NTC Week 4: Process Map for Cloud Computing Implementation
VerifiedAdded on 2023/06/12
|7
|980
|364
Practical Assignment
AI Summary
This assignment presents a detailed process map for cloud computing implementation, specifically tailored for a large credit card processing company. The map highlights key components such as security (biometric modality), virtualization (servers, networks, storage), and databases (Amazon RDS, Google Cloud SQL, etc.). It also identifies responsible parties, including vendors (Amazon, Google, etc.), in-house IT, outsourced IT, security teams, and hybrid groups. The process map illustrates the sequential steps involved in cloud deployment, from initial approval and virtualization to database selection and security implementation, emphasizing the importance of data security and infrastructure reliability. The document concludes that successful cloud computing deployment relies on the effective management of databases, storage, and virtualization, along with the collaborative efforts of responsible parties to maintain data integrity and security.

Running head: PROCESS MAP FOR CLOUD COMPUTING
Process Map for Cloud Computing
Name of the Student
Name of the University
Authors note
Process Map for Cloud Computing
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PROCESS MAP FOR CLOUD COMPUTING
Process map for cloud computing
A 3-page process map using Lucid Chart has been designed that shows components of
cloud computing and responsibility for implementing cloud. The process map includes
following points.
Cloud computing components
1. Security- Biometric modality
2. Virtualization- Servers, networks and storages
3. Databases- Amazon relational database service, Google cloud SQL, Oracle Database
cloud service, Microsoft azure SQL database, Amazon DynamoDB, Amazon
SimpleDB, Azure DocumentDB and Google Cloud Datastore
Responsible parties
1. Vendors- Amazon, Google, Oracle and Microsoft
2. In-house IT- employees and management
3. Outsourced IT- Virtualization manager
4. Security team- Cyber security team
5. Hybrid group- Users/customers
The process map for cloud computing is designed to understand the implementation of
cloud computing in large company dealing with credit card processing. The cloud computing
is a growing technology consisting of individual technologies integrated together for
deployment. The cloud computing has found major place in every industries and thus
industries are ready to utilize the potential of this technology (Almorsy, Grundy & Müller,
2016). The cloud computing technology provides improved security and infrastructure to
data. The credit card processing company wants to move their data to cloud computing that
provides virtualization. The data are required to be secure as because all the data are sensitive
data of customers and they will be affected badly due to data breach. The information of the
PROCESS MAP FOR CLOUD COMPUTING
Process map for cloud computing
A 3-page process map using Lucid Chart has been designed that shows components of
cloud computing and responsibility for implementing cloud. The process map includes
following points.
Cloud computing components
1. Security- Biometric modality
2. Virtualization- Servers, networks and storages
3. Databases- Amazon relational database service, Google cloud SQL, Oracle Database
cloud service, Microsoft azure SQL database, Amazon DynamoDB, Amazon
SimpleDB, Azure DocumentDB and Google Cloud Datastore
Responsible parties
1. Vendors- Amazon, Google, Oracle and Microsoft
2. In-house IT- employees and management
3. Outsourced IT- Virtualization manager
4. Security team- Cyber security team
5. Hybrid group- Users/customers
The process map for cloud computing is designed to understand the implementation of
cloud computing in large company dealing with credit card processing. The cloud computing
is a growing technology consisting of individual technologies integrated together for
deployment. The cloud computing has found major place in every industries and thus
industries are ready to utilize the potential of this technology (Almorsy, Grundy & Müller,
2016). The cloud computing technology provides improved security and infrastructure to
data. The credit card processing company wants to move their data to cloud computing that
provides virtualization. The data are required to be secure as because all the data are sensitive
data of customers and they will be affected badly due to data breach. The information of the

2
PROCESS MAP FOR CLOUD COMPUTING
users such as credit card PIN number, account number, CVV, transactions list and date of
expiry and other sensitive information. The virtualization is necessary to prevent any physical
infrastructure that will take more space and not very reliable (Wei et al., 2014). The
virtualization process consists of virtualization manager that allows servers, networks and
storages to provide data storage that eventually boosts agility and efficiency for all business
sizes. The virtualization process is then secured with database storage to store data that are
confidential.
The database providers are Amazon web services that provides both NoSQL and
relational databases. There are other vendors also that provide database and they are
characterized as SQL and NoSQL model. The SQL model are Amazon relational database
service, Google cloud SQL, Oracle Database cloud service and Microsoft Azure SQL
database. The NoSQL model are Amazon DynamoDB, Amazon SimpleDB, Azure
DocumentDB and Google Cloud Datastore. The database storage is then provided with
security to improve its storage and usage.
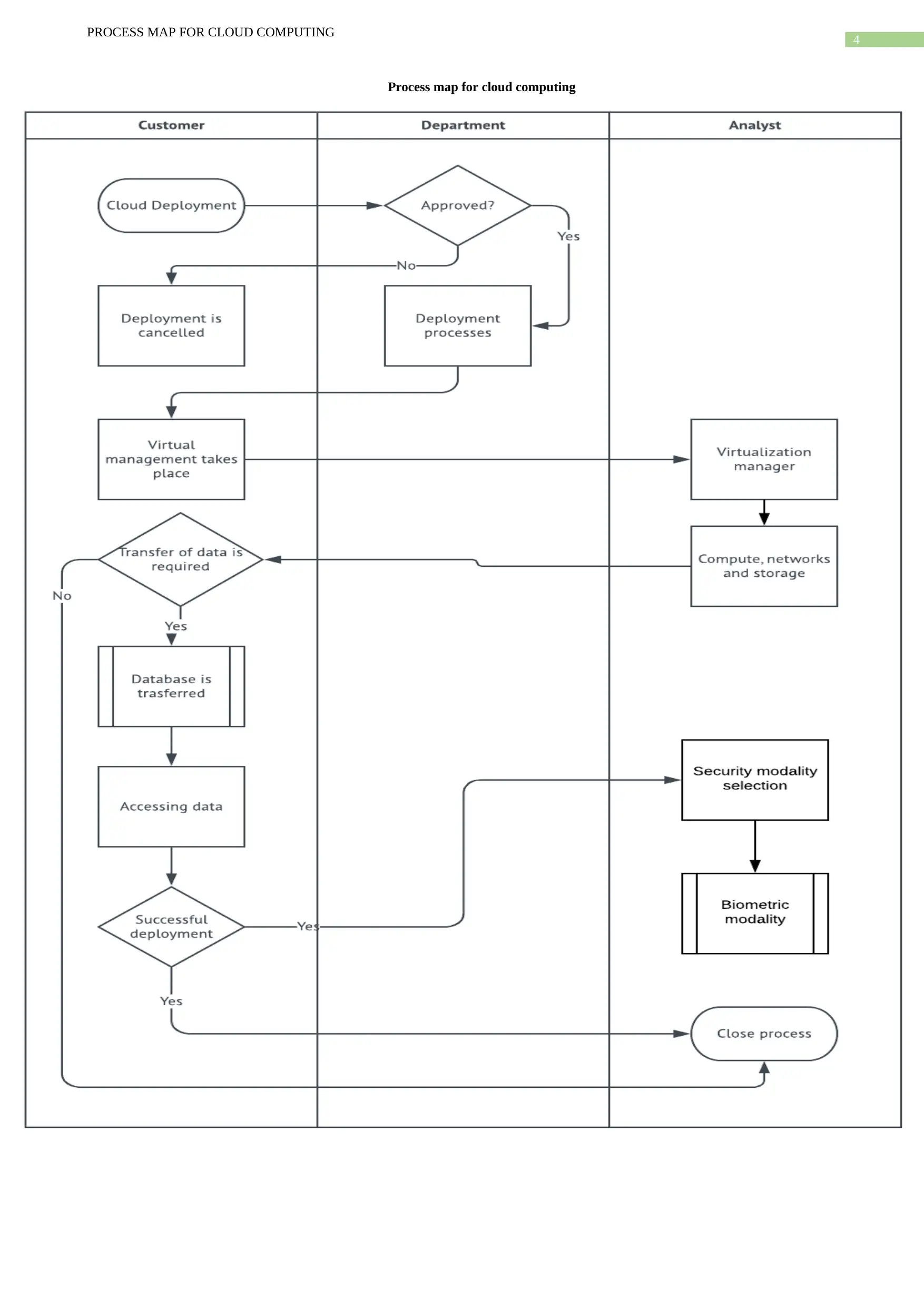
The process map shows that the deployment of Cloud computing is approved by the
department consisting of responsible parties. The responsible parties are vendors, in-house
IT, security team, outsourced IT and hybrid group. The deployment when approved it
processes further for virtualization where virtual management takes place. Here virtual
manager helps to compute, network and store data that are then transferred to database. This
data if transferred then further processing takes place otherwise closure of process takes
place. The database provided from appropriate vendors are then analyzed to select the
appropriate vendor. The database is the successfully deployed that is further checked for
security purposes. The security modality selection is done where biometric modality is
selected as it is an important process in cloud computing deployment where it helps to
PROCESS MAP FOR CLOUD COMPUTING
users such as credit card PIN number, account number, CVV, transactions list and date of
expiry and other sensitive information. The virtualization is necessary to prevent any physical
infrastructure that will take more space and not very reliable (Wei et al., 2014). The
virtualization process consists of virtualization manager that allows servers, networks and
storages to provide data storage that eventually boosts agility and efficiency for all business
sizes. The virtualization process is then secured with database storage to store data that are
confidential.
The database providers are Amazon web services that provides both NoSQL and
relational databases. There are other vendors also that provide database and they are
characterized as SQL and NoSQL model. The SQL model are Amazon relational database
service, Google cloud SQL, Oracle Database cloud service and Microsoft Azure SQL
database. The NoSQL model are Amazon DynamoDB, Amazon SimpleDB, Azure
DocumentDB and Google Cloud Datastore. The database storage is then provided with
security to improve its storage and usage.
The process map shows that the deployment of Cloud computing is approved by the
department consisting of responsible parties. The responsible parties are vendors, in-house
IT, security team, outsourced IT and hybrid group. The deployment when approved it
processes further for virtualization where virtual management takes place. Here virtual
manager helps to compute, network and store data that are then transferred to database. This
data if transferred then further processing takes place otherwise closure of process takes
place. The database provided from appropriate vendors are then analyzed to select the
appropriate vendor. The database is the successfully deployed that is further checked for
security purposes. The security modality selection is done where biometric modality is
selected as it is an important process in cloud computing deployment where it helps to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
PROCESS MAP FOR CLOUD COMPUTING
provide security to the database storage and infrastructure. The security modality selection is
done to improve the security of cloud computing.
Thus the process map for cloud computing helps to understand the deployment process of
cloud computing for large credit card processing company. The above paragraphs shows the
brief description of the process map that helps to understand the functions of components of
cloud computing. The process map helps to conclude that database, storage and virtualization
are important aspect for cloud computing deployment and implementation. These three
aspects are used for complete implementation of cloud computing in any company to provide
improved security to important and sensitive data. The parties that are responsible for cloud
computing deployment and implementation are also the most important aspect. They help to
conduct and improve the implementation of cloud computing in a systematic way. This helps
to keep integrity of cloud computing components within the organization. The parties can be
anyone from customers who are the end users to vendors and employees. The parties are
directly or indirectly connected to the organization to deploy cloud computing. Therefore,
process map is an important illustration for cloud computing development in the company
that describes the processes related to the deployment in a sequential way. The cloud
computing is the future of digital world and its deployment requires experienced expertise to
manage the process involved. The deployment of cloud is complex and it should be
maintained properly.
PROCESS MAP FOR CLOUD COMPUTING
provide security to the database storage and infrastructure. The security modality selection is
done to improve the security of cloud computing.
Thus the process map for cloud computing helps to understand the deployment process of
cloud computing for large credit card processing company. The above paragraphs shows the
brief description of the process map that helps to understand the functions of components of
cloud computing. The process map helps to conclude that database, storage and virtualization
are important aspect for cloud computing deployment and implementation. These three
aspects are used for complete implementation of cloud computing in any company to provide
improved security to important and sensitive data. The parties that are responsible for cloud
computing deployment and implementation are also the most important aspect. They help to
conduct and improve the implementation of cloud computing in a systematic way. This helps
to keep integrity of cloud computing components within the organization. The parties can be
anyone from customers who are the end users to vendors and employees. The parties are
directly or indirectly connected to the organization to deploy cloud computing. Therefore,
process map is an important illustration for cloud computing development in the company
that describes the processes related to the deployment in a sequential way. The cloud
computing is the future of digital world and its deployment requires experienced expertise to
manage the process involved. The deployment of cloud is complex and it should be
maintained properly.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
PROCESS MAP FOR CLOUD COMPUTING
Process map for cloud computing
PROCESS MAP FOR CLOUD COMPUTING
Process map for cloud computing

5
PROCESS MAP FOR CLOUD COMPUTING
PROCESS MAP FOR CLOUD COMPUTING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PROCESS MAP FOR CLOUD COMPUTING
References
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security
and privacy for storage and computation in cloud computing. Information
Sciences, 258, 371-386.
PROCESS MAP FOR CLOUD COMPUTING
References
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security
and privacy for storage and computation in cloud computing. Information
Sciences, 258, 371-386.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





