Cloud Computing Security: A Comprehensive Review of Issues and Models
VerifiedAdded on 2022/05/09
|52
|11005
|22
Report
AI Summary
This report provides a comprehensive overview of cloud computing security, analyzing various aspects of cloud technology. It begins by defining cloud computing and its evolution, emphasizing the shift from traditional computing models. The report then delves into different cloud delivery models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), detailing their characteristics and functionalities. It also explores the different types of cloud deployment models, such as public, private, community, and hybrid clouds, discussing their respective advantages and disadvantages. A significant portion of the report is dedicated to a literature review, discussing key security issues and challenges in cloud computing. The report further examines the factors that contribute to secure cloud services, emphasizing the importance of robust security measures. Finally, the report concludes with a summary of the key findings and highlights the importance of ongoing research and improvements in cloud security architecture. The report includes tables and figures to illustrate different concepts, such as cloud delivery models, service delivery features, and cloud deployment models. The report is a valuable resource for understanding the complexities of cloud computing security and provides insights into ensuring the safety and security of cloud services.

ABSTRACT
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely.
In the cloud computing sphere, a myriad of varying sub-concepts have been
implemented over time; this however produced no alterations to the chief
notion upon which cloud computing is premised. The key concept of which
entails the presence of the cloud computing resources in the service
providers’ jurisdiction and control, which the cloud users or clients rent for use
for a certain time interval – often temporary, or in continuous stints.
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service model (PaaS).
As the scope of cloud computing – and the business world alike – is
broadening ever rapidly across many fields, research focus should be
directed towards creating improvements in the technologies and processes
utilized in cloud security architecture.
This review seeks to discuss the security issues associated with cloud
computing and also examine the factors that are valuable and relevant in
ensuring that cloud services are safe and secure for deployment and use.
Keywords: Cloud Computing, Cloud Security, Cloud delivery models,
architecture and deployment models
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely.
In the cloud computing sphere, a myriad of varying sub-concepts have been
implemented over time; this however produced no alterations to the chief
notion upon which cloud computing is premised. The key concept of which
entails the presence of the cloud computing resources in the service
providers’ jurisdiction and control, which the cloud users or clients rent for use
for a certain time interval – often temporary, or in continuous stints.
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service model (PaaS).
As the scope of cloud computing – and the business world alike – is
broadening ever rapidly across many fields, research focus should be
directed towards creating improvements in the technologies and processes
utilized in cloud security architecture.
This review seeks to discuss the security issues associated with cloud
computing and also examine the factors that are valuable and relevant in
ensuring that cloud services are safe and secure for deployment and use.
Keywords: Cloud Computing, Cloud Security, Cloud delivery models,
architecture and deployment models
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...............................................................................................3
TYPES OF CLOUD DELIVERY MODELS....................................................5
Infrastructure as a Service (IaaS)............................................................6
Platform as a Service (PaaS)...................................................................6
Software as a Service (SaaS)..................................................................7
TYPES OF CLOUD......................................................................................10
Public Cloud............................................................................................10
Private Cloud...........................................................................................11
Community cloud...................................................................................11
Hybrid Cloud...........................................................................................12
LITERATURE REVIEW..................................................................................18
DISCUSSION..................................................................................................32
CONCLUSION................................................................................................47
REFERENCES................................................................................................48
INTRODUCTION...............................................................................................3
TYPES OF CLOUD DELIVERY MODELS....................................................5
Infrastructure as a Service (IaaS)............................................................6
Platform as a Service (PaaS)...................................................................6
Software as a Service (SaaS)..................................................................7
TYPES OF CLOUD......................................................................................10
Public Cloud............................................................................................10
Private Cloud...........................................................................................11
Community cloud...................................................................................11
Hybrid Cloud...........................................................................................12
LITERATURE REVIEW..................................................................................18
DISCUSSION..................................................................................................32
CONCLUSION................................................................................................47
REFERENCES................................................................................................48

TABLE OF FIGURES
Figure 1. Types of Cloud Delivery Models....................................................9
Figure 2. Features of service delivery models...........................................10
Figure 3. Types of cloud deployment models............................................14
Figure 4. Service Level Agreement (SLA)..................................................16
Figure 5. Cloud Deployment Models with respect to Cloud Service
Requirements.................................................................................................40
Figure 6. How Authentication Works..........................................................47
Figure 1. Types of Cloud Delivery Models....................................................9
Figure 2. Features of service delivery models...........................................10
Figure 3. Types of cloud deployment models............................................14
Figure 4. Service Level Agreement (SLA)..................................................16
Figure 5. Cloud Deployment Models with respect to Cloud Service
Requirements.................................................................................................40
Figure 6. How Authentication Works..........................................................47
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely (Petre, 2012; Ogigau-Neamtiu, 2012;
Singh & jangwal, 2012).
Whatever processing to be carried out is done in a remote manner as well;
this alludes that it is imperative that the client submit their data to the cloud
server or infrastructure, in order for processing to be commenced upon it;
thereafter, the output is sent back, once the necessary processing is finalized.
In a number of scenarios, there is either a potentiality or prerequisite for the
user to store data on remote cloud servers. Arising from these, are delicate
cases that call for way-forwards to be devised strategically, within and around
the milieu of cloud computing operational activities. The cases in point are
underlisted thus: The transmission of clients’ individual credentials and
sensitive information to the server of the cloud; transmission of data from the
cloud infrastructure to the computing devices of the clients and as a
concluding procedure, the storage of the clients’ credentials and personal
Innovations brought into existence of recent in the cloud computing sphere
have caused a drastic evolution in the modus operandi of computing
processes together with the notion and concept of computing resources. As
observer from the norm, resources are, more often than not, present in the
jurisdiction of another entity’s network or premise, and cloud users could only
gain access to said resources remotely (Petre, 2012; Ogigau-Neamtiu, 2012;
Singh & jangwal, 2012).
Whatever processing to be carried out is done in a remote manner as well;
this alludes that it is imperative that the client submit their data to the cloud
server or infrastructure, in order for processing to be commenced upon it;
thereafter, the output is sent back, once the necessary processing is finalized.
In a number of scenarios, there is either a potentiality or prerequisite for the
user to store data on remote cloud servers. Arising from these, are delicate
cases that call for way-forwards to be devised strategically, within and around
the milieu of cloud computing operational activities. The cases in point are
underlisted thus: The transmission of clients’ individual credentials and
sensitive information to the server of the cloud; transmission of data from the
cloud infrastructure to the computing devices of the clients and as a
concluding procedure, the storage of the clients’ credentials and personal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information on the cloud servers, which exist as remote servers and implies
that the servers cannot be client-owned.
.
Each and every one of the three stages stated in the foregoing show a high
degree of susceptibility of sabotage in terms of security; to this end, it could
prove costly to downplay the significance of research and investigative
analysis when it comes to the security aspect of cloud computing. In the cloud
computing sphere, a myriad of varying sub-concepts have been implemented
over time; this however produced no alterations to the chief notion upon
which cloud computing is premised. The key concept of which entails the
presence of the cloud computing resources in the service providers’
jurisdiction and control, which the cloud users or clients rent for use for a
certain time interval – often temporary, or in continuous stints (Bisong &
Rahman, 2011; Rashmi, Sahoo & Mehfuz, 2013; Qaisar & Khawaja, 2012).
The stored precious data (on the remote cloud servers), in certain scenarios,
are required to be estimated, by counting. As long as the infringement upon
the privacy of clients’ computers by external parties is practicable, be it by
hacking or other illegitimate contrivance through which intruders grant
themselves unsolicited access to client personal data; uncertainties surface
with greater aplomb with regard to the security situation inasmuch as the
whole idea behind cloud computing and affiliated services were incited by a
that the servers cannot be client-owned.
.
Each and every one of the three stages stated in the foregoing show a high
degree of susceptibility of sabotage in terms of security; to this end, it could
prove costly to downplay the significance of research and investigative
analysis when it comes to the security aspect of cloud computing. In the cloud
computing sphere, a myriad of varying sub-concepts have been implemented
over time; this however produced no alterations to the chief notion upon
which cloud computing is premised. The key concept of which entails the
presence of the cloud computing resources in the service providers’
jurisdiction and control, which the cloud users or clients rent for use for a
certain time interval – often temporary, or in continuous stints (Bisong &
Rahman, 2011; Rashmi, Sahoo & Mehfuz, 2013; Qaisar & Khawaja, 2012).
The stored precious data (on the remote cloud servers), in certain scenarios,
are required to be estimated, by counting. As long as the infringement upon
the privacy of clients’ computers by external parties is practicable, be it by
hacking or other illegitimate contrivance through which intruders grant
themselves unsolicited access to client personal data; uncertainties surface
with greater aplomb with regard to the security situation inasmuch as the
whole idea behind cloud computing and affiliated services were incited by a

need to explore innovative avenues to access and have control over one’s
personal data.
Owing to the above, cloud computing activities have always had, and still
have quagmires with how security is handled in the sphere. In the computing
world, matters of security are always held preponderant.
The nature and methodology used in cloud computing makes it almost
impracticable for the broadness, and vastness of said ambit to be bridled, or
totally eliminated. A formidable system of security and safe infrastructure for
computing cannot be realized with a single, one off endeavor, as it demands
continuity; for this reason, it is of the essence to conduct proper analysis and
acknowledge advanced cloud computing security as a sine qua non. By the
operating standards of the cloud computing sphere, the cloud is segmented
into three groups/types, comprising of the public cloud, private cloud,
community cloud and hybrid cloud, as evidenced by a number of studies
(Ogigau-Neamtiu, 2012; Singh & Jangwal, 2012; Rashmi et al., 2013; Qaisar
& Khawaja, 2012; Kuyoro, Ibikunle & Awodele, 2011; Suresh & Prasad, 2012;
Youssef, 2012).
personal data.
Owing to the above, cloud computing activities have always had, and still
have quagmires with how security is handled in the sphere. In the computing
world, matters of security are always held preponderant.
The nature and methodology used in cloud computing makes it almost
impracticable for the broadness, and vastness of said ambit to be bridled, or
totally eliminated. A formidable system of security and safe infrastructure for
computing cannot be realized with a single, one off endeavor, as it demands
continuity; for this reason, it is of the essence to conduct proper analysis and
acknowledge advanced cloud computing security as a sine qua non. By the
operating standards of the cloud computing sphere, the cloud is segmented
into three groups/types, comprising of the public cloud, private cloud,
community cloud and hybrid cloud, as evidenced by a number of studies
(Ogigau-Neamtiu, 2012; Singh & Jangwal, 2012; Rashmi et al., 2013; Qaisar
& Khawaja, 2012; Kuyoro, Ibikunle & Awodele, 2011; Suresh & Prasad, 2012;
Youssef, 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TYPES OF CLOUD DELIVERY MODELS
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service models (PaaS).
Infrastructure as a Service (IaaS)
Here, in the Infrastructure as a Service model – abbreviated as IaaS –
computing resources used on the cloud, take processing power, data storage
and networks as instances, are made available in form of services. The cloud
services – virtualized and standardized, to a fault – are purchased by the
client, who then supplements the received service with services they already
have in possession, for use internally or externally. To explain this with an
instance, a cloud user could rent memory for operation, data storage as well
as server time, and in simultaneity with all of that, still run an operating
system using application programs they wish to.
Platform as a Service (PaaS)
In this service delivery model, the customer is availed infrastructure in its
entirety by the PaaS provider, who makes standardized interfaces which the
customer’s services would need to implement on the platform as well. The
platform could avail – for instance – scalability, multi-tenancy, access control,
and database accesses and the likes, as services. However, the client cannot
have direct access to the underlying strata, such as hardware or operating
The delivery models for the cloud computing architecture exist in three
subdivisions, including the Software as a service (SaaS), Infrastructure as a
service (IaaS) and the Platform as a service models (PaaS).
Infrastructure as a Service (IaaS)
Here, in the Infrastructure as a Service model – abbreviated as IaaS –
computing resources used on the cloud, take processing power, data storage
and networks as instances, are made available in form of services. The cloud
services – virtualized and standardized, to a fault – are purchased by the
client, who then supplements the received service with services they already
have in possession, for use internally or externally. To explain this with an
instance, a cloud user could rent memory for operation, data storage as well
as server time, and in simultaneity with all of that, still run an operating
system using application programs they wish to.
Platform as a Service (PaaS)
In this service delivery model, the customer is availed infrastructure in its
entirety by the PaaS provider, who makes standardized interfaces which the
customer’s services would need to implement on the platform as well. The
platform could avail – for instance – scalability, multi-tenancy, access control,
and database accesses and the likes, as services. However, the client cannot
have direct access to the underlying strata, such as hardware or operating
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

system; but it must be stated that application they opt for could be run on the
platform, for which the CSP would often provide its own tools.
Software as a Service (SaaS)
Here, as a software distribution model, the Software as a Service (SaaS)
model is characterized by application hosting by a service provider or vendor
and distributed to the clients across a network, typically the internet. As
underlying technologies compatible with web-based services and service
oriented (SOA) mature and unprecedented developmental approaches
continue to progress in popularity, so does the SaaS continue to become
more prevalent as delivery model by the day, in correspondence. What is
more, the Software as a Service model has, in many cases, been seen to be
affiliated with a pay-as-you-go subscription licensing model. On the other
hand, the rate at which broadband service is accessible to facilitate user
admittance proliferates and continues to reach more regions across the
globe. Many a time, the SaaS is applied in order to make provisions for the
functionality of business software, at lessened costs whilst, at the same time,
enabling the clients to reap whatever gains would have been gotten from
internally managed software with commercial license(s). The benefits would
be devoid of the complexities with which the management, support,
installation, high initial costs and licensing are originally accompanied. What
the concept of multi-tenancy alludes here, is the capacity of the SaaS’s
infrastructure to cater to a horde of users at the same point in time; it is
worthy of note that the infrastructure was specially fabricated to function in
platform, for which the CSP would often provide its own tools.
Software as a Service (SaaS)
Here, as a software distribution model, the Software as a Service (SaaS)
model is characterized by application hosting by a service provider or vendor
and distributed to the clients across a network, typically the internet. As
underlying technologies compatible with web-based services and service
oriented (SOA) mature and unprecedented developmental approaches
continue to progress in popularity, so does the SaaS continue to become
more prevalent as delivery model by the day, in correspondence. What is
more, the Software as a Service model has, in many cases, been seen to be
affiliated with a pay-as-you-go subscription licensing model. On the other
hand, the rate at which broadband service is accessible to facilitate user
admittance proliferates and continues to reach more regions across the
globe. Many a time, the SaaS is applied in order to make provisions for the
functionality of business software, at lessened costs whilst, at the same time,
enabling the clients to reap whatever gains would have been gotten from
internally managed software with commercial license(s). The benefits would
be devoid of the complexities with which the management, support,
installation, high initial costs and licensing are originally accompanied. What
the concept of multi-tenancy alludes here, is the capacity of the SaaS’s
infrastructure to cater to a horde of users at the same point in time; it is
worthy of note that the infrastructure was specially fabricated to function in
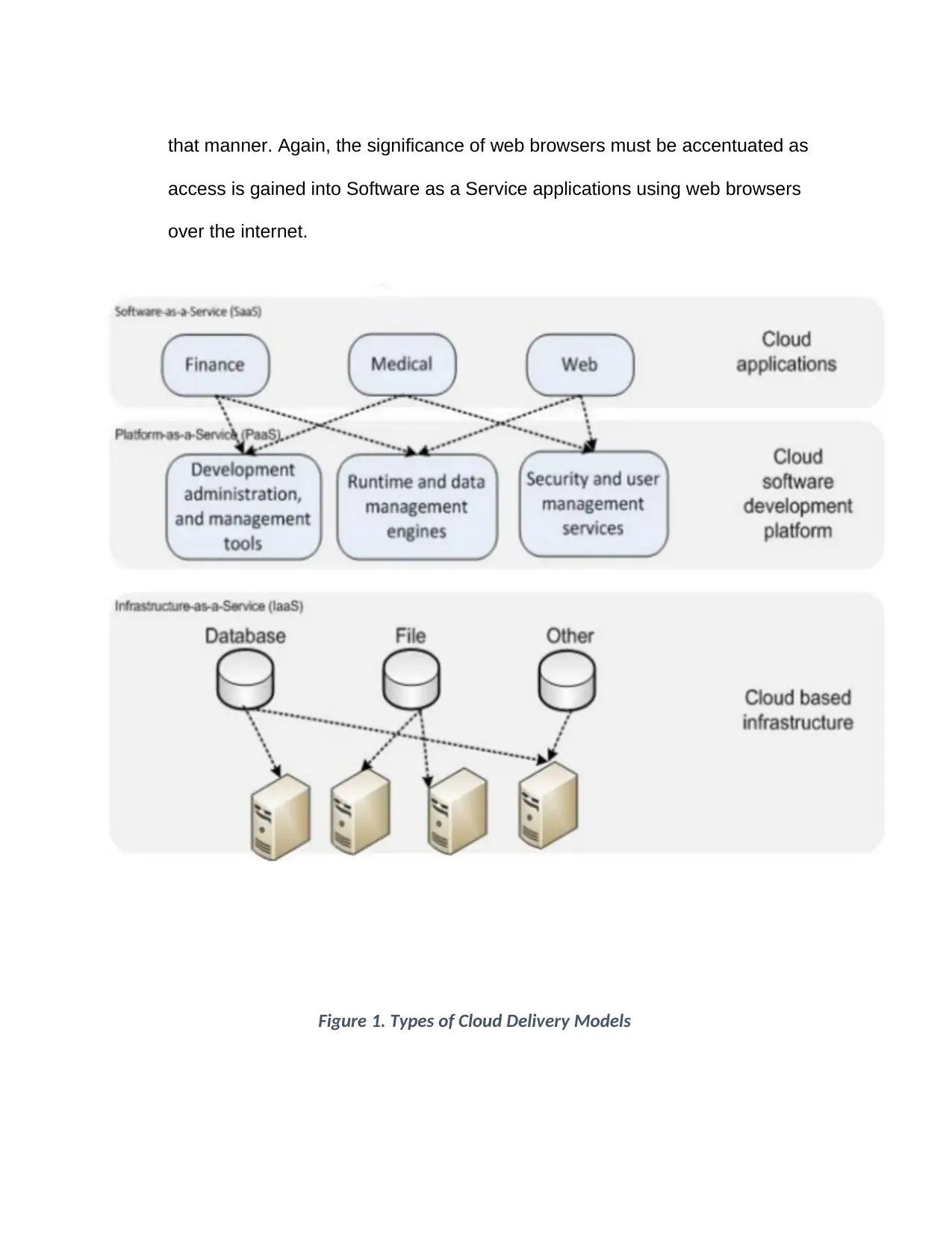
that manner. Again, the significance of web browsers must be accentuated as
access is gained into Software as a Service applications using web browsers
over the internet.
Figure 1. Types of Cloud Delivery Models
access is gained into Software as a Service applications using web browsers
over the internet.
Figure 1. Types of Cloud Delivery Models
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
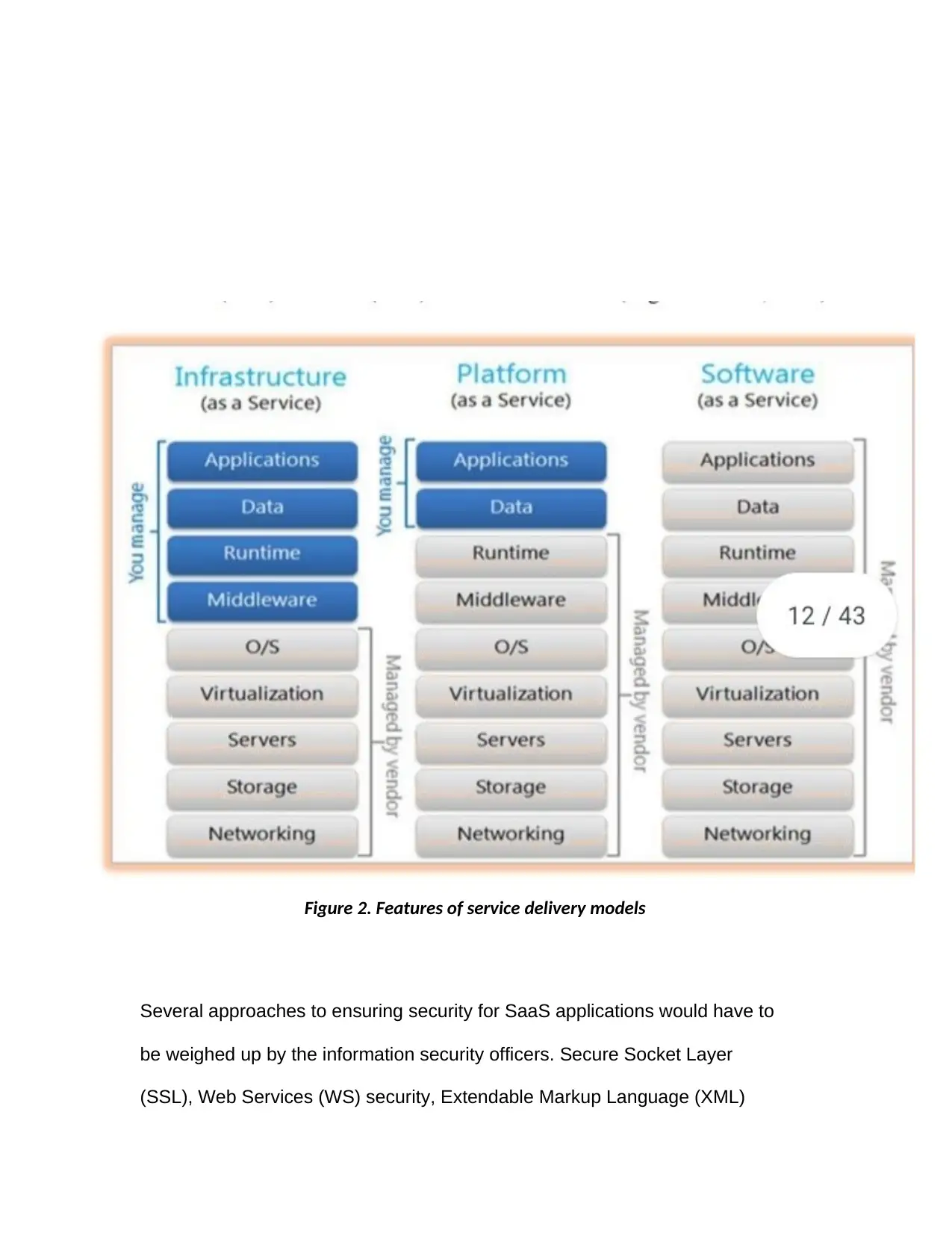
Several approaches to ensuring security for SaaS applications would have to
be weighed up by the information security officers. Secure Socket Layer
(SSL), Web Services (WS) security, Extendable Markup Language (XML)
Figure 2. Features of service delivery models
be weighed up by the information security officers. Secure Socket Layer
(SSL), Web Services (WS) security, Extendable Markup Language (XML)
Figure 2. Features of service delivery models
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

encryption and a vast array of alternatives available are used to protect data,
and create a secure network through which information is transmitted within
and about the internet, as stated by Subashini and Kavitha (2011). .
In every interface where it is necessary, the service providers for cloud
services, as well as the clients have to maintain security in the cloud
computing field.
TYPES OF CLOUD
On the basis of discrepancies as to the entity that gets admittance to the
services, who is in control of the infrastructure, the location of the
infrastructure and the manner with which it is made available; fundamentally,
there exist four deployment models for cloud computing (Woolley & Fletcher,
2009).
The elements listed in the foregoing possess separate, distinct properties,
that exert an influence on chances and uncertainties with which each and
every cloud development model is connected.
and create a secure network through which information is transmitted within
and about the internet, as stated by Subashini and Kavitha (2011). .
In every interface where it is necessary, the service providers for cloud
services, as well as the clients have to maintain security in the cloud
computing field.
TYPES OF CLOUD
On the basis of discrepancies as to the entity that gets admittance to the
services, who is in control of the infrastructure, the location of the
infrastructure and the manner with which it is made available; fundamentally,
there exist four deployment models for cloud computing (Woolley & Fletcher,
2009).
The elements listed in the foregoing possess separate, distinct properties,
that exert an influence on chances and uncertainties with which each and
every cloud development model is connected.

Public Cloud
Fundamentally, the major benefit of public cloud deployment model lies in its
capacity to offer cost efficiency to the user on the basis of management
overheads and capital expenditure. However, it is not without its downsides
as it also has risks affiliated with latency, performance, location and
ownership of data, data security and privacy attached to it as cons.
The infrastructure of this cloud is run solely for an organization. It could either
be superintended by the organization itself, or by a third party and may exist
and operate in an off-premise or on-premise form.
Private Cloud
Here, whether internal or third-party resources oriented, in the private cloud
deployment model, the control over organizational or personal information is
amplified; also, checks ingrained in architecture of this model cause a large
portion of the risks associated with the foregoing cloud deployment model to
be put in place, thus proffering solutions to the conundrums brought into
existence by said demerits.
It should be stated however, that the trade-offs come with greater costs for
renting or procuring sites, as well as managing the infrastructure upon which
the cloud runs (Kraska, 2010). In a similar manner with the model discussed
afore, the cloud infrastructure is run solely for an organization; it may be
presided over by the organization or a third party and has the capacity to run
either off-premise or on-premise.
Fundamentally, the major benefit of public cloud deployment model lies in its
capacity to offer cost efficiency to the user on the basis of management
overheads and capital expenditure. However, it is not without its downsides
as it also has risks affiliated with latency, performance, location and
ownership of data, data security and privacy attached to it as cons.
The infrastructure of this cloud is run solely for an organization. It could either
be superintended by the organization itself, or by a third party and may exist
and operate in an off-premise or on-premise form.
Private Cloud
Here, whether internal or third-party resources oriented, in the private cloud
deployment model, the control over organizational or personal information is
amplified; also, checks ingrained in architecture of this model cause a large
portion of the risks associated with the foregoing cloud deployment model to
be put in place, thus proffering solutions to the conundrums brought into
existence by said demerits.
It should be stated however, that the trade-offs come with greater costs for
renting or procuring sites, as well as managing the infrastructure upon which
the cloud runs (Kraska, 2010). In a similar manner with the model discussed
afore, the cloud infrastructure is run solely for an organization; it may be
presided over by the organization or a third party and has the capacity to run
either off-premise or on-premise.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 52
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



