Business Requirements Report: OSDS Architecture and Cloud Edge
VerifiedAdded on 2022/09/08
|18
|3834
|16
Report
AI Summary
This business requirements report addresses the needs of DSI (Department of Spatial Information), which provides spatial data through its Online Spatial Delivery System (OSDS). The report evaluates potential deployment models, focusing on cloud-based OSDS, and assesses the advantages and disadvantages of IaaS and PaaS. It explores the use of Cloud Edge for OSDS, detailing its benefits and drawbacks. The report also compares monolithic and microservice architectures, evaluating their respective strengths and weaknesses, and provides recommendations for the best architectural approach for DSI. The report concludes with a summary of findings and references.

Running head: BUSINESS REQUIRMENTS REPORTS
Business Requirements Report
Name of the Student
Name of the University
Author’s Note
Business Requirements Report
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BUSINESS REQUIREMENTS REPORT
Table of Contents
Introduction......................................................................................................................................2
Possible delivery and deployment models.......................................................................................2
IaaS and PaaS Evaluation............................................................................................................3
Possible Architecture for OSDS..................................................................................................4
Use of Cloud Edge for OSDS..........................................................................................................5
Differences between monolithic & MicroService Architectures.....................................................7
Evaluation of Software Architectures..............................................................................................9
Recommended Approach...............................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................14
Table of Contents
Introduction......................................................................................................................................2
Possible delivery and deployment models.......................................................................................2
IaaS and PaaS Evaluation............................................................................................................3
Possible Architecture for OSDS..................................................................................................4
Use of Cloud Edge for OSDS..........................................................................................................5
Differences between monolithic & MicroService Architectures.....................................................7
Evaluation of Software Architectures..............................................................................................9
Recommended Approach...............................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................14

2BUSINESS REQUIREMENTS REPORT
Introduction
DSI (Department of Spatial Information), which applies to the state government business,
offers spatial information exclusively to government agencies and limited detail to the public. It
uses the Online Spatial Delivery System (OSDS) to provide this sort of information. To handle
all that material, DSI uses the web services as well as other internal applications. As the interest
in this program grew, DSI had decided to introduce a modern knowledge management
framework, retaining the infrastructure and providing it to the public and government alike. After
figuring out several ideas DSI Executive team came up with two recommendations either to
expand the storage and hosting capability of DSI data centers or to move OSDS to cloud
provider. The executive of DSI chose to adopt the OSDS to the cloud provider for meeting their
budget restriction. Therefore, this report aims to discuss the advantages and disadvantages of
IaaS and PaaS and evaluate the usages of Cloud edge for OSDS. This report also compares the
monolithic and MicroService architectures and evaluates the software architecture.
Possible delivery and deployment models
The possible deployment model for DSI is cloud-based OSDS, which will be very
beneficial for them. An OSDS is the computer storage system, which connects the data through
containers called artifacts defined by a user or program (Noel & Lama, 2017). The objects are
positioned in the flat address space where all of them reside at the same stage and it cannot be
put within each other. It has the unique object identifier, which enables the end user or the
server for retrieving it without knowing the physical location of the data stored within.
Introduction
DSI (Department of Spatial Information), which applies to the state government business,
offers spatial information exclusively to government agencies and limited detail to the public. It
uses the Online Spatial Delivery System (OSDS) to provide this sort of information. To handle
all that material, DSI uses the web services as well as other internal applications. As the interest
in this program grew, DSI had decided to introduce a modern knowledge management
framework, retaining the infrastructure and providing it to the public and government alike. After
figuring out several ideas DSI Executive team came up with two recommendations either to
expand the storage and hosting capability of DSI data centers or to move OSDS to cloud
provider. The executive of DSI chose to adopt the OSDS to the cloud provider for meeting their
budget restriction. Therefore, this report aims to discuss the advantages and disadvantages of
IaaS and PaaS and evaluate the usages of Cloud edge for OSDS. This report also compares the
monolithic and MicroService architectures and evaluates the software architecture.
Possible delivery and deployment models
The possible deployment model for DSI is cloud-based OSDS, which will be very
beneficial for them. An OSDS is the computer storage system, which connects the data through
containers called artifacts defined by a user or program (Noel & Lama, 2017). The objects are
positioned in the flat address space where all of them reside at the same stage and it cannot be
put within each other. It has the unique object identifier, which enables the end user or the
server for retrieving it without knowing the physical location of the data stored within.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BUSINESS REQUIREMENTS REPORT
IaaS and PaaS Evaluation
For this study, the chosen service of OSDS is PaaS. PaaS (Platform as a Service) will
help in enabling DSI to reserve computing room on the computer, which offers capacity for
running applications, apps, which operating systems in the cloud as well (Yangui et al., 2016). It
will help the developers to check new applications if and when required on leased virtual
computers. There are benefits as well as a few drawbacks as in PaaS.
Advantages
Automated Upgrades: The upgrades of the applications are performed automatically and
all the new releases, improvements are available (Kolb & Wirtz, 2014). An upgrade will
not run the risk of losing out. That will save loads of time and money. Security updates
address any glitches and other technical concerns.
Low Investments: DSI will be able to use the app without needing to spend in technology
elsewhere in an in-house environment.
Reduced Costs: Because the billing process is pay-as-you-use, significant savings are
rendered for the organization without needing to buy the required tools such as
databases and server to operate the application (Amaral et al., 2015).
Collaboration: Since this is an internet-based network, it helps workers to access and
operate on the apps from anywhere, upgrade them without being physically present in the
company premises.
Focus: Instead of getting drawn to system repairs, the IT unit will rely mainly on key
applications.
Disadvantages
IaaS and PaaS Evaluation
For this study, the chosen service of OSDS is PaaS. PaaS (Platform as a Service) will
help in enabling DSI to reserve computing room on the computer, which offers capacity for
running applications, apps, which operating systems in the cloud as well (Yangui et al., 2016). It
will help the developers to check new applications if and when required on leased virtual
computers. There are benefits as well as a few drawbacks as in PaaS.
Advantages
Automated Upgrades: The upgrades of the applications are performed automatically and
all the new releases, improvements are available (Kolb & Wirtz, 2014). An upgrade will
not run the risk of losing out. That will save loads of time and money. Security updates
address any glitches and other technical concerns.
Low Investments: DSI will be able to use the app without needing to spend in technology
elsewhere in an in-house environment.
Reduced Costs: Because the billing process is pay-as-you-use, significant savings are
rendered for the organization without needing to buy the required tools such as
databases and server to operate the application (Amaral et al., 2015).
Collaboration: Since this is an internet-based network, it helps workers to access and
operate on the apps from anywhere, upgrade them without being physically present in the
company premises.
Focus: Instead of getting drawn to system repairs, the IT unit will rely mainly on key
applications.
Disadvantages
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4BUSINESS REQUIREMENTS REPORT
Lock-in risks: This is one option that the organization needs to carefully test before
they sign up with any other company. If the organization gets stuck in a certain language,
application, or interface, which could impact the organization with some unwanted
framework they do not need.
Restricted Scalability: PaaS can be marginally inflexible when the organization will need
on demand supplies (Androcec, Vrcek & Küngas, 2015). In the PaaS setting the reduction
or extension dependent on business needs is minimal.
Data Backup: While PaaS offers replication, one of the own should be done because the
system will often have the same vulnerabilities towards any accident.
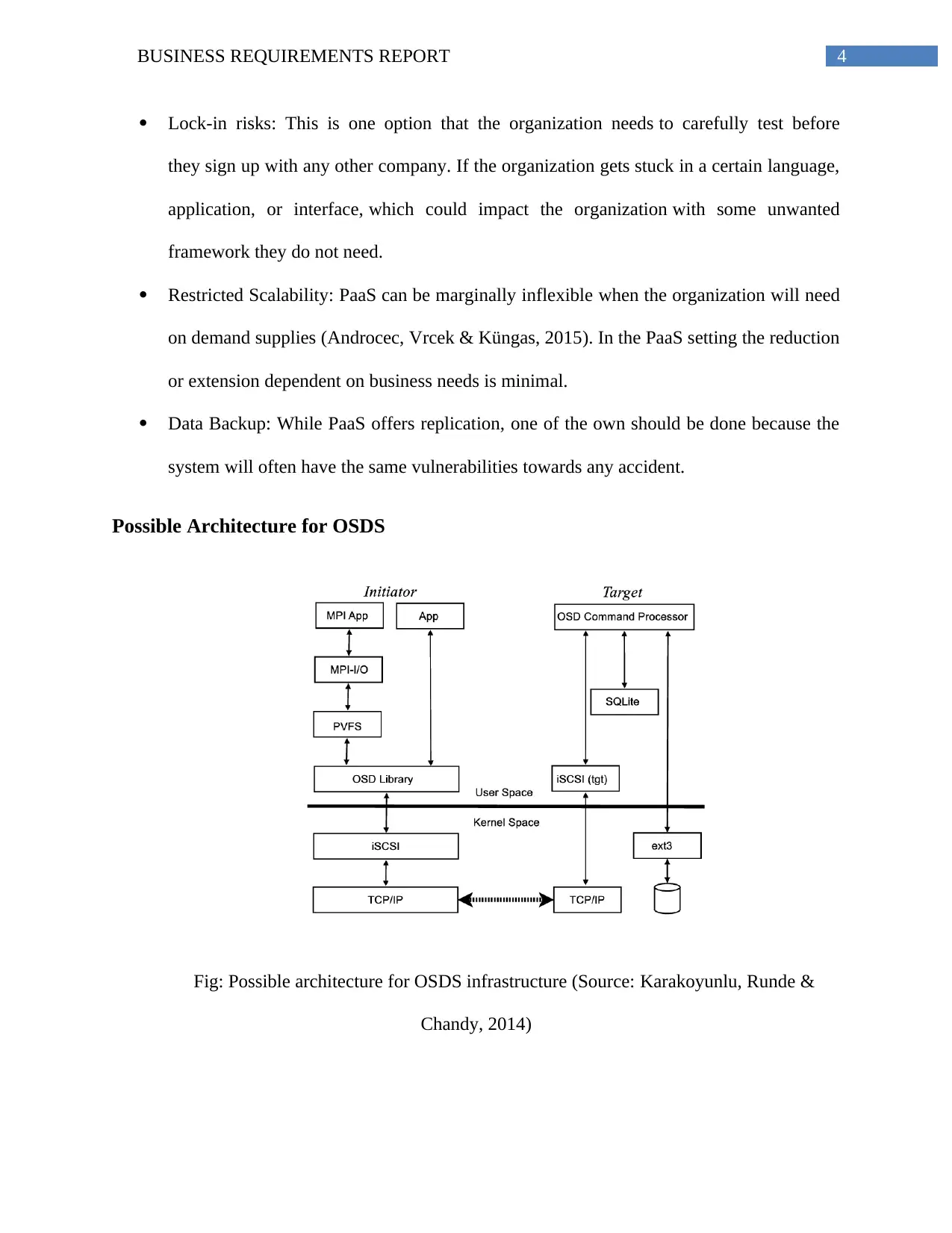
Possible Architecture for OSDS
Fig: Possible architecture for OSDS infrastructure (Source: Karakoyunlu, Runde &
Chandy, 2014)
Lock-in risks: This is one option that the organization needs to carefully test before
they sign up with any other company. If the organization gets stuck in a certain language,
application, or interface, which could impact the organization with some unwanted
framework they do not need.
Restricted Scalability: PaaS can be marginally inflexible when the organization will need
on demand supplies (Androcec, Vrcek & Küngas, 2015). In the PaaS setting the reduction
or extension dependent on business needs is minimal.
Data Backup: While PaaS offers replication, one of the own should be done because the
system will often have the same vulnerabilities towards any accident.
Possible Architecture for OSDS
Fig: Possible architecture for OSDS infrastructure (Source: Karakoyunlu, Runde &
Chandy, 2014)

5BUSINESS REQUIREMENTS REPORT
Following Image can be the possible architecture and deployment of the OSD system of
DSI. There are two key components to the program, the OSD initiator and the OSD aim. The
image displays the design elements and their partnerships. Using the iSCSI, the initiator and the
target interact among themselves. The iSCSI protocol requires the SCSI commands to be
transmitted over a network, normally TCP/IP (Gode et al., 2014). The sub-sections that follow
discuss the architecture problems and choices that DSI can make during the development of an
initiator and aim for OSD.
The initiator library of OSDS exports the code to connect with the OSD aim used by
the client applications. The OSD aim is responsible for handling iSCSI sessions, receiving
requests from the initiators, accessing or generating objects, and possibly establishing and
retrieving attributes, and eventually returning an appropriate response.
Use of Cloud Edge for OSDS
Cloud Edge is the new generation mobile broadband solution that is based on the Service-
Oriented Architecture, Network Functions Virtualization and cloud architecture developed. The
Cloud Edge framework optimizes and improves the supporting application functionality to offer
cloud-based advantages like automated installation and elastic scaling, to satisfy availability,
efficiency and other specifications for carrier-grade applications (Wang et al., 2017). Inevitable
development of cloud-based applications is edge computing. If the field of technology continues
to evolve, the IoT scope will also develop, with most electronics and computer-driven devices
eventually communicating. Moreover, the vast volume of empty computer power that remains
unused will be exploited for usage, generating thousands of times bigger storage system than the
Following Image can be the possible architecture and deployment of the OSD system of
DSI. There are two key components to the program, the OSD initiator and the OSD aim. The
image displays the design elements and their partnerships. Using the iSCSI, the initiator and the
target interact among themselves. The iSCSI protocol requires the SCSI commands to be
transmitted over a network, normally TCP/IP (Gode et al., 2014). The sub-sections that follow
discuss the architecture problems and choices that DSI can make during the development of an
initiator and aim for OSD.
The initiator library of OSDS exports the code to connect with the OSD aim used by
the client applications. The OSD aim is responsible for handling iSCSI sessions, receiving
requests from the initiators, accessing or generating objects, and possibly establishing and
retrieving attributes, and eventually returning an appropriate response.
Use of Cloud Edge for OSDS
Cloud Edge is the new generation mobile broadband solution that is based on the Service-
Oriented Architecture, Network Functions Virtualization and cloud architecture developed. The
Cloud Edge framework optimizes and improves the supporting application functionality to offer
cloud-based advantages like automated installation and elastic scaling, to satisfy availability,
efficiency and other specifications for carrier-grade applications (Wang et al., 2017). Inevitable
development of cloud-based applications is edge computing. If the field of technology continues
to evolve, the IoT scope will also develop, with most electronics and computer-driven devices
eventually communicating. Moreover, the vast volume of empty computer power that remains
unused will be exploited for usage, generating thousands of times bigger storage system than the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BUSINESS REQUIREMENTS REPORT
one actually in operation. Therefore, the organization DSI can chose the Cloud Edge
infrastructure for OSDS.
Advantages of Cloud Edge
Speed: By bringing the data collection devices and software closer to the real source of
the data, decreasing the physical distance, the data of the organization will migrate and
the time taken to transfer, edge computing significantly decreases the inactivity or latency
times, thereby improving the overall service’s sensitivity, pace and efficiency (Chang et
al., 2014).
Reliable and uninterrupted connection: Edge computing offers the local microdata
centers for the data collection and retrieval. As a result, the organization may rely on
stable networking for their IoT (Internet of Things) applications, even though it involves
cloud resources (Georgakopoulos et al., 2016). Additionally, edge computing helps IoT
devices to use less capacity and to run normally with restricted access, minimizing issues
regarding knowledge and data leakage in industries.
Low cost: The organisation will be able to minimize their costs by growing the necessary
capacity, replacing data centers with decentralized system systems, and growing data
storage demands, contributing to lower prices for IoT products and applications.
Disadvantages of Cloud Edge
There are multiple disadvantages or drawbacks, where there are benefits and edge
computing is no difference. The following drawbacks for edge computing should be known to
the organization:
one actually in operation. Therefore, the organization DSI can chose the Cloud Edge
infrastructure for OSDS.
Advantages of Cloud Edge
Speed: By bringing the data collection devices and software closer to the real source of
the data, decreasing the physical distance, the data of the organization will migrate and
the time taken to transfer, edge computing significantly decreases the inactivity or latency
times, thereby improving the overall service’s sensitivity, pace and efficiency (Chang et
al., 2014).
Reliable and uninterrupted connection: Edge computing offers the local microdata
centers for the data collection and retrieval. As a result, the organization may rely on
stable networking for their IoT (Internet of Things) applications, even though it involves
cloud resources (Georgakopoulos et al., 2016). Additionally, edge computing helps IoT
devices to use less capacity and to run normally with restricted access, minimizing issues
regarding knowledge and data leakage in industries.
Low cost: The organisation will be able to minimize their costs by growing the necessary
capacity, replacing data centers with decentralized system systems, and growing data
storage demands, contributing to lower prices for IoT products and applications.
Disadvantages of Cloud Edge
There are multiple disadvantages or drawbacks, where there are benefits and edge
computing is no difference. The following drawbacks for edge computing should be known to
the organization:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BUSINESS REQUIREMENTS REPORT
Edge computing collects and analyzes only the subset of data by discarding the raw and
unfinished knowledge (Satria, Park & Jo, 2017). Organizations will determine which
extent of the lack of knowledge is appropriate.
Edge computing will raise vectors for attacks. The possibilities for malicious hackers or
attacks to penetrate the networks and access confidential data have improved with the
introduction of IoT, network-connected machines, and built-in computers (Kozik et al.,
2017).
Edge computing for more local hardware is needed. IoT devices, for example, need an
embedded device to transmit video data across the internet and a more complex
processing method for more specialized software implementations, such as motion
tracking or facial recognition.
Differences between monolithic & MicroService Architectures
Monolithic Architecture Applications have generally been designed on a monolithic design, a paradigm in which
all components within a framework are integrated into a single, self-contained structure.
All functionality occurs inside the single codebase, indicating that the whole program is
implemented concurrently, and that scaling is accomplished by inserting additional nodes
(Namiot & Sneps-Sneppe, 2014).
Makes prototypes larger and larger and is impossible to handle because, if the
specification becomes too massive, it requires a long time to launch.
Continuous implementation is challenging, because a minor modification in the code to a
part involves redeployment of the whole program.
Edge computing collects and analyzes only the subset of data by discarding the raw and
unfinished knowledge (Satria, Park & Jo, 2017). Organizations will determine which
extent of the lack of knowledge is appropriate.
Edge computing will raise vectors for attacks. The possibilities for malicious hackers or
attacks to penetrate the networks and access confidential data have improved with the
introduction of IoT, network-connected machines, and built-in computers (Kozik et al.,
2017).
Edge computing for more local hardware is needed. IoT devices, for example, need an
embedded device to transmit video data across the internet and a more complex
processing method for more specialized software implementations, such as motion
tracking or facial recognition.
Differences between monolithic & MicroService Architectures
Monolithic Architecture Applications have generally been designed on a monolithic design, a paradigm in which
all components within a framework are integrated into a single, self-contained structure.
All functionality occurs inside the single codebase, indicating that the whole program is
implemented concurrently, and that scaling is accomplished by inserting additional nodes
(Namiot & Sneps-Sneppe, 2014).
Makes prototypes larger and larger and is impossible to handle because, if the
specification becomes too massive, it requires a long time to launch.
Continuous implementation is challenging, because a minor modification in the code to a
part involves redeployment of the whole program.

8BUSINESS REQUIREMENTS REPORT
Application scaling involves complete framework scaling that is launching several
instances of the wide monolithic program to meet the need, but only a limited portion of
the framework is resource-intensive (Fan & Ma, 2017). Monolithic is ideal because the program itself is very small, and has few logic and
modules in it. In the monolithic application, modules may deal with each other and communicate
to each other easily by utilizing internal language processes or calling the different
process as it is part of the single framework.
MicroService Architecture
The concept is to break the framework into a collection of smaller, integrated programs
rather than the single monolithic program. Increasing MicroService is the small program
that has its own hexagonal architecture is included with the business logic with multiple
different adapters (Villamizar et al., 2016).
The scale should stay considerably smaller, as each portion is dissected into smaller
facilities.
Continued delivery here is feasible, because each infrastructure may be delivered
individually.
Microservice-based design is ideally adapted if the program is very large, complicated,
and is doing a number of things.
Single component scaling is important here, since every specific component is de-
coupled to various systems, and can be distributed horizontally and independently (Singh
& Peddoju, 2017).
Application scaling involves complete framework scaling that is launching several
instances of the wide monolithic program to meet the need, but only a limited portion of
the framework is resource-intensive (Fan & Ma, 2017). Monolithic is ideal because the program itself is very small, and has few logic and
modules in it. In the monolithic application, modules may deal with each other and communicate
to each other easily by utilizing internal language processes or calling the different
process as it is part of the single framework.
MicroService Architecture
The concept is to break the framework into a collection of smaller, integrated programs
rather than the single monolithic program. Increasing MicroService is the small program
that has its own hexagonal architecture is included with the business logic with multiple
different adapters (Villamizar et al., 2016).
The scale should stay considerably smaller, as each portion is dissected into smaller
facilities.
Continued delivery here is feasible, because each infrastructure may be delivered
individually.
Microservice-based design is ideally adapted if the program is very large, complicated,
and is doing a number of things.
Single component scaling is important here, since every specific component is de-
coupled to various systems, and can be distributed horizontally and independently (Singh
& Peddoju, 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BUSINESS REQUIREMENTS REPORT
In reality, microservice-based architecture isn’t recent. While the theory behind UNIX
architecture remains just the same. While the usage of microservice-based design has
certain benefits, it is not a solution to the application creation and delivery problems.
In the case of microservice-based design, developers would have to cope with reasoning
for service-to-service intercommunication, and even manage vulnerabilities between
them.
Evaluation of Software Architectures
Fig: Difference
between Monolithic and MicroService architecture (Source: Villamizar et al., 2015)
Benefits of Monolithic Architecture
Simple in developing any program
It is very simple for testing any program. For instance, anyone can enable end-to-end
verification, by merely launching the program and checking the UI with the Selenium.
Monolithic is very simple in deploying (Villamizar et al., 2015). Only copy the bundled
code into a folder.
In reality, microservice-based architecture isn’t recent. While the theory behind UNIX
architecture remains just the same. While the usage of microservice-based design has
certain benefits, it is not a solution to the application creation and delivery problems.
In the case of microservice-based design, developers would have to cope with reasoning
for service-to-service intercommunication, and even manage vulnerabilities between
them.
Evaluation of Software Architectures
Fig: Difference
between Monolithic and MicroService architecture (Source: Villamizar et al., 2015)
Benefits of Monolithic Architecture
Simple in developing any program
It is very simple for testing any program. For instance, anyone can enable end-to-end
verification, by merely launching the program and checking the UI with the Selenium.
Monolithic is very simple in deploying (Villamizar et al., 2015). Only copy the bundled
code into a folder.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BUSINESS REQUIREMENTS REPORT
It is easy in scaling horizontally, with several copies operating behind the load balancer.
Disadvantages of Monolithic Architecture
The basic solution has complexity and limitation in size.
Technology is too large and complicated to easily and accurately comprehend and create
improvements (Kazanavičius & Mažeika, 2019).
The application size will slow down startup time.
Upon every upgrade the organization will need to redeploy the whole program.
This is challenging to continuous launch.
Advantages of MicroService Architecture
This addresses the complexity issue by breaking down framework into a series of
accessible resources that are much simpler to create, and much easier to learn and sustain.
It allows for the autonomous production of each project by a team that is based on that
business (Villamizar et al., 2015).
It removes obstacles to the introduction of emerging technology because developers are
able to select which innovations make sense for their business and are not constrained by
the choices made at the project startup.
Disadvantages of MicroService Architecture
Microservices design adds value to the project simply by rendering a distributed device a
microservices program (Singh & Peddoju, 2017). The organization will need to pick and
enforce an inter-process coordination system focused on messaging, and write code for
managing partial failure and taking other distributed computing errors into account.
It is easy in scaling horizontally, with several copies operating behind the load balancer.
Disadvantages of Monolithic Architecture
The basic solution has complexity and limitation in size.
Technology is too large and complicated to easily and accurately comprehend and create
improvements (Kazanavičius & Mažeika, 2019).
The application size will slow down startup time.
Upon every upgrade the organization will need to redeploy the whole program.
This is challenging to continuous launch.
Advantages of MicroService Architecture
This addresses the complexity issue by breaking down framework into a series of
accessible resources that are much simpler to create, and much easier to learn and sustain.
It allows for the autonomous production of each project by a team that is based on that
business (Villamizar et al., 2015).
It removes obstacles to the introduction of emerging technology because developers are
able to select which innovations make sense for their business and are not constrained by
the choices made at the project startup.
Disadvantages of MicroService Architecture
Microservices design adds value to the project simply by rendering a distributed device a
microservices program (Singh & Peddoju, 2017). The organization will need to pick and
enforce an inter-process coordination system focused on messaging, and write code for
managing partial failure and taking other distributed computing errors into account.

11BUSINESS REQUIREMENTS REPORT
In certain cases the safest alternative is a monolithic program. For instance, if any
application is small, implementing the distributed architecture such as MicroService, before it
is required will result in an unnecessarily complicated application and increased overhead
(Villamizar et al., 2016). Companies contemplating creating a mobile device from scratch or
designing proof of concept will even take benefit of accepting the monolith. Although it may
sound counterintuitive, tiny monoliths are an uncomplicated and cost-effective alternative. These
are easy in understanding and quick to model, check and disable.
Recommended Approach
Based on the study, usage of cloud infrastructure as data storage medium can be advised.
OSDS infrastructure provides an innovative approach. Data on data reveals the value of
computer collection; system repair and backup computer on existing maturity level
and on data protection priority stage (Pardeshi, 2014). OSDS deployment makes
comprehensive data management feasible with easy capital infrastructure. This is
consistent with the cloud infrastructure that handles the resource in a clear way and
through maintenance effort.
Implementation in cloud services allows network management expenses to be minimized.
Meanwhile, the sensitive data is vulnerable, and a cloud data management analysis is
required. Recommendation is rendered from low significance results. It is presumed that
the data is of low level of entry.
The organization must specifically define the files, processing activities or resources that
might be storing in cloud platform when preparing to utilize Cloud computing.
In certain cases the safest alternative is a monolithic program. For instance, if any
application is small, implementing the distributed architecture such as MicroService, before it
is required will result in an unnecessarily complicated application and increased overhead
(Villamizar et al., 2016). Companies contemplating creating a mobile device from scratch or
designing proof of concept will even take benefit of accepting the monolith. Although it may
sound counterintuitive, tiny monoliths are an uncomplicated and cost-effective alternative. These
are easy in understanding and quick to model, check and disable.
Recommended Approach
Based on the study, usage of cloud infrastructure as data storage medium can be advised.
OSDS infrastructure provides an innovative approach. Data on data reveals the value of
computer collection; system repair and backup computer on existing maturity level
and on data protection priority stage (Pardeshi, 2014). OSDS deployment makes
comprehensive data management feasible with easy capital infrastructure. This is
consistent with the cloud infrastructure that handles the resource in a clear way and
through maintenance effort.
Implementation in cloud services allows network management expenses to be minimized.
Meanwhile, the sensitive data is vulnerable, and a cloud data management analysis is
required. Recommendation is rendered from low significance results. It is presumed that
the data is of low level of entry.
The organization must specifically define the files, processing activities or resources that
might be storing in cloud platform when preparing to utilize Cloud computing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





