Challenges, Architectures, and Security of Cloud Computing with AWS
VerifiedAdded on 2021/05/30
|15
|4861
|117
Report
AI Summary
This report delves into the realm of cloud computing, examining its architectures, specifically focusing on Amazon Web Services (AWS). It explores the benefits of implementing a hybrid cloud, such as cost reduction and enhanced scalability, while also addressing associated risks like security vulnerabilities and data redundancy issues. The report presents proposed information security controls, including data encryption, risk assessments, and redundancy methods to mitigate these risks. Furthermore, it discusses the implementation of authentication and identity methods, along with strong security management practices, to ensure the secure and efficient operation of hybrid cloud environments. The analysis extends to the use of microservices and their integration within the hybrid cloud framework, highlighting the importance of interoperability and well-defined management strategies.

Abstract
Cloud Computing is the latest technological development that is in demand. It has led to the
storage of data and made it easy for organizations and companies to share resources which
include services networks applications and servers. These resources can be accessed with ease
and minimal interaction with the cloud service providers. Development of cloud computing has
its own challenges and some include developing new cloud technology software. The major
challenges are fact are due to the complexity of cloud applications when building due to the
different service providers. Each service provider has their own infrastructure and this makes it
difficult to create an application that will be able to integrate with all the providers. Cloud
computing applications demand that they be updated constantly to fit in with the ever-changing
architecture, design, testing and evolution of software. Cloud computing architectures differ in a
big way than the traditional systems and applications that we are used to. Most challenges are
architecture and infrastructure related or on services provided by other cloud service providers.
There is minimal support in terms of cloud architecture to ensure that the use of the cloud
technology is done in an efficient and systematic way. For instance, it is reasonable to think that
software architectures need to be described in a different way if they are deployed on the cloud.
Therefore, it is necessary to provide an architectural support to their project and means to model
them and capture important elements regarding the Cloud Computing paradigm.
Cloud Computing is the latest technological development that is in demand. It has led to the
storage of data and made it easy for organizations and companies to share resources which
include services networks applications and servers. These resources can be accessed with ease
and minimal interaction with the cloud service providers. Development of cloud computing has
its own challenges and some include developing new cloud technology software. The major
challenges are fact are due to the complexity of cloud applications when building due to the
different service providers. Each service provider has their own infrastructure and this makes it
difficult to create an application that will be able to integrate with all the providers. Cloud
computing applications demand that they be updated constantly to fit in with the ever-changing
architecture, design, testing and evolution of software. Cloud computing architectures differ in a
big way than the traditional systems and applications that we are used to. Most challenges are
architecture and infrastructure related or on services provided by other cloud service providers.
There is minimal support in terms of cloud architecture to ensure that the use of the cloud
technology is done in an efficient and systematic way. For instance, it is reasonable to think that
software architectures need to be described in a different way if they are deployed on the cloud.
Therefore, it is necessary to provide an architectural support to their project and means to model
them and capture important elements regarding the Cloud Computing paradigm.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Proposed Architectures for a Hybrid Cloud
Amazon Web Services (AWS)
Amazon Web Services (AWS). offers a broad set of global compute, storage, database,
analytics, application, and deployment services that help organizations move faster, lower IT
costs, and scale applications. Amazon Web Services (AWS) is provided by Amazon and
provides a mix of infrastructure as a service (IaaS), platform as a service (PaaS) and packaged
software as a service (SaaS) offerings.
AWS services include:
Amazon Elastic Computer Cloud (EC2)
Amazon Simple Storage Service (Amazon S3)
Amazon CloudFront
Amazon Relational Database Service (Amazon RDS)
Amazon SimpleDB
Amazon Simple Notification Service (Amazon SNS)
Amazon Simple Queue Service (Amazon SQS)
Amazon Virtual Private Cloud (Amazon VPC)
Compute
Instances are virtual servers found in an Amazon Elastic Compute Cloud (EC2) that assist to
increase the capacity for computing. There are different instances with different sizes and
capacity suited for a specific type of work and applications. These jobs include those that utilize
a lot of memory and jobs that need acceleration. AWS has an automatic tool designed for
increasing or decreasing the capacity so as to maintain good performance and the health of
instances
Storage
Amazon Simple Storage Service (S3) provides scalable storage which can range up to 5GB for
backup of data analysis and archive data. With S3, an enterprise can reduce cost by not accessing
its storage tier frequently or use of long-term cold storage which is provided by Amazon glacier
Amazon Web Services (AWS)
Amazon Web Services (AWS). offers a broad set of global compute, storage, database,
analytics, application, and deployment services that help organizations move faster, lower IT
costs, and scale applications. Amazon Web Services (AWS) is provided by Amazon and
provides a mix of infrastructure as a service (IaaS), platform as a service (PaaS) and packaged
software as a service (SaaS) offerings.
AWS services include:
Amazon Elastic Computer Cloud (EC2)
Amazon Simple Storage Service (Amazon S3)
Amazon CloudFront
Amazon Relational Database Service (Amazon RDS)
Amazon SimpleDB
Amazon Simple Notification Service (Amazon SNS)
Amazon Simple Queue Service (Amazon SQS)
Amazon Virtual Private Cloud (Amazon VPC)
Compute
Instances are virtual servers found in an Amazon Elastic Compute Cloud (EC2) that assist to
increase the capacity for computing. There are different instances with different sizes and
capacity suited for a specific type of work and applications. These jobs include those that utilize
a lot of memory and jobs that need acceleration. AWS has an automatic tool designed for
increasing or decreasing the capacity so as to maintain good performance and the health of
instances
Storage
Amazon Simple Storage Service (S3) provides scalable storage which can range up to 5GB for
backup of data analysis and archive data. With S3, an enterprise can reduce cost by not accessing
its storage tier frequently or use of long-term cold storage which is provided by Amazon glacier

Block-level storage volumes are provided by Amazon Elastic Block Store which ensures that
there EC2 instances have data they can use. Managed cloud-based file storage is provided by
Amazon Elastic File System.
Databases, data management
Amazon Relational Database Service can be used to manage the database services, which include
Oracle, SQL Server, PostgreSQL, MySQL and a proprietary high-performance database called
Amazon Aurora. NoSQL databases are also managed and offered by AWS through Amazon
DynamoDB.
Business intelligence tasks are made easier for data analysts to perform by use of a data
warehouse which is offered by Amazon Redshift.
Migration, hybrid cloud
Users can move applications, databases, servers and data onto its public cloud with ease through
the tools provide by AWS. AWS has a Hub used for Migration which provides monitoring of
locations and management of migrations to the cloud. The EC2 Systems helps Managers and the
IT guys in configuration of on-premises servers and instances once in the cloud.
Networking
An administrator has control over a virtual network by using the Amazon Virtual Private Cloud
(VPC). For extra protection, AWS automatically provides new resources within a VPC.
AWS has load balancing tools which enable the admins to balance network traffic. These include
Application Load Balancer and Network Load Balance. Amazon Route 53 is a domain name that
routes end users to applications is also provided by AWS.
Development tools and application services
Developers can make use of AWS command-line tools and SDKs for deployment and
management of applications and services. Management of cloud services from a windows
environment can be done by AWS Tools for PowerShell and testing and simulation of lambda
functions is done through the AWS Serverless Application Model. The platforms and languages
that are supported by AWS SDKs include Java, PHP, Python, Node.js, Ruby, C++, Android and
iOS (Gai, Journal of Network and Computer Applications,, 2016).
Management, monitoring
there EC2 instances have data they can use. Managed cloud-based file storage is provided by
Amazon Elastic File System.
Databases, data management
Amazon Relational Database Service can be used to manage the database services, which include
Oracle, SQL Server, PostgreSQL, MySQL and a proprietary high-performance database called
Amazon Aurora. NoSQL databases are also managed and offered by AWS through Amazon
DynamoDB.
Business intelligence tasks are made easier for data analysts to perform by use of a data
warehouse which is offered by Amazon Redshift.
Migration, hybrid cloud
Users can move applications, databases, servers and data onto its public cloud with ease through
the tools provide by AWS. AWS has a Hub used for Migration which provides monitoring of
locations and management of migrations to the cloud. The EC2 Systems helps Managers and the
IT guys in configuration of on-premises servers and instances once in the cloud.
Networking
An administrator has control over a virtual network by using the Amazon Virtual Private Cloud
(VPC). For extra protection, AWS automatically provides new resources within a VPC.
AWS has load balancing tools which enable the admins to balance network traffic. These include
Application Load Balancer and Network Load Balance. Amazon Route 53 is a domain name that
routes end users to applications is also provided by AWS.
Development tools and application services
Developers can make use of AWS command-line tools and SDKs for deployment and
management of applications and services. Management of cloud services from a windows
environment can be done by AWS Tools for PowerShell and testing and simulation of lambda
functions is done through the AWS Serverless Application Model. The platforms and languages
that are supported by AWS SDKs include Java, PHP, Python, Node.js, Ruby, C++, Android and
iOS (Gai, Journal of Network and Computer Applications,, 2016).
Management, monitoring
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Managing and tracking cloud resources configuration by an administrator is made easy via AWS
Configuration and AWS Configuration Rules. These tools assist the IT team avoid to configure
and deploy cloud resources in an effective and efficient manner.
AWS CloudFormation templates, AWS OpsWorks and Chef can be used by an administrator to
automatically configure systems and infrastructure.
Security, governance
An administrator can manage and define user access to resources through the use of AWS
identity and Access management tools. These tools provide cloud security. A user directory can
also be created by an admin or the admin can link the directory to an existing one such as the
Active Directory by Microsoft with the Amazon Web Directory Service. Such services help the
organization in establishing and managing policies even multiple accounts.
Potential security risks are also automatically assessed and detected by tools the service provider
has introduced or provided. An example is the Amazon Inspector which analyzes and finds
vulnerabilities in the environment that might have an impact in security and compliance.
Artificial intelligence
Artificial intelligence model development and delivery platforms is provided by AWS. The
Amazon AI suite has tools such as Polly for text to speech translation, image and facial
Recognition and analysis, Amazon Lex for voice and text chatbot technology. Smart apps can
also be built by developers which rely on complex algorithms and machine learning.
Mobile development
Mobile app developers are provided with a wide range of tools and services such as SDKs and
libraries. These collections of tools are offered by AWS Mobile Hub.
Management of user access to mobile apps can be done through the Amazon Cognito while
sending of push notifications to end users and performing of analysis on how effective these
communications are, is done by Amazon Pinpoint
Messages, notifications
Communication for users and applications can be done through the AWS messaging services.
Sending storing and receiving communication between components of a distributed applications
are managed by a Simple Queue Service in Amazon. This ensures that all the parts of the
application work as required.
Configuration and AWS Configuration Rules. These tools assist the IT team avoid to configure
and deploy cloud resources in an effective and efficient manner.
AWS CloudFormation templates, AWS OpsWorks and Chef can be used by an administrator to
automatically configure systems and infrastructure.
Security, governance
An administrator can manage and define user access to resources through the use of AWS
identity and Access management tools. These tools provide cloud security. A user directory can
also be created by an admin or the admin can link the directory to an existing one such as the
Active Directory by Microsoft with the Amazon Web Directory Service. Such services help the
organization in establishing and managing policies even multiple accounts.
Potential security risks are also automatically assessed and detected by tools the service provider
has introduced or provided. An example is the Amazon Inspector which analyzes and finds
vulnerabilities in the environment that might have an impact in security and compliance.
Artificial intelligence
Artificial intelligence model development and delivery platforms is provided by AWS. The
Amazon AI suite has tools such as Polly for text to speech translation, image and facial
Recognition and analysis, Amazon Lex for voice and text chatbot technology. Smart apps can
also be built by developers which rely on complex algorithms and machine learning.
Mobile development
Mobile app developers are provided with a wide range of tools and services such as SDKs and
libraries. These collections of tools are offered by AWS Mobile Hub.
Management of user access to mobile apps can be done through the Amazon Cognito while
sending of push notifications to end users and performing of analysis on how effective these
communications are, is done by Amazon Pinpoint
Messages, notifications
Communication for users and applications can be done through the AWS messaging services.
Sending storing and receiving communication between components of a distributed applications
are managed by a Simple Queue Service in Amazon. This ensures that all the parts of the
application work as required.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Sending of push messages and pub-sub messages to mobile devices and services are provided by
Amazon Simple Notification Service (SNS). Receiving and sending of mails is provided a simple
Email Service in Amazon
2. a.) The benefits against implementing the architecture are:
1. Cost is reduced. The entire cost of the hardware will be reduced as no computing resources
will be needed in the organisation (Botta, 2016). The will be depreciation and reduction of the
monthly cost making the monthly review of system usage to be very much absent (Wei, 2014).
The introduction of this cloud architecture will make the hardware’s used before to fade and
much ensuring that the cost that was in maintaining the data will be used in paying the services
provided by the AWS.
2. Scalability is enhanced. The flexibility and extensibility of the cloud computing has made it
possible in transferring files and information from private clouds to public cloud networks for the
purpose of testing all the latest applications.
The speed of the Service. This resources are said to be virtual in that they adopt the objectives of
the business very easily. . There has been fast expansion of the speeds of bandwidth according to
requirements (Buyya, 2013).
Lastly is the integration of the information in one platform (Chen, 2015). This has helped to
deliver the easy access to all traditional databases of SQL. It has further given opportunities to
analysis of limited requirements of the business.
Amazon Simple Notification Service (SNS). Receiving and sending of mails is provided a simple
Email Service in Amazon
2. a.) The benefits against implementing the architecture are:
1. Cost is reduced. The entire cost of the hardware will be reduced as no computing resources
will be needed in the organisation (Botta, 2016). The will be depreciation and reduction of the
monthly cost making the monthly review of system usage to be very much absent (Wei, 2014).
The introduction of this cloud architecture will make the hardware’s used before to fade and
much ensuring that the cost that was in maintaining the data will be used in paying the services
provided by the AWS.
2. Scalability is enhanced. The flexibility and extensibility of the cloud computing has made it
possible in transferring files and information from private clouds to public cloud networks for the
purpose of testing all the latest applications.
The speed of the Service. This resources are said to be virtual in that they adopt the objectives of
the business very easily. . There has been fast expansion of the speeds of bandwidth according to
requirements (Buyya, 2013).
Lastly is the integration of the information in one platform (Chen, 2015). This has helped to
deliver the easy access to all traditional databases of SQL. It has further given opportunities to
analysis of limited requirements of the business.
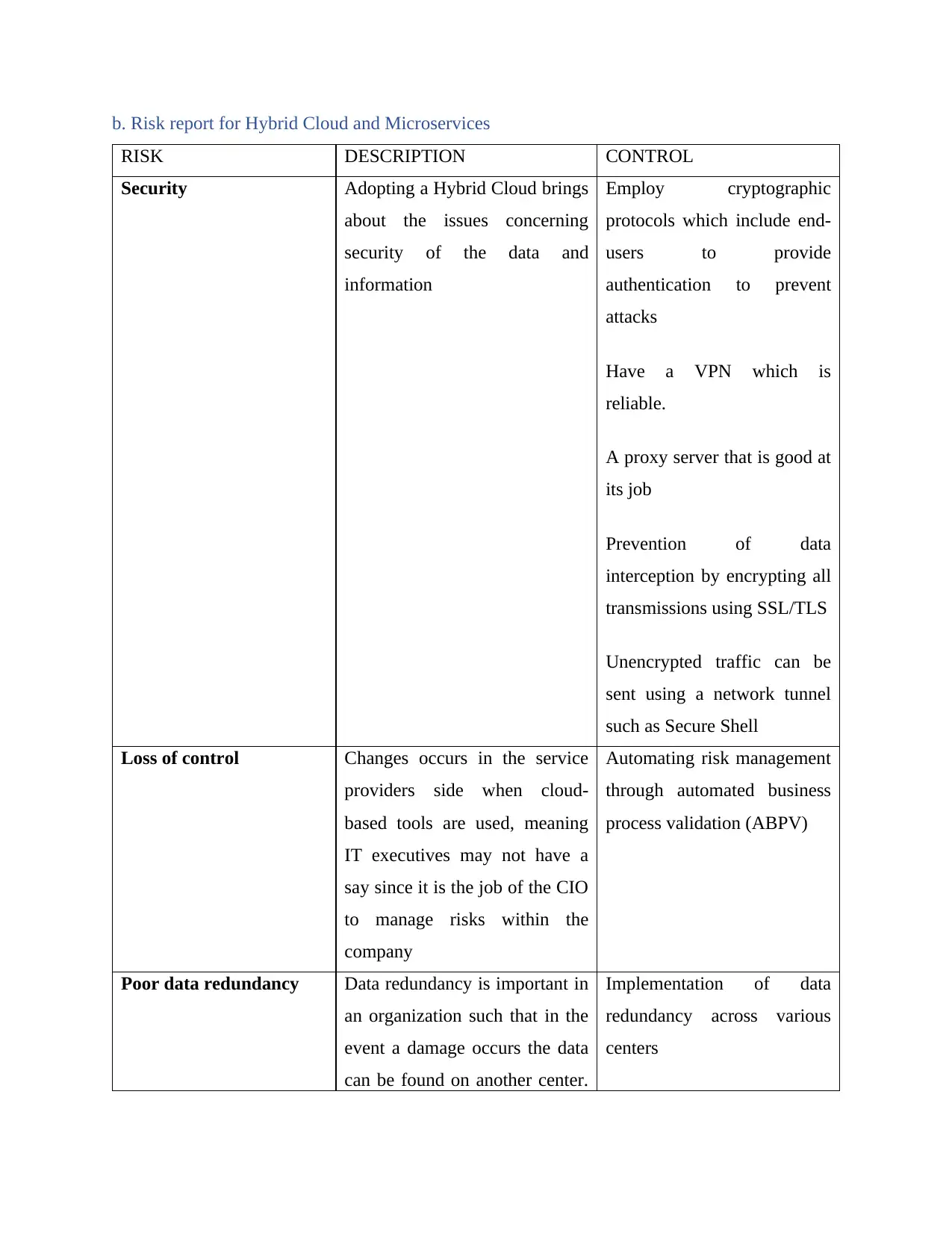
b. Risk report for Hybrid Cloud and Microservices
RISK DESCRIPTION CONTROL
Security Adopting a Hybrid Cloud brings
about the issues concerning
security of the data and
information
Employ cryptographic
protocols which include end-
users to provide
authentication to prevent
attacks
Have a VPN which is
reliable.
A proxy server that is good at
its job
Prevention of data
interception by encrypting all
transmissions using SSL/TLS
Unencrypted traffic can be
sent using a network tunnel
such as Secure Shell
Loss of control Changes occurs in the service
providers side when cloud-
based tools are used, meaning
IT executives may not have a
say since it is the job of the CIO
to manage risks within the
company
Automating risk management
through automated business
process validation (ABPV)
Poor data redundancy Data redundancy is important in
an organization such that in the
event a damage occurs the data
can be found on another center.
Implementation of data
redundancy across various
centers
RISK DESCRIPTION CONTROL
Security Adopting a Hybrid Cloud brings
about the issues concerning
security of the data and
information
Employ cryptographic
protocols which include end-
users to provide
authentication to prevent
attacks
Have a VPN which is
reliable.
A proxy server that is good at
its job
Prevention of data
interception by encrypting all
transmissions using SSL/TLS
Unencrypted traffic can be
sent using a network tunnel
such as Secure Shell
Loss of control Changes occurs in the service
providers side when cloud-
based tools are used, meaning
IT executives may not have a
say since it is the job of the CIO
to manage risks within the
company
Automating risk management
through automated business
process validation (ABPV)
Poor data redundancy Data redundancy is important in
an organization such that in the
event a damage occurs the data
can be found on another center.
Implementation of data
redundancy across various
centers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
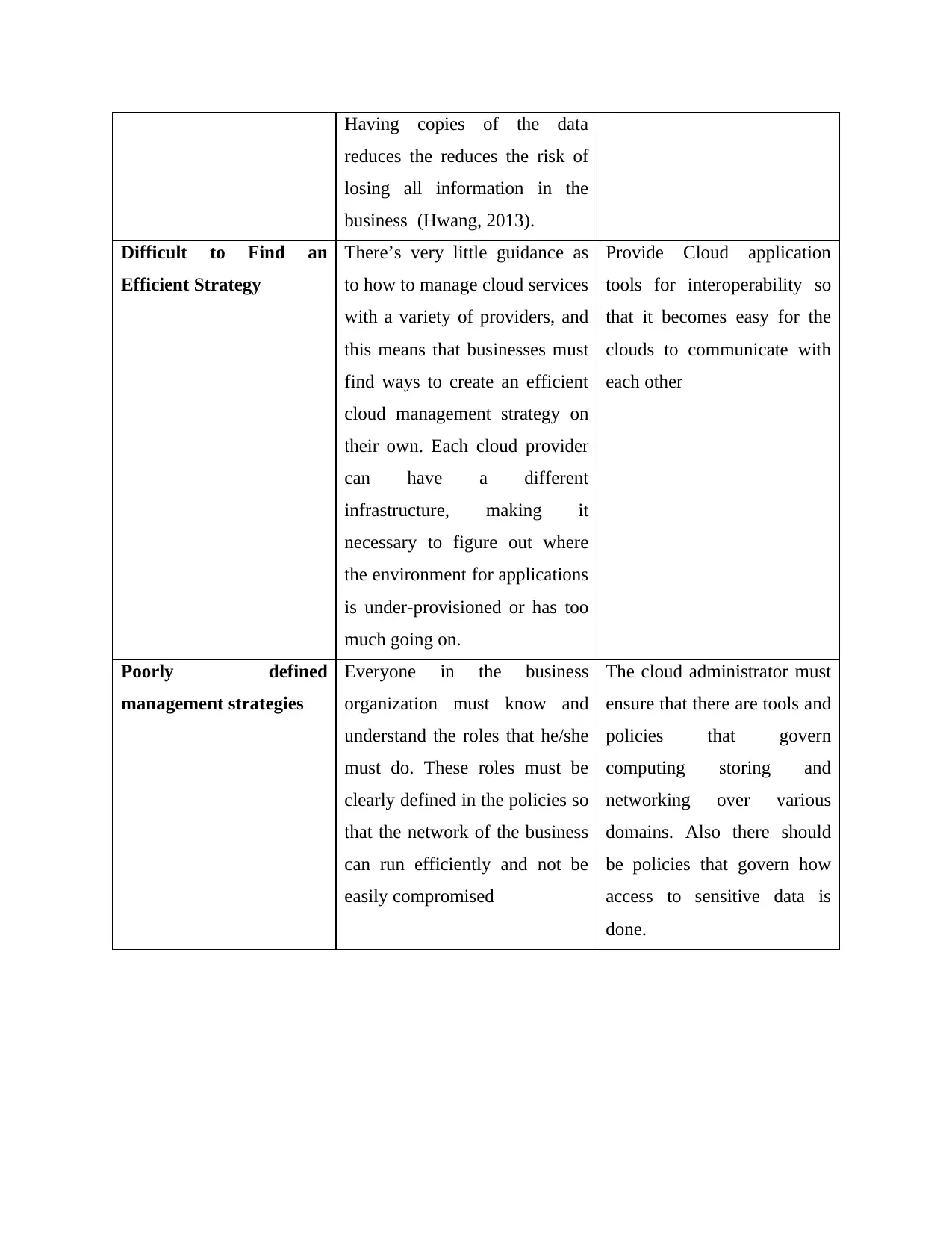
Having copies of the data
reduces the reduces the risk of
losing all information in the
business (Hwang, 2013).
Difficult to Find an
Efficient Strategy
There’s very little guidance as
to how to manage cloud services
with a variety of providers, and
this means that businesses must
find ways to create an efficient
cloud management strategy on
their own. Each cloud provider
can have a different
infrastructure, making it
necessary to figure out where
the environment for applications
is under-provisioned or has too
much going on.
Provide Cloud application
tools for interoperability so
that it becomes easy for the
clouds to communicate with
each other
Poorly defined
management strategies
Everyone in the business
organization must know and
understand the roles that he/she
must do. These roles must be
clearly defined in the policies so
that the network of the business
can run efficiently and not be
easily compromised
The cloud administrator must
ensure that there are tools and
policies that govern
computing storing and
networking over various
domains. Also there should
be policies that govern how
access to sensitive data is
done.
reduces the reduces the risk of
losing all information in the
business (Hwang, 2013).
Difficult to Find an
Efficient Strategy
There’s very little guidance as
to how to manage cloud services
with a variety of providers, and
this means that businesses must
find ways to create an efficient
cloud management strategy on
their own. Each cloud provider
can have a different
infrastructure, making it
necessary to figure out where
the environment for applications
is under-provisioned or has too
much going on.
Provide Cloud application
tools for interoperability so
that it becomes easy for the
clouds to communicate with
each other
Poorly defined
management strategies
Everyone in the business
organization must know and
understand the roles that he/she
must do. These roles must be
clearly defined in the policies so
that the network of the business
can run efficiently and not be
easily compromised
The cloud administrator must
ensure that there are tools and
policies that govern
computing storing and
networking over various
domains. Also there should
be policies that govern how
access to sensitive data is
done.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. Proposed Information Security controls
Employ data encryption techniques.
This is to avoid people from outside to eavesdrop or attack the network to gain access to the
information. E.g. Man-in-the-middle attack that impersonates endpoints and make it easier for
the intruder to acquire the information. This can be achieved by Shielding transmissions with
cryptographic protocols that include endpoint authentication, use of protocols such as Secure
Shell (SSH) to send unencrypted traffic over a network and use of a reliable proxy server and
VPN
Performing adequate security risk assessments.
This helps network administrators to determine how where and when an intrusion has occurred.
It helps minimize unwanted access to the company’s data. This can be achieved through frequent
rigorous risk prevention and assessment activities. Malicious activities should also be scanned
using IDS/IPS systems (Jula, Expert Systems with Applications, 2014).
Good data redundancy methods
Failure to implement redundancy puts the hybrid cloud and the business at risk. Distributing data
across all data centers reduces the damage that occurs when one data center fails. Implementing
redundancy can be accomplished. This can be done by using multiple data centers from one
cloud service provider.
Provision of authentication and identity methods
How to manage security is important when trying to combine public and private clouds in a
hybrid cloud. Sharing of security controls between the business and the cloud service providers
is a must. This can be achieved through monitoring and verifying all access permissions and
also synchronizing security of data by using an IP Multimedia Core Network Subsystem (IMS).
Employ data encryption techniques.
This is to avoid people from outside to eavesdrop or attack the network to gain access to the
information. E.g. Man-in-the-middle attack that impersonates endpoints and make it easier for
the intruder to acquire the information. This can be achieved by Shielding transmissions with
cryptographic protocols that include endpoint authentication, use of protocols such as Secure
Shell (SSH) to send unencrypted traffic over a network and use of a reliable proxy server and
VPN
Performing adequate security risk assessments.
This helps network administrators to determine how where and when an intrusion has occurred.
It helps minimize unwanted access to the company’s data. This can be achieved through frequent
rigorous risk prevention and assessment activities. Malicious activities should also be scanned
using IDS/IPS systems (Jula, Expert Systems with Applications, 2014).
Good data redundancy methods
Failure to implement redundancy puts the hybrid cloud and the business at risk. Distributing data
across all data centers reduces the damage that occurs when one data center fails. Implementing
redundancy can be accomplished. This can be done by using multiple data centers from one
cloud service provider.
Provision of authentication and identity methods
How to manage security is important when trying to combine public and private clouds in a
hybrid cloud. Sharing of security controls between the business and the cloud service providers
is a must. This can be achieved through monitoring and verifying all access permissions and
also synchronizing security of data by using an IP Multimedia Core Network Subsystem (IMS).

Strong security management
When the business employs security measures such as authentication of all activities,
identification of all personell and authorization procedures for both their private and public
cloud, the security of the data is strong. Data security synchronization and use of services that
integrate well with the systems the business runs such as an Identity management system,
promotes efficiency and also ensuring that there is a local storage for storing sensitive data.
Secure the API’s
APIs when left unprotected, they are prone to malicious attacks and expose sensitive information
to the unauthorized person. API keys should be encrypted and dealt in the same way as code-
signing keys. To avoid security lapses always ensure to authenticate a third party before
releasing the keys to them.
Protection of Intellectual Property
Protection of Intellectual property (IP) is important in a business organization. The security
protocols put in place to protect IP my contain high levels of encryption. An assessment to
determine vulnerability should be carried out frequently. Since automated systems are not fully
adequate to classify IP and quantify the risks involved, a manual system should be employed.
Classification of IP is important so that risks involved can easily be identified.
Ensuring the Service Level Agreements are well defined
The Service Level Agreement in a business should be well defined and also clearly spell out the
security measures and the permissions that an organization has over its data when moving to the
cloud. The agreement also should clearly spell out the rights the service provider has over the
data of the business. It should also spell out what action the customer can take if the service is
disrupted or there is a breach of their data. And finally, have the SLA reviewed by an attorney
before signing.
When the business employs security measures such as authentication of all activities,
identification of all personell and authorization procedures for both their private and public
cloud, the security of the data is strong. Data security synchronization and use of services that
integrate well with the systems the business runs such as an Identity management system,
promotes efficiency and also ensuring that there is a local storage for storing sensitive data.
Secure the API’s
APIs when left unprotected, they are prone to malicious attacks and expose sensitive information
to the unauthorized person. API keys should be encrypted and dealt in the same way as code-
signing keys. To avoid security lapses always ensure to authenticate a third party before
releasing the keys to them.
Protection of Intellectual Property
Protection of Intellectual property (IP) is important in a business organization. The security
protocols put in place to protect IP my contain high levels of encryption. An assessment to
determine vulnerability should be carried out frequently. Since automated systems are not fully
adequate to classify IP and quantify the risks involved, a manual system should be employed.
Classification of IP is important so that risks involved can easily be identified.
Ensuring the Service Level Agreements are well defined
The Service Level Agreement in a business should be well defined and also clearly spell out the
security measures and the permissions that an organization has over its data when moving to the
cloud. The agreement also should clearly spell out the rights the service provider has over the
data of the business. It should also spell out what action the customer can take if the service is
disrupted or there is a breach of their data. And finally, have the SLA reviewed by an attorney
before signing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Disgruntled or malicious employees
Not all employees in a company and insiders have good intentions for the business. Some can
use sensitive data to distabalize the business activities. Therefore, the Content Security Policy
(CSP) managers must put in place security measures to keep track of the network activities the
employees engage themselves in to avoid malicious acts. They should limit access to the
organizations critical resources and assets. Protocols should also be put in place to detect and
react immediately to any malicious or suspicious activities in the network.
Denial of Service attacks
Weaknesses in shared resources such as CPU, RAM, and disk space or network bandwidth can
cause attackers to render a cloud service inaccessible by issuing a DoS attack. Sending bad
REST or SOAP requests from the business may cause a malicious person to perform a DoS
attack by exploiting the vulnerability in the cloud service API. To prevent DoS attack traffic can
be redirected to a mitigated device by the use of flow analytics tools. The tool must be scalable
to ensure it handles the growing traffic it analyzes and gathers. One disadvantage of using these
tools is that they not productive enough in tackling volumetric (DDoS) attacks.
4. BCP Changes
For an effective business continuity plan, an organization must put into consideration the security
required to put the data into the cloud. Some of the things to consider are the minimal time taken
to recover the data and e-discovery access. The cloud service providers disaster recovery and
business continuity plans should be reviewed to ensure that they align with those of the
organization. Also, the organization should know how their service providers plans affect the
continuity of operations and access to data (Pluzhnik, In Services (SERVICES),, 2014).
Business continuity plan should address issues that arise from compliance with laws and policies
of any given country or organization. If the service provider stores the data in a different country
Not all employees in a company and insiders have good intentions for the business. Some can
use sensitive data to distabalize the business activities. Therefore, the Content Security Policy
(CSP) managers must put in place security measures to keep track of the network activities the
employees engage themselves in to avoid malicious acts. They should limit access to the
organizations critical resources and assets. Protocols should also be put in place to detect and
react immediately to any malicious or suspicious activities in the network.
Denial of Service attacks
Weaknesses in shared resources such as CPU, RAM, and disk space or network bandwidth can
cause attackers to render a cloud service inaccessible by issuing a DoS attack. Sending bad
REST or SOAP requests from the business may cause a malicious person to perform a DoS
attack by exploiting the vulnerability in the cloud service API. To prevent DoS attack traffic can
be redirected to a mitigated device by the use of flow analytics tools. The tool must be scalable
to ensure it handles the growing traffic it analyzes and gathers. One disadvantage of using these
tools is that they not productive enough in tackling volumetric (DDoS) attacks.
4. BCP Changes
For an effective business continuity plan, an organization must put into consideration the security
required to put the data into the cloud. Some of the things to consider are the minimal time taken
to recover the data and e-discovery access. The cloud service providers disaster recovery and
business continuity plans should be reviewed to ensure that they align with those of the
organization. Also, the organization should know how their service providers plans affect the
continuity of operations and access to data (Pluzhnik, In Services (SERVICES),, 2014).
Business continuity plan should address issues that arise from compliance with laws and policies
of any given country or organization. If the service provider stores the data in a different country
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

then the business should comply with the laws of that company and also the international. For
example, the Data Protection Act states that information of personal nature should be kept for a
said period of time but have a backup on the cloud service provider unless they have a secure
deletion process when reusing backup media
The business should consider having multiple ISP to ensure their Internet connection runs
smoothly without any hinderance and ensure continuity of the business. Organization data need
to be accessed on a 24hr basis, loss of internet could be disastrous to the company. Access to the
cloud information should be there at all times.
For the business to continue its plans of actions designed to achieve its objectives, migration
plans from one service provider to another are necessary in case a service provider increases its
charges or the services provided do not align with the business long term objectives. To do this
the business has to make a list of potential service providers whose policies align with that of the
business. Also the business has to know the costs it will incur in process of moving the data and
also training of staff. In doing this makes the business to have more control in the planning
process.
5. Analysis of requirements:
5.1 Remote Server Administration Tools
There are a lot of requirements that are needed when remotely accessing the server
administration tools which are in a remote place (microsoft, 2017). In this case we consider the
windows 8 which is incorporating the windows 8 server manager with all the tools such as the
management Console (snaps in), Cmdlets of the windows PowerShell and the suppliers involved
(Lu, 2015). The tools that are included are such as the Command line tools (using CMD) used
for controlling all the responsibilities and features that are used for running the window server of
2012. In some cases it may occur that some restriction may be put in place such that the
instruments that need utilization in overseeing all the parts and components that it runs on which
may be the Window Server 2008 R2 or the Window server 2008 itself. The requirements that are
used in windows Server 2008 R2 and those of Windows server 2008 will perform the same
controls as those of windows 2003 though in a more advance way.
example, the Data Protection Act states that information of personal nature should be kept for a
said period of time but have a backup on the cloud service provider unless they have a secure
deletion process when reusing backup media
The business should consider having multiple ISP to ensure their Internet connection runs
smoothly without any hinderance and ensure continuity of the business. Organization data need
to be accessed on a 24hr basis, loss of internet could be disastrous to the company. Access to the
cloud information should be there at all times.
For the business to continue its plans of actions designed to achieve its objectives, migration
plans from one service provider to another are necessary in case a service provider increases its
charges or the services provided do not align with the business long term objectives. To do this
the business has to make a list of potential service providers whose policies align with that of the
business. Also the business has to know the costs it will incur in process of moving the data and
also training of staff. In doing this makes the business to have more control in the planning
process.
5. Analysis of requirements:
5.1 Remote Server Administration Tools
There are a lot of requirements that are needed when remotely accessing the server
administration tools which are in a remote place (microsoft, 2017). In this case we consider the
windows 8 which is incorporating the windows 8 server manager with all the tools such as the
management Console (snaps in), Cmdlets of the windows PowerShell and the suppliers involved
(Lu, 2015). The tools that are included are such as the Command line tools (using CMD) used
for controlling all the responsibilities and features that are used for running the window server of
2012. In some cases it may occur that some restriction may be put in place such that the
instruments that need utilization in overseeing all the parts and components that it runs on which
may be the Window Server 2008 R2 or the Window server 2008 itself. The requirements that are
used in windows Server 2008 R2 and those of Windows server 2008 will perform the same
controls as those of windows 2003 though in a more advance way.

5.2 Requirements of resource management
The second part of the requirements is understanding what is required in the management of
resources remotely (Zhang, 2014). In this case we may require the OnCommand cloud manager
in utilizing the ways we can use in delivering the core point to manage all endpoint of the data
fabric (Li, 2015). All of this done is on the cloud (Leymann, 2015). This has helped in
replicating the information that surrounds the multiple clouds and the storage of hybrid. The
OnCommand tool may further be managed on the expense of storage in the cloud.
5.3 SLA Management.
The movement in the cloud has a number of consequences that it encounters. Most of these
changes are very imperative using the standards of SLA. In the past the IT teams who were
undertaking the SLA had finished the control over all assets they owned and characterizing their
SLAs with regards to the abilities their domain can dominate in situations when it is closed or
even in the on-premises. The open cloud presentation in that it does the separation of
conventional boundaries of all data in the data center. Nevertheless, since the hybrid cloud
contains the on-premises and the different off-premises assets then it may need to cover up all its
abilities in the atmosphere of the Information Technology.
6.0 (i) Description of the steps included in plan asked
In this case the AWS will be run in that we specifically use the SharePoint. The reason for the
deployment of AWS over the Amazon Website Service is scaling, performing and making it’s to
collaborate its platform very fast (Pluzhnik, Optimal control of applications for hybrid cloud
services. In Services, 2014). The advantages of SharePoint in AWS cloud in that they are used in
benefiting the clients and users of such services and must be considered in all ways. The key
steps that are used from migrating the email instance from its current service to AWS cloud is as
follows.
1. How scalable the SharePoint over the Amazon Website Service Cloud will be when we
migrate. In this case we have to ask so many questions with regards to what we want in
future with regards to storage and access. This is a very key point for any migration
process and If the platform will not allow expansion or extensibility then it might be hard
for a company to adapt to such services as it will not meet their requirements.
The second part of the requirements is understanding what is required in the management of
resources remotely (Zhang, 2014). In this case we may require the OnCommand cloud manager
in utilizing the ways we can use in delivering the core point to manage all endpoint of the data
fabric (Li, 2015). All of this done is on the cloud (Leymann, 2015). This has helped in
replicating the information that surrounds the multiple clouds and the storage of hybrid. The
OnCommand tool may further be managed on the expense of storage in the cloud.
5.3 SLA Management.
The movement in the cloud has a number of consequences that it encounters. Most of these
changes are very imperative using the standards of SLA. In the past the IT teams who were
undertaking the SLA had finished the control over all assets they owned and characterizing their
SLAs with regards to the abilities their domain can dominate in situations when it is closed or
even in the on-premises. The open cloud presentation in that it does the separation of
conventional boundaries of all data in the data center. Nevertheless, since the hybrid cloud
contains the on-premises and the different off-premises assets then it may need to cover up all its
abilities in the atmosphere of the Information Technology.
6.0 (i) Description of the steps included in plan asked
In this case the AWS will be run in that we specifically use the SharePoint. The reason for the
deployment of AWS over the Amazon Website Service is scaling, performing and making it’s to
collaborate its platform very fast (Pluzhnik, Optimal control of applications for hybrid cloud
services. In Services, 2014). The advantages of SharePoint in AWS cloud in that they are used in
benefiting the clients and users of such services and must be considered in all ways. The key
steps that are used from migrating the email instance from its current service to AWS cloud is as
follows.
1. How scalable the SharePoint over the Amazon Website Service Cloud will be when we
migrate. In this case we have to ask so many questions with regards to what we want in
future with regards to storage and access. This is a very key point for any migration
process and If the platform will not allow expansion or extensibility then it might be hard
for a company to adapt to such services as it will not meet their requirements.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




