In-Depth Report on Cloud Computing: Types, Security, and Challenges
VerifiedAdded on 2023/06/07
|19
|4561
|259
Report
AI Summary
This report provides a comprehensive overview of cloud computing, beginning with the advantages such as cost savings, enhanced security, and increased flexibility. It contrasts public and private cloud models across tenancy, exposure, data center location, service management, and hardware components. The report then delves into considerations for implementing a private cloud, focusing on backup and recovery, security, performance, and flexibility. It also discusses the role of System Center in private cloud monitoring and operation. Furthermore, the report identifies security issues like data breaches, malware injection, insecure APIs, and denial-of-service attacks, proposing security controls such as strong data security policies, encryption, and DLP. Finally, it evaluates selection criteria for private and public cloud security and verifies the health status of System Center components such as Operations Manager and Virtual Machine Manager, emphasizing their roles in maintaining a healthy cloud environment. Desklib offers this and many more solved assignments for students.

Running Head: CLOUD COMPUTING 1
CLOUD COMPUTING
Student Name
Institution Affiliation
Facilitator
Course
Date
CLOUD COMPUTING
Student Name
Institution Affiliation
Facilitator
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING 2
Question 1:
(a) Advantages of Cloud Computing
Cost savings
once an organization migrates to cloud services, accessing the company data becomes
easy and fast hence saving time and resources in project startups. Again, the cloud infrastructure
has currently cleared the worry about paying for what an organization has not used through pay-
as-you-go approach. Meaning the organization will only pay for what it has used (Avram, 2014).
The system of pay as you go will equally apply on the data storage service implying that an
organization gets as much space as it needs but won’t be charged for space it doesn’t use. Keenly
considered together, these two factors will result into lower costs and higher returns.
Security
The issue of cloud computing security has been among the major hang ups worrying
organizations when it comes to adopting cloud computing solutions. After all, when organization
programs and files are not kept securely on site it’s not easy to detect (Botta, Persico & Pescapé,
2016). Again, the same way an organization can access its data remotely, it’s the same way cyber
criminals can access the same data. Considering that the full time role of cloud hosts is to
monitor the security of their client’s data, this makes the technology more secure as compared to
conventional in house systems where organizations divide the effort of security provision as a
myriad of its IT concerns. Statistics have indicated that most data breaches in organizations are
facilitated internally and therefore cloud computing can be much safer to store the organization’s
sensitive information off-site (Gangwar, Date & Ramaswamy, 2015).
Flexibility
Question 1:
(a) Advantages of Cloud Computing
Cost savings
once an organization migrates to cloud services, accessing the company data becomes
easy and fast hence saving time and resources in project startups. Again, the cloud infrastructure
has currently cleared the worry about paying for what an organization has not used through pay-
as-you-go approach. Meaning the organization will only pay for what it has used (Avram, 2014).
The system of pay as you go will equally apply on the data storage service implying that an
organization gets as much space as it needs but won’t be charged for space it doesn’t use. Keenly
considered together, these two factors will result into lower costs and higher returns.
Security
The issue of cloud computing security has been among the major hang ups worrying
organizations when it comes to adopting cloud computing solutions. After all, when organization
programs and files are not kept securely on site it’s not easy to detect (Botta, Persico & Pescapé,
2016). Again, the same way an organization can access its data remotely, it’s the same way cyber
criminals can access the same data. Considering that the full time role of cloud hosts is to
monitor the security of their client’s data, this makes the technology more secure as compared to
conventional in house systems where organizations divide the effort of security provision as a
myriad of its IT concerns. Statistics have indicated that most data breaches in organizations are
facilitated internally and therefore cloud computing can be much safer to store the organization’s
sensitive information off-site (Gangwar, Date & Ramaswamy, 2015).
Flexibility

CLOUD COMPUTING 3
Any business strives to achieve its goals and meet all its customer demands. However, if
the finite time the business management has is divided into other responsibilities like IT
concerns, it becomes very hard for such a business to achieve its two main agendas. Also, relying
on third party organizations to take care of the organization’s IT infrastructure creates more time
for the organization to devote towards the main aspects affecting it directly. Cloud technology
enables a business to be more flexible compared to when servers are hosted locally (Botta,
Persico & Pescapé, 2016). Lastly, because businesses keep on expanding, to get extra bandwidth
becomes easier when under cloud-based service than when under local hosting where the process
of updating the whole IT infrastructure is needed.
Disaster recovery
Ensuring business control has been a major factor to many businesses and which is
accorded the necessary attention by most of organizations (Botta, Persico & Pescapé, 2016).
Unfortunately, however much an organization tries to be fully in control of its operations there
will always be some incidences that run out of control and which can have resoundingly negative
impacts especially in today’s market trends. For instance, a small downtime in an organization
services may lead to lost productivity, brand reputation and revenue. Cloud-based services in
such scenarios provide fast data recovery for all kinds of emergencies right from natural disasters
like earthquakes to power outages (Wang, Zheng, Lou & Hou, 2015).
(b) Differences between Public Cloud and Private Cloud
Categorically, the differences between private cloud and public cloud can be grouped into
five domains (Krishnan, Bhagwat & Utpat, 2015): Tenancy, exposure to public, data center
location, cloud service management and hardware components. In regard to tenancy, private
Any business strives to achieve its goals and meet all its customer demands. However, if
the finite time the business management has is divided into other responsibilities like IT
concerns, it becomes very hard for such a business to achieve its two main agendas. Also, relying
on third party organizations to take care of the organization’s IT infrastructure creates more time
for the organization to devote towards the main aspects affecting it directly. Cloud technology
enables a business to be more flexible compared to when servers are hosted locally (Botta,
Persico & Pescapé, 2016). Lastly, because businesses keep on expanding, to get extra bandwidth
becomes easier when under cloud-based service than when under local hosting where the process
of updating the whole IT infrastructure is needed.
Disaster recovery
Ensuring business control has been a major factor to many businesses and which is
accorded the necessary attention by most of organizations (Botta, Persico & Pescapé, 2016).
Unfortunately, however much an organization tries to be fully in control of its operations there
will always be some incidences that run out of control and which can have resoundingly negative
impacts especially in today’s market trends. For instance, a small downtime in an organization
services may lead to lost productivity, brand reputation and revenue. Cloud-based services in
such scenarios provide fast data recovery for all kinds of emergencies right from natural disasters
like earthquakes to power outages (Wang, Zheng, Lou & Hou, 2015).
(b) Differences between Public Cloud and Private Cloud
Categorically, the differences between private cloud and public cloud can be grouped into
five domains (Krishnan, Bhagwat & Utpat, 2015): Tenancy, exposure to public, data center
location, cloud service management and hardware components. In regard to tenancy, private
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD COMPUTING 4
cloud operates in a single tenancy because the data in this cloud belongs to a single organization.
On the other hand, public cloud operates as a multi-tenancy because it deals with data from
multiple organizations in a shared environment (Ali, Khan & Vasilakos, 2015).
In terms of exposure to public exposure, the private cloud does not allow exposure
because it’s only the organization itself that can use the cloud services (Goyal, 2014). For, public
cloud; the infrastructure allows exposure of the services to all the organizations which wishes to
use it under shared environment. For private cloud, data center is located within the organization
network while for public cloud it’s located anywhere on the internet where the cloud service
provider is located (Krishnan, Bhagwat & Utpat, 2015).
In regard to cloud service management, under private cloud management of cloud
services is done by the internal team while under public cloud it’s the responsibility of the
service provider to manage and control the cloud service where organization data is stored.
Finally, in regard to hardware components of the two services, in private cloud the organization
provides the components which entail servers and other storage devices while in public cloud
that’s the responsibility of CSP (Rittinghouse & Ransome, 2016).
Question 2
(a) Considerations when Implementing Private Cloud
Although, on premise data centers have problems when it comes to resources,
management skills and monitoring, there are some instances where private cloud is more
preferable than the public cloud. This depends on the client requirements. Here are some of the
cases I would advise a client to go for private cloud services (Cooper, Nedbal & Nadkarni,
2017).
Backup and Recovery needs of the Organization
cloud operates in a single tenancy because the data in this cloud belongs to a single organization.
On the other hand, public cloud operates as a multi-tenancy because it deals with data from
multiple organizations in a shared environment (Ali, Khan & Vasilakos, 2015).
In terms of exposure to public exposure, the private cloud does not allow exposure
because it’s only the organization itself that can use the cloud services (Goyal, 2014). For, public
cloud; the infrastructure allows exposure of the services to all the organizations which wishes to
use it under shared environment. For private cloud, data center is located within the organization
network while for public cloud it’s located anywhere on the internet where the cloud service
provider is located (Krishnan, Bhagwat & Utpat, 2015).
In regard to cloud service management, under private cloud management of cloud
services is done by the internal team while under public cloud it’s the responsibility of the
service provider to manage and control the cloud service where organization data is stored.
Finally, in regard to hardware components of the two services, in private cloud the organization
provides the components which entail servers and other storage devices while in public cloud
that’s the responsibility of CSP (Rittinghouse & Ransome, 2016).
Question 2
(a) Considerations when Implementing Private Cloud
Although, on premise data centers have problems when it comes to resources,
management skills and monitoring, there are some instances where private cloud is more
preferable than the public cloud. This depends on the client requirements. Here are some of the
cases I would advise a client to go for private cloud services (Cooper, Nedbal & Nadkarni,
2017).
Backup and Recovery needs of the Organization
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING 5
If the client would like to have full control of their backup frequencies and recovery, I
would advise the clients to go for this cloud service because in public cloud service they would
get what is supported by the service provider regardless of whether it meets their demands or not
(Krishnan, Bhagwat & Utpat, 2015).
Security aspect
It’s beyond any reasonable doubt that public cloud service has some weaknesses in
regard to organization data privacy and encryption has remained to be a challenge. So, if the
client is handling sensitive data which requires high levels of privacy, I would encourage him to
go for private cloud service which won’t compromise with its requirements in terms of privacy
goals (Krishnan, Bhagwat & Utpat, 2015).
Performance aspect
Although both public and private cloud services have good performance, in public cloud
service the client will be confiscated on the level of performance provided by the service
provider. However, if the client needs to remain in full control of his or her data center
performance like moving certain information to faster disks or pushing something into memory
and increase caching performance whenever a need arises, private cloud is the best (Jiang, Song,
Wang, Gu, Sun & Sha, 2017).).
Flexibility aspect
Beyond the flexibility offered by both public and private cloud services in terms of
servers and storage, private cloud service has an additional flexibility aspect of allowing the
If the client would like to have full control of their backup frequencies and recovery, I
would advise the clients to go for this cloud service because in public cloud service they would
get what is supported by the service provider regardless of whether it meets their demands or not
(Krishnan, Bhagwat & Utpat, 2015).
Security aspect
It’s beyond any reasonable doubt that public cloud service has some weaknesses in
regard to organization data privacy and encryption has remained to be a challenge. So, if the
client is handling sensitive data which requires high levels of privacy, I would encourage him to
go for private cloud service which won’t compromise with its requirements in terms of privacy
goals (Krishnan, Bhagwat & Utpat, 2015).
Performance aspect
Although both public and private cloud services have good performance, in public cloud
service the client will be confiscated on the level of performance provided by the service
provider. However, if the client needs to remain in full control of his or her data center
performance like moving certain information to faster disks or pushing something into memory
and increase caching performance whenever a need arises, private cloud is the best (Jiang, Song,
Wang, Gu, Sun & Sha, 2017).).
Flexibility aspect
Beyond the flexibility offered by both public and private cloud services in terms of
servers and storage, private cloud service has an additional flexibility aspect of allowing the

CLOUD COMPUTING 6
client to do what he or she wants at any instance. For such a case, the client should consider
private cloud.
(b) Private Cloud Monitoring and Operation by System Centre
Mainly, private cloud monitoring and operation solution relies on System Centers as the
virtualization engine platforms that enable pooling and sharing of computing resources like
network, storage and memory. Also System Centers support private cloud security and isolation
of hosted services (Krishnan, Bhagwat & Utpat, 2015). The components of System Center which
include System Center Virtual Machine Manager, System Center Configuration Manager,
System Center Operations Manager, System Center Data Protection Manager, System Center
App Controller, System Center Service Manager and System Center Orchestrator work together
to provide automation, operation, and management of private cloud, as well as enabling the
elasticity, self-service, and metering attributes.
Question 3
(a) (I) Security issues with Cloud Computing
Data Breaches
Considering the fact that data breaches have been existing for quite a long time while
cloud computing is a new technology which has not been scrutinized fully by the IT security
experts, this clearly shows that security in cloud computing must be low (Krishnan, Bhagwat &
Utpat, 2015). A research conducted by Ponemon Institute indicated that over 50% of the IT
security professionals were not adequately conversant with the security aspects of cloud
client to do what he or she wants at any instance. For such a case, the client should consider
private cloud.
(b) Private Cloud Monitoring and Operation by System Centre
Mainly, private cloud monitoring and operation solution relies on System Centers as the
virtualization engine platforms that enable pooling and sharing of computing resources like
network, storage and memory. Also System Centers support private cloud security and isolation
of hosted services (Krishnan, Bhagwat & Utpat, 2015). The components of System Center which
include System Center Virtual Machine Manager, System Center Configuration Manager,
System Center Operations Manager, System Center Data Protection Manager, System Center
App Controller, System Center Service Manager and System Center Orchestrator work together
to provide automation, operation, and management of private cloud, as well as enabling the
elasticity, self-service, and metering attributes.
Question 3
(a) (I) Security issues with Cloud Computing
Data Breaches
Considering the fact that data breaches have been existing for quite a long time while
cloud computing is a new technology which has not been scrutinized fully by the IT security
experts, this clearly shows that security in cloud computing must be low (Krishnan, Bhagwat &
Utpat, 2015). A research conducted by Ponemon Institute indicated that over 50% of the IT
security professionals were not adequately conversant with the security aspects of cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD COMPUTING 7
computing. For that matter, they believed that security in cloud computing infrastructure was
highly exposed to data breaches.
Malware Injection
These are scripts and codes which are embedded into the cloud services to act as “valid
instances” and run as normal SaaS to the cloud servers. Once these injections are executed and
cloud begins to operate in tandem with them, attackers can easily eavesdrop hence compromising
the integrity of data inside the servers especially if it’s sensitive data, they can also steal the data
(Krishnan, Bhagwat & Utpat, 2015).
Insecure APIs
For users to be able to customize their cloud experience, cloud technology uses
Application Programming Interfaces (API). However, these APIs have turned to be a threat in
cloud security because they can also give attackers the chance to customize features of the cloud
services to fit target goals by authenticating, provide access, and effecting encryption just like the
real users (Krishnan, Bhagwat & Utpat, 2015).
Denial of Service Attacks
Rather than other cyberattacks, DoS attacks usually make organization servers at the
cloud environment unavailable with an aim of legitimizing users. In other instances , however,
DoS attacks are used as smokescreens for other malicious activities like taking down the security
appliances like web application firewalls.
(ii) Security Controls in Cloud Security Architecture
computing. For that matter, they believed that security in cloud computing infrastructure was
highly exposed to data breaches.
Malware Injection
These are scripts and codes which are embedded into the cloud services to act as “valid
instances” and run as normal SaaS to the cloud servers. Once these injections are executed and
cloud begins to operate in tandem with them, attackers can easily eavesdrop hence compromising
the integrity of data inside the servers especially if it’s sensitive data, they can also steal the data
(Krishnan, Bhagwat & Utpat, 2015).
Insecure APIs
For users to be able to customize their cloud experience, cloud technology uses
Application Programming Interfaces (API). However, these APIs have turned to be a threat in
cloud security because they can also give attackers the chance to customize features of the cloud
services to fit target goals by authenticating, provide access, and effecting encryption just like the
real users (Krishnan, Bhagwat & Utpat, 2015).
Denial of Service Attacks
Rather than other cyberattacks, DoS attacks usually make organization servers at the
cloud environment unavailable with an aim of legitimizing users. In other instances , however,
DoS attacks are used as smokescreens for other malicious activities like taking down the security
appliances like web application firewalls.
(ii) Security Controls in Cloud Security Architecture
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD COMPUTING 8
Setting up strong cloud data security policies
Strong policies play a very crucial role in preventing organization data breaches and
maintaining security within the cloud computing environment. Policies help in preventing data
breaches originating from the inside of the organization and which has been ranked as the top
source of the current data breaches (Julian et al, 2017).
Encryptions to sensitive data
Sensitive data and which is more prone to compromises should always be kept in
encrypted manner whether being retrieved of under storage. That way, even under successful
attacks the data is secure because it’s meaningless to the attackers who may not have decryption
keys. This control measure backed up by the strong security policies ensures high security of
data in cloud computing infrastructures (Rittinghouse & Ransome, 2016).
DLP and Activity Monitoring
Data leaks in organizations can also be caused by employees, and whether they are
whether inadvertently or maliciously pose security concerns to the organization. So,
organizations need to back up their security policies and the encryption strategies with Data Loss
Prevention (DLP) and activity monitoring solutions which helps in detecting any attempts made
to access or transmit sensitive data from the cloud servers (Rittinghouse & Ransome, 2016).
(b) Selection Criteria Assessment for Private and Public Cloud Security Aspect
Setting up strong cloud data security policies
Strong policies play a very crucial role in preventing organization data breaches and
maintaining security within the cloud computing environment. Policies help in preventing data
breaches originating from the inside of the organization and which has been ranked as the top
source of the current data breaches (Julian et al, 2017).
Encryptions to sensitive data
Sensitive data and which is more prone to compromises should always be kept in
encrypted manner whether being retrieved of under storage. That way, even under successful
attacks the data is secure because it’s meaningless to the attackers who may not have decryption
keys. This control measure backed up by the strong security policies ensures high security of
data in cloud computing infrastructures (Rittinghouse & Ransome, 2016).
DLP and Activity Monitoring
Data leaks in organizations can also be caused by employees, and whether they are
whether inadvertently or maliciously pose security concerns to the organization. So,
organizations need to back up their security policies and the encryption strategies with Data Loss
Prevention (DLP) and activity monitoring solutions which helps in detecting any attempts made
to access or transmit sensitive data from the cloud servers (Rittinghouse & Ransome, 2016).
(b) Selection Criteria Assessment for Private and Public Cloud Security Aspect

CLOUD COMPUTING 9
The main selection criteria of private and public cloud services in regard to security are
the sensitivity of data being handled and the level of privacy required. Looking at this criterion
however, there are a lot of concerns. First, if data privacy can be compromised in the cloud
computing environment implies that security of data from different angles can also be
compromised. For that matter, data security can either be 100% or 0% and therefore any
organization that worries of privacy in any of these two should also be worried of insecurity from
the rest of data security aspects (Rittinghouse & Ransome, 2016).
Question 4: Verifying the Health Status of System Center Components
Operations Manager
The main function of this component is to keep eye on cloud servers, operating systems,
applications and networks. So, if tested through System Center Configuration Manager (SCCM)
and cannot return the results based on the status of the three, it is deemed to have a fault.
However, if it can return the status its health status is approved (Kampas, Tarkowski, Portell &
Bhatti, 2016).
Virtual Machine Manager
This component manages fabric infrastructure for virtualization right from the hosts,
networks to clusters. When tested through System Center Configuration Manager (SCCM) and
accessibility of virtual machines does not go through, it is deemed to have a fault. However, if it
can be accessed its said to be healthy.
The main selection criteria of private and public cloud services in regard to security are
the sensitivity of data being handled and the level of privacy required. Looking at this criterion
however, there are a lot of concerns. First, if data privacy can be compromised in the cloud
computing environment implies that security of data from different angles can also be
compromised. For that matter, data security can either be 100% or 0% and therefore any
organization that worries of privacy in any of these two should also be worried of insecurity from
the rest of data security aspects (Rittinghouse & Ransome, 2016).
Question 4: Verifying the Health Status of System Center Components
Operations Manager
The main function of this component is to keep eye on cloud servers, operating systems,
applications and networks. So, if tested through System Center Configuration Manager (SCCM)
and cannot return the results based on the status of the three, it is deemed to have a fault.
However, if it can return the status its health status is approved (Kampas, Tarkowski, Portell &
Bhatti, 2016).
Virtual Machine Manager
This component manages fabric infrastructure for virtualization right from the hosts,
networks to clusters. When tested through System Center Configuration Manager (SCCM) and
accessibility of virtual machines does not go through, it is deemed to have a fault. However, if it
can be accessed its said to be healthy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD COMPUTING 10
Service Manager
Service manager acts as a help desk system that helps in tracking incidents, changing
requests and configuring management at the configuration management database. If it can’t
achieve these functionalities when tested by a System Center Configuration Manager (SCCM)
then its deemed fault otherwise its healthy.
Orchestrator
This component links and integrates all the other components of System Center through
automation. So, if the components of system center are not integrated at any instance, it is
deemed as fault, otherwise it is seen as healthy.
Application Controller
This component allows the end users to see Virtual Machine Manager Private clouds as
well as the services deployed in them. If the end users cannot see the Virtual Machine Manager
Private Cloud, the component is declared faulty otherwise it is considered healthy.
Question 5: Service Models in Cloud Computing
Service Manager
Service manager acts as a help desk system that helps in tracking incidents, changing
requests and configuring management at the configuration management database. If it can’t
achieve these functionalities when tested by a System Center Configuration Manager (SCCM)
then its deemed fault otherwise its healthy.
Orchestrator
This component links and integrates all the other components of System Center through
automation. So, if the components of system center are not integrated at any instance, it is
deemed as fault, otherwise it is seen as healthy.
Application Controller
This component allows the end users to see Virtual Machine Manager Private clouds as
well as the services deployed in them. If the end users cannot see the Virtual Machine Manager
Private Cloud, the component is declared faulty otherwise it is considered healthy.
Question 5: Service Models in Cloud Computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CLOUD COMPUTING 11
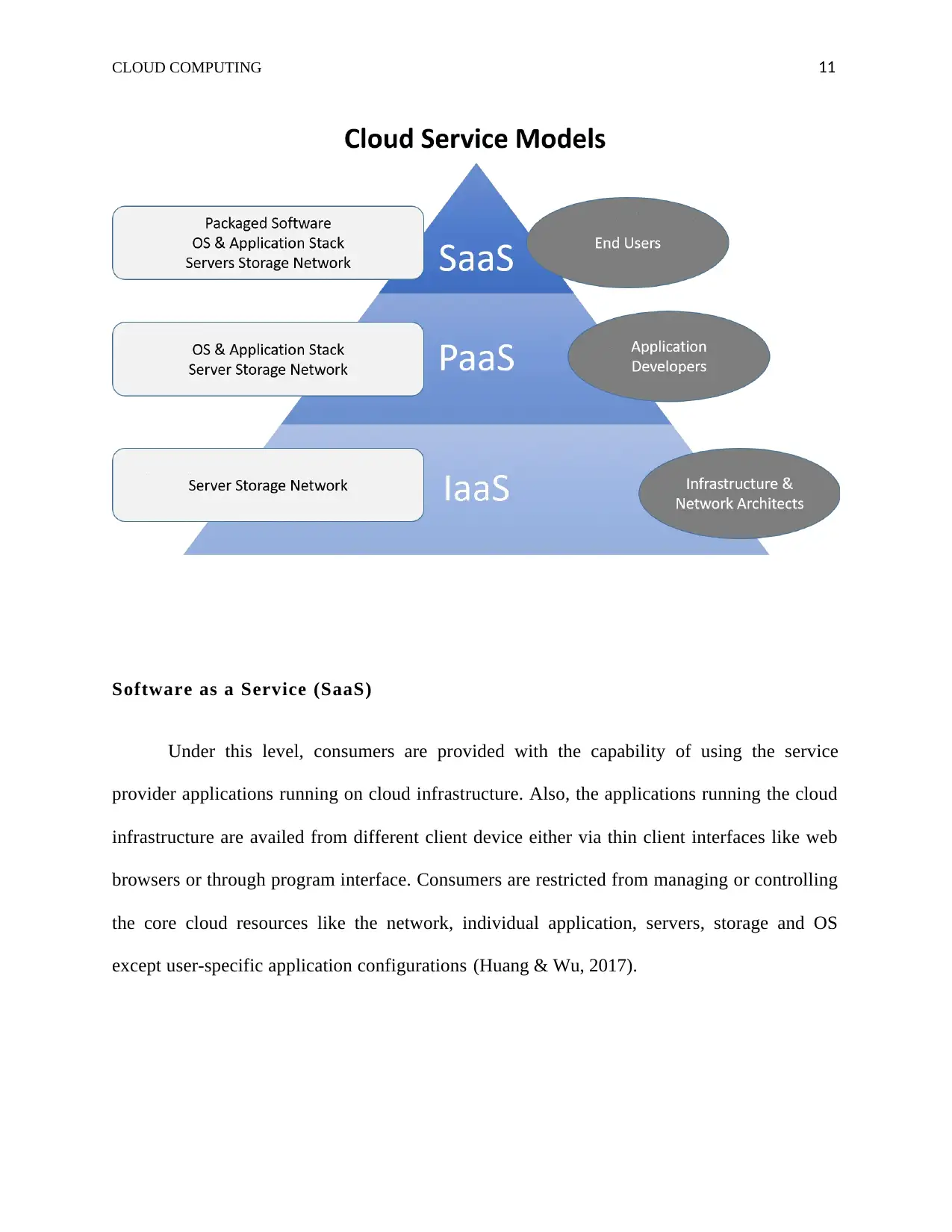
Software as a Service (SaaS)
Under this level, consumers are provided with the capability of using the service
provider applications running on cloud infrastructure. Also, the applications running the cloud
infrastructure are availed from different client device either via thin client interfaces like web
browsers or through program interface. Consumers are restricted from managing or controlling
the core cloud resources like the network, individual application, servers, storage and OS
except user-specific application configurations (Huang & Wu, 2017).
Software as a Service (SaaS)
Under this level, consumers are provided with the capability of using the service
provider applications running on cloud infrastructure. Also, the applications running the cloud
infrastructure are availed from different client device either via thin client interfaces like web
browsers or through program interface. Consumers are restricted from managing or controlling
the core cloud resources like the network, individual application, servers, storage and OS
except user-specific application configurations (Huang & Wu, 2017).

CLOUD COMPUTING 12
Platform as a Service (PaaS)
Under this level, consumers are provided with the ability to deploy client applications
onto cloud platform by the use of programming languages, libraries and services. At this level,
consumers are not privileged to manage and control any underlying cloud resources like
servers, networks, storage and operating system. They are however accorded control over
installed applications and configuration settings in the applications-hosting environments
(Manuel, 2015).
Infrastructure as a Service (IaaS)
At this level, consumers are provided with the capability of provision processing,
managing fundamental computing resources like storage and networks and can install and run
subjective softwares like operating system and other applications. Consumers are not
privileged to manage and control the primary cloud infrastructure but have control over
deployed applications, operating system and storage (Jula, Sundararajan & Othman, 2014).
(b) Key Features of VMM and their Role in Private Cloud
Windows PowerShell
This feature enables the VMM to have a great automation and control as well as being
fully scriptable. The role of this tool in the private cloud infrastructure is to enable IT
administrators to execute scripted services remotely against virtual machines hence avoiding
labor-intensive processes performed manually in graphic user interfaces (Levchenko & Cardoso,
2018).
Fast and Reliable Physical to Virtual (P2V) Conversions
Platform as a Service (PaaS)
Under this level, consumers are provided with the ability to deploy client applications
onto cloud platform by the use of programming languages, libraries and services. At this level,
consumers are not privileged to manage and control any underlying cloud resources like
servers, networks, storage and operating system. They are however accorded control over
installed applications and configuration settings in the applications-hosting environments
(Manuel, 2015).
Infrastructure as a Service (IaaS)
At this level, consumers are provided with the capability of provision processing,
managing fundamental computing resources like storage and networks and can install and run
subjective softwares like operating system and other applications. Consumers are not
privileged to manage and control the primary cloud infrastructure but have control over
deployed applications, operating system and storage (Jula, Sundararajan & Othman, 2014).
(b) Key Features of VMM and their Role in Private Cloud
Windows PowerShell
This feature enables the VMM to have a great automation and control as well as being
fully scriptable. The role of this tool in the private cloud infrastructure is to enable IT
administrators to execute scripted services remotely against virtual machines hence avoiding
labor-intensive processes performed manually in graphic user interfaces (Levchenko & Cardoso,
2018).
Fast and Reliable Physical to Virtual (P2V) Conversions
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




