Computer Security Report: Protecting Cheswold Park Hospital's Data
VerifiedAdded on 2021/02/21
|10
|2742
|144
Report
AI Summary
This report provides a comprehensive overview of computer security, focusing on incident response and data protection strategies for Cheswold Park Hospital. It begins by defining computer security and its importance, addressing vulnerabilities like the WannaCry ransomware attack and the assumptions made regarding its impact. The report details technical and non-technical vulnerabilities, how attacks penetrate networks, and the importance of incident response plans. It outlines steps for securing data through encryption and backups, along with detailed incident response plans, including preparation, identification, containment, eradication, recovery, review, and lessons learned. Furthermore, the report provides insights into recovering infected files and eliminating infections from systems. It also covers safeguarding systems, data, and applications, including essential security controls, techniques, and strategies for protecting against future attacks, such as data encryption, access controls, and regular system updates. The report emphasizes the need for proactive measures to ensure data integrity and system security, making it a valuable resource for understanding and implementing effective computer security practices.

Computer Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
Overview..........................................................................................................................................1
Incident response ............................................................................................................................2
Safeguarding systems, data and applications...................................................................................5
Network Design for Cheswold Park Hospital.............................................................................6
Conclusion.......................................................................................................................................6
References........................................................................................................................................8
INTRODUCTION...........................................................................................................................1
Overview..........................................................................................................................................1
Incident response ............................................................................................................................2
Safeguarding systems, data and applications...................................................................................5
Network Design for Cheswold Park Hospital.............................................................................6
Conclusion.......................................................................................................................................6
References........................................................................................................................................8

INTRODUCTION
Computer security refers to process of securing computer systems from any kind of
damage or theft to electronic data, software or hardware. Generally, it denotes controls that are
made for ensuring confidentiality, availability and integrity of all the components of systems
(Basta and et. al, 2013). Security is related with precautions for vandalism, theft of data, fraud
like wanna cry and invasion of privacy. WannaCry is a ransomware attack in which data is
encrypted and ransom is demanded for the same. This report is based on Cheswold Park
Hospital, which deals with providing care to personality disorder, mental illness as well as
intellectual disabilities. This report deals with some assumptions, ways in which data can be
secured and protection of data, applications as well as systems.
Overview
Assumptions
Certain assumptions have been made with respect to WannaCry attack. They have been
depicted below:
Technical
Microsoft has issued a patch fixing certain vulnerabilities before ransomware attack
WannaCry took place but various trusts did not deployed that which lead them to expose their
systems to virus (The WannaCry ransomware attack left the NHS with a £73m IT bill, 2019). If
Cheswold Park Hospital would update their systems then it will lead them to stay away from
attacks.
Non-technical
Technical team of Cheswold Park Hospital needs to be careful while clicking on any
unknown link as this can lead to some harmful attack. But it can also be intentional attempt for
earning money just similar to WannaCry attack (WannaCry masterminds collect the spoils of
global ransomware attack, 2019).
Type of Vulnerabilities
Weaknesses that can be exploited through attacker for carrying out unauthorised actions
is referred to as vulnerabilities in a computer system. It denotes loophole in a system that will
lead to an attack. There exist wide range of computer security vulnerabilities, they are bugs
(errors in software or procedures or hardware), weak passwords, lack of data encryption, OS
1
Computer security refers to process of securing computer systems from any kind of
damage or theft to electronic data, software or hardware. Generally, it denotes controls that are
made for ensuring confidentiality, availability and integrity of all the components of systems
(Basta and et. al, 2013). Security is related with precautions for vandalism, theft of data, fraud
like wanna cry and invasion of privacy. WannaCry is a ransomware attack in which data is
encrypted and ransom is demanded for the same. This report is based on Cheswold Park
Hospital, which deals with providing care to personality disorder, mental illness as well as
intellectual disabilities. This report deals with some assumptions, ways in which data can be
secured and protection of data, applications as well as systems.
Overview
Assumptions
Certain assumptions have been made with respect to WannaCry attack. They have been
depicted below:
Technical
Microsoft has issued a patch fixing certain vulnerabilities before ransomware attack
WannaCry took place but various trusts did not deployed that which lead them to expose their
systems to virus (The WannaCry ransomware attack left the NHS with a £73m IT bill, 2019). If
Cheswold Park Hospital would update their systems then it will lead them to stay away from
attacks.
Non-technical
Technical team of Cheswold Park Hospital needs to be careful while clicking on any
unknown link as this can lead to some harmful attack. But it can also be intentional attempt for
earning money just similar to WannaCry attack (WannaCry masterminds collect the spoils of
global ransomware attack, 2019).
Type of Vulnerabilities
Weaknesses that can be exploited through attacker for carrying out unauthorised actions
is referred to as vulnerabilities in a computer system. It denotes loophole in a system that will
lead to an attack. There exist wide range of computer security vulnerabilities, they are bugs
(errors in software or procedures or hardware), weak passwords, lack of data encryption, OS
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

command injection, broken algorithms, buffer overflow, path traversal, URL redirection to
untrusted sites and various others. With respect to WannaCry ransomware, the vulnerabilities
associated was EternalBlue which was based on execution of SMB (Server message block)
protocol within Windows. In this interprocess communication share created a null session which
denotes that multiple commands were sent by client to server. The purpose of this was execution
of exploitation tools (Carroll, 2014).
How attack get into network by those vulnerabilities
Vulnerabilities can be found within systems through Thunderbolt ports that execute
within macOS, Windows, FreeBSD and Linux. Vulnerabilities were exposed through
Thunderclap which caused interaction with OS. Pug-in devices such as graphic cards, projectors,
chargers and network do their work appropriately but it also lead to compromise host machine.
Peripheral devices graphic processing units and NIC (network interface cards) possess DMA
(Direct memory access) which allows to bypass security policies of operating system. The
control as well as sensitive information from target machines can be accessed by DMA (Most
laptops, desktops vulnerable to cyber attacks through plug-in devices, 2019).
Apart from this, to understand this an example can be taken into consideration. Suppose
the passwords which are used within main system like head of IT department. Then hacker can
make use of different attacks such as brute force or dictionary attack to break the system
sometimes hit and trial also works. This will lead them to have access to system which will be
containing details about all systems that are present within network. Intruder or hacker can have
details which they were looking for. Along with this, if they do have other intentions then they
can send mail by email id of head which makes, it obvious that every employee will go through
this. It can be supposed that intruder might have got access through Trojan Horse (in which head
can enter into system of others and have complete access). When they click on that link anything
can happen to do systems depending upon attack made by third person (Peltier, 2013).
Incident response
How to secure data
With the usage of different algorithms such as RSA, AES
(Advanced encryption standard) or DES (Data encryption standard) can be used for encryption
of data. The keys which are being used for this must not be simple characters that can be easily
decrypted by the usage of any software or any attack. Along with this, backup of data must be
2
untrusted sites and various others. With respect to WannaCry ransomware, the vulnerabilities
associated was EternalBlue which was based on execution of SMB (Server message block)
protocol within Windows. In this interprocess communication share created a null session which
denotes that multiple commands were sent by client to server. The purpose of this was execution
of exploitation tools (Carroll, 2014).
How attack get into network by those vulnerabilities
Vulnerabilities can be found within systems through Thunderbolt ports that execute
within macOS, Windows, FreeBSD and Linux. Vulnerabilities were exposed through
Thunderclap which caused interaction with OS. Pug-in devices such as graphic cards, projectors,
chargers and network do their work appropriately but it also lead to compromise host machine.
Peripheral devices graphic processing units and NIC (network interface cards) possess DMA
(Direct memory access) which allows to bypass security policies of operating system. The
control as well as sensitive information from target machines can be accessed by DMA (Most
laptops, desktops vulnerable to cyber attacks through plug-in devices, 2019).
Apart from this, to understand this an example can be taken into consideration. Suppose
the passwords which are used within main system like head of IT department. Then hacker can
make use of different attacks such as brute force or dictionary attack to break the system
sometimes hit and trial also works. This will lead them to have access to system which will be
containing details about all systems that are present within network. Intruder or hacker can have
details which they were looking for. Along with this, if they do have other intentions then they
can send mail by email id of head which makes, it obvious that every employee will go through
this. It can be supposed that intruder might have got access through Trojan Horse (in which head
can enter into system of others and have complete access). When they click on that link anything
can happen to do systems depending upon attack made by third person (Peltier, 2013).
Incident response
How to secure data
With the usage of different algorithms such as RSA, AES
(Advanced encryption standard) or DES (Data encryption standard) can be used for encryption
of data. The keys which are being used for this must not be simple characters that can be easily
decrypted by the usage of any software or any attack. Along with this, backup of data must be
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

created which denotes that suppose if files or hard disk is corrupted then still copy of it will be
available that means that work will not be hampered. In addition to this, there needs to be proxy
authentication for ensuring three-tier security. Unapproved software must not be installed and
unknown links that are shared on email should be avoided. Along with this, system must be
updated on regular basis. With respect to Cheswold Park Hospital, as they are making use of
cloud for storage of information, the management needs to ensure that sensitive information is
not stored on cloud, cloud services that encrypt the data must be used and anti-virus software
must be utilised (Pfleeger and Pfleeger, 2012). Different vendors like amazon web services,
salesforce, Microsoft Azure, etc. provides different options with respect to security of
information. Organisation can avail the facilities accordingly.
Detail analysis to incident response plan to identify as well as contain this attack
It is an organised approach for management as well as addressing aftermath of
cyberattack or security breach which is also referred to security or IT incident. Every
organisation have their own computer security incident response team (CSIRT) for dealing with
adverse situations. With respect to WannaCry attack that took place within NHS led to
cancellation of different surgeries. Similarly when large activities associated with welfare have
to be carried out then it becomes necessary to maintain integrity as well as secure data before the
minor issues turns into major loopholes. Cheswold Park Hospital needs to formulate incident
response plan, it has been shown below:
Preparation: Policies must be formulated that includes use of organisation data,
ramification for infringement of of security as well define security incident. There needs
step by step guide to handle security incidents.
Identification: There needs to be quick determination of issues like if in any hard drive
like USB a ransom is found or a alert on system with respect to Brute Force Attack
Detected needs to trigger the plan (Pieprzyk, Hardjono and Seberry, 2013). For an
instance, an abnormal access that is combined with alert on unusual upload on cloud
within same hour acts as a trigger that something suspicious is happening.
Containment: It denotes both short and long-term threat. Short-term denotes immediate
response which will stop threat from spreading as well as creating any more damage.
Back-up can be created by team of Cheswold Park Hospital for all affected systems and
later on forensics can be carried out later. Long term containment comprises of all
3
available that means that work will not be hampered. In addition to this, there needs to be proxy
authentication for ensuring three-tier security. Unapproved software must not be installed and
unknown links that are shared on email should be avoided. Along with this, system must be
updated on regular basis. With respect to Cheswold Park Hospital, as they are making use of
cloud for storage of information, the management needs to ensure that sensitive information is
not stored on cloud, cloud services that encrypt the data must be used and anti-virus software
must be utilised (Pfleeger and Pfleeger, 2012). Different vendors like amazon web services,
salesforce, Microsoft Azure, etc. provides different options with respect to security of
information. Organisation can avail the facilities accordingly.
Detail analysis to incident response plan to identify as well as contain this attack
It is an organised approach for management as well as addressing aftermath of
cyberattack or security breach which is also referred to security or IT incident. Every
organisation have their own computer security incident response team (CSIRT) for dealing with
adverse situations. With respect to WannaCry attack that took place within NHS led to
cancellation of different surgeries. Similarly when large activities associated with welfare have
to be carried out then it becomes necessary to maintain integrity as well as secure data before the
minor issues turns into major loopholes. Cheswold Park Hospital needs to formulate incident
response plan, it has been shown below:
Preparation: Policies must be formulated that includes use of organisation data,
ramification for infringement of of security as well define security incident. There needs
step by step guide to handle security incidents.
Identification: There needs to be quick determination of issues like if in any hard drive
like USB a ransom is found or a alert on system with respect to Brute Force Attack
Detected needs to trigger the plan (Pieprzyk, Hardjono and Seberry, 2013). For an
instance, an abnormal access that is combined with alert on unusual upload on cloud
within same hour acts as a trigger that something suspicious is happening.
Containment: It denotes both short and long-term threat. Short-term denotes immediate
response which will stop threat from spreading as well as creating any more damage.
Back-up can be created by team of Cheswold Park Hospital for all affected systems and
later on forensics can be carried out later. Long term containment comprises of all
3

systems returning to production for allowing standard operations of business but the
changes will be made in such a way that previous accounts as well as backdoors are
closed.
Eradication: Processes must be established for restoring affected systems. It will be
beneficial to eliminate each and every trace associated with security incident to ensure
that similar instances do not take place again (Stallings and et. al 2012). Along with this,
defence systems must be updated for prevention of identical incidents. Like Cheswold
Park Hospital can update their operating system, can opt for more security features from
cloud, firewall must be enabled and anti-virus should also be updated.
Recovery: After it has been ensured that systems are clean and they are not affected any
more, they can be used again for carrying out operations. Along with this, making sure
that they are free from any kind of nastiness that would lead to creation of new security
incidents.
Review lessons learned: For the training purpose, documentation must be reviewed with
CSIRT. In addition to this, IR plan must be updated with respect to feedback as well as
identified deficiencies.
Approach for recovering infected files
The files can be recovered by the usage of attrib command. This is applicable to recovery
of virus infected files, hidden, lost and deleted files. But while typing command,
individual needs to be careful as small mistake can lead to adverse results. For an
instance type within command prompt or terminal:
attrib -h -r -s/s/d drive letter:\*.*
Here each alphabet have relevant meaning which denotes their attributes:
-h: hidden files -r: read only -s: system file d: process folders
The other approach that can be used for recovering infected files from hard drive is
Remo Recover. It is a professional file recovery software that assists within recovery of
files that have been infected by virus. They might be stored either within internal or
external hard disk or USB.
Eliminate infection from system
Cheswold Park Hospital need to ensure safety of their system but if still infection affects
their operations then there are certain steps that can be taken for removing infection from system
4
changes will be made in such a way that previous accounts as well as backdoors are
closed.
Eradication: Processes must be established for restoring affected systems. It will be
beneficial to eliminate each and every trace associated with security incident to ensure
that similar instances do not take place again (Stallings and et. al 2012). Along with this,
defence systems must be updated for prevention of identical incidents. Like Cheswold
Park Hospital can update their operating system, can opt for more security features from
cloud, firewall must be enabled and anti-virus should also be updated.
Recovery: After it has been ensured that systems are clean and they are not affected any
more, they can be used again for carrying out operations. Along with this, making sure
that they are free from any kind of nastiness that would lead to creation of new security
incidents.
Review lessons learned: For the training purpose, documentation must be reviewed with
CSIRT. In addition to this, IR plan must be updated with respect to feedback as well as
identified deficiencies.
Approach for recovering infected files
The files can be recovered by the usage of attrib command. This is applicable to recovery
of virus infected files, hidden, lost and deleted files. But while typing command,
individual needs to be careful as small mistake can lead to adverse results. For an
instance type within command prompt or terminal:
attrib -h -r -s/s/d drive letter:\*.*
Here each alphabet have relevant meaning which denotes their attributes:
-h: hidden files -r: read only -s: system file d: process folders
The other approach that can be used for recovering infected files from hard drive is
Remo Recover. It is a professional file recovery software that assists within recovery of
files that have been infected by virus. They might be stored either within internal or
external hard disk or USB.
Eliminate infection from system
Cheswold Park Hospital need to ensure safety of their system but if still infection affects
their operations then there are certain steps that can be taken for removing infection from system
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

(Vacca, 2012). The initial step is to protect files that are present on system that means back up
must be created of files. Then disconnect from internet, the reason behind this is that most of the
virus comes into system when user is connected to a network or is making use of any hard drive
like USB. Now boot in safe mode or with usage of antivirus rescue disk. Now scan the system
through different programs until no infected files or folders or applications are found within the
system. Temporary files must be removed as well as worthless programs. This is done to free up
space as well as there is a possibility that any harmful file may be present. Now get into the
system restore within control panel and remove those points. There is need to fix post-malware
removal problems, for this Microsoft's Fix It tool or Re-Enable II tool can be used for them. At
last, it is necessary to change password of system so that any files associated with that password
can be avoided.
Safeguarding systems, data and applications
Needed security controls as well as techniques for safeguarding data & systems
Data encryption is not the only solution for protection of files. With respect to cloud
when security is concern with respect to storage as well as processing of data within community,
hybrid or public cloud, then this denotes that access control, recognition, validation, integrity
checking and various other factors are included. Authentication and identity which will be in
form security token or in the form of some measurable quality like fingerprint. Multiple
authentication factor is used within cloud. Along with this, access control techniques comprises
of key that will be responsible for integrity as well as separation at diverse levels. Cheswold Park
Hospital can opt for cloud security protocols for securing their data on cloud. For this, they can
opt for DAC (Discretionary access control), MAC (Mandatory access control) and RBAC (Role
based access control). These three controls can be integrated for rendering multi-level security
for cloud data (Data Protection Controls Techniques & Types of Security Controls, 2019). In
these controls management of Cheswold Park Hospital posses the privilege to whom they want
that access must be given. This will safeguard their network, their systems along with data and
applications present on them.
How to protect from future attack
With respect to attacks such as WannaCry, Cheswold Park Hospital need to ensure that
they have secured system which will lead them to safeguard themselves from future attacks.
They can have back up of their entire data so that if any kind of attack occurs then it can be
5
must be created of files. Then disconnect from internet, the reason behind this is that most of the
virus comes into system when user is connected to a network or is making use of any hard drive
like USB. Now boot in safe mode or with usage of antivirus rescue disk. Now scan the system
through different programs until no infected files or folders or applications are found within the
system. Temporary files must be removed as well as worthless programs. This is done to free up
space as well as there is a possibility that any harmful file may be present. Now get into the
system restore within control panel and remove those points. There is need to fix post-malware
removal problems, for this Microsoft's Fix It tool or Re-Enable II tool can be used for them. At
last, it is necessary to change password of system so that any files associated with that password
can be avoided.
Safeguarding systems, data and applications
Needed security controls as well as techniques for safeguarding data & systems
Data encryption is not the only solution for protection of files. With respect to cloud
when security is concern with respect to storage as well as processing of data within community,
hybrid or public cloud, then this denotes that access control, recognition, validation, integrity
checking and various other factors are included. Authentication and identity which will be in
form security token or in the form of some measurable quality like fingerprint. Multiple
authentication factor is used within cloud. Along with this, access control techniques comprises
of key that will be responsible for integrity as well as separation at diverse levels. Cheswold Park
Hospital can opt for cloud security protocols for securing their data on cloud. For this, they can
opt for DAC (Discretionary access control), MAC (Mandatory access control) and RBAC (Role
based access control). These three controls can be integrated for rendering multi-level security
for cloud data (Data Protection Controls Techniques & Types of Security Controls, 2019). In
these controls management of Cheswold Park Hospital posses the privilege to whom they want
that access must be given. This will safeguard their network, their systems along with data and
applications present on them.
How to protect from future attack
With respect to attacks such as WannaCry, Cheswold Park Hospital need to ensure that
they have secured system which will lead them to safeguard themselves from future attacks.
They can have back up of their entire data so that if any kind of attack occurs then it can be
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
prevented from spreading to other systems that are present within network. Along with this, they
can update their system on regular basis as well as applications before they become vulnerable to
attacks. Employees who makes use of system must be trained with respect to sources of attacks
like they need not to click unknown links (Pieprzyk, Hardjono and Seberry, 2013). Security must
be infused by Cheswold Park Hospital from endpoint to email till Domain name server (DNS)
layer. Along with this, technologies such as intrusion prevention system (IPS) or next-generation
firewall (NGFW). Along with this, IT department of hospital need an eye on network activities
to analyse and uncover attacks that bypass perimeter.
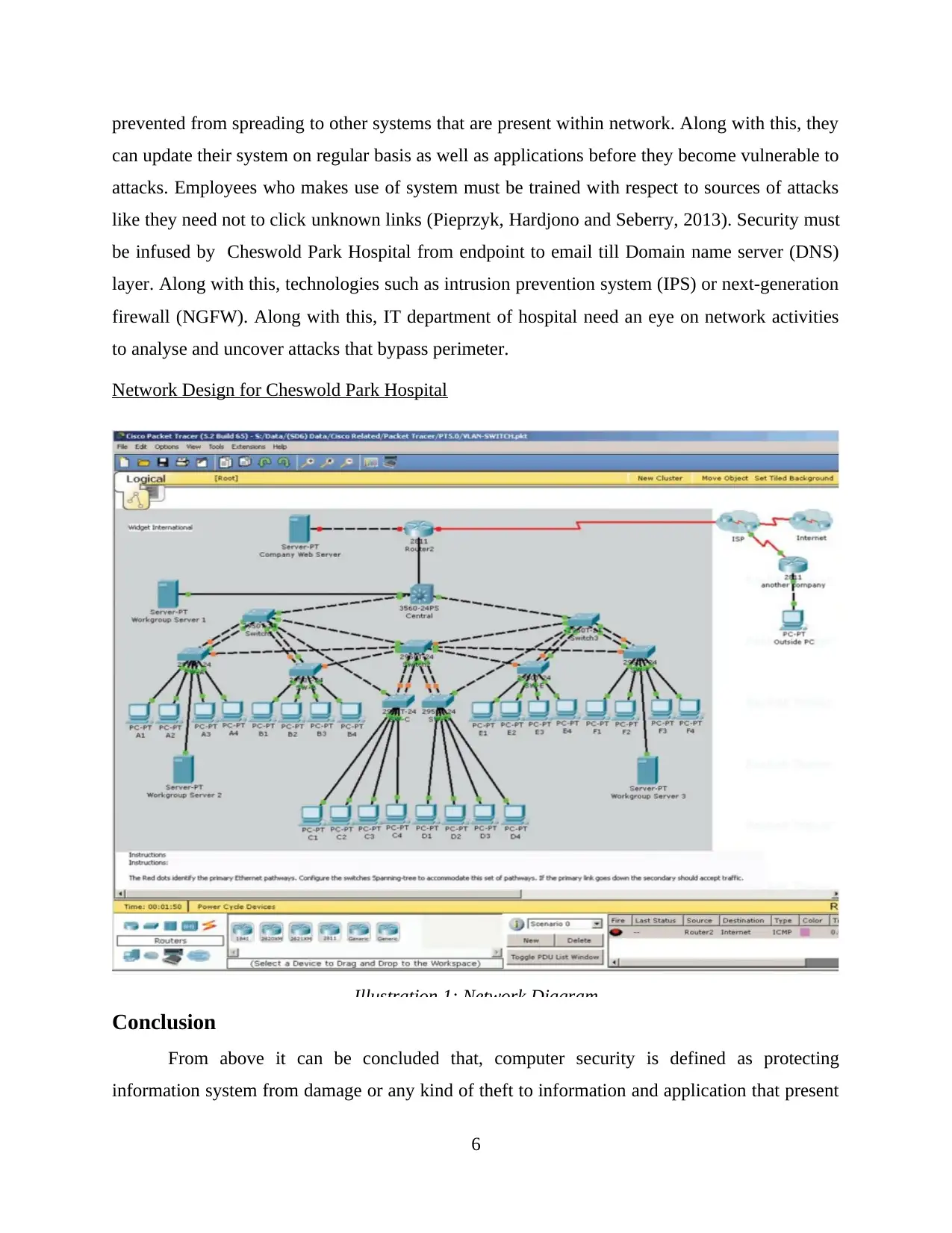
Network Design for Cheswold Park Hospital
Conclusion
From above it can be concluded that, computer security is defined as protecting
information system from damage or any kind of theft to information and application that present
6
Illustration 1: Network Diagram
can update their system on regular basis as well as applications before they become vulnerable to
attacks. Employees who makes use of system must be trained with respect to sources of attacks
like they need not to click unknown links (Pieprzyk, Hardjono and Seberry, 2013). Security must
be infused by Cheswold Park Hospital from endpoint to email till Domain name server (DNS)
layer. Along with this, technologies such as intrusion prevention system (IPS) or next-generation
firewall (NGFW). Along with this, IT department of hospital need an eye on network activities
to analyse and uncover attacks that bypass perimeter.
Network Design for Cheswold Park Hospital
Conclusion
From above it can be concluded that, computer security is defined as protecting
information system from damage or any kind of theft to information and application that present
6
Illustration 1: Network Diagram

on either hardware or software. It comprises of four areas, they are: authentication, availability,
confidentiality as well as integrity. Vulnerability denotes loopholes that are present within
system and acts as focal point to have access within system. Organisation need to have incident
response plan for attacks which leads to loss of data, system or money (as in case of WannaCry
attack). They need to safeguard systems along with this with respect to future network must be
monitored on continuous basis so that such kind of attacks can be prevented in future.
7
confidentiality as well as integrity. Vulnerability denotes loopholes that are present within
system and acts as focal point to have access within system. Organisation need to have incident
response plan for attacks which leads to loss of data, system or money (as in case of WannaCry
attack). They need to safeguard systems along with this with respect to future network must be
monitored on continuous basis so that such kind of attacks can be prevented in future.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Books & Journals
Basta, A. and et. Al, 2013. Computer security and penetration testing. Cengage Learning.
Carroll, J. M., 2014. Computer security. Butterworth-Heinemann.
Peltier, T. R., 2013. Information security fundamentals. CRC press.
Pfleeger, C. P. and Pfleeger, S. L., 2012. Analyzing computer security: a
threat/vulnerability/countermeasure approach. Prentice Hall Professional.
Pieprzyk, J., Hardjono, T. and Seberry, J., 2013. Fundamentals of computer security. Springer
Science & Business Media.
Stallings, W. and et. Al 2012. Computer security: principles and practice (pp. 978-0). Upper
Saddle River (NJ: Pearson Education.
Vacca, J. R., 2012. Computer and information security handbook. Newnes.
Online
Data Protection Controls Techniques & Types of Security Controls. 2019. [Online]. Availabile
through: <https://www.cloudcodes.com/blog/data-protection-controls-techniques.html>.
Most laptops, desktops vulnerable to cyber attacks through plug-in devices. 2019. [Online].
Available through: <https://economictimes.indiatimes.com/magazines/panache/most-
laptops-desktops-vulnerable-to-cyber-attacks-through-plug-in-devices/articleshow/
68166550.cms>.
The WannaCry ransomware attack left the NHS with a £73m IT bill. 2019. [Online]. Availabile
through: <https://tech.newstatesman.com/security/cost-wannacry-ransomware-attack-
nhs>.
WannaCry masterminds collect the spoils of global ransomware attack. 2019. [Online].
Available through: <https://tech.newstatesman.com/news/wannacry-bitcoin-moved>.
8
Books & Journals
Basta, A. and et. Al, 2013. Computer security and penetration testing. Cengage Learning.
Carroll, J. M., 2014. Computer security. Butterworth-Heinemann.
Peltier, T. R., 2013. Information security fundamentals. CRC press.
Pfleeger, C. P. and Pfleeger, S. L., 2012. Analyzing computer security: a
threat/vulnerability/countermeasure approach. Prentice Hall Professional.
Pieprzyk, J., Hardjono, T. and Seberry, J., 2013. Fundamentals of computer security. Springer
Science & Business Media.
Stallings, W. and et. Al 2012. Computer security: principles and practice (pp. 978-0). Upper
Saddle River (NJ: Pearson Education.
Vacca, J. R., 2012. Computer and information security handbook. Newnes.
Online
Data Protection Controls Techniques & Types of Security Controls. 2019. [Online]. Availabile
through: <https://www.cloudcodes.com/blog/data-protection-controls-techniques.html>.
Most laptops, desktops vulnerable to cyber attacks through plug-in devices. 2019. [Online].
Available through: <https://economictimes.indiatimes.com/magazines/panache/most-
laptops-desktops-vulnerable-to-cyber-attacks-through-plug-in-devices/articleshow/
68166550.cms>.
The WannaCry ransomware attack left the NHS with a £73m IT bill. 2019. [Online]. Availabile
through: <https://tech.newstatesman.com/security/cost-wannacry-ransomware-attack-
nhs>.
WannaCry masterminds collect the spoils of global ransomware attack. 2019. [Online].
Available through: <https://tech.newstatesman.com/news/wannacry-bitcoin-moved>.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




