MITS5002 Software Engineering: State-of-the-Art Cyber-Security
VerifiedAdded on 2022/09/18
|13
|900
|44
Report
AI Summary
This report provides an overview of cyber security in cloud computing, highlighting the features and characteristics of cloud computing and discussing various cloud service models. It examines service deployment models such as private, public, and hybrid clouds, and identifies the security challenges related to data security, cloud infrastructure, and application security. The report classifies cyber-security threats, discusses techniques to avoid them, and summarizes approachable threats with potential solutions. It also explores the use of encryption algorithms like AES and FHE, authentication and authorization methods, and security approaches like SLAs and Kerberos. The paper concludes by outlining possible future solutions based on further research in cloud computing. Desklib is your go-to platform for accessing similar solved assignments and past papers.
Overview of the State-of-the-Art
of Cloud Computing Cyber-
Security
Name of the Student
Name of the University
of Cloud Computing Cyber-
Security
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Purpose of the Paper
The research identifies the aspect of cyber security
in cloud computing
Highlights have been discussed on the features and
characteristics of cloud computing (Bennasar,
Bendahmane and Essaaidi 2017)
Understanding of the various cloud service models
have been discussed in brief
The research identifies the aspect of cyber security
in cloud computing
Highlights have been discussed on the features and
characteristics of cloud computing (Bennasar,
Bendahmane and Essaaidi 2017)
Understanding of the various cloud service models
have been discussed in brief

Purpose of the Paper
The service deployment in cloud has been
considered in the paper while understanding the
features being offered (Bhamare et al. 2015)
Challenges in the area of cloud security have been
shown and analyzed from different viewpoints
Approaches to understand the risks and mitigate
them from cloud computing have been researched
and analysed
The service deployment in cloud has been
considered in the paper while understanding the
features being offered (Bhamare et al. 2015)
Challenges in the area of cloud security have been
shown and analyzed from different viewpoints
Approaches to understand the risks and mitigate
them from cloud computing have been researched
and analysed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Overview of Cloud Computing and
Security
Cloud computing is considered as one of the prime computing
resources
Cloud offers a shared pool of resources such as Platform as a
Service (PaaS), Software as a Service (SaaS) and Infrastructure
as a Service (IaaS) (Freet et al. 2015)
Service deployment within the cloud deployment model have
been classified as – Private cloud, Public cloud and hybrid
cloud
Security
Cloud computing is considered as one of the prime computing
resources
Cloud offers a shared pool of resources such as Platform as a
Service (PaaS), Software as a Service (SaaS) and Infrastructure
as a Service (IaaS) (Freet et al. 2015)
Service deployment within the cloud deployment model have
been classified as – Private cloud, Public cloud and hybrid
cloud
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Overview of Cloud Computing and
Security
Various cloud actors form a part of the vast pool of cloud
resources
Security challenges are broadly posed over cloud security,
which are: data security, cloud infrastructure, cloud
applications security
Cyber-security threats and techniques to avoid have been
classified as: authorization and authentication, data integrity
and denial of service (Pustchi, Krishnan and Sandhu 2015)
The paper also highlights on the summary of approachable
threats and directions for the solutions for overcoming them
Security
Various cloud actors form a part of the vast pool of cloud
resources
Security challenges are broadly posed over cloud security,
which are: data security, cloud infrastructure, cloud
applications security
Cyber-security threats and techniques to avoid have been
classified as: authorization and authentication, data integrity
and denial of service (Pustchi, Krishnan and Sandhu 2015)
The paper also highlights on the summary of approachable
threats and directions for the solutions for overcoming them
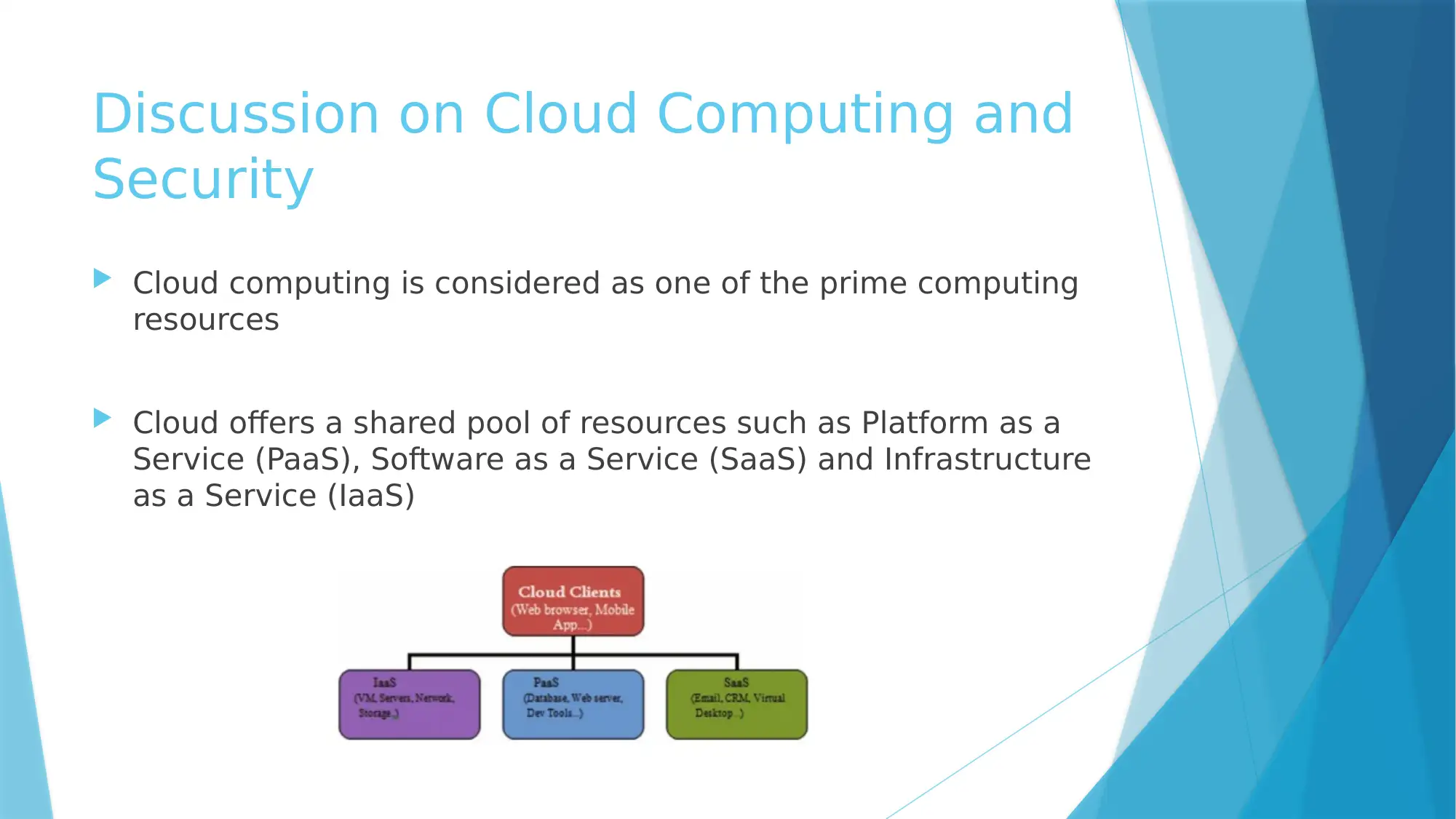
Discussion on Cloud Computing and
Security
Cloud computing is considered as one of the prime computing
resources
Cloud offers a shared pool of resources such as Platform as a
Service (PaaS), Software as a Service (SaaS) and Infrastructure
as a Service (IaaS)
Security
Cloud computing is considered as one of the prime computing
resources
Cloud offers a shared pool of resources such as Platform as a
Service (PaaS), Software as a Service (SaaS) and Infrastructure
as a Service (IaaS)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Discussion on Cloud Computing and
Security
Cyber-security challenges discussed in the paper focuses on:
Data security – Data stored in cloud repositories are primarily
attacked by DDoS attacks
Cloud Infrastructure Security – Untrusted network leads to
the prime security concern for cloud actors
Application Security – Cloud-based applications are mostly
affected to threats since they store millions of customer data
Security
Cyber-security challenges discussed in the paper focuses on:
Data security – Data stored in cloud repositories are primarily
attacked by DDoS attacks
Cloud Infrastructure Security – Untrusted network leads to
the prime security concern for cloud actors
Application Security – Cloud-based applications are mostly
affected to threats since they store millions of customer data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ensuring Security within Cloud
Computing
Encryption algorithms such as AES, Fully Homomorphic
Encryption (FHE), Plain RSA and FDE could be impactful for the
cloud (Yassein et al. 2017)
Performing authentication and authorization could help in
preventing attacks such as malicious intruders, account
hijacking and others
Security approaches such as Service Level Agreements (SLAs)
and Kerberos could be approached
Computing
Encryption algorithms such as AES, Fully Homomorphic
Encryption (FHE), Plain RSA and FDE could be impactful for the
cloud (Yassein et al. 2017)
Performing authentication and authorization could help in
preventing attacks such as malicious intruders, account
hijacking and others
Security approaches such as Service Level Agreements (SLAs)
and Kerberos could be approached

Ensuring Security within Cloud
Computing
Denial of Service threats could be mitigated with the following
approaches:
Network firewalls could be utilized for rejecting untrusted requests
(Jakimoski 2016)
IDPS would help in providing real-time intrusion system and method
while responding dynamically and blocking unwanted traffic
Reputation-based Voting (RBV) approach could be impactful for
large0scale grid computing systems
Computing
Denial of Service threats could be mitigated with the following
approaches:
Network firewalls could be utilized for rejecting untrusted requests
(Jakimoski 2016)
IDPS would help in providing real-time intrusion system and method
while responding dynamically and blocking unwanted traffic
Reputation-based Voting (RBV) approach could be impactful for
large0scale grid computing systems
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Conclusion of the Paper
The paper focus on the understanding of different
cloud service models and the underlying actors within
An overview over the security models and functioning
of the cloud resources have been formed
The threats posed within the cloud service platforms
have been outlined and discussed
The paper focus on the understanding of different
cloud service models and the underlying actors within
An overview over the security models and functioning
of the cloud resources have been formed
The threats posed within the cloud service platforms
have been outlined and discussed
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion of the Paper
Different major threats have been discussed and
understood
The approaches that could be taken for mitigating
them accordingly have been revised
Possible future solutions based on further research
over cloud computing have been focused.
Different major threats have been discussed and
understood
The approaches that could be taken for mitigating
them accordingly have been revised
Possible future solutions based on further research
over cloud computing have been focused.

References
Bennasar, H., Bendahmane, A. and Essaaidi, M., 2017, April. An overview of the state-of-the-art of
cloud computing cyber-security. In International Conference on Codes, Cryptology, and
Information Security (pp. 56-67). Springer, Cham.
Bhamare, D., Jain, R., Samaka, M., Vaszkun, G. and Erbad, A., 2015, March. Multi-cloud
distribution of virtual functions and dynamic service deployment: Open ADN perspective. In 2015
IEEE International Conference on Cloud Engineering (pp. 299-304). IEEE.
Freet, D., Agrawal, R., John, S. and Walker, J.J., 2015, October. Cloud forensics challenges from a
service model standpoint: IaaS, PaaS and SaaS. In Proceedings of the 7th International
Conference on Management of computational and collective intElligence in Digital
EcoSystems (pp. 148-155).
Jakimoski, K., 2016. Security techniques for data protection in cloud computing. International
Journal of Grid and Distributed Computing, 9(1), pp.49-56.
Pustchi, N., Krishnan, R. and Sandhu, R., 2015, April. Authorization federation in IaaS multi cloud.
In Proceedings of the 3rd International Workshop on Security in Cloud Computing (pp. 63-71).
Yassein, M.B., Aljawarneh, S., Qawasmeh, E., Mardini, W. and Khamayseh, Y., 2017, August.
Comprehensive study of symmetric key and asymmetric key encryption algorithms. In 2017
international conference on engineering and technology (ICET) (pp. 1-7). IEEE.
Bennasar, H., Bendahmane, A. and Essaaidi, M., 2017, April. An overview of the state-of-the-art of
cloud computing cyber-security. In International Conference on Codes, Cryptology, and
Information Security (pp. 56-67). Springer, Cham.
Bhamare, D., Jain, R., Samaka, M., Vaszkun, G. and Erbad, A., 2015, March. Multi-cloud
distribution of virtual functions and dynamic service deployment: Open ADN perspective. In 2015
IEEE International Conference on Cloud Engineering (pp. 299-304). IEEE.
Freet, D., Agrawal, R., John, S. and Walker, J.J., 2015, October. Cloud forensics challenges from a
service model standpoint: IaaS, PaaS and SaaS. In Proceedings of the 7th International
Conference on Management of computational and collective intElligence in Digital
EcoSystems (pp. 148-155).
Jakimoski, K., 2016. Security techniques for data protection in cloud computing. International
Journal of Grid and Distributed Computing, 9(1), pp.49-56.
Pustchi, N., Krishnan, R. and Sandhu, R., 2015, April. Authorization federation in IaaS multi cloud.
In Proceedings of the 3rd International Workshop on Security in Cloud Computing (pp. 63-71).
Yassein, M.B., Aljawarneh, S., Qawasmeh, E., Mardini, W. and Khamayseh, Y., 2017, August.
Comprehensive study of symmetric key and asymmetric key encryption algorithms. In 2017
international conference on engineering and technology (ICET) (pp. 1-7). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





