Comparative Analysis of OpenSAMM and BSIMM Security Maturity Models
VerifiedAdded on 2022/11/24
|7
|1359
|162
Report
AI Summary
This report provides a comprehensive analysis of two prominent software security maturity models: OpenSAMM and BSIMM. It begins with an introduction highlighting the increasing importance of software security in the face of growing cyber threats. The report then delves into the specifics of each model, describing their structures, business functions, and domains. OpenSAMM, a prescriptive model, is contrasted with BSIMM, a descriptive model that reflects real-world practices. The report further compares and contrasts the two models, discussing their similarities and differences in terms of their approaches to providing guidance and their maturity assessment processes. The pros and cons of applying each model are thoroughly examined, providing valuable insights for organizations. The report concludes with a recommendation to adopt BSIMM for the U.S. Department of Health and Human Services, along with implementation steps, making this report a valuable resource for anyone seeking to enhance their software security posture.

OpenSAMM and BSIMM
Name
Institution
Name
Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
With IT becoming a critical requirement in government and business operations, threats of
malicious attacks have increased exponentially. A major enabler of security bleaches is the
existence of vulnerabilities in new and existing software in use by organizations. As such,
subjecting a software solution to rigorous review and testing is very critical. Such reviews and
tests helps in eliminating vulnerabilities, by performing extensive code reviews, thus reducing
chances of malicious attacks (Jaatun, 2015). Organizations therefore have to adopt a software
maturing model; a framework that helps organizations in formulating and implementing
strategies for software security, tailored to the specific risks facing an organization. Some of the
most commonly used frameworks include the OpenSAMM and BSIMM.
This report presents an analysis of OpenSAMM and BSIMM software security maturity models.
The report compares and contrasts the two models, besides giving the pros and cons of applying
each of the models. The analysis is done in the context of applying the models to the U.S.
Department of Health and Human Services’ software development and maintenance activities.
OpenSAMM
Open Software Assurance Maturity Model (OpenSAMM) is a prescriptive model, maintained by
the OWASP project (Heiland, Thomas,Welch & Jackson, 2013). This model classifies the
application security maturity into four business functions, namely;
Governance: this aspect outlines how the software is to be managed within the
organization
Construction: the aspect details how software applications are to be built.
Verification: outlines details of how software applications are to be tested
Deployment: specifies details on how applications are to be deployed and supported in a
production environment (Jaatun, 2015).
With IT becoming a critical requirement in government and business operations, threats of
malicious attacks have increased exponentially. A major enabler of security bleaches is the
existence of vulnerabilities in new and existing software in use by organizations. As such,
subjecting a software solution to rigorous review and testing is very critical. Such reviews and
tests helps in eliminating vulnerabilities, by performing extensive code reviews, thus reducing
chances of malicious attacks (Jaatun, 2015). Organizations therefore have to adopt a software
maturing model; a framework that helps organizations in formulating and implementing
strategies for software security, tailored to the specific risks facing an organization. Some of the
most commonly used frameworks include the OpenSAMM and BSIMM.
This report presents an analysis of OpenSAMM and BSIMM software security maturity models.
The report compares and contrasts the two models, besides giving the pros and cons of applying
each of the models. The analysis is done in the context of applying the models to the U.S.
Department of Health and Human Services’ software development and maintenance activities.
OpenSAMM
Open Software Assurance Maturity Model (OpenSAMM) is a prescriptive model, maintained by
the OWASP project (Heiland, Thomas,Welch & Jackson, 2013). This model classifies the
application security maturity into four business functions, namely;
Governance: this aspect outlines how the software is to be managed within the
organization
Construction: the aspect details how software applications are to be built.
Verification: outlines details of how software applications are to be tested
Deployment: specifies details on how applications are to be deployed and supported in a
production environment (Jaatun, 2015).

Figure 1.0 Overview of Open Software Assurance Maturity Model
Building Security in Maturity Model (BSIMM)
The BSIMM is a descriptive security maturity model, which consists of 12 defined practices,
which are categorized into four domains; “governance, intelligence, secure software
development lifecycle (S-SDLC) touch points, and deployments” (McGraw, 2015).
Under the Governance domain, BSIMM outlines the strategies and metrics, policies and
compliance as well as training. Under the Intelligence domain, the framework outlines the attack
models, design of security features and the required standards. On the SSDL touch points, the
model describes the architectural analysis, code review and security testing. Finally, under
deployment domain, BSIMM outlines the steps in penetration testing, the deployment software
environment, configuration and management of vulnerabilities (McGraw, Migues & West, 2015).
Building Security in Maturity Model (BSIMM)
The BSIMM is a descriptive security maturity model, which consists of 12 defined practices,
which are categorized into four domains; “governance, intelligence, secure software
development lifecycle (S-SDLC) touch points, and deployments” (McGraw, 2015).
Under the Governance domain, BSIMM outlines the strategies and metrics, policies and
compliance as well as training. Under the Intelligence domain, the framework outlines the attack
models, design of security features and the required standards. On the SSDL touch points, the
model describes the architectural analysis, code review and security testing. Finally, under
deployment domain, BSIMM outlines the steps in penetration testing, the deployment software
environment, configuration and management of vulnerabilities (McGraw, Migues & West, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
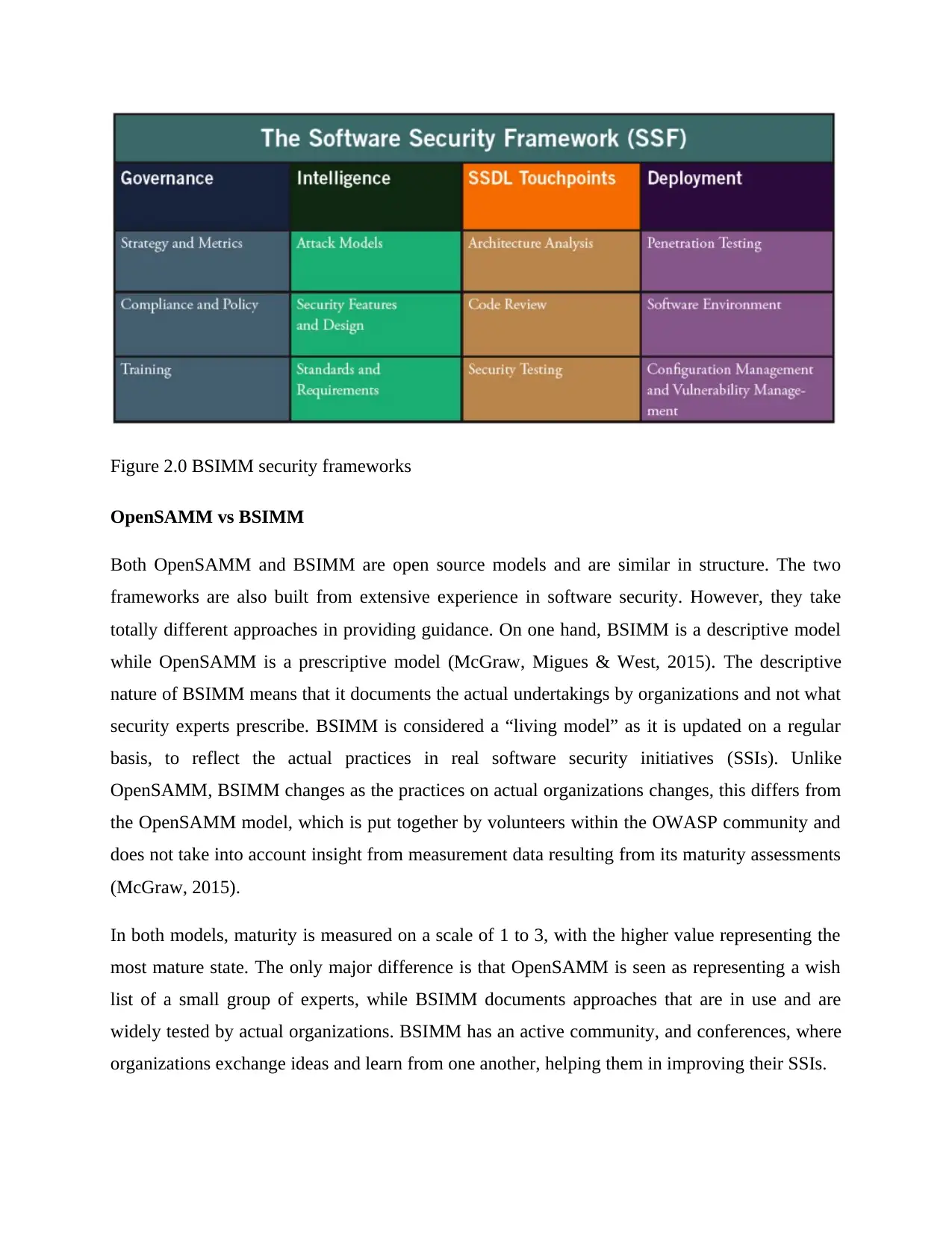
Figure 2.0 BSIMM security frameworks
OpenSAMM vs BSIMM
Both OpenSAMM and BSIMM are open source models and are similar in structure. The two
frameworks are also built from extensive experience in software security. However, they take
totally different approaches in providing guidance. On one hand, BSIMM is a descriptive model
while OpenSAMM is a prescriptive model (McGraw, Migues & West, 2015). The descriptive
nature of BSIMM means that it documents the actual undertakings by organizations and not what
security experts prescribe. BSIMM is considered a “living model” as it is updated on a regular
basis, to reflect the actual practices in real software security initiatives (SSIs). Unlike
OpenSAMM, BSIMM changes as the practices on actual organizations changes, this differs from
the OpenSAMM model, which is put together by volunteers within the OWASP community and
does not take into account insight from measurement data resulting from its maturity assessments
(McGraw, 2015).
In both models, maturity is measured on a scale of 1 to 3, with the higher value representing the
most mature state. The only major difference is that OpenSAMM is seen as representing a wish
list of a small group of experts, while BSIMM documents approaches that are in use and are
widely tested by actual organizations. BSIMM has an active community, and conferences, where
organizations exchange ideas and learn from one another, helping them in improving their SSIs.
OpenSAMM vs BSIMM
Both OpenSAMM and BSIMM are open source models and are similar in structure. The two
frameworks are also built from extensive experience in software security. However, they take
totally different approaches in providing guidance. On one hand, BSIMM is a descriptive model
while OpenSAMM is a prescriptive model (McGraw, Migues & West, 2015). The descriptive
nature of BSIMM means that it documents the actual undertakings by organizations and not what
security experts prescribe. BSIMM is considered a “living model” as it is updated on a regular
basis, to reflect the actual practices in real software security initiatives (SSIs). Unlike
OpenSAMM, BSIMM changes as the practices on actual organizations changes, this differs from
the OpenSAMM model, which is put together by volunteers within the OWASP community and
does not take into account insight from measurement data resulting from its maturity assessments
(McGraw, 2015).
In both models, maturity is measured on a scale of 1 to 3, with the higher value representing the
most mature state. The only major difference is that OpenSAMM is seen as representing a wish
list of a small group of experts, while BSIMM documents approaches that are in use and are
widely tested by actual organizations. BSIMM has an active community, and conferences, where
organizations exchange ideas and learn from one another, helping them in improving their SSIs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Pros and Cons for applying each model
OpenSAMM Benefits:
The model helps in building a balanced Software Security Assurance program in
systematic and well defined iterations.
The model defines clear and measurable organization-wide security activities
OpenSAMM Disadvantages
The model is seen as a wish list of a handful of IT security experts
The model fails to incorporate insight from measurement data resulting from its maturity
assessments.
Advantages of BSIMM
The descriptive nature of BSIMM means that it documents the actual undertakings by
organizations and not what security experts prescribe.
The model has an active community and conferences, where organization can exchange
ideas and update their SSIs.
Disadvantages of BSIMM
BSIMM fails to evaluate the effectiveness of a given organization in implementing a
specific activity. For that reason, an organization may get credit for performing a certain
security procedure or activity, but not on how effective the undertaking is in ensuring
software security.
BSIMM is built on experience of organizations, therefore it lacks a forward-looking
approach in which future security measures needs to be developed or thought about. The
model entirely relies on what was done in the past, thus lacking proactive growth.
Recommendation
OpenSAMM Benefits:
The model helps in building a balanced Software Security Assurance program in
systematic and well defined iterations.
The model defines clear and measurable organization-wide security activities
OpenSAMM Disadvantages
The model is seen as a wish list of a handful of IT security experts
The model fails to incorporate insight from measurement data resulting from its maturity
assessments.
Advantages of BSIMM
The descriptive nature of BSIMM means that it documents the actual undertakings by
organizations and not what security experts prescribe.
The model has an active community and conferences, where organization can exchange
ideas and update their SSIs.
Disadvantages of BSIMM
BSIMM fails to evaluate the effectiveness of a given organization in implementing a
specific activity. For that reason, an organization may get credit for performing a certain
security procedure or activity, but not on how effective the undertaking is in ensuring
software security.
BSIMM is built on experience of organizations, therefore it lacks a forward-looking
approach in which future security measures needs to be developed or thought about. The
model entirely relies on what was done in the past, thus lacking proactive growth.
Recommendation

Considering the nature of systems to be maintained and developed at HHS, the recommended
model is the BSIMM. BSIMM is more extensive than OpenSAMM, and its continuous
improvement approach would be ideal for an organization that evolves over time. The model
will give the government an approach that provides practices that have been tested extensively by
different types of organizations. Adopting BSIMM will help in defining critical measures and
activities in managing the systems, attack models, design of security features, architectural
analysis, code review, testing and deployment of key systems including the future website of the
government project.
Implementation Steps for BSIMM
From analysis of a wide range of organizations that have implemented BSIMM, a skeleton
BSIMM is provided, which outlines steps for assessing security initiates by use of BSIMM.
The 12 activities form the recommended steps or core activities undertaken by most
organizations in implementing BSIMM. They include;
“SM1.4 Identify gate locations, gather necessary artifacts”
“CP1.2 Identify PII obligations”
“T1.1 Provide awareness training”
“AM1.5 Gather attack intelligence”
“SFD1.1 Build and publish security features”
“SR1.1 Create security standards”
“AA1.1 Perform security feature review”
“CR1.4 Use automated tools along with manual review”
“ST1.1 Ensure quality assurance (QA) supports edge/boundary value condition testing”
“PT1.1 Use external penetration testers to find problems; ”
“SE1.2 Ensure host and network security basics are in place”
“CMVM1.2 Identify software defects found in operations monitoring and feed them back
to development”
References
model is the BSIMM. BSIMM is more extensive than OpenSAMM, and its continuous
improvement approach would be ideal for an organization that evolves over time. The model
will give the government an approach that provides practices that have been tested extensively by
different types of organizations. Adopting BSIMM will help in defining critical measures and
activities in managing the systems, attack models, design of security features, architectural
analysis, code review, testing and deployment of key systems including the future website of the
government project.
Implementation Steps for BSIMM
From analysis of a wide range of organizations that have implemented BSIMM, a skeleton
BSIMM is provided, which outlines steps for assessing security initiates by use of BSIMM.
The 12 activities form the recommended steps or core activities undertaken by most
organizations in implementing BSIMM. They include;
“SM1.4 Identify gate locations, gather necessary artifacts”
“CP1.2 Identify PII obligations”
“T1.1 Provide awareness training”
“AM1.5 Gather attack intelligence”
“SFD1.1 Build and publish security features”
“SR1.1 Create security standards”
“AA1.1 Perform security feature review”
“CR1.4 Use automated tools along with manual review”
“ST1.1 Ensure quality assurance (QA) supports edge/boundary value condition testing”
“PT1.1 Use external penetration testers to find problems; ”
“SE1.2 Ensure host and network security basics are in place”
“CMVM1.2 Identify software defects found in operations monitoring and feed them back
to development”
References
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Heiland, R., Thomas, B., Welch, V., & Jackson, C. (2013). Toward a Research Software Security
Maturity Model. arXiv preprint arXiv:1309.1677.
Jaatun, M. G., Cruzes, D. S., Bernsmed, K., Tøndel, I. A., & Røstad, L. (2015, September).
Software security maturity in public organisations. In International Conference on
Information Security (pp. 120-138). Springer, Cham.
McGraw, G. (2015). Software security and the building security in maturity model
(BSIMM). Journal of Computing Sciences in Colleges, 30(3), 7-8.
McGraw, G., Migues, S., & West, J. (2015). Building Security In Maturity Model (BSIMM)
Version 6.
Maturity Model. arXiv preprint arXiv:1309.1677.
Jaatun, M. G., Cruzes, D. S., Bernsmed, K., Tøndel, I. A., & Røstad, L. (2015, September).
Software security maturity in public organisations. In International Conference on
Information Security (pp. 120-138). Springer, Cham.
McGraw, G. (2015). Software security and the building security in maturity model
(BSIMM). Journal of Computing Sciences in Colleges, 30(3), 7-8.
McGraw, G., Migues, S., & West, J. (2015). Building Security In Maturity Model (BSIMM)
Version 6.
1 out of 7
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

