CDU Asset Security & Risk Management: Recommendations & Best Practices
VerifiedAdded on 2023/06/12
|8
|581
|475
Report
AI Summary
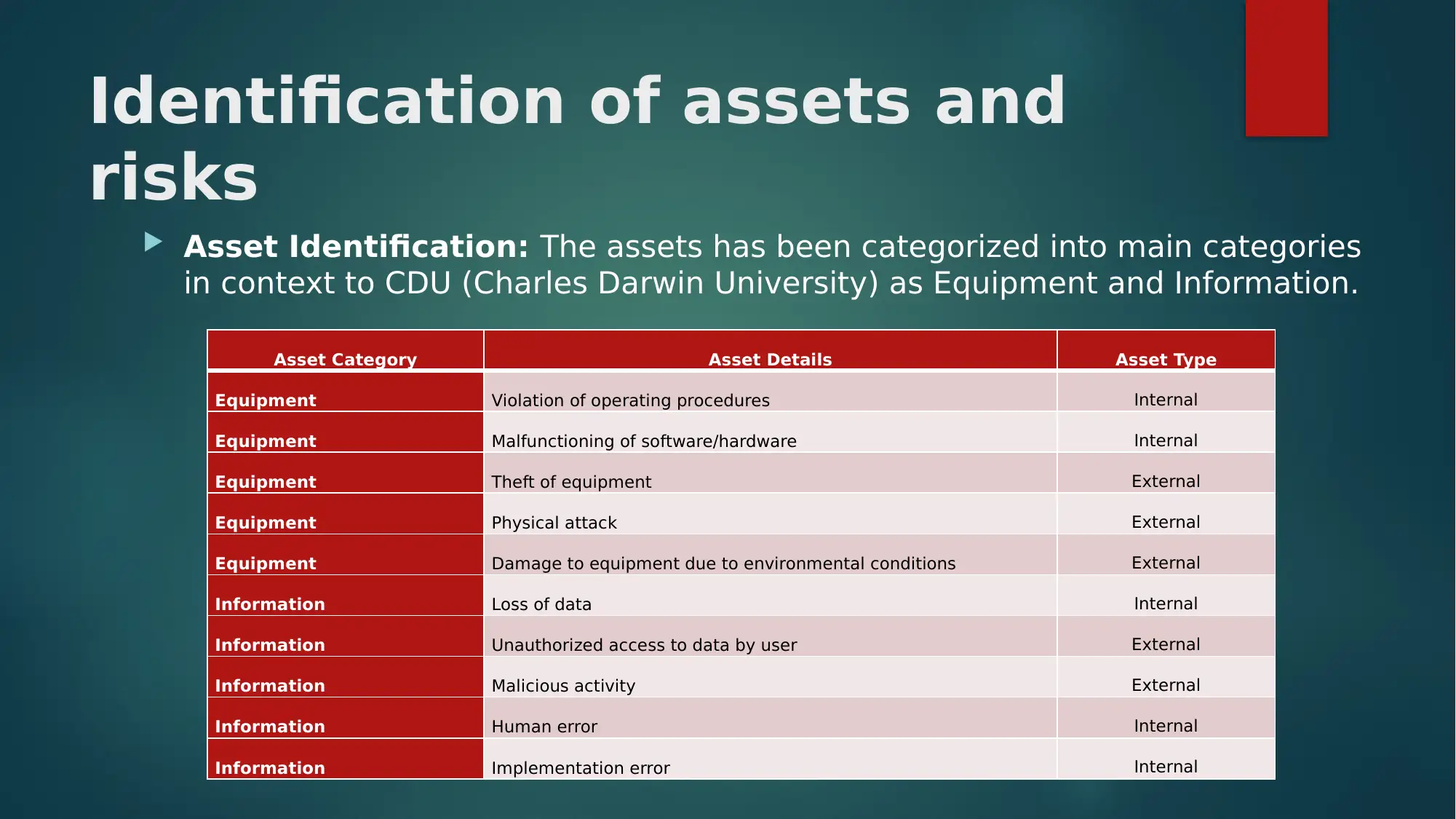
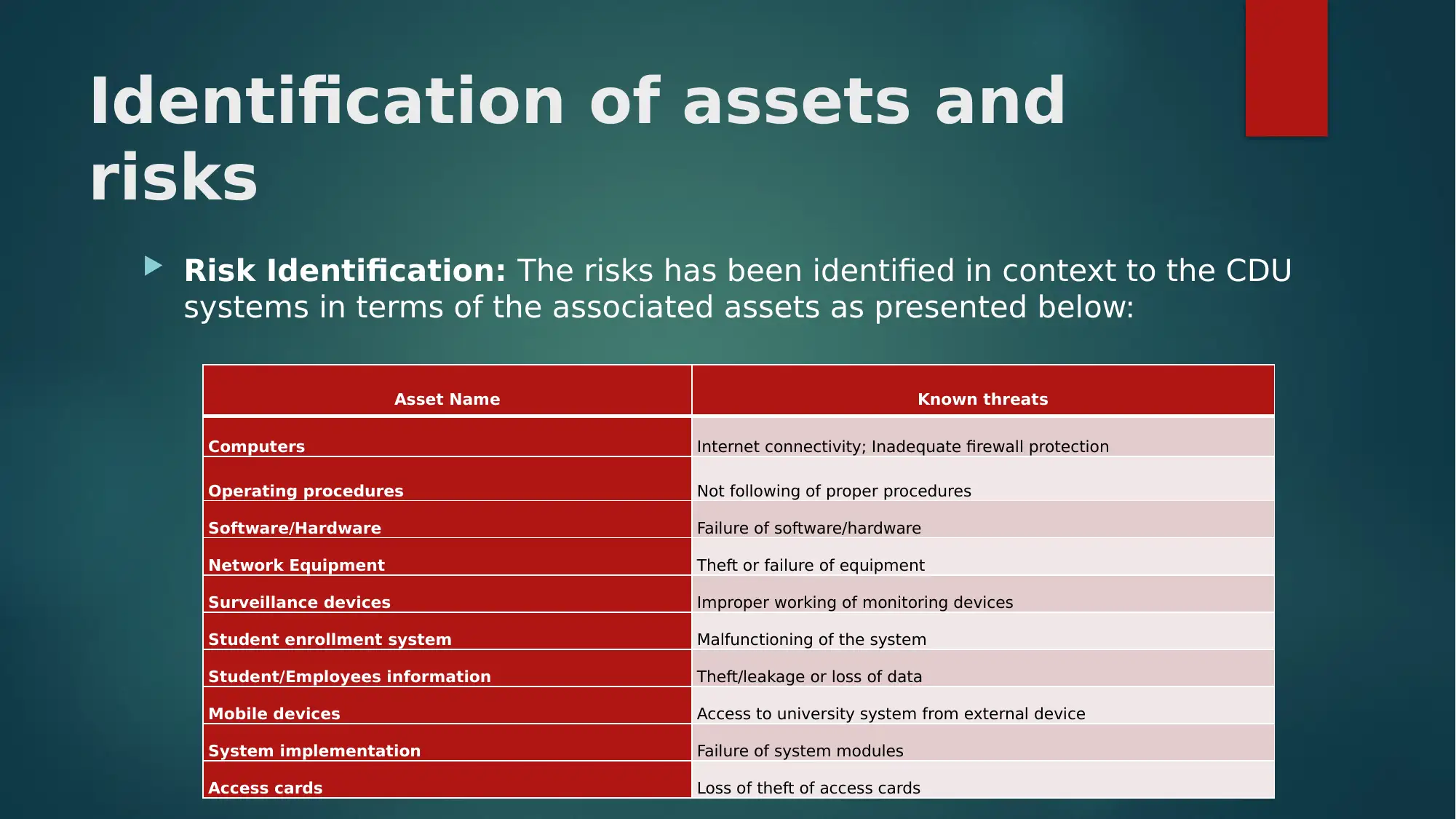
This report assesses asset security and risk management at Charles Darwin University (CDU), identifying key assets such as equipment and information, and associated risks like data loss, unauthorized access, and equipment theft. It categorizes assets, details their types and owners, and proposes treatments for identified risks. The report emphasizes the importance of protecting student and employee credentials and recommends strategies for improving CDU's security landscape, including stakeholder identification, information security strategy development, and security awareness programs. It concludes that effective risk management and mitigation strategies are essential for securing CDU's assets and mitigating potential threats. Access more solved assignments and study resources on Desklib.
1 out of 8












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)