Business Impact Analysis and Risk Mitigation for AE Kalina Cycle
VerifiedAdded on 2020/03/16
|13
|2496
|60
Report
AI Summary
This report provides a comprehensive Business Impact Analysis (BIA) for the AE Kalina Cycle, focusing on risk mitigation strategies. It begins with an overview of BIA, explaining its role in determining and evaluating the effects of disruptions on critical business operations. The report details risk descriptions, including big data collection methods and critical process determination. It outlines the step-by-step BIA process, covering outage impacts, estimated downtime, resource requirements, and recovery priorities. The analysis identifies and assesses various risks, such as system failures, natural disasters, human-caused catastrophes, and legal costs. Furthermore, it examines specific risks like increased security threats from outdated ERP systems, unauthorized access to customer data, and data leakage. The report also delves into the implications of non-compliance with standards. The conclusion emphasizes the importance of BIA in preventing and mitigating risks to ensure business continuity. It uses MTD, RTO and RPO to show how the business could recover from a disaster.

Running Head: Risk Mitigation of an Organisation
Risk Management of the AE Kalina Cycle
Risk Management of the AE Kalina Cycle
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Business Impact Analysis
Table of Contents
Overview....................................................................................................................................2
Risk Description of an organisation...........................................................................................2
Big Data Collection....................................................................................................................2
Determine Process and Risk Critically......................................................................................3
Step one of the BIA Process...................................................................................................3
Identify Outage Impacts and Estimated:.............................................................................3
Outage Impacts...........................................................................................................................4
Estimated Downtime..............................................................................................................5
Identify Resource Requirements............................................................................................6
Identify Recovery Priorities for System Resources................................................................6
Analysis on the Business Impact Analysis for the critical risks................................................6
One risk’s that put more focus...................................................................................................8
Increased security threat and exposure as a result of using an out-dated ERP system..........8
Conclusion..................................................................................................................................9
References................................................................................................................................10
1
Table of Contents
Overview....................................................................................................................................2
Risk Description of an organisation...........................................................................................2
Big Data Collection....................................................................................................................2
Determine Process and Risk Critically......................................................................................3
Step one of the BIA Process...................................................................................................3
Identify Outage Impacts and Estimated:.............................................................................3
Outage Impacts...........................................................................................................................4
Estimated Downtime..............................................................................................................5
Identify Resource Requirements............................................................................................6
Identify Recovery Priorities for System Resources................................................................6
Analysis on the Business Impact Analysis for the critical risks................................................6
One risk’s that put more focus...................................................................................................8
Increased security threat and exposure as a result of using an out-dated ERP system..........8
Conclusion..................................................................................................................................9
References................................................................................................................................10
1

Business Impact Analysis
Overview
Business Impact Analysis is the systematic approach for determining and evaluating the
possible effects for breaking the critical business operations as a result of a disaster, calamity
or emergency. It is an essential component of the organisations business continuous plan. It
generally includes a descriptive component to expose the susceptibilities and for this planning
component is essential developing the strategies so as to overcomer from the risks or the
disasters (Scholten et al., 2014). Business continuity process analyses the critical function
which mainly identifies and computes to the greater impact of the loss of the functions. It
basically identifies the effects on the financial, life, regulatory, legal etc. of the natural and
the man-made events on business operations.
Risk Description of an organisation
The risk assessment is an easy way of identifying the potential hazards such as any disaster
calamity like earthquake, supplier failure, fire or cyber-attack, which generally tends to
evaluate the areas which are more prone and our vulnerable for occurring of the hazards. Risk
assessment generally includes the people, property, supply chain, information technology,
business reputation etc. A mitigation strategy has been developed for reducing the maximum
probability of occurrence of any hazardous activity which have the significant impact on it
(Pritchard and PMP, 2014). In the risk assessment stage the BIA is been examined against the
hazardous scenarios which have the adverse effects on impacting on the business operations.
It is generally used for making the justification in the cost from prevention and mitigation of
the risks for implementing and designing the strategies
Big Data Collection
It is the heart of all good calamities or the disaster recovery planning projects. It is essential
for collecting the data and information from the organisations. Those organisations that can
2
Overview
Business Impact Analysis is the systematic approach for determining and evaluating the
possible effects for breaking the critical business operations as a result of a disaster, calamity
or emergency. It is an essential component of the organisations business continuous plan. It
generally includes a descriptive component to expose the susceptibilities and for this planning
component is essential developing the strategies so as to overcomer from the risks or the
disasters (Scholten et al., 2014). Business continuity process analyses the critical function
which mainly identifies and computes to the greater impact of the loss of the functions. It
basically identifies the effects on the financial, life, regulatory, legal etc. of the natural and
the man-made events on business operations.
Risk Description of an organisation
The risk assessment is an easy way of identifying the potential hazards such as any disaster
calamity like earthquake, supplier failure, fire or cyber-attack, which generally tends to
evaluate the areas which are more prone and our vulnerable for occurring of the hazards. Risk
assessment generally includes the people, property, supply chain, information technology,
business reputation etc. A mitigation strategy has been developed for reducing the maximum
probability of occurrence of any hazardous activity which have the significant impact on it
(Pritchard and PMP, 2014). In the risk assessment stage the BIA is been examined against the
hazardous scenarios which have the adverse effects on impacting on the business operations.
It is generally used for making the justification in the cost from prevention and mitigation of
the risks for implementing and designing the strategies
Big Data Collection
It is the heart of all good calamities or the disaster recovery planning projects. It is essential
for collecting the data and information from the organisations. Those organisations that can
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Business Impact Analysis
actually access to the functions and can perform to all the business operations can access to
the critically business functions. The big data collection can actually collected from the
interviews, workshops, questionnaires etc. It is important to have a clear picture of all the
documents and the main mission on the critical analysis on the collection of the information.
Determine Process and Risk Critically
Step one of the BIA Process- Identification of the key systems, functions, processes, etc.
which are critical for the success of the organisation. As these processes are the significant
areas where any failure would cost the company to suffer heavy losses. Information security
in these areas is indispensable so to maintain the smooth functioning of business. Following
are some of the areas where data is required to be safeguarded using proper risk management
techniques.
Mission/Business Process Description
System Failures
Any unwanted threats or malicious activities
happened in the system from the intruders.
Natural Disasters Any natural calamity occurred in an organization
Human Caused Catastrophes
Risks arise due to the frauds made in the organization
by the personnel’s or using the essential information
and sharing to the public domain.
Legal Costs Risks
Cost and loss of income in the legal uncertainty, cost
of litigation.
3
actually access to the functions and can perform to all the business operations can access to
the critically business functions. The big data collection can actually collected from the
interviews, workshops, questionnaires etc. It is important to have a clear picture of all the
documents and the main mission on the critical analysis on the collection of the information.
Determine Process and Risk Critically
Step one of the BIA Process- Identification of the key systems, functions, processes, etc.
which are critical for the success of the organisation. As these processes are the significant
areas where any failure would cost the company to suffer heavy losses. Information security
in these areas is indispensable so to maintain the smooth functioning of business. Following
are some of the areas where data is required to be safeguarded using proper risk management
techniques.
Mission/Business Process Description
System Failures
Any unwanted threats or malicious activities
happened in the system from the intruders.
Natural Disasters Any natural calamity occurred in an organization
Human Caused Catastrophes
Risks arise due to the frauds made in the organization
by the personnel’s or using the essential information
and sharing to the public domain.
Legal Costs Risks
Cost and loss of income in the legal uncertainty, cost
of litigation.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Business Impact Analysis
Identify Outage Impacts and Estimated:
I. System Failures
1) Failure occurs in the System Failures: There are risks that the intruders enter into
the system and divert the files regarding to the information of the company and to the
original transaction failure.
2) Impact- it will result in the failures
3) Responsible Department-Whole Organisational Structure
4) Impact Category: Major
5) Impact Values: 50000-500000
II. Natural Disasters
1. Failure due to Natural Disasters: The failure is occurred in the organisation due to
any natural disaster calamity occurred in the organisation and it mainly affect to the
whole organisational behaviour and stop the all the business operations for the
performance.
2. Impact- loss of useful inventory, turnover loss, loss in the whole organisation.
3. Responsible Department: Natural calamity.
4. Impact Category: catastrophic
5. Impact Values: 100000-1000000
III. Human Caused Catastrophes
1. Failure due to Human Caused Catastrophes – The risks is raised due to the man-
made frauds and crimes, loss of valuable information assets of business.
4
Identify Outage Impacts and Estimated:
I. System Failures
1) Failure occurs in the System Failures: There are risks that the intruders enter into
the system and divert the files regarding to the information of the company and to the
original transaction failure.
2) Impact- it will result in the failures
3) Responsible Department-Whole Organisational Structure
4) Impact Category: Major
5) Impact Values: 50000-500000
II. Natural Disasters
1. Failure due to Natural Disasters: The failure is occurred in the organisation due to
any natural disaster calamity occurred in the organisation and it mainly affect to the
whole organisational behaviour and stop the all the business operations for the
performance.
2. Impact- loss of useful inventory, turnover loss, loss in the whole organisation.
3. Responsible Department: Natural calamity.
4. Impact Category: catastrophic
5. Impact Values: 100000-1000000
III. Human Caused Catastrophes
1. Failure due to Human Caused Catastrophes – The risks is raised due to the man-
made frauds and crimes, loss of valuable information assets of business.
4
Business Impact Analysis
2. Impact- loss of funds affecting the overall profitability of business, financial loss due,
legal repercussions, loss of competitive edge, sabotage.
3. Responsible Department: Individual or personnel’s.
4. Impact Category: major
5. Impact Values: 100000-1000000
IV. Legal Costs Risks: Failure in Legal Costs Risks: The important data is misused by
the members of the organisation, imprisonment, penalties and fines
1. Impact: Loss of sensitive information, bankrupt services, expenditure on the audit of
legal fee.
2. Responsible Department: Finance and Accounts department.
3. Impact Category: major
4. Impact Values: 50000-700000
Outage Impacts
They are the adverse effects because of the failures in the respective field.
Mission/Business Process
Impact Category
Insignific
ant
Minor Major Catastr
ophic
Impact
System Failures
Loss in the system
failures due to
unwanted files and
5
2. Impact- loss of funds affecting the overall profitability of business, financial loss due,
legal repercussions, loss of competitive edge, sabotage.
3. Responsible Department: Individual or personnel’s.
4. Impact Category: major
5. Impact Values: 100000-1000000
IV. Legal Costs Risks: Failure in Legal Costs Risks: The important data is misused by
the members of the organisation, imprisonment, penalties and fines
1. Impact: Loss of sensitive information, bankrupt services, expenditure on the audit of
legal fee.
2. Responsible Department: Finance and Accounts department.
3. Impact Category: major
4. Impact Values: 50000-700000
Outage Impacts
They are the adverse effects because of the failures in the respective field.
Mission/Business Process
Impact Category
Insignific
ant
Minor Major Catastr
ophic
Impact
System Failures
Loss in the system
failures due to
unwanted files and
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Business Impact Analysis
Mission/Business Process
Impact Category
Insignific
ant
Minor Major Catastr
ophic
Impact
folders affected by the
intruders.
Natural Disasters
Occurrence of the
Natural Calamity
which mainly destroy
the business processes
and organization.
Human Caused Catastrophes
When the human
change the relevant
information and data
which has the original
file and folders
change it into
duplicate files and
Loss in the Sensitive
Information.
Legal Costs Risks If the breach of
information security
acts various penalties,
fines and other
6
Mission/Business Process
Impact Category
Insignific
ant
Minor Major Catastr
ophic
Impact
folders affected by the
intruders.
Natural Disasters
Occurrence of the
Natural Calamity
which mainly destroy
the business processes
and organization.
Human Caused Catastrophes
When the human
change the relevant
information and data
which has the original
file and folders
change it into
duplicate files and
Loss in the Sensitive
Information.
Legal Costs Risks If the breach of
information security
acts various penalties,
fines and other
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Business Impact Analysis
Mission/Business Process
Impact Category
Insignific
ant
Minor Major Catastr
ophic
Impact
governmental actions
are imposed.
Estimated Downtime
Maximum Tolerable Downtime (MTD)-It is used for identifying the time duration taken for
detecting the risks in all the business process in which it can be engaged before the
significant damage or to the long term feasibility is threatened. They are been published in to
the same database or the spread sheets which specify all the business processes (Li et al.,
2017).
Recovery Time Objective (RTO) - It is the period of time from the risk been detected to the
recommencement of all the business process.
Recovery Point Objective (RPO) - It is the maximum period of the data been loss when the
disaster counting backwards.
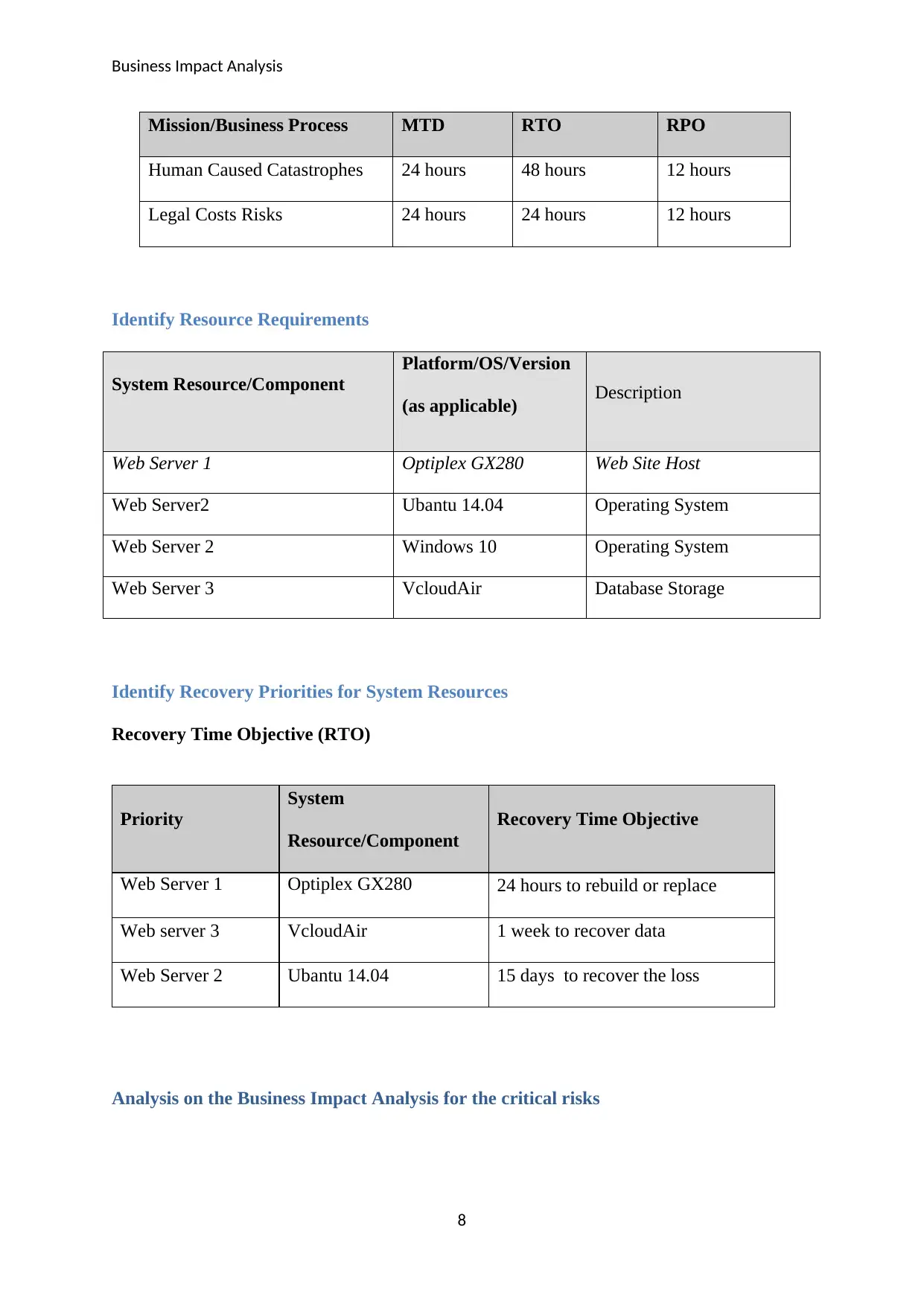
Mission/Business Process MTD RTO RPO
System Failures 72 hours 48 hours
12 hours (last
backup)
Natural Disasters 1 week 15days 48 hours
7
Mission/Business Process
Impact Category
Insignific
ant
Minor Major Catastr
ophic
Impact
governmental actions
are imposed.
Estimated Downtime
Maximum Tolerable Downtime (MTD)-It is used for identifying the time duration taken for
detecting the risks in all the business process in which it can be engaged before the
significant damage or to the long term feasibility is threatened. They are been published in to
the same database or the spread sheets which specify all the business processes (Li et al.,
2017).
Recovery Time Objective (RTO) - It is the period of time from the risk been detected to the
recommencement of all the business process.
Recovery Point Objective (RPO) - It is the maximum period of the data been loss when the
disaster counting backwards.
Mission/Business Process MTD RTO RPO
System Failures 72 hours 48 hours
12 hours (last
backup)
Natural Disasters 1 week 15days 48 hours
7
Business Impact Analysis
Mission/Business Process MTD RTO RPO
Human Caused Catastrophes 24 hours 48 hours 12 hours
Legal Costs Risks 24 hours 24 hours 12 hours
Identify Resource Requirements
System Resource/Component
Platform/OS/Version
(as applicable) Description
Web Server 1 Optiplex GX280 Web Site Host
Web Server2 Ubantu 14.04 Operating System
Web Server 2 Windows 10 Operating System
Web Server 3 VcloudAir Database Storage
Identify Recovery Priorities for System Resources
Recovery Time Objective (RTO)
Priority
System
Resource/Component
Recovery Time Objective
Web Server 1 Optiplex GX280 24 hours to rebuild or replace
Web server 3 VcloudAir 1 week to recover data
Web Server 2 Ubantu 14.04 15 days to recover the loss
Analysis on the Business Impact Analysis for the critical risks
8
Mission/Business Process MTD RTO RPO
Human Caused Catastrophes 24 hours 48 hours 12 hours
Legal Costs Risks 24 hours 24 hours 12 hours
Identify Resource Requirements
System Resource/Component
Platform/OS/Version
(as applicable) Description
Web Server 1 Optiplex GX280 Web Site Host
Web Server2 Ubantu 14.04 Operating System
Web Server 2 Windows 10 Operating System
Web Server 3 VcloudAir Database Storage
Identify Recovery Priorities for System Resources
Recovery Time Objective (RTO)
Priority
System
Resource/Component
Recovery Time Objective
Web Server 1 Optiplex GX280 24 hours to rebuild or replace
Web server 3 VcloudAir 1 week to recover data
Web Server 2 Ubantu 14.04 15 days to recover the loss
Analysis on the Business Impact Analysis for the critical risks
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Business Impact Analysis
1. Injuries and losses to the lives of employees as a result of flooding at AEKC
locations- It provides the speaking approach which mainly combines and provides the
tools for lash flooding and forecasting to reduce and to overcome from the potential
disaster. It mainly affected to the main causes of the business investments, stock in the
business, resources and equipment’s used, plant etc. as well as the treats caused to the
safety of the employees and to the customers. Etc. It made the business closed for the
certain period of time.
2. Increased security threat and exposure as a result of using an out-dated ERP
system- The application security mainly aim to control the design work and to the
systems. The usability of the out-dated ERP system leads to the crashes and to
integration issues. Because the older software versions and are not compatible with the
new products and the services and for this even the browsers and the servers are
adversely affected from this (Verner et al., 2014). It also results in the insufficient
reporting capability which mainly leads to the loss of the data. Using of the old ERP can
lack to the system functionalities.
3. Unauthorized access to customer data as a result of migrating to a cloud HR
solution: The organisation is lacking behind storing the data in the cloud HR technology
as they using the same technology for storing the important data and information of the
customers in the same software. The new technology provides the platform for making
the information secured, authorized and authenticated of the users. The AEKC lacks in
creating the outstanding business views and the functionalities of the latest technologies
without investing in any complex IT solutions. It also heading up to the data loss
prevention which tends to leaked the data to the public domain.
4. Leakage of transaction information to third parties as a result of employees
working on personal computers: In today’s scenario it is very common dealing with
9
1. Injuries and losses to the lives of employees as a result of flooding at AEKC
locations- It provides the speaking approach which mainly combines and provides the
tools for lash flooding and forecasting to reduce and to overcome from the potential
disaster. It mainly affected to the main causes of the business investments, stock in the
business, resources and equipment’s used, plant etc. as well as the treats caused to the
safety of the employees and to the customers. Etc. It made the business closed for the
certain period of time.
2. Increased security threat and exposure as a result of using an out-dated ERP
system- The application security mainly aim to control the design work and to the
systems. The usability of the out-dated ERP system leads to the crashes and to
integration issues. Because the older software versions and are not compatible with the
new products and the services and for this even the browsers and the servers are
adversely affected from this (Verner et al., 2014). It also results in the insufficient
reporting capability which mainly leads to the loss of the data. Using of the old ERP can
lack to the system functionalities.
3. Unauthorized access to customer data as a result of migrating to a cloud HR
solution: The organisation is lacking behind storing the data in the cloud HR technology
as they using the same technology for storing the important data and information of the
customers in the same software. The new technology provides the platform for making
the information secured, authorized and authenticated of the users. The AEKC lacks in
creating the outstanding business views and the functionalities of the latest technologies
without investing in any complex IT solutions. It also heading up to the data loss
prevention which tends to leaked the data to the public domain.
4. Leakage of transaction information to third parties as a result of employees
working on personal computers: In today’s scenario it is very common dealing with
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Business Impact Analysis
the leakage of the data and the information of the organisation. The insiders have become
a major part of the biggest security threat of the company. The retort to the damages of
data formerly has deliberated to security has mutated from shock to shrug. Assaults and
threats on the corporate databases have become the new way of disclosing and making
the data publically (Chen et al., 2013). And a peer group of workers familiarized to
sharing of information which has grown numb to its undesirable consequences. Most of
the threats are being generated form the victimized organisations which mainly allows
the cyber attackers to burrow in and to grant permission for infecting the databases.
Some of the third party contractors take the privilege for breaching the client’s networks
through malice or by accident.
5. Loss of revenue due to non-compliance with Australian standards: It is essential to
measure the entity of the resources so as to avoid the loss of an organisation. It is critical
objective for measuring the revenue and the amount of the assets and of selling expenses
(Chen et al., 2013).
One risk’s that put more focus
Increased security threat and exposure as a result of using an out-dated ERP
system
1. ERP system becoming a liability on organisation- The ERP should be installed
before, was a wise decision made for the making the streamline process and
improving the efficiency on the organisation process. In today’s scenario, ERP is
majorly consuming the majority of the time in the system up gradations, rising
cost of the maintenance cost and the innovation time left for innovating the
business process.
10
the leakage of the data and the information of the organisation. The insiders have become
a major part of the biggest security threat of the company. The retort to the damages of
data formerly has deliberated to security has mutated from shock to shrug. Assaults and
threats on the corporate databases have become the new way of disclosing and making
the data publically (Chen et al., 2013). And a peer group of workers familiarized to
sharing of information which has grown numb to its undesirable consequences. Most of
the threats are being generated form the victimized organisations which mainly allows
the cyber attackers to burrow in and to grant permission for infecting the databases.
Some of the third party contractors take the privilege for breaching the client’s networks
through malice or by accident.
5. Loss of revenue due to non-compliance with Australian standards: It is essential to
measure the entity of the resources so as to avoid the loss of an organisation. It is critical
objective for measuring the revenue and the amount of the assets and of selling expenses
(Chen et al., 2013).
One risk’s that put more focus
Increased security threat and exposure as a result of using an out-dated ERP
system
1. ERP system becoming a liability on organisation- The ERP should be installed
before, was a wise decision made for the making the streamline process and
improving the efficiency on the organisation process. In today’s scenario, ERP is
majorly consuming the majority of the time in the system up gradations, rising
cost of the maintenance cost and the innovation time left for innovating the
business process.
10

Business Impact Analysis
2. Lagging Process: It is the proc3ess of efficiency which mainly have the
significance on the rising past. But since the time has been past there is no such
improvement in the process or to the efficiency (Berger, 2015). All the efforts
should be made on the future complexities. The main target is to achieve the
efficiency in the increasing output.
3. No database support- In today’s scenario it is essential to maintain the
organisational database in the cloud. But there is no flexibility of moving the data
in the cloud storage. It is the smart choice for the current scenario in an
organisation for generating the automatic updates, maintenance, scalability,
accessibility to the real time data etc.
4. Lacking in Workforce- It is based on the employees who are currently working
with an organisation so as to achieve all the tasks. They initially tends to turn the
organisation in the exciting form of the comparison made on time-consuming
methods. Higher the scope of the organisation, higher the main goal of an
organisation.
5. Lack of real-time business information- It is necessary to maintain the real time
connectivity of the business to fasten the process. More ERP enabled companies
more the organisation would reach for achieving the task. It is necessary to look
for the real time collaboration (Berger, 2015).
Conclusion
It is essential in today’s scenario from preventing for the risks and the threats which has
occurred in an organisation so as to mitigate the risks. The main effectiveness of accessing
the risks totally depends upon the improvement in the organisation and the proper strategies
being implemented on time. It is essential to have the security postures on the events which
11
2. Lagging Process: It is the proc3ess of efficiency which mainly have the
significance on the rising past. But since the time has been past there is no such
improvement in the process or to the efficiency (Berger, 2015). All the efforts
should be made on the future complexities. The main target is to achieve the
efficiency in the increasing output.
3. No database support- In today’s scenario it is essential to maintain the
organisational database in the cloud. But there is no flexibility of moving the data
in the cloud storage. It is the smart choice for the current scenario in an
organisation for generating the automatic updates, maintenance, scalability,
accessibility to the real time data etc.
4. Lacking in Workforce- It is based on the employees who are currently working
with an organisation so as to achieve all the tasks. They initially tends to turn the
organisation in the exciting form of the comparison made on time-consuming
methods. Higher the scope of the organisation, higher the main goal of an
organisation.
5. Lack of real-time business information- It is necessary to maintain the real time
connectivity of the business to fasten the process. More ERP enabled companies
more the organisation would reach for achieving the task. It is necessary to look
for the real time collaboration (Berger, 2015).
Conclusion
It is essential in today’s scenario from preventing for the risks and the threats which has
occurred in an organisation so as to mitigate the risks. The main effectiveness of accessing
the risks totally depends upon the improvement in the organisation and the proper strategies
being implemented on time. It is essential to have the security postures on the events which
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





