Business Process Analysis of Global Management Accounting Services
VerifiedAdded on 2020/03/16
|13
|3080
|37
Report
AI Summary
This report provides a comprehensive business process analysis for Global Management Accounting Services (GMAS). It begins with an introduction to GMAS and its services, followed by a list of participants, inputs, and outputs within the current system. The report then details the current business process model, highlighting its strengths such as strong report management and integration, while also identifying inefficiencies, particularly in security and the use of technology. The core of the report focuses on business process re-engineering and the use of IT to improve the system, proposing the implementation of technologies such as Business Intelligence, Big Data tools, cloud databases, and various security tools. A proposed workflow diagram is included, along with a discussion of the operations of the newly re-engineered business process and concluding with recommendations and conclusions to enhance the system's efficiency and security. The report emphasizes the importance of incorporating the latest technological advancements for improved data management and security.

Accounting Information Systems
Business Process Analysis
10/9/2017
Business Process Analysis
10/9/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Business Process Analysis
Table of Contents
Introduction.................................................................................................................................................3
List of Participants, Inputs and Outputs.......................................................................................................3
Current Business Process Model.................................................................................................................4
Strengths of the Current System..................................................................................................................4
Inefficiencies of the Current System............................................................................................................5
Improvement through Business Process Re-Engineering & Use of IT........................................................5
Technologies for Business Process Improvement........................................................................................6
Business Intelligence...............................................................................................................................6
Big Data Tools.........................................................................................................................................7
Cloud Databases......................................................................................................................................7
Security Tools..........................................................................................................................................8
Other Technologies.................................................................................................................................9
Proposed Workflow Diagram....................................................................................................................10
Operations of the Newly Re-Engineered Business Process.......................................................................11
Recommendations & Conclusion..............................................................................................................11
References.................................................................................................................................................13
2
Table of Contents
Introduction.................................................................................................................................................3
List of Participants, Inputs and Outputs.......................................................................................................3
Current Business Process Model.................................................................................................................4
Strengths of the Current System..................................................................................................................4
Inefficiencies of the Current System............................................................................................................5
Improvement through Business Process Re-Engineering & Use of IT........................................................5
Technologies for Business Process Improvement........................................................................................6
Business Intelligence...............................................................................................................................6
Big Data Tools.........................................................................................................................................7
Cloud Databases......................................................................................................................................7
Security Tools..........................................................................................................................................8
Other Technologies.................................................................................................................................9
Proposed Workflow Diagram....................................................................................................................10
Operations of the Newly Re-Engineered Business Process.......................................................................11
Recommendations & Conclusion..............................................................................................................11
References.................................................................................................................................................13
2

Business Process Analysis
Introduction
Global Management Accounting Services (GMAS) is an integrated suite of outsourced accounts
management services that are provided to several small and medium sized business units and
organizations. It aims to maintain the quality and continuity of the operations, implementation of
the technologies, resource management and optimization along with better management of labor.
There are various services and operations that are carried out by GMAS. The report covers the
analysis of the business process that is followed and carried out in GMAS. The strengths and
weaknesses of the current system along with the new systems and technologies that can be
implemented have been covered in the report.
List of Participants, Inputs and Outputs
The participants in the current system include the managerial and operational members of the
staff at GMAS along with the various clients that are associated with GMAS. The accounting
system that is associated with GMAS is also a participant that is used in the purpose of providing
the desired services and applications.
The set of inputs include the sales data and records. The information of the contract signed by the
client, claim details, customer and supplier information come under the inputs that are provided
to the system.
The set of outputs include copies of invoice, forms of unpaid debt, reconciliation statement and
payroll reports.
3
Introduction
Global Management Accounting Services (GMAS) is an integrated suite of outsourced accounts
management services that are provided to several small and medium sized business units and
organizations. It aims to maintain the quality and continuity of the operations, implementation of
the technologies, resource management and optimization along with better management of labor.
There are various services and operations that are carried out by GMAS. The report covers the
analysis of the business process that is followed and carried out in GMAS. The strengths and
weaknesses of the current system along with the new systems and technologies that can be
implemented have been covered in the report.
List of Participants, Inputs and Outputs
The participants in the current system include the managerial and operational members of the
staff at GMAS along with the various clients that are associated with GMAS. The accounting
system that is associated with GMAS is also a participant that is used in the purpose of providing
the desired services and applications.
The set of inputs include the sales data and records. The information of the contract signed by the
client, claim details, customer and supplier information come under the inputs that are provided
to the system.
The set of outputs include copies of invoice, forms of unpaid debt, reconciliation statement and
payroll reports.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Business Process Analysis
Current Business Process Model
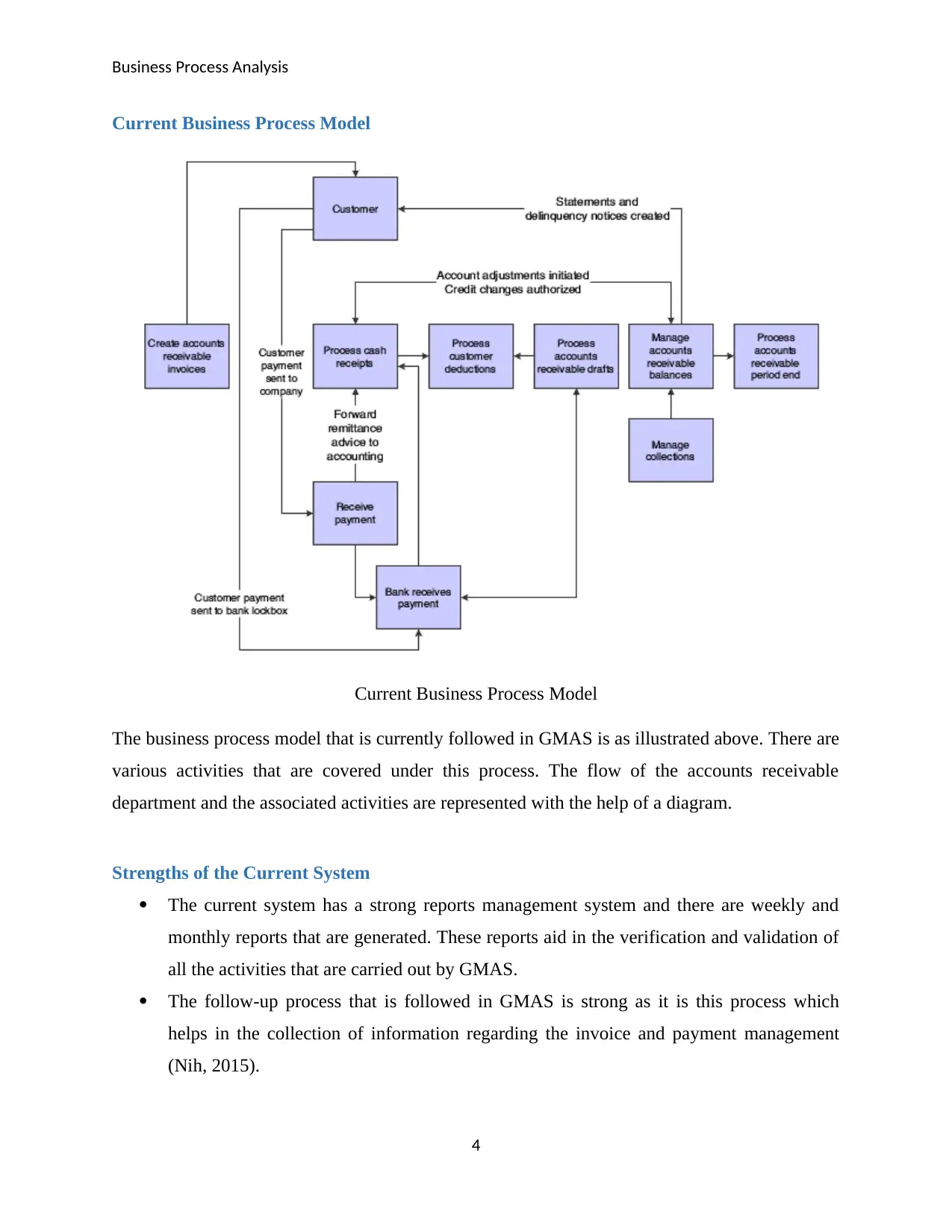
Current Business Process Model
The business process model that is currently followed in GMAS is as illustrated above. There are
various activities that are covered under this process. The flow of the accounts receivable
department and the associated activities are represented with the help of a diagram.
Strengths of the Current System
The current system has a strong reports management system and there are weekly and
monthly reports that are generated. These reports aid in the verification and validation of
all the activities that are carried out by GMAS.
The follow-up process that is followed in GMAS is strong as it is this process which
helps in the collection of information regarding the invoice and payment management
(Nih, 2015).
4
Current Business Process Model
Current Business Process Model
The business process model that is currently followed in GMAS is as illustrated above. There are
various activities that are covered under this process. The flow of the accounts receivable
department and the associated activities are represented with the help of a diagram.
Strengths of the Current System
The current system has a strong reports management system and there are weekly and
monthly reports that are generated. These reports aid in the verification and validation of
all the activities that are carried out by GMAS.
The follow-up process that is followed in GMAS is strong as it is this process which
helps in the collection of information regarding the invoice and payment management
(Nih, 2015).
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Business Process Analysis
The integration and cohesiveness of the current system is also one of its major strengths
as all the activities are inter-linked and inter-dependent on each other.
The members of the staff are used to the current system which makes it easy for them to
understand the processing of the system.
Inefficiencies of the Current System
Security is one of the major challenge and drawbacks that has been observed in
association with the current system. There may be security risks and attacks that may
impact the sensitive accounting and financial details. These security vulnerabilities and
weaknesses may give rise to the security risks and attacks, such as:
o Risks to the information sets by the occurrence of the security attacks like
information breaching, information loss and leakage, denial of service attacks,
malware attacks etc.
o SQL injection attacks may be executed to damage the database being used in
GMAS.
o There may be various forms of network attacks that may also take place which
may have an adverse implication on the network security. These attacks include
man in the middle attack, eavesdropping attack etc.
The use of technology and technical tools in the current system is not as per the latest
advancements. There are several automated and advanced technologies that are present in
terms of the Business Intelligence services and activities. This has led to the involvement
of certain replicated and unnecessary activities that could be avoided for faster processing
of the operations.
Improvement through Business Process Re-Engineering & Use of IT
There are various modifications that need to be done to the current set of business processes that
are carried out in GMAS.
The core business processes include accounts receivable, claims process and management,
invoice generation and management, verification and validation, information management, cash
5
The integration and cohesiveness of the current system is also one of its major strengths
as all the activities are inter-linked and inter-dependent on each other.
The members of the staff are used to the current system which makes it easy for them to
understand the processing of the system.
Inefficiencies of the Current System
Security is one of the major challenge and drawbacks that has been observed in
association with the current system. There may be security risks and attacks that may
impact the sensitive accounting and financial details. These security vulnerabilities and
weaknesses may give rise to the security risks and attacks, such as:
o Risks to the information sets by the occurrence of the security attacks like
information breaching, information loss and leakage, denial of service attacks,
malware attacks etc.
o SQL injection attacks may be executed to damage the database being used in
GMAS.
o There may be various forms of network attacks that may also take place which
may have an adverse implication on the network security. These attacks include
man in the middle attack, eavesdropping attack etc.
The use of technology and technical tools in the current system is not as per the latest
advancements. There are several automated and advanced technologies that are present in
terms of the Business Intelligence services and activities. This has led to the involvement
of certain replicated and unnecessary activities that could be avoided for faster processing
of the operations.
Improvement through Business Process Re-Engineering & Use of IT
There are various modifications that need to be done to the current set of business processes that
are carried out in GMAS.
The core business processes include accounts receivable, claims process and management,
invoice generation and management, verification and validation, information management, cash
5

Business Process Analysis
flows and credit processing. There are sub-activities that are involved in each of these processes
(Zigiaris, 2010).
There are certain inefficiencies that are associated with the current processes as listed and
described in the section above.
IT can be of great aid for the elimination of the inefficiencies listed above.
There are many of the security tools and techniques that can be used and applied for each of the
business process for the enhancement of the security of the overall system. These security
techniques shall be applied so that the financial transactions and information is secure and is also
kept private.
There are many technological tools that have been developed under the umbrella of Big Data and
Business Intelligence. These tools and technologies shall also be used and applied to make sure
that the tasks such as information analysis and management are carried out in an automated
manner.
Technologies for Business Process Improvement
Business Intelligence
Business Intelligence (BI) is a technology that is used for the analysis of the data to allow the
management with the ability to take easy business decisions.
There are many technologies that come under BI, such as data analysis, data mining, Online
Analytical Processing (OLAP), data warehousing and many more. These technologies can be
applied in this case for the enhancement and improvement of the business processes.
Data analytics and Online Analytics Processing (OLAP) are the technologies that can be used for
the analysis of the supplier and customer information. There are also a lot many details that are
associated with the operation of claims processing. The information around claims such as claim
type, premium details, insurance plan, owner details etc. can be automatically analyzed using
data analytics tools to identify whether the claim is valid or not (Babu, 2012).
OLAP includes the analysis on the multi-dimensional aspects and the results that are obtained
after the analysis bring out the solutions to the complex and huge calculations that are involved
6
flows and credit processing. There are sub-activities that are involved in each of these processes
(Zigiaris, 2010).
There are certain inefficiencies that are associated with the current processes as listed and
described in the section above.
IT can be of great aid for the elimination of the inefficiencies listed above.
There are many of the security tools and techniques that can be used and applied for each of the
business process for the enhancement of the security of the overall system. These security
techniques shall be applied so that the financial transactions and information is secure and is also
kept private.
There are many technological tools that have been developed under the umbrella of Big Data and
Business Intelligence. These tools and technologies shall also be used and applied to make sure
that the tasks such as information analysis and management are carried out in an automated
manner.
Technologies for Business Process Improvement
Business Intelligence
Business Intelligence (BI) is a technology that is used for the analysis of the data to allow the
management with the ability to take easy business decisions.
There are many technologies that come under BI, such as data analysis, data mining, Online
Analytical Processing (OLAP), data warehousing and many more. These technologies can be
applied in this case for the enhancement and improvement of the business processes.
Data analytics and Online Analytics Processing (OLAP) are the technologies that can be used for
the analysis of the supplier and customer information. There are also a lot many details that are
associated with the operation of claims processing. The information around claims such as claim
type, premium details, insurance plan, owner details etc. can be automatically analyzed using
data analytics tools to identify whether the claim is valid or not (Babu, 2012).
OLAP includes the analysis on the multi-dimensional aspects and the results that are obtained
after the analysis bring out the solutions to the complex and huge calculations that are involved
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Business Process Analysis
in the accounting operations and activities. Trend analysis along with sophisticated data
modeling is also carried out by using the same. Similarly, data mining and data warehousing are
the technologies that come under BI which are used for intelligent analysis and management of
the data (Nakhaei, 2012).
Big Data Tools
Big Data is a buzzword that is present in the field of technology in the current times. These tools
make sure that the huge clusters of data are managed with ease and the necessary business
information is also extracted from the same.
In the case of GMAS, there is a lot of data and information that is involved in terms of the
accounts related data, supplier and customer information and a lot more. This data may be of
different types, such as, structured and unstructured data along with semi-structured data. There
are also different types and formats of data that are involved in the information and data sets
associated with GMAS (Jain, 2013).
Big Data tools can be applied in the case of GMAS for efficient management of the data and the
streamlining of the business processes and operations.
Cloud Databases
Traditional databases are no longer applicable and suitable as per the need of the current data
requirements. It has become necessary to make use of advanced databases for the management,
storage and retrieval of information and data sets.
Cloud databases have recently come into the picture after the huge success and adaptation of
cloud computing platforms in various business sectors. Cloud services are being used by every
industry and accounts management department is no different (Arora, 2012).
Cloud databases are the databases that are created and are present on the cloud platforms. These
virtual storage spaces allow the users and business organizations to store and perform all of the
data operations on the cloud. There are many cloud databases that have been created by different
vendors as per the necessary cloud model and the requirements of the organization.
7
in the accounting operations and activities. Trend analysis along with sophisticated data
modeling is also carried out by using the same. Similarly, data mining and data warehousing are
the technologies that come under BI which are used for intelligent analysis and management of
the data (Nakhaei, 2012).
Big Data Tools
Big Data is a buzzword that is present in the field of technology in the current times. These tools
make sure that the huge clusters of data are managed with ease and the necessary business
information is also extracted from the same.
In the case of GMAS, there is a lot of data and information that is involved in terms of the
accounts related data, supplier and customer information and a lot more. This data may be of
different types, such as, structured and unstructured data along with semi-structured data. There
are also different types and formats of data that are involved in the information and data sets
associated with GMAS (Jain, 2013).
Big Data tools can be applied in the case of GMAS for efficient management of the data and the
streamlining of the business processes and operations.
Cloud Databases
Traditional databases are no longer applicable and suitable as per the need of the current data
requirements. It has become necessary to make use of advanced databases for the management,
storage and retrieval of information and data sets.
Cloud databases have recently come into the picture after the huge success and adaptation of
cloud computing platforms in various business sectors. Cloud services are being used by every
industry and accounts management department is no different (Arora, 2012).
Cloud databases are the databases that are created and are present on the cloud platforms. These
virtual storage spaces allow the users and business organizations to store and perform all of the
data operations on the cloud. There are many cloud databases that have been created by different
vendors as per the necessary cloud model and the requirements of the organization.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Business Process Analysis
In case of GMAS, private cloud model shall be used for the creation and setting up of the cloud
database. In this manner, there will be abundant storage space that will be available with the
elimination of the infrastructural costs associated with the databases.
These cloud databases are also compatible with the latest technical tools and applications, such
as Big Data tools and Business Intelligence applications. This would allow GMAS to include
enhanced level of automation in its set of services and business operations (Curino, 2011).
Security Tools
Security is one the critical and most significant aspects of the financial and accounting
information. It is because of the reason that this category of information is extremely sensitive
and its exposure to the unauthorized entities and units can be very dangerous.
There can be legal implications and punishments that may also come up in case of a security
attack or occurrence.
Technology shall therefore be used in the area of security for the secure management of data and
information. There are many security tools that have been developed that can automatically
detect the malicious activities and the attempts of the intruders to enter or access the sensitive
data sets.
Network security tools can be used in the case of GMAS as the use of cloud databases and cloud
services may bring in many network related security attacks. There are network based intrusion
detection and prevention systems that have been created. These systems have the capability to
detect the network intruders as soon as they attempt to scan, monitor or enter the networks
(Pareek, 2011). There are alerts that are created by these security tools that aid in the prevention
and avoidance of the security risks and attacks. There are also automated network scanning and
monitoring systems that can also be used in association with GMAS. These systems will keep a
log of the network data and information so that the malevolent activities can be detected and the
information around the same is regularly maintained and updated (Boneh & Mitchell, 2010).
There are security tools that are also created for malware protection. There can be various
malicious codes that may be launched by the attackers and intruders along with the attempt to
execute the denial of service attacks. These attacks and codes can be avoided and prevented by
using anti-malware and anti-denial tools. These tools will regularly scan the information sets and
8
In case of GMAS, private cloud model shall be used for the creation and setting up of the cloud
database. In this manner, there will be abundant storage space that will be available with the
elimination of the infrastructural costs associated with the databases.
These cloud databases are also compatible with the latest technical tools and applications, such
as Big Data tools and Business Intelligence applications. This would allow GMAS to include
enhanced level of automation in its set of services and business operations (Curino, 2011).
Security Tools
Security is one the critical and most significant aspects of the financial and accounting
information. It is because of the reason that this category of information is extremely sensitive
and its exposure to the unauthorized entities and units can be very dangerous.
There can be legal implications and punishments that may also come up in case of a security
attack or occurrence.
Technology shall therefore be used in the area of security for the secure management of data and
information. There are many security tools that have been developed that can automatically
detect the malicious activities and the attempts of the intruders to enter or access the sensitive
data sets.
Network security tools can be used in the case of GMAS as the use of cloud databases and cloud
services may bring in many network related security attacks. There are network based intrusion
detection and prevention systems that have been created. These systems have the capability to
detect the network intruders as soon as they attempt to scan, monitor or enter the networks
(Pareek, 2011). There are alerts that are created by these security tools that aid in the prevention
and avoidance of the security risks and attacks. There are also automated network scanning and
monitoring systems that can also be used in association with GMAS. These systems will keep a
log of the network data and information so that the malevolent activities can be detected and the
information around the same is regularly maintained and updated (Boneh & Mitchell, 2010).
There are security tools that are also created for malware protection. There can be various
malicious codes that may be launched by the attackers and intruders along with the attempt to
execute the denial of service attacks. These attacks and codes can be avoided and prevented by
using anti-malware and anti-denial tools. These tools will regularly scan the information sets and
8

Business Process Analysis
the networks to make sure that such security attacks do not take place. There are also features to
control the ransomware attacks that are present in some of these tools.
Access control and authentication are two measures that are necessary to make sure that the
security of the information and the system is always maintained. There are many access control
mechanisms that are available and have been created with the advancement of technology. There
are tools that can also be used in this regard in terms of role based and attribute based access
control mechanisms. The authentication of the users and entities can also be done by using
technical authentication checks and controls such as biometric based authentication systems and
likewise (Thion, 2008).
Other Technologies
There are various ready to use accounts management systems and software that have been
created. These packages can be observed and analyzed by the executive of GMAS to understand
the strengths and weaknesses of each system. In this manner, the details around the pros and cons
of the systems and the flaws present in the current process followed at GMAS will be
highlighted.
The management may then decide to adopt a customized version of such packages or a sub-
system of such packages in their business operations and activates. There are automated
packages that are available for payroll management services, claims processing systems, invoice
and billing generation and likewise.
9
the networks to make sure that such security attacks do not take place. There are also features to
control the ransomware attacks that are present in some of these tools.
Access control and authentication are two measures that are necessary to make sure that the
security of the information and the system is always maintained. There are many access control
mechanisms that are available and have been created with the advancement of technology. There
are tools that can also be used in this regard in terms of role based and attribute based access
control mechanisms. The authentication of the users and entities can also be done by using
technical authentication checks and controls such as biometric based authentication systems and
likewise (Thion, 2008).
Other Technologies
There are various ready to use accounts management systems and software that have been
created. These packages can be observed and analyzed by the executive of GMAS to understand
the strengths and weaknesses of each system. In this manner, the details around the pros and cons
of the systems and the flaws present in the current process followed at GMAS will be
highlighted.
The management may then decide to adopt a customized version of such packages or a sub-
system of such packages in their business operations and activates. There are automated
packages that are available for payroll management services, claims processing systems, invoice
and billing generation and likewise.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Business Process Analysis
Proposed Workflow Diagram
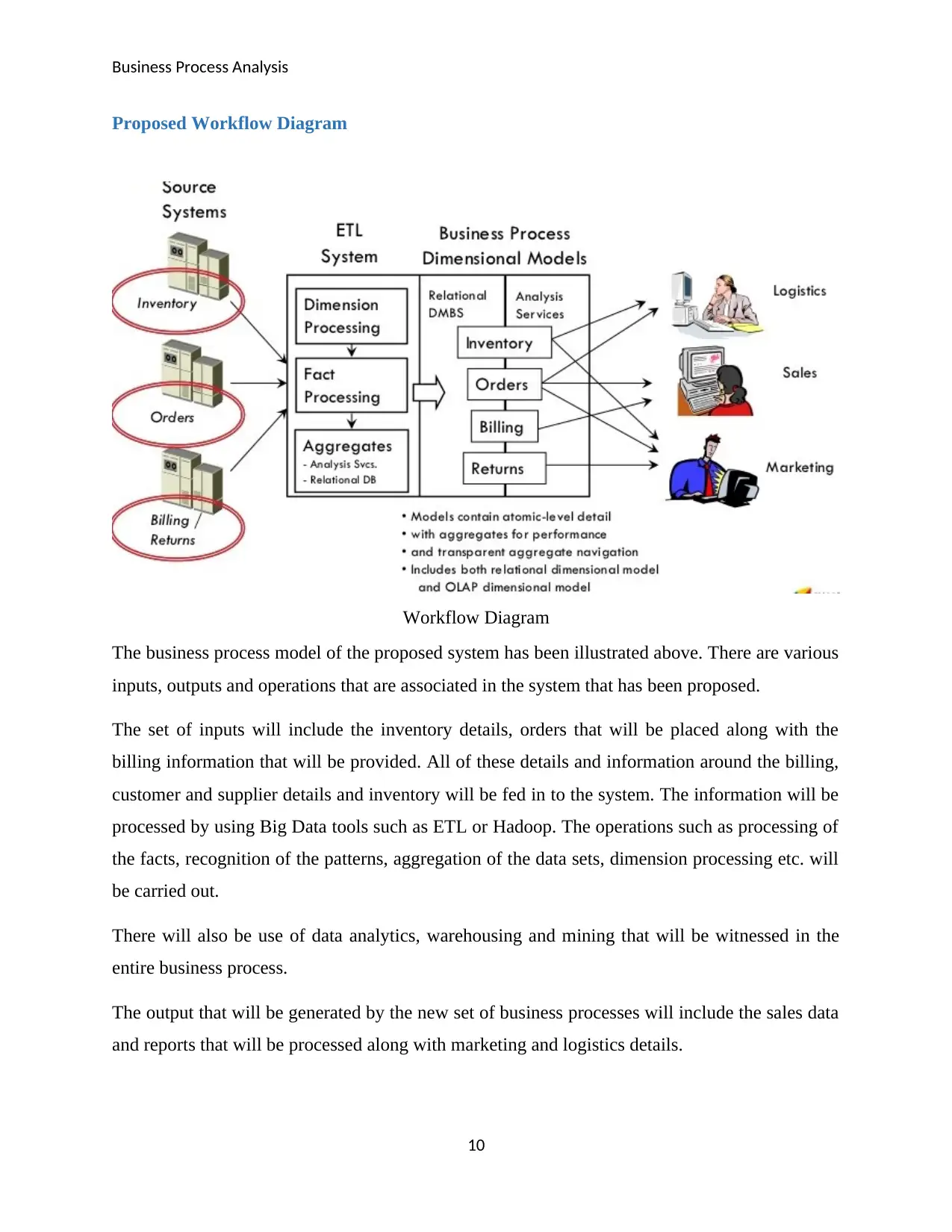
Workflow Diagram
The business process model of the proposed system has been illustrated above. There are various
inputs, outputs and operations that are associated in the system that has been proposed.
The set of inputs will include the inventory details, orders that will be placed along with the
billing information that will be provided. All of these details and information around the billing,
customer and supplier details and inventory will be fed in to the system. The information will be
processed by using Big Data tools such as ETL or Hadoop. The operations such as processing of
the facts, recognition of the patterns, aggregation of the data sets, dimension processing etc. will
be carried out.
There will also be use of data analytics, warehousing and mining that will be witnessed in the
entire business process.
The output that will be generated by the new set of business processes will include the sales data
and reports that will be processed along with marketing and logistics details.
10
Proposed Workflow Diagram
Workflow Diagram
The business process model of the proposed system has been illustrated above. There are various
inputs, outputs and operations that are associated in the system that has been proposed.
The set of inputs will include the inventory details, orders that will be placed along with the
billing information that will be provided. All of these details and information around the billing,
customer and supplier details and inventory will be fed in to the system. The information will be
processed by using Big Data tools such as ETL or Hadoop. The operations such as processing of
the facts, recognition of the patterns, aggregation of the data sets, dimension processing etc. will
be carried out.
There will also be use of data analytics, warehousing and mining that will be witnessed in the
entire business process.
The output that will be generated by the new set of business processes will include the sales data
and reports that will be processed along with marketing and logistics details.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Business Process Analysis
There will be involvement of security tools and concepts that will also be witnessed in each
stage.
Operations of the Newly Re-Engineered Business Process
There will be many activities and operations that will be carried out by the new system that has
been proposed.
The new system will have a variation from the current system and there will be addition of the
technologies and concepts from the areas of security, Big Data and Business Intelligence in the
new system.
The data and information around billing, customer and supplier details will be fed in the system.
The processing of the information and claims along with the calculation of payroll activities such
as salaries of the employees and likewise will be done in the system. However, it will have an
additional process of validation and verification at each step from the aspect of security.
The security tools will make sure that the information and the activities that are involved are not
exposed to the unauthorized entities.
Once the processing of information will be done, there will be outputs that will be generated in
the forms of processed claims, sales reports and records along with the reports on the operational
data and information.
Recommendations & Conclusion
GMAS is set of services that involve financial data and information. This information is sensitive
and critical in nature. It aims to maintain the quality and continuity of the operations,
implementation of the technologies, resource management and optimization along with better
management of labor. Reports management, follow-up processes and level of integration are
some of the strengths of the current system. There are also many inefficiencies and weaknesses
that are involved with the system in terms of security of the information along with the use of
outdated technology. Many new technologies and technical concepts shall be used in GMAS for
the enhancement of the business continuity and the streamlining of the operations. There are
many technological tools that have been developed under the umbrella of Big Data and Business
11
There will be involvement of security tools and concepts that will also be witnessed in each
stage.
Operations of the Newly Re-Engineered Business Process
There will be many activities and operations that will be carried out by the new system that has
been proposed.
The new system will have a variation from the current system and there will be addition of the
technologies and concepts from the areas of security, Big Data and Business Intelligence in the
new system.
The data and information around billing, customer and supplier details will be fed in the system.
The processing of the information and claims along with the calculation of payroll activities such
as salaries of the employees and likewise will be done in the system. However, it will have an
additional process of validation and verification at each step from the aspect of security.
The security tools will make sure that the information and the activities that are involved are not
exposed to the unauthorized entities.
Once the processing of information will be done, there will be outputs that will be generated in
the forms of processed claims, sales reports and records along with the reports on the operational
data and information.
Recommendations & Conclusion
GMAS is set of services that involve financial data and information. This information is sensitive
and critical in nature. It aims to maintain the quality and continuity of the operations,
implementation of the technologies, resource management and optimization along with better
management of labor. Reports management, follow-up processes and level of integration are
some of the strengths of the current system. There are also many inefficiencies and weaknesses
that are involved with the system in terms of security of the information along with the use of
outdated technology. Many new technologies and technical concepts shall be used in GMAS for
the enhancement of the business continuity and the streamlining of the operations. There are
many technological tools that have been developed under the umbrella of Big Data and Business
11

Business Process Analysis
Intelligence. These tools and technologies shall also be used and applied to make sure that the
tasks such as information analysis and management are carried out in an automated manner.
There are many of the security tools and techniques that can be used and applied for each of the
business process for the enhancement of the security of the overall system. These security
techniques shall be applied so that the financial transactions and information is secure and is also
kept private. These technologies shall be analyzed on the basis of the needs and requirements of
the organization and shall be applied and used thereafter.
12
Intelligence. These tools and technologies shall also be used and applied to make sure that the
tasks such as information analysis and management are carried out in an automated manner.
There are many of the security tools and techniques that can be used and applied for each of the
business process for the enhancement of the security of the overall system. These security
techniques shall be applied so that the financial transactions and information is secure and is also
kept private. These technologies shall be analyzed on the basis of the needs and requirements of
the organization and shall be applied and used thereafter.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




