Cyberpsychology: Analyzing the Catfishing Case Study of Casey Donovan
VerifiedAdded on 2022/02/04
|13
|3168
|42
Case Study
AI Summary
This case study examines the phenomenon of catfishing, using the experience of Casey Donovan as a primary example. The assignment delves into the definition of catfishing, highlighting its deceptive nature and the use of fabricated identities. It explores the psychological aspects exploited by catfishers, including elicitation, preloading, pretexting, and rapport-building, to manipulate victims. The study analyzes the social engineering framework employed, breaking down the preparation, handshaking, and attacking stages. Furthermore, it discusses the impact of catfishing on victims, emphasizing emotional devastation, mental health issues, and the erosion of trust. The case study underscores the importance of understanding the tactics used by catfishers and the potential consequences of online deception, providing insights into the vulnerability of individuals in online relationships. The assignment also references supporting literature to bolster its claims.

1
Running header: CATFISHING
Cyberpsychology: Catfishing
Institution Affiliation
Author Name
Running header: CATFISHING
Cyberpsychology: Catfishing
Institution Affiliation
Author Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
CATFISHING
Introduction
A catfish is a person who uses fake information to get someone online into a trap that
does not represent their real identities. It includes utilizing stolen or edited photos mostly taken
from unwitty persons. Catfish will use this information to develop a more appealing version of
themselves then proceed in one-to-one interactions with other persons who are not aware of the
catfish.
Case study
The leading case study for this work is Casey Donovan. As per the case study, reports
illustrate that relationship with a man with a fake identity for six years. His name was Campbell,
who was a hoax all the past six years. Casey reveals that in her book that her long romance with
the so-called Campell, who claimed to be an IT professional, was fake and did not even exist
even in real life. According to a newspaper that the man had quickly snatched her into the
mystery by Campell through her phone. She was sixteen years old when the relationship starts
just after winning her award named Australian Idol. She adds that as insecure, an overweight
fluffy teenager is taken in very quickly. She adds that I was not too pretty; I was too fat. I used to
say wrong things about myself and made a fool of myself; thus, I did not understand what he saw
in me.
The mobile phone conversation started while she was on tour in 2004 and multiply;
however, the man always made excuses when she asks him to meet in real life. One of the
excuses he claims that he had to visit Queensland to attend his aunt was sick and his car was not
working well; his cousin had passed away. His sister was pregnant. Casey wrote Big, Beautiful,
CATFISHING
Introduction
A catfish is a person who uses fake information to get someone online into a trap that
does not represent their real identities. It includes utilizing stolen or edited photos mostly taken
from unwitty persons. Catfish will use this information to develop a more appealing version of
themselves then proceed in one-to-one interactions with other persons who are not aware of the
catfish.
Case study
The leading case study for this work is Casey Donovan. As per the case study, reports
illustrate that relationship with a man with a fake identity for six years. His name was Campbell,
who was a hoax all the past six years. Casey reveals that in her book that her long romance with
the so-called Campell, who claimed to be an IT professional, was fake and did not even exist
even in real life. According to a newspaper that the man had quickly snatched her into the
mystery by Campell through her phone. She was sixteen years old when the relationship starts
just after winning her award named Australian Idol. She adds that as insecure, an overweight
fluffy teenager is taken in very quickly. She adds that I was not too pretty; I was too fat. I used to
say wrong things about myself and made a fool of myself; thus, I did not understand what he saw
in me.
The mobile phone conversation started while she was on tour in 2004 and multiply;
however, the man always made excuses when she asks him to meet in real life. One of the
excuses he claims that he had to visit Queensland to attend his aunt was sick and his car was not
working well; his cousin had passed away. His sister was pregnant. Casey wrote Big, Beautiful,

3
CATFISHING
and Sexy, just identifying a few of his excuses he always uses. Casey also writes that Campbell
had introduced her to a woman named Olga, who she became very closes friends him. According
to Cross, C. (2019), Campbel insisted that Casey sleep with Olga. All that Casey was that she felt
only dirty and uneasy and used up '' I was too ashamed of the person I am," says Donovan. Casey
later found that after the past six years that the reason for avoidance is that Olga invented him.
The all-false relationship ends when Donovan identifies a SIM card known to be Campbell,
found in Olga's room. After a thorough confrontation, Olga admitted that everything was a lie.
Towards the end, Olga confessed that she was the whole thing and everything was a lie,
and she was Campbell himself. Casey quote 'I finally heard from the devil mouth. 'She
breakdown and cry she felt humiliation she has been stupid all those years. She had spent six
years loving someone who never existed in real life and was only supported by her friend whom
she was deceiving from the first day and pully different strings of lies. She felt heartbroken and
lost herself. She could not heal her emotion tortured. Marissa A. (2019) argued that Casey
mentions that she had not had any boyfriend in her life, and she had been longing for one and
finally met Campell. She had trusted all processes, and she felt she is well-groomed and ready
for everything for love. Casey says that she left no room for any relationship in the Sapphires'
stage production, which she claimed that relationship for the remaining time and total focus in
her career.
Anatomy of attack
Catfishing follows the social engineering framework, which has six phases; according to
the case study, it's clear the catfisher had used all four core stages to execute the attacks. The
catfisher, who is Campbell, and the victim met through the phone. Also, the victim is a famous
CATFISHING
and Sexy, just identifying a few of his excuses he always uses. Casey also writes that Campbell
had introduced her to a woman named Olga, who she became very closes friends him. According
to Cross, C. (2019), Campbel insisted that Casey sleep with Olga. All that Casey was that she felt
only dirty and uneasy and used up '' I was too ashamed of the person I am," says Donovan. Casey
later found that after the past six years that the reason for avoidance is that Olga invented him.
The all-false relationship ends when Donovan identifies a SIM card known to be Campbell,
found in Olga's room. After a thorough confrontation, Olga admitted that everything was a lie.
Towards the end, Olga confessed that she was the whole thing and everything was a lie,
and she was Campbell himself. Casey quote 'I finally heard from the devil mouth. 'She
breakdown and cry she felt humiliation she has been stupid all those years. She had spent six
years loving someone who never existed in real life and was only supported by her friend whom
she was deceiving from the first day and pully different strings of lies. She felt heartbroken and
lost herself. She could not heal her emotion tortured. Marissa A. (2019) argued that Casey
mentions that she had not had any boyfriend in her life, and she had been longing for one and
finally met Campell. She had trusted all processes, and she felt she is well-groomed and ready
for everything for love. Casey says that she left no room for any relationship in the Sapphires'
stage production, which she claimed that relationship for the remaining time and total focus in
her career.
Anatomy of attack
Catfishing follows the social engineering framework, which has six phases; according to
the case study, it's clear the catfisher had used all four core stages to execute the attacks. The
catfisher, who is Campbell, and the victim met through the phone. Also, the victim is a famous
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
CATFISHING
singer, which implies that most er information is available online on social media platforms.
First, the main focus is the psychological aspects the catfishers consider to deceive people; they
use different techniques most to achieve their motives. The psychological elements the catfisher
had used over the victim.
Elicitation implies bringing out or reach a conclusion the truth reali8ty logically. In a case
study, elicitation works well for many reasons; most people are always very polite to strangers
by nature. It is what happened to Casey; she fails to trap for being nice to the catfisher for the
first time over the phone. Reichart Smith, L. (2017) argued that professionals always want to be
more professional and appear very intelligent; thus, Casy as a singer, could not easily escape the
trap. Also, most people tend to respond appropriately to the people they seem to care for them,
which is a trap for Casey since the stranger appears to love her and she was too fat and fluffy,
which made him accept the money quickly.
The next aspect used is preloading, which is to plant ideas or different thoughts to people
in a pronounced way. In our case study, Campbell uses some of the right ideas to win Casey's
heart. Since he was her friend living together next door, he had all the information regarding
Casey. Thus, ideas were accepted readily; one of the social engineering aims to initiate the
attack. In the case study, there is a development of the rapport during Conversation by agreement
upon the set principles.
Another physiological concept is the pretexting, which implies telling all the background
stories such as lifestyle, dressing code, personalities, and attitudes in making up the character for
the social engineers it refers as the social engineering audit. Since pretexting is termed as
creating an inverted scenario for persuading target victims for the release information. In the case
CATFISHING
singer, which implies that most er information is available online on social media platforms.
First, the main focus is the psychological aspects the catfishers consider to deceive people; they
use different techniques most to achieve their motives. The psychological elements the catfisher
had used over the victim.
Elicitation implies bringing out or reach a conclusion the truth reali8ty logically. In a case
study, elicitation works well for many reasons; most people are always very polite to strangers
by nature. It is what happened to Casey; she fails to trap for being nice to the catfisher for the
first time over the phone. Reichart Smith, L. (2017) argued that professionals always want to be
more professional and appear very intelligent; thus, Casy as a singer, could not easily escape the
trap. Also, most people tend to respond appropriately to the people they seem to care for them,
which is a trap for Casey since the stranger appears to love her and she was too fat and fluffy,
which made him accept the money quickly.
The next aspect used is preloading, which is to plant ideas or different thoughts to people
in a pronounced way. In our case study, Campbell uses some of the right ideas to win Casey's
heart. Since he was her friend living together next door, he had all the information regarding
Casey. Thus, ideas were accepted readily; one of the social engineering aims to initiate the
attack. In the case study, there is a development of the rapport during Conversation by agreement
upon the set principles.
Another physiological concept is the pretexting, which implies telling all the background
stories such as lifestyle, dressing code, personalities, and attitudes in making up the character for
the social engineers it refers as the social engineering audit. Since pretexting is termed as
creating an inverted scenario for persuading target victims for the release information. In the case
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
CATFISHING
study is clear that Cambel has used this aspect by lying about his profession as IT experts, and
Casey fall into the trap of believing it.
Also, building rapport is one of the aspects used by the catfisher to gain trust. It’s one of
the mind tricks being used by being much friendly and with many empathy approaches to earn
trust from other people. It includes body gestures, voices, and playing with ordinary senses. It
plays a very significant role in catfishing. A microexpression has happiness, sadness, surprise,
disgust, and anger, which social engineers utilize to set up the circumstances. It implies gaining
all the control over the victim before carrying out social engineering attack. According to
Lamphere, R.D. (2019 ), catfisher has played with Casey's feelings by making an excuse of not
meeting with her, which has some emotions. For example, he was attending the sick aunt to help
gain sympathy from the victim. And Casey falls for the same physiological aspects.
Lastly, it's the influencing aspects that imply acting to get someone else or need to do,
react, think, or even believe in a way you want them to become since these aspects use the
persuasion, which develops a rapport which is the crucial act. Trying to get empathy with other
conditions is an efficient means to trust and gain confidence. Casey being a singer, fall easily
into this aspect since she wants to be known globally requires promotions.
CATFISHING
study is clear that Cambel has used this aspect by lying about his profession as IT experts, and
Casey fall into the trap of believing it.
Also, building rapport is one of the aspects used by the catfisher to gain trust. It’s one of
the mind tricks being used by being much friendly and with many empathy approaches to earn
trust from other people. It includes body gestures, voices, and playing with ordinary senses. It
plays a very significant role in catfishing. A microexpression has happiness, sadness, surprise,
disgust, and anger, which social engineers utilize to set up the circumstances. It implies gaining
all the control over the victim before carrying out social engineering attack. According to
Lamphere, R.D. (2019 ), catfisher has played with Casey's feelings by making an excuse of not
meeting with her, which has some emotions. For example, he was attending the sick aunt to help
gain sympathy from the victim. And Casey falls for the same physiological aspects.
Lastly, it's the influencing aspects that imply acting to get someone else or need to do,
react, think, or even believe in a way you want them to become since these aspects use the
persuasion, which develops a rapport which is the crucial act. Trying to get empathy with other
conditions is an efficient means to trust and gain confidence. Casey being a singer, fall easily
into this aspect since she wants to be known globally requires promotions.
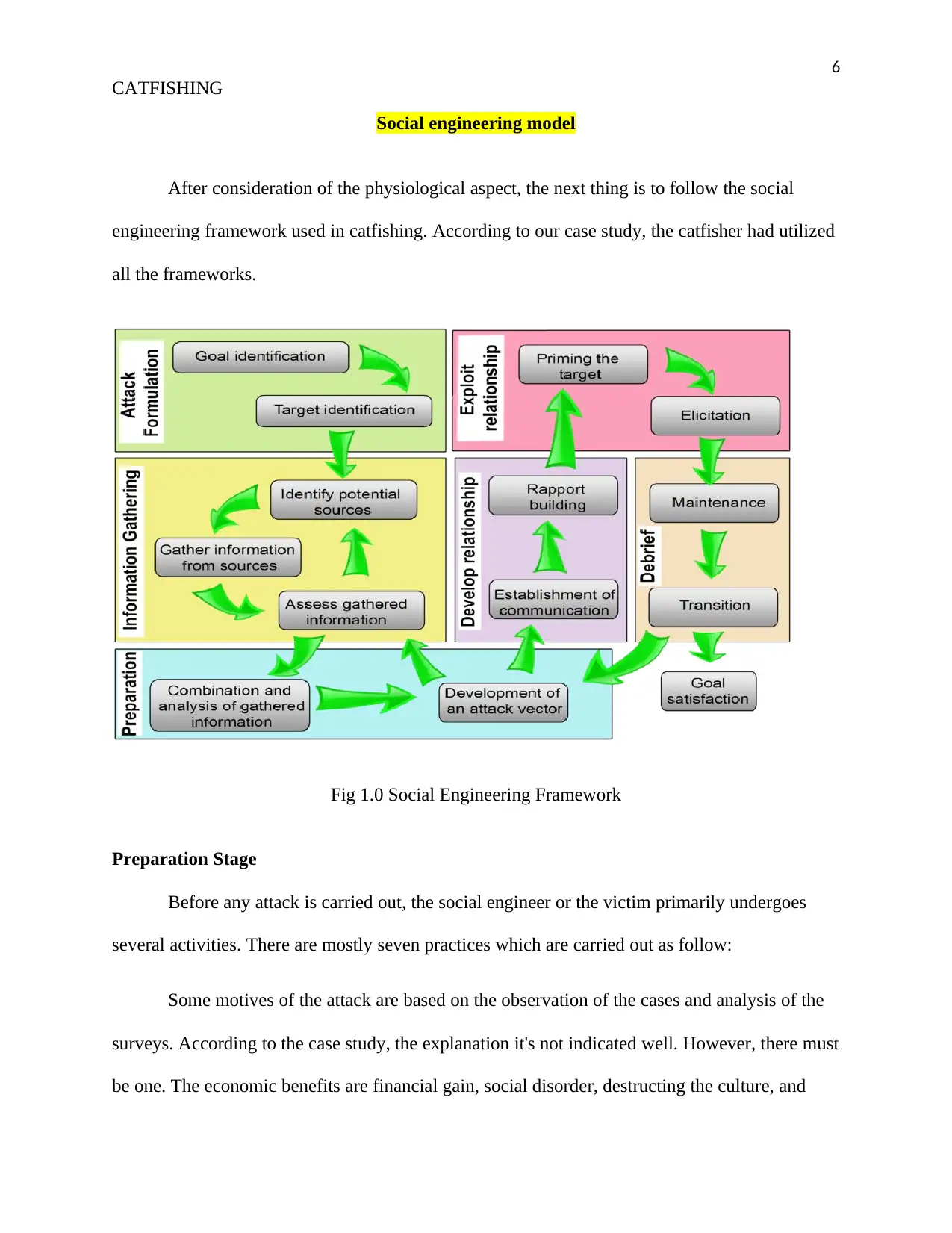
6
CATFISHING
Social engineering model
After consideration of the physiological aspect, the next thing is to follow the social
engineering framework used in catfishing. According to our case study, the catfisher had utilized
all the frameworks.
Fig 1.0 Social Engineering Framework
Preparation Stage
Before any attack is carried out, the social engineer or the victim primarily undergoes
several activities. There are mostly seven practices which are carried out as follow:
Some motives of the attack are based on the observation of the cases and analysis of the
surveys. According to the case study, the explanation it's not indicated well. However, there must
be one. The economic benefits are financial gain, social disorder, destructing the culture, and
CATFISHING
Social engineering model
After consideration of the physiological aspect, the next thing is to follow the social
engineering framework used in catfishing. According to our case study, the catfisher had utilized
all the frameworks.
Fig 1.0 Social Engineering Framework
Preparation Stage
Before any attack is carried out, the social engineer or the victim primarily undergoes
several activities. There are mostly seven practices which are carried out as follow:
Some motives of the attack are based on the observation of the cases and analysis of the
surveys. According to the case study, the explanation it's not indicated well. However, there must
be one. The economic benefits are financial gain, social disorder, destructing the culture, and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
CATFISHING
image spoiling. According to the case study, there must be a motive for the action, which can be
financial gain since the catfisher was the victim's friend and knew everything about the victim.
Target selection implies that in each attack, there will be specific groups or individuals
that the social engineers target. It's based on the characteristic of the victims; thus, it's simple to
categorize the type of target. For example, the target is the celebrities since the target is the
singer who is popular in Australia.
Environment analysis is the next step taken by the catfisher since the target does stay in
the closed environment that might have a security perimeter intact. Hence, the social engineers
conduct particular observation and analysis to conduct the study and the attributes and elements.
As per the Casey incident, the catfisher might have check all how he could lead the attack. That's
the reason he chooses catfishing, which I managed through the phone.
Perimeter scanning -most of the electronic which are based system the IS and technology,
are created tangible and intangible assets required to make all the efforts successful.
According to the initial steps, the following information requirements analysis includes
environmental research and perimeter scanning, which impacts a list of needs regarding what
type of data assets is required to make the efforts succeed is defined. Lauckner, C., (2019) said
that information is essential to social engineers since the main target by the catfishers is the
victim. One to conduct the process, he or she should get the technical and non-technical
requirements. As per the case study, it's unclear if the catfisher had completed this stage or not
since no much technical activity involved.
CATFISHING
image spoiling. According to the case study, there must be a motive for the action, which can be
financial gain since the catfisher was the victim's friend and knew everything about the victim.
Target selection implies that in each attack, there will be specific groups or individuals
that the social engineers target. It's based on the characteristic of the victims; thus, it's simple to
categorize the type of target. For example, the target is the celebrities since the target is the
singer who is popular in Australia.
Environment analysis is the next step taken by the catfisher since the target does stay in
the closed environment that might have a security perimeter intact. Hence, the social engineers
conduct particular observation and analysis to conduct the study and the attributes and elements.
As per the Casey incident, the catfisher might have check all how he could lead the attack. That's
the reason he chooses catfishing, which I managed through the phone.
Perimeter scanning -most of the electronic which are based system the IS and technology,
are created tangible and intangible assets required to make all the efforts successful.
According to the initial steps, the following information requirements analysis includes
environmental research and perimeter scanning, which impacts a list of needs regarding what
type of data assets is required to make the efforts succeed is defined. Lauckner, C., (2019) said
that information is essential to social engineers since the main target by the catfishers is the
victim. One to conduct the process, he or she should get the technical and non-technical
requirements. As per the case study, it's unclear if the catfisher had completed this stage or not
since no much technical activity involved.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
CATFISHING
Assets Owner Determination is the other stage that requires to be addressed by the
catfisher. It includes understanding literacy with the related information and technology. It's
helpful for the catfisher in dividing the literate.
The last phase is scenario development which the last phase for the social engineering
frameworks. It comes after defining the target and the victim.
Handshaking Stage
This the second stage in which the first contact is established between the catfisher and
the target victims. There are at least eight stages followed in this phase. However, as per our case
study, the catfisher had used the relationship initiation not to develop suspiciousness with the
victim. He made the first call to appear in just normal condition. It seems the logical relationship
between the catfisher and victim needs to be well developed. In our case study, the catfisher talks
with Casey as her fan, and he requires to know each other, which was a trap, and the victim falls
into it.
Attacking Stage
This the last stage in which the catfisher deploys the attack, this stage consist of four
phases. According to the case study, it's clear the catfisher had used the first stage, the comfort
zone establishment, that the fits thing to be accomplished by the catfisher feel that they have
succeeded in building victim trust in their comfort zone. For example, in our case study, the
catfisher won Casey's trust by buying loving and felt it since she had not been with any boyfriend
before.
Impact Analysis
CATFISHING
Assets Owner Determination is the other stage that requires to be addressed by the
catfisher. It includes understanding literacy with the related information and technology. It's
helpful for the catfisher in dividing the literate.
The last phase is scenario development which the last phase for the social engineering
frameworks. It comes after defining the target and the victim.
Handshaking Stage
This the second stage in which the first contact is established between the catfisher and
the target victims. There are at least eight stages followed in this phase. However, as per our case
study, the catfisher had used the relationship initiation not to develop suspiciousness with the
victim. He made the first call to appear in just normal condition. It seems the logical relationship
between the catfisher and victim needs to be well developed. In our case study, the catfisher talks
with Casey as her fan, and he requires to know each other, which was a trap, and the victim falls
into it.
Attacking Stage
This the last stage in which the catfisher deploys the attack, this stage consist of four
phases. According to the case study, it's clear the catfisher had used the first stage, the comfort
zone establishment, that the fits thing to be accomplished by the catfisher feel that they have
succeeded in building victim trust in their comfort zone. For example, in our case study, the
catfisher won Casey's trust by buying loving and felt it since she had not been with any boyfriend
before.
Impact Analysis

9
CATFISHING
According to the analysis catfishing case scenario, there are some effects. It’s clear when
someone catfished; it does generally damage mental health, as seen in Casey. When the emotions
are invested in friendship or romantic relationship with catfisher, it results in mental health. Our
case study involved a romantic relationship in which Casey, the victim, suffered exceptionally
mentally ill. Amedie, J (2015) argued that after the catfishing, victims could not trust anyone due
to a bad experience. She wants not able also to be in a relationship.
Another impact is the emotional devastation to someone who has catfished. For our case
its Casey went through, she faces a lot of embarrassment and a lot of regrets for believing and
falling for the complete non-existent individual. Also, financial loss and mental illness, which
includes anxiety and depression, can result from catfishing.
The victim feels paranoid in life; mostly in our case study, they had romance relationship.
Hence, they had sent explicit images such as nudes with catfisher Campbell. Casey felt her trust
has been completely betrayed and feels paranoid of the risk of being exposed publicly in any
means such as porn. It can contribute to long terms challenges such as disorder, anxiety, and
depression.
Also, another impact we can see that in the case study Casey the victim lost self-esteem,
and it can lead later to one committing suicide. One will lose his self-esteem in everything and
start living in their world of thoughts; they find themselves very low. For example, the victim in
our case study can easily break down when she had anything about relationships. She is not
ready to be in love again, only prepared to focus on her career.
Recommended Approach and Conclusion
CATFISHING
According to the analysis catfishing case scenario, there are some effects. It’s clear when
someone catfished; it does generally damage mental health, as seen in Casey. When the emotions
are invested in friendship or romantic relationship with catfisher, it results in mental health. Our
case study involved a romantic relationship in which Casey, the victim, suffered exceptionally
mentally ill. Amedie, J (2015) argued that after the catfishing, victims could not trust anyone due
to a bad experience. She wants not able also to be in a relationship.
Another impact is the emotional devastation to someone who has catfished. For our case
its Casey went through, she faces a lot of embarrassment and a lot of regrets for believing and
falling for the complete non-existent individual. Also, financial loss and mental illness, which
includes anxiety and depression, can result from catfishing.
The victim feels paranoid in life; mostly in our case study, they had romance relationship.
Hence, they had sent explicit images such as nudes with catfisher Campbell. Casey felt her trust
has been completely betrayed and feels paranoid of the risk of being exposed publicly in any
means such as porn. It can contribute to long terms challenges such as disorder, anxiety, and
depression.
Also, another impact we can see that in the case study Casey the victim lost self-esteem,
and it can lead later to one committing suicide. One will lose his self-esteem in everything and
start living in their world of thoughts; they find themselves very low. For example, the victim in
our case study can easily break down when she had anything about relationships. She is not
ready to be in love again, only prepared to focus on her career.
Recommended Approach and Conclusion
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
CATFISHING
According to the case study of Casey being a victim of catfisher, we have learned of
some impacts which one experiences. Some approaches are used to protect one solve from the
risk identified above as a result of catfishing.
Always be suspicious if a person contacts you out of the blue.
Always think of the online Conversation logically like in a real-life situation. For example, the
only strangers who can come to your house are the salespersons who sell something or market.
Online also is not different; suppose someone contacts you from nowhere he or she has a motive.
Mostly are the people trying to deceive, such as fake friends. Always one is required to be alert
from an unknown call, text, or email, among others. Thus, will help prevent some of the risk
such loss of self-esteem embarrassment among others.
Adhere to higher quality dating sites.
This approach is applicable for our scenario since Casey catfished due to romantic
relationships. Thus, in any case, one needs any relationship to adhere to quality dating sites.
Since typically, quality sites charge their members to subscribe. It helps remove the online
scammers since they provide some information for the registration and payment process and can
tie them in case of any scamming.
Stay in control
Please do not allow anyone to tell you how to contact them, send money, or provide
personal credentials. One should control the situation. Reichart Smith, L., (2017) argued that it
depends on you the way you wish to chat to them either skype to talk no one should take control
of you. It will help you only meet with appropriate people and protect yourself from being
catfished.
CATFISHING
According to the case study of Casey being a victim of catfisher, we have learned of
some impacts which one experiences. Some approaches are used to protect one solve from the
risk identified above as a result of catfishing.
Always be suspicious if a person contacts you out of the blue.
Always think of the online Conversation logically like in a real-life situation. For example, the
only strangers who can come to your house are the salespersons who sell something or market.
Online also is not different; suppose someone contacts you from nowhere he or she has a motive.
Mostly are the people trying to deceive, such as fake friends. Always one is required to be alert
from an unknown call, text, or email, among others. Thus, will help prevent some of the risk
such loss of self-esteem embarrassment among others.
Adhere to higher quality dating sites.
This approach is applicable for our scenario since Casey catfished due to romantic
relationships. Thus, in any case, one needs any relationship to adhere to quality dating sites.
Since typically, quality sites charge their members to subscribe. It helps remove the online
scammers since they provide some information for the registration and payment process and can
tie them in case of any scamming.
Stay in control
Please do not allow anyone to tell you how to contact them, send money, or provide
personal credentials. One should control the situation. Reichart Smith, L., (2017) argued that it
depends on you the way you wish to chat to them either skype to talk no one should take control
of you. It will help you only meet with appropriate people and protect yourself from being
catfished.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
CATFISHING
Ask for proof of who they are are
It's continually OK to ask someone for proof of identity of whom they are really. Suppose
you have been in communication with someone for some time; it's essential to ask for
identification see in person. It will help prevent catfishing, which impacts immensely to
someone's mental life, as seen in the case study.
In conclusion, catfishing is very extremely dangerous to the social life of an individual.
One should always be keen on the ways to identify catfishing. Take time before attending any
call or message on social media platforms or any place. Always take social media as real life.
Also, they should consider critical approaches as outline above, including staying in control.
CATFISHING
Ask for proof of who they are are
It's continually OK to ask someone for proof of identity of whom they are really. Suppose
you have been in communication with someone for some time; it's essential to ask for
identification see in person. It will help prevent catfishing, which impacts immensely to
someone's mental life, as seen in the case study.
In conclusion, catfishing is very extremely dangerous to the social life of an individual.
One should always be keen on the ways to identify catfishing. Take time before attending any
call or message on social media platforms or any place. Always take social media as real life.
Also, they should consider critical approaches as outline above, including staying in control.

12
CATFISHING
Reference
Amedee, J., 2015. The impact of social media on society.
Cross, C., 2019. From catfish to romance fraud, how to avoid getting caught in any online scam.
The Conversation, pp.1-4.
Lamphere, R.D. and Lucas, K.T., 2019. Online Romance in the 21st Century: Deceptive Online
Dating, Catfishing, Romance Scams, and “Mail Order” Marriages. In Handbook of
Research on Deception, Fake News, and Misinformation Online (pp. 475-488). IGI
Global.
Lauckner, C., Truszczynski, N., Lambert, D., Kottamasu, V., Meherally, S., Schipani-
McLaughlin, A.M., Taylor, E., and Hansen, N., 2019. "Catfishing," cyberbullying, and
coercion: An exploration of the risks associated with dating app use among rural sexual
minority males. Journal of Gay & Lesbian Mental Health, 23(3), pp.289-306.
Marissa A., Morgan Lancaster, M. L. Parker, and Kelly Campbell. "Adult attachment and online
dating deception: A theory modernized." Sexual and relationship Therapy 35, no. 2
(2020): 227-243.
Reichart Smith, L., Smith, K.D. and Blazka, M., 2017. Follow Me, What's the Harm:
Considerations of Catfishing and Utilizing Fake Online Personas on social media. J.
Legal Aspects Sport, 27, p.32.
Reichart Smith, L., Smith, K.D. and Blazka, M., 2017. Follow Me, What's the Harm:
Considerations of Catfishing and Utilizing Fake Online Personas on social media. J.
Legal Aspects Sport, 27, p.32.
CATFISHING
Reference
Amedee, J., 2015. The impact of social media on society.
Cross, C., 2019. From catfish to romance fraud, how to avoid getting caught in any online scam.
The Conversation, pp.1-4.
Lamphere, R.D. and Lucas, K.T., 2019. Online Romance in the 21st Century: Deceptive Online
Dating, Catfishing, Romance Scams, and “Mail Order” Marriages. In Handbook of
Research on Deception, Fake News, and Misinformation Online (pp. 475-488). IGI
Global.
Lauckner, C., Truszczynski, N., Lambert, D., Kottamasu, V., Meherally, S., Schipani-
McLaughlin, A.M., Taylor, E., and Hansen, N., 2019. "Catfishing," cyberbullying, and
coercion: An exploration of the risks associated with dating app use among rural sexual
minority males. Journal of Gay & Lesbian Mental Health, 23(3), pp.289-306.
Marissa A., Morgan Lancaster, M. L. Parker, and Kelly Campbell. "Adult attachment and online
dating deception: A theory modernized." Sexual and relationship Therapy 35, no. 2
(2020): 227-243.
Reichart Smith, L., Smith, K.D. and Blazka, M., 2017. Follow Me, What's the Harm:
Considerations of Catfishing and Utilizing Fake Online Personas on social media. J.
Legal Aspects Sport, 27, p.32.
Reichart Smith, L., Smith, K.D. and Blazka, M., 2017. Follow Me, What's the Harm:
Considerations of Catfishing and Utilizing Fake Online Personas on social media. J.
Legal Aspects Sport, 27, p.32.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





