Cyber Security Management and the Smart Grid: A Case Study
VerifiedAdded on 2022/10/11
|19
|1135
|45
Presentation
AI Summary
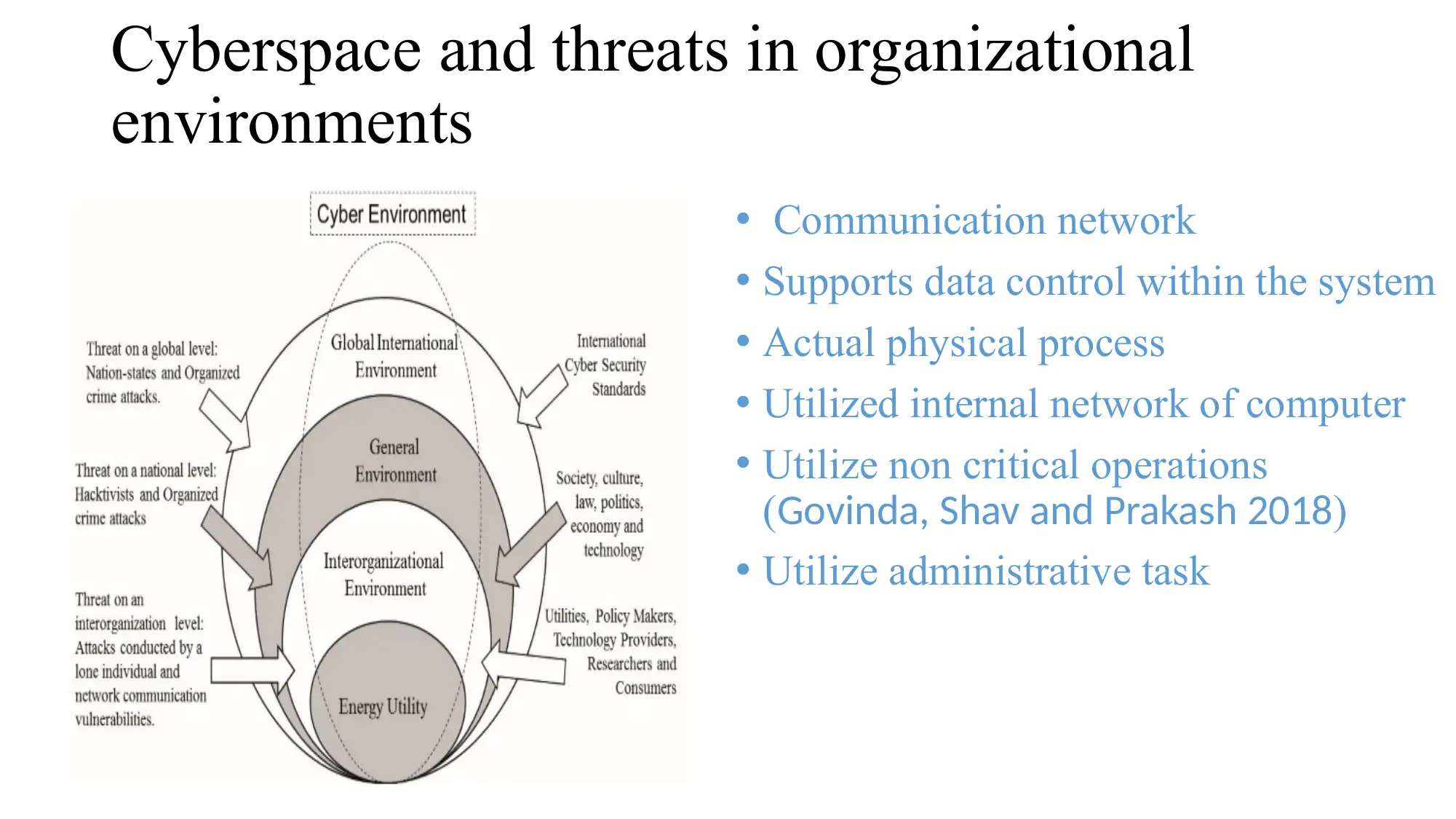
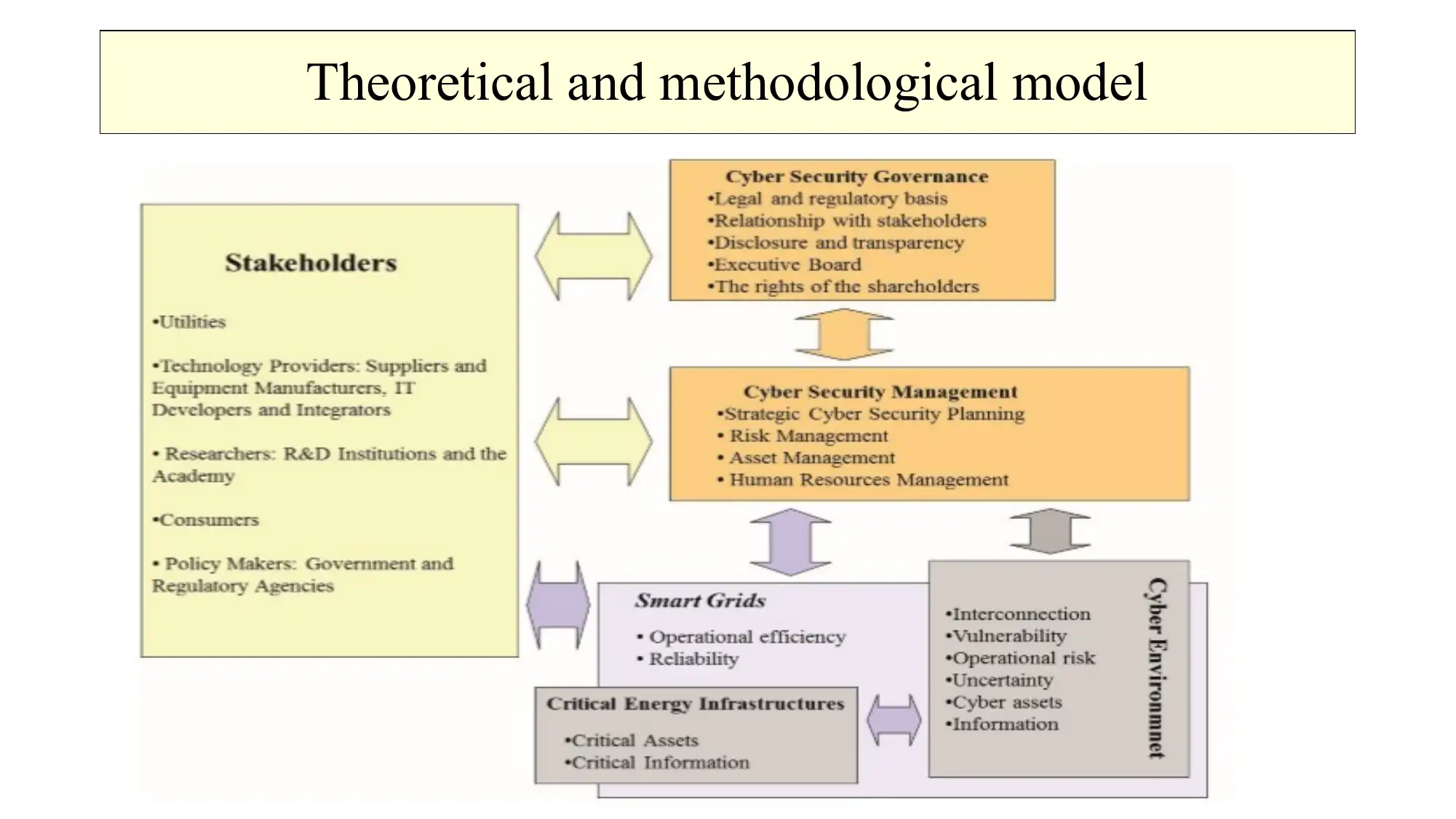
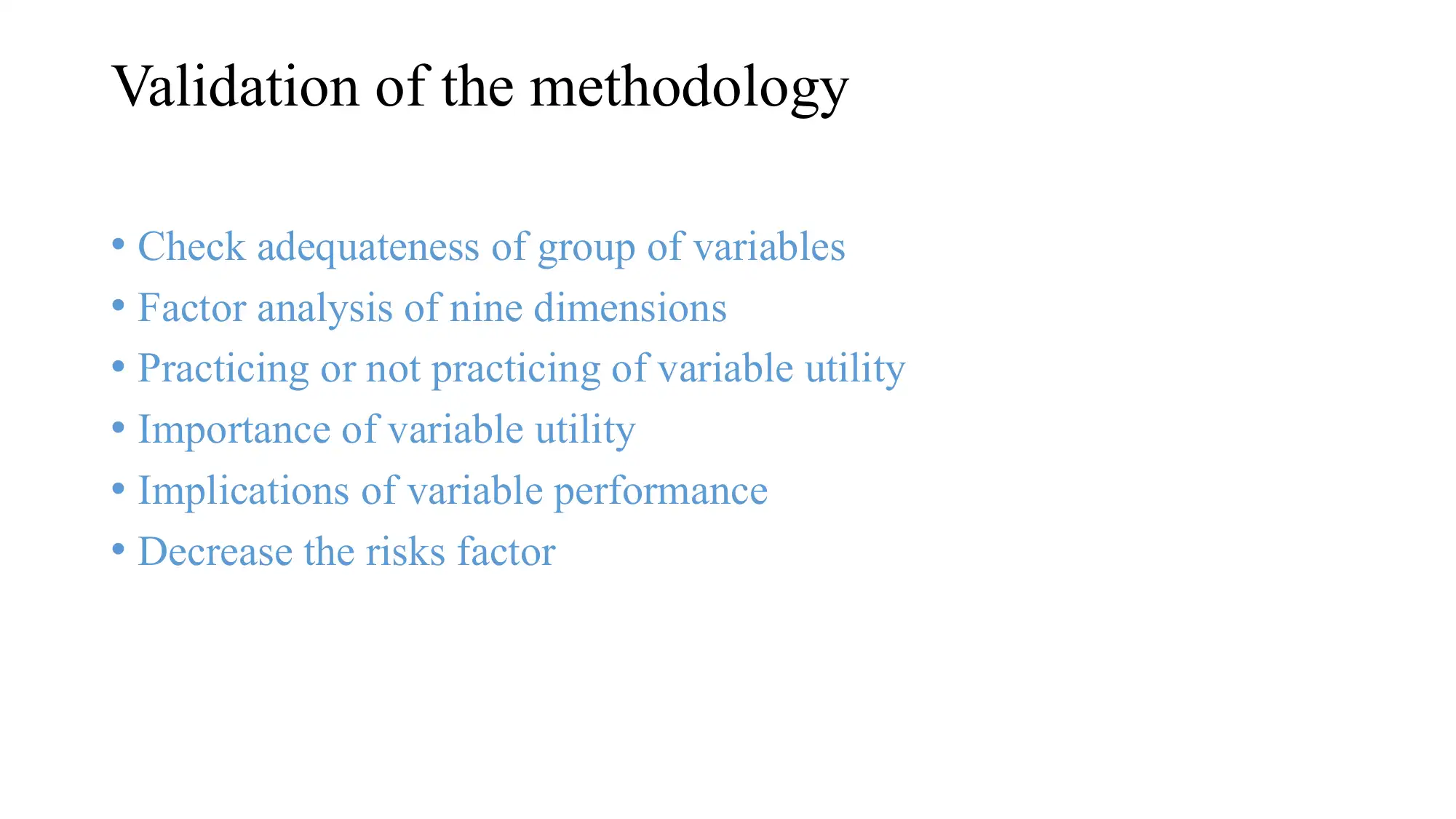
This presentation analyzes cyber security management within the context of smart grids, with a specific focus on the Brazilian energy utility sector. The presentation begins by introducing the importance of energy and the smart grid system, highlighting its complexities and vulnerabilities. It defines the cyber environment and critical cyber assets, outlining the goals of a smart grid system and its associated risks. The presentation delves into the MNG (Management, Normative, Governance) model, explaining its role in protecting cyber assets and environments. The methodology involves the Delphi technique to create a theoretical and methodological model, followed by data collection, statistical analysis, and validation. The presentation also covers strategic planning, risk management, asset management, human resource management, and operational security. The conclusion emphasizes the need for active operational cyber security planning, detection, and response to vulnerabilities and threats within the Brazilian energy utility sector, emphasizing the importance of integrating cyber security into all aspects of smart grid operations.
1 out of 19











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)