ITC506 Assignment 1: Early Launch Scenario Ethics Analysis
VerifiedAdded on 2020/03/04
|6
|2373
|30
Homework Assignment
AI Summary
This assignment analyzes an ethical dilemma arising from the early launch of software, as instructed by the CEO, without completing the encryption process. The student utilizes the 'Doing Ethics Technique' to identify the facts, non-ethical issues, stakeholders (client, company, employees, and users), and ethical concerns, including data security, privacy, and the implications of potential data breaches. The analysis explores the importance of encryption, the risks of data insecurity, and the potential impact on the company's reputation, client relationships, and legal liabilities. The student evaluates different options, such as seeking an extension to ensure proper security measures, and ultimately argues that prioritizing the client's security and the software's stability is the best approach to maintain data integrity and ethical standards. The assignment also includes a detailed discussion of the ethical issues involved and provides references to relevant literature.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
Early Launch/Scenario3
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:
Early Launch/Scenario3
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Early Launch/Scenario3
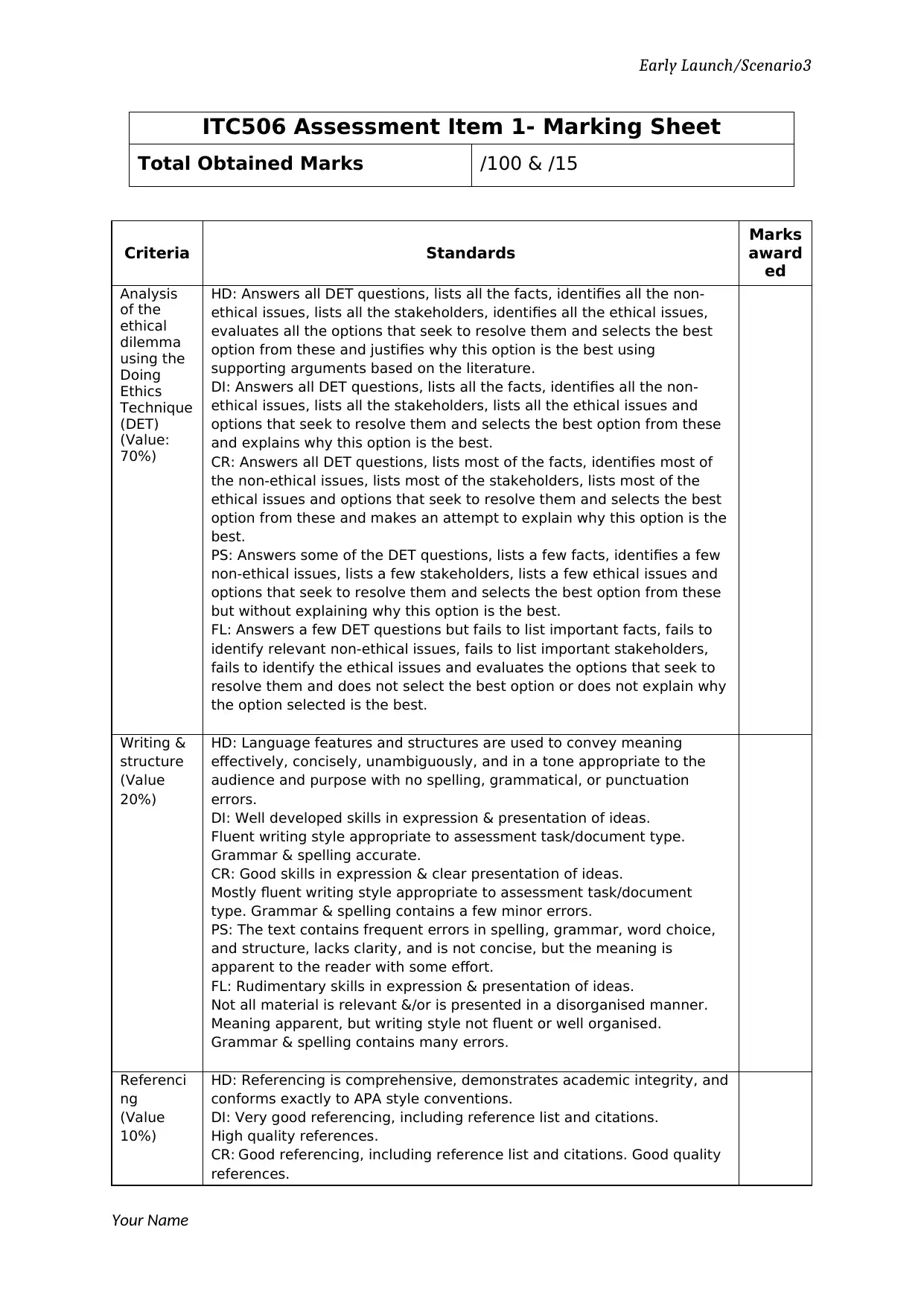
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
Your Name
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
Your Name
Early Launch/Scenario3
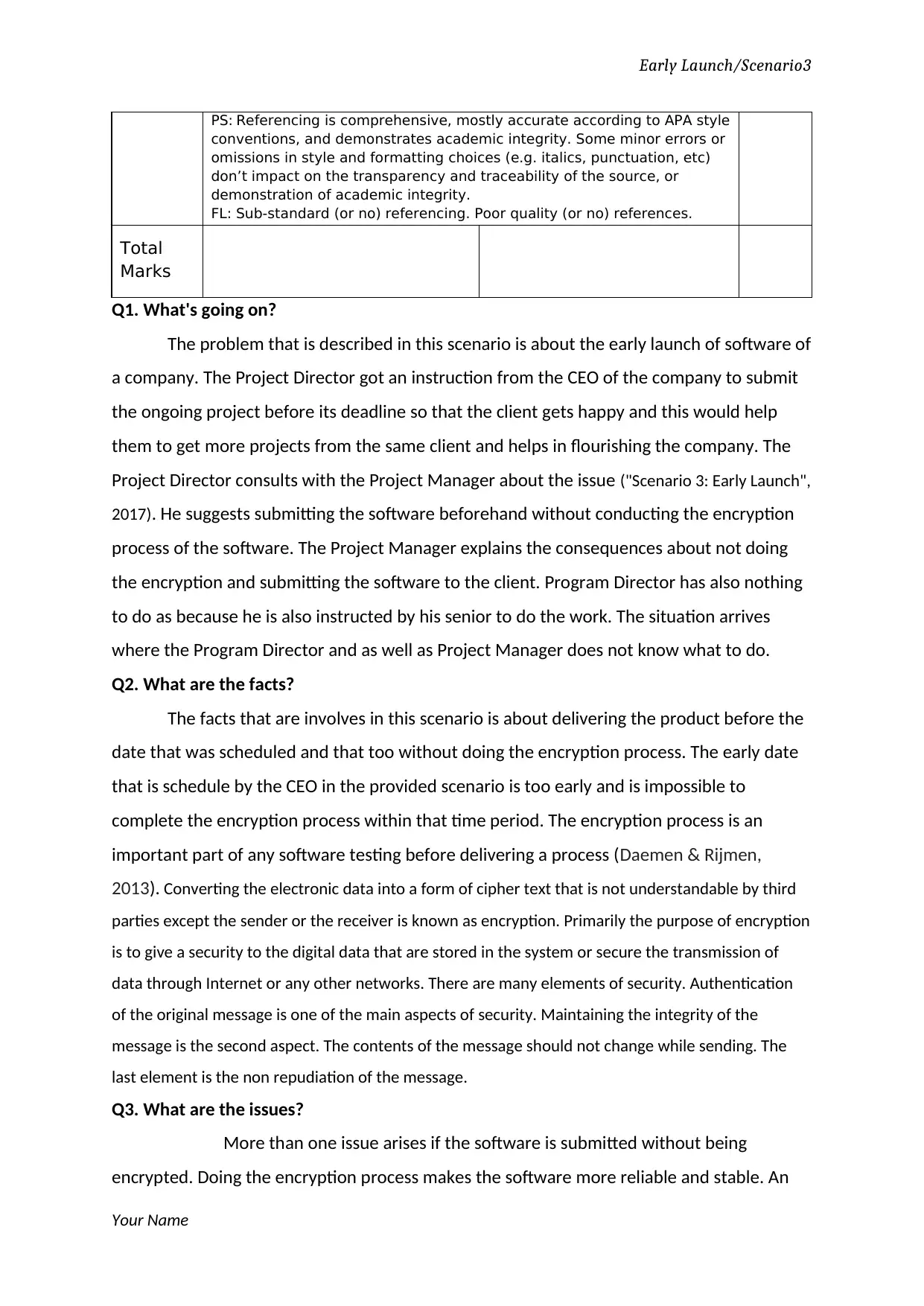
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
The problem that is described in this scenario is about the early launch of software of
a company. The Project Director got an instruction from the CEO of the company to submit
the ongoing project before its deadline so that the client gets happy and this would help
them to get more projects from the same client and helps in flourishing the company. The
Project Director consults with the Project Manager about the issue ("Scenario 3: Early Launch",
2017). He suggests submitting the software beforehand without conducting the encryption
process of the software. The Project Manager explains the consequences about not doing
the encryption and submitting the software to the client. Program Director has also nothing
to do as because he is also instructed by his senior to do the work. The situation arrives
where the Program Director and as well as Project Manager does not know what to do.
Q2. What are the facts?
The facts that are involves in this scenario is about delivering the product before the
date that was scheduled and that too without doing the encryption process. The early date
that is schedule by the CEO in the provided scenario is too early and is impossible to
complete the encryption process within that time period. The encryption process is an
important part of any software testing before delivering a process (Daemen & Rijmen,
2013). Converting the electronic data into a form of cipher text that is not understandable by third
parties except the sender or the receiver is known as encryption. Primarily the purpose of encryption
is to give a security to the digital data that are stored in the system or secure the transmission of
data through Internet or any other networks. There are many elements of security. Authentication
of the original message is one of the main aspects of security. Maintaining the integrity of the
message is the second aspect. The contents of the message should not change while sending. The
last element is the non repudiation of the message.
Q3. What are the issues?
More than one issue arises if the software is submitted without being
encrypted. Doing the encryption process makes the software more reliable and stable. An
Your Name
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
The problem that is described in this scenario is about the early launch of software of
a company. The Project Director got an instruction from the CEO of the company to submit
the ongoing project before its deadline so that the client gets happy and this would help
them to get more projects from the same client and helps in flourishing the company. The
Project Director consults with the Project Manager about the issue ("Scenario 3: Early Launch",
2017). He suggests submitting the software beforehand without conducting the encryption
process of the software. The Project Manager explains the consequences about not doing
the encryption and submitting the software to the client. Program Director has also nothing
to do as because he is also instructed by his senior to do the work. The situation arrives
where the Program Director and as well as Project Manager does not know what to do.
Q2. What are the facts?
The facts that are involves in this scenario is about delivering the product before the
date that was scheduled and that too without doing the encryption process. The early date
that is schedule by the CEO in the provided scenario is too early and is impossible to
complete the encryption process within that time period. The encryption process is an
important part of any software testing before delivering a process (Daemen & Rijmen,
2013). Converting the electronic data into a form of cipher text that is not understandable by third
parties except the sender or the receiver is known as encryption. Primarily the purpose of encryption
is to give a security to the digital data that are stored in the system or secure the transmission of
data through Internet or any other networks. There are many elements of security. Authentication
of the original message is one of the main aspects of security. Maintaining the integrity of the
message is the second aspect. The contents of the message should not change while sending. The
last element is the non repudiation of the message.
Q3. What are the issues?
More than one issue arises if the software is submitted without being
encrypted. Doing the encryption process makes the software more reliable and stable. An
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Early Launch/Scenario3
unstable project may hamper the reputation of the company (Tasch et al., 2014). The mainly
issue that arises is regarding the data security and privacy of the data. The software may face data
insecurity if the encryption is not done. The main motive of encryption is to provide proper
authentication, maintain integrity of the data and also look after the non-repudiation of the
software. The chances of getting hacked increases if the software is not encrypted (Brech et al.,
2017). The software becomes unstable which may lead to future risk of the client.
Q4. Who is affected?
The person who directly gets affected by this issue is the client whose project
is undergoing and the company who is undertaking the project. The client gives the tender to
the company of doing the software within a fixed time period. If the company does not looks after
the security of the software they are delivering to the client, then the client faces the problem in
future. The data integrity of the client gets lost if there is no security of the software (Dotcenko,
Vladyko & Letenko, 2014). Consequently if the customer gets affected, the company also gets
affected. The reputation of the company gets lost. The particular customer will not provide any other
projects to that company and they may not get any similar kinds of software in future. The company
loses the trust of the client. The company gets ruined by getting a legal notice from the court
regarding the fraud issue.
The persons who are indirectly affected are the employees of the company and all the users
who use the software.
Q5. What are the ethical issues and their implications?
The ethical issues that can arrive if the encryption is not done are some functions of
the system may not work properly creating a problem among the users about
authenticating the software. The main ethical issue of the data encryption is to protect the data in
terms of availability, integrity and confidentiality. The data breach of information may lead to great
extend of economic cost (Shin et al., 2013). The data that gets breached are much more valuable
than other hardware of a system or software. The loss of data security leads to emotional harm.
Breaches of software or system may even lead to death or injury which occurs in safety critical
systems (Daniel et al., 2014). To protect the data in terms of availability, integrity and
confidentiality is also involved in the issues if the system is not tested. The data breach of
information may lead to great extend of economic cost (Shmueli et al., 2014). The data that gets
breached are much more valuable than other hardware of a system or software. The loss of data
security leads to emotional harm. Breaches of software or system may even lead to death or injury
Your Name
unstable project may hamper the reputation of the company (Tasch et al., 2014). The mainly
issue that arises is regarding the data security and privacy of the data. The software may face data
insecurity if the encryption is not done. The main motive of encryption is to provide proper
authentication, maintain integrity of the data and also look after the non-repudiation of the
software. The chances of getting hacked increases if the software is not encrypted (Brech et al.,
2017). The software becomes unstable which may lead to future risk of the client.
Q4. Who is affected?
The person who directly gets affected by this issue is the client whose project
is undergoing and the company who is undertaking the project. The client gives the tender to
the company of doing the software within a fixed time period. If the company does not looks after
the security of the software they are delivering to the client, then the client faces the problem in
future. The data integrity of the client gets lost if there is no security of the software (Dotcenko,
Vladyko & Letenko, 2014). Consequently if the customer gets affected, the company also gets
affected. The reputation of the company gets lost. The particular customer will not provide any other
projects to that company and they may not get any similar kinds of software in future. The company
loses the trust of the client. The company gets ruined by getting a legal notice from the court
regarding the fraud issue.
The persons who are indirectly affected are the employees of the company and all the users
who use the software.
Q5. What are the ethical issues and their implications?
The ethical issues that can arrive if the encryption is not done are some functions of
the system may not work properly creating a problem among the users about
authenticating the software. The main ethical issue of the data encryption is to protect the data in
terms of availability, integrity and confidentiality. The data breach of information may lead to great
extend of economic cost (Shin et al., 2013). The data that gets breached are much more valuable
than other hardware of a system or software. The loss of data security leads to emotional harm.
Breaches of software or system may even lead to death or injury which occurs in safety critical
systems (Daniel et al., 2014). To protect the data in terms of availability, integrity and
confidentiality is also involved in the issues if the system is not tested. The data breach of
information may lead to great extend of economic cost (Shmueli et al., 2014). The data that gets
breached are much more valuable than other hardware of a system or software. The loss of data
security leads to emotional harm. Breaches of software or system may even lead to death or injury
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Early Launch/Scenario3
which occurs in safety critical systems (Brakerski & Vaikuntanathan, 2014). The implication that
mainly comes from the fact is that each and every function of the system should be checked
separately to avoid the implications.
Q6. What could have been done about it?
More than one way of solutions are available that can be done. As security of the
customer is the main issue related with the software, so that should be kept in mind. The
software should be kept stable and secure. The client should be satisfied and should be given
assurance about the security of the software they are delivering. Without securing the software,
delivering the project before its scheduled date is not at a work of pride. If the software is good
enough and stable, more such assignments would come to the company. For that no need to deliver
the project before the scheduled date without securing the process.
Q7. What are the options?
The options that are highlighted in the scenario are as follows.
1. The Project Manager suggests the Program Director to convince the CEO of the
company to ask for one month extension of the project and deliver the project with
a stable condition.
2. When the Project Manager gives the suggestion to the Program Director to have a
talk with the CEO of the company to extend the deadline, the Program Director
refuses to do so and orders the Manager to do the way as suggested by the seniors.
3. Lastly, the Program Manager succeeds in convincing the Project Manager to submit
the project as stated by the CEO beforehand. He pressurize the Manager so that he
gets all the remaining work done by the his team members and deliver the software
without the encryption process done. He suggests that the Manager may work with
the encryption process after the delivery and can attach the files afterwards.
Q8. Which option is the best and why?
The best of all the option is the option where the Program Manager suggests getting an
extension of one month and submitting the software without any drawback. Security of the
client should the main aspect of the company and it is the best thing to do.
Your Name
which occurs in safety critical systems (Brakerski & Vaikuntanathan, 2014). The implication that
mainly comes from the fact is that each and every function of the system should be checked
separately to avoid the implications.
Q6. What could have been done about it?
More than one way of solutions are available that can be done. As security of the
customer is the main issue related with the software, so that should be kept in mind. The
software should be kept stable and secure. The client should be satisfied and should be given
assurance about the security of the software they are delivering. Without securing the software,
delivering the project before its scheduled date is not at a work of pride. If the software is good
enough and stable, more such assignments would come to the company. For that no need to deliver
the project before the scheduled date without securing the process.
Q7. What are the options?
The options that are highlighted in the scenario are as follows.
1. The Project Manager suggests the Program Director to convince the CEO of the
company to ask for one month extension of the project and deliver the project with
a stable condition.
2. When the Project Manager gives the suggestion to the Program Director to have a
talk with the CEO of the company to extend the deadline, the Program Director
refuses to do so and orders the Manager to do the way as suggested by the seniors.
3. Lastly, the Program Manager succeeds in convincing the Project Manager to submit
the project as stated by the CEO beforehand. He pressurize the Manager so that he
gets all the remaining work done by the his team members and deliver the software
without the encryption process done. He suggests that the Manager may work with
the encryption process after the delivery and can attach the files afterwards.
Q8. Which option is the best and why?
The best of all the option is the option where the Program Manager suggests getting an
extension of one month and submitting the software without any drawback. Security of the
client should the main aspect of the company and it is the best thing to do.
Your Name

Early Launch/Scenario3
References
Brakerski, Z., & Vaikuntanathan, V. (2014). Efficient fully homomorphic encryption from
(standard) LWE. SIAM Journal on Computing, 43(2), 831-871.
Brech, B. L., Crowder, S. W., Franke, H., Halim, N., Hogstrom, M. R., Li, C. S., ... & Williams,
M. D. (2017). U.S. Patent Application No. 15/474,207.
Daemen, J., & Rijmen, V. (2013). The design of Rijndael: AES-the advanced
encryptionstandard. Springer Science & Business Media.
Daniel, W. K., Chen, D., Liu, Q., Wang, F., & Wei, Z. (2014, September). Emerging issues in
cloud storage security: Encryption, key management, data redundancy, trust
mechanism. In International Conference, MISNC (pp. 297-310). Springer, Berlin,
Heidelberg.
Dotcenko, S., Vladyko, A., & Letenko, I. (2014, February). A fuzzy logic-based information
security management for software-defined networks. In Advanced Communication
Technology (ICACT), 2014 16th International Conference on (pp. 167-171). IEEE.
Scenario 3: Early Launch. (2017). YouTube. Retrieved 6 August 2017, from
https://www.youtube.com/watch?v=v5M7ohdZ6qA
Shin, S., Porras, P. A., Yegneswaran, V., Fong, M. W., Gu, G., & Tyson, M. (2013, February).
FRESCO: Modular Composable Security Services for Software-Defined Networks.
In NDSS.
Shmueli, E., Vaisenberg, R., Gudes, E., & Elovici, Y. (2014). Implementing a database
encryption solution, design and implementation issues. Computers & security, 44,
33-50.
Tasch, M., Khondoker, R., Marx, R., & Bayarou, K. (2014, November). Security analysis of
security applications for software defined networks. In Proceedings of the AINTEC
2014 on Asian Internet Engineering Conference(p. 23). ACM.
Your Name
References
Brakerski, Z., & Vaikuntanathan, V. (2014). Efficient fully homomorphic encryption from
(standard) LWE. SIAM Journal on Computing, 43(2), 831-871.
Brech, B. L., Crowder, S. W., Franke, H., Halim, N., Hogstrom, M. R., Li, C. S., ... & Williams,
M. D. (2017). U.S. Patent Application No. 15/474,207.
Daemen, J., & Rijmen, V. (2013). The design of Rijndael: AES-the advanced
encryptionstandard. Springer Science & Business Media.
Daniel, W. K., Chen, D., Liu, Q., Wang, F., & Wei, Z. (2014, September). Emerging issues in
cloud storage security: Encryption, key management, data redundancy, trust
mechanism. In International Conference, MISNC (pp. 297-310). Springer, Berlin,
Heidelberg.
Dotcenko, S., Vladyko, A., & Letenko, I. (2014, February). A fuzzy logic-based information
security management for software-defined networks. In Advanced Communication
Technology (ICACT), 2014 16th International Conference on (pp. 167-171). IEEE.
Scenario 3: Early Launch. (2017). YouTube. Retrieved 6 August 2017, from
https://www.youtube.com/watch?v=v5M7ohdZ6qA
Shin, S., Porras, P. A., Yegneswaran, V., Fong, M. W., Gu, G., & Tyson, M. (2013, February).
FRESCO: Modular Composable Security Services for Software-Defined Networks.
In NDSS.
Shmueli, E., Vaisenberg, R., Gudes, E., & Elovici, Y. (2014). Implementing a database
encryption solution, design and implementation issues. Computers & security, 44,
33-50.
Tasch, M., Khondoker, R., Marx, R., & Bayarou, K. (2014, November). Security analysis of
security applications for software defined networks. In Proceedings of the AINTEC
2014 on Asian Internet Engineering Conference(p. 23). ACM.
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





