad ElSheikh, Mahmoud A. Ghoneim, and Mohsen
Rashwan. "BotCap: Machine Learning Approach for Botnet Detection Based on
Statistical Features." International Journal of Computer Network and Information
Security (IJCNIS) 10, no. 3 : 563-579, 2018.
[9] Karim, Ahmad, Rosli Bin Salleh, Muhammad Shiraz, Syed Adeel Ali Shah, Irfan Awan,
and Nor Badrul Anuar. "Botnet detection techniques: review, future trends, and
issues." Journal of Zhejiang University SCIENCE C 15, no. 11 : 943-983, 2014.
[10] Hoque, Nazrul, Dhruba K. Bhattacharyya, and Jugal K. Kalita. "Botnet in DDoS
attacks: trends and challenges." IEEE Communications Surveys & Tutorials 17, no. 4 :
2242-2270, 2015.
[11] Gadelrab, Mohammed S., Muhammad ElSheikh, Mahmoud A. Ghoneim, and Mohsen
Rashwan. "BotCap: Machine Learning Approach for Botnet Detection Based on
Statistical Features." International Journal of Computer Network and Information
Security (IJCNIS) 10, no. 3 : 563-579, 2018.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





