Business Intelligence Report: Data Analysis and Loan Delinquency
VerifiedAdded on 2023/06/03
|28
|4403
|439
Report
AI Summary
This report delves into various aspects of business intelligence, starting with the importance of electronic information recording systems, particularly in healthcare. It examines the evolution of electronically stored health records and the crucial role of data security. The report then transitions to a practical application, analyzing loan delinquency using RapidMiner, exploring data attributes, and interpreting correlation matrices. The analysis includes insights into customer demographics, loan defaulting habits, and the utilization of unsecured lines. The document concludes by highlighting the significance of data management in organizational decision-making and compliance with regulatory requirements, emphasizing the need for robust data protection measures.

Running head: BUSINESS INTELLIGENCE
Business Intelligence
Name of the Student
Name of the University
Course ID
Business Intelligence
Name of the Student
Name of the University
Course ID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BUSINESS INTELLIGENCE
Table of Contents
Task 1...............................................................................................................................................2
Introduction..................................................................................................................................2
Importance of electronic information recording system..............................................................3
Detecting the Evolution in electronically stored health record...................................................4
Task 2:.............................................................................................................................................7
Task 2.1:......................................................................................................................................7
Task 2.2:....................................................................................................................................13
Task 2.3:....................................................................................................................................16
Task 2.4......................................................................................................................................17
Task 3.............................................................................................................................................19
Task 3.1..........................................................................................................................................19
Task 3.2..........................................................................................................................................19
Task 3.3..........................................................................................................................................20
Task 3.4..........................................................................................................................................22
References......................................................................................................................................24
Table of Contents
Task 1...............................................................................................................................................2
Introduction..................................................................................................................................2
Importance of electronic information recording system..............................................................3
Detecting the Evolution in electronically stored health record...................................................4
Task 2:.............................................................................................................................................7
Task 2.1:......................................................................................................................................7
Task 2.2:....................................................................................................................................13
Task 2.3:....................................................................................................................................16
Task 2.4......................................................................................................................................17
Task 3.............................................................................................................................................19
Task 3.1..........................................................................................................................................19
Task 3.2..........................................................................................................................................19
Task 3.3..........................................................................................................................................20
Task 3.4..........................................................................................................................................22
References......................................................................................................................................24

2BUSINESS INTELLIGENCE
Task 1
Introduction
Privacy concerns in the health research has now a day become one issue that attract
considerable attention. In designing relevant health care service, research is required regarding
health related issues. Data or information are considered as one vital asset of any organization. In
the information set, special attention needs to be given on confidential information. The
organization should provide proper focus on maintaining terms of confidentiality of the
information set. Securing confidential information by using different software and hardware is
known as information security. It implies a combined internal and external system of operation
where collected information and data are kept protected. In functioning of an organization,
recorded data and information plat several important roles. The information security consists of
different functions. The first primary responsibility is to maintain the privacy of the collected
data. A secure information system also protects capacity of the concerned organization in
performing its assigned functions. Another important aspect the security to the accessed
technology of the organization. Organization gives special attention to protection of the
information as the unauthorized access to the confidential information has adverse effect on
people directly or indirectly connected to the organization.
All the health related data in Australia re documented under the supervision of digital
health agency of Australia. With increasing prevalence of various health issues, load of gathered
information is increasing at a rapid pace in a very short span of time. The concerned agency
gathers and maintains all these health related information. Growing concerns for various diseases
encourage more people to take health care services. The number of people willing to have
different health care service far exceed the number of available service providers
Task 1
Introduction
Privacy concerns in the health research has now a day become one issue that attract
considerable attention. In designing relevant health care service, research is required regarding
health related issues. Data or information are considered as one vital asset of any organization. In
the information set, special attention needs to be given on confidential information. The
organization should provide proper focus on maintaining terms of confidentiality of the
information set. Securing confidential information by using different software and hardware is
known as information security. It implies a combined internal and external system of operation
where collected information and data are kept protected. In functioning of an organization,
recorded data and information plat several important roles. The information security consists of
different functions. The first primary responsibility is to maintain the privacy of the collected
data. A secure information system also protects capacity of the concerned organization in
performing its assigned functions. Another important aspect the security to the accessed
technology of the organization. Organization gives special attention to protection of the
information as the unauthorized access to the confidential information has adverse effect on
people directly or indirectly connected to the organization.
All the health related data in Australia re documented under the supervision of digital
health agency of Australia. With increasing prevalence of various health issues, load of gathered
information is increasing at a rapid pace in a very short span of time. The concerned agency
gathers and maintains all these health related information. Growing concerns for various diseases
encourage more people to take health care services. The number of people willing to have
different health care service far exceed the number of available service providers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BUSINESS INTELLIGENCE
(Digitalhealth.gov.au. 2018). Therefore, maintenance of detailed information regarding about the
individual recipient has become extremely important. Information are collected regarding
personal details and status of health. The technological advancement in several equipment and
machinery used by different health care service unit increases information availability related to
individual recipient. Data related to prenatal testing is the most easily accessible. Analysis of the
health related risk factors is an important aspect determining continuation of required services.
Maintenance of proper data and information also provide protection against unjustified allegation
or claims. In addition to direct health care, various other aspects are considered under primary
health care service. It is the responsibility of the service providers to document observations and
instructions. Intervention by the third party is often observed in the system where relevant
information are used to pay for the used services.
Importance of electronic information recording system
Health care organizations today pay great attention in securing information. Given large
volume of health care data, security system is designed to maintain confidentiality of the
personal information. Unless proper security, it would be very easy to access and misuse these
information. Now, information are recorded and shared using electronic medium instead of
earlier paper based method of documentation (Dinev et al. 2018). The paper-based method of
photocopying important documents is a laborious process and require more time compared to
storing data electronically.
Various sources have been used in gathering the relevant data, which is combined and
connected to other profiles. Therefore, with the electronic process it is easier exploring the
database within the build network for extracting the data from different remote locations.
Nevertheless, the system relevantly increases the chance of third party accesses of the data,
(Digitalhealth.gov.au. 2018). Therefore, maintenance of detailed information regarding about the
individual recipient has become extremely important. Information are collected regarding
personal details and status of health. The technological advancement in several equipment and
machinery used by different health care service unit increases information availability related to
individual recipient. Data related to prenatal testing is the most easily accessible. Analysis of the
health related risk factors is an important aspect determining continuation of required services.
Maintenance of proper data and information also provide protection against unjustified allegation
or claims. In addition to direct health care, various other aspects are considered under primary
health care service. It is the responsibility of the service providers to document observations and
instructions. Intervention by the third party is often observed in the system where relevant
information are used to pay for the used services.
Importance of electronic information recording system
Health care organizations today pay great attention in securing information. Given large
volume of health care data, security system is designed to maintain confidentiality of the
personal information. Unless proper security, it would be very easy to access and misuse these
information. Now, information are recorded and shared using electronic medium instead of
earlier paper based method of documentation (Dinev et al. 2018). The paper-based method of
photocopying important documents is a laborious process and require more time compared to
storing data electronically.
Various sources have been used in gathering the relevant data, which is combined and
connected to other profiles. Therefore, with the electronic process it is easier exploring the
database within the build network for extracting the data from different remote locations.
Nevertheless, the system relevantly increases the chance of third party accesses of the data,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BUSINESS INTELLIGENCE
which is being stored. Hence, the overall system indicates the absence of adequate security,
which is not protecting the overall data of the organization, while making the access process
easy. The individual can access the data without leaving any kind of trace for such kind of
incident. Moreover, the system has directly allowed the service providers to understand the trend
of the data, which indicates the health conditions of the population. The service providers depict
easy access and understanding of the information presented in data based (Van Cauteren et al.
2016). The information is relevantly used with the advancements in the technology for
supporting the electronic health care record to the individuals. Mobile technology is also used in
detecting the required level of data for the individuals. The major significance of HER is to
support activities of the industry. Thus, with the continuous evolution of the system along with
the improvements directly increase the quality of health care service that is being contributed to
the overall system.
There are different measures, where the information related to the statues of store data is
electronically kept and reduces the overall error processing. Therefore, with this measure risk of
malpractices can be avoided for meeting the reimbursement claims. However, there are
drawback of the current legal framework that is being used in the health care recording process.
Moreover, the obligation of the health care is also based on electronic and paper-based methods.
Thus, it could be detected that the confidentiality conditions may vary on the information holder.
Detecting the Evolution in electronically stored health record
The rapid growth in the health record burden has relevantly flourished the use of
electronically based recording system, which directly supports the service providers. Therefore,
with the large variation in the nation forced the creation of huge support is electronic health
record. The electronic health record has played a significant role in major hospitals, as its allows
which is being stored. Hence, the overall system indicates the absence of adequate security,
which is not protecting the overall data of the organization, while making the access process
easy. The individual can access the data without leaving any kind of trace for such kind of
incident. Moreover, the system has directly allowed the service providers to understand the trend
of the data, which indicates the health conditions of the population. The service providers depict
easy access and understanding of the information presented in data based (Van Cauteren et al.
2016). The information is relevantly used with the advancements in the technology for
supporting the electronic health care record to the individuals. Mobile technology is also used in
detecting the required level of data for the individuals. The major significance of HER is to
support activities of the industry. Thus, with the continuous evolution of the system along with
the improvements directly increase the quality of health care service that is being contributed to
the overall system.
There are different measures, where the information related to the statues of store data is
electronically kept and reduces the overall error processing. Therefore, with this measure risk of
malpractices can be avoided for meeting the reimbursement claims. However, there are
drawback of the current legal framework that is being used in the health care recording process.
Moreover, the obligation of the health care is also based on electronic and paper-based methods.
Thus, it could be detected that the confidentiality conditions may vary on the information holder.
Detecting the Evolution in electronically stored health record
The rapid growth in the health record burden has relevantly flourished the use of
electronically based recording system, which directly supports the service providers. Therefore,
with the large variation in the nation forced the creation of huge support is electronic health
record. The electronic health record has played a significant role in major hospitals, as its allows

5BUSINESS INTELLIGENCE
the authorities to understand the history of the patients. The national center has relevantly
indicated that 75% of the service provers are able to enhance the quality of patient care with the
use of electronic data. Consequently, with the electronic recording system the has relevantly
allowed the individuals to access information regarding the patients and make adequate decision
during critical hours (Kim et al. 2017). The system has relevantly provided alerts for the new
medication and physicians that the patients are considering for their health issues. Hence, it could
be understood that the digital health technology has undergone serious changes in recent years
for supporting the hospitals with information regarding the patients. The structure of the health
record system has also played an adequate role in distributing the information of different
hospitals.
The personal information of the Australian citizen and other personal data of the citizen
are stored in the Australian Data Agency. Since the data is composed of the Australian Citizen
personal and crucial, important documents the same needs to be stored and governed by the
regulatory act such as the Privacy Act of 1998. The health record system manages all the
personal information of the organization in a more classified way. The personal data and
information collected and stored are useful and is always viable for an consideration for an
option when the same is identified for the use of the communication process and for the
management purpose. The use of “My Health Record System has enabled and widely used by the
company and the operators for reclassification and arraignment of the data. The crucial
information, which are gathered about the health care products and services rendered are stored
in a structured and the same is stored with privacy. The data protection and the personal data
gathered is a privacy matter for the company and the same should be regulated with the
regulatory bodies by imposing certain rules and guidelines for the same. The regulatory body can
the authorities to understand the history of the patients. The national center has relevantly
indicated that 75% of the service provers are able to enhance the quality of patient care with the
use of electronic data. Consequently, with the electronic recording system the has relevantly
allowed the individuals to access information regarding the patients and make adequate decision
during critical hours (Kim et al. 2017). The system has relevantly provided alerts for the new
medication and physicians that the patients are considering for their health issues. Hence, it could
be understood that the digital health technology has undergone serious changes in recent years
for supporting the hospitals with information regarding the patients. The structure of the health
record system has also played an adequate role in distributing the information of different
hospitals.
The personal information of the Australian citizen and other personal data of the citizen
are stored in the Australian Data Agency. Since the data is composed of the Australian Citizen
personal and crucial, important documents the same needs to be stored and governed by the
regulatory act such as the Privacy Act of 1998. The health record system manages all the
personal information of the organization in a more classified way. The personal data and
information collected and stored are useful and is always viable for an consideration for an
option when the same is identified for the use of the communication process and for the
management purpose. The use of “My Health Record System has enabled and widely used by the
company and the operators for reclassification and arraignment of the data. The crucial
information, which are gathered about the health care products and services rendered are stored
in a structured and the same is stored with privacy. The data protection and the personal data
gathered is a privacy matter for the company and the same should be regulated with the
regulatory bodies by imposing certain rules and guidelines for the same. The regulatory body can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BUSINESS INTELLIGENCE
take several steps by including steps such as imposition of penalty and fines and imposing
several regulatory and criminal proceedings against those involved in the breaching of secured
and private data of the organization (Zingg et al.2015).
The organization has several ways through which the data inflow to the organization such
as data recorded via telephonic conversations, emails and other general letters and all, which may
contain certain other privy data. The Organizations collect several and various kind of
employment related data also, which should also be managed and stored effectively. The process
of data collection and data processing is well managed by the company in terms of managing
relation with the employees of the organizations (Watanabe 2015). It is crucial to note that the
management of the company should assess crucial important situations and scenario where the
data collected and gathered may be for the use in making effective decision process. Situation
arises when the organization reviews data management and the same is used in the various
process and steps of the company like in the contract, workforce management, and meeting the
obligations and rules of the regulatory bodies and for association of goods with the market
information available to the management of the company. There are several requirement by the
Human service Department for the for providing health data records and information which is
ensured by the regulatory body to ensure betted data management and data processing. The
registration are also taken for those interested in registration of the digital health care system and
the security for the same ios an important factor. Certain and several steps needs to be taken into
consideration for enabling and protecting the data of the organizations (Booth et al. 2018).
There should be several steps and accessibility to the data should be given to those
individuals after having careful analyzing of their identity. The parental responsibility should
take several steps by including steps such as imposition of penalty and fines and imposing
several regulatory and criminal proceedings against those involved in the breaching of secured
and private data of the organization (Zingg et al.2015).
The organization has several ways through which the data inflow to the organization such
as data recorded via telephonic conversations, emails and other general letters and all, which may
contain certain other privy data. The Organizations collect several and various kind of
employment related data also, which should also be managed and stored effectively. The process
of data collection and data processing is well managed by the company in terms of managing
relation with the employees of the organizations (Watanabe 2015). It is crucial to note that the
management of the company should assess crucial important situations and scenario where the
data collected and gathered may be for the use in making effective decision process. Situation
arises when the organization reviews data management and the same is used in the various
process and steps of the company like in the contract, workforce management, and meeting the
obligations and rules of the regulatory bodies and for association of goods with the market
information available to the management of the company. There are several requirement by the
Human service Department for the for providing health data records and information which is
ensured by the regulatory body to ensure betted data management and data processing. The
registration are also taken for those interested in registration of the digital health care system and
the security for the same ios an important factor. Certain and several steps needs to be taken into
consideration for enabling and protecting the data of the organizations (Booth et al. 2018).
There should be several steps and accessibility to the data should be given to those
individuals after having careful analyzing of their identity. The parental responsibility should
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7BUSINESS INTELLIGENCE
also be taken care where the responsibility of the same should be regarding authorized
representative should be over the age of 18.
also be taken care where the responsibility of the same should be regarding authorized
representative should be over the age of 18.
8BUSINESS INTELLIGENCE
Task 2:
Task 2.1:
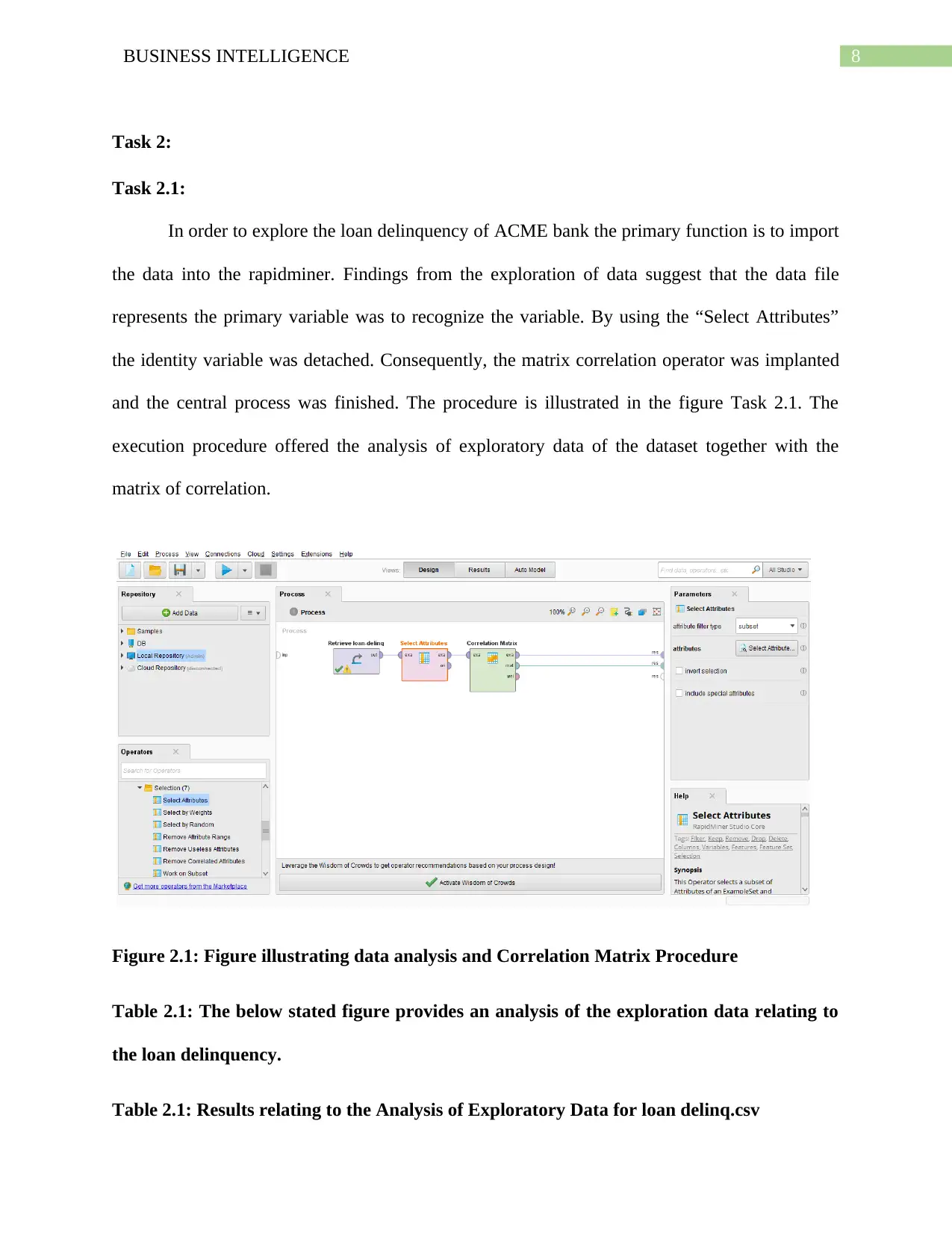
In order to explore the loan delinquency of ACME bank the primary function is to import
the data into the rapidminer. Findings from the exploration of data suggest that the data file
represents the primary variable was to recognize the variable. By using the “Select Attributes”
the identity variable was detached. Consequently, the matrix correlation operator was implanted
and the central process was finished. The procedure is illustrated in the figure Task 2.1. The
execution procedure offered the analysis of exploratory data of the dataset together with the
matrix of correlation.
Figure 2.1: Figure illustrating data analysis and Correlation Matrix Procedure
Table 2.1: The below stated figure provides an analysis of the exploration data relating to
the loan delinquency.
Table 2.1: Results relating to the Analysis of Exploratory Data for loan delinq.csv
Task 2:
Task 2.1:
In order to explore the loan delinquency of ACME bank the primary function is to import
the data into the rapidminer. Findings from the exploration of data suggest that the data file
represents the primary variable was to recognize the variable. By using the “Select Attributes”
the identity variable was detached. Consequently, the matrix correlation operator was implanted
and the central process was finished. The procedure is illustrated in the figure Task 2.1. The
execution procedure offered the analysis of exploratory data of the dataset together with the
matrix of correlation.
Figure 2.1: Figure illustrating data analysis and Correlation Matrix Procedure
Table 2.1: The below stated figure provides an analysis of the exploration data relating to
the loan delinquency.
Table 2.1: Results relating to the Analysis of Exploratory Data for loan delinq.csv
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BUSINESS INTELLIGENCE
As understood from the analysis of data it represents that to review the information
relating to loan delinquency that has been collected. The information comprises the data relating
to the 1.5 lakh customers of bank. Additionally, it is noticed that barring the monthly earnings
and number of dependents information relating to all the attributes are present in it. Data relating
to the monthly earnings of 29731 customers are missing. Similarly, data relating to the total
number of dependents for 3924 customers are also omitted.
As understood from the analysis of data it represents that to review the information
relating to loan delinquency that has been collected. The information comprises the data relating
to the 1.5 lakh customers of bank. Additionally, it is noticed that barring the monthly earnings
and number of dependents information relating to all the attributes are present in it. Data relating
to the monthly earnings of 29731 customers are missing. Similarly, data relating to the total
number of dependents for 3924 customers are also omitted.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10BUSINESS INTELLIGENCE
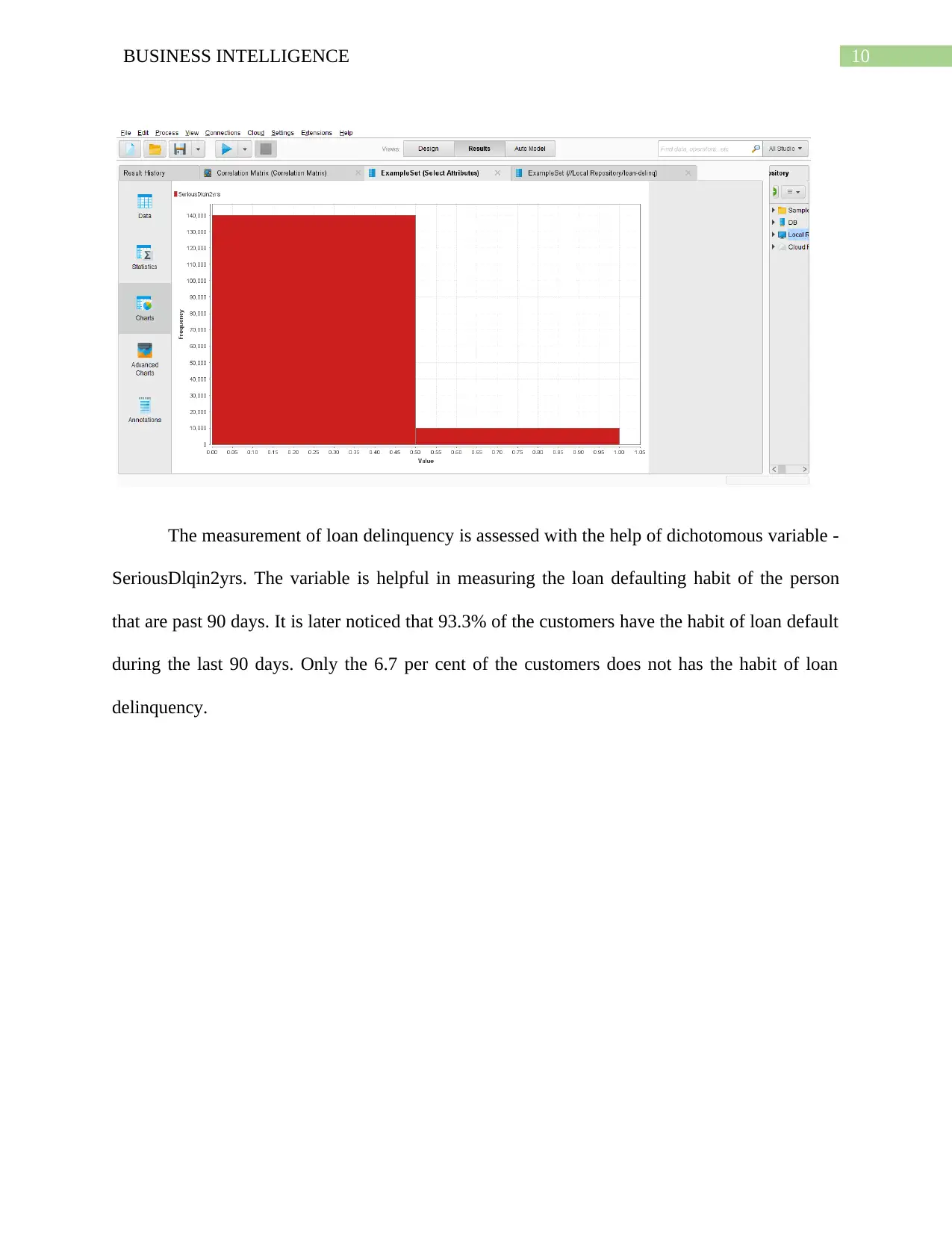
The measurement of loan delinquency is assessed with the help of dichotomous variable -
SeriousDlqin2yrs. The variable is helpful in measuring the loan defaulting habit of the person
that are past 90 days. It is later noticed that 93.3% of the customers have the habit of loan default
during the last 90 days. Only the 6.7 per cent of the customers does not has the habit of loan
delinquency.
The measurement of loan delinquency is assessed with the help of dichotomous variable -
SeriousDlqin2yrs. The variable is helpful in measuring the loan defaulting habit of the person
that are past 90 days. It is later noticed that 93.3% of the customers have the habit of loan default
during the last 90 days. Only the 6.7 per cent of the customers does not has the habit of loan
delinquency.
11BUSINESS INTELLIGENCE
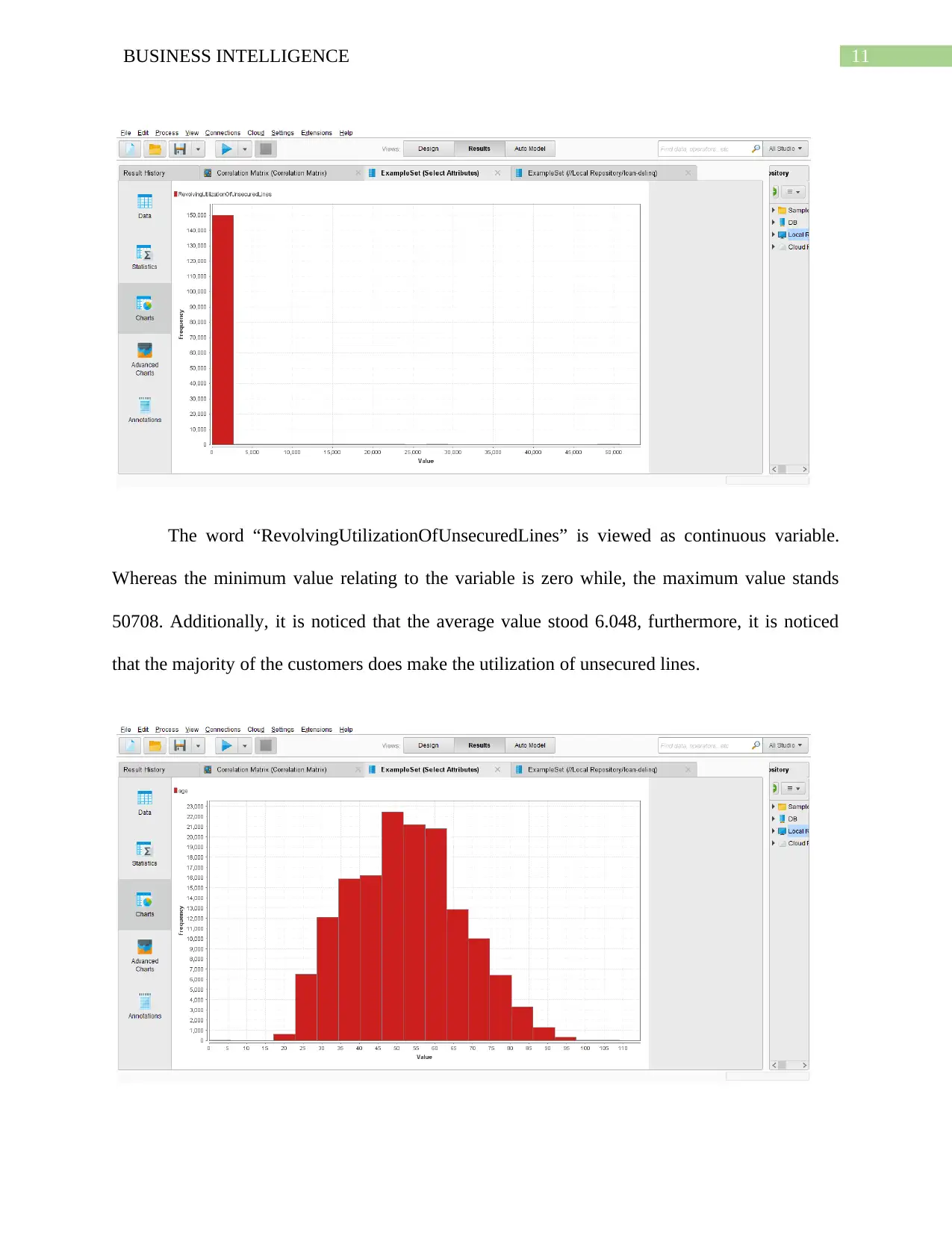
The word “RevolvingUtilizationOfUnsecuredLines” is viewed as continuous variable.
Whereas the minimum value relating to the variable is zero while, the maximum value stands
50708. Additionally, it is noticed that the average value stood 6.048, furthermore, it is noticed
that the majority of the customers does make the utilization of unsecured lines.
The word “RevolvingUtilizationOfUnsecuredLines” is viewed as continuous variable.
Whereas the minimum value relating to the variable is zero while, the maximum value stands
50708. Additionally, it is noticed that the average value stood 6.048, furthermore, it is noticed
that the majority of the customers does make the utilization of unsecured lines.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





