An Analysis of Cybersecurity Challenges in the Business Environment
VerifiedAdded on 2020/06/05
|9
|2702
|72
Report
AI Summary
This report provides a comprehensive overview of the challenges businesses face in maintaining robust cybersecurity. It begins by defining cybersecurity and emphasizing its importance in protecting systems, data, and information from various threats. The report then outlines key objectives, including analyzing cybersecurity concepts, identifying challenges, and recommending solutions. A literature review explores the concept of cybersecurity, highlighting the increasing number of cyberattacks and the need for skilled personnel. The report identifies malware, user-related vulnerabilities, and budget constraints as significant challenges. The research design and methodology section details the use of qualitative data collection through primary sources like surveys and interviews, with simple random sampling. The report also addresses research limitations, such as time and budget constraints, and provides a detailed timescale for the research process, outlining activities across eight weeks. The conclusion summarizes the findings and recommendations for addressing the identified cybersecurity challenges. The report underscores the need for businesses to proactively address these challenges to protect their operations and data.

Challenges in cyber security for
business
business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
Aim.........................................................................................................................................1
Objectives...............................................................................................................................1
Scope of the project.........................................................................................................................1
Research Question...........................................................................................................................1
Literature Review.............................................................................................................................2
Concept and importance of cyber security.............................................................................2
Factors as challenges in cyber security..................................................................................2
Research Design and Methodology.................................................................................................3
Validity and Reliability..........................................................................................................4
Sampling.................................................................................................................................4
Data Collection.......................................................................................................................4
Research Limitations..............................................................................................................5
Timescale................................................................................................................................5
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................7
INTRODUCTION...........................................................................................................................1
Aim.........................................................................................................................................1
Objectives...............................................................................................................................1
Scope of the project.........................................................................................................................1
Research Question...........................................................................................................................1
Literature Review.............................................................................................................................2
Concept and importance of cyber security.............................................................................2
Factors as challenges in cyber security..................................................................................2
Research Design and Methodology.................................................................................................3
Validity and Reliability..........................................................................................................4
Sampling.................................................................................................................................4
Data Collection.......................................................................................................................4
Research Limitations..............................................................................................................5
Timescale................................................................................................................................5
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................7

INTRODUCTION
Cyber security is considered as providing protection to the systems from various issues
like some sort of damage or theft of any particular software, hardware or the data and
information of some firm. So, it has its control over the physical access of the hardware, software
and other applications (Elmaghraby and Losavio, 2014). As there has been a growth of the
business in the market place, it is obvious enough that as the business grows, the challenges for it
increases as well. Some very well known and popular challenges of cyber security for any
business can be considered as the functional growth in the information and data as well as the
security measures that are especially meant for providing protection to the business and all its
internal processes such as data and information etc. Also, there has been observed that there has
been a sort of shortage for skilled and talented personnel for evaluating the risk and improving
them.
Aim
To understand the challenges and barriers in the cyber security for business
Objectives
To analyse the idea and importance of cyber security.
To understand the challenges that can occur in the cyber security.
To recommend ways by which challenges can be resolved in the cyber security.
Scope of the project
The scope of the project is very wide because it involves all concept of cyber security and
it is much wide to understand. There is a need of cyber security because the overall number of
cyber attackers and risks has been increasing day by day because of which it also is giving rise to
various incidents that are being done by the innocents involved. There are enormous risks that
come under the cyber crimes and it actually has a bad impact on the lives of the person. Various
factors are also that act as some challenge or barrier in the cyber security such as malware etc.
So, it is important to study the project as the scope of the project is much wide.
Research Question
Q1 What is the concept and importance of cyber security?
Q2 What are the factors that can act as challenges and barriers for the cyber security in the
business?
1
Cyber security is considered as providing protection to the systems from various issues
like some sort of damage or theft of any particular software, hardware or the data and
information of some firm. So, it has its control over the physical access of the hardware, software
and other applications (Elmaghraby and Losavio, 2014). As there has been a growth of the
business in the market place, it is obvious enough that as the business grows, the challenges for it
increases as well. Some very well known and popular challenges of cyber security for any
business can be considered as the functional growth in the information and data as well as the
security measures that are especially meant for providing protection to the business and all its
internal processes such as data and information etc. Also, there has been observed that there has
been a sort of shortage for skilled and talented personnel for evaluating the risk and improving
them.
Aim
To understand the challenges and barriers in the cyber security for business
Objectives
To analyse the idea and importance of cyber security.
To understand the challenges that can occur in the cyber security.
To recommend ways by which challenges can be resolved in the cyber security.
Scope of the project
The scope of the project is very wide because it involves all concept of cyber security and
it is much wide to understand. There is a need of cyber security because the overall number of
cyber attackers and risks has been increasing day by day because of which it also is giving rise to
various incidents that are being done by the innocents involved. There are enormous risks that
come under the cyber crimes and it actually has a bad impact on the lives of the person. Various
factors are also that act as some challenge or barrier in the cyber security such as malware etc.
So, it is important to study the project as the scope of the project is much wide.
Research Question
Q1 What is the concept and importance of cyber security?
Q2 What are the factors that can act as challenges and barriers for the cyber security in the
business?
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Q3 What can be recommended to resolve the challenges for cyber security?
Literature Review
Concept and importance of cyber security
Cyber security is termed as providing security measures to the computer systems, various
programs running on it and all the information and data over the complete network. The crimes
related to it are increasing in number day by day, so there is a huge requirement of the cyber
security. There are some specified areas that get covered under the cyber security and these
involve the application security, network security, disaster recovery and the informational and
operational security. The biggest issue is the maximizing rate of risks that are being seen across
in various situations. Cyber crimes are increasing day by day and for resolving them, there is a
strong need of cyber security so that these crimes can be stopped. There is a wide range of cyber
crimes and these involve child pornography, sextortion, hacking someone's personal data and
information, pictures and misusing them etc. So, cyber security plays a very important role as it
helps various innocent people to stay protected from such acts (Choo, 2011). Cyber attackers are
considered as the people that make use of some malicious software for entering in some other
computer's code and data and try to extract all the data and information from the same. There is a
complete management in cyber security that follows the whole set of activities as first they
identify the risk is or any such situation happened, then, they search for the address of the system
and location from where the activity has been happened and uploaded. After detecting the
address, they respond and recover the matter. Also, make changes as if necessary, remove the
stuff and the process of penalties start for the culprits.
Factors as challenges in cyber security
Cyber security is very important as it helps in resolving various issues that are associated
with cyber crimes and attackers. The average rate of cyber crimes is increasing day by day, thus
maximizing the rate of challenges as well. Although professionals at cyber security are well
trained and skilled of the fact that how to manage such cases of cyber crimes but there are
various factors that act as a barrier in the cyber security for any business and these are discussed
as under:
Malware
Malware is also considered as malicious software that can be in the form of any file or
application that somehow proves harmful for the system. It includes worms, Trojan horses etc.
2
Literature Review
Concept and importance of cyber security
Cyber security is termed as providing security measures to the computer systems, various
programs running on it and all the information and data over the complete network. The crimes
related to it are increasing in number day by day, so there is a huge requirement of the cyber
security. There are some specified areas that get covered under the cyber security and these
involve the application security, network security, disaster recovery and the informational and
operational security. The biggest issue is the maximizing rate of risks that are being seen across
in various situations. Cyber crimes are increasing day by day and for resolving them, there is a
strong need of cyber security so that these crimes can be stopped. There is a wide range of cyber
crimes and these involve child pornography, sextortion, hacking someone's personal data and
information, pictures and misusing them etc. So, cyber security plays a very important role as it
helps various innocent people to stay protected from such acts (Choo, 2011). Cyber attackers are
considered as the people that make use of some malicious software for entering in some other
computer's code and data and try to extract all the data and information from the same. There is a
complete management in cyber security that follows the whole set of activities as first they
identify the risk is or any such situation happened, then, they search for the address of the system
and location from where the activity has been happened and uploaded. After detecting the
address, they respond and recover the matter. Also, make changes as if necessary, remove the
stuff and the process of penalties start for the culprits.
Factors as challenges in cyber security
Cyber security is very important as it helps in resolving various issues that are associated
with cyber crimes and attackers. The average rate of cyber crimes is increasing day by day, thus
maximizing the rate of challenges as well. Although professionals at cyber security are well
trained and skilled of the fact that how to manage such cases of cyber crimes but there are
various factors that act as a barrier in the cyber security for any business and these are discussed
as under:
Malware
Malware is also considered as malicious software that can be in the form of any file or
application that somehow proves harmful for the system. It includes worms, Trojan horses etc.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

All these programs are responsible for doing their functioning of stealing, encrypting and
deleting the information from the computer etc. So, this can be considered as a challenge for the
cyber security because whenever such incidents happen, it is the responsibility of the cyber
security to take specific measures to manage the case (Li and Zhu, 2012). In some cases, it is
quite easy to find the location and details but in some, the cyber security has to give much
amount of time and usually it can be observed in the case of very experienced attackers who are
well aware of the ways to dodge the security.
Users
Users can also sometimes, act as a barrier for the cyber security, whether they are from
inside of the organisation or from any external source. This can be well defined by using an
example that if there is the presence of some insider risk person or it can be because of some
accidental act as well (Yan and et.al, 2012). Such as if the administrator of some server decides
to erase the whole data from the server and store it some key stroke. So, in such cases, there is a
high possibility that the data and information can be stolen easily.
Budget
It is not possible for every organisation to afford the financial status for a perfect and
appropriate cyber security. Although the organisation usually increases their standards after some
breach or any incident happen in the company that has some bad and negative impact on the
popularity of the company. So, the organisation should at the time of planning, must ensure the
financial status for each factor and operation of the company because in bigger organisations, it
is very important to protect the data of the customers, employees and regarding the personal
details of the company, operations and financial stability. By this way, the budget cannot act as a
challenge any more in providing the efficient and appropriate cyber security to all the essential
information and data in an organisation.
Research Design and Methodology
Research is considered as a systematic way of collecting all the information and data that
can be sued in the research. Also, it helps the researcher to reach till various new conclusions.
Research methodology is considered as a theoretical evaluation of all the ways and techniques
that are being used in the whole research. It can be further classified in two types, either the
qualitative or the quantitative (Wang and Chow, 2010). The qualitative one aims for a complete
description of the data collected and observed whereas the quantitative one covers the statistical
3
deleting the information from the computer etc. So, this can be considered as a challenge for the
cyber security because whenever such incidents happen, it is the responsibility of the cyber
security to take specific measures to manage the case (Li and Zhu, 2012). In some cases, it is
quite easy to find the location and details but in some, the cyber security has to give much
amount of time and usually it can be observed in the case of very experienced attackers who are
well aware of the ways to dodge the security.
Users
Users can also sometimes, act as a barrier for the cyber security, whether they are from
inside of the organisation or from any external source. This can be well defined by using an
example that if there is the presence of some insider risk person or it can be because of some
accidental act as well (Yan and et.al, 2012). Such as if the administrator of some server decides
to erase the whole data from the server and store it some key stroke. So, in such cases, there is a
high possibility that the data and information can be stolen easily.
Budget
It is not possible for every organisation to afford the financial status for a perfect and
appropriate cyber security. Although the organisation usually increases their standards after some
breach or any incident happen in the company that has some bad and negative impact on the
popularity of the company. So, the organisation should at the time of planning, must ensure the
financial status for each factor and operation of the company because in bigger organisations, it
is very important to protect the data of the customers, employees and regarding the personal
details of the company, operations and financial stability. By this way, the budget cannot act as a
challenge any more in providing the efficient and appropriate cyber security to all the essential
information and data in an organisation.
Research Design and Methodology
Research is considered as a systematic way of collecting all the information and data that
can be sued in the research. Also, it helps the researcher to reach till various new conclusions.
Research methodology is considered as a theoretical evaluation of all the ways and techniques
that are being used in the whole research. It can be further classified in two types, either the
qualitative or the quantitative (Wang and Chow, 2010). The qualitative one aims for a complete
description of the data collected and observed whereas the quantitative one covers the statistical
3

or tabular data. So, for getting effective and appropriate information, the researcher will make
use of the qualitative data and information.
Validity and Reliability
Validity is considered as a sort of indication which helps in analysing the sound ability of
the whole research. It includes all the techniques along with the design of the research.
Reliability is also considered as a way of checking and assessing the quality of the whole
procedure that has been used for gathering the data and information in the research. The validity
and reliability of research is important so that the researcher has to ensure about both these
factors for making a better analysis of the need of cyber security in an organisation.
Sampling
Sampling is considered as a process in which a few samples are been taken from a large
population in order to perform the function as by taking the interviews and performing surveys
from them. Sampling can be classified in various types such as simple random sampling (SRS),
cluster sampling, stratified sampling, systematic sampling and the multistage sampling. In this
research, the researcher will make use of the simple random sampling because by this, the
researcher can take a few random samples and ask the questions from them as it will help them
in getting more appropriate and efficient information about cyber security in an organisation.
Data Collection
Data collection is also referred to as the gathering of data and information for making the
research more efficient and appropriate. There are two ways by which the data can be collected
and these are the primary and the secondary data. The primary data is the data that is being
collected for the first time and it is being done by sources like questionnaire, surveys, focused
groups and interviews (Bhagat and Bhagat Bhavesh C, 2012). Secondary data is the data that has
already been collected by some external body and it is being done by sources like books, online,
journals etc. In this research, the researcher will make use of the primary data because surveys
and interviews can help in getting more appropriate information regarding the cyber security and
challenges being faced in it. It is important as well because in case of secondary data, there is a
possibility that the data might be old which cannot make the research effective as well, so the
researcher will make use of the primary data.
4
use of the qualitative data and information.
Validity and Reliability
Validity is considered as a sort of indication which helps in analysing the sound ability of
the whole research. It includes all the techniques along with the design of the research.
Reliability is also considered as a way of checking and assessing the quality of the whole
procedure that has been used for gathering the data and information in the research. The validity
and reliability of research is important so that the researcher has to ensure about both these
factors for making a better analysis of the need of cyber security in an organisation.
Sampling
Sampling is considered as a process in which a few samples are been taken from a large
population in order to perform the function as by taking the interviews and performing surveys
from them. Sampling can be classified in various types such as simple random sampling (SRS),
cluster sampling, stratified sampling, systematic sampling and the multistage sampling. In this
research, the researcher will make use of the simple random sampling because by this, the
researcher can take a few random samples and ask the questions from them as it will help them
in getting more appropriate and efficient information about cyber security in an organisation.
Data Collection
Data collection is also referred to as the gathering of data and information for making the
research more efficient and appropriate. There are two ways by which the data can be collected
and these are the primary and the secondary data. The primary data is the data that is being
collected for the first time and it is being done by sources like questionnaire, surveys, focused
groups and interviews (Bhagat and Bhagat Bhavesh C, 2012). Secondary data is the data that has
already been collected by some external body and it is being done by sources like books, online,
journals etc. In this research, the researcher will make use of the primary data because surveys
and interviews can help in getting more appropriate information regarding the cyber security and
challenges being faced in it. It is important as well because in case of secondary data, there is a
possibility that the data might be old which cannot make the research effective as well, so the
researcher will make use of the primary data.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Research Limitations
Research limitations are considered as the factors that may act as a challenge or barrier at
any time in the research. Like if in case, the researcher wants to give more time to the research,
for that they should ensure the availability of more cost and time as well. It is because when the
time will be extended to do a particular research, it is obvious enough that more cost and time
will be required as well. So, in such cases, if there is no availability of the cost and time factor,
then these two can act as a sort of limitation in the research. Then, they can act as a barrier in the
research. So, the researcher should ensure the fact to complete the research in the given deadline
only so that no factor can act as a limitation or barrier while implementing the research.
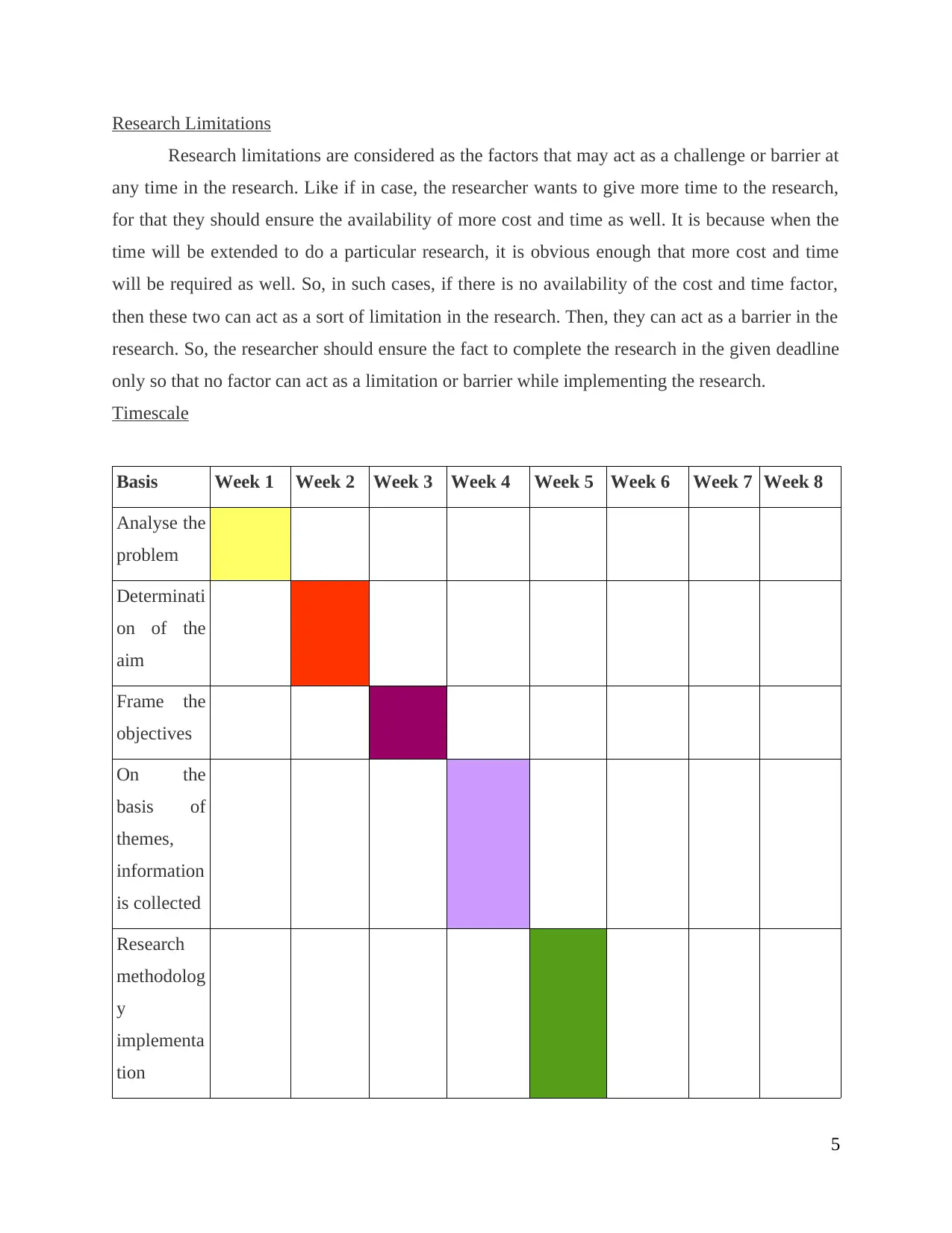
Timescale
Basis Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7 Week 8
Analyse the
problem
Determinati
on of the
aim
Frame the
objectives
On the
basis of
themes,
information
is collected
Research
methodolog
y
implementa
tion
5
Research limitations are considered as the factors that may act as a challenge or barrier at
any time in the research. Like if in case, the researcher wants to give more time to the research,
for that they should ensure the availability of more cost and time as well. It is because when the
time will be extended to do a particular research, it is obvious enough that more cost and time
will be required as well. So, in such cases, if there is no availability of the cost and time factor,
then these two can act as a sort of limitation in the research. Then, they can act as a barrier in the
research. So, the researcher should ensure the fact to complete the research in the given deadline
only so that no factor can act as a limitation or barrier while implementing the research.
Timescale
Basis Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7 Week 8
Analyse the
problem
Determinati
on of the
aim
Frame the
objectives
On the
basis of
themes,
information
is collected
Research
methodolog
y
implementa
tion
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
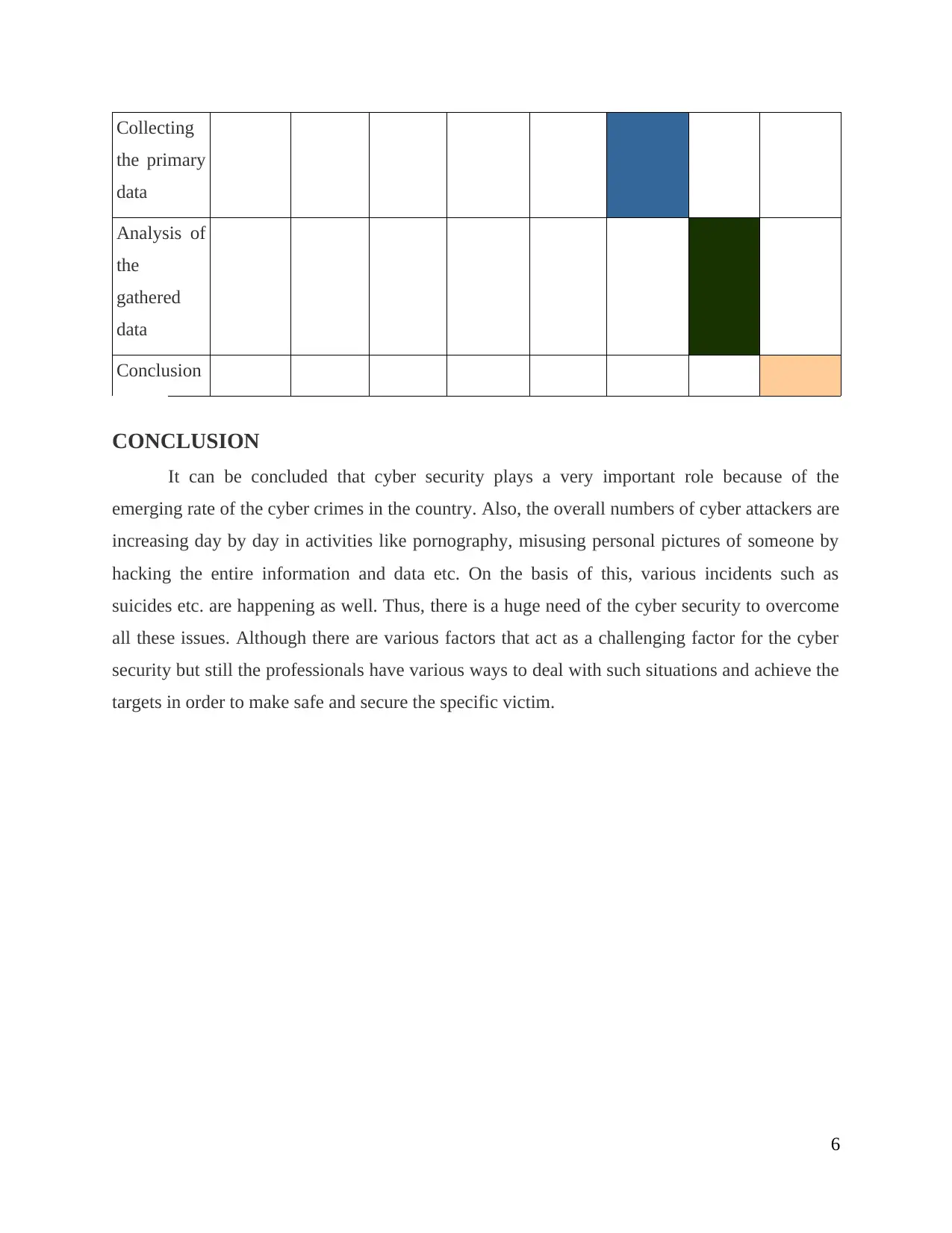
Collecting
the primary
data
Analysis of
the
gathered
data
Conclusion
CONCLUSION
It can be concluded that cyber security plays a very important role because of the
emerging rate of the cyber crimes in the country. Also, the overall numbers of cyber attackers are
increasing day by day in activities like pornography, misusing personal pictures of someone by
hacking the entire information and data etc. On the basis of this, various incidents such as
suicides etc. are happening as well. Thus, there is a huge need of the cyber security to overcome
all these issues. Although there are various factors that act as a challenging factor for the cyber
security but still the professionals have various ways to deal with such situations and achieve the
targets in order to make safe and secure the specific victim.
6
the primary
data
Analysis of
the
gathered
data
Conclusion
CONCLUSION
It can be concluded that cyber security plays a very important role because of the
emerging rate of the cyber crimes in the country. Also, the overall numbers of cyber attackers are
increasing day by day in activities like pornography, misusing personal pictures of someone by
hacking the entire information and data etc. On the basis of this, various incidents such as
suicides etc. are happening as well. Thus, there is a huge need of the cyber security to overcome
all these issues. Although there are various factors that act as a challenging factor for the cyber
security but still the professionals have various ways to deal with such situations and achieve the
targets in order to make safe and secure the specific victim.
6

REFERENCES
Books and Journals:
Bhagat, B.C. and Bhagat Bhavesh C, 2012. Cloud Computing Governance, Cyber Security, Risk,
and Compliance Business Rules System and Method. U.S. Patent Application
13/016,999.
Choo, K. K. R., 2011. The cyber threat landscape: Challenges and future research
directions. Computers & Security. 30(8). pp.719-731.
Elmaghraby, A. S. and Losavio, M. M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research. 5(4). pp.491-497.
Li, X. and Zhu, H., 2012. Securing smart grid: cyber attacks, countermeasures, and
challenges. IEEE Communications Magazine. 50(8).
Li, X. and et.al., 2012. Securing smart grid: cyber attacks, countermeasures, and
challenges. IEEE Communications Magazine. 52(8).
Wang, E. K. and Chow, K.P., 2010, December. Security issues and challenges for cyber physical
system. In Proceedings of the 2010 IEEE/ACM Int'l Conference on Green Computing
and Communications & Int'l Conference on Cyber, Physical and Social Computing (pp.
733-738). IEEE Computer Society.
Yan, Y. and et.al., 2012. A survey on cyber security for smart grid communications. IEEE
Communications Surveys and tutorials. 14(4). pp.998-1010.
7
Books and Journals:
Bhagat, B.C. and Bhagat Bhavesh C, 2012. Cloud Computing Governance, Cyber Security, Risk,
and Compliance Business Rules System and Method. U.S. Patent Application
13/016,999.
Choo, K. K. R., 2011. The cyber threat landscape: Challenges and future research
directions. Computers & Security. 30(8). pp.719-731.
Elmaghraby, A. S. and Losavio, M. M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research. 5(4). pp.491-497.
Li, X. and Zhu, H., 2012. Securing smart grid: cyber attacks, countermeasures, and
challenges. IEEE Communications Magazine. 50(8).
Li, X. and et.al., 2012. Securing smart grid: cyber attacks, countermeasures, and
challenges. IEEE Communications Magazine. 52(8).
Wang, E. K. and Chow, K.P., 2010, December. Security issues and challenges for cyber physical
system. In Proceedings of the 2010 IEEE/ACM Int'l Conference on Green Computing
and Communications & Int'l Conference on Cyber, Physical and Social Computing (pp.
733-738). IEEE Computer Society.
Yan, Y. and et.al., 2012. A survey on cyber security for smart grid communications. IEEE
Communications Surveys and tutorials. 14(4). pp.998-1010.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





