Change Management Procedures Report
VerifiedAdded on 2019/09/20
|10
|1432
|400
Report
AI Summary
This document outlines the procedures for managing change requests within an IT system. It details the process of raising a change request, including who can initiate it, the required approvals, and the necessary information to include. The document also describes the change control process, which involves reviewing the request, assigning it to a team, setting priorities, and documenting the work performed. The report includes sample change request and change control forms, along with guidelines for peer reviews and release approvals. The procedures are designed to track and control moderate production system changes, ensuring that all modifications are well-considered and communicated effectively.

Change Management Procedures
Introduction 3
Change Request Form 4
Raising a Change Request 4
Change Control Form 6
Appendix 1: Change Request Form 8
Appendix 2: Change Control Form 9
Acknowledgement 10
1 ICTSAS411 V1, Assignment 1
Introduction 3
Change Request Form 4
Raising a Change Request 4
Change Control Form 6
Appendix 1: Change Request Form 8
Appendix 2: Change Control Form 9
Acknowledgement 10
1 ICTSAS411 V1, Assignment 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Change Request and Change Control
These are used to request minor to medium system modifications. Anything
that will result in the system being modified, for example request system
patch, modifies scripts, install additional software.
Change Requests are managed internally and when completed are filed for
audit and documentation purposes.
2 ICTSAS411 V1, Assignment 1
Change Request and Change Control
These are used to request minor to medium system modifications. Anything
that will result in the system being modified, for example request system
patch, modifies scripts, install additional software.
Change Requests are managed internally and when completed are filed for
audit and documentation purposes.
2 ICTSAS411 V1, Assignment 1

Change Request Form
Raising a Change Request
A Change Request can be raised by anyone who uses, is affected by,
maintains or administers an IT system. This includes day to day users who
want to initiate a modification, administrators who want to correct or extend
functionality and systems owners who want to upgrade or modify
applications.
The request must be supported by either the Systems Owner (delegate) or, in
special cases, a Manager in IT Services or IT Director. The systems owner
is the usual authority for approving change but in exceptional circumstances
the Manager IT Services or IT Director can approve changes to a system.
These instances might occur when there is immediate threat to a system (or
other systems) and the Systems Owner cannot be readily contacted.
Change Request forms do not replace Helpdesk requests, regular
maintenance or project work but are intended to track and control moderate
production system changes.
Change Request description
The person raising the Change Request should fully describe the work being
requested to the best of their ability. In most cases this will be expressed as
business requirements and should include the overall objective and the
benefits that the modification will bring.
If the person raising the request knows, or can describe technical aspects of
the change then these should also be included. Eg
A user request to upgrade the web servers might simply state web server
performance is too slow and is causing processing errors when
attempting to do data entry in “X” screen doing “Y” work.
A Systems Administrator might raise a Change Request and refer to
specific patch identifiers or software versions and detail how the
work is to be performed.
3 ICTSAS411 V1, Assignment 1
Raising a Change Request
A Change Request can be raised by anyone who uses, is affected by,
maintains or administers an IT system. This includes day to day users who
want to initiate a modification, administrators who want to correct or extend
functionality and systems owners who want to upgrade or modify
applications.
The request must be supported by either the Systems Owner (delegate) or, in
special cases, a Manager in IT Services or IT Director. The systems owner
is the usual authority for approving change but in exceptional circumstances
the Manager IT Services or IT Director can approve changes to a system.
These instances might occur when there is immediate threat to a system (or
other systems) and the Systems Owner cannot be readily contacted.
Change Request forms do not replace Helpdesk requests, regular
maintenance or project work but are intended to track and control moderate
production system changes.
Change Request description
The person raising the Change Request should fully describe the work being
requested to the best of their ability. In most cases this will be expressed as
business requirements and should include the overall objective and the
benefits that the modification will bring.
If the person raising the request knows, or can describe technical aspects of
the change then these should also be included. Eg
A user request to upgrade the web servers might simply state web server
performance is too slow and is causing processing errors when
attempting to do data entry in “X” screen doing “Y” work.
A Systems Administrator might raise a Change Request and refer to
specific patch identifiers or software versions and detail how the
work is to be performed.
3 ICTSAS411 V1, Assignment 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Business priority
The person requesting the service should set the priority of the work to the
business unit. Be reasonable, everything cannot be critical. ITS will try to
comply with the delivery of the service within the priority specified but is
constrained by resource and systems availability. In some cases ITS will
need to reassign priority in conjunction with the systems owner.
Priority settings are:-
Low – Will be done when resources and time permits.
Standard– Is performed at the next, appropriate scheduled maintenance
period.
Urgent – Requires coordinated downtime at earliest the opportunity
outside (maybe inside) normal business ours.
Critical – Requires immediate attention and possible disruption to
service during business hours. ITS will use this authority to
discontinue production services with minimal co-ordination and
notice, eg it is discovered that the use of an application is causing
damage to data.
Required date
This is the expected due date and must be set with good reason and
practicality. Everything cannot be done today!
Systems 0wners Information
The system owner is the person with overall responsibility for the system.
This may be the head of a division, senior or a line manager. The
responsibility for systems can be delegate to another individual who can
then perform the tasks of a systems owner and with their authority.
4 ICTSAS411 V1, Assignment 1
The person requesting the service should set the priority of the work to the
business unit. Be reasonable, everything cannot be critical. ITS will try to
comply with the delivery of the service within the priority specified but is
constrained by resource and systems availability. In some cases ITS will
need to reassign priority in conjunction with the systems owner.
Priority settings are:-
Low – Will be done when resources and time permits.
Standard– Is performed at the next, appropriate scheduled maintenance
period.
Urgent – Requires coordinated downtime at earliest the opportunity
outside (maybe inside) normal business ours.
Critical – Requires immediate attention and possible disruption to
service during business hours. ITS will use this authority to
discontinue production services with minimal co-ordination and
notice, eg it is discovered that the use of an application is causing
damage to data.
Required date
This is the expected due date and must be set with good reason and
practicality. Everything cannot be done today!
Systems 0wners Information
The system owner is the person with overall responsibility for the system.
This may be the head of a division, senior or a line manager. The
responsibility for systems can be delegate to another individual who can
then perform the tasks of a systems owner and with their authority.
4 ICTSAS411 V1, Assignment 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Change Control Form
Systems services review the request and determine if it is feasible and
practicable to continue. This decision making process is performed in
conjunction with the systems owner/delegate and will consider things such
as IT Security, administration practices, current operational practices, etc. If
service is declined a set of reasons will be provided.
Assigned
To proceed with the request, it is assigned to an individual or group who
will perform the tasks or behave as co-ordinator should additional
individuals/groups need to be involved.
Authorised and IT priority
IT priorities are set by the IT manager and reflect the work load of the group
and a comparison to other activity being undertaken at the time. Where the
IT priority differs from the Business Priority or the requested date cannot be
achieved then the Requesting User is informed.
Start and finish dates
The start and finish dates are estimated against work load and priorities to
become the base line for the task. The actual start and finish dates are
recorded by the person/group responsible for performing the task.
Description of work performed
The work performed to service the request is described in reasonable detail.
It will include such things as patch identifiers; software used or installed;
hardware that was modified etc.
It may include GO/NO GO points if processing inside a tight time frame,
database schemas, flowchart, job task list, or anything that demonstrates the
job has been well considered and communicated.
5 ICTSAS411 V1, Assignment 1
Systems services review the request and determine if it is feasible and
practicable to continue. This decision making process is performed in
conjunction with the systems owner/delegate and will consider things such
as IT Security, administration practices, current operational practices, etc. If
service is declined a set of reasons will be provided.
Assigned
To proceed with the request, it is assigned to an individual or group who
will perform the tasks or behave as co-ordinator should additional
individuals/groups need to be involved.
Authorised and IT priority
IT priorities are set by the IT manager and reflect the work load of the group
and a comparison to other activity being undertaken at the time. Where the
IT priority differs from the Business Priority or the requested date cannot be
achieved then the Requesting User is informed.
Start and finish dates
The start and finish dates are estimated against work load and priorities to
become the base line for the task. The actual start and finish dates are
recorded by the person/group responsible for performing the task.
Description of work performed
The work performed to service the request is described in reasonable detail.
It will include such things as patch identifiers; software used or installed;
hardware that was modified etc.
It may include GO/NO GO points if processing inside a tight time frame,
database schemas, flowchart, job task list, or anything that demonstrates the
job has been well considered and communicated.
5 ICTSAS411 V1, Assignment 1
Reviews
Peer reviews are meetings of members of the assignee’s team where the
modifications are discussed. The review looks at weather all points are
covered, that the modifications are compatible with other systems and
requirements or policies and procedures. He peer review can also include
people from outside the group when appropriate.
The specific group reviews, such as IT Security, Operations, desktop, etc are
included as necessary.
Release approval
Depending on the type of work performed the final step of the change
request is approved by one, some or all of the managers/directors listed
Job closed
The job is closed when all the tasks are complete, the changes are signed off
and the modifications are now part of the production systems. The change
control form and all associated material and references are filed in the
Change control book/file in the local area.
6 ICTSAS411 V1, Assignment 1
Peer reviews are meetings of members of the assignee’s team where the
modifications are discussed. The review looks at weather all points are
covered, that the modifications are compatible with other systems and
requirements or policies and procedures. He peer review can also include
people from outside the group when appropriate.
The specific group reviews, such as IT Security, Operations, desktop, etc are
included as necessary.
Release approval
Depending on the type of work performed the final step of the change
request is approved by one, some or all of the managers/directors listed
Job closed
The job is closed when all the tasks are complete, the changes are signed off
and the modifications are now part of the production systems. The change
control form and all associated material and references are filed in the
Change control book/file in the local area.
6 ICTSAS411 V1, Assignment 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
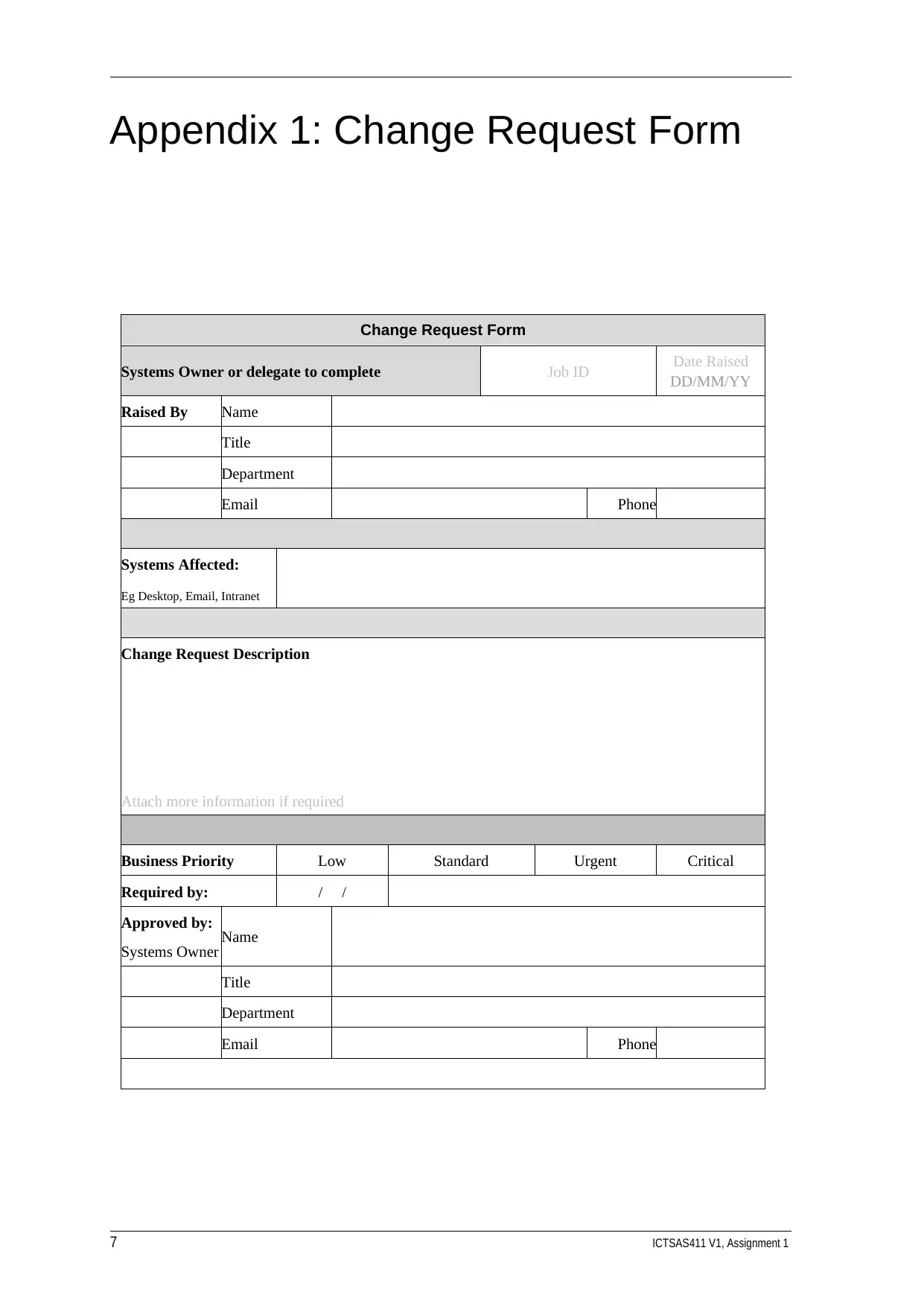
Appendix 1: Change Request Form
Change Request Form
Systems Owner or delegate to complete Job ID Date Raised
DD/MM/YY
Raised By Name
Title
Department
Email Phone
Systems Affected:
Eg Desktop, Email, Intranet
Change Request Description
Attach more information if required
Business Priority Low Standard Urgent Critical
Required by: / /
Approved by:
Systems Owner Name
Title
Department
Email Phone
7 ICTSAS411 V1, Assignment 1
Change Request Form
Systems Owner or delegate to complete Job ID Date Raised
DD/MM/YY
Raised By Name
Title
Department
Email Phone
Systems Affected:
Eg Desktop, Email, Intranet
Change Request Description
Attach more information if required
Business Priority Low Standard Urgent Critical
Required by: / /
Approved by:
Systems Owner Name
Title
Department
Email Phone
7 ICTSAS411 V1, Assignment 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Appendix 2: Change Control Form
Change Control Form
Section 1 - IT Services to Complete Job ID Received: DD/MM/YY
Assigned to
Authorised / /
IT Priority Low Standard Urgent Critical
Estimated Start / / Estimated Finish / /
Actual Start / / Actual Finish / /
Section 2 - Work Progress
Description of Work Performed / /
Description of Work Performed / /
Description of Work Performed / /
Description of Work Performed / /
Attach more information if required
Section 3 - Peer Reviews
Team/Peer Reviewer’s comment / /
Team/Peer Reviewer’s comment / /
Other members as required
Desktop / /
IT Security / /
Networks / /
/ /
Section 4 - Release Approval
Manager – IT Services / /
Director – IT Services / /
/ /
Section 5 - Job Closed
Completed By: / /
8 ICTSAS411 V1, Assignment 1
Change Control Form
Section 1 - IT Services to Complete Job ID Received: DD/MM/YY
Assigned to
Authorised / /
IT Priority Low Standard Urgent Critical
Estimated Start / / Estimated Finish / /
Actual Start / / Actual Finish / /
Section 2 - Work Progress
Description of Work Performed / /
Description of Work Performed / /
Description of Work Performed / /
Description of Work Performed / /
Attach more information if required
Section 3 - Peer Reviews
Team/Peer Reviewer’s comment / /
Team/Peer Reviewer’s comment / /
Other members as required
Desktop / /
IT Security / /
Networks / /
/ /
Section 4 - Release Approval
Manager – IT Services / /
Director – IT Services / /
/ /
Section 5 - Job Closed
Completed By: / /
8 ICTSAS411 V1, Assignment 1

9 ICTSAS411 V1, Assignment 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Acknowledgement
The procedures document is from:
Information Technology Services (ITS) Macquarie University (2007),
Change request form (online).
Available: http://www.its.mq.edu.au/web/services/changereq.pdf [Accessed
2 October 2007].
10 ICTSAS411 V1, Assignment 1
The procedures document is from:
Information Technology Services (ITS) Macquarie University (2007),
Change request form (online).
Available: http://www.its.mq.edu.au/web/services/changereq.pdf [Accessed
2 October 2007].
10 ICTSAS411 V1, Assignment 1
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

