Security Management Report: Capital One Data Breach and Risk
VerifiedAdded on 2023/01/19
|24
|6782
|52
Report
AI Summary
This report delves into the critical aspects of security management, using the Capital One data breach as a central case study. It begins with an introduction to security management principles and then analyzes the Capital One incident, detailing the scope of the breach, the organization's background, and the specifics of the data compromise. The report then explores information security risk assessment and management, including asset inventory, risk registers, risk treatment, and gap analysis. Furthermore, it covers disaster recovery and business continuity planning, essential elements for mitigating the impact of security incidents. The assignment concludes with a critical analysis of how the chosen scenario organization can improve overall information security, along with a student's contribution to the coursework, offering a comprehensive view of the challenges and solutions in modern security management.

Security Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
TASK 1.1 Capital one data breach incident.....................................................................................1
TASK 2 Information Security Risks Assessment and Management...............................................7
2.1 : Information Security Risk Management Justification....................................................7
2.2 : Inventory of assets..........................................................................................................7
2.3 : Risk Register................................................................................................................15
2.4 : Risk Treatment.............................................................................................................15
2.5 : Gap analysis and Summary..........................................................................................16
Task 3: Disaster recovery and business continuity........................................................................16
Disaster Recovery Plan.........................................................................................................16
Business continuity Plan.......................................................................................................17
TASK 4..........................................................................................................................................18
Please summarize your contribution to the course work (250 words max):........................18
TASK 5..........................................................................................................................................19
Your critical analysis how the chosen scenario organisation can improve the overall
information security..............................................................................................................19
CONCLUSION..............................................................................................................................21
REFERENCES..............................................................................................................................22
INTRODUCTION...........................................................................................................................1
TASK 1.1 Capital one data breach incident.....................................................................................1
TASK 2 Information Security Risks Assessment and Management...............................................7
2.1 : Information Security Risk Management Justification....................................................7
2.2 : Inventory of assets..........................................................................................................7
2.3 : Risk Register................................................................................................................15
2.4 : Risk Treatment.............................................................................................................15
2.5 : Gap analysis and Summary..........................................................................................16
Task 3: Disaster recovery and business continuity........................................................................16
Disaster Recovery Plan.........................................................................................................16
Business continuity Plan.......................................................................................................17
TASK 4..........................................................................................................................................18
Please summarize your contribution to the course work (250 words max):........................18
TASK 5..........................................................................................................................................19
Your critical analysis how the chosen scenario organisation can improve the overall
information security..............................................................................................................19
CONCLUSION..............................................................................................................................21
REFERENCES..............................................................................................................................22

INTRODUCTION
Security Management can be explained as the assets of an individual or even of business
organisation which are preserved securely. It is necessary because it helps to avoid any sort of
problem and risk which person might face. In present situation, lots of problem occurs on daily
basis related to the cyber attack and it takes place just because of weaker security management. In
context of the file, two different task are needed to be solved in which first task will explain about
the detail information about Capital One Bank Ltd where as in second task there will be
discussion about Japanese Exchange Bit Points.
TASK 1.1 Capital one data breach incident.
INTRODUCTION: This is a data breach incident report that occurred at Capital One US
company which affected personal data of many customers. Capital One is a US based bank
company that specializes in banking, loans, credit and debit card, payment protection, phone
banking, pay lending, online banking and savings. Capital One serves customers few businesses
and commercial clients worldwide. The breach resulted to unauthorized access to applicants and
customers personal details (information). The incident exposes the personal identifiable
information of 100 million Americans and 6 million Canadians. The customer’s data was
illegally accessed based on this report according to the federal prosecutor. The incident was set to
be one of the biggest in the history of bank industry. The incident reportedly an overwork a
configuration vulnerability in Capital One’s infrastructure which included at least one known
firewall misconfiguration, allowing access to customer data stored on Amazon Web Services’
cloud.
Scope: Talking about the scope, the major agenda will be what were the main reason that
the data breach incident took place and how many people were affected from the outcome. And,
also what are the possible ways to prevent this sort of action in future period.
The affected asset were personal data of about 100 million Americans and 6 million Canadians
(Customers and few businesses) which also included approximately:
Names, address, phone numbers and dates of birth as well.
Self-reported income.
Limit balances and payments records.
Plenty US Social Security numbers.
1
Security Management can be explained as the assets of an individual or even of business
organisation which are preserved securely. It is necessary because it helps to avoid any sort of
problem and risk which person might face. In present situation, lots of problem occurs on daily
basis related to the cyber attack and it takes place just because of weaker security management. In
context of the file, two different task are needed to be solved in which first task will explain about
the detail information about Capital One Bank Ltd where as in second task there will be
discussion about Japanese Exchange Bit Points.
TASK 1.1 Capital one data breach incident.
INTRODUCTION: This is a data breach incident report that occurred at Capital One US
company which affected personal data of many customers. Capital One is a US based bank
company that specializes in banking, loans, credit and debit card, payment protection, phone
banking, pay lending, online banking and savings. Capital One serves customers few businesses
and commercial clients worldwide. The breach resulted to unauthorized access to applicants and
customers personal details (information). The incident exposes the personal identifiable
information of 100 million Americans and 6 million Canadians. The customer’s data was
illegally accessed based on this report according to the federal prosecutor. The incident was set to
be one of the biggest in the history of bank industry. The incident reportedly an overwork a
configuration vulnerability in Capital One’s infrastructure which included at least one known
firewall misconfiguration, allowing access to customer data stored on Amazon Web Services’
cloud.
Scope: Talking about the scope, the major agenda will be what were the main reason that
the data breach incident took place and how many people were affected from the outcome. And,
also what are the possible ways to prevent this sort of action in future period.
The affected asset were personal data of about 100 million Americans and 6 million Canadians
(Customers and few businesses) which also included approximately:
Names, address, phone numbers and dates of birth as well.
Self-reported income.
Limit balances and payments records.
Plenty US Social Security numbers.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information stolen relate to credit cards applications from the year 2005 through the year 2019.
Organisation Detail: Capital One bank is moreover a bank holding company which
offers various products such as credit cards, auto loans, saving accounts, banking and many more.
It is a US based bank headquartered in McLean, Virginia. The bank is ranked 10th in the list of
largest banks of the US as per the assets and has its operations in UK, Canada and United States.
Capital one operates in three divisions which are credit cards, consumer banking and customer
banking. In terms of issuing credit cards they stood at 3rd place after JP Morgan and Citigroup.
Also they offers various baking services such as saving accounts, money market accounts and
checking accounts which helps them to cater a large number of customers from different
segments. After setting up their business they have been expanding their business by adding more
and more activities. Earlier they were known as Monoline credit card company in which they
used to have one product i.e., credit card. Later on gradually they expanded their business and
introduces various other services. In 1998 they acquired a auto finance company and then they
expanded their business into retail banking in 2005. Due to low rate environment and excessive
competition in the mortgage market the ceased their mortgage origination business operations
and recently in 2018 they have acquired a digital identity and fraud alert services. They have been
facing various issues such as they were penalised for misleading customers for extra payment for
the services, automated dialing on customer phones and in 2019 they faced an issue of security
breach. In this security breach, they found that unauthorised access has occurred to the data
because of which the data of millions of people has compromised. A former employee of
Amazon has stolen the consumer application for credit from Capital One of more than one
million people.
Incident Detail: The incident of breach of data took place on March 22nd and 23rd but
company found that breach of data have taken place on July 19. The main thing that had
happened in the case is that all of the data were hacked which were related with the personal
information such as name, address, date of birth, credit scores, transaction data, social security
numbers and linked bank account numbers (Information on the Capital One Cyber Incident,
2019). As capital banks is delivering there services to different part of the world so it was found
that people living within United States and Canada have to suffer from the problem of data
hacking. It was one of the data breach which have huge negative impact on social media because
company was unable to find single information or hint related to the hacking incident. The
2
Organisation Detail: Capital One bank is moreover a bank holding company which
offers various products such as credit cards, auto loans, saving accounts, banking and many more.
It is a US based bank headquartered in McLean, Virginia. The bank is ranked 10th in the list of
largest banks of the US as per the assets and has its operations in UK, Canada and United States.
Capital one operates in three divisions which are credit cards, consumer banking and customer
banking. In terms of issuing credit cards they stood at 3rd place after JP Morgan and Citigroup.
Also they offers various baking services such as saving accounts, money market accounts and
checking accounts which helps them to cater a large number of customers from different
segments. After setting up their business they have been expanding their business by adding more
and more activities. Earlier they were known as Monoline credit card company in which they
used to have one product i.e., credit card. Later on gradually they expanded their business and
introduces various other services. In 1998 they acquired a auto finance company and then they
expanded their business into retail banking in 2005. Due to low rate environment and excessive
competition in the mortgage market the ceased their mortgage origination business operations
and recently in 2018 they have acquired a digital identity and fraud alert services. They have been
facing various issues such as they were penalised for misleading customers for extra payment for
the services, automated dialing on customer phones and in 2019 they faced an issue of security
breach. In this security breach, they found that unauthorised access has occurred to the data
because of which the data of millions of people has compromised. A former employee of
Amazon has stolen the consumer application for credit from Capital One of more than one
million people.
Incident Detail: The incident of breach of data took place on March 22nd and 23rd but
company found that breach of data have taken place on July 19. The main thing that had
happened in the case is that all of the data were hacked which were related with the personal
information such as name, address, date of birth, credit scores, transaction data, social security
numbers and linked bank account numbers (Information on the Capital One Cyber Incident,
2019). As capital banks is delivering there services to different part of the world so it was found
that people living within United States and Canada have to suffer from the problem of data
hacking. It was one of the data breach which have huge negative impact on social media because
company was unable to find single information or hint related to the hacking incident. The
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

complete incident took place in the year 2019 were whole of the information were disclosed that
data of the company has been hacked and almost all of the customers are affected from it who has
been connected with Capital One Bank since year 2005-2019.
The data and information which were available in the Bank were sensitivity and it was
necessary that it must not have been disclosed to outsiders because it has created lots of issues for
them. All of the information were disclosed and it was necessary for the customers that must not
operate any of the information where were available in the bank. The sources which were taken
to access the data of general public was directly from internet. In this, data traffic mode were
used in which different IP address were used due to which it was not possible to find that what
were the main sources of hacking the confidential information. The team which have conducted
whole of this process is unknown but they have collected all of the information which they
requires personal benefits.
It was one of the preplanned data breach due to which around 100 million users were
affected and almost each and every system were compromised because if bank wants to add on
any of the new customers then all of the information were being shared with the main server due
to which even new users were also affected. It was found that the main server was hacked in it
due to which every single system was affected. In addition, the number of banks which were
connected with Capital one bank was also affected because there data were also copied due to
which customers excess were available with the one who have hacked the system (Pathan, 2016).
While talking about the Data compromised, Capital One Bank have disclosed that former
employees who were the part of company and even working in the top level position might be the
one who have compromised all of the data. It has been found that former employees have the
information of customers which are related wit account number, telephone number, transaction
history and even social security number. It was one of the major source of collecting all of the
relevant information related to customers and this is how data were beached.
Talking about the number of customers were affected it can be easily said that almost 106
million customers were affected (Capital One data breach involves 100 million credit card
applications, 2019). Among all of those customers, there were around 6 million customers who
belongs to Canada but they were the part of Bank. They were affected because there personal
information were available with other person due to their capital was not secure even there was
huge possibility that customers might have to face different sort of problems in future period of
3
data of the company has been hacked and almost all of the customers are affected from it who has
been connected with Capital One Bank since year 2005-2019.
The data and information which were available in the Bank were sensitivity and it was
necessary that it must not have been disclosed to outsiders because it has created lots of issues for
them. All of the information were disclosed and it was necessary for the customers that must not
operate any of the information where were available in the bank. The sources which were taken
to access the data of general public was directly from internet. In this, data traffic mode were
used in which different IP address were used due to which it was not possible to find that what
were the main sources of hacking the confidential information. The team which have conducted
whole of this process is unknown but they have collected all of the information which they
requires personal benefits.
It was one of the preplanned data breach due to which around 100 million users were
affected and almost each and every system were compromised because if bank wants to add on
any of the new customers then all of the information were being shared with the main server due
to which even new users were also affected. It was found that the main server was hacked in it
due to which every single system was affected. In addition, the number of banks which were
connected with Capital one bank was also affected because there data were also copied due to
which customers excess were available with the one who have hacked the system (Pathan, 2016).
While talking about the Data compromised, Capital One Bank have disclosed that former
employees who were the part of company and even working in the top level position might be the
one who have compromised all of the data. It has been found that former employees have the
information of customers which are related wit account number, telephone number, transaction
history and even social security number. It was one of the major source of collecting all of the
relevant information related to customers and this is how data were beached.
Talking about the number of customers were affected it can be easily said that almost 106
million customers were affected (Capital One data breach involves 100 million credit card
applications, 2019). Among all of those customers, there were around 6 million customers who
belongs to Canada but they were the part of Bank. They were affected because there personal
information were available with other person due to their capital was not secure even there was
huge possibility that customers might have to face different sort of problems in future period of
3

time. As per the collected information about the bank it was found that the users who were
connected with the bank were affected but there personal websites were also affected due to
which currently company is not available to provide online services. Also number of sites were
affected but the main problem which were raised is that some of the other financial institute and
other banks who were the part of Capital One Bank was also affected from this respective
incident. Even information were given to every customers that they must try to avoid each and
every activities which they want to do online because company is still facing the problem.
Incident Analysis: There were number of reason due to which whole of this incident took
place but the main problem which was found is that company was using the open source web
application which is allowing the hackers to copy each and every information which they were
willing to copy. They were also taking the help of different operational hosted in the cloud with
Amazon Web Services to provide the services which there customers want. These are some of
the main reason that information were easily available for the hackers to collect and misuse them
for personal benefits. The main target of hackers was to focus that how they can reach up to the
cloud security through which they can easily collect all of the information which they want for
there personal interest.
There were number of reasons due to which whole of this incident took place but the main
problem which was found is that the company was using an open source web application which
often allows hackers to copy each information they were willing to copy. The main target of
hackers was to focus on how they can reach up to the cloud security through which they can
easily collect all the information which they want for their personal interest. Firstly, the hacker
initially run a scan of the internet using Wireshark (web vulnerability scanning tool) to capture
data packets in the network in real time and to get vulnerable computers in which will be easier to
access the company’s internal networks. In this scenario the vulnerable computers were the weak
point in which the threat actor used as the attack door to exploit.
In disadvantage, the hacker tried so many ways as possible to find the ones that were not
locked and unguarded. She was able to find access through the Amazon Web Services’ metadata
service (vulnerability), allowing an entry into the Capital one’s systems. This sort of incident is
likely to be refer to as Server-Side Request Forgery, situation in which a server can be tricked
into getting somewhere it shouldn’t have access. Once inside other flaws now were found
exploited. Due to some misconfigured networks, the hacker was able to uncover some sensitive
4
connected with the bank were affected but there personal websites were also affected due to
which currently company is not available to provide online services. Also number of sites were
affected but the main problem which were raised is that some of the other financial institute and
other banks who were the part of Capital One Bank was also affected from this respective
incident. Even information were given to every customers that they must try to avoid each and
every activities which they want to do online because company is still facing the problem.
Incident Analysis: There were number of reason due to which whole of this incident took
place but the main problem which was found is that company was using the open source web
application which is allowing the hackers to copy each and every information which they were
willing to copy. They were also taking the help of different operational hosted in the cloud with
Amazon Web Services to provide the services which there customers want. These are some of
the main reason that information were easily available for the hackers to collect and misuse them
for personal benefits. The main target of hackers was to focus that how they can reach up to the
cloud security through which they can easily collect all of the information which they want for
there personal interest.
There were number of reasons due to which whole of this incident took place but the main
problem which was found is that the company was using an open source web application which
often allows hackers to copy each information they were willing to copy. The main target of
hackers was to focus on how they can reach up to the cloud security through which they can
easily collect all the information which they want for their personal interest. Firstly, the hacker
initially run a scan of the internet using Wireshark (web vulnerability scanning tool) to capture
data packets in the network in real time and to get vulnerable computers in which will be easier to
access the company’s internal networks. In this scenario the vulnerable computers were the weak
point in which the threat actor used as the attack door to exploit.
In disadvantage, the hacker tried so many ways as possible to find the ones that were not
locked and unguarded. She was able to find access through the Amazon Web Services’ metadata
service (vulnerability), allowing an entry into the Capital one’s systems. This sort of incident is
likely to be refer to as Server-Side Request Forgery, situation in which a server can be tricked
into getting somewhere it shouldn’t have access. Once inside other flaws now were found
exploited. Due to some misconfigured networks, the hacker was able to uncover some sensitive
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
documents from the cloud which was the actual keys she required to access the data vault and
download the customers information stored. A lack of understanding of potential vulnerabilities
results to unnecessary risk for business encrypting information saved in the cloud.
Based on this research, the hacker penetrates using a spyware (software that infiltrates a
computing devices). Different coding programs were used through which malware were created
that can easily decode the data securing process. Also, hackers used the malicious code that have
helped to cause undesired effects, security breaches or damage to a system. It is one of the
software which can affect the company’s antivirus software and will not be way through which
positive results can be obtained. Also, as the company used the open web services due to which
there were number of occasions in which errors might occurs and even those error have the
potential that whole of the data can be transferred to different networking system.
Network, different types of network were used within the company such as Personal Area
Network (PAN), Local Area Network (LAN), Wireless Local Area Network (WLAN) through
which all the information was being transferred from one system to another.Capital One banks
was unable to take the help of this networking system and they were transferring the data to
different web engine due to which it become very easy for the hacker to collect all the relevant
information through which they can hack the data of customers who relate to Capital One Bank.
Control: Steps taken so far: It is one of the major case which has created lots of problem
for the business organisation and it is necessary that some of the important steps must have been
taken so that positive outcomes can be achieved. Different steps were taken in this which started
from the networking system as none of the employees will be able to share the information of
company outside the organisation. However, some of the controls includes:
Table 1.1.1
CONTROL
NAME
SPECIFICATION REFERENCE
CA-1 Security assessment and organization
authorization policy and procedures.
NIST 800-53
CA-2 Security assessment. NIST 800-53
CA-3 System interconnection. NIST 800-53
CA-4 System certification. NIST 800-53
CA-5 Plan of action and milestones. NIST 800-53
5
download the customers information stored. A lack of understanding of potential vulnerabilities
results to unnecessary risk for business encrypting information saved in the cloud.
Based on this research, the hacker penetrates using a spyware (software that infiltrates a
computing devices). Different coding programs were used through which malware were created
that can easily decode the data securing process. Also, hackers used the malicious code that have
helped to cause undesired effects, security breaches or damage to a system. It is one of the
software which can affect the company’s antivirus software and will not be way through which
positive results can be obtained. Also, as the company used the open web services due to which
there were number of occasions in which errors might occurs and even those error have the
potential that whole of the data can be transferred to different networking system.
Network, different types of network were used within the company such as Personal Area
Network (PAN), Local Area Network (LAN), Wireless Local Area Network (WLAN) through
which all the information was being transferred from one system to another.Capital One banks
was unable to take the help of this networking system and they were transferring the data to
different web engine due to which it become very easy for the hacker to collect all the relevant
information through which they can hack the data of customers who relate to Capital One Bank.
Control: Steps taken so far: It is one of the major case which has created lots of problem
for the business organisation and it is necessary that some of the important steps must have been
taken so that positive outcomes can be achieved. Different steps were taken in this which started
from the networking system as none of the employees will be able to share the information of
company outside the organisation. However, some of the controls includes:
Table 1.1.1
CONTROL
NAME
SPECIFICATION REFERENCE
CA-1 Security assessment and organization
authorization policy and procedures.
NIST 800-53
CA-2 Security assessment. NIST 800-53
CA-3 System interconnection. NIST 800-53
CA-4 System certification. NIST 800-53
CA-5 Plan of action and milestones. NIST 800-53
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CA-6 Security authorization. NIST 800-53
CA-7 Continuous monitoring. NIST 800-53
In current scenario, company is not using the social networking sites to make data
secured. This was one of the incidents where every single user was given the information that
their accounts have been hacked and they must not do further transaction in current situation
because it might create number of problems for them.
Incident status: The Government believes that the data has been recovered and there is
no such evidence to as to data being used for fraud or shared by the hacker.
People who were Notified after the incident: The following people were notified after
the incident:
(a) The Government Agency.
(b) The Stakeholders.
(c) Those individuals whose social security numbers or linked bank account numbers
were compromised were notified by mail. The Company also provides free credit
monitoring and identity protection to those affected.
Lesson Learned: It was one of the case where complete mistake was of company so it is
important for any of the organisation that they must not share the information of company with
outsiders. It is necessary for the company to use secure form of data to share the personal
information of any of the customers who are connected with the company. The main things
which can be learned from whole of this incident is that different sources should be used to
maintain the data of customers because it will keep the chance to secure the data for longer period
of time. Even at a single time multiple data will not be allowed to hack which will enhance the
productivity of a company. Also, customers will get the chance to feel safe to maintain their data
with different organisation for personal benefits (Erfani, 2012). Also, it is important for business
organisation that they must not allow any of the employees to access the data of any customers
because it was one of the reason that company have to suffer from multiple problems. To avoid
our own data breaches, we must ensure that all possible weaknesses are addressed to maintain
robust security. Also, it is necessary to ensure that secure installation of servers and databases
follow industry specifications due to which other get less opportunity to perform the similar
mistakes.
6
CA-7 Continuous monitoring. NIST 800-53
In current scenario, company is not using the social networking sites to make data
secured. This was one of the incidents where every single user was given the information that
their accounts have been hacked and they must not do further transaction in current situation
because it might create number of problems for them.
Incident status: The Government believes that the data has been recovered and there is
no such evidence to as to data being used for fraud or shared by the hacker.
People who were Notified after the incident: The following people were notified after
the incident:
(a) The Government Agency.
(b) The Stakeholders.
(c) Those individuals whose social security numbers or linked bank account numbers
were compromised were notified by mail. The Company also provides free credit
monitoring and identity protection to those affected.
Lesson Learned: It was one of the case where complete mistake was of company so it is
important for any of the organisation that they must not share the information of company with
outsiders. It is necessary for the company to use secure form of data to share the personal
information of any of the customers who are connected with the company. The main things
which can be learned from whole of this incident is that different sources should be used to
maintain the data of customers because it will keep the chance to secure the data for longer period
of time. Even at a single time multiple data will not be allowed to hack which will enhance the
productivity of a company. Also, customers will get the chance to feel safe to maintain their data
with different organisation for personal benefits (Erfani, 2012). Also, it is important for business
organisation that they must not allow any of the employees to access the data of any customers
because it was one of the reason that company have to suffer from multiple problems. To avoid
our own data breaches, we must ensure that all possible weaknesses are addressed to maintain
robust security. Also, it is necessary to ensure that secure installation of servers and databases
follow industry specifications due to which other get less opportunity to perform the similar
mistakes.
6
TASK 2 Information Security Risks Assessment and Management
2.1 : Information Security Risk Management Justification
The organisation faces uncertainty because of the risks which arises due to various
internal and external factors. The management of such risk is important as without which it is
difficult to define the future objectives of the organisation. In today's time it is important for the
companies to implement risk management which helps them to identify the risks, assess them and
controlling the threats that can affect the business directly. While in baseline approach only
heuristics, simple statistics are used which does not provides the clear picture of the threats that
can affect the business (Jerhotova and Antonini, Honeywell International Inc, 2015). With the
increasing complexity the businesses need to implement an effective risk management system in
the organisation.
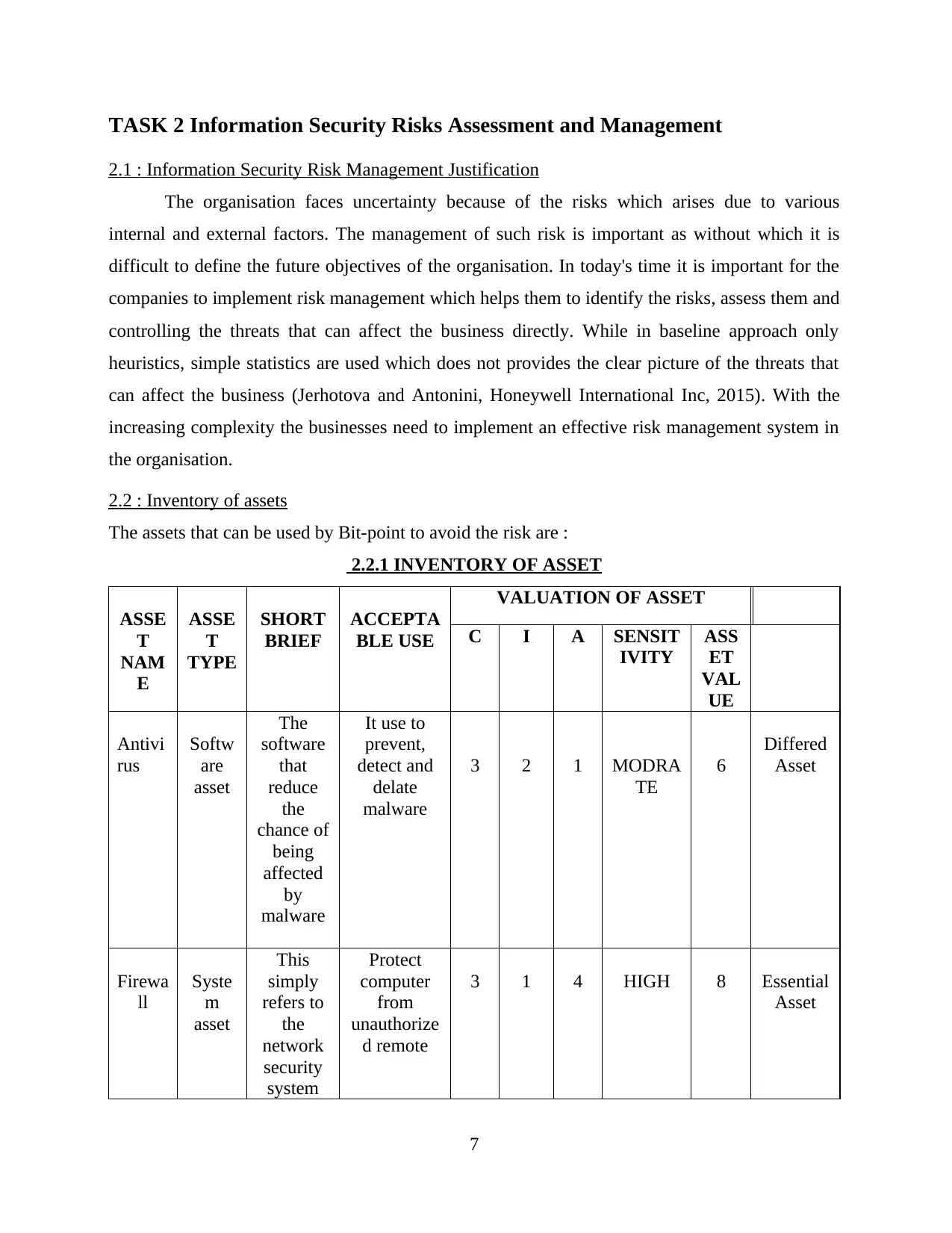
2.2 : Inventory of assets
The assets that can be used by Bit-point to avoid the risk are :
2.2.1 INVENTORY OF ASSET
ASSE
T
NAM
E
ASSE
T
TYPE
SHORT
BRIEF
ACCEPTA
BLE USE
VALUATION OF ASSET
C I A SENSIT
IVITY
ASS
ET
VAL
UE
Antivi
rus
Softw
are
asset
The
software
that
reduce
the
chance of
being
affected
by
malware
It use to
prevent,
detect and
delate
malware
3 2 1 MODRA
TE
6
Differed
Asset
Firewa
ll
Syste
m
asset
This
simply
refers to
the
network
security
system
Protect
computer
from
unauthorize
d remote
3 1 4 HIGH 8 Essential
Asset
7
2.1 : Information Security Risk Management Justification
The organisation faces uncertainty because of the risks which arises due to various
internal and external factors. The management of such risk is important as without which it is
difficult to define the future objectives of the organisation. In today's time it is important for the
companies to implement risk management which helps them to identify the risks, assess them and
controlling the threats that can affect the business directly. While in baseline approach only
heuristics, simple statistics are used which does not provides the clear picture of the threats that
can affect the business (Jerhotova and Antonini, Honeywell International Inc, 2015). With the
increasing complexity the businesses need to implement an effective risk management system in
the organisation.
2.2 : Inventory of assets
The assets that can be used by Bit-point to avoid the risk are :
2.2.1 INVENTORY OF ASSET
ASSE
T
NAM
E
ASSE
T
TYPE
SHORT
BRIEF
ACCEPTA
BLE USE
VALUATION OF ASSET
C I A SENSIT
IVITY
ASS
ET
VAL
UE
Antivi
rus
Softw
are
asset
The
software
that
reduce
the
chance of
being
affected
by
malware
It use to
prevent,
detect and
delate
malware
3 2 1 MODRA
TE
6
Differed
Asset
Firewa
ll
Syste
m
asset
This
simply
refers to
the
network
security
system
Protect
computer
from
unauthorize
d remote
3 1 4 HIGH 8 Essential
Asset
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Websi
te
Syste
m
asset
This is a
platform
where
data is
shared
It is used in
sharing
information
and give
customers
access to
their data
1 3 4 HIGH 8
Essential
Asset
Disk Physic
al
asset
This is a
storage
device
like hard
disk, cd
drive
It is used for
storing
organization
al data
3 3 4 HIGH 10 Essential
Asset
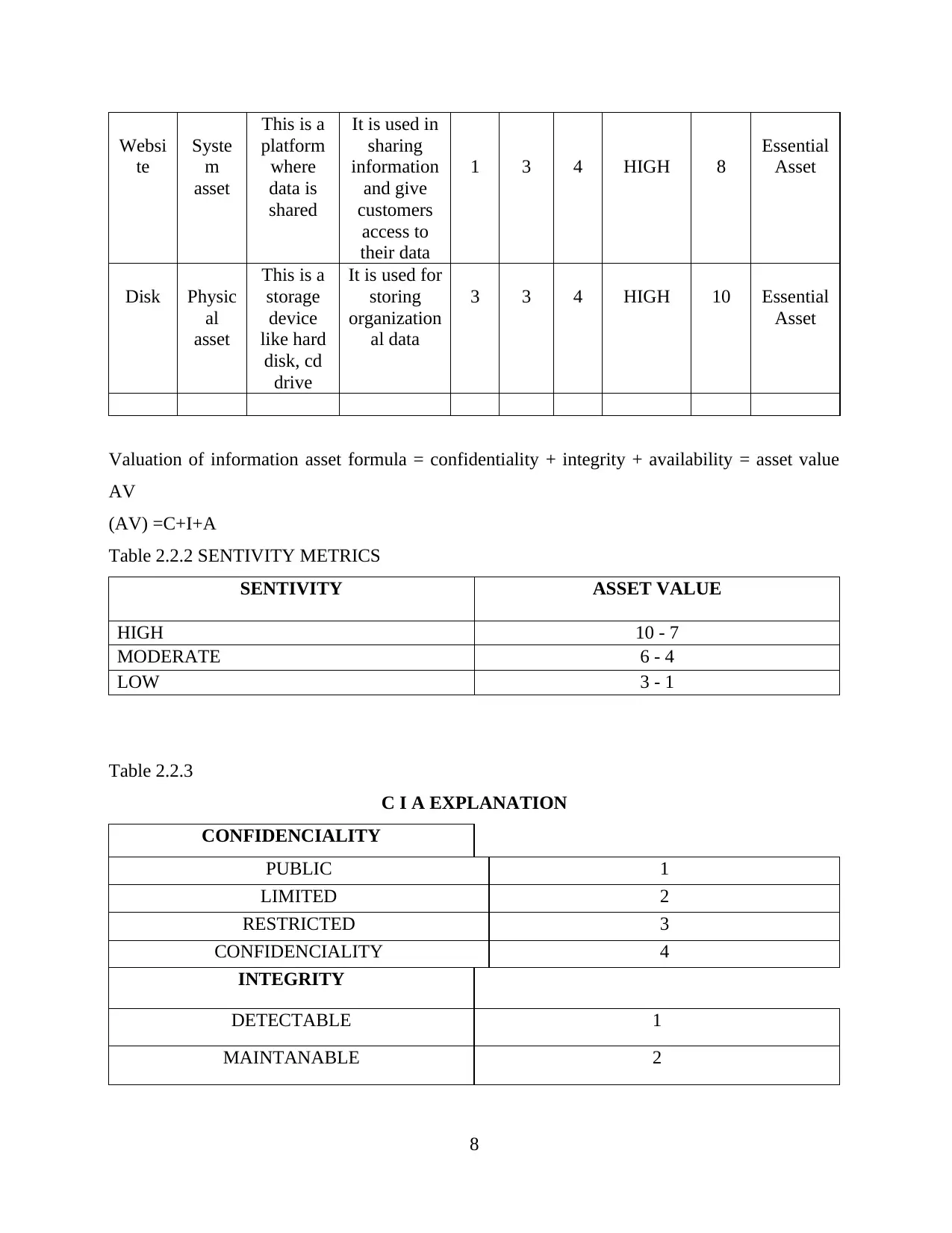
Valuation of information asset formula = confidentiality + integrity + availability = asset value
AV
(AV) =C+I+A
Table 2.2.2 SENTIVITY METRICS
SENTIVITY ASSET VALUE
HIGH 10 - 7
MODERATE 6 - 4
LOW 3 - 1
Table 2.2.3
C I A EXPLANATION
CONFIDENCIALITY
PUBLIC 1
LIMITED 2
RESTRICTED 3
CONFIDENCIALITY 4
INTEGRITY
DETECTABLE 1
MAINTANABLE 2
8
te
Syste
m
asset
This is a
platform
where
data is
shared
It is used in
sharing
information
and give
customers
access to
their data
1 3 4 HIGH 8
Essential
Asset
Disk Physic
al
asset
This is a
storage
device
like hard
disk, cd
drive
It is used for
storing
organization
al data
3 3 4 HIGH 10 Essential
Asset
Valuation of information asset formula = confidentiality + integrity + availability = asset value
AV
(AV) =C+I+A
Table 2.2.2 SENTIVITY METRICS
SENTIVITY ASSET VALUE
HIGH 10 - 7
MODERATE 6 - 4
LOW 3 - 1
Table 2.2.3
C I A EXPLANATION
CONFIDENCIALITY
PUBLIC 1
LIMITED 2
RESTRICTED 3
CONFIDENCIALITY 4
INTEGRITY
DETECTABLE 1
MAINTANABLE 2
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INTAGRATED 3
AVAILABILITY
Data should be available between 72 hours 1
Data should be available between 24 to 72
hours
2
Data should be available between 10 to 24
hours
3
Less than 10 hours 4
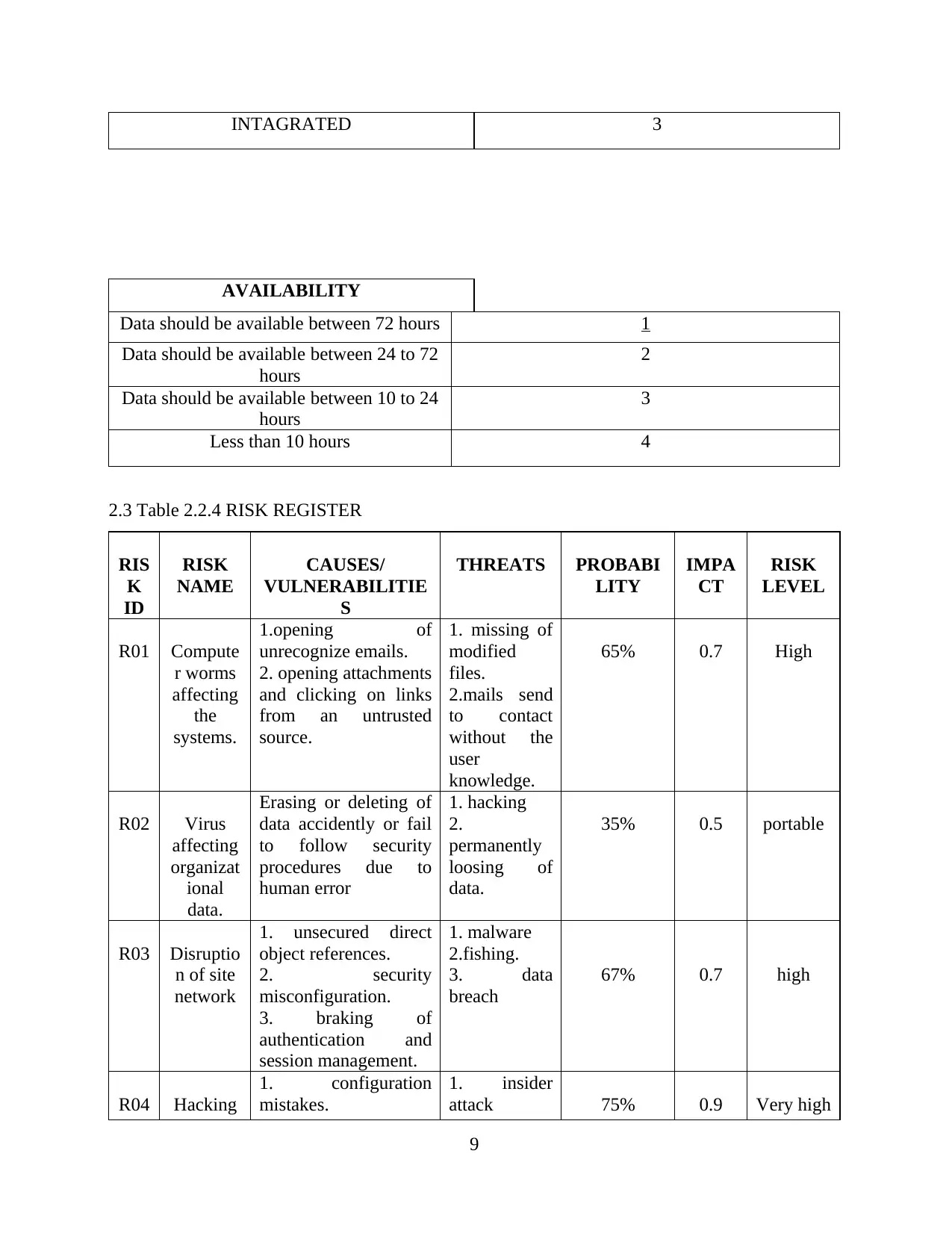
2.3 Table 2.2.4 RISK REGISTER
RIS
K
ID
RISK
NAME
CAUSES/
VULNERABILITIE
S
THREATS PROBABI
LITY
IMPA
CT
RISK
LEVEL
R01 Compute
r worms
affecting
the
systems.
1.opening of
unrecognize emails.
2. opening attachments
and clicking on links
from an untrusted
source.
1. missing of
modified
files.
2.mails send
to contact
without the
user
knowledge.
65% 0.7 High
R02 Virus
affecting
organizat
ional
data.
Erasing or deleting of
data accidently or fail
to follow security
procedures due to
human error
1. hacking
2.
permanently
loosing of
data.
35% 0.5 portable
R03 Disruptio
n of site
network
1. unsecured direct
object references.
2. security
misconfiguration.
3. braking of
authentication and
session management.
1. malware
2.fishing.
3. data
breach
67% 0.7 high
R04 Hacking
1. configuration
mistakes.
1. insider
attack 75% 0.9 Very high
9
AVAILABILITY
Data should be available between 72 hours 1
Data should be available between 24 to 72
hours
2
Data should be available between 10 to 24
hours
3
Less than 10 hours 4
2.3 Table 2.2.4 RISK REGISTER
RIS
K
ID
RISK
NAME
CAUSES/
VULNERABILITIE
S
THREATS PROBABI
LITY
IMPA
CT
RISK
LEVEL
R01 Compute
r worms
affecting
the
systems.
1.opening of
unrecognize emails.
2. opening attachments
and clicking on links
from an untrusted
source.
1. missing of
modified
files.
2.mails send
to contact
without the
user
knowledge.
65% 0.7 High
R02 Virus
affecting
organizat
ional
data.
Erasing or deleting of
data accidently or fail
to follow security
procedures due to
human error
1. hacking
2.
permanently
loosing of
data.
35% 0.5 portable
R03 Disruptio
n of site
network
1. unsecured direct
object references.
2. security
misconfiguration.
3. braking of
authentication and
session management.
1. malware
2.fishing.
3. data
breach
67% 0.7 high
R04 Hacking
1. configuration
mistakes.
1. insider
attack 75% 0.9 Very high
9
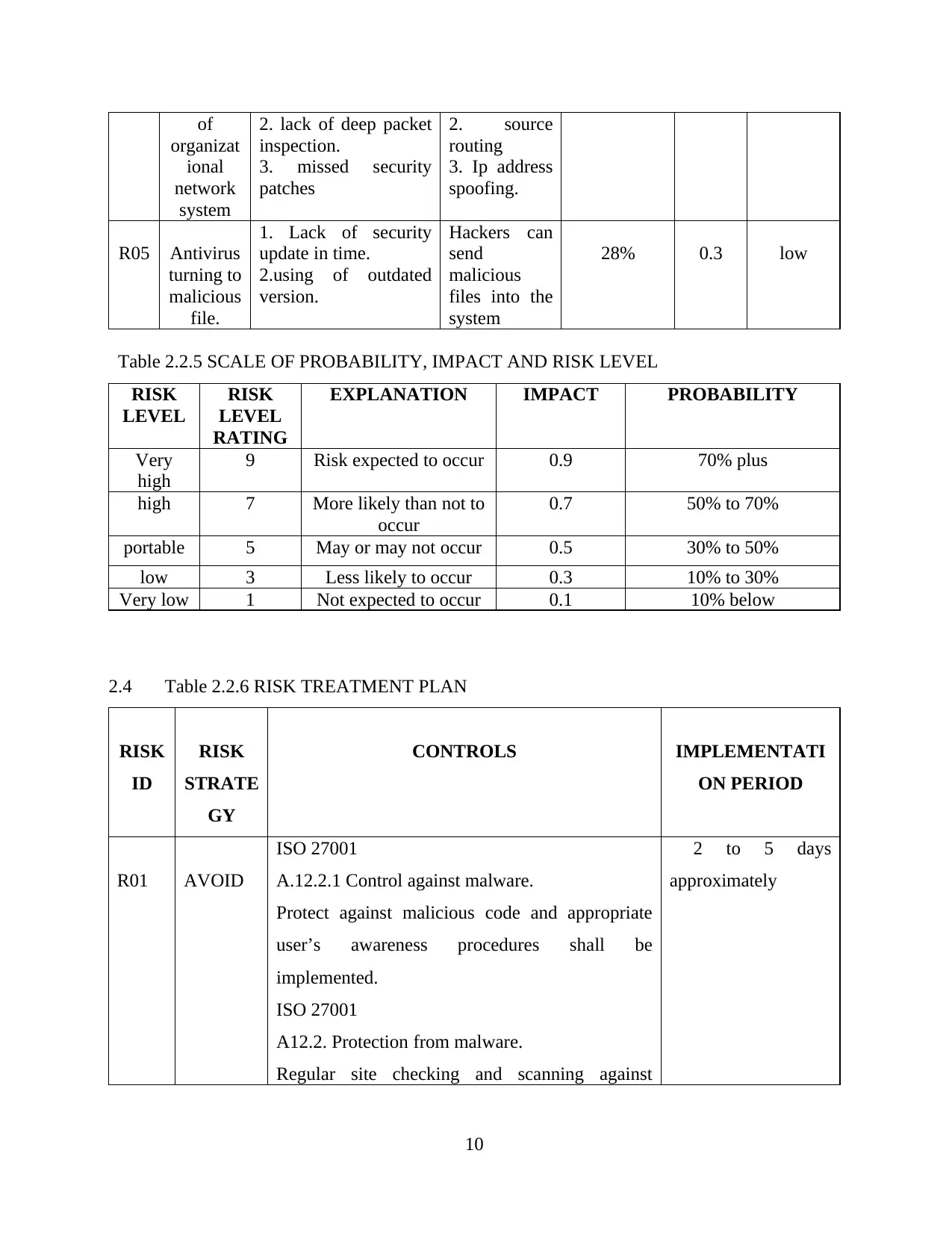
of
organizat
ional
network
system
2. lack of deep packet
inspection.
3. missed security
patches
2. source
routing
3. Ip address
spoofing.
R05 Antivirus
turning to
malicious
file.
1. Lack of security
update in time.
2.using of outdated
version.
Hackers can
send
malicious
files into the
system
28% 0.3 low
Table 2.2.5 SCALE OF PROBABILITY, IMPACT AND RISK LEVEL
RISK
LEVEL
RISK
LEVEL
RATING
EXPLANATION IMPACT PROBABILITY
Very
high
9 Risk expected to occur 0.9 70% plus
high 7 More likely than not to
occur
0.7 50% to 70%
portable 5 May or may not occur 0.5 30% to 50%
low 3 Less likely to occur 0.3 10% to 30%
Very low 1 Not expected to occur 0.1 10% below
2.4 Table 2.2.6 RISK TREATMENT PLAN
RISK
ID
RISK
STRATE
GY
CONTROLS IMPLEMENTATI
ON PERIOD
R01 AVOID
ISO 27001
A.12.2.1 Control against malware.
Protect against malicious code and appropriate
user’s awareness procedures shall be
implemented.
ISO 27001
A12.2. Protection from malware.
Regular site checking and scanning against
2 to 5 days
approximately
10
organizat
ional
network
system
2. lack of deep packet
inspection.
3. missed security
patches
2. source
routing
3. Ip address
spoofing.
R05 Antivirus
turning to
malicious
file.
1. Lack of security
update in time.
2.using of outdated
version.
Hackers can
send
malicious
files into the
system
28% 0.3 low
Table 2.2.5 SCALE OF PROBABILITY, IMPACT AND RISK LEVEL
RISK
LEVEL
RISK
LEVEL
RATING
EXPLANATION IMPACT PROBABILITY
Very
high
9 Risk expected to occur 0.9 70% plus
high 7 More likely than not to
occur
0.7 50% to 70%
portable 5 May or may not occur 0.5 30% to 50%
low 3 Less likely to occur 0.3 10% to 30%
Very low 1 Not expected to occur 0.1 10% below
2.4 Table 2.2.6 RISK TREATMENT PLAN
RISK
ID
RISK
STRATE
GY
CONTROLS IMPLEMENTATI
ON PERIOD
R01 AVOID
ISO 27001
A.12.2.1 Control against malware.
Protect against malicious code and appropriate
user’s awareness procedures shall be
implemented.
ISO 27001
A12.2. Protection from malware.
Regular site checking and scanning against
2 to 5 days
approximately
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





