Cloud Computing: Technology and its Mechanisms Report
VerifiedAdded on 2023/01/13
|19
|916
|84
Report
AI Summary
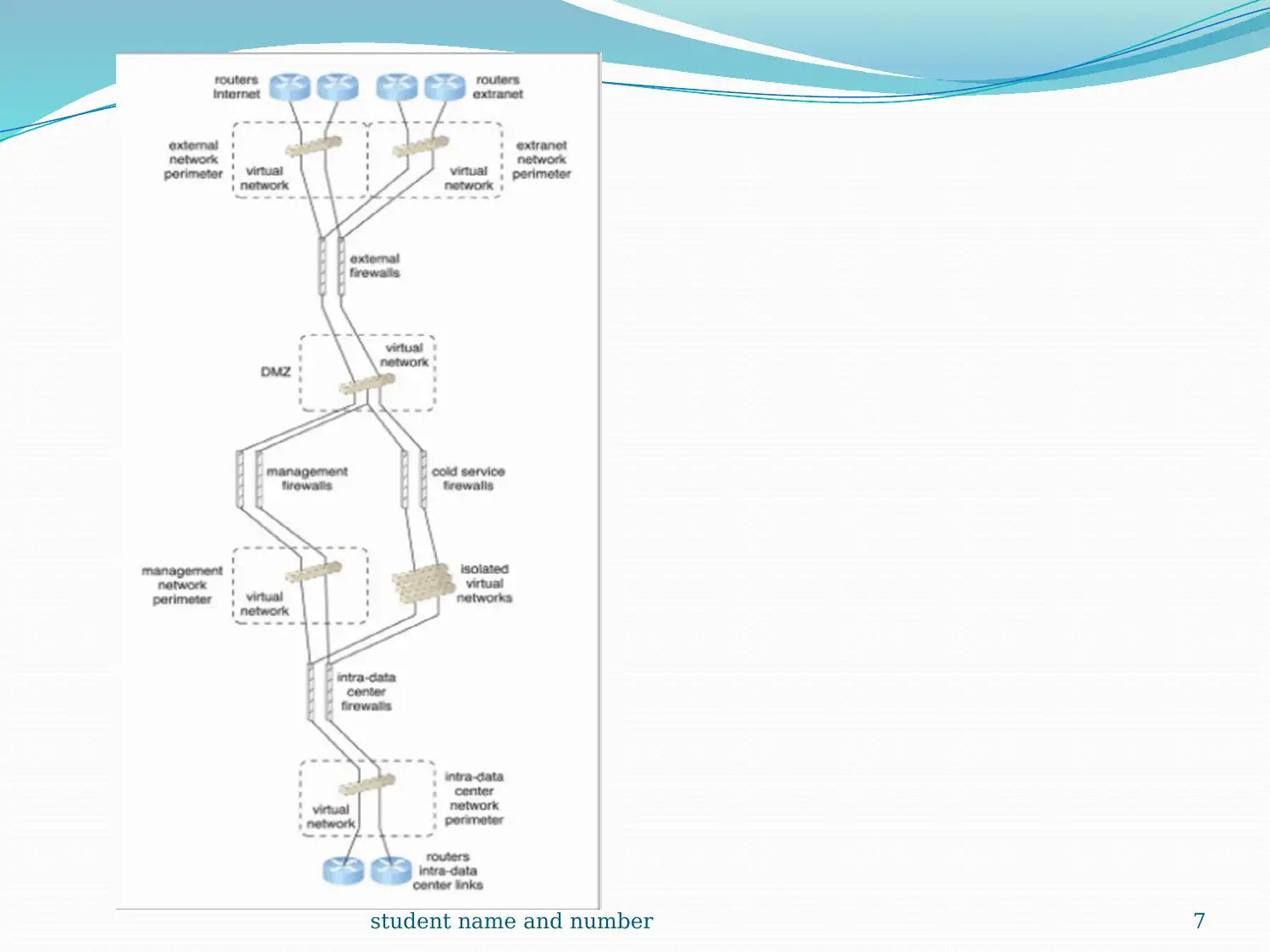
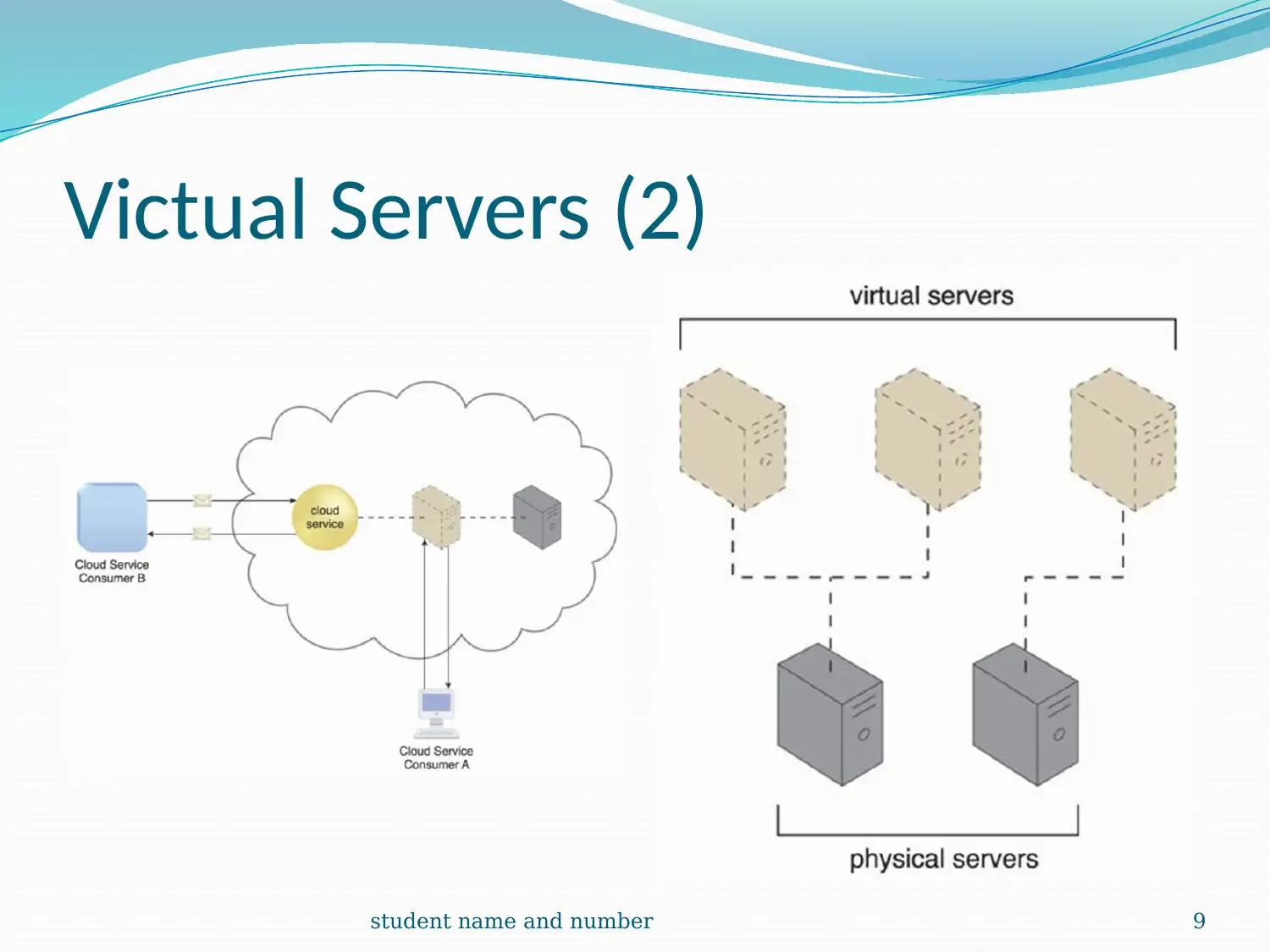
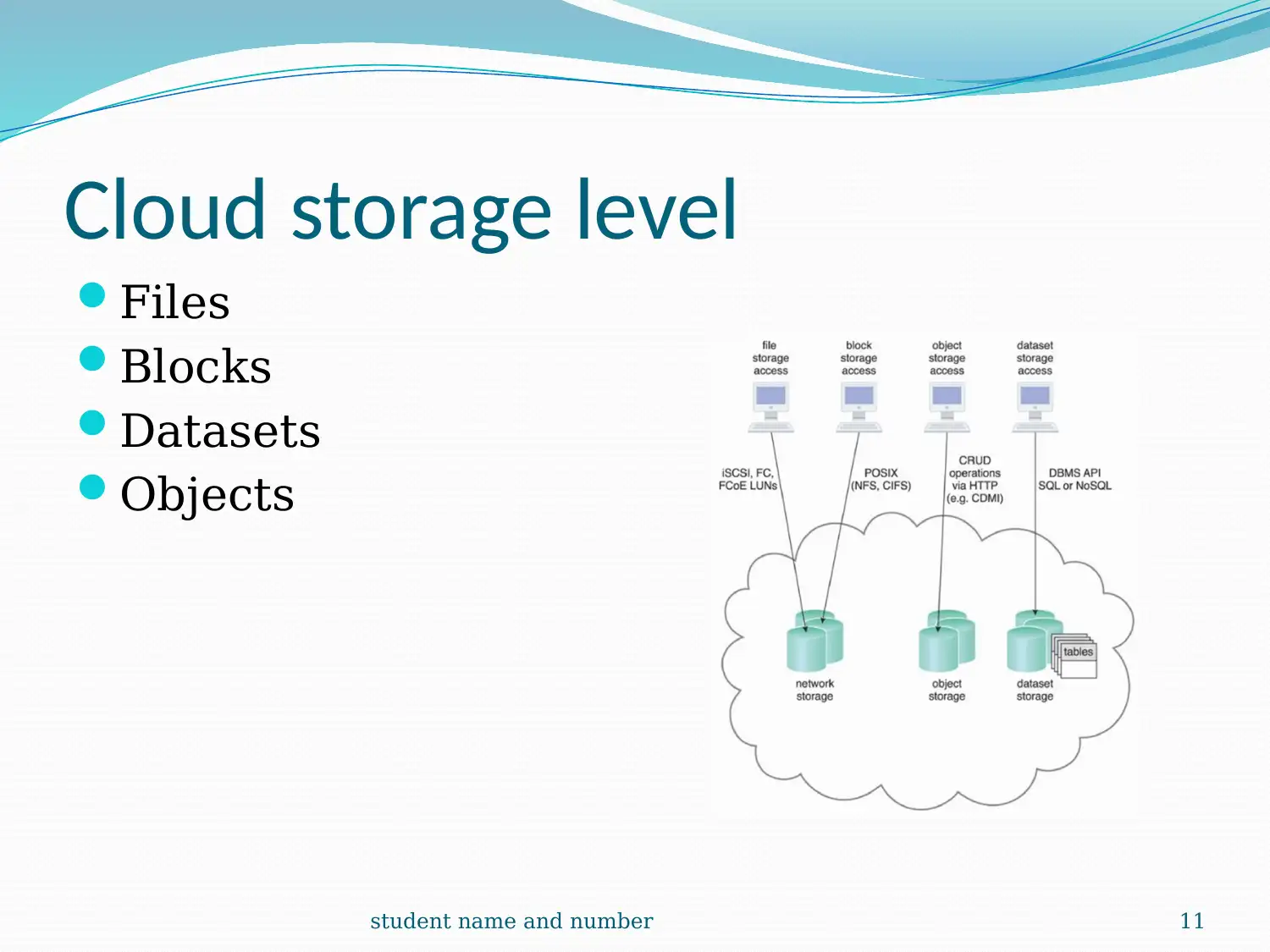
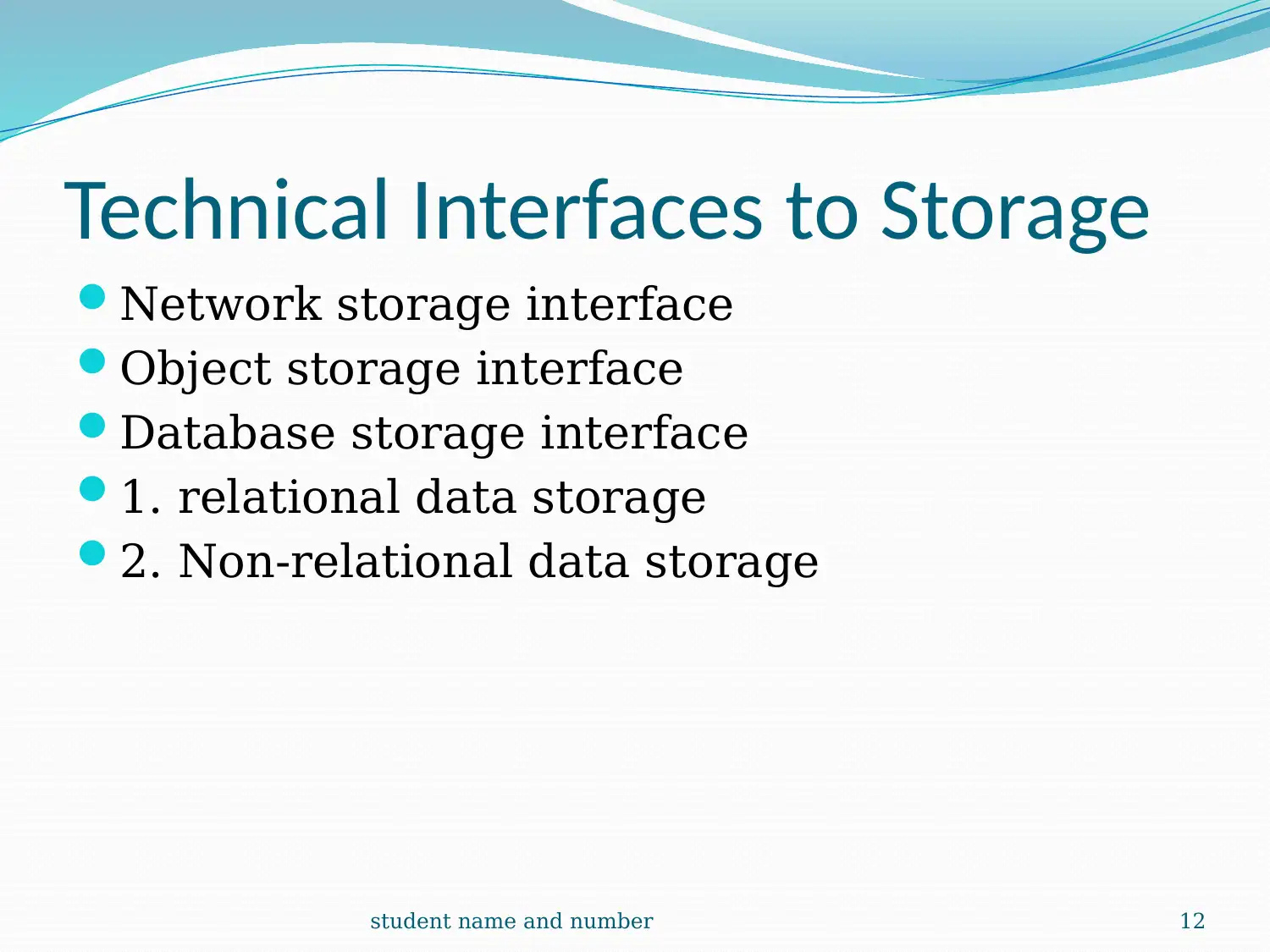
This report provides a comprehensive overview of cloud computing, detailing its infrastructure, logical network perimeters, and virtual servers. It explores cloud storage devices, levels, and technical interfaces, along with cloud usage monitor mechanisms, including monitoring, resource, and polling agents. The report also covers resource replication and ready-made environments, such as Platform-as-a-Service (PaaS). A case study of DTGOV organization highlights the practical application of these concepts, including the use of routers, DMZ zones, and firewalls. The report emphasizes the virtualization of cloud storage devices and their pay-per-use mechanisms. It concludes with references to relevant research papers and resources.
1 out of 19









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)