Developing a Bulletin Board System Using TCP/IP Network Communication
VerifiedAdded on 2020/07/23
|19
|5253
|130
Project
AI Summary
This project details the design, development, and evaluation of a simple client-server bulletin board system using the TCP/IP protocol suite. The project begins with a design phase, exploring application-level protocols like HTTP and IRC, and focusing on the TCP protocol for reliable data transfer. The design includes the TCP three-way handshake mechanism and a description of the user interface features such as login, posting messages, and viewing topics. The development phase involves C++ code for the bulletin_board, topic, and message functionalities. The testing phase addresses challenges encountered during implementation. Finally, the evaluation assesses the system's functionality, robustness, and security. The project emphasizes the role of TCP in breaking messages into packets, handling ordering, and ensuring data integrity through checksums. The user interface is designed to be simple, enabling users to connect to the server, post messages under different topics, and view messages. The project underscores the importance of TCP's three-way handshake for connection establishment and data transfer, highlighting its advantages over UDP for this application. The document provides a detailed overview of network communication principles and their practical application in building a client-server bulletin board system.

Network Communication using the TCP/IP protocol suite 1
Network Communication using the TCP/IP protocol suite
Student’s Name:
Instructor’s Name:
Date:
Network Communication using the TCP/IP protocol suite
Student’s Name:
Instructor’s Name:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Communication using the TCP/IP protocol suite 2
Contents
The Task – A Simple Client-Server Bulletin-Board....................................................................2
Stage 1: Design.........................................................................................................................2
Application Level Protocol – HyperText Transfer Protocol [1].............................................2
Application Level Protocol – Internet Relay Chat [2]............................................................2
Transport Layer Protocol – TCP [3][4][5]..............................................................................3
TCP three way handshake mechanism.................................................................................3
Packet...................................................................................................................................4
User Interface.......................................................................................................................5
Stage 2: Development.............................................................................................................6
Bulletin_board.cc................................................................................................................. 6
topic.cc............................................................................................................................... 12
message.cc......................................................................................................................... 13
Stage 3: Testing [6].................................................................................................................14
Challenges faced during the test........................................................................................15
Stage 4: Evaluation.................................................................................................................16
The bulletin board system is evaluated against the following parameters........................16
1) Functionality............................................................................................................16
2) Robustness.............................................................................................................. 16
3) Security....................................................................................................................16
References............................................................................................................................. 17
Contents
The Task – A Simple Client-Server Bulletin-Board....................................................................2
Stage 1: Design.........................................................................................................................2
Application Level Protocol – HyperText Transfer Protocol [1].............................................2
Application Level Protocol – Internet Relay Chat [2]............................................................2
Transport Layer Protocol – TCP [3][4][5]..............................................................................3
TCP three way handshake mechanism.................................................................................3
Packet...................................................................................................................................4
User Interface.......................................................................................................................5
Stage 2: Development.............................................................................................................6
Bulletin_board.cc................................................................................................................. 6
topic.cc............................................................................................................................... 12
message.cc......................................................................................................................... 13
Stage 3: Testing [6].................................................................................................................14
Challenges faced during the test........................................................................................15
Stage 4: Evaluation.................................................................................................................16
The bulletin board system is evaluated against the following parameters........................16
1) Functionality............................................................................................................16
2) Robustness.............................................................................................................. 16
3) Security....................................................................................................................16
References............................................................................................................................. 17

Network Communication using the TCP/IP protocol suite 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Communication using the TCP/IP protocol suite 4
The Task – A Simple Client-Server Bulletin-Board
Stage 1: Design
By definition, protocol represents a set of rules that decide how two entities communicate
with one another. Protocols are used on a regular basis. As communication becomes difficult
and complicated, the protocols would become complicated. Activities like communication
need protocols for efficient and prompt data transfer. These protocols are also known as
network communication protocols.
Application Level Protocol – HyperText Transfer Protocol [1]
In Application level, the most common protocol would be “HyperText Transfer Protocol
(HTTP)”. The protocol is responsible for transferring HyperText from the client to the server.
There are simple HTTP functions to trigger communication between the server and client. It
relies on request/response patterns to ensure reliable communication between the server and
client. “Request” is treated as the “ask” and “Response” is the reply! Both the responses and
requests have resources and data associated with it.
There are nine different types of HTTP requests.
1) GET
2) HEAD
3) POST
4) PUT
5) DELETE
6) PATCH
7) OPTIONS
8) CONNECT
9) TRACE
The very first line of a HTTP response is known as the status line. This line represents the
status in a numeric form. For example, “404” represents “Resource Not Found”. And, “200”
is the most common HTTP response. Here, “200” means “OK” or “Successful”.
Application Level Protocol – Internet Relay Chat [2]
The current project revolves around a bulletin-board system. Just the BBS, there is an
existing Internet Relay Chat protocol to help users send and receive messages in the form of
text. This is known as a chat protocol. The protocol makes use of a client-server model. In the
Internet Relay Chat protocol, clients should install a program in their machine. This program
connects to a server. When clients wish to send a message, they communicate with the central
server. This server relays the message to all other users. In the beginning, internet relay chat
protocols were used in discussion forums. These forums were known as channels. This
protocol supports one to one texts too. These texts are sent and received through private
messages. Of course, the internet relay chat protocol supports data and file transfers. This
protocol gives users the freedom to communicate using commands. These commands can be
The Task – A Simple Client-Server Bulletin-Board
Stage 1: Design
By definition, protocol represents a set of rules that decide how two entities communicate
with one another. Protocols are used on a regular basis. As communication becomes difficult
and complicated, the protocols would become complicated. Activities like communication
need protocols for efficient and prompt data transfer. These protocols are also known as
network communication protocols.
Application Level Protocol – HyperText Transfer Protocol [1]
In Application level, the most common protocol would be “HyperText Transfer Protocol
(HTTP)”. The protocol is responsible for transferring HyperText from the client to the server.
There are simple HTTP functions to trigger communication between the server and client. It
relies on request/response patterns to ensure reliable communication between the server and
client. “Request” is treated as the “ask” and “Response” is the reply! Both the responses and
requests have resources and data associated with it.
There are nine different types of HTTP requests.
1) GET
2) HEAD
3) POST
4) PUT
5) DELETE
6) PATCH
7) OPTIONS
8) CONNECT
9) TRACE
The very first line of a HTTP response is known as the status line. This line represents the
status in a numeric form. For example, “404” represents “Resource Not Found”. And, “200”
is the most common HTTP response. Here, “200” means “OK” or “Successful”.
Application Level Protocol – Internet Relay Chat [2]
The current project revolves around a bulletin-board system. Just the BBS, there is an
existing Internet Relay Chat protocol to help users send and receive messages in the form of
text. This is known as a chat protocol. The protocol makes use of a client-server model. In the
Internet Relay Chat protocol, clients should install a program in their machine. This program
connects to a server. When clients wish to send a message, they communicate with the central
server. This server relays the message to all other users. In the beginning, internet relay chat
protocols were used in discussion forums. These forums were known as channels. This
protocol supports one to one texts too. These texts are sent and received through private
messages. Of course, the internet relay chat protocol supports data and file transfers. This
protocol gives users the freedom to communicate using commands. These commands can be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Communication using the TCP/IP protocol suite 5
used to interact with clients, servers and other users. For example, /ADMIN can be used to
identify who the administrator is. It is possible to start group conversations too. Group
conversations are performed over chat rooms. The groups exist as channels. One server can
have multiple channels, and it allows all users to join.
Both the HTTP and IRC protocols depend on an important transport layer protocol. TCP/IP
ensures that data is transferred efficiently and reliably. Regardless of the location or data,
TCP/IP ensures data transfer happens. Below TCP/IP is a layer that is not reliable for
transfers. This layer can cause many concerns during data transfers. That is why ever protocol
uses a separate approach to deliver data.
Transport Layer Protocol – TCP [3][4][5]
TCP is the “Transmission Control Protocol”. This is a very important protocol in the internet.
To complete the current problem statement, a TCP protocol is required. This protocol breaks
messages into smaller packers. The packet represents a segment of data that can be integrated
together. Once all the packets are merged, a complete message is formed (something like a
bulletin message, email or HTTP request can be downloaded). When a message has to be
sent, it is broken into packets and sent over the internet. Namely, it is transported from the
client to the server. The server assembles these packets and stores them together. By breaking
down huge messages into smaller packets, issues like “congestion” can be avoided in the
network.
However, there are chances of the following problems:
1) Delay in packet transfer
2) Loss of packets
3) Corruption of packets
TCP takes care of these problems strategically. It makes use of techniques like ordering and
checksums. Ordering is a way of stitching packets together. The TCP protocol gives each
packet a unique sequence number. This number is used to order packets. If packets go out of
order, TCP waits for the missing packets to arrive. Sooner, it bundles the packets together in
order. Checksum is another important concept in network communication. Checksum is a
way of storing information about the packets The checksums can be used to detect coding
schemes and errors. The checksums can be used to correct issues. If the checksums are
incorrect, packets become useless. Thus, the data packets can be resent.
TCP three way handshake mechanism
TCP relies on a three-way handshake mechanism. The handshake is: SYN-SYN-ACK. The
handshake involves three messages for negotiation and starting a session.
To begin with:
1) Client sends a “SYNchronize” packet to the server.
2) The server receives the SYN.
3) The server sends a SYNchronize-ACKnowledgement to the client
used to interact with clients, servers and other users. For example, /ADMIN can be used to
identify who the administrator is. It is possible to start group conversations too. Group
conversations are performed over chat rooms. The groups exist as channels. One server can
have multiple channels, and it allows all users to join.
Both the HTTP and IRC protocols depend on an important transport layer protocol. TCP/IP
ensures that data is transferred efficiently and reliably. Regardless of the location or data,
TCP/IP ensures data transfer happens. Below TCP/IP is a layer that is not reliable for
transfers. This layer can cause many concerns during data transfers. That is why ever protocol
uses a separate approach to deliver data.
Transport Layer Protocol – TCP [3][4][5]
TCP is the “Transmission Control Protocol”. This is a very important protocol in the internet.
To complete the current problem statement, a TCP protocol is required. This protocol breaks
messages into smaller packers. The packet represents a segment of data that can be integrated
together. Once all the packets are merged, a complete message is formed (something like a
bulletin message, email or HTTP request can be downloaded). When a message has to be
sent, it is broken into packets and sent over the internet. Namely, it is transported from the
client to the server. The server assembles these packets and stores them together. By breaking
down huge messages into smaller packets, issues like “congestion” can be avoided in the
network.
However, there are chances of the following problems:
1) Delay in packet transfer
2) Loss of packets
3) Corruption of packets
TCP takes care of these problems strategically. It makes use of techniques like ordering and
checksums. Ordering is a way of stitching packets together. The TCP protocol gives each
packet a unique sequence number. This number is used to order packets. If packets go out of
order, TCP waits for the missing packets to arrive. Sooner, it bundles the packets together in
order. Checksum is another important concept in network communication. Checksum is a
way of storing information about the packets The checksums can be used to detect coding
schemes and errors. The checksums can be used to correct issues. If the checksums are
incorrect, packets become useless. Thus, the data packets can be resent.
TCP three way handshake mechanism
TCP relies on a three-way handshake mechanism. The handshake is: SYN-SYN-ACK. The
handshake involves three messages for negotiation and starting a session.
To begin with:
1) Client sends a “SYNchronize” packet to the server.
2) The server receives the SYN.
3) The server sends a SYNchronize-ACKnowledgement to the client

Network Communication using the TCP/IP protocol suite 6
4) The client receives server’s SYN-ACK
5) The client sends an ACKnowledge
6) The server receives an ACK
7) The connection between the server and client is established
SYN and ACK are a part of the TCP header. A bit is set inside the TCP header to identify if
SYN or ACK was set. TCP is programmed to identify if the socket connection is open,
synchronized and established using the SYN-ACK messages. When a client and server wants
to communicate, the 3-way messages are required to open and tear down connections. The
teardown and setup of connection are a part of the reliable TCP protocol. For example, TCP
acknowledges that data is received and reassembled successful. This differentiates TCP from
UDP. User Datagram Protocol is connectionless. It doesn’t establish any form of connection
like TCP. Also, UDP doesn’t make any handshakes. That is why UDP is treated as an
unreliable protocol. With this being said, TCP is an ideal protocol to design this bulletin
board system.
All other protocols: SSH, Telnet, FTP, IMAP, SMTP, HTTPS, POP3 and HTTP ride above
the TCP. These protocols make use of the three way handshake to open, establish and close
connections. Meanwhile, TCP rides above the Internet Protocol (IP). In the protocol stack,
both TCP and IP work together. TCP segments are carefully passed in the payload section of
IP. IP takes care of routing and addressing. However, TCP is responsible for the actual
communication between endpoints.
Packet
TCP relies on packet headers as a part of data transfer in network connections. The header
contains parameters alias fields that are defined by the technical specifications. The TCP
header has 10 fields that sum up to 20 bytes (160 bits). The header has 40 optional bytes.
The source and destination numbers represent the endpoints of a TCP communication. These
numbers are required for sending and receiving messages. Data starts from the source
location and ends at the destination.
TCP achieves ordering with the help of sequence numbers. Message senders should order
messages using the sequence numbers. Both the senders and receivers attach an
acknowledgement number based on these sequence numbers. Every message has a
corresponding acknowledge to be sent.
4) The client receives server’s SYN-ACK
5) The client sends an ACKnowledge
6) The server receives an ACK
7) The connection between the server and client is established
SYN and ACK are a part of the TCP header. A bit is set inside the TCP header to identify if
SYN or ACK was set. TCP is programmed to identify if the socket connection is open,
synchronized and established using the SYN-ACK messages. When a client and server wants
to communicate, the 3-way messages are required to open and tear down connections. The
teardown and setup of connection are a part of the reliable TCP protocol. For example, TCP
acknowledges that data is received and reassembled successful. This differentiates TCP from
UDP. User Datagram Protocol is connectionless. It doesn’t establish any form of connection
like TCP. Also, UDP doesn’t make any handshakes. That is why UDP is treated as an
unreliable protocol. With this being said, TCP is an ideal protocol to design this bulletin
board system.
All other protocols: SSH, Telnet, FTP, IMAP, SMTP, HTTPS, POP3 and HTTP ride above
the TCP. These protocols make use of the three way handshake to open, establish and close
connections. Meanwhile, TCP rides above the Internet Protocol (IP). In the protocol stack,
both TCP and IP work together. TCP segments are carefully passed in the payload section of
IP. IP takes care of routing and addressing. However, TCP is responsible for the actual
communication between endpoints.
Packet
TCP relies on packet headers as a part of data transfer in network connections. The header
contains parameters alias fields that are defined by the technical specifications. The TCP
header has 10 fields that sum up to 20 bytes (160 bits). The header has 40 optional bytes.
The source and destination numbers represent the endpoints of a TCP communication. These
numbers are required for sending and receiving messages. Data starts from the source
location and ends at the destination.
TCP achieves ordering with the help of sequence numbers. Message senders should order
messages using the sequence numbers. Both the senders and receivers attach an
acknowledgement number based on these sequence numbers. Every message has a
corresponding acknowledge to be sent.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Communication using the TCP/IP protocol suite 7
The TCP data offset field comes in multiples of four bytes.
Reserved data is a special field in TCP headers. In most cases, reserved data has a value of
zero. This field is useful in aligning the header size. It makes sure the total header size is a
multiple of four bytes. The protocol uses reserved data to ensure efficient data processing.
TCP uses six control flags (on or off) to handle data flow. For example, one of the flags is
“Reset”. It states if the connection should be reset or not.
“Window size” plays an important role in TCP. The window size determines how much data
can be transferred by the client. This amount of data can be sent before asking for an
acknowledgement. As the window size decreases, the network is likely to become slower. On
the other hand, high window size can make the entire network saturated. The receivers will
not be able to handle incoming data efficiently. There are special windowing algorithms to
decide the window size.
The checksum is a mathematical value that helps the receiver verify if data was corrupted or
tampered. The checksum protocol shared by the server and client are the same. This protocol
is decided even before communication starts between the endpoints.
TCP has a special urgent pointer header field. In most cases, this header is ignored or set to
zero. However, it can be paired with a control flag. In certain situations, the urgent pointer is
used as a data offset. It marks the subset of the data transferred.
All these header fields play an important role during data transfer. They are responsible for
making sure data goes from the client to the server and a response is received successfully.
The sequence number is required for ordering and the checksum ensures on the validity of
data. It is quite easy to verify if a packet is corrupted, lost or tampered with the help of these
header fields. And, all these header fields are carefully inserted into the message stream.
User Interface
The Bulletin-Board has a very simple user interface.
The interface should allow the following functionalities:
1) Login to the Bulletin Board System
2) Ability to refresh/clear existing screen
3) Ability to connect with remote server
4) Ability to post a message under separate themes/topics
5) Ability to view all messages under separate themes/topics
6) Ability to view all messages posted into the remote server
7) Ability to filter messages that are posted into the remote server
8) Ability to restrict access to certain messages in the remote server
9) Ability to disconnect from system
The GUI can be designed using C++. The very first interface would be the “Login”. Here the
user has to enter his/her username and password. If the username and password combination
The TCP data offset field comes in multiples of four bytes.
Reserved data is a special field in TCP headers. In most cases, reserved data has a value of
zero. This field is useful in aligning the header size. It makes sure the total header size is a
multiple of four bytes. The protocol uses reserved data to ensure efficient data processing.
TCP uses six control flags (on or off) to handle data flow. For example, one of the flags is
“Reset”. It states if the connection should be reset or not.
“Window size” plays an important role in TCP. The window size determines how much data
can be transferred by the client. This amount of data can be sent before asking for an
acknowledgement. As the window size decreases, the network is likely to become slower. On
the other hand, high window size can make the entire network saturated. The receivers will
not be able to handle incoming data efficiently. There are special windowing algorithms to
decide the window size.
The checksum is a mathematical value that helps the receiver verify if data was corrupted or
tampered. The checksum protocol shared by the server and client are the same. This protocol
is decided even before communication starts between the endpoints.
TCP has a special urgent pointer header field. In most cases, this header is ignored or set to
zero. However, it can be paired with a control flag. In certain situations, the urgent pointer is
used as a data offset. It marks the subset of the data transferred.
All these header fields play an important role during data transfer. They are responsible for
making sure data goes from the client to the server and a response is received successfully.
The sequence number is required for ordering and the checksum ensures on the validity of
data. It is quite easy to verify if a packet is corrupted, lost or tampered with the help of these
header fields. And, all these header fields are carefully inserted into the message stream.
User Interface
The Bulletin-Board has a very simple user interface.
The interface should allow the following functionalities:
1) Login to the Bulletin Board System
2) Ability to refresh/clear existing screen
3) Ability to connect with remote server
4) Ability to post a message under separate themes/topics
5) Ability to view all messages under separate themes/topics
6) Ability to view all messages posted into the remote server
7) Ability to filter messages that are posted into the remote server
8) Ability to restrict access to certain messages in the remote server
9) Ability to disconnect from system
The GUI can be designed using C++. The very first interface would be the “Login”. Here the
user has to enter his/her username and password. If the username and password combination
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Communication using the TCP/IP protocol suite 8
is accurate, the very next screen that allows the user to connect and post must be displayed. If
the username and password combination is incorrect, an error message has to be displayed. In
the long run, the views can be customized based on the user credentials.
This bulletin board system allows users to post messages under different topics. The topics
can be created by the user or administrator. The bulletin board has few default topics. Once
the user connects to the server from the client machine and makes a post, the post would be
stored at the remote server. This server can be accessed from any client machine that is
authenticated. Packets are sent and received between the client and server using TCP/IP
protocol. With every message, the three-way handshake happens. This makes sure posts are
stored at the remote server. Also, the client needs to establish a three-way handshake to
connect with the server.
The GUI design must take into consideration the following factors:
1) The interface should be easy to use. It must let the client perform tasks with just few
clicks of a button.
2) The interface should allow the client to establish a safe connection with the server.
The connection must be established easily. If anything goes wrong, the interface must
have a comprehensive way of notifying the user.
3) The Bulletin Board system should have a crisp way of presenting information. It must
be easier for users to search for posts. Also, the users should be able to post messages
against a specific topic easily.
4) If there are special privileges for certain users (e.g. ADMIN), the interface must have
a way of showing them.
The above points revolve around the following factors: Ease of Use, Reliability,
Comprehensibility, Function, Secure and Intuitive. These factors make it easier to handle this
Bulletin Board System. The underlying TCP communication protocols are carefully covered
from the end user. The client will be able to perform operations without having any clue of
the underlying network communication protocols. This makes the bulletin board solution a
robust one.
Stage 2: Development
Bulletin_board.cc
#include"bulletin_board.h"
usingnamespacestd;
unsigned message_count = 0;
void
BulletinBoard::addUser( const string & username, const string & pw )
{
list_of_users.push_back( User(username, pw) );
}
is accurate, the very next screen that allows the user to connect and post must be displayed. If
the username and password combination is incorrect, an error message has to be displayed. In
the long run, the views can be customized based on the user credentials.
This bulletin board system allows users to post messages under different topics. The topics
can be created by the user or administrator. The bulletin board has few default topics. Once
the user connects to the server from the client machine and makes a post, the post would be
stored at the remote server. This server can be accessed from any client machine that is
authenticated. Packets are sent and received between the client and server using TCP/IP
protocol. With every message, the three-way handshake happens. This makes sure posts are
stored at the remote server. Also, the client needs to establish a three-way handshake to
connect with the server.
The GUI design must take into consideration the following factors:
1) The interface should be easy to use. It must let the client perform tasks with just few
clicks of a button.
2) The interface should allow the client to establish a safe connection with the server.
The connection must be established easily. If anything goes wrong, the interface must
have a comprehensive way of notifying the user.
3) The Bulletin Board system should have a crisp way of presenting information. It must
be easier for users to search for posts. Also, the users should be able to post messages
against a specific topic easily.
4) If there are special privileges for certain users (e.g. ADMIN), the interface must have
a way of showing them.
The above points revolve around the following factors: Ease of Use, Reliability,
Comprehensibility, Function, Secure and Intuitive. These factors make it easier to handle this
Bulletin Board System. The underlying TCP communication protocols are carefully covered
from the end user. The client will be able to perform operations without having any clue of
the underlying network communication protocols. This makes the bulletin board solution a
robust one.
Stage 2: Development
Bulletin_board.cc
#include"bulletin_board.h"
usingnamespacestd;
unsigned message_count = 0;
void
BulletinBoard::addUser( const string & username, const string & pw )
{
list_of_users.push_back( User(username, pw) );
}
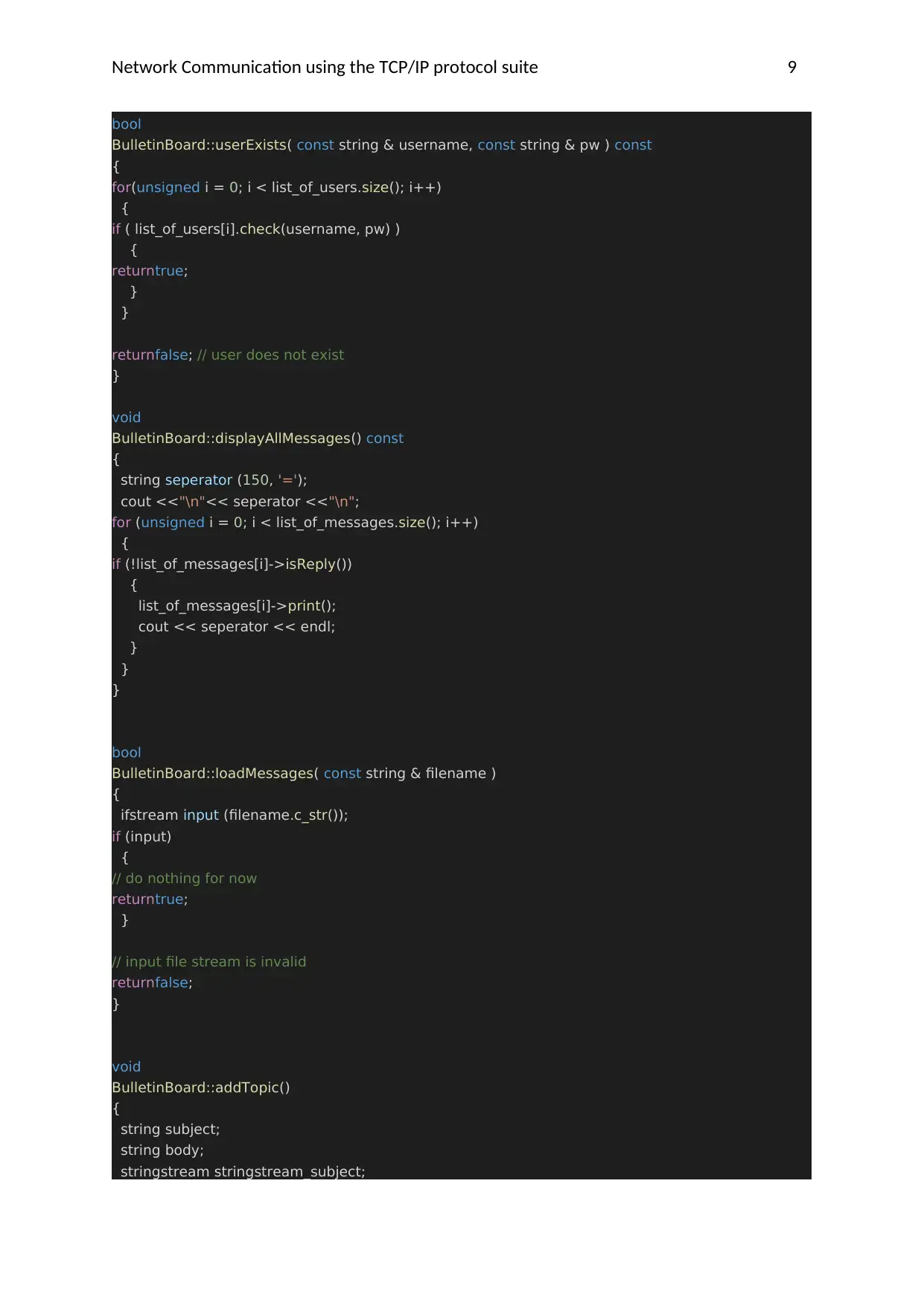
Network Communication using the TCP/IP protocol suite 9
bool
BulletinBoard::userExists( const string & username, const string & pw ) const
{
for(unsigned i = 0; i < list_of_users.size(); i++)
{
if ( list_of_users[i].check(username, pw) )
{
returntrue;
}
}
returnfalse; // user does not exist
}
void
BulletinBoard::displayAllMessages() const
{
string seperator (150, '=');
cout <<"\n"<< seperator <<"\n";
for (unsigned i = 0; i < list_of_messages.size(); i++)
{
if (!list_of_messages[i]->isReply())
{
list_of_messages[i]->print();
cout << seperator << endl;
}
}
}
bool
BulletinBoard::loadMessages( const string & filename )
{
ifstream input (filename.c_str());
if (input)
{
// do nothing for now
returntrue;
}
// input file stream is invalid
returnfalse;
}
void
BulletinBoard::addTopic()
{
string subject;
string body;
stringstream stringstream_subject;
bool
BulletinBoard::userExists( const string & username, const string & pw ) const
{
for(unsigned i = 0; i < list_of_users.size(); i++)
{
if ( list_of_users[i].check(username, pw) )
{
returntrue;
}
}
returnfalse; // user does not exist
}
void
BulletinBoard::displayAllMessages() const
{
string seperator (150, '=');
cout <<"\n"<< seperator <<"\n";
for (unsigned i = 0; i < list_of_messages.size(); i++)
{
if (!list_of_messages[i]->isReply())
{
list_of_messages[i]->print();
cout << seperator << endl;
}
}
}
bool
BulletinBoard::loadMessages( const string & filename )
{
ifstream input (filename.c_str());
if (input)
{
// do nothing for now
returntrue;
}
// input file stream is invalid
returnfalse;
}
void
BulletinBoard::addTopic()
{
string subject;
string body;
stringstream stringstream_subject;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
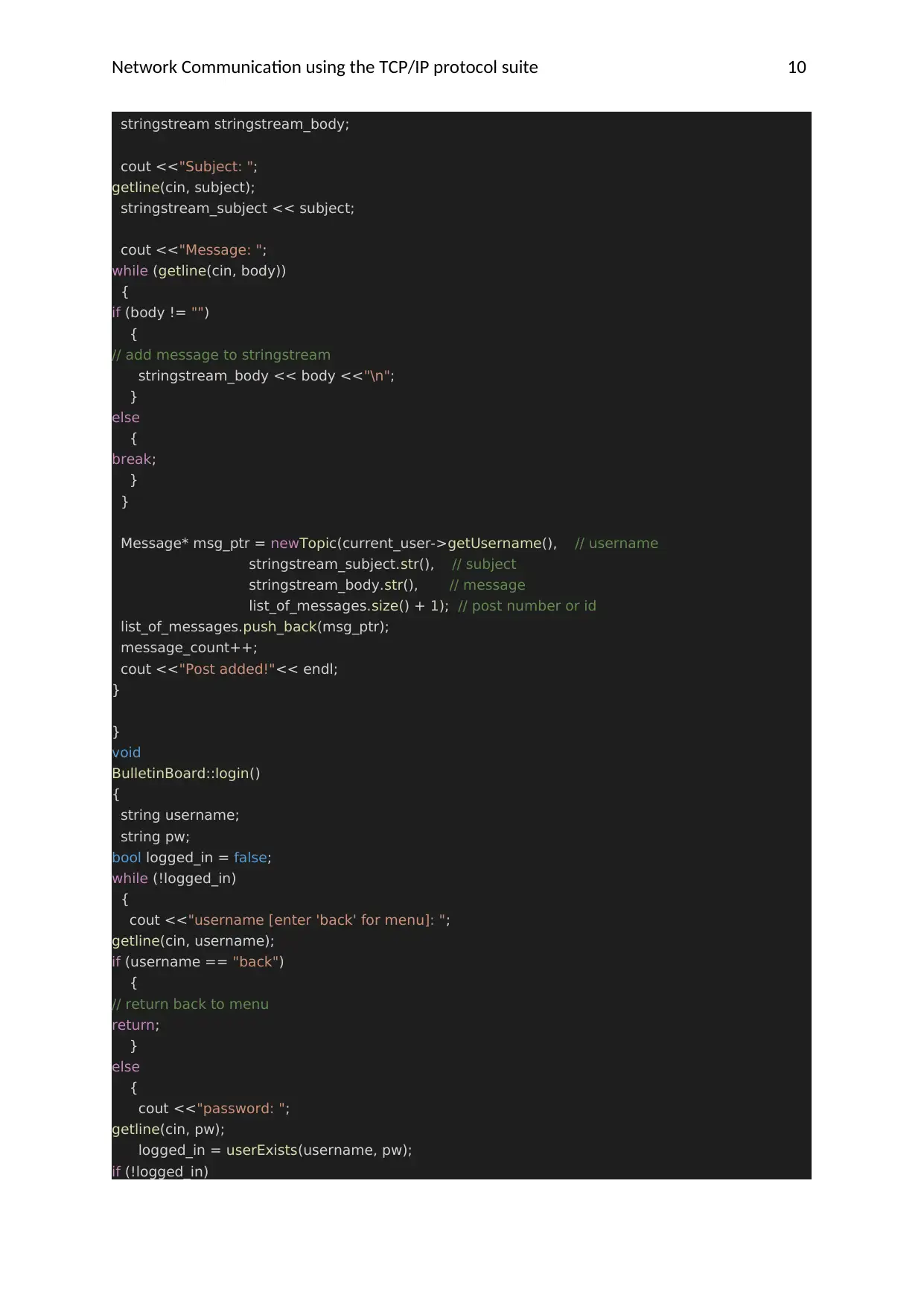
Network Communication using the TCP/IP protocol suite 10
stringstream stringstream_body;
cout <<"Subject: ";
getline(cin, subject);
stringstream_subject << subject;
cout <<"Message: ";
while (getline(cin, body))
{
if (body != "")
{
// add message to stringstream
stringstream_body << body <<"\n";
}
else
{
break;
}
}
Message* msg_ptr = newTopic(current_user->getUsername(), // username
stringstream_subject.str(), // subject
stringstream_body.str(), // message
list_of_messages.size() + 1); // post number or id
list_of_messages.push_back(msg_ptr);
message_count++;
cout <<"Post added!"<< endl;
}
}
void
BulletinBoard::login()
{
string username;
string pw;
bool logged_in = false;
while (!logged_in)
{
cout <<"username [enter 'back' for menu]: ";
getline(cin, username);
if (username == "back")
{
// return back to menu
return;
}
else
{
cout <<"password: ";
getline(cin, pw);
logged_in = userExists(username, pw);
if (!logged_in)
stringstream stringstream_body;
cout <<"Subject: ";
getline(cin, subject);
stringstream_subject << subject;
cout <<"Message: ";
while (getline(cin, body))
{
if (body != "")
{
// add message to stringstream
stringstream_body << body <<"\n";
}
else
{
break;
}
}
Message* msg_ptr = newTopic(current_user->getUsername(), // username
stringstream_subject.str(), // subject
stringstream_body.str(), // message
list_of_messages.size() + 1); // post number or id
list_of_messages.push_back(msg_ptr);
message_count++;
cout <<"Post added!"<< endl;
}
}
void
BulletinBoard::login()
{
string username;
string pw;
bool logged_in = false;
while (!logged_in)
{
cout <<"username [enter 'back' for menu]: ";
getline(cin, username);
if (username == "back")
{
// return back to menu
return;
}
else
{
cout <<"password: ";
getline(cin, pw);
logged_in = userExists(username, pw);
if (!logged_in)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
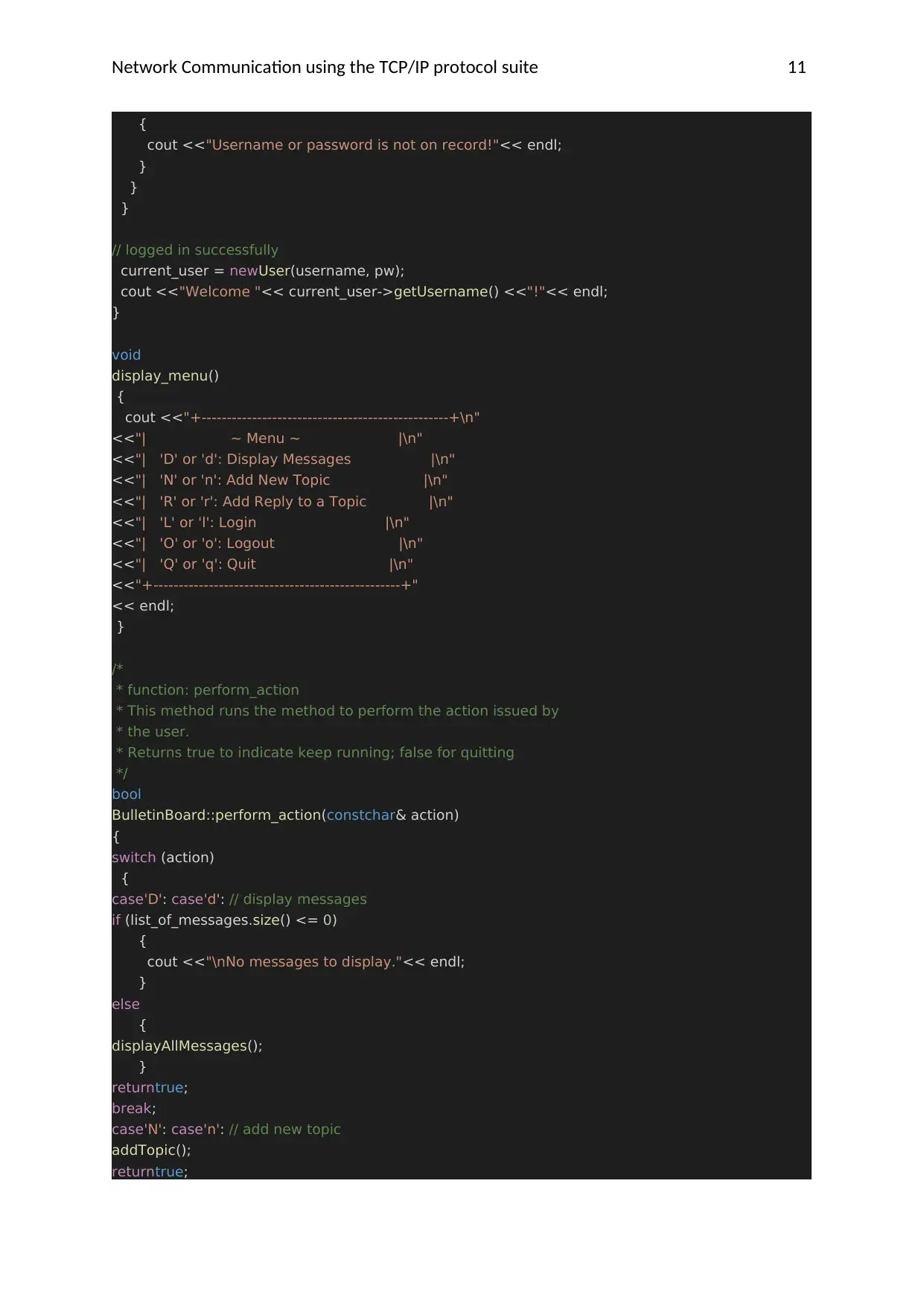
Network Communication using the TCP/IP protocol suite 11
{
cout <<"Username or password is not on record!"<< endl;
}
}
}
// logged in successfully
current_user = newUser(username, pw);
cout <<"Welcome "<< current_user->getUsername() <<"!"<< endl;
}
void
display_menu()
{
cout <<"+-------------------------------------------------+\n"
<<"| ~ Menu ~ |\n"
<<"| 'D' or 'd': Display Messages |\n"
<<"| 'N' or 'n': Add New Topic |\n"
<<"| 'R' or 'r': Add Reply to a Topic |\n"
<<"| 'L' or 'l': Login |\n"
<<"| 'O' or 'o': Logout |\n"
<<"| 'Q' or 'q': Quit |\n"
<<"+-------------------------------------------------+"
<< endl;
}
/*
* function: perform_action
* This method runs the method to perform the action issued by
* the user.
* Returns true to indicate keep running; false for quitting
*/
bool
BulletinBoard::perform_action(constchar& action)
{
switch (action)
{
case'D': case'd': // display messages
if (list_of_messages.size() <= 0)
{
cout <<"\nNo messages to display."<< endl;
}
else
{
displayAllMessages();
}
returntrue;
break;
case'N': case'n': // add new topic
addTopic();
returntrue;
{
cout <<"Username or password is not on record!"<< endl;
}
}
}
// logged in successfully
current_user = newUser(username, pw);
cout <<"Welcome "<< current_user->getUsername() <<"!"<< endl;
}
void
display_menu()
{
cout <<"+-------------------------------------------------+\n"
<<"| ~ Menu ~ |\n"
<<"| 'D' or 'd': Display Messages |\n"
<<"| 'N' or 'n': Add New Topic |\n"
<<"| 'R' or 'r': Add Reply to a Topic |\n"
<<"| 'L' or 'l': Login |\n"
<<"| 'O' or 'o': Logout |\n"
<<"| 'Q' or 'q': Quit |\n"
<<"+-------------------------------------------------+"
<< endl;
}
/*
* function: perform_action
* This method runs the method to perform the action issued by
* the user.
* Returns true to indicate keep running; false for quitting
*/
bool
BulletinBoard::perform_action(constchar& action)
{
switch (action)
{
case'D': case'd': // display messages
if (list_of_messages.size() <= 0)
{
cout <<"\nNo messages to display."<< endl;
}
else
{
displayAllMessages();
}
returntrue;
break;
case'N': case'n': // add new topic
addTopic();
returntrue;
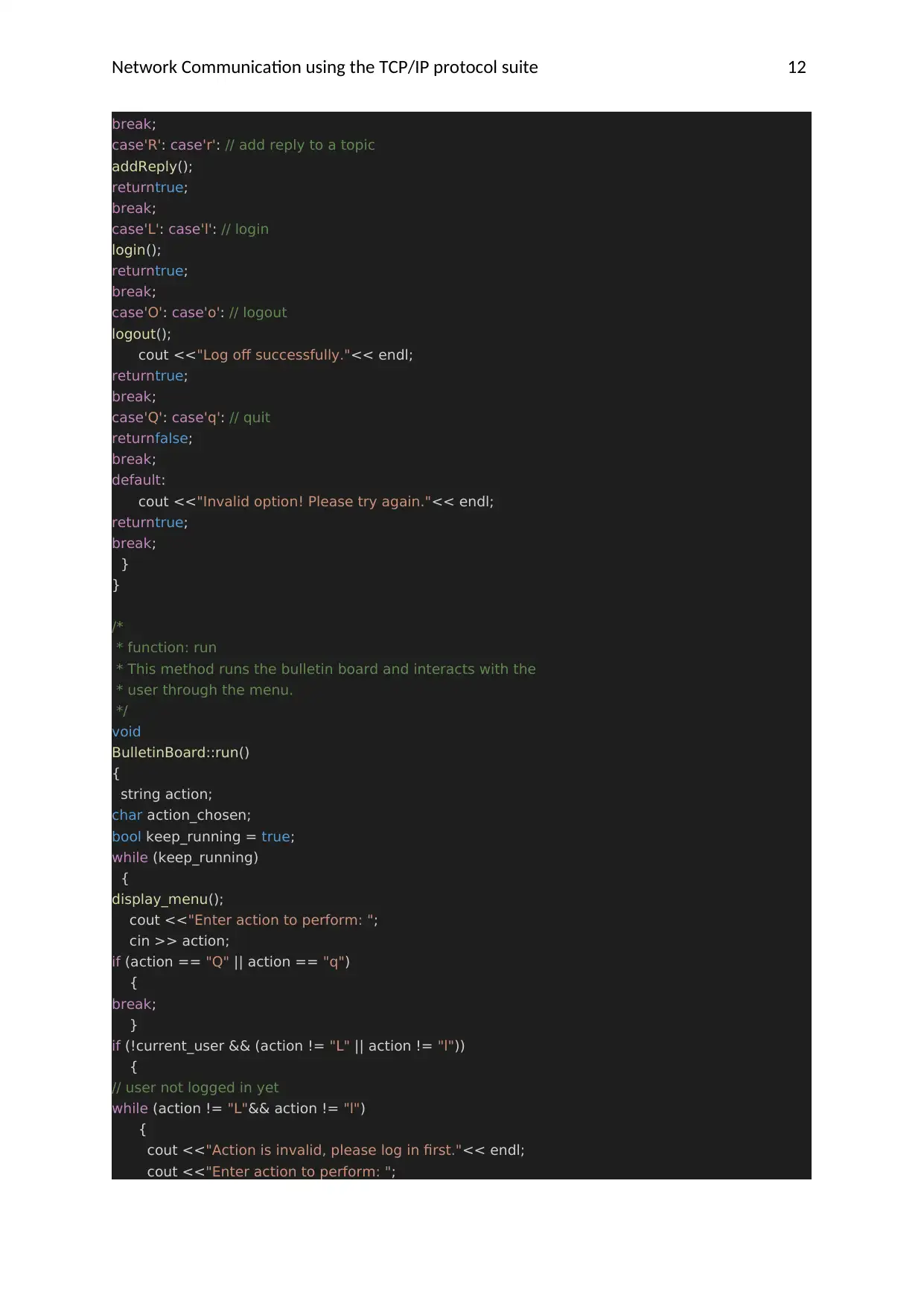
Network Communication using the TCP/IP protocol suite 12
break;
case'R': case'r': // add reply to a topic
addReply();
returntrue;
break;
case'L': case'l': // login
login();
returntrue;
break;
case'O': case'o': // logout
logout();
cout <<"Log off successfully."<< endl;
returntrue;
break;
case'Q': case'q': // quit
returnfalse;
break;
default:
cout <<"Invalid option! Please try again."<< endl;
returntrue;
break;
}
}
/*
* function: run
* This method runs the bulletin board and interacts with the
* user through the menu.
*/
void
BulletinBoard::run()
{
string action;
char action_chosen;
bool keep_running = true;
while (keep_running)
{
display_menu();
cout <<"Enter action to perform: ";
cin >> action;
if (action == "Q" || action == "q")
{
break;
}
if (!current_user && (action != "L" || action != "l"))
{
// user not logged in yet
while (action != "L"&& action != "l")
{
cout <<"Action is invalid, please log in first."<< endl;
cout <<"Enter action to perform: ";
break;
case'R': case'r': // add reply to a topic
addReply();
returntrue;
break;
case'L': case'l': // login
login();
returntrue;
break;
case'O': case'o': // logout
logout();
cout <<"Log off successfully."<< endl;
returntrue;
break;
case'Q': case'q': // quit
returnfalse;
break;
default:
cout <<"Invalid option! Please try again."<< endl;
returntrue;
break;
}
}
/*
* function: run
* This method runs the bulletin board and interacts with the
* user through the menu.
*/
void
BulletinBoard::run()
{
string action;
char action_chosen;
bool keep_running = true;
while (keep_running)
{
display_menu();
cout <<"Enter action to perform: ";
cin >> action;
if (action == "Q" || action == "q")
{
break;
}
if (!current_user && (action != "L" || action != "l"))
{
// user not logged in yet
while (action != "L"&& action != "l")
{
cout <<"Action is invalid, please log in first."<< endl;
cout <<"Enter action to perform: ";
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





