A Detailed Study of Security and Privacy Issues in Cloud Computing
VerifiedAdded on 2020/10/01
|22
|7085
|56
Report
AI Summary
This report offers a comprehensive analysis of cloud computing security and privacy, addressing critical issues such as data protection, access control, and various security threats. It begins with an abstract and introduction, highlighting the rising popularity of cloud computing and the associated security concerns. The report delves into the problem domain, identifying privacy, compliance, and trust as major challenges. It then provides a detailed review of related work, covering topics like privacy protection frameworks, access control mechanisms, and attribute-based encryption. The core of the report examines specific security and privacy issues across different cloud service models (SaaS, PaaS, IaaS), along with experimental analysis and a conclusion summarizing key findings. The report emphasizes the importance of addressing these security concerns to ensure the widespread adoption of cloud computing, providing insights into existing solutions and potential countermeasures to mitigate risks. It also includes a synopsis and a list of references for further reading.

Table of Contents
ABSTRACT....................................................................................................................................................2
INTRODUCTION...........................................................................................................................................2
PROBLEM DOMAIN......................................................................................................................................2
BACKGROUND/RELATED WORK..................................................................................................................3
1. Privacy Protection and Data Security in Cloud Computing: A Survey, Challenges, and Solutions....3
2. A Study and Survey of Security and Privacy Issues in Cloud Computing..........................................5
3. Database Security in Cloud..............................................................................................................7
4. Identity and Access Management in Cloud Environment: Mechanisms and Challenges.................9
5. Service Delivery Models of Cloud Computing: Security Issues and Open Challenges....................10
6. Cloud Computing Security and Privacy: An Empirical Study..........................................................11
7. Security and Privacy of Sensitive Data in Cloud Computing: A Survey of Recent Developments...12
8. SEPRICC: Security and Privacy in Cloud Computing.......................................................................13
9. Layers of Cloud – IaaS, PaaS and SaaS: A Survey............................................................................14
10. Challenges and Prosperity Research in Cloud Computing..............................................................14
11. Cloud Computing Service Models: A Comparative Study...............................................................15
12. A Review Paper on Cloud Computing............................................................................................16
EXPERIMENTAL ANALYSIS:.........................................................................................................................17
CONCLUSION.............................................................................................................................................20
SYNOPSIS...................................................................................................................................................20
Aim of the Project..................................................................................................................................20
Method..................................................................................................................................................20
Results...................................................................................................................................................20
Discussion..............................................................................................................................................21
Conclusion.............................................................................................................................................21
REFERENCES..............................................................................................................................................21
1
ABSTRACT....................................................................................................................................................2
INTRODUCTION...........................................................................................................................................2
PROBLEM DOMAIN......................................................................................................................................2
BACKGROUND/RELATED WORK..................................................................................................................3
1. Privacy Protection and Data Security in Cloud Computing: A Survey, Challenges, and Solutions....3
2. A Study and Survey of Security and Privacy Issues in Cloud Computing..........................................5
3. Database Security in Cloud..............................................................................................................7
4. Identity and Access Management in Cloud Environment: Mechanisms and Challenges.................9
5. Service Delivery Models of Cloud Computing: Security Issues and Open Challenges....................10
6. Cloud Computing Security and Privacy: An Empirical Study..........................................................11
7. Security and Privacy of Sensitive Data in Cloud Computing: A Survey of Recent Developments...12
8. SEPRICC: Security and Privacy in Cloud Computing.......................................................................13
9. Layers of Cloud – IaaS, PaaS and SaaS: A Survey............................................................................14
10. Challenges and Prosperity Research in Cloud Computing..............................................................14
11. Cloud Computing Service Models: A Comparative Study...............................................................15
12. A Review Paper on Cloud Computing............................................................................................16
EXPERIMENTAL ANALYSIS:.........................................................................................................................17
CONCLUSION.............................................................................................................................................20
SYNOPSIS...................................................................................................................................................20
Aim of the Project..................................................................................................................................20
Method..................................................................................................................................................20
Results...................................................................................................................................................20
Discussion..............................................................................................................................................21
Conclusion.............................................................................................................................................21
REFERENCES..............................................................................................................................................21
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ABSTRACT: With the recent advancements, the technology of cloud computing has also gaining rise
in terms of popularity and success. Cloud computing is a rising technology standard which relocates
recent technological as well as concept of computing into solutions like utility familiar to water systems
and electricity. Cloud computing is providing huge amount of advantages which includes economic
saving, service flexibility and configurable computer resources. Although with this increasing popularity
of cloud computing carries some critical security and privacy issues due to the outsourcing of business
applications and data to third party. The concerns related to security and privacy are seems to be initial
hurdle in the adoption of cloud in vast amount. Cloud introduces some advance concepts like resource
sharing, multi tenancy and outsourcing comes along with new challenges in the security community.
Hence the goal of this study is to address the recent existing security and privacy issues in cloud
environment. Additionally the capability to pursue and adapt the measures of security that was developed
for traditional computing systems, initiating new security policies, models and protocols for addressing
distinct security challenges of cloud. We present a comprehensive study about cloud computing and its
related security and privacy concerns.
INTRODUCTION: Cloud computer constitutes as an advance firm in the field of information
technology and related to the virtualization of the available resources of computer on request. Cloud
computing liberates times as well as cost for businesses. Along with that the process of computing
contemplates revolutionary advancement in technology related to how companies are constructs,
organizes and deployed enterprise applications on the internet. Those clouds computing that are
virtualized specifically provides delivery models of cloud computing i.e. software as a service, platform
as a service and infrastructure as a service. However in recent times, the issues regarding security and
privacy in cloud computing considered as a serious component in the any model adaptation of cloud
service delivery. Cloud computing support few technologies in its process hence this model somehow
includes possible security hazards. Hence so far, the security issues in cloud computing have hardly
receive at service delivery level. Some specific security concerns are network security, integrations, web
application security, vulnerabilities presents in virtualized environment, physical security and data
security. The goal of this research is to provide a comprehensive study of security threats regarding to
their respected cloud service deliver model. We also characterized five most specific security and privacy
aspects such as confidentiality, integrity, accountability, availability and privacy preservability. Our main
aim behind this research is to comprehensively present the security threats with respect to their cloud
service deliver models. This study also determines how service delivery models differ from existing
enterprise applications, classify these models, and investigate the inherent security challenges. This study
primarily focuses on the security concerns of each layer of the cloud-service delivery model, as well as on
existing solutions and approaches. In addition, countermeasures to potential security threats are also
presented for each cloud model.
PROBLEM DOMAIN: From previous years, cloud computing is considered as an important
platform from the perspective of hosting and delivering services through the internet. It gained popularity
by providing several computing services like cloud hosting, cloud storage and cloud servers etc. in order
to assist multiple kind businesses as well as in academics [2]. But it suffers from few major security and
privacy challenges. Privacy is cloud an important aspect for the customers. If we consider privacy in
cloud there are many threats for sensitive data of users over the cloud storage. Although the structure of
2
in terms of popularity and success. Cloud computing is a rising technology standard which relocates
recent technological as well as concept of computing into solutions like utility familiar to water systems
and electricity. Cloud computing is providing huge amount of advantages which includes economic
saving, service flexibility and configurable computer resources. Although with this increasing popularity
of cloud computing carries some critical security and privacy issues due to the outsourcing of business
applications and data to third party. The concerns related to security and privacy are seems to be initial
hurdle in the adoption of cloud in vast amount. Cloud introduces some advance concepts like resource
sharing, multi tenancy and outsourcing comes along with new challenges in the security community.
Hence the goal of this study is to address the recent existing security and privacy issues in cloud
environment. Additionally the capability to pursue and adapt the measures of security that was developed
for traditional computing systems, initiating new security policies, models and protocols for addressing
distinct security challenges of cloud. We present a comprehensive study about cloud computing and its
related security and privacy concerns.
INTRODUCTION: Cloud computer constitutes as an advance firm in the field of information
technology and related to the virtualization of the available resources of computer on request. Cloud
computing liberates times as well as cost for businesses. Along with that the process of computing
contemplates revolutionary advancement in technology related to how companies are constructs,
organizes and deployed enterprise applications on the internet. Those clouds computing that are
virtualized specifically provides delivery models of cloud computing i.e. software as a service, platform
as a service and infrastructure as a service. However in recent times, the issues regarding security and
privacy in cloud computing considered as a serious component in the any model adaptation of cloud
service delivery. Cloud computing support few technologies in its process hence this model somehow
includes possible security hazards. Hence so far, the security issues in cloud computing have hardly
receive at service delivery level. Some specific security concerns are network security, integrations, web
application security, vulnerabilities presents in virtualized environment, physical security and data
security. The goal of this research is to provide a comprehensive study of security threats regarding to
their respected cloud service deliver model. We also characterized five most specific security and privacy
aspects such as confidentiality, integrity, accountability, availability and privacy preservability. Our main
aim behind this research is to comprehensively present the security threats with respect to their cloud
service deliver models. This study also determines how service delivery models differ from existing
enterprise applications, classify these models, and investigate the inherent security challenges. This study
primarily focuses on the security concerns of each layer of the cloud-service delivery model, as well as on
existing solutions and approaches. In addition, countermeasures to potential security threats are also
presented for each cloud model.
PROBLEM DOMAIN: From previous years, cloud computing is considered as an important
platform from the perspective of hosting and delivering services through the internet. It gained popularity
by providing several computing services like cloud hosting, cloud storage and cloud servers etc. in order
to assist multiple kind businesses as well as in academics [2]. But it suffers from few major security and
privacy challenges. Privacy is cloud an important aspect for the customers. If we consider privacy in
cloud there are many threats for sensitive data of users over the cloud storage. Although the structure of
2

cloud computing is getting advance and progressing fast conceptually as well as in reality. But service
quality, security and privacy, economic, contractual issues still remains crucial challenges.
After reviewing several research articles, we conclude that they somehow interlinked over these familiar
categories:
Issues of privacy, compliance, trust, legal and audit in cloud.
Vulnerabilities and threats present in cloud.
Challenges faced by organizations while adopting cloud solution
Recommendations and solutions for cloud security issues and concerns
BACKGROUND/RELATED WORK:
1. Privacy Protection and Data Security in Cloud Computing: A Survey,
Challenges, and Solutions
Privacy and security related issues are very critical with regards to cloud computing. There are many
current research schemes carries out related to access control based cloud computing privacy
protection, trust and reputation and Attribute Based Encryption (ABE). Along with that it also discusses
KP-ABE i.e. Key Policy Attribute Based Encryption, CP i.e. Ciphertext Policy Attribute Based Encryption ,
revocation, mechanism, fine grain, trace mechanism, access structure, multi authority, proxy re-
encryption, reputation, trust, searchable encryption, hierarchical encryption, hierarchical key and
extension of tradition access control . Still they are dissipate or had insufficient unified logic. This paper
reviewed and identified progressive researches related to these factors and concludes the result on the
basis of its characterization.
1. Access control based Mechanism
2. Trust and Reputation of cloud computing
3. Attribute Based Encryption
CLOUD COMPUTING PRIVACY PROTECTION FRAMEWORK
Privacy data of user is confidential in cloud computing. Although the presence of virtualization, big data,
multi-tenancy, data outsourcing storage and some other technologies hence generate the risk of privacy
disclosure of user’s data (Sun, 2019).
3
quality, security and privacy, economic, contractual issues still remains crucial challenges.
After reviewing several research articles, we conclude that they somehow interlinked over these familiar
categories:
Issues of privacy, compliance, trust, legal and audit in cloud.
Vulnerabilities and threats present in cloud.
Challenges faced by organizations while adopting cloud solution
Recommendations and solutions for cloud security issues and concerns
BACKGROUND/RELATED WORK:
1. Privacy Protection and Data Security in Cloud Computing: A Survey,
Challenges, and Solutions
Privacy and security related issues are very critical with regards to cloud computing. There are many
current research schemes carries out related to access control based cloud computing privacy
protection, trust and reputation and Attribute Based Encryption (ABE). Along with that it also discusses
KP-ABE i.e. Key Policy Attribute Based Encryption, CP i.e. Ciphertext Policy Attribute Based Encryption ,
revocation, mechanism, fine grain, trace mechanism, access structure, multi authority, proxy re-
encryption, reputation, trust, searchable encryption, hierarchical encryption, hierarchical key and
extension of tradition access control . Still they are dissipate or had insufficient unified logic. This paper
reviewed and identified progressive researches related to these factors and concludes the result on the
basis of its characterization.
1. Access control based Mechanism
2. Trust and Reputation of cloud computing
3. Attribute Based Encryption
CLOUD COMPUTING PRIVACY PROTECTION FRAMEWORK
Privacy data of user is confidential in cloud computing. Although the presence of virtualization, big data,
multi-tenancy, data outsourcing storage and some other technologies hence generate the risk of privacy
disclosure of user’s data (Sun, 2019).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
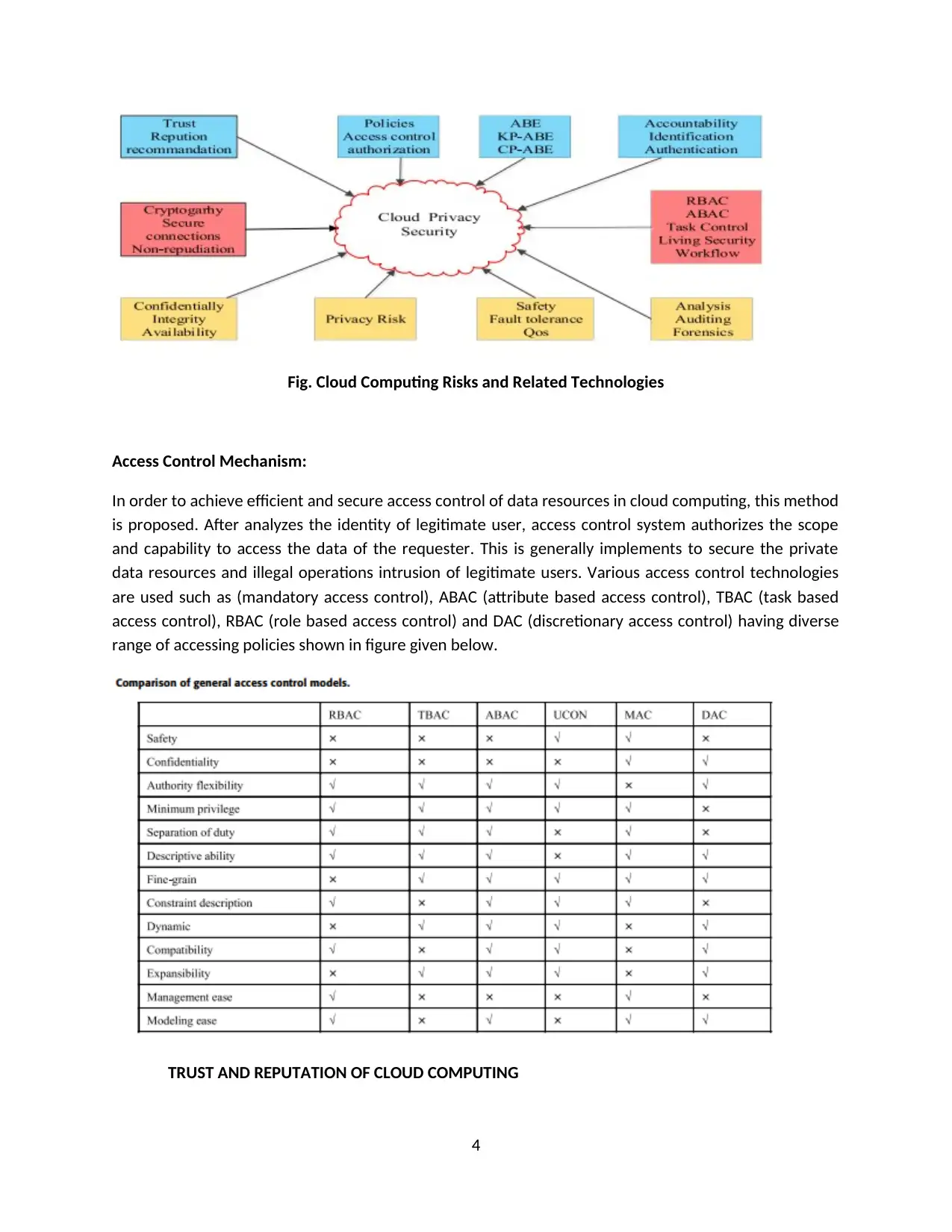
Fig. Cloud Computing Risks and Related Technologies
Access Control Mechanism:
In order to achieve efficient and secure access control of data resources in cloud computing, this method
is proposed. After analyzes the identity of legitimate user, access control system authorizes the scope
and capability to access the data of the requester. This is generally implements to secure the private
data resources and illegal operations intrusion of legitimate users. Various access control technologies
are used such as (mandatory access control), ABAC (attribute based access control), TBAC (task based
access control), RBAC (role based access control) and DAC (discretionary access control) having diverse
range of accessing policies shown in figure given below.
TRUST AND REPUTATION OF CLOUD COMPUTING
4
Access Control Mechanism:
In order to achieve efficient and secure access control of data resources in cloud computing, this method
is proposed. After analyzes the identity of legitimate user, access control system authorizes the scope
and capability to access the data of the requester. This is generally implements to secure the private
data resources and illegal operations intrusion of legitimate users. Various access control technologies
are used such as (mandatory access control), ABAC (attribute based access control), TBAC (task based
access control), RBAC (role based access control) and DAC (discretionary access control) having diverse
range of accessing policies shown in figure given below.
TRUST AND REPUTATION OF CLOUD COMPUTING
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Trust and Reputation TR are very crucial to consider for the adaptation of cloud service and are
firmly relatable to privacy protection. Cloud computing system needs trust of user and
reputation concerning to information to be entirely disclosed that will introduce undiscovered
privacy risks of users. Lately different compounds of multiple methods give a nearly optimal
solution for the management of TR in privacy protection of cloud computing services.
ABE OF CLOUD COMPUTING
ABE related to public key mechanism. The object is decryption of a group instead of a single
user. Its essential feature is the origination of attribute concept. This group is related to those
users that belong to specific fusion of attribute values. ABE introduces advantages in cloud
computing. ABE is preferable for architecture of cloud computing. Additionally it also provides
the ability to entirely implements data access control in the platform of cloud. Researches has
shown significant progress like attribute revocation, proxy re-encryption, multi-authority,
hierarchical encryption, policy flexibility etc. Still there are multiple issues that require further
research [10].
Fig. Comparison of several access control model-based encryption
2. A Study and Survey of Security and Privacy Issues in Cloud Computing
Cloud computing is an emerging model which transforms the information technological ways of
individuals as well as the organizations. It involves some significant aspects like broad network,
rapid elasticity, resource pooling board network access and characterizes services that help the
organization in converting to agile. Characteristics of cloud are related to few open issues such
as scalability, availability, interoperability and security. The security and privacy problems
generally come along with cloud deployment, delivery models are main source behind these
issues in current cloud computing world. This paper discusses security and privacy issues
addressed between the development and delivery.
Cloud computing becomes a fragment of business strategies universally now. Cloud adoption is
now become a part of business strategies globally. All sectors of enterprises, research institutes,
financial institutes, government agencies and education sectors are adopting cloud computing.
Latest advance technologies such as social media, big data analysis and mobility are basic reason
behind the enforcement of cloud computing in organizations. Few popular cloud providers are
Salesforce.com, Amazon’s EC2 (Elastic Compute Cloud), Google’s suite of apps (Google Docs,
Google Calendar and Gmail etc), IBM blue cloud, Microsoft’s Azure etc. Along with many
advantages cloud computing involves issues regarding privacy and security of users. Even after
many years of cloud existence it still requires adequate trust level in terms of requirements of
security and privacy (Ahmad, 2017)
5
firmly relatable to privacy protection. Cloud computing system needs trust of user and
reputation concerning to information to be entirely disclosed that will introduce undiscovered
privacy risks of users. Lately different compounds of multiple methods give a nearly optimal
solution for the management of TR in privacy protection of cloud computing services.
ABE OF CLOUD COMPUTING
ABE related to public key mechanism. The object is decryption of a group instead of a single
user. Its essential feature is the origination of attribute concept. This group is related to those
users that belong to specific fusion of attribute values. ABE introduces advantages in cloud
computing. ABE is preferable for architecture of cloud computing. Additionally it also provides
the ability to entirely implements data access control in the platform of cloud. Researches has
shown significant progress like attribute revocation, proxy re-encryption, multi-authority,
hierarchical encryption, policy flexibility etc. Still there are multiple issues that require further
research [10].
Fig. Comparison of several access control model-based encryption
2. A Study and Survey of Security and Privacy Issues in Cloud Computing
Cloud computing is an emerging model which transforms the information technological ways of
individuals as well as the organizations. It involves some significant aspects like broad network,
rapid elasticity, resource pooling board network access and characterizes services that help the
organization in converting to agile. Characteristics of cloud are related to few open issues such
as scalability, availability, interoperability and security. The security and privacy problems
generally come along with cloud deployment, delivery models are main source behind these
issues in current cloud computing world. This paper discusses security and privacy issues
addressed between the development and delivery.
Cloud computing becomes a fragment of business strategies universally now. Cloud adoption is
now become a part of business strategies globally. All sectors of enterprises, research institutes,
financial institutes, government agencies and education sectors are adopting cloud computing.
Latest advance technologies such as social media, big data analysis and mobility are basic reason
behind the enforcement of cloud computing in organizations. Few popular cloud providers are
Salesforce.com, Amazon’s EC2 (Elastic Compute Cloud), Google’s suite of apps (Google Docs,
Google Calendar and Gmail etc), IBM blue cloud, Microsoft’s Azure etc. Along with many
advantages cloud computing involves issues regarding privacy and security of users. Even after
many years of cloud existence it still requires adequate trust level in terms of requirements of
security and privacy (Ahmad, 2017)
5
SaaS: SaaS provides service to multiple consumers by distributing its separate data and
sessions. SaaS provides user the ability the access the application from any location as per
demand and utilize it by web browser on many operating systems.
PaaS: PaaS provides the ability to application developers and design applications based on
cloud by implementing programming languages, class libraries and tools that are used to
support cloud provider. PaaS provides consumers the ability to construct high scalable cloud
applications that are efficient enough to support huge amount of end users. The scalability
and elasticity are transparently provided by cloud infrastructure.
IaaS: IaaS gives the ability to consumers for hiring IT resources like storage capacity,
network bandwidth and computer systems from the provider of cloud service. The provider
is also responsible for managed and deployed the underlying cloud infrastructure. Software
like operating systems, applications and databases are configured and deployed by
consumers over cloud resources.
Hybrid Cloud
Hybrid cloud joins two or more separate clouds. This combination may involves private,
public or community cloud. There are several feasible compositions of hybrid clouds. It has
diverse propertied regarding to parameters like security, cost, performance etc. Component
clouds are joined by using open or exclusive technology In Hybrid cloud environment, like
6
sessions. SaaS provides user the ability the access the application from any location as per
demand and utilize it by web browser on many operating systems.
PaaS: PaaS provides the ability to application developers and design applications based on
cloud by implementing programming languages, class libraries and tools that are used to
support cloud provider. PaaS provides consumers the ability to construct high scalable cloud
applications that are efficient enough to support huge amount of end users. The scalability
and elasticity are transparently provided by cloud infrastructure.
IaaS: IaaS gives the ability to consumers for hiring IT resources like storage capacity,
network bandwidth and computer systems from the provider of cloud service. The provider
is also responsible for managed and deployed the underlying cloud infrastructure. Software
like operating systems, applications and databases are configured and deployed by
consumers over cloud resources.
Hybrid Cloud
Hybrid cloud joins two or more separate clouds. This combination may involves private,
public or community cloud. There are several feasible compositions of hybrid clouds. It has
diverse propertied regarding to parameters like security, cost, performance etc. Component
clouds are joined by using open or exclusive technology In Hybrid cloud environment, like
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

protocols, architectures, application programming interfaces (APIs) and data formats etc.
Portability of data and applications is possible by the combination of diverse technologies.
3. Database Security in Cloud
Database migration towards cloud environment introduces multiple security concerns that are
required to be considered by organization because its an organization’s utmost responsibility
for the security assurance of data instead of the providers. The users should assured about the
implementation of proper security measurements encompasses with data integrity, availability
and confidentiality in the location before migrating their internal database having sensitive
data towards the cloud. Some major factors of database security in cloud are data requires to be
secured enough either its in rest, in use, accessing or transmits should be control [8].
Some main challenges of security that are faced by cloud databases are as follows:
1. Availability: It can be define as the extent to which the resources of system are usable and
accessible by its users and organizations. Its is a serious security factor that organizations
required to take into account while the consideration of cloud database services. The affect
7
Portability of data and applications is possible by the combination of diverse technologies.
3. Database Security in Cloud
Database migration towards cloud environment introduces multiple security concerns that are
required to be considered by organization because its an organization’s utmost responsibility
for the security assurance of data instead of the providers. The users should assured about the
implementation of proper security measurements encompasses with data integrity, availability
and confidentiality in the location before migrating their internal database having sensitive
data towards the cloud. Some major factors of database security in cloud are data requires to be
secured enough either its in rest, in use, accessing or transmits should be control [8].
Some main challenges of security that are faced by cloud databases are as follows:
1. Availability: It can be define as the extent to which the resources of system are usable and
accessible by its users and organizations. Its is a serious security factor that organizations
required to take into account while the consideration of cloud database services. The affect
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

of availability failure can be permanent or temporary and the loss can also be fully or
partially. There are multiple threats to availability such equipment failure, Dos attack or
nature disasters etc. Mostly the downtime is not planned which leads to some serious effect
on the daily routine of organization. Databases does not need availability of 100% still
specific applications suffers much incase of unavailability of database for unmeasured time
period. Services of cloud computing are designed to give reliability, high availability and
suffers unplanned outages instead of having infrastructure.
2. Access control issues in public cloud: Access control is considered as one of the major
security threat in cloud environment. The outsourcing of sensitive data of to cloud
providers leads to the lose of logical, physical and personnel control on it and it introduces
inbuilt risk of security. Inspite of the fact that external threats are a huge concern still
from the recent studies it proves that mostly threats related to access control doesn’t only
comes from internal employee of organizations but also from cloud service provider
employees. Hence proper monitoring and access control procedures for administrators of
cloud database are very crucial in terms of ensuring sensitive data security. Background
checks are generally perform by organizations over privilege user prior to recruiting them
and along with that apply continuous physical monitoring through security cameras or
security personnel in order to protect sensitive data of their onsite databases
3. Monitoring and auditing issues: Even though flexibility and elasticity is contemplate
among vital advantages that cloud computing offers but along with that it introduces
some inherent security isses with it. Databases of cloud scale up and down rapidly in
order to meet the needs of customers, it means that those physical servers that host
databases are provisioned and de provisioned frequently without any earlier knowledge
of consumers. Additionally for achieving high availability and redundancy, the data of
consumers is replicated around many data centers in various locations. These factors lead
to non static environment which have almost no accessibility and visibility to physical
infrastructure of consumers.
4. Data Sanitization: It is another kind of risk related to the physical security is the deletion
of data from storage devices is known as data sanitization. Sanitization of data includes
degaussing, removing data from storage media through overwriting or demotion of data
itself in order to prevent it from unauthorized information disclosure. Additionally
complications increases due to the backups that carried out in cloud environment
regularly in order to ensure high redundancy. There are various examples where
researchers brought utilized drive from online auction in order to retrieve huge amount of
sensitive data from it. Incase data doesn’t removed properly this data can be recovered
later from failed drives by using proper equipments. Hence it is crucial that SLA s should
clear that whether clod providers give enough measurements in order to ensure that data
sanitization is appropriately performs in the entire lifecycle of the system (Sakhi,2012).
8
partially. There are multiple threats to availability such equipment failure, Dos attack or
nature disasters etc. Mostly the downtime is not planned which leads to some serious effect
on the daily routine of organization. Databases does not need availability of 100% still
specific applications suffers much incase of unavailability of database for unmeasured time
period. Services of cloud computing are designed to give reliability, high availability and
suffers unplanned outages instead of having infrastructure.
2. Access control issues in public cloud: Access control is considered as one of the major
security threat in cloud environment. The outsourcing of sensitive data of to cloud
providers leads to the lose of logical, physical and personnel control on it and it introduces
inbuilt risk of security. Inspite of the fact that external threats are a huge concern still
from the recent studies it proves that mostly threats related to access control doesn’t only
comes from internal employee of organizations but also from cloud service provider
employees. Hence proper monitoring and access control procedures for administrators of
cloud database are very crucial in terms of ensuring sensitive data security. Background
checks are generally perform by organizations over privilege user prior to recruiting them
and along with that apply continuous physical monitoring through security cameras or
security personnel in order to protect sensitive data of their onsite databases
3. Monitoring and auditing issues: Even though flexibility and elasticity is contemplate
among vital advantages that cloud computing offers but along with that it introduces
some inherent security isses with it. Databases of cloud scale up and down rapidly in
order to meet the needs of customers, it means that those physical servers that host
databases are provisioned and de provisioned frequently without any earlier knowledge
of consumers. Additionally for achieving high availability and redundancy, the data of
consumers is replicated around many data centers in various locations. These factors lead
to non static environment which have almost no accessibility and visibility to physical
infrastructure of consumers.
4. Data Sanitization: It is another kind of risk related to the physical security is the deletion
of data from storage devices is known as data sanitization. Sanitization of data includes
degaussing, removing data from storage media through overwriting or demotion of data
itself in order to prevent it from unauthorized information disclosure. Additionally
complications increases due to the backups that carried out in cloud environment
regularly in order to ensure high redundancy. There are various examples where
researchers brought utilized drive from online auction in order to retrieve huge amount of
sensitive data from it. Incase data doesn’t removed properly this data can be recovered
later from failed drives by using proper equipments. Hence it is crucial that SLA s should
clear that whether clod providers give enough measurements in order to ensure that data
sanitization is appropriately performs in the entire lifecycle of the system (Sakhi,2012).
8
4. Identity and Access Management in Cloud Environment: Mechanisms
and Challenges
One of the best methods to identify security measures is Identity and access management
(IAM).Recently, IAM is providing efficient security for cloud systems. In order to provide security,
many effective security mechanisms have been introduced by IAM. IAM executes many
operations in cloud environment for achieving security, this includes authorization, verification,
provision of storage and authentication. Security of attribute and identities of cloud users is
guaranteed by IAM system in order to make sure that authorize user are allowed in cloud
system. IAM also assist to maintain rights of access by examining if correct person with right
privileges are retrieving data that is kept in the cloud system. Many organizations are using
systems of IAM currently for sensitive information stored in cloud environment (Vidhyacharan,
2018)
Digital security mechanisms:
1. Credentials and secure shell keys: Credentials are the verification of authority, access right,
entitlements and status. It provides the proof that specific user is granted or deserves to use
services and resources. Credentials are similar to one time password and pattern while
captcha is a conventional way for the securing the system from malicious acts and attacks.
Some common used mechanisms for managing access credentials in cloud environment are
Microsoft Active Directory MAD technologies, AD servers, Lightweight Directory Access
Protocol LDAP are either control by vendors of third party or inside the organizational
network in cloud. When various applications are employed on these conventional credential
mechanism then cloud maintenance overhead will be increased.
2. Multifactor authentication: This is another method to secure transactions and digital
resources over the internet. Specifically patterns or Captchas, One Time Password OTP are
utilized as secondary authentication mechanisms with credentials. An additional layer of
security is given by multifactor over the authentication of traditional credentials. Mostly One
9
and Challenges
One of the best methods to identify security measures is Identity and access management
(IAM).Recently, IAM is providing efficient security for cloud systems. In order to provide security,
many effective security mechanisms have been introduced by IAM. IAM executes many
operations in cloud environment for achieving security, this includes authorization, verification,
provision of storage and authentication. Security of attribute and identities of cloud users is
guaranteed by IAM system in order to make sure that authorize user are allowed in cloud
system. IAM also assist to maintain rights of access by examining if correct person with right
privileges are retrieving data that is kept in the cloud system. Many organizations are using
systems of IAM currently for sensitive information stored in cloud environment (Vidhyacharan,
2018)
Digital security mechanisms:
1. Credentials and secure shell keys: Credentials are the verification of authority, access right,
entitlements and status. It provides the proof that specific user is granted or deserves to use
services and resources. Credentials are similar to one time password and pattern while
captcha is a conventional way for the securing the system from malicious acts and attacks.
Some common used mechanisms for managing access credentials in cloud environment are
Microsoft Active Directory MAD technologies, AD servers, Lightweight Directory Access
Protocol LDAP are either control by vendors of third party or inside the organizational
network in cloud. When various applications are employed on these conventional credential
mechanism then cloud maintenance overhead will be increased.
2. Multifactor authentication: This is another method to secure transactions and digital
resources over the internet. Specifically patterns or Captchas, One Time Password OTP are
utilized as secondary authentication mechanisms with credentials. An additional layer of
security is given by multifactor over the authentication of traditional credentials. Mostly One
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Time Password are authenticated in online transactions. In online financial transactions, one
time password is generated by server by using particular algorithms that are related to its
configuration and produce OTP is sent to the user through email or registered mobile
number.
3. PIN and Chip: Identification Number (PIN) and Chip is a traditional authentication method in
business transactions. This can be utilized for service/machines authentication in an
organization’s network. Asymmetric encryption technology utilizes private and public keys in
order to encrypt and decrypt data that is used in PIN and chip mechanism. For protecting
data from fraud and unethical use, this microprocessor chip save the security keys and data
of user by generating unique data transaction. By using security key that is stored in chip,
communication among terminals with authentication server is signed and encrypted. The
signature is verified and communication is decrypted by using pairing keys that are stored in
server. To authenticate terminal for retrieving keys from chips and data of user, PIN method
is used [13].
5. Service Delivery Models of Cloud Computing: Security Issues and Open
Challenges
Cloud computing appeared as successful technology which is adapted by almost every organization in
recent times for facilitating elasticity in their business in terms of exchange, transform and data storage
that provides them the ability to advance their capabilities, income and interoperability. The network
community enhanced every model of cloud computing that involves public cloud, private cloud, hybrid
cloud and community cloud. Cloud commuting is altering recent IT delivery models for the services. It
advantages IT and business field through facilitating scalability, flexibility, economic, data access on
10
time password is generated by server by using particular algorithms that are related to its
configuration and produce OTP is sent to the user through email or registered mobile
number.
3. PIN and Chip: Identification Number (PIN) and Chip is a traditional authentication method in
business transactions. This can be utilized for service/machines authentication in an
organization’s network. Asymmetric encryption technology utilizes private and public keys in
order to encrypt and decrypt data that is used in PIN and chip mechanism. For protecting
data from fraud and unethical use, this microprocessor chip save the security keys and data
of user by generating unique data transaction. By using security key that is stored in chip,
communication among terminals with authentication server is signed and encrypted. The
signature is verified and communication is decrypted by using pairing keys that are stored in
server. To authenticate terminal for retrieving keys from chips and data of user, PIN method
is used [13].
5. Service Delivery Models of Cloud Computing: Security Issues and Open
Challenges
Cloud computing appeared as successful technology which is adapted by almost every organization in
recent times for facilitating elasticity in their business in terms of exchange, transform and data storage
that provides them the ability to advance their capabilities, income and interoperability. The network
community enhanced every model of cloud computing that involves public cloud, private cloud, hybrid
cloud and community cloud. Cloud commuting is altering recent IT delivery models for the services. It
advantages IT and business field through facilitating scalability, flexibility, economic, data access on
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
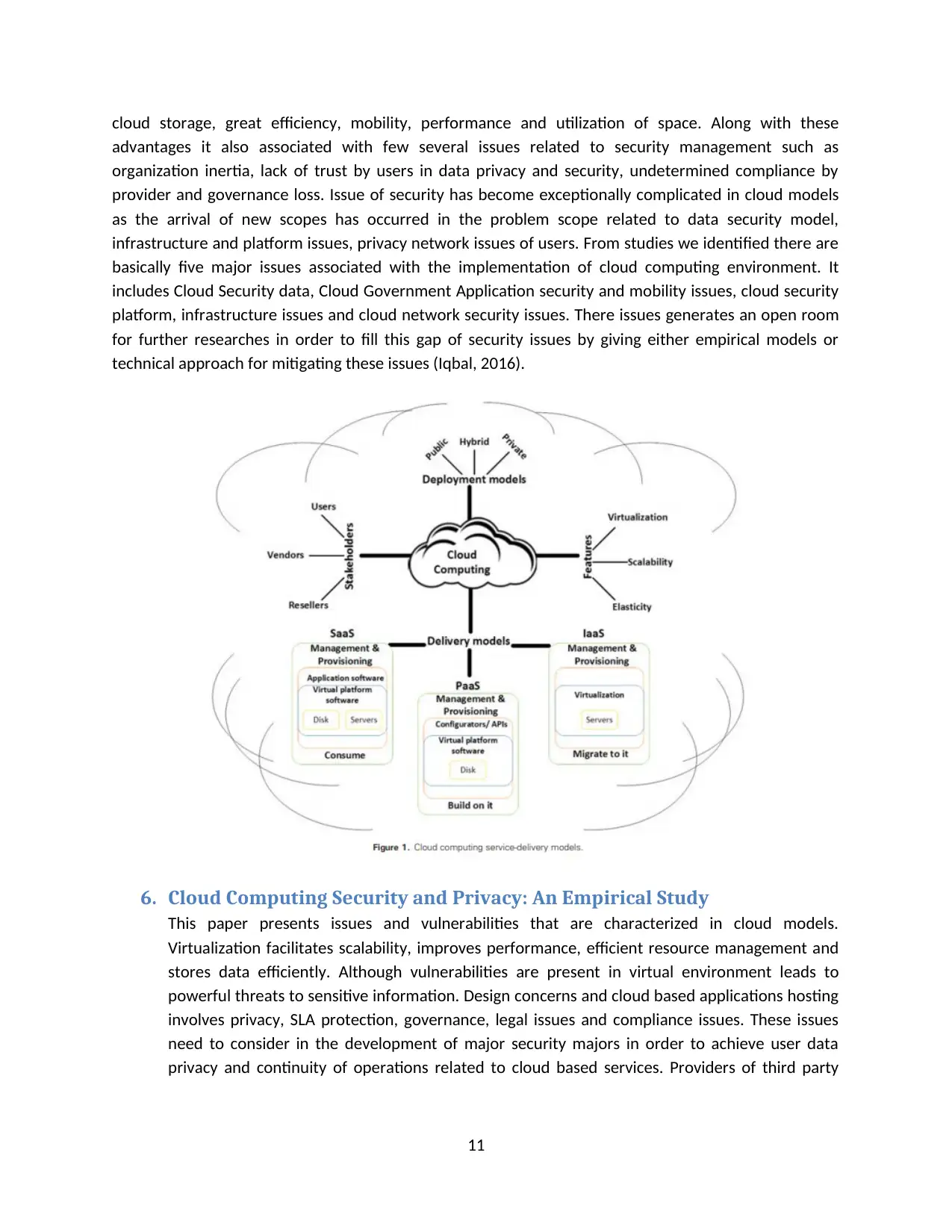
cloud storage, great efficiency, mobility, performance and utilization of space. Along with these
advantages it also associated with few several issues related to security management such as
organization inertia, lack of trust by users in data privacy and security, undetermined compliance by
provider and governance loss. Issue of security has become exceptionally complicated in cloud models
as the arrival of new scopes has occurred in the problem scope related to data security model,
infrastructure and platform issues, privacy network issues of users. From studies we identified there are
basically five major issues associated with the implementation of cloud computing environment. It
includes Cloud Security data, Cloud Government Application security and mobility issues, cloud security
platform, infrastructure issues and cloud network security issues. There issues generates an open room
for further researches in order to fill this gap of security issues by giving either empirical models or
technical approach for mitigating these issues (Iqbal, 2016).
6. Cloud Computing Security and Privacy: An Empirical Study
This paper presents issues and vulnerabilities that are characterized in cloud models.
Virtualization facilitates scalability, improves performance, efficient resource management and
stores data efficiently. Although vulnerabilities are present in virtual environment leads to
powerful threats to sensitive information. Design concerns and cloud based applications hosting
involves privacy, SLA protection, governance, legal issues and compliance issues. These issues
need to consider in the development of major security majors in order to achieve user data
privacy and continuity of operations related to cloud based services. Providers of third party
11
advantages it also associated with few several issues related to security management such as
organization inertia, lack of trust by users in data privacy and security, undetermined compliance by
provider and governance loss. Issue of security has become exceptionally complicated in cloud models
as the arrival of new scopes has occurred in the problem scope related to data security model,
infrastructure and platform issues, privacy network issues of users. From studies we identified there are
basically five major issues associated with the implementation of cloud computing environment. It
includes Cloud Security data, Cloud Government Application security and mobility issues, cloud security
platform, infrastructure issues and cloud network security issues. There issues generates an open room
for further researches in order to fill this gap of security issues by giving either empirical models or
technical approach for mitigating these issues (Iqbal, 2016).
6. Cloud Computing Security and Privacy: An Empirical Study
This paper presents issues and vulnerabilities that are characterized in cloud models.
Virtualization facilitates scalability, improves performance, efficient resource management and
stores data efficiently. Although vulnerabilities are present in virtual environment leads to
powerful threats to sensitive information. Design concerns and cloud based applications hosting
involves privacy, SLA protection, governance, legal issues and compliance issues. These issues
need to consider in the development of major security majors in order to achieve user data
privacy and continuity of operations related to cloud based services. Providers of third party
11
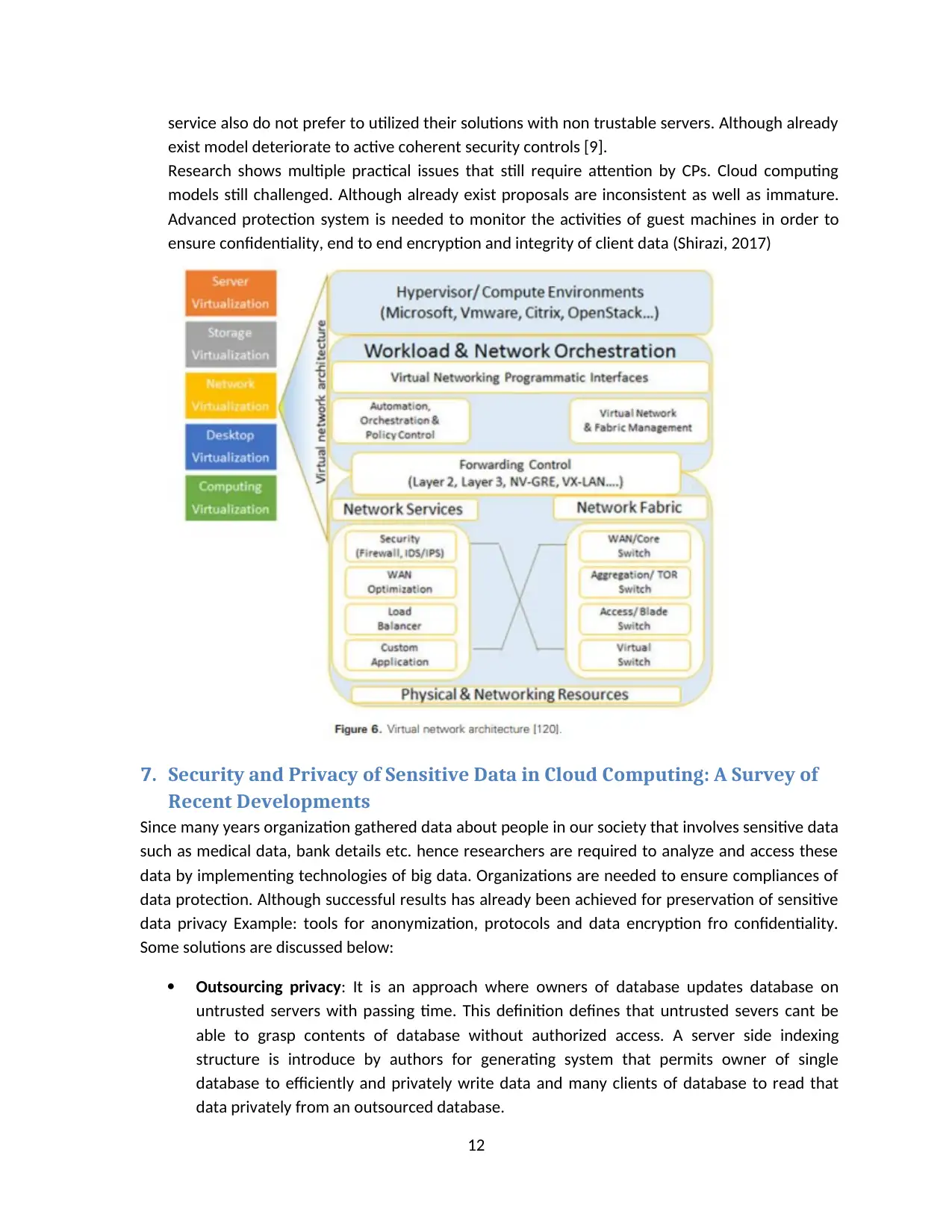
service also do not prefer to utilized their solutions with non trustable servers. Although already
exist model deteriorate to active coherent security controls [9].
Research shows multiple practical issues that still require attention by CPs. Cloud computing
models still challenged. Although already exist proposals are inconsistent as well as immature.
Advanced protection system is needed to monitor the activities of guest machines in order to
ensure confidentiality, end to end encryption and integrity of client data (Shirazi, 2017)
7. Security and Privacy of Sensitive Data in Cloud Computing: A Survey of
Recent Developments
Since many years organization gathered data about people in our society that involves sensitive data
such as medical data, bank details etc. hence researchers are required to analyze and access these
data by implementing technologies of big data. Organizations are needed to ensure compliances of
data protection. Although successful results has already been achieved for preservation of sensitive
data privacy Example: tools for anonymization, protocols and data encryption fro confidentiality.
Some solutions are discussed below:
Outsourcing privacy: It is an approach where owners of database updates database on
untrusted servers with passing time. This definition defines that untrusted severs cant be
able to grasp contents of database without authorized access. A server side indexing
structure is introduce by authors for generating system that permits owner of single
database to efficiently and privately write data and many clients of database to read that
data privately from an outsourced database.
12
exist model deteriorate to active coherent security controls [9].
Research shows multiple practical issues that still require attention by CPs. Cloud computing
models still challenged. Although already exist proposals are inconsistent as well as immature.
Advanced protection system is needed to monitor the activities of guest machines in order to
ensure confidentiality, end to end encryption and integrity of client data (Shirazi, 2017)
7. Security and Privacy of Sensitive Data in Cloud Computing: A Survey of
Recent Developments
Since many years organization gathered data about people in our society that involves sensitive data
such as medical data, bank details etc. hence researchers are required to analyze and access these
data by implementing technologies of big data. Organizations are needed to ensure compliances of
data protection. Although successful results has already been achieved for preservation of sensitive
data privacy Example: tools for anonymization, protocols and data encryption fro confidentiality.
Some solutions are discussed below:
Outsourcing privacy: It is an approach where owners of database updates database on
untrusted servers with passing time. This definition defines that untrusted severs cant be
able to grasp contents of database without authorized access. A server side indexing
structure is introduce by authors for generating system that permits owner of single
database to efficiently and privately write data and many clients of database to read that
data privately from an outsourced database.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



