Comprehensive Analysis of IoT Security Challenges: MSc Project
VerifiedAdded on 2023/06/10
|81
|22608
|228
Project
AI Summary
This MSc project delves into the multifaceted security challenges inherent in the Internet of Things (IoT). The project begins with an introduction to the IoT, its architecture, and its layered structure, encompassing perception, network, and application layers. A comprehensive literature review examines existing research on IoT security, identifying vulnerabilities and threats across different layers. The methodology employs a secondary data analysis technique to evaluate security issues in four real-world IoT applications: a Fitbit health tracker, BMW's Connected Drive system, the HomeEasy protocol for home automation, and the Eye-Fi SD-card. The findings and analysis reveal specific security weaknesses and potential attack vectors within each application. The results and discussion chapters elaborate on current and future challenges, including constraints and emerging threats. The project concludes with recommendations for mitigating these challenges, emphasizing the need for robust security measures to safeguard IoT devices and data. The practical component involves creating a webpage using WordPress to further illustrate the concepts discussed.

Running head: COMPUTER NETWORK SECURITY
Challenges of the Internet of Things (IoT) in Term of Security
MSc Computer Network Security
Supervisor:
Dr. Dhiya Al-jumeily
Done by:
SALEH A. ALFAHAD
(777730)
S.A.Alfahad@2017.ljmu.ac.uk
Challenges of the Internet of Things (IoT) in Term of Security
MSc Computer Network Security
Supervisor:
Dr. Dhiya Al-jumeily
Done by:
SALEH A. ALFAHAD
(777730)
S.A.Alfahad@2017.ljmu.ac.uk
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER NETWORK SECURITY
Acknowledgement
I would like to thank our supervisor Dr. Dhiya Al-jumeily who gave me this golden opportunity
of doing this wonderful project. I would also like to express my special thanks to him to for his
provision and guidance during the entire project. I would also like to extend my thanks to my
classmates who have helped me to the conduct this research project successfully.
Acknowledgement
I would like to thank our supervisor Dr. Dhiya Al-jumeily who gave me this golden opportunity
of doing this wonderful project. I would also like to express my special thanks to him to for his
provision and guidance during the entire project. I would also like to extend my thanks to my
classmates who have helped me to the conduct this research project successfully.

2COMPUTER NETWORK SECURITY
Abstract
This focus of this project is on demonstrating the challenges being faced in Internet of Things
(IoT) in terms of security. The discussions as well as analysis are executed out in this project to
illustrate on the security issues within IoT and some solutions have also been proposed. The
security issues have been clearly stated categorizing them into different layers.
Further, analysis has been done on four applications of IoT to evaluate the issues and present
them so that those can be solved with proper mitigation strategies. In this research project,
secondary data analysis technique has been used which shows the security challenges of IoT in
four different fields of application. The issues have been elaborated in the results and discussion
to focus on the current and future challenges of IoT.
Finally, in the last chapter, a conclusion has been drawn to the study to present the outcomes that
are achieved from the project. Moreover, some recommendations have been provided so that
proper mechanisms can be implemented to prevent the challenges of IoT in terms of security.
Abstract
This focus of this project is on demonstrating the challenges being faced in Internet of Things
(IoT) in terms of security. The discussions as well as analysis are executed out in this project to
illustrate on the security issues within IoT and some solutions have also been proposed. The
security issues have been clearly stated categorizing them into different layers.
Further, analysis has been done on four applications of IoT to evaluate the issues and present
them so that those can be solved with proper mitigation strategies. In this research project,
secondary data analysis technique has been used which shows the security challenges of IoT in
four different fields of application. The issues have been elaborated in the results and discussion
to focus on the current and future challenges of IoT.
Finally, in the last chapter, a conclusion has been drawn to the study to present the outcomes that
are achieved from the project. Moreover, some recommendations have been provided so that
proper mechanisms can be implemented to prevent the challenges of IoT in terms of security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER NETWORK SECURITY
Table of Contents
1. Introduction..................................................................................................................................6
1.1 Aims and Objectives of the project.......................................................................................7
1. Main Objective....................................................................................................................7
2. Specific Objectives..............................................................................................................7
1.2 Project Plan............................................................................................................................7
2. Literature Review......................................................................................................................10
2.1 Internet of Things Architecture...........................................................................................10
2.2 Internet of Things Layers.....................................................................................................11
1. Perception layer.................................................................................................................12
2. Network layer....................................................................................................................12
3. Application layer...............................................................................................................13
2.3 IoT Applications..................................................................................................................13
2.4 Security Challenges in IoT Layers......................................................................................15
1. Perception Layer................................................................................................................15
2. Network Layer...................................................................................................................16
3. Application Layer..............................................................................................................17
2.5 Threats Facing IoT...............................................................................................................17
2.6 The fundamental differences between Internet of things and traditional Internet...............18
2.7 Security Directions for IoT layers.......................................................................................20
Table of Contents
1. Introduction..................................................................................................................................6
1.1 Aims and Objectives of the project.......................................................................................7
1. Main Objective....................................................................................................................7
2. Specific Objectives..............................................................................................................7
1.2 Project Plan............................................................................................................................7
2. Literature Review......................................................................................................................10
2.1 Internet of Things Architecture...........................................................................................10
2.2 Internet of Things Layers.....................................................................................................11
1. Perception layer.................................................................................................................12
2. Network layer....................................................................................................................12
3. Application layer...............................................................................................................13
2.3 IoT Applications..................................................................................................................13
2.4 Security Challenges in IoT Layers......................................................................................15
1. Perception Layer................................................................................................................15
2. Network Layer...................................................................................................................16
3. Application Layer..............................................................................................................17
2.5 Threats Facing IoT...............................................................................................................17
2.6 The fundamental differences between Internet of things and traditional Internet...............18
2.7 Security Directions for IoT layers.......................................................................................20
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER NETWORK SECURITY
3. Methodology..............................................................................................................................23
3.1 Introduction..........................................................................................................................23
3.2 Research Philosophy............................................................................................................23
3.3 Research Approach..............................................................................................................25
3.4 Research Design..................................................................................................................26
3.5 Data Collection Method.......................................................................................................27
1. Data sources.......................................................................................................................27
2. Data techniques..................................................................................................................28
3. Data Analysis Method.......................................................................................................29
3.6 Ethical Consideration...........................................................................................................29
3.7 Research Limitation.............................................................................................................30
3.8 Summary..............................................................................................................................31
4. Findings and Analysis................................................................................................................32
4.1 Introduction..........................................................................................................................32
4.2 Analysis...............................................................................................................................32
1. Analyzing the Fitbit Health Tracker..................................................................................33
2. Analyzing the BMW Connected Drive System for Automobiles.....................................36
3. Analysis of the HomeEasy Protocol for Home Automation.............................................37
4. Analyzing the Eye-Fi Internet-Connected SD-Card for Digital Cameras.........................41
4.3 Summary..............................................................................................................................43
3. Methodology..............................................................................................................................23
3.1 Introduction..........................................................................................................................23
3.2 Research Philosophy............................................................................................................23
3.3 Research Approach..............................................................................................................25
3.4 Research Design..................................................................................................................26
3.5 Data Collection Method.......................................................................................................27
1. Data sources.......................................................................................................................27
2. Data techniques..................................................................................................................28
3. Data Analysis Method.......................................................................................................29
3.6 Ethical Consideration...........................................................................................................29
3.7 Research Limitation.............................................................................................................30
3.8 Summary..............................................................................................................................31
4. Findings and Analysis................................................................................................................32
4.1 Introduction..........................................................................................................................32
4.2 Analysis...............................................................................................................................32
1. Analyzing the Fitbit Health Tracker..................................................................................33
2. Analyzing the BMW Connected Drive System for Automobiles.....................................36
3. Analysis of the HomeEasy Protocol for Home Automation.............................................37
4. Analyzing the Eye-Fi Internet-Connected SD-Card for Digital Cameras.........................41
4.3 Summary..............................................................................................................................43

5COMPUTER NETWORK SECURITY
5. Results and Discussion..............................................................................................................45
5.1 Introduction..........................................................................................................................45
5.2 Discussion............................................................................................................................45
1. Constraints.........................................................................................................................47
2. Current challenges.............................................................................................................49
3. Future challenges...............................................................................................................53
5.3 Summary..............................................................................................................................54
6. Conclusion and Recommendations............................................................................................56
6.1 Conclusion...........................................................................................................................56
6.2 Recommendations................................................................................................................58
References......................................................................................................................................61
Appendix – Practical Work...........................................................................................................77
Table of Figures
Figure 1: Interact the IoT with different things...............................................................................7
Figure 2: Generic service-oriented architecture for IoT................................................................11
Figure 3: Types of Research Philosophy.......................................................................................24
Figure 4: Fitbit activity tracker......................................................................................................34
Figure 5: BMW Connected Drive Application..............................................................................36
Figure 6: HomeEasy protocol packet format and security exploit state diagram..........................39
Figure 7: Microcontroller used for HomeEasy protocol packet transmission...............................40
Figure 8: The EyeFi Mobi SD card...............................................................................................41
Figure 9: Key setup procedure for EyeFi......................................................................................42
5. Results and Discussion..............................................................................................................45
5.1 Introduction..........................................................................................................................45
5.2 Discussion............................................................................................................................45
1. Constraints.........................................................................................................................47
2. Current challenges.............................................................................................................49
3. Future challenges...............................................................................................................53
5.3 Summary..............................................................................................................................54
6. Conclusion and Recommendations............................................................................................56
6.1 Conclusion...........................................................................................................................56
6.2 Recommendations................................................................................................................58
References......................................................................................................................................61
Appendix – Practical Work...........................................................................................................77
Table of Figures
Figure 1: Interact the IoT with different things...............................................................................7
Figure 2: Generic service-oriented architecture for IoT................................................................11
Figure 3: Types of Research Philosophy.......................................................................................24
Figure 4: Fitbit activity tracker......................................................................................................34
Figure 5: BMW Connected Drive Application..............................................................................36
Figure 6: HomeEasy protocol packet format and security exploit state diagram..........................39
Figure 7: Microcontroller used for HomeEasy protocol packet transmission...............................40
Figure 8: The EyeFi Mobi SD card...............................................................................................41
Figure 9: Key setup procedure for EyeFi......................................................................................42
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER NETWORK SECURITY
1. Introduction
The term “Internet of Things” was first used in 1999 by Kevin Ashton- former MIT’s
Auto-ID centre director in his Procter and Gamble presentation (Mario, 2016). Since then, the
term is so popular, an event that made the International Telecommunication Union (ITU) to use
the Internet of things in 2006 Internet Report (Mario, 2016). Internet of things (IoT), is a
convenient way of linking devices with each other. It connects numerous objects within a single
source of the network that assists in the completion of tasks requiring such connectivity. The
connection can be made remotely across the present network infrastructure, enabling the
integration of the physical world into computerized systems. In effect, it results in enhanced
efficiency, accuracy as well as minimized human intervention. The application of IoT is broad,
as such the devices connected to this system can be in cities, houses, and factories and even in
schools (Floarea et al., 2017). According to Zhang et al. (2011), Internet of things is an
interconnected network infrastructure of self-configured and intelligent nodes (things), which
interact with each other unconditionally. Studies on this matter estimate that the IoT will consist
of between 50 to 100 billion objects, shortly following the current trend, where, in 2017, 31%
increment of these devices was recorded (Sedrati and Mezrioui, 2017). None could predict these
figures 20 years back, therefore, if this is something to go with, the future of the Internet is
almost impossible to predict.
1. Introduction
The term “Internet of Things” was first used in 1999 by Kevin Ashton- former MIT’s
Auto-ID centre director in his Procter and Gamble presentation (Mario, 2016). Since then, the
term is so popular, an event that made the International Telecommunication Union (ITU) to use
the Internet of things in 2006 Internet Report (Mario, 2016). Internet of things (IoT), is a
convenient way of linking devices with each other. It connects numerous objects within a single
source of the network that assists in the completion of tasks requiring such connectivity. The
connection can be made remotely across the present network infrastructure, enabling the
integration of the physical world into computerized systems. In effect, it results in enhanced
efficiency, accuracy as well as minimized human intervention. The application of IoT is broad,
as such the devices connected to this system can be in cities, houses, and factories and even in
schools (Floarea et al., 2017). According to Zhang et al. (2011), Internet of things is an
interconnected network infrastructure of self-configured and intelligent nodes (things), which
interact with each other unconditionally. Studies on this matter estimate that the IoT will consist
of between 50 to 100 billion objects, shortly following the current trend, where, in 2017, 31%
increment of these devices was recorded (Sedrati and Mezrioui, 2017). None could predict these
figures 20 years back, therefore, if this is something to go with, the future of the Internet is
almost impossible to predict.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER NETWORK SECURITY
Figure 1: Interact the IoT with different things
(Source: Iotamy.com., 2018)
1.1 Aims and Objectives of the project
1. Main Objective
The main aim of this project is to assess the existing IoT security goals and challenges to
establish more advanced ways of protecting the system against any threat.
2. Specific Objectives
i. To identify the ways through which the Internet of things protects the collected data.
ii. To identify the differences between Internet of things and the traditional Internet.
iii. To identify the security challenges in the Internet of things.
1.2 Project Plan
Planning is an essential part of any successful study. It enables the researcher to
accomplish various tasks within the stipulated period. Besides, it allows for evaluation and
improvement in areas of less strength to achieve the set objectives. Research is an expensive
Figure 1: Interact the IoT with different things
(Source: Iotamy.com., 2018)
1.1 Aims and Objectives of the project
1. Main Objective
The main aim of this project is to assess the existing IoT security goals and challenges to
establish more advanced ways of protecting the system against any threat.
2. Specific Objectives
i. To identify the ways through which the Internet of things protects the collected data.
ii. To identify the differences between Internet of things and the traditional Internet.
iii. To identify the security challenges in the Internet of things.
1.2 Project Plan
Planning is an essential part of any successful study. It enables the researcher to
accomplish various tasks within the stipulated period. Besides, it allows for evaluation and
improvement in areas of less strength to achieve the set objectives. Research is an expensive
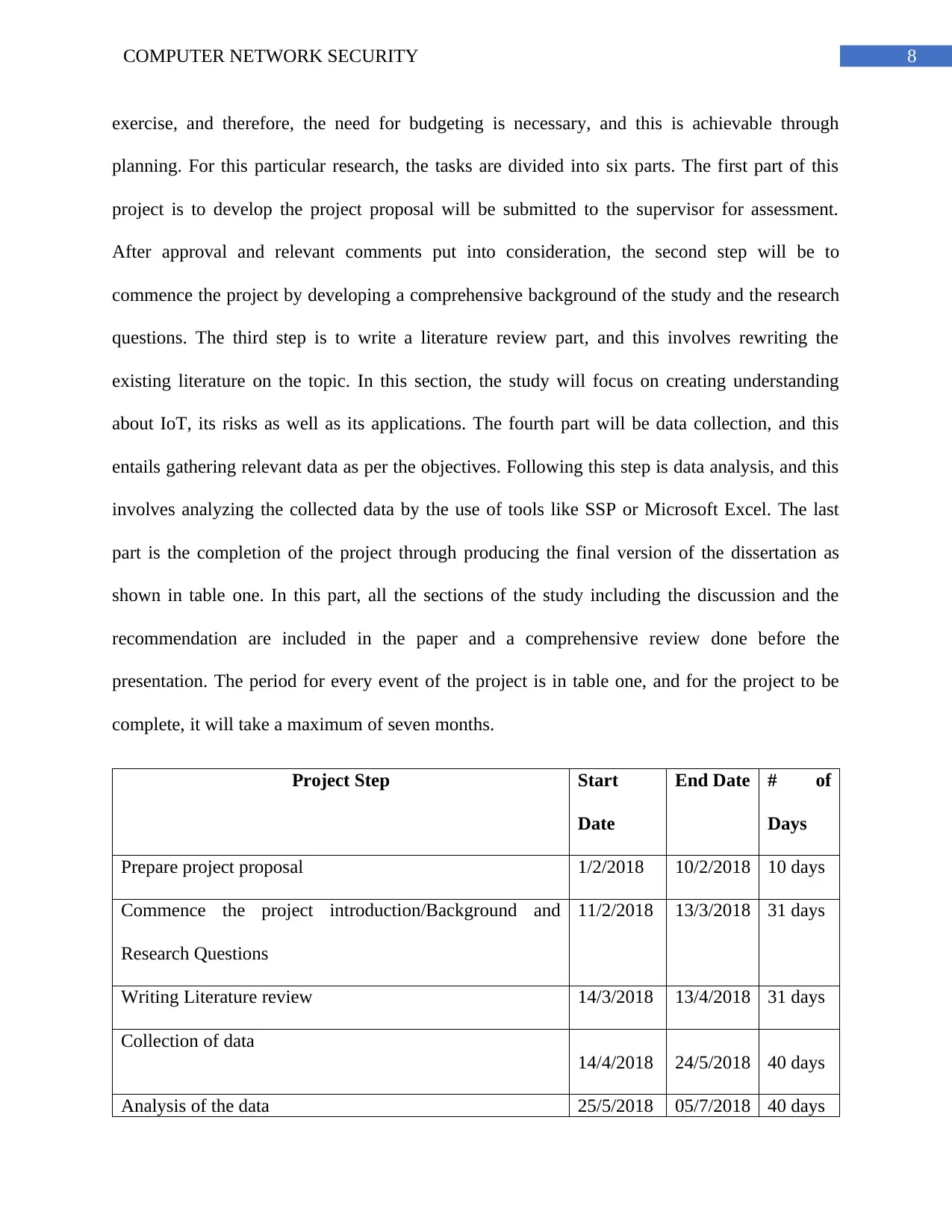
8COMPUTER NETWORK SECURITY
exercise, and therefore, the need for budgeting is necessary, and this is achievable through
planning. For this particular research, the tasks are divided into six parts. The first part of this
project is to develop the project proposal will be submitted to the supervisor for assessment.
After approval and relevant comments put into consideration, the second step will be to
commence the project by developing a comprehensive background of the study and the research
questions. The third step is to write a literature review part, and this involves rewriting the
existing literature on the topic. In this section, the study will focus on creating understanding
about IoT, its risks as well as its applications. The fourth part will be data collection, and this
entails gathering relevant data as per the objectives. Following this step is data analysis, and this
involves analyzing the collected data by the use of tools like SSP or Microsoft Excel. The last
part is the completion of the project through producing the final version of the dissertation as
shown in table one. In this part, all the sections of the study including the discussion and the
recommendation are included in the paper and a comprehensive review done before the
presentation. The period for every event of the project is in table one, and for the project to be
complete, it will take a maximum of seven months.
Project Step Start
Date
End Date # of
Days
Prepare project proposal 1/2/2018 10/2/2018 10 days
Commence the project introduction/Background and
Research Questions
11/2/2018 13/3/2018 31 days
Writing Literature review 14/3/2018 13/4/2018 31 days
Collection of data
14/4/2018 24/5/2018 40 days
Analysis of the data 25/5/2018 05/7/2018 40 days
exercise, and therefore, the need for budgeting is necessary, and this is achievable through
planning. For this particular research, the tasks are divided into six parts. The first part of this
project is to develop the project proposal will be submitted to the supervisor for assessment.
After approval and relevant comments put into consideration, the second step will be to
commence the project by developing a comprehensive background of the study and the research
questions. The third step is to write a literature review part, and this involves rewriting the
existing literature on the topic. In this section, the study will focus on creating understanding
about IoT, its risks as well as its applications. The fourth part will be data collection, and this
entails gathering relevant data as per the objectives. Following this step is data analysis, and this
involves analyzing the collected data by the use of tools like SSP or Microsoft Excel. The last
part is the completion of the project through producing the final version of the dissertation as
shown in table one. In this part, all the sections of the study including the discussion and the
recommendation are included in the paper and a comprehensive review done before the
presentation. The period for every event of the project is in table one, and for the project to be
complete, it will take a maximum of seven months.
Project Step Start
Date
End Date # of
Days
Prepare project proposal 1/2/2018 10/2/2018 10 days
Commence the project introduction/Background and
Research Questions
11/2/2018 13/3/2018 31 days
Writing Literature review 14/3/2018 13/4/2018 31 days
Collection of data
14/4/2018 24/5/2018 40 days
Analysis of the data 25/5/2018 05/7/2018 40 days
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
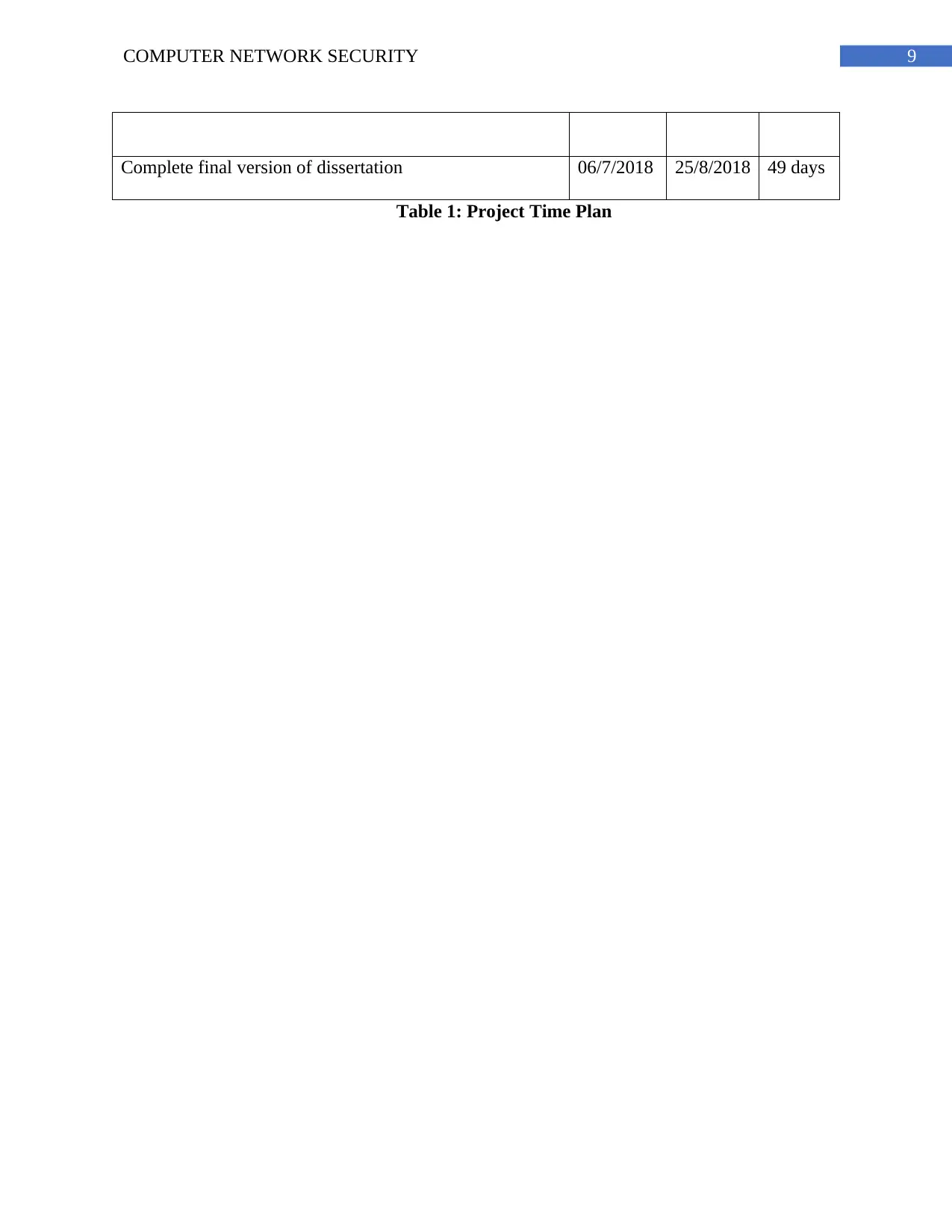
9COMPUTER NETWORK SECURITY
Complete final version of dissertation 06/7/2018 25/8/2018 49 days
Table 1: Project Time Plan
Complete final version of dissertation 06/7/2018 25/8/2018 49 days
Table 1: Project Time Plan
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER NETWORK SECURITY
2. Literature Review
2.1 Internet of Things Architecture
Hardware and software are the most basic Internet of things components. The hardware
component consists of Radio-Frequency Identification (RFID), Near Field Communication
(NFC) and Sensor Networks. RFID works by the use of radio- frequency electromagnetic fields
which allows the communication between the RFID tag and RFID reader. One form of the tag's
data is the Electronic Product Code (EPC) which IoT utilizes to identify an object. NFC, on the
other hand, is a new technology, and it uses a short-range communication standard. Through its
Unique Identification (UID) capability, NFC allows devices to communicate with each other in
touch or to fall close to one another. Conversely, Sensor Networks are used to observe particular
occurrences in the environment or weather. For instance, sensors can monitor temperature or
humidity.
Internet of things largely depend on the current hardware infrastructure, therefore, the
need to develop software that allows compatibility among various devices is vital. The
component that lies between the Internet of things hardware component and its applications is
middleware. In this case, middleware will include various devices that generate incredible
information. Consequently middleware component enables the developer to provide new
services without necessarily creating a distinctive code for every device. Internet of things
network currently used to display and index information on the web content is inconsistent, and
this calls for the need of Browsing. Browsing or searching enables the search for specific
information, and this solves the problems resulting from the extensive information produced by
2. Literature Review
2.1 Internet of Things Architecture
Hardware and software are the most basic Internet of things components. The hardware
component consists of Radio-Frequency Identification (RFID), Near Field Communication
(NFC) and Sensor Networks. RFID works by the use of radio- frequency electromagnetic fields
which allows the communication between the RFID tag and RFID reader. One form of the tag's
data is the Electronic Product Code (EPC) which IoT utilizes to identify an object. NFC, on the
other hand, is a new technology, and it uses a short-range communication standard. Through its
Unique Identification (UID) capability, NFC allows devices to communicate with each other in
touch or to fall close to one another. Conversely, Sensor Networks are used to observe particular
occurrences in the environment or weather. For instance, sensors can monitor temperature or
humidity.
Internet of things largely depend on the current hardware infrastructure, therefore, the
need to develop software that allows compatibility among various devices is vital. The
component that lies between the Internet of things hardware component and its applications is
middleware. In this case, middleware will include various devices that generate incredible
information. Consequently middleware component enables the developer to provide new
services without necessarily creating a distinctive code for every device. Internet of things
network currently used to display and index information on the web content is inconsistent, and
this calls for the need of Browsing. Browsing or searching enables the search for specific
information, and this solves the problems resulting from the extensive information produced by
11COMPUTER NETWORK SECURITY
IoT. Therefore, Browsing software is a requirement in the entire Internet of things so that its
users can benefit from the resulting functions.
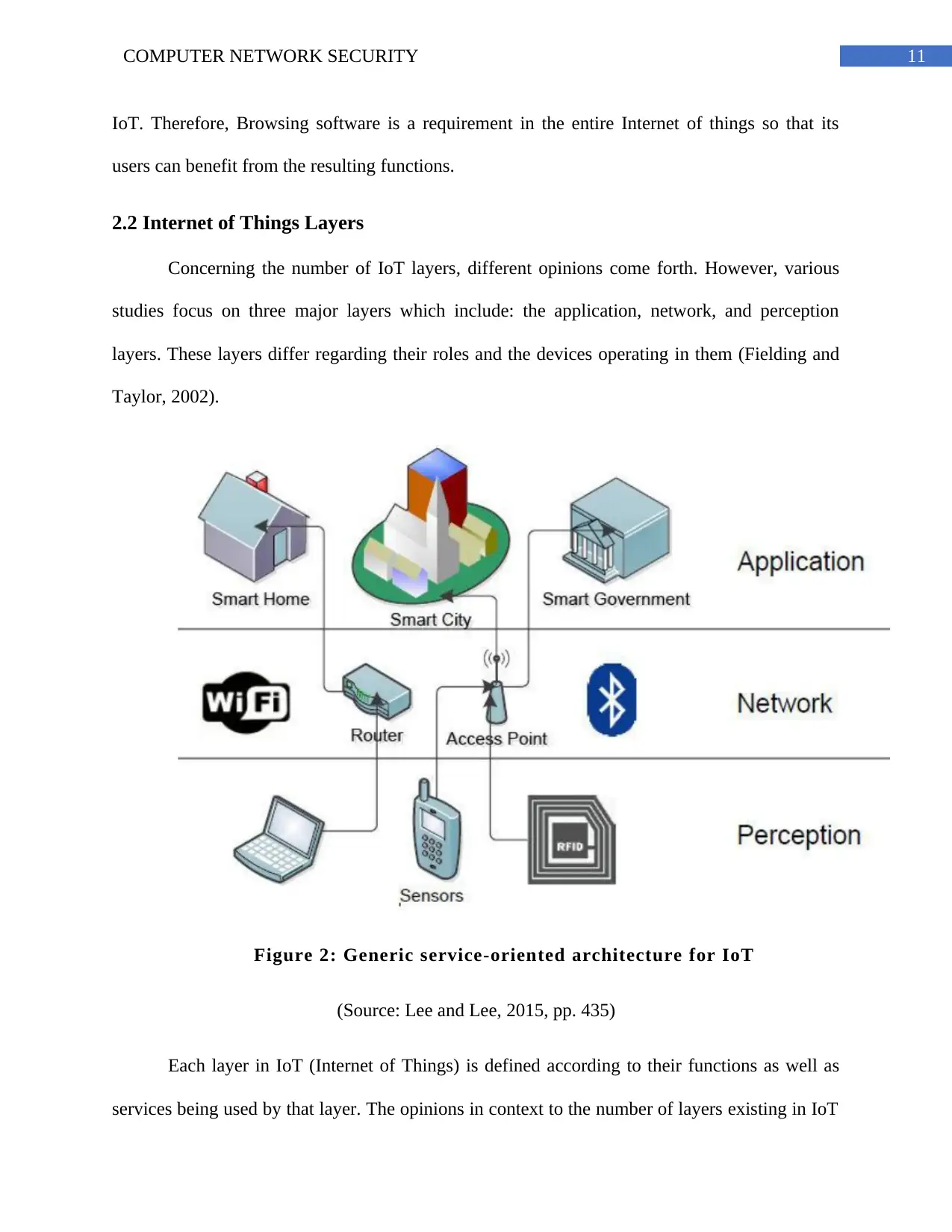
2.2 Internet of Things Layers
Concerning the number of IoT layers, different opinions come forth. However, various
studies focus on three major layers which include: the application, network, and perception
layers. These layers differ regarding their roles and the devices operating in them (Fielding and
Taylor, 2002).
Figure 2: Generic service-oriented architecture for IoT
(Source: Lee and Lee, 2015, pp. 435)
Each layer in IoT (Internet of Things) is defined according to their functions as well as
services being used by that layer. The opinions in context to the number of layers existing in IoT
IoT. Therefore, Browsing software is a requirement in the entire Internet of things so that its
users can benefit from the resulting functions.
2.2 Internet of Things Layers
Concerning the number of IoT layers, different opinions come forth. However, various
studies focus on three major layers which include: the application, network, and perception
layers. These layers differ regarding their roles and the devices operating in them (Fielding and
Taylor, 2002).
Figure 2: Generic service-oriented architecture for IoT
(Source: Lee and Lee, 2015, pp. 435)
Each layer in IoT (Internet of Things) is defined according to their functions as well as
services being used by that layer. The opinions in context to the number of layers existing in IoT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 81
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



