Cloud Computing Project: Enhancing Data Security and Access
VerifiedAdded on 2021/04/17
|14
|2602
|55
Project
AI Summary
This project explores cloud computing, addressing the challenges organizations face in securely storing confidential data. The project investigates the benefits of cloud computing in enhancing data accessibility and security, including cost savings, increased flexibility, and improved collaboration. It delves into research questions about adopting cloud computing, including the necessary steps, and how it enhances data accessibility and security. The conceptual framework discusses the usefulness of cloud computing in enhancing data accessibility and security, supported by academic sources. The methodology section describes the use of the System Development Life Cycle (SDLC) and secondary data collection methods. Ethical issues, compliance requirements, and data analysis are also covered. The project plan includes deliverables, a work breakdown structure (WBS), risk analysis, a duration schedule, and a Gantt chart for project management. The project highlights the importance of data encryption, off-site data storage, and a comprehensive approach to cloud computing implementation.

Running head: CLOUD COMPUTING
Cloud Computing
Name of the Student
Name of the University
Author’s Note
Cloud Computing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD COMPUTING
Table of Contents
1. Rationale................................................................................................................................2
1.1 Problem domain...............................................................................................................2
1.2 Purpose and justification..................................................................................................2
2. Research Questions................................................................................................................2
3. Conceptual or theoretical framework.....................................................................................3
3.1 Usefulness of cloud computing in enhancing accessibility of data and information.......3
3.2 Usefulness of cloud computing in increasing security of data and information..............3
3.3 Steps for adopting cloud computing................................................................................4
4. Methodology..........................................................................................................................5
4.1 Research and Systems Development method(s)..............................................................5
4.2 Data collection or systems design methods.....................................................................5
4.3 Ethical Issues....................................................................................................................5
4.4 Compliance Requirements (Workplace, Industry or Government regulations)...............6
4.5 Analysis of data................................................................................................................6
5. Project Plan............................................................................................................................6
5.1 Deliverables......................................................................................................................6
5.2 Work breakdown structure (WBS)...................................................................................7
5.3 Risk Analysis...................................................................................................................8
5.4 Duration............................................................................................................................9
5.5 Gantt chart......................................................................................................................12
References................................................................................................................................13
CLOUD COMPUTING
Table of Contents
1. Rationale................................................................................................................................2
1.1 Problem domain...............................................................................................................2
1.2 Purpose and justification..................................................................................................2
2. Research Questions................................................................................................................2
3. Conceptual or theoretical framework.....................................................................................3
3.1 Usefulness of cloud computing in enhancing accessibility of data and information.......3
3.2 Usefulness of cloud computing in increasing security of data and information..............3
3.3 Steps for adopting cloud computing................................................................................4
4. Methodology..........................................................................................................................5
4.1 Research and Systems Development method(s)..............................................................5
4.2 Data collection or systems design methods.....................................................................5
4.3 Ethical Issues....................................................................................................................5
4.4 Compliance Requirements (Workplace, Industry or Government regulations)...............6
4.5 Analysis of data................................................................................................................6
5. Project Plan............................................................................................................................6
5.1 Deliverables......................................................................................................................6
5.2 Work breakdown structure (WBS)...................................................................................7
5.3 Risk Analysis...................................................................................................................8
5.4 Duration............................................................................................................................9
5.5 Gantt chart......................................................................................................................12
References................................................................................................................................13

2
CLOUD COMPUTING
1. Rationale
1.1 Problem domain
It is identified that organizations faces number of issues as well as challenges in
storing confidential data as well as information properly on the site due to lack of proper
security. It is found that if any issue problem occurs within the system then the organization
faces number of challenges in accessing data. In order to resolve this issue, it is quite
important for the organizations to adopt loud computing technology within the organization.
1.2 Purpose and justification
The problems that the organization faces due to lack of security as well as
accessibility can be easily resolved with the adoption of cloud computing technology. It is
found that cloud host mainly involves in monitoring security, which is very much efficient in
comparison to in-house system. Utilization of cloud computing helps in providing greater
security and the data as well as information, which are mainly stored within the cloud, can be
accessed in spite of location and time. In addition to this, utilization of cloud computing helps
in saving cost, increasing flexibility, mobility as well as collaboration within the
organization.
2. Research Questions
The research questions include:
What are the steps that needs to be conducted in order to adopt cloud computing ?
How cloud computing enhances accessibility of data and information?
How security of data and information can be enhanced due to the utilization cloud
computing?
CLOUD COMPUTING
1. Rationale
1.1 Problem domain
It is identified that organizations faces number of issues as well as challenges in
storing confidential data as well as information properly on the site due to lack of proper
security. It is found that if any issue problem occurs within the system then the organization
faces number of challenges in accessing data. In order to resolve this issue, it is quite
important for the organizations to adopt loud computing technology within the organization.
1.2 Purpose and justification
The problems that the organization faces due to lack of security as well as
accessibility can be easily resolved with the adoption of cloud computing technology. It is
found that cloud host mainly involves in monitoring security, which is very much efficient in
comparison to in-house system. Utilization of cloud computing helps in providing greater
security and the data as well as information, which are mainly stored within the cloud, can be
accessed in spite of location and time. In addition to this, utilization of cloud computing helps
in saving cost, increasing flexibility, mobility as well as collaboration within the
organization.
2. Research Questions
The research questions include:
What are the steps that needs to be conducted in order to adopt cloud computing ?
How cloud computing enhances accessibility of data and information?
How security of data and information can be enhanced due to the utilization cloud
computing?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD COMPUTING
3. Conceptual or theoretical framework
3.1 Usefulness of cloud computing in enhancing accessibility of data and information
According to Tao et al. (2014), the data as well as information of the organization is
mainly stored in the cloud, which can also be accessible if the machine on which the
information is present is not working. Proper accessibility of information as well as data
irrespective of time and location is very much necessary when two or more member of the
team is working together. Cloud computing assist in providing a collaborative simple process
with the help of which, information can be accessible as well as shared securely on a cloud-
based platform state it (Hashem et al., 2015). The ability to access information or to get
connected to the office from anywhere irrespective of place reflects that person with some
disability can also access the interface to connect with relevant infrastructure of work by
utilizing proper cloud computing technology.
3.2 Usefulness of cloud computing in increasing security of data and information
It is identified that numerous level of control within a network infrastructure is
provided with the adoption of cloud in order to afford protection from continuity. It is stated
by Chen (2015) that the main job of the cloud host is to properly monitor security, which is
found to be quite efficient in comparison to in-house system. As most of the business
generally does not want to consider the chances of internal data theft, however it is analyzed
that high percentage of data theft mainly occurs internally (Gai et al., 2015). Thus, in order to
secure the confidential as well as sensitive data as it is very much necessary to keep the
sensitive data or information of the organization off-site. The main amped up security is
considered as data encryption for data that is being transmitted over the network and stored
within the databases.
CLOUD COMPUTING
3. Conceptual or theoretical framework
3.1 Usefulness of cloud computing in enhancing accessibility of data and information
According to Tao et al. (2014), the data as well as information of the organization is
mainly stored in the cloud, which can also be accessible if the machine on which the
information is present is not working. Proper accessibility of information as well as data
irrespective of time and location is very much necessary when two or more member of the
team is working together. Cloud computing assist in providing a collaborative simple process
with the help of which, information can be accessible as well as shared securely on a cloud-
based platform state it (Hashem et al., 2015). The ability to access information or to get
connected to the office from anywhere irrespective of place reflects that person with some
disability can also access the interface to connect with relevant infrastructure of work by
utilizing proper cloud computing technology.
3.2 Usefulness of cloud computing in increasing security of data and information
It is identified that numerous level of control within a network infrastructure is
provided with the adoption of cloud in order to afford protection from continuity. It is stated
by Chen (2015) that the main job of the cloud host is to properly monitor security, which is
found to be quite efficient in comparison to in-house system. As most of the business
generally does not want to consider the chances of internal data theft, however it is analyzed
that high percentage of data theft mainly occurs internally (Gai et al., 2015). Thus, in order to
secure the confidential as well as sensitive data as it is very much necessary to keep the
sensitive data or information of the organization off-site. The main amped up security is
considered as data encryption for data that is being transmitted over the network and stored
within the databases.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD COMPUTING
3.3 Steps for adopting cloud computing
The steps that are necessary for adopting cloud computing are illustrated below:
Assessment: It is stated by Tao et al., (2014) that after envisioning of the IT
environment, the technology advisors generally needs to conduct a assessment for the
infrastructure of the organization. This evaluation generally assists in providing proper
baseline for developing timeframe, costs as well as resources.
Alignment: According to Chen (2015), the client organization is always advised to
align its technical infrastructure with proper cloud solution. The step generally helps in
providing a roadmap for ensuring that the client has clear idea about the transformation of its
infrastructure from current to future states.
Design: The most important step is the design of the best cloud solution in order to
help the organization in realizing its various business goals as well as objectives (Zheng et
al., 2015).
Transition: After proper design of the solution, the various steps, which are very
much necessary for the transition of current environment to the future, are generally outlined
in order to create a proper transition plan.
Improvement: With proper technical requirements, internal utilization as well as
publication licensing are generally required in order to make sure that IT environments are
quite necessary for providing the greatest ROI (Gai et al., 2015).
CLOUD COMPUTING
3.3 Steps for adopting cloud computing
The steps that are necessary for adopting cloud computing are illustrated below:
Assessment: It is stated by Tao et al., (2014) that after envisioning of the IT
environment, the technology advisors generally needs to conduct a assessment for the
infrastructure of the organization. This evaluation generally assists in providing proper
baseline for developing timeframe, costs as well as resources.
Alignment: According to Chen (2015), the client organization is always advised to
align its technical infrastructure with proper cloud solution. The step generally helps in
providing a roadmap for ensuring that the client has clear idea about the transformation of its
infrastructure from current to future states.
Design: The most important step is the design of the best cloud solution in order to
help the organization in realizing its various business goals as well as objectives (Zheng et
al., 2015).
Transition: After proper design of the solution, the various steps, which are very
much necessary for the transition of current environment to the future, are generally outlined
in order to create a proper transition plan.
Improvement: With proper technical requirements, internal utilization as well as
publication licensing are generally required in order to make sure that IT environments are
quite necessary for providing the greatest ROI (Gai et al., 2015).

5
CLOUD COMPUTING
4. Methodology
4.1 Research and Systems Development method(s)
It is identified that in this research, system development life cycle methods is utilized
in order to describe the processes that are mainly associated with planning, creating, testing
as well as deploying an information system (Akmeemana & Wickramasinghe, 2016). It is
identified that SDLC method is mainly applied to number of software and hardware
configuration that are very much necessary in order to implement cloud computing within
organizations.
4.2 Data collection or systems design methods
In this research, secondary data collection method is used in order to gather
information about cloud computing technology. It is identified that in order to collect
information various journal articles are generally reviewed so that proper information about
the benefits, accessibility as well as security of cloud computing can be properly gathered.
4.3 Ethical Issues
The ethical issues, which can occur include:
Confidentiality: It is very much necessary to keep the confidential data and
information secure. If proper security of data and information is not maintained then there are
number of chances of data loss.
Do not harm: The people who are involved within the research must not be harmed
otherwise there will be chances of occurring ethical issues.
Respect for privacy: It is very much necessary to respect the privacy of information
and data properly. If privacy is not maintained within the organization then there are number
of chances of occurring ethical issues.
CLOUD COMPUTING
4. Methodology
4.1 Research and Systems Development method(s)
It is identified that in this research, system development life cycle methods is utilized
in order to describe the processes that are mainly associated with planning, creating, testing
as well as deploying an information system (Akmeemana & Wickramasinghe, 2016). It is
identified that SDLC method is mainly applied to number of software and hardware
configuration that are very much necessary in order to implement cloud computing within
organizations.
4.2 Data collection or systems design methods
In this research, secondary data collection method is used in order to gather
information about cloud computing technology. It is identified that in order to collect
information various journal articles are generally reviewed so that proper information about
the benefits, accessibility as well as security of cloud computing can be properly gathered.
4.3 Ethical Issues
The ethical issues, which can occur include:
Confidentiality: It is very much necessary to keep the confidential data and
information secure. If proper security of data and information is not maintained then there are
number of chances of data loss.
Do not harm: The people who are involved within the research must not be harmed
otherwise there will be chances of occurring ethical issues.
Respect for privacy: It is very much necessary to respect the privacy of information
and data properly. If privacy is not maintained within the organization then there are number
of chances of occurring ethical issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CLOUD COMPUTING
4.4 Compliance Requirements (Workplace, Industry or Government regulations)
As per occupational health and safety act, it is very much necessary to maintain
proper as well as safe working environment for the employees of the organization in order to
avoid various type of workplace accidents as well as injuries. Proper maintenance of
occupational health and safety environment within the organization is very much necessary
for proper implementation of cloud computing.
4.5 Analysis of data
After undertaking a survey, it is analyzed that the organizations who adopted cloud
computing are facing less challenges as compared to organization that does not have proper
facility to store their data as well as information within the cloud. Out of 25 organization, 3 of
them faces minor security related issues which can be easily managed by adopting proper
security management strategies. In addition to this, it is found that with the adoption of cloud
computing within organizations, accessing data becomes one of the easiest way to collect
information and perform activities by the stakeholders irrespective of time and location.
5. Project Plan
5.1 Deliverables
The deliverables of the project mainly include:
Designing scalable infrastructure
Finalize the hosting facility and bandwidth requirement
Procuring infrastructure components
Deployment of cloud computing infrastructure
Planning for disaster recovery and continuity
Integration of monitoring solution
CLOUD COMPUTING
4.4 Compliance Requirements (Workplace, Industry or Government regulations)
As per occupational health and safety act, it is very much necessary to maintain
proper as well as safe working environment for the employees of the organization in order to
avoid various type of workplace accidents as well as injuries. Proper maintenance of
occupational health and safety environment within the organization is very much necessary
for proper implementation of cloud computing.
4.5 Analysis of data
After undertaking a survey, it is analyzed that the organizations who adopted cloud
computing are facing less challenges as compared to organization that does not have proper
facility to store their data as well as information within the cloud. Out of 25 organization, 3 of
them faces minor security related issues which can be easily managed by adopting proper
security management strategies. In addition to this, it is found that with the adoption of cloud
computing within organizations, accessing data becomes one of the easiest way to collect
information and perform activities by the stakeholders irrespective of time and location.
5. Project Plan
5.1 Deliverables
The deliverables of the project mainly include:
Designing scalable infrastructure
Finalize the hosting facility and bandwidth requirement
Procuring infrastructure components
Deployment of cloud computing infrastructure
Planning for disaster recovery and continuity
Integration of monitoring solution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
CLOUD COMPUTING
Preparing for customer call centre
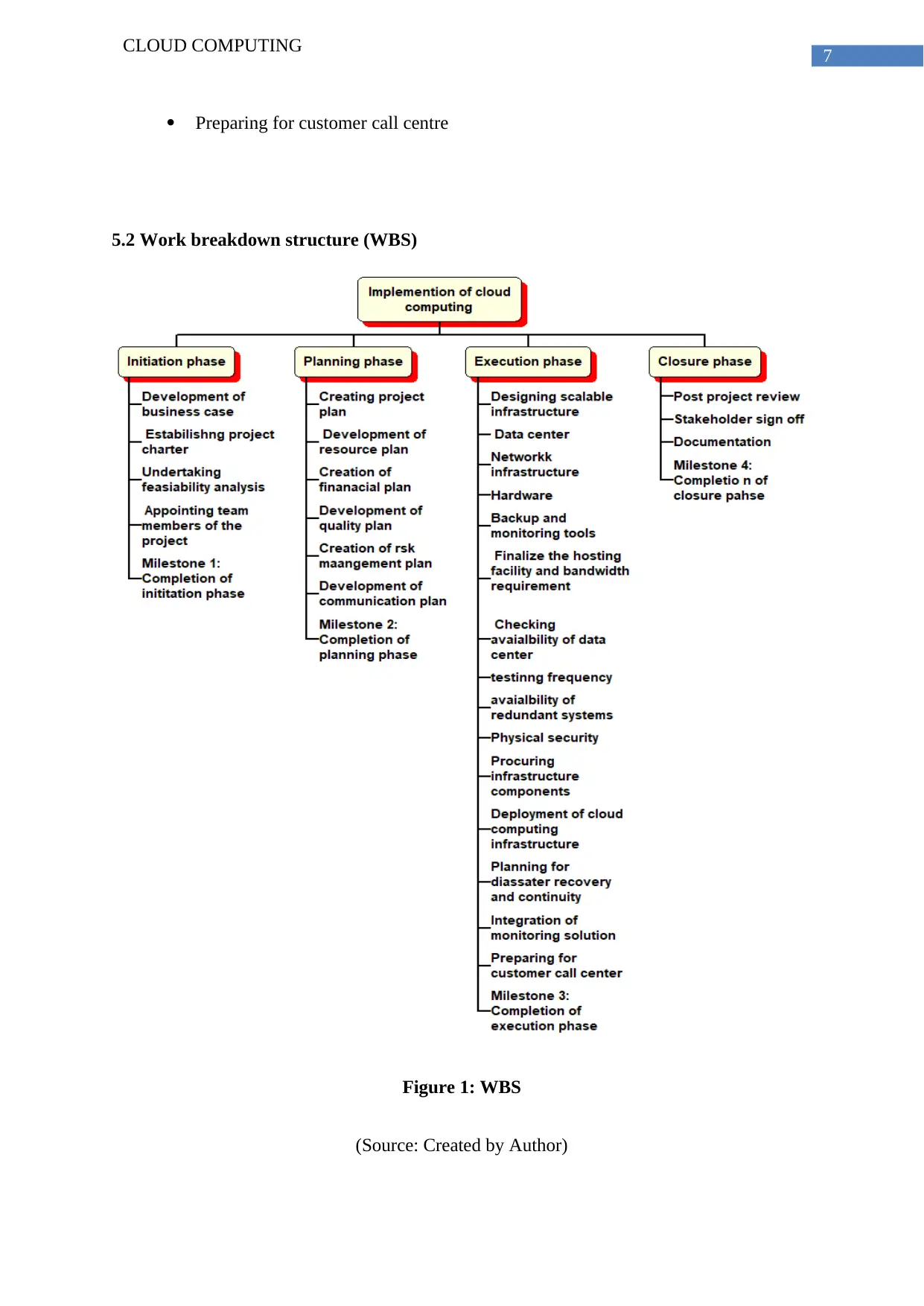
5.2 Work breakdown structure (WBS)
Figure 1: WBS
(Source: Created by Author)
CLOUD COMPUTING
Preparing for customer call centre
5.2 Work breakdown structure (WBS)
Figure 1: WBS
(Source: Created by Author)
8
CLOUD COMPUTING
5.3 Risk Analysis
Risk Description Impact Likelihood Mitigation
Strategies
Improper
budget
assumption
Due to
improper budget
assumption, the
project
managers face
financial issues
while
progressing with
the project.
High High The budget of
the project must
be assumed after
undertaking
proper market
analysis about
the cost of
resources and
materials.
Inappropriate
management of
project
schedule
If the project
managers does
not maintain the
schedule of the
project properly
then it will be
quite difficult to
complete the
project on time.
High High Proper
management of
project activities
is necessary in
order to compete
the project on
time.
Security issues The security
concerns in
cloud computing
mainly include
High High In order to
resolve security
issue,
cryptographic
CLOUD COMPUTING
5.3 Risk Analysis
Risk Description Impact Likelihood Mitigation
Strategies
Improper
budget
assumption
Due to
improper budget
assumption, the
project
managers face
financial issues
while
progressing with
the project.
High High The budget of
the project must
be assumed after
undertaking
proper market
analysis about
the cost of
resources and
materials.
Inappropriate
management of
project
schedule
If the project
managers does
not maintain the
schedule of the
project properly
then it will be
quite difficult to
complete the
project on time.
High High Proper
management of
project activities
is necessary in
order to compete
the project on
time.
Security issues The security
concerns in
cloud computing
mainly include
High High In order to
resolve security
issue,
cryptographic
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
CLOUD COMPUTING
data at rest as
well as data at
transit .
encryption
mechanism must
be used.
Inexperienced
project
managers
As the project
managers are
not experienced
they face
difficulty in
managing the
project properly
thus completing
the entire project
on time.
High Medium Experienced
project
managers must
be hired so that
the project does
not faces any
type of
management
issues.
5.4 Duration
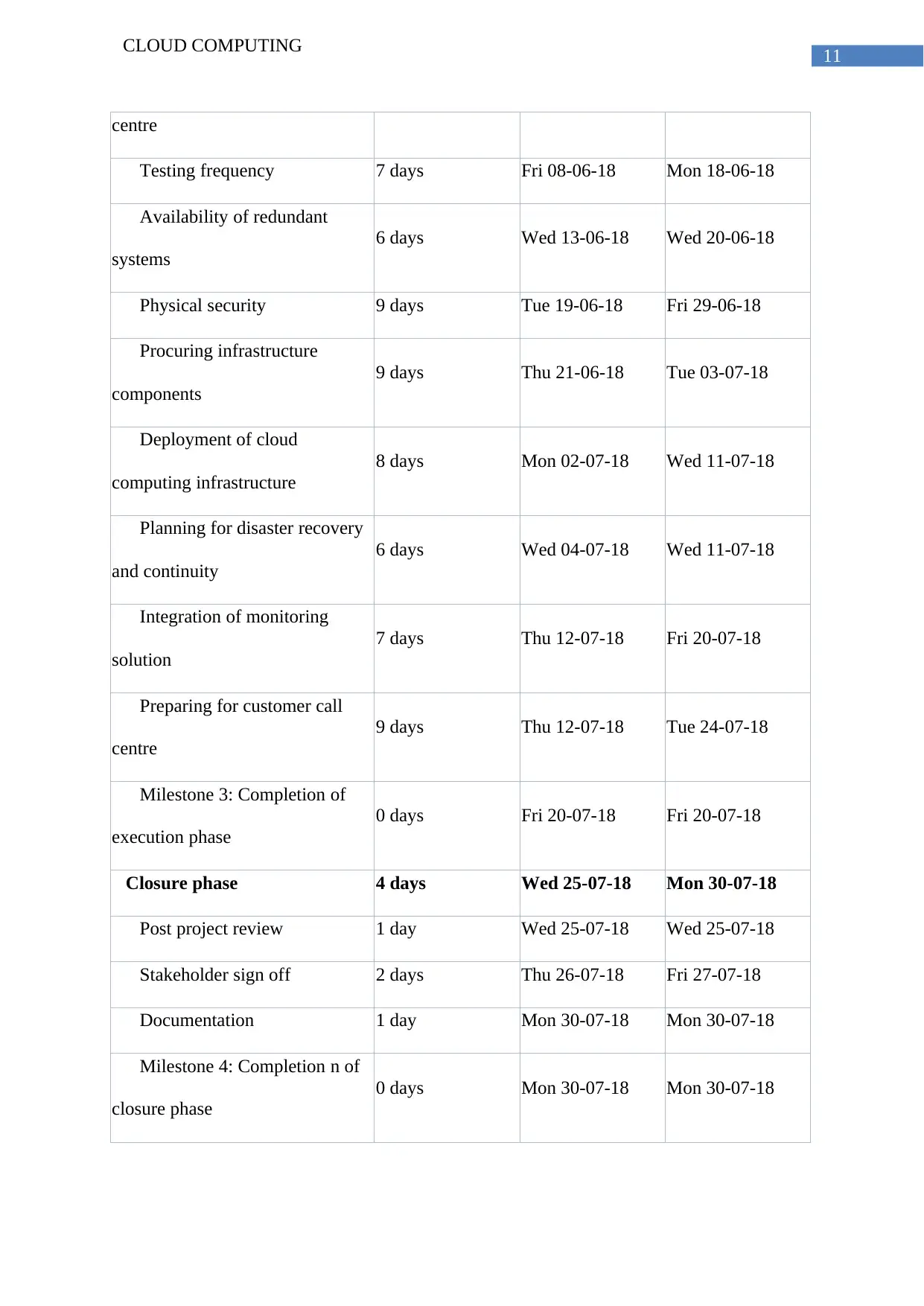
Task Name Duration Start Finish
Implementation of cloud
computing
95 days Tue 20-03-18 Mon 30-07-18
Initiation phase 10 days Tue 20-03-18 Mon 02-04-18
Development of business case 2 days Tue 20-03-18 Wed 21-03-18
Establishing project charter 3 days Thu 22-03-18 Mon 26-03-18
Undertaking feasibility
analysis
2 days Tue 27-03-18 Wed 28-03-18
Appointing team members of 3 days Thu 29-03-18 Mon 02-04-18
CLOUD COMPUTING
data at rest as
well as data at
transit .
encryption
mechanism must
be used.
Inexperienced
project
managers
As the project
managers are
not experienced
they face
difficulty in
managing the
project properly
thus completing
the entire project
on time.
High Medium Experienced
project
managers must
be hired so that
the project does
not faces any
type of
management
issues.
5.4 Duration
Task Name Duration Start Finish
Implementation of cloud
computing
95 days Tue 20-03-18 Mon 30-07-18
Initiation phase 10 days Tue 20-03-18 Mon 02-04-18
Development of business case 2 days Tue 20-03-18 Wed 21-03-18
Establishing project charter 3 days Thu 22-03-18 Mon 26-03-18
Undertaking feasibility
analysis
2 days Tue 27-03-18 Wed 28-03-18
Appointing team members of 3 days Thu 29-03-18 Mon 02-04-18
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
CLOUD COMPUTING
the project
Milestone 1: Completion of
initiation phase
0 days Mon 02-04-18 Mon 02-04-18
Planning phase 18 days Tue 03-04-18 Thu 26-04-18
Creating project plan 3 days Tue 03-04-18 Thu 05-04-18
Development of resource plan 2 days Fri 06-04-18 Mon 09-04-18
Creation of financial plan 3 days Tue 10-04-18 Thu 12-04-18
Development of quality plan 3 days Fri 13-04-18 Tue 17-04-18
Creation of risk management
plan
4 days Wed 18-04-18 Mon 23-04-18
Development of
communication plan
3 days Tue 24-04-18 Thu 26-04-18
Milestone 2: Completion of
planning phase
0 days Thu 26-04-18 Thu 26-04-18
Execution phase 63 days Fri 27-04-18 Tue 24-07-18
Designing scalable
infrastructure
3 days Fri 27-04-18 Tue 01-05-18
Data centre 6 days Wed 02-05-18 Wed 09-05-18
Network infrastructure 7 days Thu 10-05-18 Fri 18-05-18
Hardware 5 days Mon 21-05-18 Fri 25-05-18
Backup and monitoring tools 4 days Mon 28-05-18 Thu 31-05-18
Finalize the hosting facility
and bandwidth requirement
5 days Fri 01-06-18 Thu 07-06-18
Checking availability of data 8 days Fri 01-06-18 Tue 12-06-18
CLOUD COMPUTING
the project
Milestone 1: Completion of
initiation phase
0 days Mon 02-04-18 Mon 02-04-18
Planning phase 18 days Tue 03-04-18 Thu 26-04-18
Creating project plan 3 days Tue 03-04-18 Thu 05-04-18
Development of resource plan 2 days Fri 06-04-18 Mon 09-04-18
Creation of financial plan 3 days Tue 10-04-18 Thu 12-04-18
Development of quality plan 3 days Fri 13-04-18 Tue 17-04-18
Creation of risk management
plan
4 days Wed 18-04-18 Mon 23-04-18
Development of
communication plan
3 days Tue 24-04-18 Thu 26-04-18
Milestone 2: Completion of
planning phase
0 days Thu 26-04-18 Thu 26-04-18
Execution phase 63 days Fri 27-04-18 Tue 24-07-18
Designing scalable
infrastructure
3 days Fri 27-04-18 Tue 01-05-18
Data centre 6 days Wed 02-05-18 Wed 09-05-18
Network infrastructure 7 days Thu 10-05-18 Fri 18-05-18
Hardware 5 days Mon 21-05-18 Fri 25-05-18
Backup and monitoring tools 4 days Mon 28-05-18 Thu 31-05-18
Finalize the hosting facility
and bandwidth requirement
5 days Fri 01-06-18 Thu 07-06-18
Checking availability of data 8 days Fri 01-06-18 Tue 12-06-18
11
CLOUD COMPUTING
centre
Testing frequency 7 days Fri 08-06-18 Mon 18-06-18
Availability of redundant
systems
6 days Wed 13-06-18 Wed 20-06-18
Physical security 9 days Tue 19-06-18 Fri 29-06-18
Procuring infrastructure
components
9 days Thu 21-06-18 Tue 03-07-18
Deployment of cloud
computing infrastructure
8 days Mon 02-07-18 Wed 11-07-18
Planning for disaster recovery
and continuity
6 days Wed 04-07-18 Wed 11-07-18
Integration of monitoring
solution
7 days Thu 12-07-18 Fri 20-07-18
Preparing for customer call
centre
9 days Thu 12-07-18 Tue 24-07-18
Milestone 3: Completion of
execution phase
0 days Fri 20-07-18 Fri 20-07-18
Closure phase 4 days Wed 25-07-18 Mon 30-07-18
Post project review 1 day Wed 25-07-18 Wed 25-07-18
Stakeholder sign off 2 days Thu 26-07-18 Fri 27-07-18
Documentation 1 day Mon 30-07-18 Mon 30-07-18
Milestone 4: Completion n of
closure phase
0 days Mon 30-07-18 Mon 30-07-18
CLOUD COMPUTING
centre
Testing frequency 7 days Fri 08-06-18 Mon 18-06-18
Availability of redundant
systems
6 days Wed 13-06-18 Wed 20-06-18
Physical security 9 days Tue 19-06-18 Fri 29-06-18
Procuring infrastructure
components
9 days Thu 21-06-18 Tue 03-07-18
Deployment of cloud
computing infrastructure
8 days Mon 02-07-18 Wed 11-07-18
Planning for disaster recovery
and continuity
6 days Wed 04-07-18 Wed 11-07-18
Integration of monitoring
solution
7 days Thu 12-07-18 Fri 20-07-18
Preparing for customer call
centre
9 days Thu 12-07-18 Tue 24-07-18
Milestone 3: Completion of
execution phase
0 days Fri 20-07-18 Fri 20-07-18
Closure phase 4 days Wed 25-07-18 Mon 30-07-18
Post project review 1 day Wed 25-07-18 Wed 25-07-18
Stakeholder sign off 2 days Thu 26-07-18 Fri 27-07-18
Documentation 1 day Mon 30-07-18 Mon 30-07-18
Milestone 4: Completion n of
closure phase
0 days Mon 30-07-18 Mon 30-07-18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





