Object Modelling Report: ATM System and Stakeholder Analysis
VerifiedAdded on 2021/04/17
|10
|1792
|50
Report
AI Summary
This report provides a detailed analysis of object modelling within a business information system, specifically focusing on an ATM system. It begins with an introduction highlighting the importance of Business Information Systems in various enterprise settings and their role in deploying ICT for business process improvement. The report then presents a system vision document for a Collin’s ATM system, outlining its advantages, such as easy money withdrawal and 24/7 service, and disadvantages, including potential security risks and limitations. It further details the required resources, including card readers, keypads, and cash dispensers, and constructs a stakeholder map identifying primary, secondary, and tertiary stakeholders. The report also addresses various risks associated with ATMs, such as physical and logical security threats and fraud, including skimming and malware attacks. The conclusion summarizes the key aspects of the business information system, system vision, resources, stakeholder map, and risk analysis, offering insights into the benefits and drawbacks of ATM systems and potential problems. Finally, the report includes a comprehensive list of references.

Running head: OBJECT MODELLING
Object modelling
Assessment 1
[Name of the student]
[Name of the university]
Object modelling
Assessment 1
[Name of the student]
[Name of the university]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1OBJECT MODELLING
Table of Contents
Introduction 2
Discussion 2
System vision Document 2
Required Resources 4
Stakeholders Map 5
Risk 5
Conclusion 6
References 6
Table of Contents
Introduction 2
Discussion 2
System vision Document 2
Required Resources 4
Stakeholders Map 5
Risk 5
Conclusion 6
References 6

2OBJECT MODELLING
Introduction
Business Information System plays an important role in the economy and various kinds
of enterprise settings by properly strategic procurements, outsourcing at a global kind of platform
and physical distribution operations(Kraan et al., 2013). Business Information System plays an
important role in boundary spanning field. It generally focusses on the fact that how (ICT)
information and communication technologies can be easily deployed for improvisation of
various business process and adding organization value. It generally focusses on the fact which is
required by organization need to produce and delivering goods and services all-round the globe.
It can be easily achieved by efficient, effective and competitive use of ICT (Yazici&Muradoglu,
2015). Business Information System generally helps students for developing skills which is
needed for effective system in global information based and technology driven environment.
In the coming pages of the report the effectiveness of business Information System has
been described in details. A complete kind of report has been provided which consist of system
vision document, required amount of resources, stakeholder map and risk involved in the project.
An analysis has been done on the various kinds of risk which is involved in the project.
Discussion
System vision Document
System vision document of Collin’s ATM system will consist of detail information of
card reader, keypad, a cash dispenser, printer and by the help of this cash which can be easily
deposited (Sukanya, 2015). There are large number of advantages of using ATM like
It provides easy withdraw of money.
Introduction
Business Information System plays an important role in the economy and various kinds
of enterprise settings by properly strategic procurements, outsourcing at a global kind of platform
and physical distribution operations(Kraan et al., 2013). Business Information System plays an
important role in boundary spanning field. It generally focusses on the fact that how (ICT)
information and communication technologies can be easily deployed for improvisation of
various business process and adding organization value. It generally focusses on the fact which is
required by organization need to produce and delivering goods and services all-round the globe.
It can be easily achieved by efficient, effective and competitive use of ICT (Yazici&Muradoglu,
2015). Business Information System generally helps students for developing skills which is
needed for effective system in global information based and technology driven environment.
In the coming pages of the report the effectiveness of business Information System has
been described in details. A complete kind of report has been provided which consist of system
vision document, required amount of resources, stakeholder map and risk involved in the project.
An analysis has been done on the various kinds of risk which is involved in the project.
Discussion
System vision Document
System vision document of Collin’s ATM system will consist of detail information of
card reader, keypad, a cash dispenser, printer and by the help of this cash which can be easily
deposited (Sukanya, 2015). There are large number of advantages of using ATM like
It provides easy withdraw of money.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3OBJECT MODELLING
At any place the amount of remaining money can be easily checked.
ATM provides round clock services like banking services to the customers to
round clock, that is 24x7 and for all days of the year.
The customer with ATM can access their account of bank from any place in
world. All the services like withdrawals, deposits, can be easily accessed from
any part of the world, and transfer the funds.
Basically, the service of ATM can be expanded so that all the users can use it
from any where the user like to. This can be only achieved by providing
electronic access to large of customers round the globe (Rogoff, 2015).
For the purpose of shopping, various types of shopping malls, restaurants and
many other kinds of organization that generally accepts payments through debit as
well as credit cards.
There are certain number of disadvantages of ATM like:
If any kind of issue arises then an individual cannot withdraw their amount of
money.
There are chances of the ATM credentials being hacked or taken by someone else.
If one forgets his or her pin number, then the ATM card is useless to him or her.
Then ATM card cannot be used for extracting money.
In some of the rural areas ATM cards cannot be used because various banks have
non-computerized branches and has very large number of rural branches. This is
the main disadvantage with the ATM.
There are many limitations to withdrawals of Cash from ATM: There is certain
number of transaction possible for withdrawing cash from various ATMs. Many
At any place the amount of remaining money can be easily checked.
ATM provides round clock services like banking services to the customers to
round clock, that is 24x7 and for all days of the year.
The customer with ATM can access their account of bank from any place in
world. All the services like withdrawals, deposits, can be easily accessed from
any part of the world, and transfer the funds.
Basically, the service of ATM can be expanded so that all the users can use it
from any where the user like to. This can be only achieved by providing
electronic access to large of customers round the globe (Rogoff, 2015).
For the purpose of shopping, various types of shopping malls, restaurants and
many other kinds of organization that generally accepts payments through debit as
well as credit cards.
There are certain number of disadvantages of ATM like:
If any kind of issue arises then an individual cannot withdraw their amount of
money.
There are chances of the ATM credentials being hacked or taken by someone else.
If one forgets his or her pin number, then the ATM card is useless to him or her.
Then ATM card cannot be used for extracting money.
In some of the rural areas ATM cards cannot be used because various banks have
non-computerized branches and has very large number of rural branches. This is
the main disadvantage with the ATM.
There are many limitations to withdrawals of Cash from ATM: There is certain
number of transaction possible for withdrawing cash from various ATMs. Many
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4OBJECT MODELLING
of the banks also do not permit to withdraw more than 25,000 amount (Prasanthi
et al., 2014).
Facility of Cash is not very much safe and secure: The facility of cash deposit is
considered to be a restricted one. It is not at all safe as this method is similar to
dropping of dropping of envelop. So ATM method is considered to be advisable
thing.
There are certain numbers of misusing the ATM card: If the ATM card stolen,
misplaced, or lost. There are large number of reports related to misuse of ATM
cards.
ATM increases the distance of personal touch between customers and banks. So
as a result customer loses personal touch with various bankers.
There are large number of problem which can be encountered in an ATM. If the ATM machine
goes out of service, then the customers would be left without the ability to make any kind of
transaction until and unless the bank opens for next opening hours (Patel & Patel, 2015). The
ATM machine does not provides guarantee the 100% availability of Cash. In many cases it is
seen ATM run of low funds and customer will have to wait till the management takes care of the
fact. Presence of various kinds of constraints like illiteracy, security concern makes it difficult to
easily introduce ATM services.
Required Resources
There are many resources which are needed for various kinds of banking activities like
reading the ATM card of different customers, to insert the pin a keypad is required, a display
screen which provides information of ongoing operation in the ATM machine (Agwu& Carter,
of the banks also do not permit to withdraw more than 25,000 amount (Prasanthi
et al., 2014).
Facility of Cash is not very much safe and secure: The facility of cash deposit is
considered to be a restricted one. It is not at all safe as this method is similar to
dropping of dropping of envelop. So ATM method is considered to be advisable
thing.
There are certain numbers of misusing the ATM card: If the ATM card stolen,
misplaced, or lost. There are large number of reports related to misuse of ATM
cards.
ATM increases the distance of personal touch between customers and banks. So
as a result customer loses personal touch with various bankers.
There are large number of problem which can be encountered in an ATM. If the ATM machine
goes out of service, then the customers would be left without the ability to make any kind of
transaction until and unless the bank opens for next opening hours (Patel & Patel, 2015). The
ATM machine does not provides guarantee the 100% availability of Cash. In many cases it is
seen ATM run of low funds and customer will have to wait till the management takes care of the
fact. Presence of various kinds of constraints like illiteracy, security concern makes it difficult to
easily introduce ATM services.
Required Resources
There are many resources which are needed for various kinds of banking activities like
reading the ATM card of different customers, to insert the pin a keypad is required, a display
screen which provides information of ongoing operation in the ATM machine (Agwu& Carter,

5OBJECT MODELLING
2018). A cash dispenser, a printer for all the details of the transaction. A chute is required to
make deposition related to Cheques and cash.
Stakeholders Map
There are three type of stakeholders namely primary stakeholders, secondary
stakeholders and tertiary stakeholders involved with ATM machines. Clients making transaction
through any of the ATM machines can be considered to be a primary type of stakeholder
(Duvey, Goyal&Hemrajani, 2013). The manufacture of the ATM is generally considered as a
tertiary system because any kind of problem related to transaction are involved with it.
There are certain number of advantages and disadvantages for the stakeholders. There are
advantages for the use of stakeholders for an ATM like primarily it makes various kinds of
transaction at much faster rate, it also comes with chances of less kinds of errors (Alley et al.,
2016). All the transactions that are done with the ATM works smoothly, then the user using the
ATM will recommend others also to use that particular bank ATM and as a result more ATMs
will be built.
2018). A cash dispenser, a printer for all the details of the transaction. A chute is required to
make deposition related to Cheques and cash.
Stakeholders Map
There are three type of stakeholders namely primary stakeholders, secondary
stakeholders and tertiary stakeholders involved with ATM machines. Clients making transaction
through any of the ATM machines can be considered to be a primary type of stakeholder
(Duvey, Goyal&Hemrajani, 2013). The manufacture of the ATM is generally considered as a
tertiary system because any kind of problem related to transaction are involved with it.
There are certain number of advantages and disadvantages for the stakeholders. There are
advantages for the use of stakeholders for an ATM like primarily it makes various kinds of
transaction at much faster rate, it also comes with chances of less kinds of errors (Alley et al.,
2016). All the transactions that are done with the ATM works smoothly, then the user using the
ATM will recommend others also to use that particular bank ATM and as a result more ATMs
will be built.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
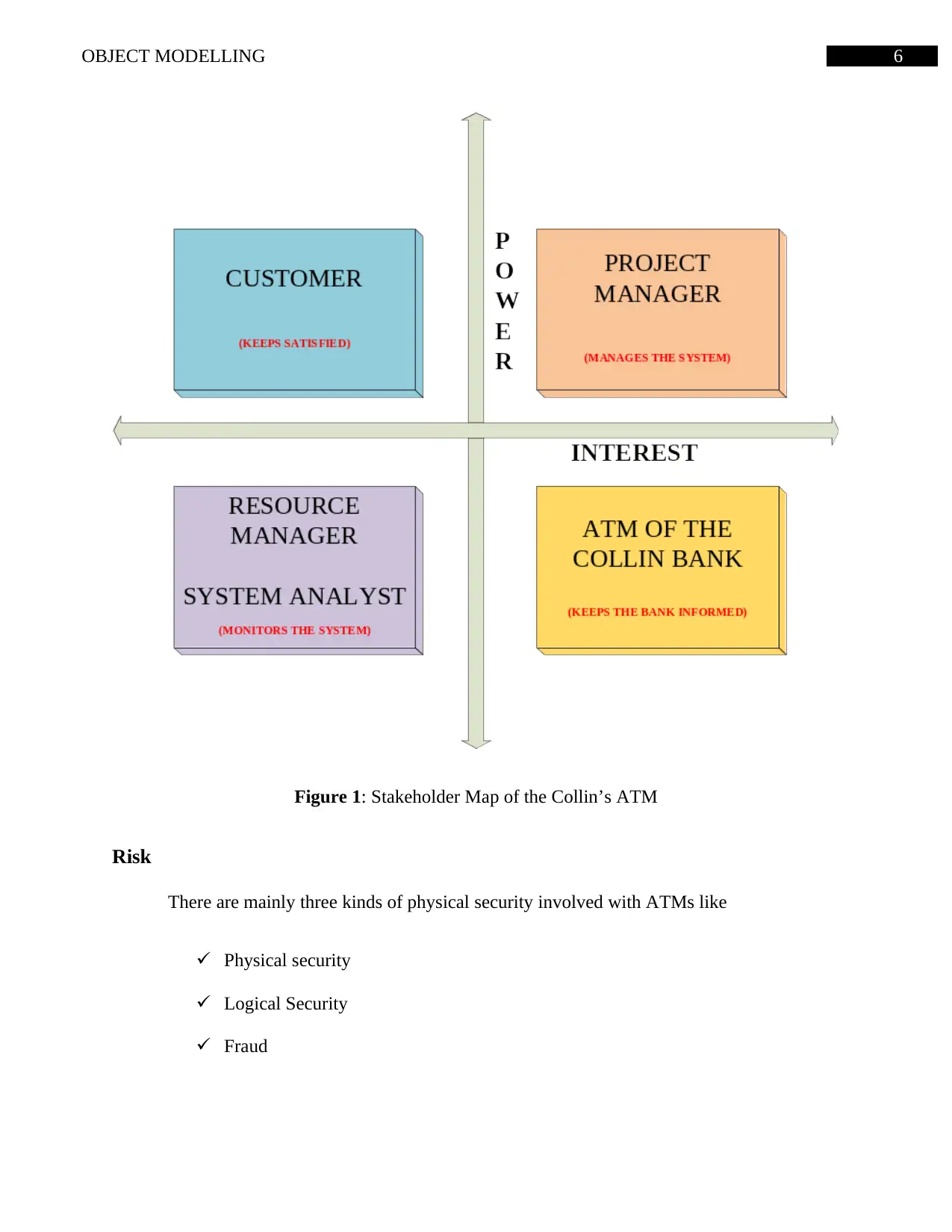
6OBJECT MODELLING
Figure 1: Stakeholder Map of the Collin’s ATM
Risk
There are mainly three kinds of physical security involved with ATMs like
Physical security
Logical Security
Fraud
Figure 1: Stakeholder Map of the Collin’s ATM
Risk
There are mainly three kinds of physical security involved with ATMs like
Physical security
Logical Security
Fraud
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7OBJECT MODELLING
Fraud also known as Skimmers is nothing but the attachment of external kind of
skimmers on the machine so that pin can be easily recorded on the skimmer device (Van
Grinsven et al., 2013). At present malware attacks in eastern Europe and America have raised a
lot of concern.
Conclusion
This report summarizes a detail information regarding business information system.
Various roles and objective of business information system has been discussed. The document
related to system vision has been provided. The system vision portion of the document generally
focus on benefits and drawbacks of various ATMs. A list of resources has been provided which
focus on ATM cards, Cheques and cash. A stakeholder’s map has been provided which consist
of primary, secondary and tertiary stakeholders has been provided. Various kinds of kinds of risk
involved with ATMs has been described in details which focus on certain parameters like
physical security, logical security and lastly fraud. Various kinds of benefits of system vision
documents like easy withdraw of money, unlimited access to bank from any place in the world,
expanding their services to various regions of the world, shopping. Various disadvantages like
technical issues may result in failure of withdrawal of money. It also focuses on limitation to
withdrawing of cash from bank ATMs. Various problems with respect to ATM’s has been
described in details.
Fraud also known as Skimmers is nothing but the attachment of external kind of
skimmers on the machine so that pin can be easily recorded on the skimmer device (Van
Grinsven et al., 2013). At present malware attacks in eastern Europe and America have raised a
lot of concern.
Conclusion
This report summarizes a detail information regarding business information system.
Various roles and objective of business information system has been discussed. The document
related to system vision has been provided. The system vision portion of the document generally
focus on benefits and drawbacks of various ATMs. A list of resources has been provided which
focus on ATM cards, Cheques and cash. A stakeholder’s map has been provided which consist
of primary, secondary and tertiary stakeholders has been provided. Various kinds of kinds of risk
involved with ATMs has been described in details which focus on certain parameters like
physical security, logical security and lastly fraud. Various kinds of benefits of system vision
documents like easy withdraw of money, unlimited access to bank from any place in the world,
expanding their services to various regions of the world, shopping. Various disadvantages like
technical issues may result in failure of withdrawal of money. It also focuses on limitation to
withdrawing of cash from bank ATMs. Various problems with respect to ATM’s has been
described in details.

8OBJECT MODELLING
References
Agwu, E., & Carter, A. L. (2018). Mobile phone banking in Nigeria: benefits, problems and
prospects.
Alley, I. S., Adebayo, L. A., Oligbi, B., &Lawal, A. (2016). Cancellation of ATM Withdrawal
Charges and the Cash Policy in Nigeria. Global Journal of Management And Business
Research.
Duvey, A. A., Goyal, D., &Hemrajani, D. N. (2013). A reliable ATM protocol and comparative
analysis on various parameters with other ATM protocols. International Journal of
Communication and Computer Technologies, 1(56), 192-197.
Kraan, M., Uhlmann, S., Steenbergen, J., Van Helmond, A. T. M., & Van Hoof, L. (2013). The
optimal process of self‐sampling in fisheries: lessons learned in the Netherlandsa. Journal
of fish biology, 83(4), 963-973.
Patel, H., & Patel, R. (2015). Cloud Analyst: An Insight of Service Broker Policy. International
Journal of Advanced Research in Computer and Communication Engineering, 4(1), 122-
127.
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security Enhancement of
ATM System with Fingerprint and DNA Data. International Journal of Advanced
Research in Computer Science and Software Engineering.
Rogoff, K. (2015). Costs and benefits to phasing out paper currency. NBER Macroeconomics
Annual, 29(1), 445-456.
References
Agwu, E., & Carter, A. L. (2018). Mobile phone banking in Nigeria: benefits, problems and
prospects.
Alley, I. S., Adebayo, L. A., Oligbi, B., &Lawal, A. (2016). Cancellation of ATM Withdrawal
Charges and the Cash Policy in Nigeria. Global Journal of Management And Business
Research.
Duvey, A. A., Goyal, D., &Hemrajani, D. N. (2013). A reliable ATM protocol and comparative
analysis on various parameters with other ATM protocols. International Journal of
Communication and Computer Technologies, 1(56), 192-197.
Kraan, M., Uhlmann, S., Steenbergen, J., Van Helmond, A. T. M., & Van Hoof, L. (2013). The
optimal process of self‐sampling in fisheries: lessons learned in the Netherlandsa. Journal
of fish biology, 83(4), 963-973.
Patel, H., & Patel, R. (2015). Cloud Analyst: An Insight of Service Broker Policy. International
Journal of Advanced Research in Computer and Communication Engineering, 4(1), 122-
127.
Prasanthi, B. V., Jyothi, U. P., Sridevi, B., & Krishna, T. V. (2014). Security Enhancement of
ATM System with Fingerprint and DNA Data. International Journal of Advanced
Research in Computer Science and Software Engineering.
Rogoff, K. (2015). Costs and benefits to phasing out paper currency. NBER Macroeconomics
Annual, 29(1), 445-456.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9OBJECT MODELLING
Sukanya, R. (2015). Jan Dhan–Issues and challenges. Abhinav International Monthly Refereed
Journal of Research in Management and Technology, 4(1).
Van Grinsven, H. J., Holland, M., Jacobsen, B. H., Klimont, Z., Sutton, M. A., &Jaap Willems,
W. (2013). Costs and benefits of nitrogen for Europe and implications for
mitigation. Environmental science & technology, 47(8), 3571-3579.
Yazici, B., &Muradoglu, Y. G. (2015). Dissemination of stock recommendations and small
investors: who benefits?.
Sukanya, R. (2015). Jan Dhan–Issues and challenges. Abhinav International Monthly Refereed
Journal of Research in Management and Technology, 4(1).
Van Grinsven, H. J., Holland, M., Jacobsen, B. H., Klimont, Z., Sutton, M. A., &Jaap Willems,
W. (2013). Costs and benefits of nitrogen for Europe and implications for
mitigation. Environmental science & technology, 47(8), 3571-3579.
Yazici, B., &Muradoglu, Y. G. (2015). Dissemination of stock recommendations and small
investors: who benefits?.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





