Cache Poisoned Denial of Service (CPDoS) Exploit Analysis
VerifiedAdded on 2022/08/20
|13
|2760
|11
Report
AI Summary
This report provides a comprehensive analysis of the Cache Poisoned Denial of Service (CPDoS) exploit, a modern threat targeting web resources distributed through Content Delivery Networks (CDNs). The report begins by defining CPDoS and explaining its mechanism, which involves exploiting vulnerabilities in CDNs through malicious HTTP requests and headers. It then delves into the principles of CDNs, illustrating their function in content distribution and highlighting their role in the exploit. The report provides examples of CPDoS attacks and discusses two potential solutions: sanitizing HTTP headers and ensuring that backend web servers do not trust any content within HTTP requests. Furthermore, it analyzes the future importance and effectiveness of CPDoS, emphasizing the vulnerability of distributed systems and the need for robust security measures. The conclusion summarizes the key findings, underscoring the significance of understanding and mitigating CPDoS attacks to safeguard web applications and maintain their availability.

Running head: NETWORKING
NETWORKING
Name of the Student
Name of the University
Author Note:
NETWORKING
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORKING
Table of Contents
Introduction..........................................................................................................................2
Principles of CDN............................................................................................................2
Example of Use of CDN..................................................................................................3
Description of CPDoS exploit.........................................................................................4
Critical discussion of two possible solution to CPDoS exploit.......................................5
Future importance and effectiveness of CPDoS..............................................................6
Conclusion...........................................................................................................................7
References............................................................................................................................8
Table of Contents
Introduction..........................................................................................................................2
Principles of CDN............................................................................................................2
Example of Use of CDN..................................................................................................3
Description of CPDoS exploit.........................................................................................4
Critical discussion of two possible solution to CPDoS exploit.......................................5
Future importance and effectiveness of CPDoS..............................................................6
Conclusion...........................................................................................................................7
References............................................................................................................................8

2NETWORKING
Introduction
Cache poisoned denial of services (CPDoS) can be defined as the new class of new cache
poisoning attacks which focus on disabling the given web resources and websites. CPDoS can
easily block and disable any kind of web resources that are distributed through content
distributed networks (Nguyen, Iacono, and Federrath 2019). The main task of CPDoS can easily
block and disable any kind of web resources which is completely distributed through content
distributed, HTTP request and malicious header. In this, attacker simply send a simple HTTP,
which puts a request for the malicious header for the given target source given by web server
(DiBenedetto and Papadopoulos 2016). Most of the legitimate user focus on the target resource
with requests when they gets cached error page instead of the original content.
In the coming pages of the report, an idea has been provided regarding the principles of
CDN. The next section deals with the description of CPDoS exploit. In addition, the report
discusses with respect to two possible solutions for CPDoS exploit. The last section of the
report's future importance and effectiveness of CPDoS has been discussed in detail.
Principles of CDN
CDN stands for Content Distribution Network, which is defined as the system of
distributed servers that provide webpages and other kinds of web content to users. This is
completely based on the geographical location of the user (Prabadevi and Jeyanthi 2018). It
completely works that close content of web hosting provider’s is the user. It will become much
faster as it is easily accessible to that particular person. CDN is merely used for streaming both
audio and video content. This merely helps in the optimization of load distribution of servers and
enhancing the overall experience of the user. CDN does not require to have a system of physical
servers (Prabadevi et al. 2019). This is merely achieved by establishing a connection between
Introduction
Cache poisoned denial of services (CPDoS) can be defined as the new class of new cache
poisoning attacks which focus on disabling the given web resources and websites. CPDoS can
easily block and disable any kind of web resources that are distributed through content
distributed networks (Nguyen, Iacono, and Federrath 2019). The main task of CPDoS can easily
block and disable any kind of web resources which is completely distributed through content
distributed, HTTP request and malicious header. In this, attacker simply send a simple HTTP,
which puts a request for the malicious header for the given target source given by web server
(DiBenedetto and Papadopoulos 2016). Most of the legitimate user focus on the target resource
with requests when they gets cached error page instead of the original content.
In the coming pages of the report, an idea has been provided regarding the principles of
CDN. The next section deals with the description of CPDoS exploit. In addition, the report
discusses with respect to two possible solutions for CPDoS exploit. The last section of the
report's future importance and effectiveness of CPDoS has been discussed in detail.
Principles of CDN
CDN stands for Content Distribution Network, which is defined as the system of
distributed servers that provide webpages and other kinds of web content to users. This is
completely based on the geographical location of the user (Prabadevi and Jeyanthi 2018). It
completely works that close content of web hosting provider’s is the user. It will become much
faster as it is easily accessible to that particular person. CDN is merely used for streaming both
audio and video content. This merely helps in the optimization of load distribution of servers and
enhancing the overall experience of the user. CDN does not require to have a system of physical
servers (Prabadevi et al. 2019). This is merely achieved by establishing a connection between
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
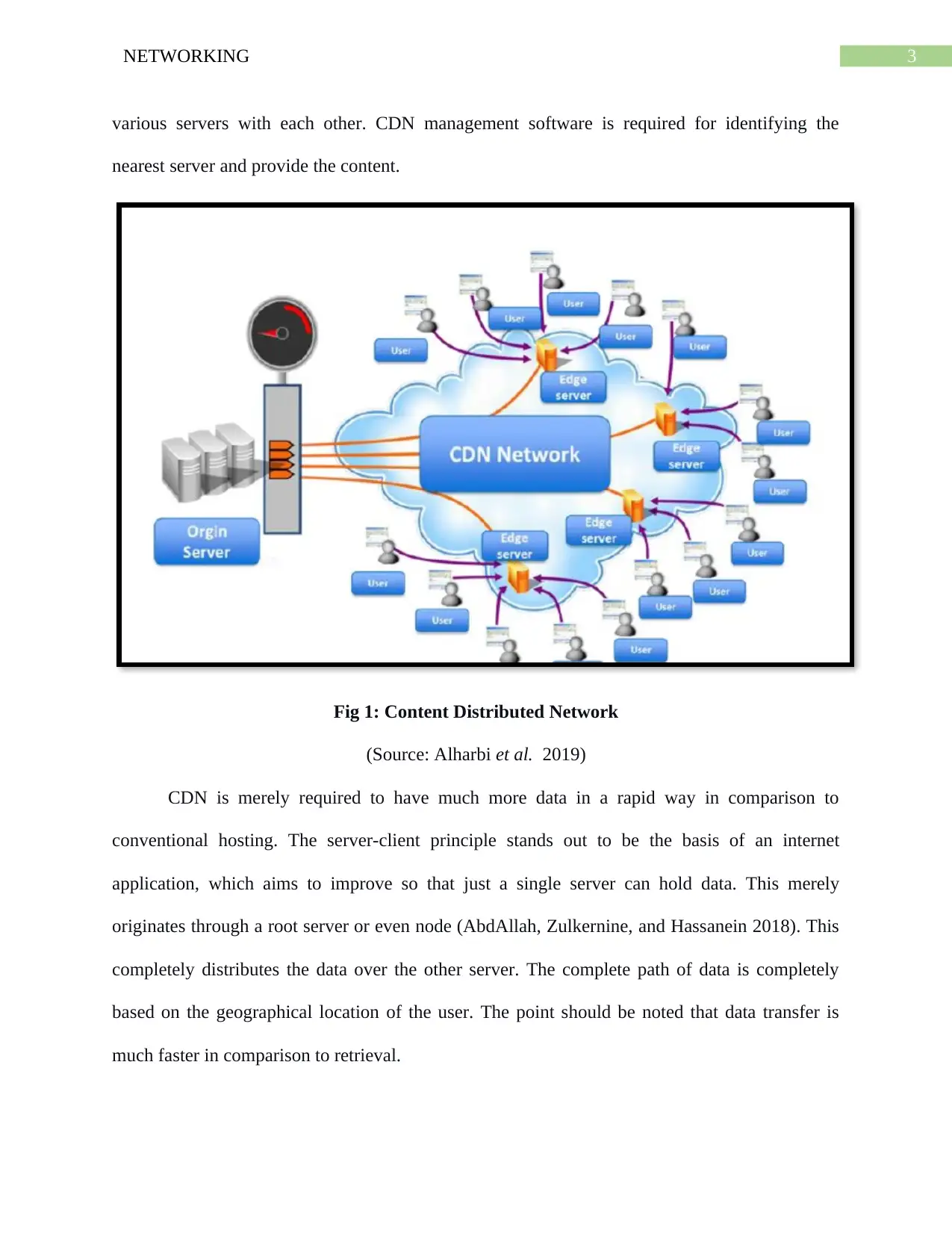
3NETWORKING
various servers with each other. CDN management software is required for identifying the
nearest server and provide the content.
Fig 1: Content Distributed Network
(Source: Alharbi et al. 2019)
CDN is merely required to have much more data in a rapid way in comparison to
conventional hosting. The server-client principle stands out to be the basis of an internet
application, which aims to improve so that just a single server can hold data. This merely
originates through a root server or even node (AbdAllah, Zulkernine, and Hassanein 2018). This
completely distributes the data over the other server. The complete path of data is completely
based on the geographical location of the user. The point should be noted that data transfer is
much faster in comparison to retrieval.
various servers with each other. CDN management software is required for identifying the
nearest server and provide the content.
Fig 1: Content Distributed Network
(Source: Alharbi et al. 2019)
CDN is merely required to have much more data in a rapid way in comparison to
conventional hosting. The server-client principle stands out to be the basis of an internet
application, which aims to improve so that just a single server can hold data. This merely
originates through a root server or even node (AbdAllah, Zulkernine, and Hassanein 2018). This
completely distributes the data over the other server. The complete path of data is completely
based on the geographical location of the user. The point should be noted that data transfer is
much faster in comparison to retrieval.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORKING
The root server mirrors the content to a system of server distribution on a global platform.
It merely acts as a quick way to a request as the path to the server is a much shorter time interval.
The point should be noted that the path to the telecommunication data needs to be delivered at a
much faster rate. The equation of speed stands out to be equal distance, which requires the
implication of time (Singh 2018). CDN system focus on reducing the server timeouts, incorrect
data packets, and jitter. The bandwidth of internet connection is used effectively. CDN aims to
optimize the data in an effective way that exists in between server and client. It merely helps in
ensuring a much better experience by minimizing both load times and reducing waits.
Example of Use of CDN
CDN can help in improving the loading time of the website by complete the distribution
of content in a close way. It merely focuses on nearby CND servers where the visitor can
experience much faster loading pages (Shah and Cosgrove 2019). When the visitor clicks away
from the slow-loading website, a CDN can quickly bounce the rates and even increase the
amount of time spend on site.
Description of CPDoS exploit
CPDoS stands out for Cache- Poisoned Denial of Services that can overcome the
semantic gaps in between shared cache and origin server. The attack is entirely initiated by
sending an HTTP request with a malicious header, which specifically targets a victim domain.
The given request is processed by making use of intermediate cache and completely remains
undetected (Yu et al. 2020). Cache request needs to be forwarded to the origin server, and the
origin server completely provokes error as a result of malicious header. The origin server returns
with an error message, and the error completely gets stored in the cache. If the attack is found to
be successful, then the attacker will have an error page with the response to legitimate users
The root server mirrors the content to a system of server distribution on a global platform.
It merely acts as a quick way to a request as the path to the server is a much shorter time interval.
The point should be noted that the path to the telecommunication data needs to be delivered at a
much faster rate. The equation of speed stands out to be equal distance, which requires the
implication of time (Singh 2018). CDN system focus on reducing the server timeouts, incorrect
data packets, and jitter. The bandwidth of internet connection is used effectively. CDN aims to
optimize the data in an effective way that exists in between server and client. It merely helps in
ensuring a much better experience by minimizing both load times and reducing waits.
Example of Use of CDN
CDN can help in improving the loading time of the website by complete the distribution
of content in a close way. It merely focuses on nearby CND servers where the visitor can
experience much faster loading pages (Shah and Cosgrove 2019). When the visitor clicks away
from the slow-loading website, a CDN can quickly bounce the rates and even increase the
amount of time spend on site.
Description of CPDoS exploit
CPDoS stands out for Cache- Poisoned Denial of Services that can overcome the
semantic gaps in between shared cache and origin server. The attack is entirely initiated by
sending an HTTP request with a malicious header, which specifically targets a victim domain.
The given request is processed by making use of intermediate cache and completely remains
undetected (Yu et al. 2020). Cache request needs to be forwarded to the origin server, and the
origin server completely provokes error as a result of malicious header. The origin server returns
with an error message, and the error completely gets stored in the cache. If the attack is found to
be successful, then the attacker will have an error page with the response to legitimate users

5NETWORKING
(Alharbi et al. 2019). Most of the customers do not take any particular action in order to protect
themselves from newly disclosed vulnerabilities. It merely reaches the website when the cache
has an error page. There are mainly three variations of CPDoS like
HTTP Header Oversize: It only works by sending a large header in comparison to a size
that is supported by the origin server. The whole attack works where the web application makes
use of the cache, which can accept a much larger header size limit in comparison to the origin
server limit (Pandey and Saini 2016). Some of the common web frameworks which support
header in order to override HTTP method is provided in HTTP request. GET request is sent with
X-HTTP method, which is treated by the origin post request. An attacker can make use of this
kind of behavior in order to trick CDN into this caching poisoned content.
HTTP Meta Character: In the HMC CPDoS attack, instead of sending the oversized
header, the attacker bypass an invalid Meta character. The attacker can send a large header where
CDN can pass to origin (Singh, Dhariwal, and Kumar 2017). This stands out to be too large for
the server in the origin to tackle. If, in this case, the shared cache stands out to be cacheable, it
will ultimately result in denial of services.
HTTP Method override: In this method, the attack can override the blocked request like
PUT and DELETE (Mittal and Gupta 2018). The same attack is oversized for HTTP headers,
except the attack, which makes use of some special character for returning errors.
(Alharbi et al. 2019). Most of the customers do not take any particular action in order to protect
themselves from newly disclosed vulnerabilities. It merely reaches the website when the cache
has an error page. There are mainly three variations of CPDoS like
HTTP Header Oversize: It only works by sending a large header in comparison to a size
that is supported by the origin server. The whole attack works where the web application makes
use of the cache, which can accept a much larger header size limit in comparison to the origin
server limit (Pandey and Saini 2016). Some of the common web frameworks which support
header in order to override HTTP method is provided in HTTP request. GET request is sent with
X-HTTP method, which is treated by the origin post request. An attacker can make use of this
kind of behavior in order to trick CDN into this caching poisoned content.
HTTP Meta Character: In the HMC CPDoS attack, instead of sending the oversized
header, the attacker bypass an invalid Meta character. The attacker can send a large header where
CDN can pass to origin (Singh, Dhariwal, and Kumar 2017). This stands out to be too large for
the server in the origin to tackle. If, in this case, the shared cache stands out to be cacheable, it
will ultimately result in denial of services.
HTTP Method override: In this method, the attack can override the blocked request like
PUT and DELETE (Mittal and Gupta 2018). The same attack is oversized for HTTP headers,
except the attack, which makes use of some special character for returning errors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
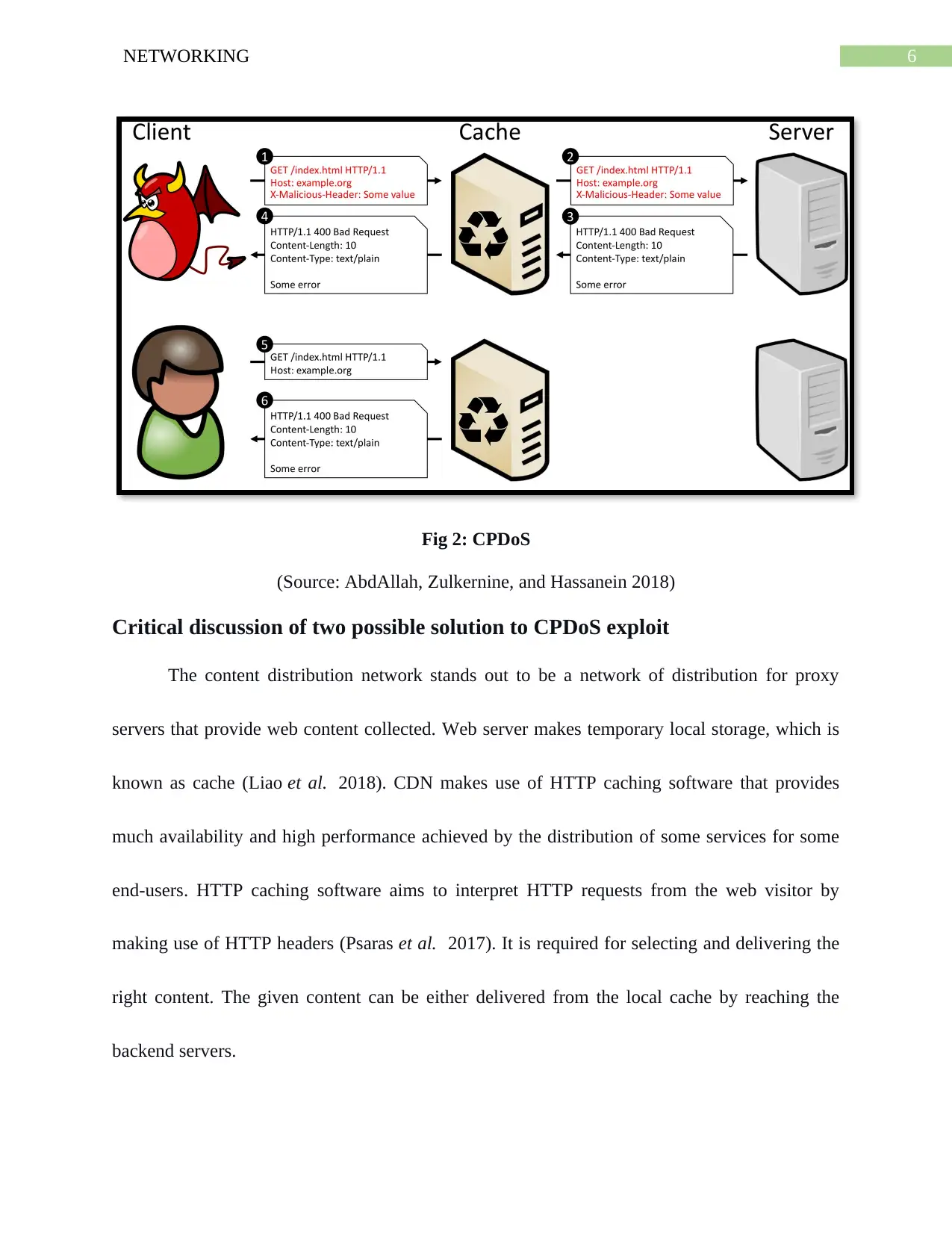
6NETWORKING
Fig 2: CPDoS
(Source: AbdAllah, Zulkernine, and Hassanein 2018)
Critical discussion of two possible solution to CPDoS exploit
The content distribution network stands out to be a network of distribution for proxy
servers that provide web content collected. Web server makes temporary local storage, which is
known as cache (Liao et al. 2018). CDN makes use of HTTP caching software that provides
much availability and high performance achieved by the distribution of some services for some
end-users. HTTP caching software aims to interpret HTTP requests from the web visitor by
making use of HTTP headers (Psaras et al. 2017). It is required for selecting and delivering the
right content. The given content can be either delivered from the local cache by reaching the
backend servers.
Fig 2: CPDoS
(Source: AbdAllah, Zulkernine, and Hassanein 2018)
Critical discussion of two possible solution to CPDoS exploit
The content distribution network stands out to be a network of distribution for proxy
servers that provide web content collected. Web server makes temporary local storage, which is
known as cache (Liao et al. 2018). CDN makes use of HTTP caching software that provides
much availability and high performance achieved by the distribution of some services for some
end-users. HTTP caching software aims to interpret HTTP requests from the web visitor by
making use of HTTP headers (Psaras et al. 2017). It is required for selecting and delivering the
right content. The given content can be either delivered from the local cache by reaching the
backend servers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORKING
Fig 3: CPDoS Exploit
(Source: Singh, Dhariwal, and Kumar 2017)
The whole vulnerability works by providing arbitrary headers into the HTTP request
team, which is processed by back end servers. It is inclusive of attackers that can inject content
in response without the need for any kind of sanitization. As soon as the malicious content of the
attacker is returned, this is cached by making use of HTTP software (Nguyen, Iacono, and
Federrath 2019). It merely allows the attacker to have arbitrary content as soon as the multiple
future visitors are hosted.
There are mainly two possible solutions for this attack like
CDN needs to inspect and sanitize the header by making use of right enforcement. It
follows strict adherence which is applied to RFCs prior to forwarding these to headers to
web servers.
Fig 3: CPDoS Exploit
(Source: Singh, Dhariwal, and Kumar 2017)
The whole vulnerability works by providing arbitrary headers into the HTTP request
team, which is processed by back end servers. It is inclusive of attackers that can inject content
in response without the need for any kind of sanitization. As soon as the malicious content of the
attacker is returned, this is cached by making use of HTTP software (Nguyen, Iacono, and
Federrath 2019). It merely allows the attacker to have arbitrary content as soon as the multiple
future visitors are hosted.
There are mainly two possible solutions for this attack like
CDN needs to inspect and sanitize the header by making use of right enforcement. It
follows strict adherence which is applied to RFCs prior to forwarding these to headers to
web servers.

8NETWORKING
CDN needs to replace, remove, or even append headers after sanitization, which is
submitted by the client (DiBenedetto and Papadopoulos 2016). It is expected to be
generated or even validated by making use of CDN.
Back end web servers should not trust any content, which is considered as the part of HTTP
requests (Prabadevi and Jeyanthi 2018). Web servers need to implement secure encodes for the
right output for encoding the output of common targets in the domain of web applications.
Future importance and effectiveness of CPDoS
Web cache helps in the reuse of HTTP responses with the target of reducing the request
number reaching the origin server. The overall volume of network traffic ultimately comes into a
picture from the different resources from requests (Prabadevi et al. 2019). Cache stands out to
an essential component that is used in the present distribution network as it helps the application
to scale in large. Along with network optimization, the cache provides complete protection
against DoS attack.
CDN needs to replace, remove, or even append headers after sanitization, which is
submitted by the client (DiBenedetto and Papadopoulos 2016). It is expected to be
generated or even validated by making use of CDN.
Back end web servers should not trust any content, which is considered as the part of HTTP
requests (Prabadevi and Jeyanthi 2018). Web servers need to implement secure encodes for the
right output for encoding the output of common targets in the domain of web applications.
Future importance and effectiveness of CPDoS
Web cache helps in the reuse of HTTP responses with the target of reducing the request
number reaching the origin server. The overall volume of network traffic ultimately comes into a
picture from the different resources from requests (Prabadevi et al. 2019). Cache stands out to
an essential component that is used in the present distribution network as it helps the application
to scale in large. Along with network optimization, the cache provides complete protection
against DoS attack.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORKING
Fig 4: New sites of CPDoS Web cache Poisoning Attacks
(Source : DiBenedetto and Papadopoulos 2016)
Caching is used as a network that aims to reduce the overall traffic. It helps in optimizing
the performance of the application. Cache aims to store recycle response with the target of reuse,
which is needed for recurring client requests (AbdAllah, Zulkernine and Hassanein 2018).
Cached resources are ultimately identified by the cache, which comprises of standard HTTP
method used in the URL. The web caching system aims to provide many benefits concerning
communication optimization and the performance of the different applications. Web caches can
be exploited, which affects both the privacy and reliability of the application. The steaming of
vulnerabilities stands out to be an essential security threat (Singh 2018). Distributed systems
stand out to be especially for this kind of attack, which comprises of various layers. HTTP
archive data set stands out to be potential, which is vulnerable to offenses related to CPDoS
attack. Cache contents comprise of mission-critical firmware and any kind of updated files (Shah
and Cosgrove 2019). The point should be taken into account that the distributed application aims
to follow microservices and service-oriented architecture. In this, the design principles are
nothing but services implemented with various kinds of programming languages (Yu et
al. 2020). This is completely operated by making use of distinct entities that have gap
vulnerabilities in the near future. There is a need for understanding vulnerabilities which require
to be gathered for developing safeguards. It does not depend on particular implementing and
addition of system layers.
Conclusion
The above pages help us in concluding the point that this report is all about cache
poisoned denial of services vulnerability that is seen from 2019. In the report, an overview has
Fig 4: New sites of CPDoS Web cache Poisoning Attacks
(Source : DiBenedetto and Papadopoulos 2016)
Caching is used as a network that aims to reduce the overall traffic. It helps in optimizing
the performance of the application. Cache aims to store recycle response with the target of reuse,
which is needed for recurring client requests (AbdAllah, Zulkernine and Hassanein 2018).
Cached resources are ultimately identified by the cache, which comprises of standard HTTP
method used in the URL. The web caching system aims to provide many benefits concerning
communication optimization and the performance of the different applications. Web caches can
be exploited, which affects both the privacy and reliability of the application. The steaming of
vulnerabilities stands out to be an essential security threat (Singh 2018). Distributed systems
stand out to be especially for this kind of attack, which comprises of various layers. HTTP
archive data set stands out to be potential, which is vulnerable to offenses related to CPDoS
attack. Cache contents comprise of mission-critical firmware and any kind of updated files (Shah
and Cosgrove 2019). The point should be taken into account that the distributed application aims
to follow microservices and service-oriented architecture. In this, the design principles are
nothing but services implemented with various kinds of programming languages (Yu et
al. 2020). This is completely operated by making use of distinct entities that have gap
vulnerabilities in the near future. There is a need for understanding vulnerabilities which require
to be gathered for developing safeguards. It does not depend on particular implementing and
addition of system layers.
Conclusion
The above pages help us in concluding the point that this report is all about cache
poisoned denial of services vulnerability that is seen from 2019. In the report, an overview has
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORKING
been provided regarding content distributed networks, it's working, and how this can be used. A
short description of CPDoS and its pattern of exploiting has been discussed. Two solutions have
been provided in order to establish a defense mechanism against it. The last section of the report
deals with the prediction and impact of DDoS. Web stands out to be one of the largest distributed
systems. With the ever-growing amount of data on the web platform, there is a need for a vital
pillar for scalability. Web caching system comes into the picture for in-path location, which lies
in between client and server origin. Web-caching standard aims to define a collection of controls
that are needed for instructing cache. It merely focus on how it is stored and reused for recycling.
been provided regarding content distributed networks, it's working, and how this can be used. A
short description of CPDoS and its pattern of exploiting has been discussed. Two solutions have
been provided in order to establish a defense mechanism against it. The last section of the report
deals with the prediction and impact of DDoS. Web stands out to be one of the largest distributed
systems. With the ever-growing amount of data on the web platform, there is a need for a vital
pillar for scalability. Web caching system comes into the picture for in-path location, which lies
in between client and server origin. Web-caching standard aims to define a collection of controls
that are needed for instructing cache. It merely focus on how it is stored and reused for recycling.

11NETWORKING
References
AbdAllah, E.G., Zulkernine, M. and Hassanein, H.S., 2018. DADI: Defending against distributed
denial of service in information‐centric networking routing and caching. Security and
Privacy, 1(2), p.e16.
Alharbi, F., Chang, J., Zhou, Y., Qian, F., Qian, Z. and Abu-Ghazaleh, N., 2019, April.
Collaborative Client-Side DNS Cache Poisoning Attack. In IEEE INFOCOM 2019-IEEE
Conference on Computer Communications (pp. 1153-1161). IEEE.
DiBenedetto, S. and Papadopoulos, C., 2016, April. Mitigating poisoned content with forwarding
strategy. In 2016 IEEE Conference on Computer Communications Workshops (INFOCOM
WKSHPS) (pp. 164-169). IEEE.
Liao, D., Sun, G., Yang, G. and Chang, V., 2018. Energy-efficient virtual content distribution
network provisioning in cloud-based data centers. Future Generation Computer Systems, 83,
pp.347-357.
Mittal, G. and Gupta, V., 2018, September. KarmaNet: SDN solution to DNS-based Denial-of-
Service. In International Symposium on Security in Computing and Communication (pp. 431-
442). Springer, Singapore.
Nguyen, H.V., Iacono, L.L. and Federrath, H., 2019, November. Your Cache Has Fallen: Cache-
Poisoned Denial-of-Service Attack. In Proceedings of the 2019 ACM SIGSAC Conference on
Computer and Communications Security (pp. 1915-1936).
Pandey, A. and Saini, J.R., 2016. Comprehensive Security Mechanism for Defending Cyber
Attacks based upon Spoofing and Poisoning. Our Major Indexing at International Level, p.1011.
References
AbdAllah, E.G., Zulkernine, M. and Hassanein, H.S., 2018. DADI: Defending against distributed
denial of service in information‐centric networking routing and caching. Security and
Privacy, 1(2), p.e16.
Alharbi, F., Chang, J., Zhou, Y., Qian, F., Qian, Z. and Abu-Ghazaleh, N., 2019, April.
Collaborative Client-Side DNS Cache Poisoning Attack. In IEEE INFOCOM 2019-IEEE
Conference on Computer Communications (pp. 1153-1161). IEEE.
DiBenedetto, S. and Papadopoulos, C., 2016, April. Mitigating poisoned content with forwarding
strategy. In 2016 IEEE Conference on Computer Communications Workshops (INFOCOM
WKSHPS) (pp. 164-169). IEEE.
Liao, D., Sun, G., Yang, G. and Chang, V., 2018. Energy-efficient virtual content distribution
network provisioning in cloud-based data centers. Future Generation Computer Systems, 83,
pp.347-357.
Mittal, G. and Gupta, V., 2018, September. KarmaNet: SDN solution to DNS-based Denial-of-
Service. In International Symposium on Security in Computing and Communication (pp. 431-
442). Springer, Singapore.
Nguyen, H.V., Iacono, L.L. and Federrath, H., 2019, November. Your Cache Has Fallen: Cache-
Poisoned Denial-of-Service Attack. In Proceedings of the 2019 ACM SIGSAC Conference on
Computer and Communications Security (pp. 1915-1936).
Pandey, A. and Saini, J.R., 2016. Comprehensive Security Mechanism for Defending Cyber
Attacks based upon Spoofing and Poisoning. Our Major Indexing at International Level, p.1011.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





