Cloud Computing Report: Infrastructure, Services, and Usage Mechanisms
VerifiedAdded on 2023/04/20
|18
|945
|412
Report
AI Summary
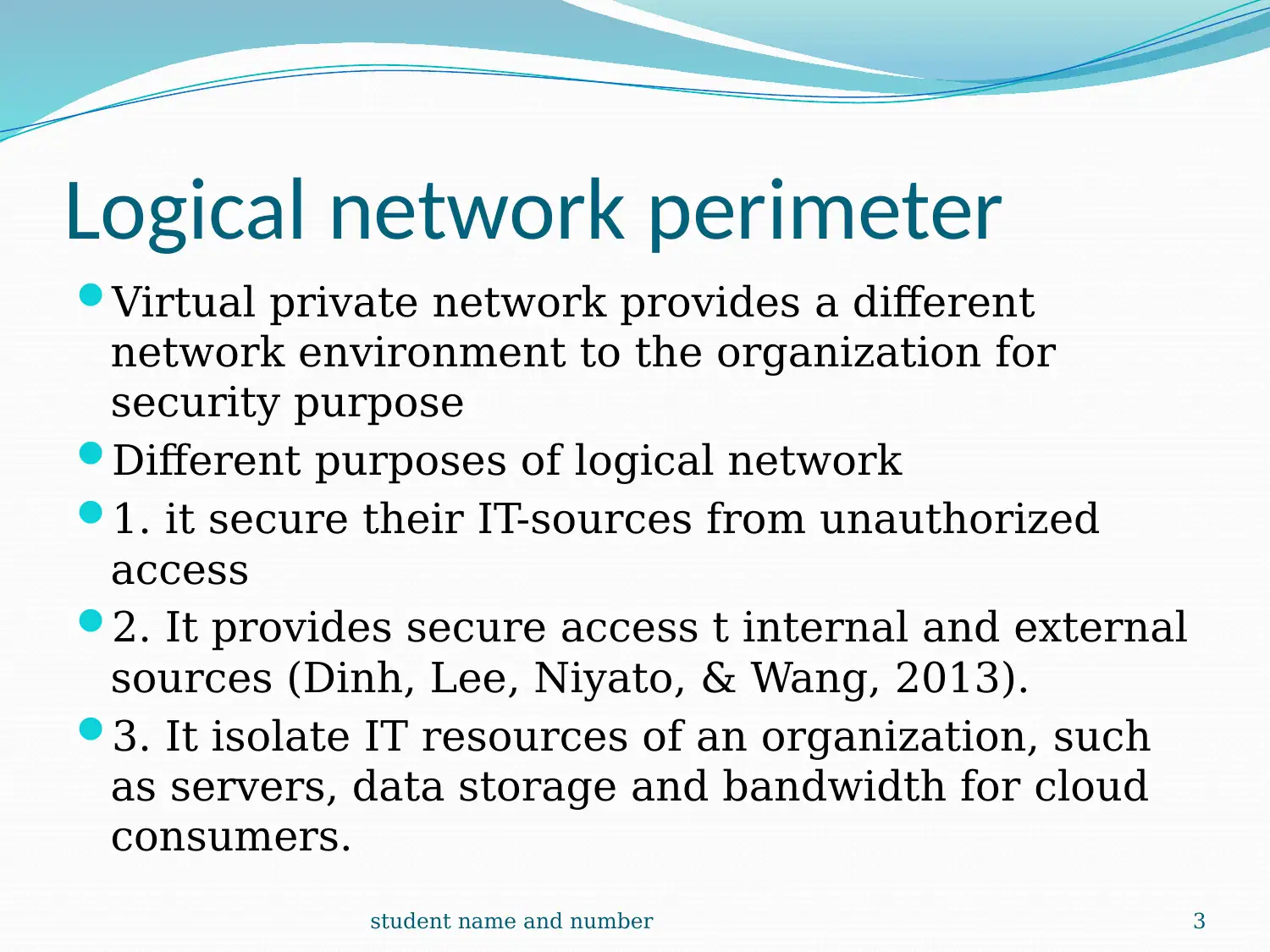
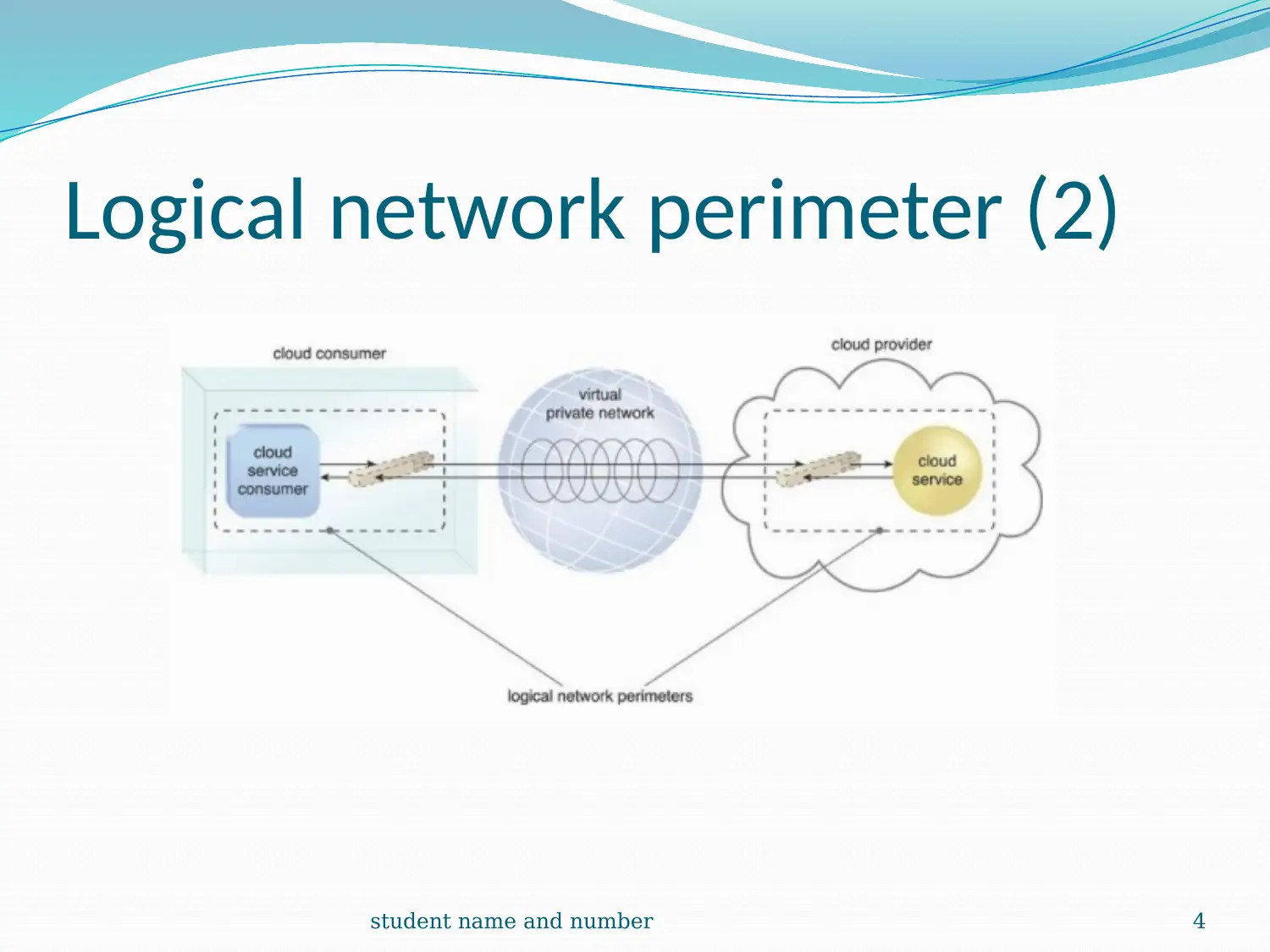
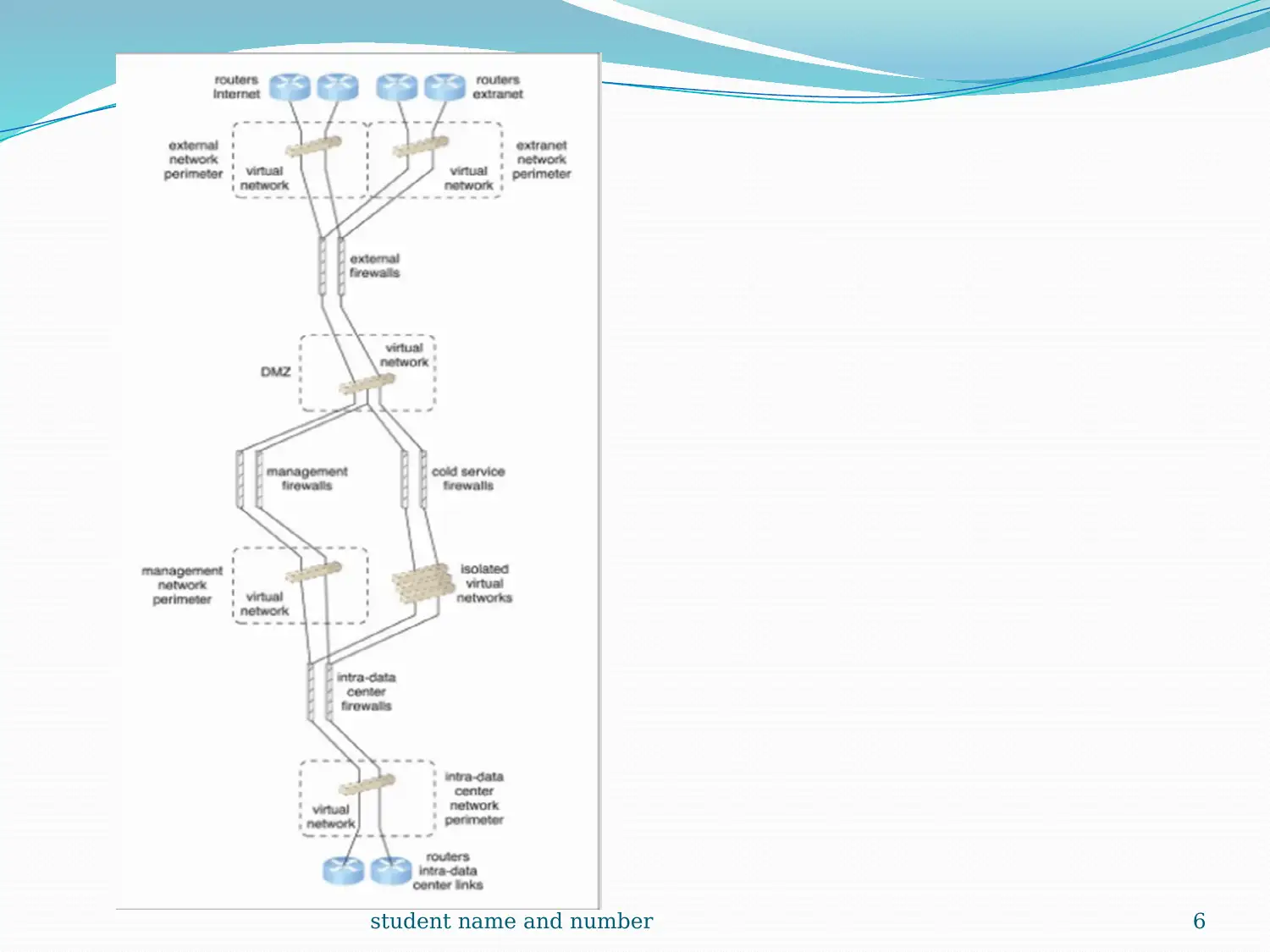
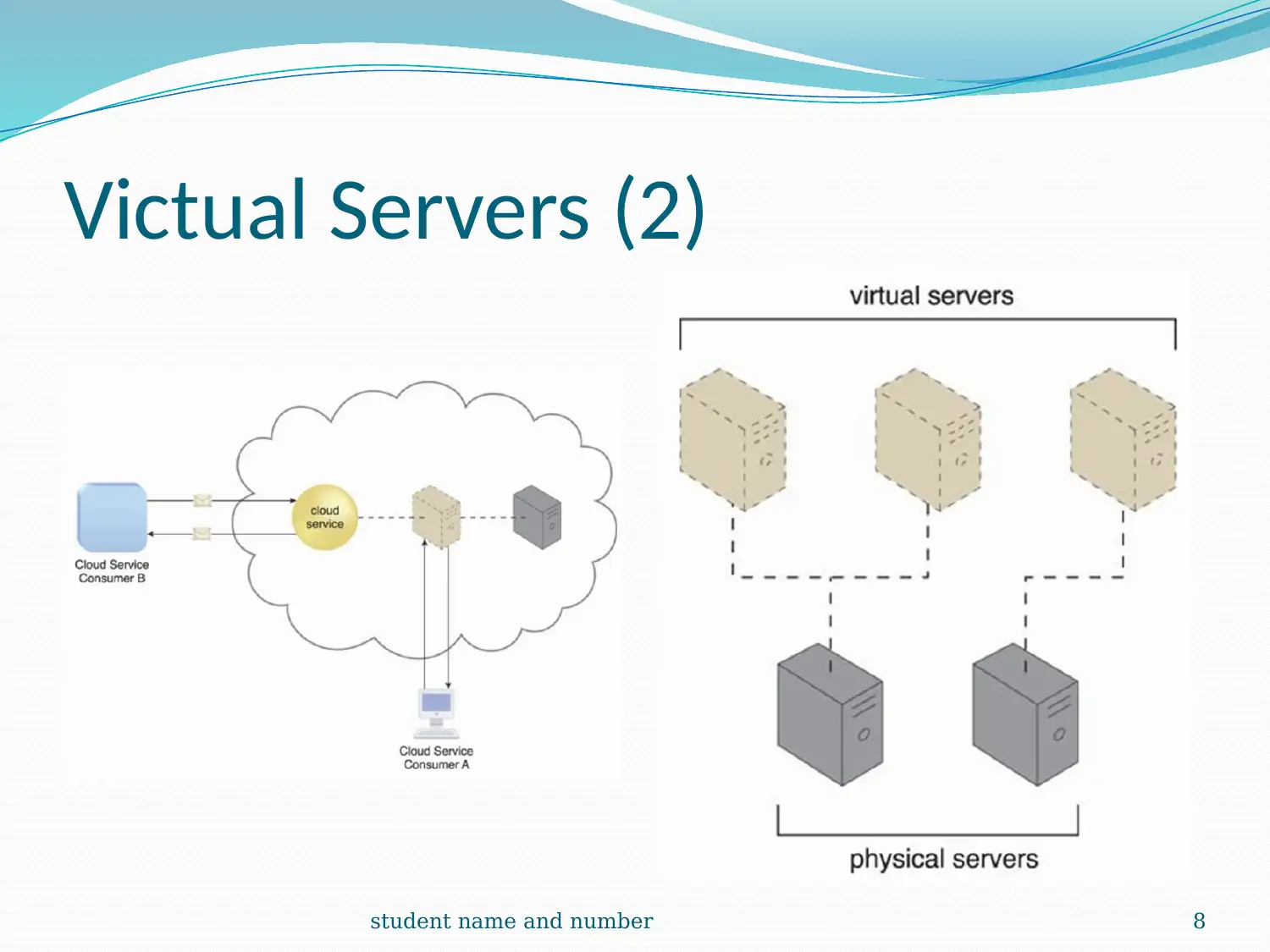
This report provides a comprehensive introduction to cloud computing, exploring its foundational aspects and various service models. It begins by defining cloud infrastructure as a complete solution for organizational operations, detailing services like data storage and software development kits. The report then delves into the logical network perimeter, emphasizing its role in securing IT resources and providing secure access. A case study on DTGOV illustrates practical applications, highlighting the use of routers, DMZ, and firewalls. The discussion extends to virtual servers and cloud storage devices, explaining their virtualization capabilities and pay-per-use mechanisms. Technical interfaces, including network, object, and database storage interfaces, are also examined. Furthermore, the report covers cloud usage-monitor mechanisms, discussing monitoring and resource agents, along with resource replication and the Platform-as-a-Service (PaaS) model. The content is supported by multiple references to enhance understanding.
1 out of 18









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)