Digital Forensic Report: IT Security at Building Finance PVT Ltd
VerifiedAdded on 2021/05/31
|19
|4670
|77
Report
AI Summary
This digital forensic report details an investigation into a security breach at Building Finance PVT Ltd. The report outlines the investigation process, which includes the digital forensic methodology implemented by the audit team, and the resources utilized. It covers the approach for data and evidence identification and acquisition, including the collection of volatile and non-volatile memory, network traffic analysis, and the use of various forensic tools. The analysis phase focuses on keyword searches, deleted file recovery, and registry data extraction. The report also addresses relevant security policies and provides recommendations to improve the company's security posture. The investigation aims to identify the source of the compromise and protect the system and network with the necessary security standards.

Forensic Digital Report
Forensic Digital Report
Student Name
University Name
Student number
Student email address
Tutor Name
Unit Coordinator
1
Forensic Digital Report
Student Name
University Name
Student number
Student email address
Tutor Name
Unit Coordinator
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Forensic Digital Report
Executive Summary
Information Technology now becomes an integral or most important part of a human life. Today
almost all businesses used information technology as a great deal so that all business related activities
are automatically done to minimize time as well as to increase the business productivity. Although
there is an excellent and exciting aspect of IT, but with that cyber crime is also increasing with the
same speed. Therefore, it is important to emphasize the safety and security of intellectual information
so that companies can do automation for information technology. Building Finance PVT Ltd
Company has implemented financial management software information technology and invested in IT
for supporting all its business related operations to achieve competitive benefits over its rivals and
competitors but faced huge challenges of system compromise. Digital forensic examination team has
to face such challenges so that the main sources of big compromise can be found and the system and
network will be protected with the necessary security standards.
2
Executive Summary
Information Technology now becomes an integral or most important part of a human life. Today
almost all businesses used information technology as a great deal so that all business related activities
are automatically done to minimize time as well as to increase the business productivity. Although
there is an excellent and exciting aspect of IT, but with that cyber crime is also increasing with the
same speed. Therefore, it is important to emphasize the safety and security of intellectual information
so that companies can do automation for information technology. Building Finance PVT Ltd
Company has implemented financial management software information technology and invested in IT
for supporting all its business related operations to achieve competitive benefits over its rivals and
competitors but faced huge challenges of system compromise. Digital forensic examination team has
to face such challenges so that the main sources of big compromise can be found and the system and
network will be protected with the necessary security standards.
2

Forensic Digital Report
Contents
Introduction..............................................................................................................................................4
Compnay & Background......................................................................................................................4
Digital Forensic Report............................................................................................................................5
Part 1....................................................................................................................................................5
Digital forensic methodology...........................................................................................................5
Digital Forensic examination or Investigation Approach................................................................5
Part 2....................................................................................................................................................6
Digital Forensic Investigation Approach Resources........................................................................6
Part 3....................................................................................................................................................7
Approach for data/evidence identification and acquisition..............................................................7
Part 4..................................................................................................................................................11
Analysis phase................................................................................................................................11
Part 5..................................................................................................................................................12
Relevant security policies for the Company..................................................................................12
Part 6..................................................................................................................................................14
Recommendations..............................................................................................................................14
Conclusion..............................................................................................................................................15
References..............................................................................................................................................16
3
Contents
Introduction..............................................................................................................................................4
Compnay & Background......................................................................................................................4
Digital Forensic Report............................................................................................................................5
Part 1....................................................................................................................................................5
Digital forensic methodology...........................................................................................................5
Digital Forensic examination or Investigation Approach................................................................5
Part 2....................................................................................................................................................6
Digital Forensic Investigation Approach Resources........................................................................6
Part 3....................................................................................................................................................7
Approach for data/evidence identification and acquisition..............................................................7
Part 4..................................................................................................................................................11
Analysis phase................................................................................................................................11
Part 5..................................................................................................................................................12
Relevant security policies for the Company..................................................................................12
Part 6..................................................................................................................................................14
Recommendations..............................................................................................................................14
Conclusion..............................................................................................................................................15
References..............................................................................................................................................16
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Forensic Digital Report
Introduction
A team of Brisbane Office contacted the IT Security Office immediately to the Department of
Finance, with few concerns about the Office of Computer Systems. He suspects some illegal activities
someone has compromised some computers in his office building with his computer. The
investigation audit team has been set up to examine the compromised source. The branch team has
been deployed for digital forensic examination. Manager noted that some innovative features of the
finance management system software introduced in computer system. Additionally, some files of the
customer's personal data have been customized from some official computers. In Brisbane office, a
team of digital forensic investigators has been formed to investigate the suspect. In addition to
reviewing paperwork based company documents, the team has the task of conducting a digital forensic
examination of networks and computer systems in Brisbane office. These include organizing network
analysis, collecting digital proofs from servers, PCs and e-mail accounts, organizing cloud inspections,
and checking social media etc.
Compnay & Background
Building Finance PVT Ltd is a leading client company in the Australia. Building Finance is operating
more than 1,000 workers and Building Finance has more than three million customer services in
Australia. Building Finance PVT Ltd offers different services such as car loans, personal loans, credit
cards, interest-free retailing in finance and personal insurance. Building Finance has made huge
investments for the motion technology to support its commercial operations and to achieve
competitive advantages over its competitors (Wong and Ma, 2014). The company had invested
heavily in early 2000, but management has lost focus on updating network and layout structures,
which in turn has supported business practices in recent years. All network premises in Building
Finance Company offices are flat as well as relatively unobstructed. Users at one office can get
systems plus servers from some another office. Servers and Workstations are commonly known as
4
Introduction
A team of Brisbane Office contacted the IT Security Office immediately to the Department of
Finance, with few concerns about the Office of Computer Systems. He suspects some illegal activities
someone has compromised some computers in his office building with his computer. The
investigation audit team has been set up to examine the compromised source. The branch team has
been deployed for digital forensic examination. Manager noted that some innovative features of the
finance management system software introduced in computer system. Additionally, some files of the
customer's personal data have been customized from some official computers. In Brisbane office, a
team of digital forensic investigators has been formed to investigate the suspect. In addition to
reviewing paperwork based company documents, the team has the task of conducting a digital forensic
examination of networks and computer systems in Brisbane office. These include organizing network
analysis, collecting digital proofs from servers, PCs and e-mail accounts, organizing cloud inspections,
and checking social media etc.
Compnay & Background
Building Finance PVT Ltd is a leading client company in the Australia. Building Finance is operating
more than 1,000 workers and Building Finance has more than three million customer services in
Australia. Building Finance PVT Ltd offers different services such as car loans, personal loans, credit
cards, interest-free retailing in finance and personal insurance. Building Finance has made huge
investments for the motion technology to support its commercial operations and to achieve
competitive advantages over its competitors (Wong and Ma, 2014). The company had invested
heavily in early 2000, but management has lost focus on updating network and layout structures,
which in turn has supported business practices in recent years. All network premises in Building
Finance Company offices are flat as well as relatively unobstructed. Users at one office can get
systems plus servers from some another office. Servers and Workstations are commonly known as
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Forensic Digital Report
Microsoft Windows. The Firewalls as well as network partitions have been implemented all through
the entire environment. Resolve recognition moreover logging on the system exists but it is not used
effectively (Soyer and Tettenborn, 2016).
Digital Forensic Report
Part 1
Digital forensic methodology
DFM are also preferred to process and execute through the IT security Office. This is just because all
methods like computer forensics, mobile forensics, data retrieval and network forensic can give only
partial inspection results instead of checking the sources of compromises because these are the sub-
departments of digital forensics. The following scope is the digital forensic examination conducted in
the local Office of Building Finance PVT Ltd.
Finding Safety Laps in the Regional Office Network
Malicious activities recognition with details such as what, who, when, where and why
Find out the legal process if the cybercrime is unlawful
Determining the effect of the compromised administrator’s computer, if something is
compromised (Bornmann and Leydesdorff, 2014)
Digital Forensic examination or Investigation Approach
The Building Finance Company Audit team has implemented four step forensic processes and named
it as FSFP (Tian, Jiang and Li, 2015). The Digital Forensic Exploration Model is the most influential
model to investigate the compromise in the provincial branch of Building Finance PVT Ltd.
5
Microsoft Windows. The Firewalls as well as network partitions have been implemented all through
the entire environment. Resolve recognition moreover logging on the system exists but it is not used
effectively (Soyer and Tettenborn, 2016).
Digital Forensic Report
Part 1
Digital forensic methodology
DFM are also preferred to process and execute through the IT security Office. This is just because all
methods like computer forensics, mobile forensics, data retrieval and network forensic can give only
partial inspection results instead of checking the sources of compromises because these are the sub-
departments of digital forensics. The following scope is the digital forensic examination conducted in
the local Office of Building Finance PVT Ltd.
Finding Safety Laps in the Regional Office Network
Malicious activities recognition with details such as what, who, when, where and why
Find out the legal process if the cybercrime is unlawful
Determining the effect of the compromised administrator’s computer, if something is
compromised (Bornmann and Leydesdorff, 2014)
Digital Forensic examination or Investigation Approach
The Building Finance Company Audit team has implemented four step forensic processes and named
it as FSFP (Tian, Jiang and Li, 2015). The Digital Forensic Exploration Model is the most influential
model to investigate the compromise in the provincial branch of Building Finance PVT Ltd.
5

Forensic Digital Report
Part 2
Digital Forensic Investigation Approach Resources
Digital forensic investigations require significant resources to appropriately process as well as create
reports for this purpose. It requires technical support as well as tools and techniques to implement the
process and requires extensive audit team expertise. Digital forensics methods that may also be
implemented or executed are statics methods or dynamic methods. Several tools, such as
ProDiscover , EnCase, as well as many other tools, require a thorough examination of the existing
network systems of the branches. The ACPO or the main police association is a set of standard
guidelines consisting of different standards when conducting PC and digital forensic examination
audit or review group must follow below mentioned principles (Saini and Kaur, 2016).
Principle 1: Information or data collected from the targeted computers and collected is saved without
any change or change (Bholebawa and Dalal, 2016).
Principle 2: The compiled data should be securely protected, so that the auditing team must have
sufficient expertise in addition to be able to handle or manage the data jointly and should be required
to act with it when necessary during the process (Forshaw, 2018).
Principle 3: Documentation and review footprint should clearly be prepared and protected. Similar
results are expected when the third party processes the process (Miguel, Sundaram and Aung, 2016).
Principle 4: The audit team must be responsible for the complete inspection of each team member.
Audit team members must have a core level OS, networking system moreover sufficient expertise in
the required tools and technologies needed to investigate. Skill sets must be comprehensive to
manifold dimensions, such as cybercrime knowledge, legal process and several related to it (Park and
Lee, 2015). FTK imager forensic computer tools have been used for sophisticated applications using
easy-to-use and convenient graphical user interface based access to command line environments.
Advance search patterns are very useful in these tools. Computers are available for all types of
6
Part 2
Digital Forensic Investigation Approach Resources
Digital forensic investigations require significant resources to appropriately process as well as create
reports for this purpose. It requires technical support as well as tools and techniques to implement the
process and requires extensive audit team expertise. Digital forensics methods that may also be
implemented or executed are statics methods or dynamic methods. Several tools, such as
ProDiscover , EnCase, as well as many other tools, require a thorough examination of the existing
network systems of the branches. The ACPO or the main police association is a set of standard
guidelines consisting of different standards when conducting PC and digital forensic examination
audit or review group must follow below mentioned principles (Saini and Kaur, 2016).
Principle 1: Information or data collected from the targeted computers and collected is saved without
any change or change (Bholebawa and Dalal, 2016).
Principle 2: The compiled data should be securely protected, so that the auditing team must have
sufficient expertise in addition to be able to handle or manage the data jointly and should be required
to act with it when necessary during the process (Forshaw, 2018).
Principle 3: Documentation and review footprint should clearly be prepared and protected. Similar
results are expected when the third party processes the process (Miguel, Sundaram and Aung, 2016).
Principle 4: The audit team must be responsible for the complete inspection of each team member.
Audit team members must have a core level OS, networking system moreover sufficient expertise in
the required tools and technologies needed to investigate. Skill sets must be comprehensive to
manifold dimensions, such as cybercrime knowledge, legal process and several related to it (Park and
Lee, 2015). FTK imager forensic computer tools have been used for sophisticated applications using
easy-to-use and convenient graphical user interface based access to command line environments.
Advance search patterns are very useful in these tools. Computers are available for all types of
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Forensic Digital Report
forensic toll-free and professional versions which support scientific testing. The National Institute of
Standards and Technology has proposed a computer forensic device and its framework defines the
functioning and requirements of such devices. Specific requirements the forensic toolkit is a bundle of
many components such as viewing the registry, filing a known file, and so on. All components have
their own installation modules. Image modules are basically imaging components that capture media,
image files and folder contents on disk. Some decisions have to be made when an FTK device is
started, the investigator is based on selecting a preview or taking mode and choosing to do the future
extends the screen about the function of the FTK device (Zayets, 2017). Different types of networks
are forensic devices, each with diverse functions. Some are only packet sniffers as well as some of
these are related to identity cards, fingerprinting, mapping, location, web services, and email
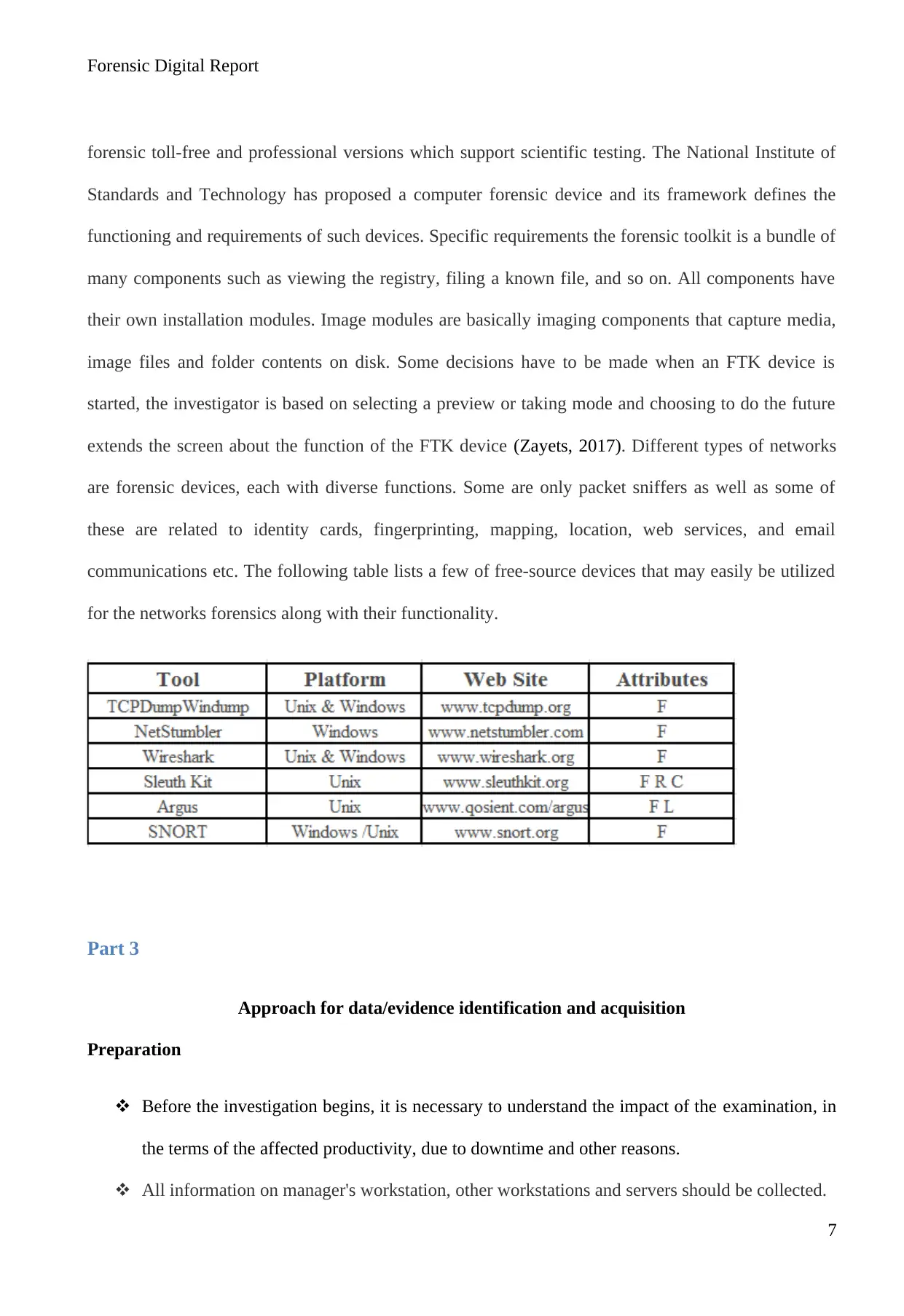
communications etc. The following table lists a few of free-source devices that may easily be utilized
for the networks forensics along with their functionality.
Part 3
Approach for data/evidence identification and acquisition
Preparation
Before the investigation begins, it is necessary to understand the impact of the examination, in
the terms of the affected productivity, due to downtime and other reasons.
All information on manager's workstation, other workstations and servers should be collected.
7
forensic toll-free and professional versions which support scientific testing. The National Institute of
Standards and Technology has proposed a computer forensic device and its framework defines the
functioning and requirements of such devices. Specific requirements the forensic toolkit is a bundle of
many components such as viewing the registry, filing a known file, and so on. All components have
their own installation modules. Image modules are basically imaging components that capture media,
image files and folder contents on disk. Some decisions have to be made when an FTK device is
started, the investigator is based on selecting a preview or taking mode and choosing to do the future
extends the screen about the function of the FTK device (Zayets, 2017). Different types of networks
are forensic devices, each with diverse functions. Some are only packet sniffers as well as some of
these are related to identity cards, fingerprinting, mapping, location, web services, and email
communications etc. The following table lists a few of free-source devices that may easily be utilized
for the networks forensics along with their functionality.
Part 3
Approach for data/evidence identification and acquisition
Preparation
Before the investigation begins, it is necessary to understand the impact of the examination, in
the terms of the affected productivity, due to downtime and other reasons.
All information on manager's workstation, other workstations and servers should be collected.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Forensic Digital Report
Get the significant network information
Recognize storage components, both external and internal devices
Forensic devices used and used for inquiry should be listed as well as made available for use.
Every activity should be properly documented at the time of investigation process
It is important to have a computational forensic imaging and then check the reliability of the
information (Walter, Unger and Cimiano, 2016).
Capture the live traffic network
Managers present in the regional office must collect workstations, others and digital evidences from
the server. The following evidence is useful.
IP addresses
Windows registry data
System Log documents or files
Network diagrams and Network topology
Network data that consist of network topology documentation, routers, hubs, switches,
network diagrams, servers as well as firewalls
Data from both external storage moreover internal storage devices, for example, DVD,
flash drive, CD, remote computers, USB drive, and portable hard discs also memory cards.
Digital evidences archive: Digital proof of digital proofs should be done in two phases of the Global
Finance Company's Regional Branch. Unstable memory is a provisional memory, and for this data is
organized, only when the server and workstation is running. It is mainly unstable memory RAM. To
access this data, you must enter the same LAN to access the master's computer (Rashidian, Mandil
and Mahjour, 2017).
Give command, cryptcat 6543 –k key
PC information is acquired with commands: cryptcat -1 –p 6543 –k key >>
8
Get the significant network information
Recognize storage components, both external and internal devices
Forensic devices used and used for inquiry should be listed as well as made available for use.
Every activity should be properly documented at the time of investigation process
It is important to have a computational forensic imaging and then check the reliability of the
information (Walter, Unger and Cimiano, 2016).
Capture the live traffic network
Managers present in the regional office must collect workstations, others and digital evidences from
the server. The following evidence is useful.
IP addresses
Windows registry data
System Log documents or files
Network diagrams and Network topology
Network data that consist of network topology documentation, routers, hubs, switches,
network diagrams, servers as well as firewalls
Data from both external storage moreover internal storage devices, for example, DVD,
flash drive, CD, remote computers, USB drive, and portable hard discs also memory cards.
Digital evidences archive: Digital proof of digital proofs should be done in two phases of the Global
Finance Company's Regional Branch. Unstable memory is a provisional memory, and for this data is
organized, only when the server and workstation is running. It is mainly unstable memory RAM. To
access this data, you must enter the same LAN to access the master's computer (Rashidian, Mandil
and Mahjour, 2017).
Give command, cryptcat 6543 –k key
PC information is acquired with commands: cryptcat -1 –p 6543 –k key >>
8

Forensic Digital Report
Additionally these commands, GUI tools such as Tcpview, Process Explorer and Rootkit Revealer
will help audit team to recover unstable data such as system data, time, open ports, logged users,
network connections and running processes.
There are some of the tools utilized for a Windows-based system for unstable data capture,
To identify all network traffic on NetSlasers and Cusors, Netfile, HBGRA F-Response, iPaponging,
HBGrhe Fast Dump, DOSCIN, Manager's PC Clipboard content with possible digital evidences are
also gathered by a team.
Non-Volatile Memory Acquisitions
Non-volatile and Permanent memory is important sources for digital forensic testing. The Permanent
information gathered with the help of online as well as offline ways. The Offline information are
aggregated from a hard drives duplicate tool, for example Guymager, IXimager, FTK imager, EnCase
furthermore DCFLdd are utilized to gather data from the workstation of managers, other workstations
and hard drives of servers. Other stable storage devices such as CDs, DVDs, flash drives, memory
cards, pen drives, as well as drives are likewise collected by the office. Audit team examine online
data such as firewall logs, domain controllers and antivirus logs are collected with assistance of tools
such as ethereal as well as Wireshark tools.
Examination
When possible digital forensic evidence is collected, a detailed checkup is also done by collecting
original as well as logical copies and checking for any hypotheses as well as deviations. Such tests can
suggest how auditing director’s compromises are compromised. Properly detail tests are complete for
the network forensics, Windows registry, as well as file systems plus also database forensics. Team
simply utilizes the subsequent command for this (Ma and Chowdhury, 2015).
C: echo text mess > file1.txt:file2.txt
9
Additionally these commands, GUI tools such as Tcpview, Process Explorer and Rootkit Revealer
will help audit team to recover unstable data such as system data, time, open ports, logged users,
network connections and running processes.
There are some of the tools utilized for a Windows-based system for unstable data capture,
To identify all network traffic on NetSlasers and Cusors, Netfile, HBGRA F-Response, iPaponging,
HBGrhe Fast Dump, DOSCIN, Manager's PC Clipboard content with possible digital evidences are
also gathered by a team.
Non-Volatile Memory Acquisitions
Non-volatile and Permanent memory is important sources for digital forensic testing. The Permanent
information gathered with the help of online as well as offline ways. The Offline information are
aggregated from a hard drives duplicate tool, for example Guymager, IXimager, FTK imager, EnCase
furthermore DCFLdd are utilized to gather data from the workstation of managers, other workstations
and hard drives of servers. Other stable storage devices such as CDs, DVDs, flash drives, memory
cards, pen drives, as well as drives are likewise collected by the office. Audit team examine online
data such as firewall logs, domain controllers and antivirus logs are collected with assistance of tools
such as ethereal as well as Wireshark tools.
Examination
When possible digital forensic evidence is collected, a detailed checkup is also done by collecting
original as well as logical copies and checking for any hypotheses as well as deviations. Such tests can
suggest how auditing director’s compromises are compromised. Properly detail tests are complete for
the network forensics, Windows registry, as well as file systems plus also database forensics. Team
simply utilizes the subsequent command for this (Ma and Chowdhury, 2015).
C: echo text mess > file1.txt:file2.txt
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Forensic Digital Report
These above files are then retrieving through command,
C: more <file1.txt:file2.txt
Windows registry examination is done with the following hives and structures present in it,
• HKEY_USER
• HKEY_CURRENT_USERs
• HKEY_CURRENT_CONFIG
• HKEY_CLASSES_ROOT
• HKEY_LOCAL_MACHINE
The networks are totally enabled use forensic technologies and tools to access information from
computer's computer (Lukongo and Miller, 2018).
System data
Services listings
Registry data
Process listings
Networks connections
Logged on users and Registered users
Binary dump in the memory (Kornhuber and Zoicas, 2017)
Part 4
Analysis phase
To analyze compiled and verified evidence, several tools and methods are utilized by the forensic
auditing team. The analysis is done as follows
10
These above files are then retrieving through command,
C: more <file1.txt:file2.txt
Windows registry examination is done with the following hives and structures present in it,
• HKEY_USER
• HKEY_CURRENT_USERs
• HKEY_CURRENT_CONFIG
• HKEY_CLASSES_ROOT
• HKEY_LOCAL_MACHINE
The networks are totally enabled use forensic technologies and tools to access information from
computer's computer (Lukongo and Miller, 2018).
System data
Services listings
Registry data
Process listings
Networks connections
Logged on users and Registered users
Binary dump in the memory (Kornhuber and Zoicas, 2017)
Part 4
Analysis phase
To analyze compiled and verified evidence, several tools and methods are utilized by the forensic
auditing team. The analysis is done as follows
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Forensic Digital Report
Search keywords in all files
Recover deleted files
The Extraction of registry data from the workstation of managers and other systems
EnCase, ILOOKIX and FTK are the tools used for this team. These tools help to recover the Internet
document, images, emails, internet record, chat logs, accessibility, as well as deleted location
manager's computers or OS cache file. The hash mark digital forensic tools also support to found
significant file. When the SSD drive exists in system, then data can be retrieved even after securing a
safe operation (Hou and He, 2014).
Once the team has analyzed it, it answers the following objectives:
1- Program Reconstruction Opportunity
2- Responsibility for users and administrators
3- Check violation investigation
4- Providing Data to recognize the problem
Report
Final report has been prepared by the forensic auditing team with all the reports.
Final Report
11
Search keywords in all files
Recover deleted files
The Extraction of registry data from the workstation of managers and other systems
EnCase, ILOOKIX and FTK are the tools used for this team. These tools help to recover the Internet
document, images, emails, internet record, chat logs, accessibility, as well as deleted location
manager's computers or OS cache file. The hash mark digital forensic tools also support to found
significant file. When the SSD drive exists in system, then data can be retrieved even after securing a
safe operation (Hou and He, 2014).
Once the team has analyzed it, it answers the following objectives:
1- Program Reconstruction Opportunity
2- Responsibility for users and administrators
3- Check violation investigation
4- Providing Data to recognize the problem
Report
Final report has been prepared by the forensic auditing team with all the reports.
Final Report
11

Forensic Digital Report
Initially, the forensic team needed to analyze the evidence gathered and verified. The forensic team
will pay close attention to this information to see if any hidden files and exception files have been
submitted. Then, if exception handling is in progress and any sockets are open, the forensic digital
team will also see if any application requests an exception. The forensic team will then examine the
account and then submit some unusual accounts. The forensic team can also find out the degree of
repair system (Hitchcock, Le-Khac and Scanlon, 2016). Through the analysis results, the forensic
team will know if any malicious activities have been introduced, and then the forensic team will
develop another kind of court search strategy, such as complete memory analysis, complete analysis of
the file system, and events. According to the study of this matter, there was malicious activity in their
networks frameworks and it was also confirmed through our preliminary recognization.
Part 5
Relevant security policies for the Company
Full standards for assessing the organization of the organization's security system International
standard ISO 1777: Practice code for the information safety management has been accepted in 2000.
Standard ISO 17799 are an global adaptation of the British standard7799. There are practical
standards for information in ISO 17799. Security management as well as administrative, technical and
physical safety measures (ISO/IEC 17797: 2005) can be used as criteria for evaluating institutional
level safety practices (CHELGHOUM, LOUAI and NAIT-SAID, 2014).
Practical rules divided according to following sections:
1- Information security organization;
2- Security Policy;
3- Property management;
4- Human Resource Protection;
12
Initially, the forensic team needed to analyze the evidence gathered and verified. The forensic team
will pay close attention to this information to see if any hidden files and exception files have been
submitted. Then, if exception handling is in progress and any sockets are open, the forensic digital
team will also see if any application requests an exception. The forensic team will then examine the
account and then submit some unusual accounts. The forensic team can also find out the degree of
repair system (Hitchcock, Le-Khac and Scanlon, 2016). Through the analysis results, the forensic
team will know if any malicious activities have been introduced, and then the forensic team will
develop another kind of court search strategy, such as complete memory analysis, complete analysis of
the file system, and events. According to the study of this matter, there was malicious activity in their
networks frameworks and it was also confirmed through our preliminary recognization.
Part 5
Relevant security policies for the Company
Full standards for assessing the organization of the organization's security system International
standard ISO 1777: Practice code for the information safety management has been accepted in 2000.
Standard ISO 17799 are an global adaptation of the British standard7799. There are practical
standards for information in ISO 17799. Security management as well as administrative, technical and
physical safety measures (ISO/IEC 17797: 2005) can be used as criteria for evaluating institutional
level safety practices (CHELGHOUM, LOUAI and NAIT-SAID, 2014).
Practical rules divided according to following sections:
1- Information security organization;
2- Security Policy;
3- Property management;
4- Human Resource Protection;
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





