Detailed Risk Assessment of Cloud Computing Adoption for Aztek Finance
VerifiedAdded on 2020/03/28
|22
|6043
|213
Report
AI Summary
This report provides a risk assessment for Aztek, focusing on the adoption of cloud computing within the Australian finance industry. It examines the current state of cloud adoption, highlighting benefits like cost reduction and accessibility, while also addressing challenges such as data privacy, security concerns, vendor lock-in, and compliance. The report details security issues like compromised management interfaces, isolation failures, and data deletion vulnerabilities. A comprehensive risk assessment is presented, including the identification of threats, assets, vulnerabilities, and associated risks, culminating in a risk assessment matrix to prioritize security measures. The report also discusses data security measures and proposes strategies to mitigate potential risks, ultimately aiming to support information security management and minimize vulnerabilities. Examples of cloud adoption in the finance industry are also provided, including CME Clearport and Microsoft Azure DataMarket.

Running head: CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
Cloud Computing Adoption
(Risk Assessment for Aztek)
Name of the Student
Name of the University
Author Note
Cloud Computing Adoption
(Risk Assessment for Aztek)
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
Executive Summary
The purpose of this report is to present a risk assessment for the Aztek for the threats, issues,
vulnerabilities, and risks that could arise within the organization after adopting Cloud Computing
within the system. Australian finance industries are showing their interest on this technology and
adopting it for the beneficial factors and least expenditure on the resources. This could provide
the organization benefits of access to the data and information at anywhere via connecting to the
internet. Installation is much easier and not extra expanse has been made for the maintenance of
the information as the third party that is providing the cloud services took all the responsibilities
of the maintenance. Despite of all these advantages, there are certain challenges, risks,
vulnerabilities, and issues in adopting cloud computing within the organization. This could even
raise data security issues that lead to the necessity of the information security management
within the organization. This report proposes a risk assessment in manner to support the
information security management and minimize the risks to the extent level. This report also
proposes a severity matrix that can be beneficial in prioritizing the securities based on their
impact. Data security has also been discussed in this report and related issues and measures to
mitigate them.
Executive Summary
The purpose of this report is to present a risk assessment for the Aztek for the threats, issues,
vulnerabilities, and risks that could arise within the organization after adopting Cloud Computing
within the system. Australian finance industries are showing their interest on this technology and
adopting it for the beneficial factors and least expenditure on the resources. This could provide
the organization benefits of access to the data and information at anywhere via connecting to the
internet. Installation is much easier and not extra expanse has been made for the maintenance of
the information as the third party that is providing the cloud services took all the responsibilities
of the maintenance. Despite of all these advantages, there are certain challenges, risks,
vulnerabilities, and issues in adopting cloud computing within the organization. This could even
raise data security issues that lead to the necessity of the information security management
within the organization. This report proposes a risk assessment in manner to support the
information security management and minimize the risks to the extent level. This report also
proposes a severity matrix that can be beneficial in prioritizing the securities based on their
impact. Data security has also been discussed in this report and related issues and measures to
mitigate them.

2CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
Table of Contents
Introduction......................................................................................................................................2
Cloud Adoption in Australian Finance Sectors...............................................................................2
Current State and Approach to Cloud computing........................................................................2
Cloud adoption Example (Finance Industries)............................................................................4
Challenges........................................................................................................................................5
Security Issues.................................................................................................................................6
Threats, Assets, Vulnerabilities, and Risks Assessments................................................................9
Risk Assessment Matrix............................................................................................................14
Conclusion.....................................................................................................................................15
References:....................................................................................................................................16
Table of Contents
Introduction......................................................................................................................................2
Cloud Adoption in Australian Finance Sectors...............................................................................2
Current State and Approach to Cloud computing........................................................................2
Cloud adoption Example (Finance Industries)............................................................................4
Challenges........................................................................................................................................5
Security Issues.................................................................................................................................6
Threats, Assets, Vulnerabilities, and Risks Assessments................................................................9
Risk Assessment Matrix............................................................................................................14
Conclusion.....................................................................................................................................15
References:....................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
Introduction
New world is moving rapidly towards being digital and Cloud computing is offering
industries to be more automated and much efficiently led the operational activities. Australian
finance industries have been implementing Cloud computing for the enhancement of their
performance. It was becoming heavy burden for the industries to manage the in-house IT
departments and Cloud computing is providing the solutions for those issues. Cloud computing is
much cheaper than the in-house IT departments and it has been maintained by the third party that
implies that the organization will have to no worry about the maintenance and services related to
the data and information including the information security management. Most of the Australian
finance industries have not adopted Cloud computing in their existing system yet however many
of them have adopted it.
Cloud Computing can be defined as the on-demand service that allows the users to store
data in the Cloud and let them access wherever they want via connecting to the internet. This
basically performs on three platforms that can be listed as: SaaS (Software-as-a-Service), PaaS
(Platform-as-a-service), and IaaS (Information-as-a-service). These platforms are being deployed
through four basic models that can be listed as: Public Cloud, private Cloud, Hybrid Cloud, and
Community Cloud.
Cloud Adoption in Australian Finance Sectors
Current State and Approach to Cloud computing
Australian finance industry is in its toddling stage of Cloud adoption as many of the
financial industries’ range of Cloud based services are limited. For some of the cases the
Introduction
New world is moving rapidly towards being digital and Cloud computing is offering
industries to be more automated and much efficiently led the operational activities. Australian
finance industries have been implementing Cloud computing for the enhancement of their
performance. It was becoming heavy burden for the industries to manage the in-house IT
departments and Cloud computing is providing the solutions for those issues. Cloud computing is
much cheaper than the in-house IT departments and it has been maintained by the third party that
implies that the organization will have to no worry about the maintenance and services related to
the data and information including the information security management. Most of the Australian
finance industries have not adopted Cloud computing in their existing system yet however many
of them have adopted it.
Cloud Computing can be defined as the on-demand service that allows the users to store
data in the Cloud and let them access wherever they want via connecting to the internet. This
basically performs on three platforms that can be listed as: SaaS (Software-as-a-Service), PaaS
(Platform-as-a-service), and IaaS (Information-as-a-service). These platforms are being deployed
through four basic models that can be listed as: Public Cloud, private Cloud, Hybrid Cloud, and
Community Cloud.
Cloud Adoption in Australian Finance Sectors
Current State and Approach to Cloud computing
Australian finance industry is in its toddling stage of Cloud adoption as many of the
financial industries’ range of Cloud based services are limited. For some of the cases the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
consumers would not be aware of the services that could be provided by the Cloud computing
and its approach is still not strategically sound. A survey (made by) suggests almost 88% of the
financial industries are using Cloud-based services and implementation of Cloud computing at its
utmost pace and among them 81% of the industries were aware with the services offered by
Cloud computing (Chang, Walters & Wills, 2014).
Due to the common approach for financial industries 50% of the Australian Finance
industries are linked to the use of hybrid of private Cloud and public Cloud. In-house IT and
moving non-critical services like content management tools, collaboration and email
management to the Cloud based services is being practiced by 40% of the industries. Some of the
financial industries are using Cloud services as a testing environment in manner to plead the
development of use cases that could be better option for assessing the hybrid of Public Cloud and
on premises, in-house hosting applications of the Cloud services (Schulte et al., 2015). The
financial industries are also using it as test beds for new and innovative applications and among
all the industries only 8% of the industries are using strict Private Cloud only policy. Compliance
and privacy concerns including the confidence that the Private Cloud can satisfy the business
requirements of the organization are its main objectives. 92% of the industries that are using
Cloud based services have a strategically developed strategy that is based on hybrid of Private
and Public Cloud hosted both in-house and externally IT services. It can be stated based on the
discussion that the confidence among the financial industries has been increasing towards
adopting Cloud Computing services within the system of the organization (Gai, 2014).
Otherwise, a certain level of prudency on the context of migration towards Cloud computing can
also be noted. Digital transformation of the business is still preferable to many consumers rather
than migration of their data to the Cloud.
consumers would not be aware of the services that could be provided by the Cloud computing
and its approach is still not strategically sound. A survey (made by) suggests almost 88% of the
financial industries are using Cloud-based services and implementation of Cloud computing at its
utmost pace and among them 81% of the industries were aware with the services offered by
Cloud computing (Chang, Walters & Wills, 2014).
Due to the common approach for financial industries 50% of the Australian Finance
industries are linked to the use of hybrid of private Cloud and public Cloud. In-house IT and
moving non-critical services like content management tools, collaboration and email
management to the Cloud based services is being practiced by 40% of the industries. Some of the
financial industries are using Cloud services as a testing environment in manner to plead the
development of use cases that could be better option for assessing the hybrid of Public Cloud and
on premises, in-house hosting applications of the Cloud services (Schulte et al., 2015). The
financial industries are also using it as test beds for new and innovative applications and among
all the industries only 8% of the industries are using strict Private Cloud only policy. Compliance
and privacy concerns including the confidence that the Private Cloud can satisfy the business
requirements of the organization are its main objectives. 92% of the industries that are using
Cloud based services have a strategically developed strategy that is based on hybrid of Private
and Public Cloud hosted both in-house and externally IT services. It can be stated based on the
discussion that the confidence among the financial industries has been increasing towards
adopting Cloud Computing services within the system of the organization (Gai, 2014).
Otherwise, a certain level of prudency on the context of migration towards Cloud computing can
also be noted. Digital transformation of the business is still preferable to many consumers rather
than migration of their data to the Cloud.

5CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
Cloud adoption Example (Finance Industries)
CME Clearport OTC Data on-demand: An on-demand Software-as-a-services
(SaaS) web service working on the same platform Xignite and is proving to be helpful in offering
accesses to end-of- day OTC volume, open interest, and settlement data in manner to provide
support to the markets that are available through CME Clearport® (Pattnaik, Prusty & Dash,
2016).
NASDAQ OMX Data on-demand: Known software that provides flexibility and easy access to
massive amount of data is Software-as-a-service (SaaS) and is made available to the market by
the support and skills of Xignite. API (Application programming interface) can be used to get an
access to it and can be helpful in managing users to purchase data online as a web application to
give it more comfort ability. It can also be used as plain texts (Mahmood et al., 2014).
Microsoft Azure DataMarket for the Energy Industry: For enabling the exploration,
discovery and consumption of data from the commercial data sources and trusted public domains
Cloud services offered by IT giant Microsoft DataMarket SaaS. Public domains for example,
health, demographics, weather, real estates, navigation, transportation, and location- based
services, and many more are making its use to the limit. Analytics for enabling insight from that
data and visualization is also included in it (Coleman et al., 2016). For incorporating these data
into software applications for any of the devices common API are the easiest approach. To create
analytic applications and energy forecasting many of the energy industries have been using these
platforms.
Gridglo real-time energy apps: Due to the demand of the services many firms are
jumping in the competition of one of the startup, Gridglo is developing SaaS services for their
Cloud adoption Example (Finance Industries)
CME Clearport OTC Data on-demand: An on-demand Software-as-a-services
(SaaS) web service working on the same platform Xignite and is proving to be helpful in offering
accesses to end-of- day OTC volume, open interest, and settlement data in manner to provide
support to the markets that are available through CME Clearport® (Pattnaik, Prusty & Dash,
2016).
NASDAQ OMX Data on-demand: Known software that provides flexibility and easy access to
massive amount of data is Software-as-a-service (SaaS) and is made available to the market by
the support and skills of Xignite. API (Application programming interface) can be used to get an
access to it and can be helpful in managing users to purchase data online as a web application to
give it more comfort ability. It can also be used as plain texts (Mahmood et al., 2014).
Microsoft Azure DataMarket for the Energy Industry: For enabling the exploration,
discovery and consumption of data from the commercial data sources and trusted public domains
Cloud services offered by IT giant Microsoft DataMarket SaaS. Public domains for example,
health, demographics, weather, real estates, navigation, transportation, and location- based
services, and many more are making its use to the limit. Analytics for enabling insight from that
data and visualization is also included in it (Coleman et al., 2016). For incorporating these data
into software applications for any of the devices common API are the easiest approach. To create
analytic applications and energy forecasting many of the energy industries have been using these
platforms.
Gridglo real-time energy apps: Due to the demand of the services many firms are
jumping in the competition of one of the startup, Gridglo is developing SaaS services for their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
startup in manner to sell information to utilities in Australia. Describing it as a mining energy
consumption data from smart meters would not be considered as illogical and thereafter the
combination of these data with data from other sources like data related to demographic and
weather, real estate, energy credit scoring and demand response analytics in manner to categorize
different types of consumers for providing tools that can be helpful in energy forecasting,
including an energy tool for financial risk.
Australian Banks using Cloud for risk analysis and non-core processes: IBM iDataPlex
servers has been used in various banks of Australia as a part of an Infrastructure-as-a-service
(IaaS) strategy in manner to evaluate and build programs related to risk analysis that can be used
for further purposes. Multiple systems can be used instead of just one separate computer to turn
into a pool of shared resource that can be referred as Cloud. Morgan Stanley is using PaaS Cloud
vendor Force.com for its recruiting applications that is proving to be way beneficial in extensive
Cloud penetration in strategy and analytics (Asatiani et al., 2014).
Challenges
Likewise, every other thing in the world there are certain challenges in implementation of
Cloud computing which can be listed as: data privacy, data security, vendor lock-in, availability,
and compliance with the existing policies (Sanei et al., 2014). Some of the ways in which these
challenges may impact the Australian finance industries are mentioned below:
Monetization of the data related to the customers may happen by Cloud vendors or the
data can even get compromised on the Public Cloud are also a factor for the concern of the
financial institutions. Examples speaks louder than words so considering that as traders in a firm
might be worrying about migrating their proprietary strategies related to trading in a Cloud
startup in manner to sell information to utilities in Australia. Describing it as a mining energy
consumption data from smart meters would not be considered as illogical and thereafter the
combination of these data with data from other sources like data related to demographic and
weather, real estate, energy credit scoring and demand response analytics in manner to categorize
different types of consumers for providing tools that can be helpful in energy forecasting,
including an energy tool for financial risk.
Australian Banks using Cloud for risk analysis and non-core processes: IBM iDataPlex
servers has been used in various banks of Australia as a part of an Infrastructure-as-a-service
(IaaS) strategy in manner to evaluate and build programs related to risk analysis that can be used
for further purposes. Multiple systems can be used instead of just one separate computer to turn
into a pool of shared resource that can be referred as Cloud. Morgan Stanley is using PaaS Cloud
vendor Force.com for its recruiting applications that is proving to be way beneficial in extensive
Cloud penetration in strategy and analytics (Asatiani et al., 2014).
Challenges
Likewise, every other thing in the world there are certain challenges in implementation of
Cloud computing which can be listed as: data privacy, data security, vendor lock-in, availability,
and compliance with the existing policies (Sanei et al., 2014). Some of the ways in which these
challenges may impact the Australian finance industries are mentioned below:
Monetization of the data related to the customers may happen by Cloud vendors or the
data can even get compromised on the Public Cloud are also a factor for the concern of the
financial institutions. Examples speaks louder than words so considering that as traders in a firm
might be worrying about migrating their proprietary strategies related to trading in a Cloud
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
because there are chances that the competitor might be using the same Cloud and get access to
the saved data due to some technical error or may be caused by some misbehaving elements
(Moreno-Vozmediano, Monentro & Liorente, 2013). This implies that risk analyst and portfolio
managers are much apprehensive about the location for the assets as it may lead to barrage of
lawsuits or have reputational implication on the firms.
Another concern related to the Cloud computing adoption is the ‘Vendor lock-in’. This
states that it becomes very hard or impossible to move to the other service provider once the
consumer has made agreement with a service provider. This made the situation as the consumer
get stuck with the single service provider. Another concern is the use of APIs that lead to the
necessity of being stuck with a single service provider. Even shifting from one vendor to the
other can cost the organization a lot and alters the budget calculation. It was the first priority for
the organizations that it cost much less to implement Cloud computing and transferring to
another vendor will eliminate this benefit too (Avram, 2014). Isolation failure and Loss of
governance are other challenges that “could put the challenge to control sufficiently resources in
the Cloud affecting the security and an unauthorized Cloud computer has the capability to
influence the systems on which the Cloud application has been adopting” (Tossi, Colheiros &
Buyya, 2014).
Security Issues
Following are the list of certain security issues that could be concerned before and/or after
implementing the Cloud computing within the organization:
Compromises Management Interface: This can be said as the part of the data breach in
which an intruder somehow get access to the network and thus get access to the data and
because there are chances that the competitor might be using the same Cloud and get access to
the saved data due to some technical error or may be caused by some misbehaving elements
(Moreno-Vozmediano, Monentro & Liorente, 2013). This implies that risk analyst and portfolio
managers are much apprehensive about the location for the assets as it may lead to barrage of
lawsuits or have reputational implication on the firms.
Another concern related to the Cloud computing adoption is the ‘Vendor lock-in’. This
states that it becomes very hard or impossible to move to the other service provider once the
consumer has made agreement with a service provider. This made the situation as the consumer
get stuck with the single service provider. Another concern is the use of APIs that lead to the
necessity of being stuck with a single service provider. Even shifting from one vendor to the
other can cost the organization a lot and alters the budget calculation. It was the first priority for
the organizations that it cost much less to implement Cloud computing and transferring to
another vendor will eliminate this benefit too (Avram, 2014). Isolation failure and Loss of
governance are other challenges that “could put the challenge to control sufficiently resources in
the Cloud affecting the security and an unauthorized Cloud computer has the capability to
influence the systems on which the Cloud application has been adopting” (Tossi, Colheiros &
Buyya, 2014).
Security Issues
Following are the list of certain security issues that could be concerned before and/or after
implementing the Cloud computing within the organization:
Compromises Management Interface: This can be said as the part of the data breach in
which an intruder somehow get access to the network and thus get access to the data and

8CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
information that is being offered by the service provider. This generally happens in the Public
Cloud service that provides the customers with management interfaces and access to the data and
information at anyplace via connecting to the internet (Almorsy, Grundy & Muller, 2016). This
results in the possibilities of higher risk to the data security, mainly in the situation when the data
is being accessed through the remote control and web browser vulnerabilities
Isolation Failure: The major benefit that is being offered by the Cloud computing is the
multi-tenancy and resource sharing that could lead to the failure of the mechanisms that controls
the server, storage, memory, technology and many others. However it can be said that this is very
less likely to be happen within the organization who has implemented Cloud computing rather
than traditional IT-infrastructure to manage the data. But this could impact very high and cause
serious loss to the organization (Hashizume et al., 2013).
Incomplete or insecure data deletion: There is not any way to completely delete the data
from the web once it is uploaded to the Cloud. The consumer requesting to delete the data would
have been assured by the service provider that the data has been deleted but even that it can be
recovered by certain coding and program. This could happen in multi-tenancy case as these are
much vulnerable to these cases (Modi et al., 2013). This also enhances the risk to the users using
the same hardware to store or transfer the data via the same network.
Data breaches: Any data that is being stored in the Cloud or in the internet is vulnerable
to data breach attacks. Looking the mirror of the present world it can be said the likelihood of
such attack has been increasing rapidly. In this attack the intruder get access to the data and
information saved into the data base and these are made intentionally either for the money or for
the personal revenge (Ahmed & Hossain, 2014). Data breaches leads to both security and privacy
information that is being offered by the service provider. This generally happens in the Public
Cloud service that provides the customers with management interfaces and access to the data and
information at anyplace via connecting to the internet (Almorsy, Grundy & Muller, 2016). This
results in the possibilities of higher risk to the data security, mainly in the situation when the data
is being accessed through the remote control and web browser vulnerabilities
Isolation Failure: The major benefit that is being offered by the Cloud computing is the
multi-tenancy and resource sharing that could lead to the failure of the mechanisms that controls
the server, storage, memory, technology and many others. However it can be said that this is very
less likely to be happen within the organization who has implemented Cloud computing rather
than traditional IT-infrastructure to manage the data. But this could impact very high and cause
serious loss to the organization (Hashizume et al., 2013).
Incomplete or insecure data deletion: There is not any way to completely delete the data
from the web once it is uploaded to the Cloud. The consumer requesting to delete the data would
have been assured by the service provider that the data has been deleted but even that it can be
recovered by certain coding and program. This could happen in multi-tenancy case as these are
much vulnerable to these cases (Modi et al., 2013). This also enhances the risk to the users using
the same hardware to store or transfer the data via the same network.
Data breaches: Any data that is being stored in the Cloud or in the internet is vulnerable
to data breach attacks. Looking the mirror of the present world it can be said the likelihood of
such attack has been increasing rapidly. In this attack the intruder get access to the data and
information saved into the data base and these are made intentionally either for the money or for
the personal revenge (Ahmed & Hossain, 2014). Data breaches leads to both security and privacy
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
risks for the consumers as the data related to the sensitive information goes into the wrong hands
and they have the access to manipulate, hamper, alter and expose the sensitive information.
Malicious insider: This is a very unusual risk but the impact is similar o the data breach
and this is mainly done for the revenge purpose. This intrusion can be made by the formal
employee of the organization or the stakeholders that have no relation with the organization
anymore but even that they have the access to the network and the data that is being saved on the
network (Stojmenovic & Wen, 2014). This intrusion can also be made by the employees who are
not trustworthy.
Expectation of the customer’s security: This belongs to the category of the policy
compliance within the organization. The consumer’s perceptive for the security of data related to
their customer might be different from the security being availed by the Cloud service providers.
A Cloud service provider generally for maintaining the budget put the security of the data at sake
and manages the budget.
Loss Governance: this is the most likely happening issue related to the Cloud computing
adoption as there is not anymore control over the personal information that is being provided to
the service provider. After hiring the third party for managing the information and data, the
consumer completely relied on the service provider for any information. Service provider never
shows how they are going to manage the information security for the data and information that
they are collecting from the consumers (Khetri, 2013). This also leads to the unsure of the
location where the data is being saved. said that “there are many such cases in which the
implementation of Cloud computing results specific kind of compliance cannot be achieved for
example PCI DSS etc”.
risks for the consumers as the data related to the sensitive information goes into the wrong hands
and they have the access to manipulate, hamper, alter and expose the sensitive information.
Malicious insider: This is a very unusual risk but the impact is similar o the data breach
and this is mainly done for the revenge purpose. This intrusion can be made by the formal
employee of the organization or the stakeholders that have no relation with the organization
anymore but even that they have the access to the network and the data that is being saved on the
network (Stojmenovic & Wen, 2014). This intrusion can also be made by the employees who are
not trustworthy.
Expectation of the customer’s security: This belongs to the category of the policy
compliance within the organization. The consumer’s perceptive for the security of data related to
their customer might be different from the security being availed by the Cloud service providers.
A Cloud service provider generally for maintaining the budget put the security of the data at sake
and manages the budget.
Loss Governance: this is the most likely happening issue related to the Cloud computing
adoption as there is not anymore control over the personal information that is being provided to
the service provider. After hiring the third party for managing the information and data, the
consumer completely relied on the service provider for any information. Service provider never
shows how they are going to manage the information security for the data and information that
they are collecting from the consumers (Khetri, 2013). This also leads to the unsure of the
location where the data is being saved. said that “there are many such cases in which the
implementation of Cloud computing results specific kind of compliance cannot be achieved for
example PCI DSS etc”.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
Availability chain: This generally happens due to the network failure or slow internet
within the organization that create an unseen boundary for the customer to avail the services and
get access to their own information and data. This generally happens from the customer side due
to the use of low bandwidth internet.
Lock-in: As discussed above it is a challenge in adopting Cloud computing including that
the customer gets completely dependent on the service provider for the tools, application and
many more other programs or tools for accessing personal data or information. There are the
possibilities that the service provider is not able to provide all the services that had been
promised even that the customer would not be able to move on another vendor for the services
(Ryan, 2013). Thus this lead to the concern for the customer in availing the services will be
beneficial or not.
Threats, Assets, Vulnerabilities, and Risks Assessments
Cloud computing is no-doubt playing a very important role in enhancing the performance
of the organization with very minimal efforts and higher efficiency. Risk can be defined as the
combination of threats and vulnerabilities that have capability to affect the assets of the
organization. Following is table and based on this a severity matrix has been proposed next to
this table. This table describes the threats their impact and probability.
VH-Very high, H- High, M- Medium, L- Low, VL- Very low
Sl. No. Issues Description Likelihood Impact Priority
R. A Loss of
Governance
The involvement of third-party can be stated as
the basic need for the Cloud adoption and it
makes the consumers to be completely
VH VH VH
Availability chain: This generally happens due to the network failure or slow internet
within the organization that create an unseen boundary for the customer to avail the services and
get access to their own information and data. This generally happens from the customer side due
to the use of low bandwidth internet.
Lock-in: As discussed above it is a challenge in adopting Cloud computing including that
the customer gets completely dependent on the service provider for the tools, application and
many more other programs or tools for accessing personal data or information. There are the
possibilities that the service provider is not able to provide all the services that had been
promised even that the customer would not be able to move on another vendor for the services
(Ryan, 2013). Thus this lead to the concern for the customer in availing the services will be
beneficial or not.
Threats, Assets, Vulnerabilities, and Risks Assessments
Cloud computing is no-doubt playing a very important role in enhancing the performance
of the organization with very minimal efforts and higher efficiency. Risk can be defined as the
combination of threats and vulnerabilities that have capability to affect the assets of the
organization. Following is table and based on this a severity matrix has been proposed next to
this table. This table describes the threats their impact and probability.
VH-Very high, H- High, M- Medium, L- Low, VL- Very low
Sl. No. Issues Description Likelihood Impact Priority
R. A Loss of
Governance
The involvement of third-party can be stated as
the basic need for the Cloud adoption and it
makes the consumers to be completely
VH VH VH
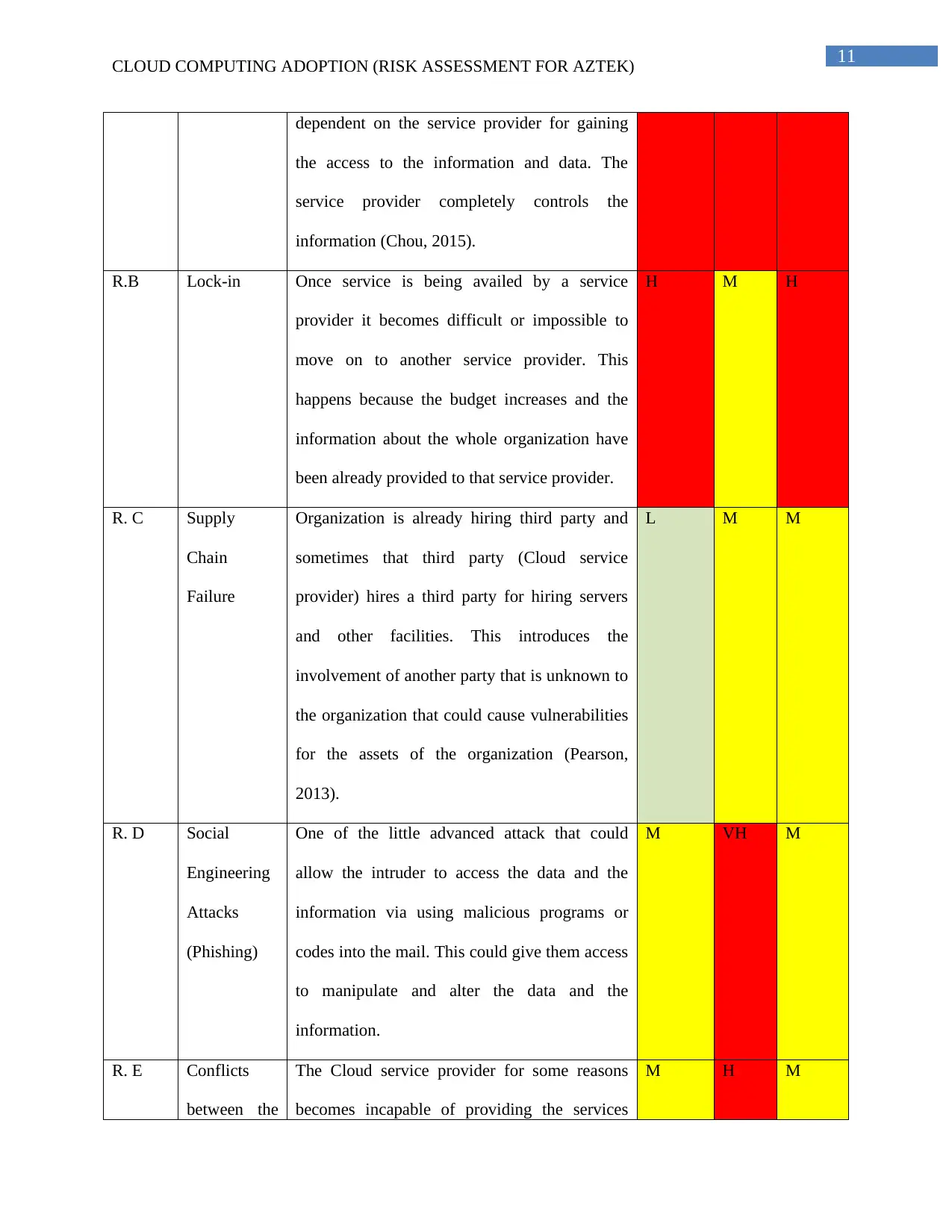
11CLOUD COMPUTING ADOPTION (RISK ASSESSMENT FOR AZTEK)
dependent on the service provider for gaining
the access to the information and data. The
service provider completely controls the
information (Chou, 2015).
R.B Lock-in Once service is being availed by a service
provider it becomes difficult or impossible to
move on to another service provider. This
happens because the budget increases and the
information about the whole organization have
been already provided to that service provider.
H M H
R. C Supply
Chain
Failure
Organization is already hiring third party and
sometimes that third party (Cloud service
provider) hires a third party for hiring servers
and other facilities. This introduces the
involvement of another party that is unknown to
the organization that could cause vulnerabilities
for the assets of the organization (Pearson,
2013).
L M M
R. D Social
Engineering
Attacks
(Phishing)
One of the little advanced attack that could
allow the intruder to access the data and the
information via using malicious programs or
codes into the mail. This could give them access
to manipulate and alter the data and the
information.
M VH M
R. E Conflicts
between the
The Cloud service provider for some reasons
becomes incapable of providing the services
M H M
dependent on the service provider for gaining
the access to the information and data. The
service provider completely controls the
information (Chou, 2015).
R.B Lock-in Once service is being availed by a service
provider it becomes difficult or impossible to
move on to another service provider. This
happens because the budget increases and the
information about the whole organization have
been already provided to that service provider.
H M H
R. C Supply
Chain
Failure
Organization is already hiring third party and
sometimes that third party (Cloud service
provider) hires a third party for hiring servers
and other facilities. This introduces the
involvement of another party that is unknown to
the organization that could cause vulnerabilities
for the assets of the organization (Pearson,
2013).
L M M
R. D Social
Engineering
Attacks
(Phishing)
One of the little advanced attack that could
allow the intruder to access the data and the
information via using malicious programs or
codes into the mail. This could give them access
to manipulate and alter the data and the
information.
M VH M
R. E Conflicts
between the
The Cloud service provider for some reasons
becomes incapable of providing the services
M H M
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





