Business Research Project: Challenges in Cyber Security
VerifiedAdded on 2021/02/19
|9
|2623
|78
Project
AI Summary
This business research project delves into the challenges of cyber security for organizations. The student's contribution includes defining the research question focused on cyber security's impact, outlining the learning experience gained from the project, and contributing to the literature review by analyzing the challenges faced by businesses in the digital landscape. The project details the research methodology, including the use of the research onion, and a debate on qualitative and quantitative data, including the use of surveys and secondary research. The student reflects on the research experience, highlighting the importance of teamwork, communication, and leadership skills. The project also includes a personal statement summarizing the learning outcomes and the development of research skills, and a conclusion emphasizing the importance of collaboration and individual contributions in a group project.

Business Research
Project
Project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
TOPIC: Challenges in Cyber Security for businesses ....................................................................3
1. Introduction .................................................................................................................................3
2. My Personal Contribution............................................................................................................3
2.1 Research question..................................................................................................................3
2.2 Learning Experience..............................................................................................................4
3. Personal Contribution to Literature Review................................................................................4
4. Personal Contribution to Research Methodology Report............................................................5
4.1 Research Methodology..........................................................................................................5
4.2 Qualitative and Quantitative Debate......................................................................................6
5. Reflection on Research Experience.............................................................................................8
6. Personal Statement ......................................................................................................................8
7. Conclusion...................................................................................................................................8
REFRENCES...................................................................................................................................9
TOPIC: Challenges in Cyber Security for businesses ....................................................................3
1. Introduction .................................................................................................................................3
2. My Personal Contribution............................................................................................................3
2.1 Research question..................................................................................................................3
2.2 Learning Experience..............................................................................................................4
3. Personal Contribution to Literature Review................................................................................4
4. Personal Contribution to Research Methodology Report............................................................5
4.1 Research Methodology..........................................................................................................5
4.2 Qualitative and Quantitative Debate......................................................................................6
5. Reflection on Research Experience.............................................................................................8
6. Personal Statement ......................................................................................................................8
7. Conclusion...................................................................................................................................8
REFRENCES...................................................................................................................................9

TOPIC: Challenges in Cyber Security for businesses
1. Introduction
For conducting a research in group, each and every member contributes equal efforts, in
order to obtain outcomes (Jennings, Sutherlin and Counts, 2018). Hereby, with the support of
each other and divide responsibilities as per skills and knowledge level, a group get success to
complete the desired goals. In this regard, to do a project on Cyber Security, I have worked under
a team of three members, where my role and contribution, are describing in present report.
2. My Personal Contribution
2.1 Research question
The project was based on the concept of social media and its impact on behavior of
consumers. For constructing the research project, by involving the participation of each member,
I have chosen the topic – ‘Cyber Security’, for analyzing its challenges for organizations and
their targeted customers. The main reason behind this was increasing the importance of cyber
security among people and within business environment (Dua, 2017). To make research on this
topic, I have given responsibility to introduce the respective problems of project, then frame
appropriate aims and objectives, with research questions.
2.2 Learning Experience
During academic course, I have got opportunity to be a part of a team and give my input
in completion of a project. But as it was my first group-project in academic year, so I felt little
bit less confident and inferior, because of less knowledge about same. For this assistance, I have
evaluated my strengths and weaknesses first to evaluate how much I am able to work under a
group. The only way to analyze it, is making a proper discussion with my seniors, that helps in
getting suggestions of them, to make desired improvement (McLeay, Robson and Yusoff, 2017).
So, I have evaluated that to work in a team, each member needs to possess skills such as Task
Orienter, Effective Communicator, Informer, Summarizer as well as Encourage, that helps in
making contribution and collaboration among all, for completion of project. Along with this, I
have read some books and journals also, for overall understanding of the terms and requirement
of exchange thoughts, for maintaining efficiencies of research. Reading and discussing, helps in
improving my previous understanding and developing desired knowledge. One of the major
strengths of my team is sharing abilities that helps in providing timely information to each
1. Introduction
For conducting a research in group, each and every member contributes equal efforts, in
order to obtain outcomes (Jennings, Sutherlin and Counts, 2018). Hereby, with the support of
each other and divide responsibilities as per skills and knowledge level, a group get success to
complete the desired goals. In this regard, to do a project on Cyber Security, I have worked under
a team of three members, where my role and contribution, are describing in present report.
2. My Personal Contribution
2.1 Research question
The project was based on the concept of social media and its impact on behavior of
consumers. For constructing the research project, by involving the participation of each member,
I have chosen the topic – ‘Cyber Security’, for analyzing its challenges for organizations and
their targeted customers. The main reason behind this was increasing the importance of cyber
security among people and within business environment (Dua, 2017). To make research on this
topic, I have given responsibility to introduce the respective problems of project, then frame
appropriate aims and objectives, with research questions.
2.2 Learning Experience
During academic course, I have got opportunity to be a part of a team and give my input
in completion of a project. But as it was my first group-project in academic year, so I felt little
bit less confident and inferior, because of less knowledge about same. For this assistance, I have
evaluated my strengths and weaknesses first to evaluate how much I am able to work under a
group. The only way to analyze it, is making a proper discussion with my seniors, that helps in
getting suggestions of them, to make desired improvement (McLeay, Robson and Yusoff, 2017).
So, I have evaluated that to work in a team, each member needs to possess skills such as Task
Orienter, Effective Communicator, Informer, Summarizer as well as Encourage, that helps in
making contribution and collaboration among all, for completion of project. Along with this, I
have read some books and journals also, for overall understanding of the terms and requirement
of exchange thoughts, for maintaining efficiencies of research. Reading and discussing, helps in
improving my previous understanding and developing desired knowledge. One of the major
strengths of my team is sharing abilities that helps in providing timely information to each
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

member, so that project will complete on time. In context of mine, leadership skill and way of
influencing others is the most effective one, that helps me to receive the best ideas from each
group member for completion of each activity in best way. Along with this, under group
meetings, I have discussed type of challenges, issues and problems that may arise while doing
tasks. At these meetings, my team-members have exchanged ideas or brainstorm with each other,
in order to come up with the best as well as most creative team solutions to handle the
challenges.
3. Personal Contribution to Literature Review
As under this team, there are three members involved, therefore, each one has given
specific tasks. With this assistance, apart from introduction and research questions, which are
considered as main part of a project, upon whom entire result is based, so, to perform this, I have
worked under guidance of my seniors, as they are well experienced in selection of topic and
conduct a report on same. In this regard, after framing appropriate research aim and questions of
Cyber Security, the another task of mine is to evaluate challenges that faced by organizations, I
have analyzed that to move business on online platform, it is essential for firms to identify the
challenges of same and develop proper strategies to overcome. In order to conduct literature
review on Cyber Security to meet research objectives, I have read a number of articles that are
available on internet, to evaluate how to support my team-members in collecting the relevant
information. As main strength of mine is my technical skills so, I have helped group people in
gathering secondary information from authenticate resources. Here, I have evaluated that today,
a number of organizations are utilizing the online platform to reach their targeted audience and
accounts of social media, by using various channels of online technology. It includes retailing,
manufacturing, telecommunication businesses and more, all these types of companies use social
media to reach at their potential customers (Hu and et. al., 2019). As cyber security also
influences the consumer buying behavior that creates a threat for those companies who have no
online presence. So, it assists the organizations to increase their online presence, in order to
attract potential customers towards own products and services (Malwa, 2019). Therefore, to
analyze how firms utilize cyber security and internet applications for enhancing customer base,
as well as type of challenges they are faced, as a team-member, I have supported my team
members in selecting the business like retailers that offer same products and services but with
different price rates to retain customers. At initial stage, I face difficulties in supervising my
influencing others is the most effective one, that helps me to receive the best ideas from each
group member for completion of each activity in best way. Along with this, under group
meetings, I have discussed type of challenges, issues and problems that may arise while doing
tasks. At these meetings, my team-members have exchanged ideas or brainstorm with each other,
in order to come up with the best as well as most creative team solutions to handle the
challenges.
3. Personal Contribution to Literature Review
As under this team, there are three members involved, therefore, each one has given
specific tasks. With this assistance, apart from introduction and research questions, which are
considered as main part of a project, upon whom entire result is based, so, to perform this, I have
worked under guidance of my seniors, as they are well experienced in selection of topic and
conduct a report on same. In this regard, after framing appropriate research aim and questions of
Cyber Security, the another task of mine is to evaluate challenges that faced by organizations, I
have analyzed that to move business on online platform, it is essential for firms to identify the
challenges of same and develop proper strategies to overcome. In order to conduct literature
review on Cyber Security to meet research objectives, I have read a number of articles that are
available on internet, to evaluate how to support my team-members in collecting the relevant
information. As main strength of mine is my technical skills so, I have helped group people in
gathering secondary information from authenticate resources. Here, I have evaluated that today,
a number of organizations are utilizing the online platform to reach their targeted audience and
accounts of social media, by using various channels of online technology. It includes retailing,
manufacturing, telecommunication businesses and more, all these types of companies use social
media to reach at their potential customers (Hu and et. al., 2019). As cyber security also
influences the consumer buying behavior that creates a threat for those companies who have no
online presence. So, it assists the organizations to increase their online presence, in order to
attract potential customers towards own products and services (Malwa, 2019). Therefore, to
analyze how firms utilize cyber security and internet applications for enhancing customer base,
as well as type of challenges they are faced, as a team-member, I have supported my team
members in selecting the business like retailers that offer same products and services but with
different price rates to retain customers. At initial stage, I face difficulties in supervising my
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

team-members to collect relevant information on chosen topic. The reason behind this is
experience gap, where I am much experienced in this field then other two members. Along with
this, ineffective communication also create barriers in making collaboration within team.
Therefore, I have improved my communication skills and leadership abilities first, to support
group people in performing their task effectively. In this regard, I have supported team members
in identifying relevant information on chosen topic by collection of authenticate sources.
4. Personal Contribution to Research Methodology Report
4.1 Research Methodology
Further activities that I have done include – prepare research methodology; arguments on
concept of qualitative and quantitative; and the last one is to identify the challenges in cyber
security. Hereby, first activity i.e. selection of topic is the most important one, because to choose
this, I have to make proper discussion with team members, to analyze what they think and if they
are able to conduct research on same. Therefore, for this process, I have made a number of
meetings with other two members to make a proper interaction with them. Furthermore, another
responsibility of mine to conduct project was selecting appropriate techniques, approaches and
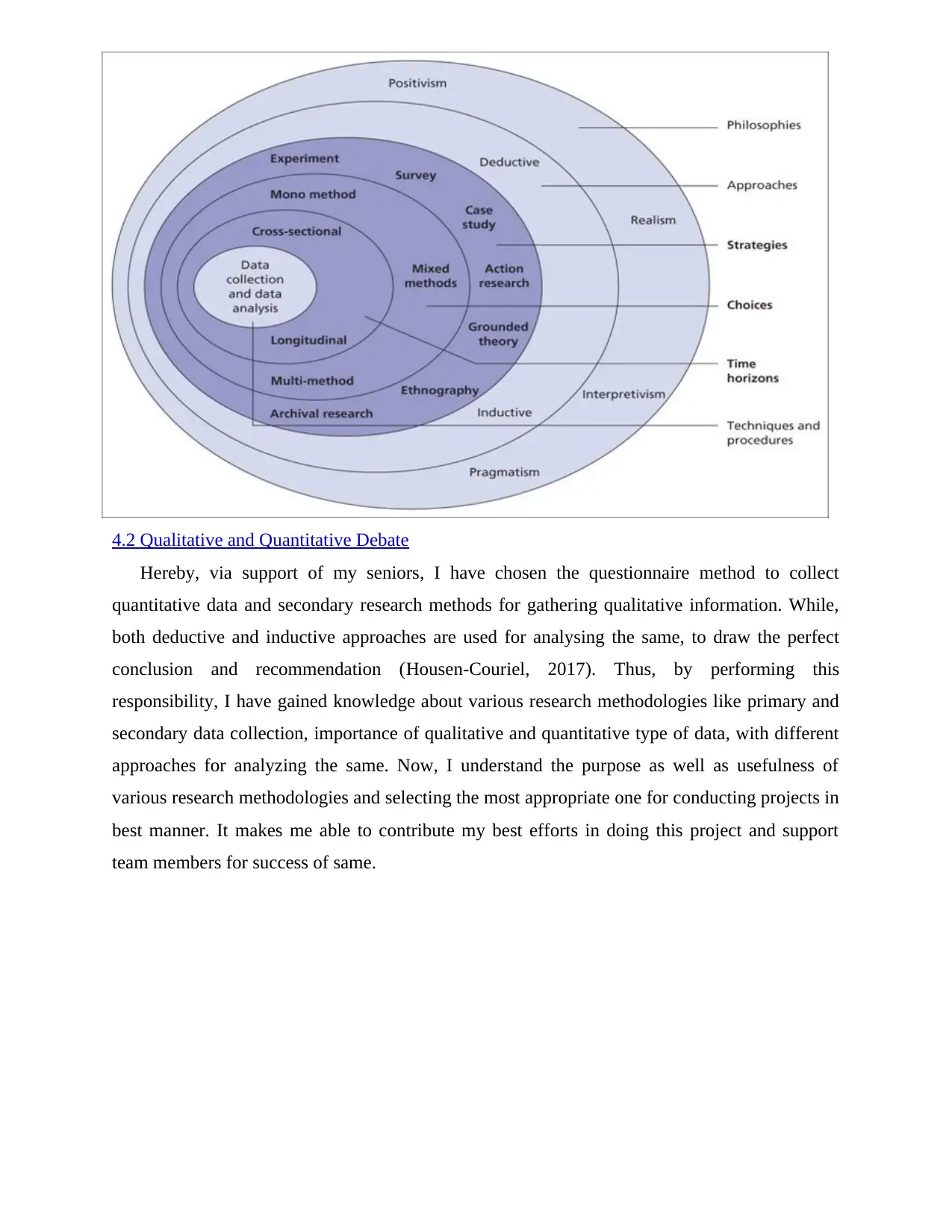
research approaches under research methodology section. For collecting information on research
methodology and different approaches, which was needed to conduct present project on Cyber
Security, I have used the concept of research onion. It helps in describing a number of
philosophies, approaches, strategies, choices, time horizons and different techniques, among
whom specific methods can be used.
experience gap, where I am much experienced in this field then other two members. Along with
this, ineffective communication also create barriers in making collaboration within team.
Therefore, I have improved my communication skills and leadership abilities first, to support
group people in performing their task effectively. In this regard, I have supported team members
in identifying relevant information on chosen topic by collection of authenticate sources.
4. Personal Contribution to Research Methodology Report
4.1 Research Methodology
Further activities that I have done include – prepare research methodology; arguments on
concept of qualitative and quantitative; and the last one is to identify the challenges in cyber
security. Hereby, first activity i.e. selection of topic is the most important one, because to choose
this, I have to make proper discussion with team members, to analyze what they think and if they
are able to conduct research on same. Therefore, for this process, I have made a number of
meetings with other two members to make a proper interaction with them. Furthermore, another
responsibility of mine to conduct project was selecting appropriate techniques, approaches and
research approaches under research methodology section. For collecting information on research
methodology and different approaches, which was needed to conduct present project on Cyber
Security, I have used the concept of research onion. It helps in describing a number of
philosophies, approaches, strategies, choices, time horizons and different techniques, among
whom specific methods can be used.
4.2 Qualitative and Quantitative Debate
Hereby, via support of my seniors, I have chosen the questionnaire method to collect
quantitative data and secondary research methods for gathering qualitative information. While,
both deductive and inductive approaches are used for analysing the same, to draw the perfect
conclusion and recommendation (Housen-Couriel, 2017). Thus, by performing this
responsibility, I have gained knowledge about various research methodologies like primary and
secondary data collection, importance of qualitative and quantitative type of data, with different
approaches for analyzing the same. Now, I understand the purpose as well as usefulness of
various research methodologies and selecting the most appropriate one for conducting projects in
best manner. It makes me able to contribute my best efforts in doing this project and support
team members for success of same.
Hereby, via support of my seniors, I have chosen the questionnaire method to collect
quantitative data and secondary research methods for gathering qualitative information. While,
both deductive and inductive approaches are used for analysing the same, to draw the perfect
conclusion and recommendation (Housen-Couriel, 2017). Thus, by performing this
responsibility, I have gained knowledge about various research methodologies like primary and
secondary data collection, importance of qualitative and quantitative type of data, with different
approaches for analyzing the same. Now, I understand the purpose as well as usefulness of
various research methodologies and selecting the most appropriate one for conducting projects in
best manner. It makes me able to contribute my best efforts in doing this project and support
team members for success of same.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Qualitative data mainly helps in collecting theoretical information from different articles,
books and journals where, previous researchers have already collected data on same topic. For
example – By using qualitative technique, I have analyzed that notion of cyber security is needed
to bring awareness among public, that influence their buying behavior as well as assists private
organizations to increase the online presence of same (Hareide and et. al., 2018). Hereby, I have
analyzed that today, people are spending most of their time on social media. This would provide
opportunity to me to analyze how organizations use social media and different channels to attract
their targeted audience towards products and services of them and influence purchasing behavior
of them. While in context with quantitative technique, I have evaluated that this method mostly
use to collect statistical information (Voramontri and Klieb, 2018). For example- To analyze
different challenges of cyber security like malware, virus etc. and how companies frame
strategies to overcome from respective possible cyber threats to maintain the confidentiality, I
have used quantitative techniques. With this assistance, I have collected data about how many
companies of Australia are facing the issues related to cyber security. Therefore, through survey
report, I have evaluated that more than 59% of organisations in Australia are faced cyber crime
issues. While, 30% of companies faced e-mail compromise incident and 33% have been targeted
due to pishing emails (Cyber security megatrends and what you can do, 2017). Therefore, it is
essential for firms to install appropriate software for protecting their business from hackers,
malware and other virtual invaders, for positively influencing consumer buying behavior.
books and journals where, previous researchers have already collected data on same topic. For
example – By using qualitative technique, I have analyzed that notion of cyber security is needed
to bring awareness among public, that influence their buying behavior as well as assists private
organizations to increase the online presence of same (Hareide and et. al., 2018). Hereby, I have
analyzed that today, people are spending most of their time on social media. This would provide
opportunity to me to analyze how organizations use social media and different channels to attract
their targeted audience towards products and services of them and influence purchasing behavior
of them. While in context with quantitative technique, I have evaluated that this method mostly
use to collect statistical information (Voramontri and Klieb, 2018). For example- To analyze
different challenges of cyber security like malware, virus etc. and how companies frame
strategies to overcome from respective possible cyber threats to maintain the confidentiality, I
have used quantitative techniques. With this assistance, I have collected data about how many
companies of Australia are facing the issues related to cyber security. Therefore, through survey
report, I have evaluated that more than 59% of organisations in Australia are faced cyber crime
issues. While, 30% of companies faced e-mail compromise incident and 33% have been targeted
due to pishing emails (Cyber security megatrends and what you can do, 2017). Therefore, it is
essential for firms to install appropriate software for protecting their business from hackers,
malware and other virtual invaders, for positively influencing consumer buying behavior.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Thus, both qualitative and quantitative methods are helped me in collecting relevant and
specific information on cyber security.
5. Reflection on Research Experience
Thus, conducting a project on this topic is quite interesting for me and my team-
members. This would help in increasing the knowledge of me in technology field, where
identifying the challenges as well as remedies to overcome from same, retain interest of my
group throughout entire research. Hereby, my mentors and supervisors have helped my team
members to distribute roles and responsibilities among each other. As my research skills and
leadership qualities are sharp and effective, so, I have given responsibility to establish proper
objectives of the present project for conducting research.
6. Personal Statement
In the light of overall study, enables me with enhancement of knowledge level regarding
with possible methods to conduct a project, on such an interesting topic i.e. cyber security. The
apprehensions of this investigation endowed me with desired understanding, which need to
exercise this acumen and contribute my best efforts for successful completion of project.
Furthermore, making apprehensions and working on given project, prove beneficial for me to
enhance research skills and develop more competence for taking challenges to complete future
challenges. Thus, working on this project, helps me in analysing the skills that I need to improve,
in order to bring collaboration among team-members. It includes communication and leadership
skills, which are necessary to work in a team. Therefore, by developing these abilities, I have
become able to work in such a team, where conflicts were mostly occurred due to experience
gap. This would also enable me to conduct future projects in group more effectively.
7. Conclusion
Thus, from overall discussion, it has been analyzed that to do a project in group, it is
essential that each member has to contribute equal roles and responsibilities, as well as support
each other to complete the same on time. This would help in maintaining and managing
efficiencies of result more effectively.
specific information on cyber security.
5. Reflection on Research Experience
Thus, conducting a project on this topic is quite interesting for me and my team-
members. This would help in increasing the knowledge of me in technology field, where
identifying the challenges as well as remedies to overcome from same, retain interest of my
group throughout entire research. Hereby, my mentors and supervisors have helped my team
members to distribute roles and responsibilities among each other. As my research skills and
leadership qualities are sharp and effective, so, I have given responsibility to establish proper
objectives of the present project for conducting research.
6. Personal Statement
In the light of overall study, enables me with enhancement of knowledge level regarding
with possible methods to conduct a project, on such an interesting topic i.e. cyber security. The
apprehensions of this investigation endowed me with desired understanding, which need to
exercise this acumen and contribute my best efforts for successful completion of project.
Furthermore, making apprehensions and working on given project, prove beneficial for me to
enhance research skills and develop more competence for taking challenges to complete future
challenges. Thus, working on this project, helps me in analysing the skills that I need to improve,
in order to bring collaboration among team-members. It includes communication and leadership
skills, which are necessary to work in a team. Therefore, by developing these abilities, I have
become able to work in such a team, where conflicts were mostly occurred due to experience
gap. This would also enable me to conduct future projects in group more effectively.
7. Conclusion
Thus, from overall discussion, it has been analyzed that to do a project in group, it is
essential that each member has to contribute equal roles and responsibilities, as well as support
each other to complete the same on time. This would help in maintaining and managing
efficiencies of result more effectively.

REFRENCES
Books and Journals
Hareide, O. S. and et. al., 2018. Enhancing navigator competence by demonstrating maritime
cyber security. The Journal of Navigation. 71(5). pp.1025-1039.
Voramontri, D. and Klieb, L., 2018. Impact of social media on consumer
behaviour. International Journal of Information and Decision Sciences. 462. pp.1-24.
Malwa, S., 2019. RESEARCH STUDY ON EFFECT OF SOCIAL MEDIA ON CONSUMER
BUYING BEHAVIOR. NOLEGEIN-Journal of Consumer Behavior & Market
Research, pp.35-42.
Hu, Y. and et. al., 2019. Generating business intelligence through social media analytics:
measuring brand personality with consumer-, employee-, and firm-generated
content. Journal of Management Information Systems. 36(3). pp.893-930.
Dua, S., 2017. Digital India: Opportunities and Challenges. International Journal of Science
Technology and Management, 6(3), p.6.
Housen-Couriel, D., 2017. National Cyber Security Organisation, Israel. NATO Cooperative
Cyber Defence Centre of Excellence.
Hussain, Z. and et. al., 2017. E-Banking Challenges in Pakistan: An Empirical Study. Journal of
Computer and Communications. 5(02). p.1.
Jennings, S., 2017. Creative drama in groupwork. Routledge.
Brown, A., 2017. Groupwork. Routledge.
Foulkes, S. H., 2018. Introduction to group-analytic psychotherapy: Studies in the social
integration of individuals and groups. Routledge.
Morris, M. and Tsakissiris, J., 2017. The importance of context in management education: A
report. Journal of Learning Design. 10(1). pp.1-10.
Harris, T. E. and Sherblom, J. C., 2018. Small group and team communication. Waveland Press.
Reibis, R. and et. al., 2019. The importance of return to work: How to achieve optimal
reintegration in ACS patients. European journal of preventive cardiology,
p.2047487319839263.
McLeay, F., Robson, A. and Yusoff, M., 2017. New applications for importance-performance
analysis (IPA) in higher education: Understanding student satisfaction. Journal of
Management Development. 36(6). pp.780-800.
Jennings, S. E., Sutherlin, M. and Counts, A. E., 2018. The importance of social presence in an
online class--“Cause One is the Loneliest Number You Will Every Do”. Journal of
Research in Business Information Systems, p.1.
Online
Cyber security megatrends and what you can do. 2017. [Online] Available Through:
<https://www.telstra.com.au/business-enterprise/campaigns/cyber-security-report>.
Books and Journals
Hareide, O. S. and et. al., 2018. Enhancing navigator competence by demonstrating maritime
cyber security. The Journal of Navigation. 71(5). pp.1025-1039.
Voramontri, D. and Klieb, L., 2018. Impact of social media on consumer
behaviour. International Journal of Information and Decision Sciences. 462. pp.1-24.
Malwa, S., 2019. RESEARCH STUDY ON EFFECT OF SOCIAL MEDIA ON CONSUMER
BUYING BEHAVIOR. NOLEGEIN-Journal of Consumer Behavior & Market
Research, pp.35-42.
Hu, Y. and et. al., 2019. Generating business intelligence through social media analytics:
measuring brand personality with consumer-, employee-, and firm-generated
content. Journal of Management Information Systems. 36(3). pp.893-930.
Dua, S., 2017. Digital India: Opportunities and Challenges. International Journal of Science
Technology and Management, 6(3), p.6.
Housen-Couriel, D., 2017. National Cyber Security Organisation, Israel. NATO Cooperative
Cyber Defence Centre of Excellence.
Hussain, Z. and et. al., 2017. E-Banking Challenges in Pakistan: An Empirical Study. Journal of
Computer and Communications. 5(02). p.1.
Jennings, S., 2017. Creative drama in groupwork. Routledge.
Brown, A., 2017. Groupwork. Routledge.
Foulkes, S. H., 2018. Introduction to group-analytic psychotherapy: Studies in the social
integration of individuals and groups. Routledge.
Morris, M. and Tsakissiris, J., 2017. The importance of context in management education: A
report. Journal of Learning Design. 10(1). pp.1-10.
Harris, T. E. and Sherblom, J. C., 2018. Small group and team communication. Waveland Press.
Reibis, R. and et. al., 2019. The importance of return to work: How to achieve optimal
reintegration in ACS patients. European journal of preventive cardiology,
p.2047487319839263.
McLeay, F., Robson, A. and Yusoff, M., 2017. New applications for importance-performance
analysis (IPA) in higher education: Understanding student satisfaction. Journal of
Management Development. 36(6). pp.780-800.
Jennings, S. E., Sutherlin, M. and Counts, A. E., 2018. The importance of social presence in an
online class--“Cause One is the Loneliest Number You Will Every Do”. Journal of
Research in Business Information Systems, p.1.
Online
Cyber security megatrends and what you can do. 2017. [Online] Available Through:
<https://www.telstra.com.au/business-enterprise/campaigns/cyber-security-report>.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





