CCNA Network Design Project: Intel's Global Network Infrastructure
VerifiedAdded on 2022/08/18
|15
|3242
|10
Project
AI Summary
This report provides a comprehensive overview of Intel's network infrastructure, focusing on its global communication capabilities. It begins with an executive summary and a business description of Intel, emphasizing its communication strategies using software-defined networks and Network Function Virtualization. The report then presents three network design diagrams illustrating global network coverage, satellite communication, and a logical office network design. It delves into IP address classification, providing an IP table with subnet allocations for key Intel locations. The report also discusses VLAN implementation, routing device configuration, and the utilization of various network components and routing protocols, including OSPF. The report concludes with best practices and concluding notes, offering insights into Intel's network security and design considerations. The project includes diagrams and references to support the analysis and design of the network.

Running head: CCNA NETWORKS AND SECURITY
CCNA Networks and Security
Name of the Student
Name of the University
Author Note
CCNA Networks and Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CCNA NETWORKS AND SECURITY
Executive Summary
Network infrastructure is an essential part in facilitating communications for any large
corporation. A secure site to site network implementation helps large companies to stay
secure from network security risks like threats posed by hackers, malware, phishing as well
as vulnerabilities that exist in network components and the applications that are being used by
the various systems of the company. The report presents how network communications are
conducted by Intel inside and outside the company. This is to be elaborated with the help of
three network designs followed by IP address classification for five of the fourteen countries
where Intel is operating, though the major network chosen supports address spaces for
networks of all countries. Next the report is to mention how the company uses VLANs to
partition the network segments of different departments of offices. After this the report is to
talk about the configuration of the routing devices and then explain how various network
components and routing protocols are to be used. Thereafter the report ends with concluding
notes.
Executive Summary
Network infrastructure is an essential part in facilitating communications for any large
corporation. A secure site to site network implementation helps large companies to stay
secure from network security risks like threats posed by hackers, malware, phishing as well
as vulnerabilities that exist in network components and the applications that are being used by
the various systems of the company. The report presents how network communications are
conducted by Intel inside and outside the company. This is to be elaborated with the help of
three network designs followed by IP address classification for five of the fourteen countries
where Intel is operating, though the major network chosen supports address spaces for
networks of all countries. Next the report is to mention how the company uses VLANs to
partition the network segments of different departments of offices. After this the report is to
talk about the configuration of the routing devices and then explain how various network
components and routing protocols are to be used. Thereafter the report ends with concluding
notes.

2CCNA NETWORKS AND SECURITY
Table of Contents
Introduction................................................................................................................................3
Business Description..................................................................................................................4
Communication..........................................................................................................................4
Network Design.........................................................................................................................5
Global Network Coverage......................................................................................................5
Satellite Communication of WAN Interconnects..................................................................6
Logical Network Design of Specific Office...........................................................................7
IP Subnet Classification.............................................................................................................8
IP Table..................................................................................................................................8
VLAN.......................................................................................................................................10
Routing and Configuration.......................................................................................................11
Components and Routing Protocols.........................................................................................11
Best Practices...........................................................................................................................11
Conclusion................................................................................................................................12
References................................................................................................................................13
Table of Contents
Introduction................................................................................................................................3
Business Description..................................................................................................................4
Communication..........................................................................................................................4
Network Design.........................................................................................................................5
Global Network Coverage......................................................................................................5
Satellite Communication of WAN Interconnects..................................................................6
Logical Network Design of Specific Office...........................................................................7
IP Subnet Classification.............................................................................................................8
IP Table..................................................................................................................................8
VLAN.......................................................................................................................................10
Routing and Configuration.......................................................................................................11
Components and Routing Protocols.........................................................................................11
Best Practices...........................................................................................................................11
Conclusion................................................................................................................................12
References................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CCNA NETWORKS AND SECURITY
Introduction
The following report tries to show how essential Network infrastructure can be for
facilitating communications in large corporations. The report begins by providing a brief
description of the company chosen, which is Intel. Then it thoroughly discusses how network
communications are achieved by Intel both inside and outside the company. To do this the
report uses three network design diagrams drawn with the help of Microsoft Visio 2013 and
explains the networking aspects demonstrated by each of these diagrams. After that the IP
address classification is provided for five of the fourteen countries where Intel happens to
operate. The major network chosen supports address spaces for networks of all countries
where Intel has offices present. Then the report mentions how the company uses VLANs for
partitioning the network segments of different departments of offices. Next the report talks
about the configuration of the routing devices and then explain how various network
components and routing protocols are to be used and specifies the best practices. After that
the report comes to an end with concluding notes.
Introduction
The following report tries to show how essential Network infrastructure can be for
facilitating communications in large corporations. The report begins by providing a brief
description of the company chosen, which is Intel. Then it thoroughly discusses how network
communications are achieved by Intel both inside and outside the company. To do this the
report uses three network design diagrams drawn with the help of Microsoft Visio 2013 and
explains the networking aspects demonstrated by each of these diagrams. After that the IP
address classification is provided for five of the fourteen countries where Intel happens to
operate. The major network chosen supports address spaces for networks of all countries
where Intel has offices present. Then the report mentions how the company uses VLANs for
partitioning the network segments of different departments of offices. Next the report talks
about the configuration of the routing devices and then explain how various network
components and routing protocols are to be used and specifies the best practices. After that
the report comes to an end with concluding notes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CCNA NETWORKS AND SECURITY
Business Description
The organization in consideration happens to be Intel which happens to be a
multinational company based in Santa Clara of California in the Silicon Valley region of the
nation, USA. They are among the top 50 of the Fortune 500 list of US companies on the basis
of revenue generation and employs more than 110,200 employees globally (Lieder et al.,
2019). It is the world’s largest, as also the most valuable chip maker and very well known for
their revenue based on semiconductor manufacturing and design.
Communication
Intel Corp. ensures that their network enables a wide range of possibilities when it
comes to conducting communications in different plants and offices from one department to
another as also between offices of multiple locations (Wang et al., 2019). Intel is ensuring
that their networks are capable enough to provide these requirements through an intelligent
network infrastructure which is both programmable and software-defined (SDN) and can be
scaled accordingly (Cui, Yu & Yan, 2016). This helps a large company like Intel to transform
the mode of communications through their network from the data centres to end devices.
A software defined network helps the company make their network programmable
such that the control plane can be separated from the data plane (Shang et al., 2017). Network
Function Virtualization or NFV enables specific functions like firewall features equipped
within specific network components (Tootoonchian et al., 2019). NFV also facilitates the use
of virtual software applications through the server based on the x86 standard (Bo et al.,
2019). These advanced networking features help Intel provide the network administrators
with centralized management and dynamic provisioning of the overall network.
Business Description
The organization in consideration happens to be Intel which happens to be a
multinational company based in Santa Clara of California in the Silicon Valley region of the
nation, USA. They are among the top 50 of the Fortune 500 list of US companies on the basis
of revenue generation and employs more than 110,200 employees globally (Lieder et al.,
2019). It is the world’s largest, as also the most valuable chip maker and very well known for
their revenue based on semiconductor manufacturing and design.
Communication
Intel Corp. ensures that their network enables a wide range of possibilities when it
comes to conducting communications in different plants and offices from one department to
another as also between offices of multiple locations (Wang et al., 2019). Intel is ensuring
that their networks are capable enough to provide these requirements through an intelligent
network infrastructure which is both programmable and software-defined (SDN) and can be
scaled accordingly (Cui, Yu & Yan, 2016). This helps a large company like Intel to transform
the mode of communications through their network from the data centres to end devices.
A software defined network helps the company make their network programmable
such that the control plane can be separated from the data plane (Shang et al., 2017). Network
Function Virtualization or NFV enables specific functions like firewall features equipped
within specific network components (Tootoonchian et al., 2019). NFV also facilitates the use
of virtual software applications through the server based on the x86 standard (Bo et al.,
2019). These advanced networking features help Intel provide the network administrators
with centralized management and dynamic provisioning of the overall network.
5CCNA NETWORKS AND SECURITY
The various data centres present across the globe as well as the server farms in
various plants and offices provide Intel with enough storage capacity and compute capability
to stream a series of high resolution videos and podcasts through their network to different
locations (Titus, 2019). The videos and content are created in the secure environment of the
company’s network and is made available to clients and customers over the Internet through
the web servers. Similarly, the company ensures secure meetings between various
management levels in different departments through the internal network.
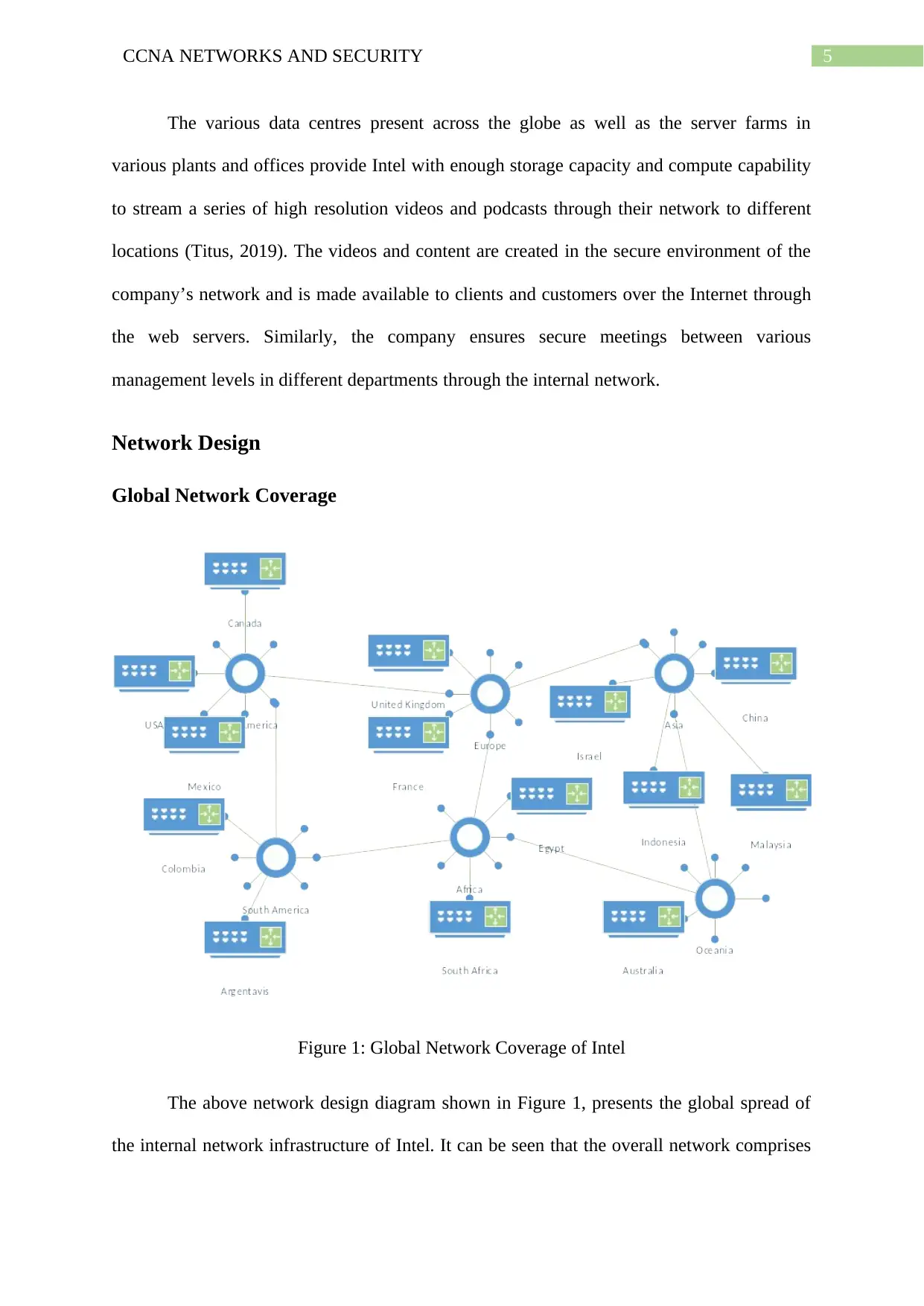
Network Design
Global Network Coverage
Figure 1: Global Network Coverage of Intel
The above network design diagram shown in Figure 1, presents the global spread of
the internal network infrastructure of Intel. It can be seen that the overall network comprises
The various data centres present across the globe as well as the server farms in
various plants and offices provide Intel with enough storage capacity and compute capability
to stream a series of high resolution videos and podcasts through their network to different
locations (Titus, 2019). The videos and content are created in the secure environment of the
company’s network and is made available to clients and customers over the Internet through
the web servers. Similarly, the company ensures secure meetings between various
management levels in different departments through the internal network.
Network Design
Global Network Coverage
Figure 1: Global Network Coverage of Intel
The above network design diagram shown in Figure 1, presents the global spread of
the internal network infrastructure of Intel. It can be seen that the overall network comprises
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CCNA NETWORKS AND SECURITY
of network interconnects of major continents like the North and South Americas, Africa,
Oceania, Asia and Europe. The network interconnects connect the router that receives the
WAN communications from remote sites and transmits the same through WAN networks to
the routers of different countries through the ring topology (Li et al., 2018). From the routers
of different countries, the network is divided among the routers of the different offices,
plants, server farms and data centres located across the country.
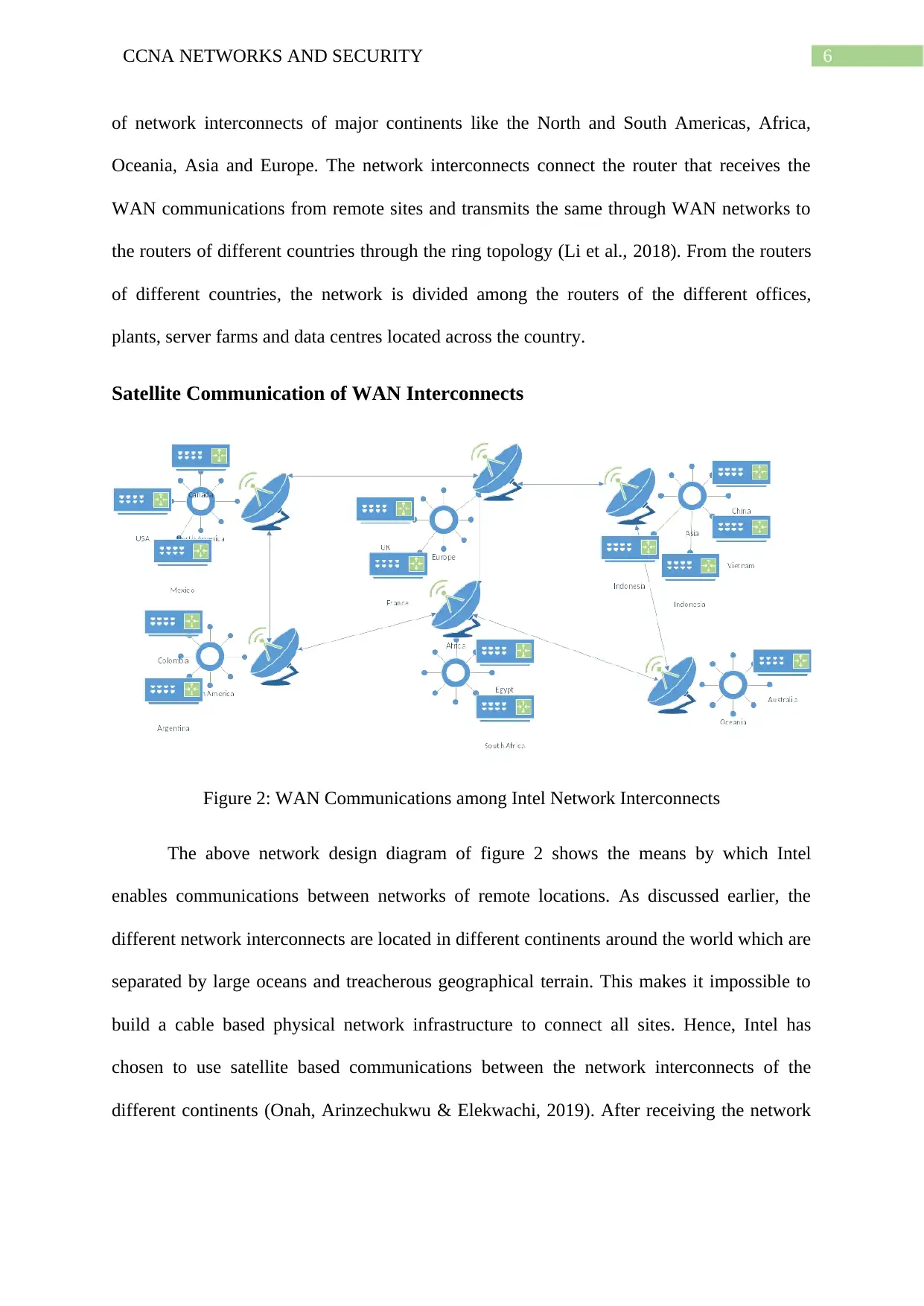
Satellite Communication of WAN Interconnects
Figure 2: WAN Communications among Intel Network Interconnects
The above network design diagram of figure 2 shows the means by which Intel
enables communications between networks of remote locations. As discussed earlier, the
different network interconnects are located in different continents around the world which are
separated by large oceans and treacherous geographical terrain. This makes it impossible to
build a cable based physical network infrastructure to connect all sites. Hence, Intel has
chosen to use satellite based communications between the network interconnects of the
different continents (Onah, Arinzechukwu & Elekwachi, 2019). After receiving the network
of network interconnects of major continents like the North and South Americas, Africa,
Oceania, Asia and Europe. The network interconnects connect the router that receives the
WAN communications from remote sites and transmits the same through WAN networks to
the routers of different countries through the ring topology (Li et al., 2018). From the routers
of different countries, the network is divided among the routers of the different offices,
plants, server farms and data centres located across the country.
Satellite Communication of WAN Interconnects
Figure 2: WAN Communications among Intel Network Interconnects
The above network design diagram of figure 2 shows the means by which Intel
enables communications between networks of remote locations. As discussed earlier, the
different network interconnects are located in different continents around the world which are
separated by large oceans and treacherous geographical terrain. This makes it impossible to
build a cable based physical network infrastructure to connect all sites. Hence, Intel has
chosen to use satellite based communications between the network interconnects of the
different continents (Onah, Arinzechukwu & Elekwachi, 2019). After receiving the network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CCNA NETWORKS AND SECURITY
from the satellite, routers of different countries use the national broadband infrastructure to
transmit the network services to the different offices and plants.
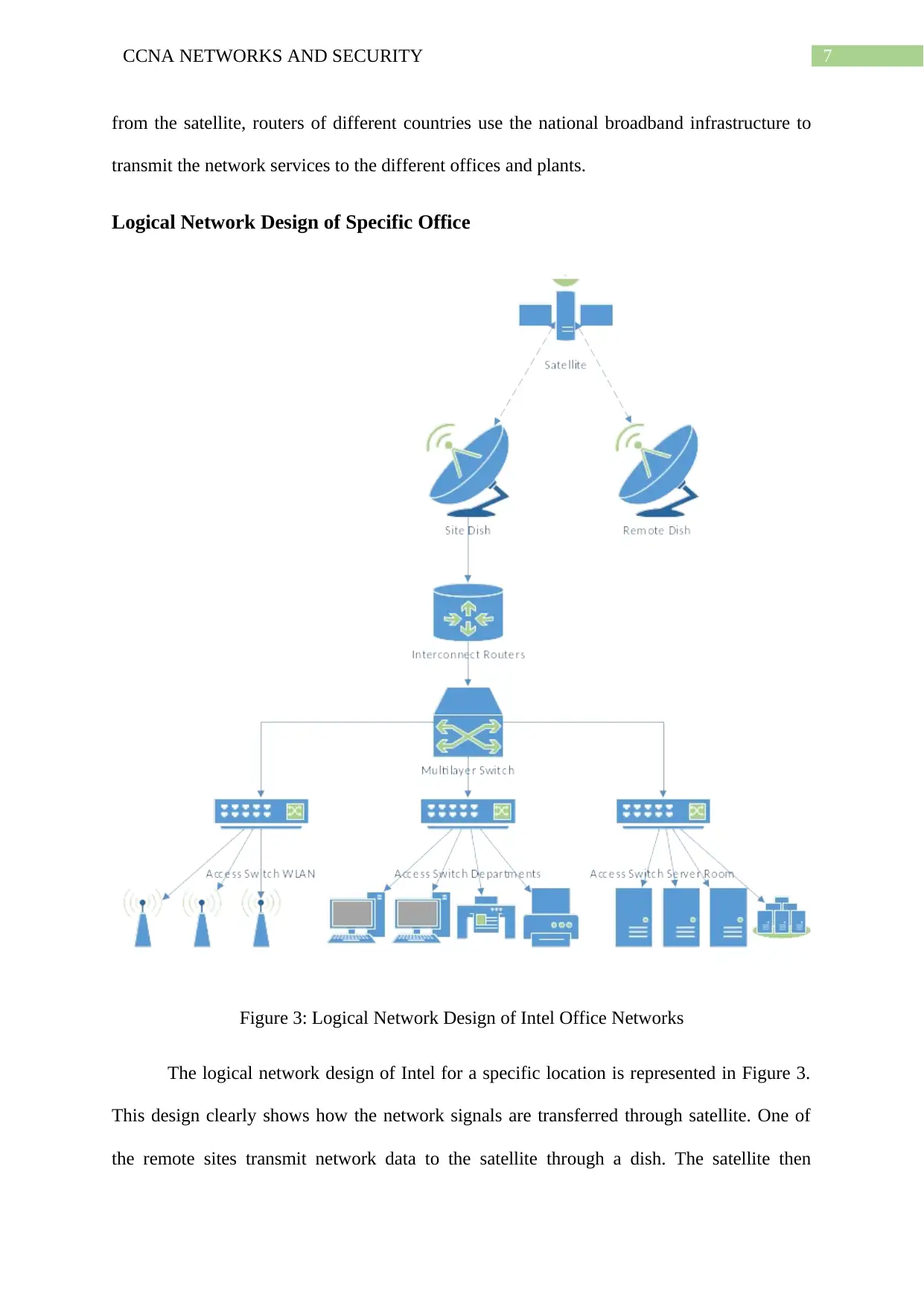
Logical Network Design of Specific Office
Figure 3: Logical Network Design of Intel Office Networks
The logical network design of Intel for a specific location is represented in Figure 3.
This design clearly shows how the network signals are transferred through satellite. One of
the remote sites transmit network data to the satellite through a dish. The satellite then
from the satellite, routers of different countries use the national broadband infrastructure to
transmit the network services to the different offices and plants.
Logical Network Design of Specific Office
Figure 3: Logical Network Design of Intel Office Networks
The logical network design of Intel for a specific location is represented in Figure 3.
This design clearly shows how the network signals are transferred through satellite. One of
the remote sites transmit network data to the satellite through a dish. The satellite then

8CCNA NETWORKS AND SECURITY
provides the network data to the dish of a specific location (Sowah et al., 2019). From here,
the network data is sent to a country specific router which uses the network infrastructure that
is hubs and switches (core and distribution) to reach the particular router of the particular
office or plant. The routers of these specific offices after obtaining the network use Network
Address Translation or NAT to hide the IP addresses of individual devices (Novo, 2018).
This way, network configurations of specific devices is kept anonymous from users of
different sites. Further security can be imposed by using IPSec VPN services through the
routers (Salman, 2017). These routers also specify the partitioning of different departments
and network segments and apply access restrictions through sub-netting, VLAN
configuration and ACL specifications (Alabady, Al-Turjman & Din, 2018). The different
network segments can include network of servers and data centres, WLAN networks and the
network segments of specific departments in an office.
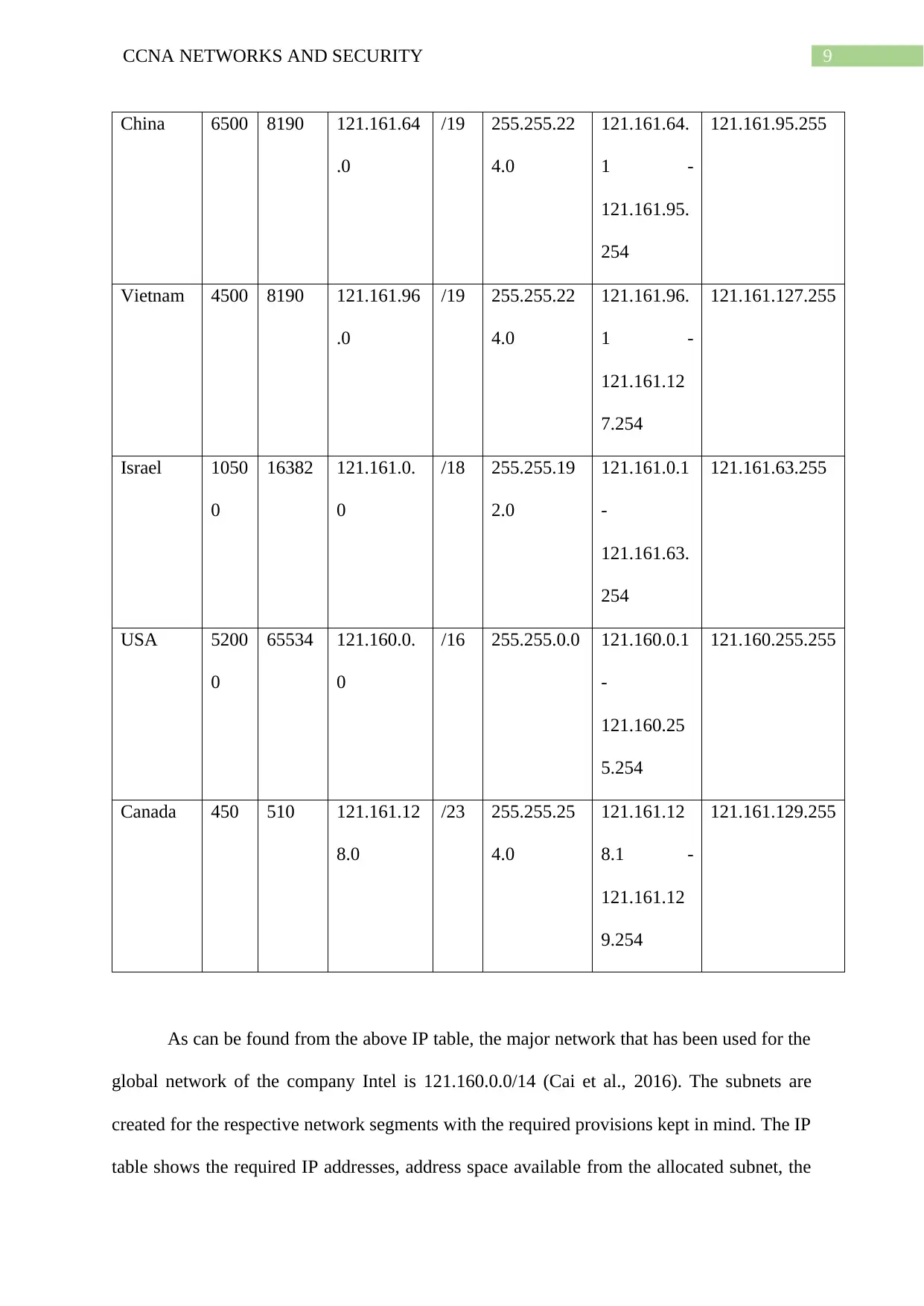
IP Subnet Classification
The following IP table shows the IP address allocation for the main routers of the
major offices of Intel in the continents of Asia and North America. It is to be noted the rough
estimates for number of employees of the company in the countries of China, Vietnam, Israel,
USA and Canada are 6000, 4000, 10000, 51000 and 400 (Klingler-Vidra & Wade, 2020).
However, additional provisions are taken for the various other routing devices present in
these locations and for possible expansions. The total number of employees of Intel across all
offices worldwide is over 100,000.
IP Table
Location
Subnets
Nee
ded
Size
Alloca
ted
Size
Network
Address
CI
DR
Subnet
Mask
IP
Addressing
Range
Broadcast
Address
provides the network data to the dish of a specific location (Sowah et al., 2019). From here,
the network data is sent to a country specific router which uses the network infrastructure that
is hubs and switches (core and distribution) to reach the particular router of the particular
office or plant. The routers of these specific offices after obtaining the network use Network
Address Translation or NAT to hide the IP addresses of individual devices (Novo, 2018).
This way, network configurations of specific devices is kept anonymous from users of
different sites. Further security can be imposed by using IPSec VPN services through the
routers (Salman, 2017). These routers also specify the partitioning of different departments
and network segments and apply access restrictions through sub-netting, VLAN
configuration and ACL specifications (Alabady, Al-Turjman & Din, 2018). The different
network segments can include network of servers and data centres, WLAN networks and the
network segments of specific departments in an office.
IP Subnet Classification
The following IP table shows the IP address allocation for the main routers of the
major offices of Intel in the continents of Asia and North America. It is to be noted the rough
estimates for number of employees of the company in the countries of China, Vietnam, Israel,
USA and Canada are 6000, 4000, 10000, 51000 and 400 (Klingler-Vidra & Wade, 2020).
However, additional provisions are taken for the various other routing devices present in
these locations and for possible expansions. The total number of employees of Intel across all
offices worldwide is over 100,000.
IP Table
Location
Subnets
Nee
ded
Size
Alloca
ted
Size
Network
Address
CI
DR
Subnet
Mask
IP
Addressing
Range
Broadcast
Address
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CCNA NETWORKS AND SECURITY
China 6500 8190 121.161.64
.0
/19 255.255.22
4.0
121.161.64.
1 -
121.161.95.
254
121.161.95.255
Vietnam 4500 8190 121.161.96
.0
/19 255.255.22
4.0
121.161.96.
1 -
121.161.12
7.254
121.161.127.255
Israel 1050
0
16382 121.161.0.
0
/18 255.255.19
2.0
121.161.0.1
-
121.161.63.
254
121.161.63.255
USA 5200
0
65534 121.160.0.
0
/16 255.255.0.0 121.160.0.1
-
121.160.25
5.254
121.160.255.255
Canada 450 510 121.161.12
8.0
/23 255.255.25
4.0
121.161.12
8.1 -
121.161.12
9.254
121.161.129.255
As can be found from the above IP table, the major network that has been used for the
global network of the company Intel is 121.160.0.0/14 (Cai et al., 2016). The subnets are
created for the respective network segments with the required provisions kept in mind. The IP
table shows the required IP addresses, address space available from the allocated subnet, the
China 6500 8190 121.161.64
.0
/19 255.255.22
4.0
121.161.64.
1 -
121.161.95.
254
121.161.95.255
Vietnam 4500 8190 121.161.96
.0
/19 255.255.22
4.0
121.161.96.
1 -
121.161.12
7.254
121.161.127.255
Israel 1050
0
16382 121.161.0.
0
/18 255.255.19
2.0
121.161.0.1
-
121.161.63.
254
121.161.63.255
USA 5200
0
65534 121.160.0.
0
/16 255.255.0.0 121.160.0.1
-
121.160.25
5.254
121.160.255.255
Canada 450 510 121.161.12
8.0
/23 255.255.25
4.0
121.161.12
8.1 -
121.161.12
9.254
121.161.129.255
As can be found from the above IP table, the major network that has been used for the
global network of the company Intel is 121.160.0.0/14 (Cai et al., 2016). The subnets are
created for the respective network segments with the required provisions kept in mind. The IP
table shows the required IP addresses, address space available from the allocated subnet, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CCNA NETWORKS AND SECURITY
network address, the broadcast address, the CIDR and Subnet masks as well as the range of
assignable IP addresses for the various subnets that have been created. It is noted that about
75 percent of the address space made available for the subnets gets used. This leaves enough
room to ensure that the network bandwidth does not get affect during peak usage of the
network. The subnet classifications for the major offices in the continents of Asia and North
America only consume 38 percent of the address space available from the major network.
Total number of IP addresses available in the major network is 262142. Number of IP
addresses required for networks of the five countries listed in the IP table is 73950 while the
number of assignable IP addresses provided by the subnets that have been created is 98806.
This means that there are adequate provisions for the networks of the nine other countries.
Many of these countries are located in different continents like Europe, Oceania, Africa and
South America.
VLAN
Virtual LANs or VLANs refer to broadcast domains which help create isolated
partitions in the data link layer of the OSI reference model of networking. These are multiple
LAN networks which companies can configure for ensuring communications such that the
network traffic appears to function on a single physical network but in practise virtually splits
the network among separate networks.
Intel makes use of VLANs for the different departments of their offices along with
ensuring different VLANs for the servers and the data centres located in specific plants. This
makes them prohibit access between different departments and manage different types of
network access by the hosts of these departments to the servers by specifying the protocols
used for the activities involved. These rules for such VLANs are created by the network
network address, the broadcast address, the CIDR and Subnet masks as well as the range of
assignable IP addresses for the various subnets that have been created. It is noted that about
75 percent of the address space made available for the subnets gets used. This leaves enough
room to ensure that the network bandwidth does not get affect during peak usage of the
network. The subnet classifications for the major offices in the continents of Asia and North
America only consume 38 percent of the address space available from the major network.
Total number of IP addresses available in the major network is 262142. Number of IP
addresses required for networks of the five countries listed in the IP table is 73950 while the
number of assignable IP addresses provided by the subnets that have been created is 98806.
This means that there are adequate provisions for the networks of the nine other countries.
Many of these countries are located in different continents like Europe, Oceania, Africa and
South America.
VLAN
Virtual LANs or VLANs refer to broadcast domains which help create isolated
partitions in the data link layer of the OSI reference model of networking. These are multiple
LAN networks which companies can configure for ensuring communications such that the
network traffic appears to function on a single physical network but in practise virtually splits
the network among separate networks.
Intel makes use of VLANs for the different departments of their offices along with
ensuring different VLANs for the servers and the data centres located in specific plants. This
makes them prohibit access between different departments and manage different types of
network access by the hosts of these departments to the servers by specifying the protocols
used for the activities involved. These rules for such VLANs are created by the network

11CCNA NETWORKS AND SECURITY
administrators of Intel as they specify the Access Control Lists (ACL) through the routers of
the offices of a particular location.
Routing and Configuration
The routers of specific offices includes configuration of interfaces that are used. This
includes configuration of sub-interfaces which includes specifying the VLANs of the specific
sub-interface and applying the respective private IP addresses. Since the number of devices to
be connected is large, DHCP pools for the VLANs are to be configured as well (Hubballi &
Tripathi, 2017). The only exception to DHCP based auto allocation of IP addresses is specific
servers like Web Server, DNS Server and FTP Server as these are to be auto configured in
end devices and hence their IP addresses should remain the same.
Components and Routing Protocols
A large company like Intel requires internetwork routing of network traffic generating
from various locations. However, the amount of traffic that needs to be routed from site to
site, across different countries throughout the world is huge and therefore it is impossible to
apply static routing. Hence, the OSPF dynamic routing is chosen. The configuration of these
routing protocols are applied on every router. The internal network partitions of network
segments are implemented through VLANs and ACL permissions. These need to be specified
in the office routers as well. Additionally, all the created VLANs need to be listed in the
VLAN database of the multilayer switch. After this, the access layer switches which are used
to directly connect the end devices, servers and wireless access points are should specify the
VLAN number for the hosts they connect in the interface itself. All interfaces of the
multilayer switch should be used in trunk mode to enable inter VLAN routing.
administrators of Intel as they specify the Access Control Lists (ACL) through the routers of
the offices of a particular location.
Routing and Configuration
The routers of specific offices includes configuration of interfaces that are used. This
includes configuration of sub-interfaces which includes specifying the VLANs of the specific
sub-interface and applying the respective private IP addresses. Since the number of devices to
be connected is large, DHCP pools for the VLANs are to be configured as well (Hubballi &
Tripathi, 2017). The only exception to DHCP based auto allocation of IP addresses is specific
servers like Web Server, DNS Server and FTP Server as these are to be auto configured in
end devices and hence their IP addresses should remain the same.
Components and Routing Protocols
A large company like Intel requires internetwork routing of network traffic generating
from various locations. However, the amount of traffic that needs to be routed from site to
site, across different countries throughout the world is huge and therefore it is impossible to
apply static routing. Hence, the OSPF dynamic routing is chosen. The configuration of these
routing protocols are applied on every router. The internal network partitions of network
segments are implemented through VLANs and ACL permissions. These need to be specified
in the office routers as well. Additionally, all the created VLANs need to be listed in the
VLAN database of the multilayer switch. After this, the access layer switches which are used
to directly connect the end devices, servers and wireless access points are should specify the
VLAN number for the hosts they connect in the interface itself. All interfaces of the
multilayer switch should be used in trunk mode to enable inter VLAN routing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





